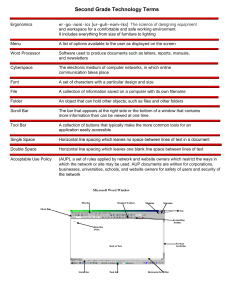
Common Security Policies Back Click on each tab to learn more. Official ISC2 CC Online Self-Paced Training - 1M Unit 6 of 8 14∕32 Chapter 5: Security Operations Data Handling Policy Privacy Policy Knowledge Check: Change Management… Policy Video: Supporting Security Policies with… Procedures Module 4: Understand 0/7 Security Awareness Training Module 5: Chapter 5 Summary End of Unit 0/4 Password Policy Acceptable Use Policy (AUP) Bring Your Own Device (BYOD) Policy Privacy Policy Change Management Policy The acceptable use policy (AUP) defines acceptable use of the organization’s network and computer systems and can help protect the organization from legal action. It should detail the appropriate and approved usage of the organization’s assets, including the IT environment, devices and data. Each employee (or anyone having access to the organization’s assets) should be required to sign a copy of the AUP, preferably in the presence of another employee of the organization, and both parties should keep a copy of the signed AUP. Policy aspects commonly included in AUPs: Data access