use policy
advertisement

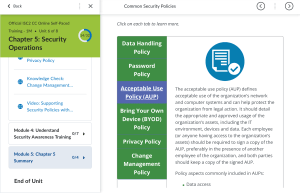
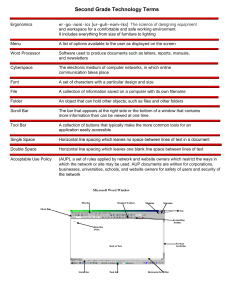
ACCEPTABLE USE POLICY An acceptable use policy (AUP), also known as an acceptable usage policy or fair use policy, is a set of rules applied by the owner or manager of a network, website or large computer system that restrict the ways in which the network, website or system may be used. AUP documents are written for corporations, businesses, universities, schools, internet service providers, and website owners, often to reduce the potential for legal action that may be taken by a user, and often with little prospect of enforcement. Wikipedia • • • • • Jalal Hafidi Mathew Joseph Tolulope Oke Denisa Teme Li Wei OVERVIEW Introduction Objective Roles & Responsibilities Purpose/Scope of Policy Policy Statements User Accounts Computing Assets Network Use Electronic Communications Data Security Enforcements Questions 1 of 12 Introduction This policy regulates the direct and indirect use of Technology resources across our organization. Technology resources = Strategic assets Computer resources and employees Expectations for appropriate use of these resources. 2 of 12 Objective Standard use of technology resources across the organization Familiarization with policy Acceptable use Unacceptable use Formal signature – binding on all employees Original copy and revisions 3 of 12 Roles & Responsibilities • • • • • Users’ Responsibility & Awareness www.mcinc.com/policies Technology Department CIO & CEO Authority & Enforcement 4 of 12 Purpose & Scope of Policy Guidelines for protecting the CIA of MC Inc.’s data Appropriate security requirements and restrictions on the organization’s technology resources Covers all organization’s technology resources 5 of 12 User Accounts Password security (system & user-level) Unique user accounts & access Illegal access to other user accounts Employee responsibility 6 of 12 Computing Assets Organization’s computer system Laptops taken outside of the organization Devices left overnight Loss & theft Password-protected screensavers, locking screens, & logging off External devices Interference 7 of 12 Network Use Copyright material ( illegal software, P2P, etc….) Unauthorized access (accounts, data, servers…) Sharing network passwords Engaging in malicious activities intentionally Using the company’s network for personal use Getting involved in activities causing a disruption of service (DoS for example) Obscene materials 8 of 12 Electronic Communications Use of phone lines Company e-mails E-mail IDs & accounts Foul languages Forgery Negative use of social media 9 of 12 Data Security Proprietary information on personal or non-company approved devices Directories, programs, files, data & documents Confidential data Unauthorized access & misuse to sensitive data Encrypted folders 10 of 12 Enforcement Violations of this Acceptable use policy may result in: Suspension or revocation of account & privileges Disciplinary action as described in the Employees’ Code of Conduct handbook Civil or criminal prosecution under federal and/or state law Penalties under such laws may include fines, orders of restitution, and imprisonment 11 of 12 Questions? Don’t Forget: When in doubt visit www.mcinc.com/policies/aup or take a walk to the Technology department 12 of 12 Contact Us Tel:123-345-7896 help@mc.com THANK YOU