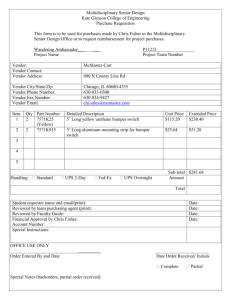
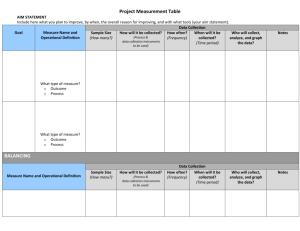
Control Balancing in Information Systems Development Offshoring
advertisement

1 Control Balancing in Information Systems Development Offshoring Projects Robert Wayne Gregory Roman Beck University of Göttingen Goethe University Frankfurt Platz der Göttinger Sieben 5 Grüneburgplatz 1 37073 Göttingen, Germany 60323 Frankfurt, Germany gregory@wiwi.uni-goettingen.de rbeck@wiwi.uni-frankfurt.de Mark Keil Georgia State University Robinson College of Business 35 Broad Street Atlanta, GA 30303, USA mkeil@gsu.edu WORKING PAPER VERSION, ACCEPTED FOR FORTHCOMING PUBLICATION IN MANAGEMENT INFORMATION SYSTEMS QUARTERLY 2 Control Balancing in Information Systems Development Offshoring Projects1 Abstract: While much is known about selecting different types of control that can be exercised in systems development (ISD) projects, the control dynamics associated with ISD offshoring projects represents an important gap in our understanding. In this paper, we develop a substantive grounded theory of control balancing that addresses this theoretical gap. Based on a longitudinal case study of an ISD offshoring project in the financial services industry, we introduce a three-dimensional control configuration category that emerged from our data, suggesting that control types is only one dimension in which control configuration decisions need to be made. The other two dimensions that we identified are control degree (tight vs. relaxed) and control style (unilateral vs. bilateral). Furthermore, we illustrate that control execution during the lifecycle of an ISD offshoring project is highly intertwined with the development of clientvendor shared understanding and that each influences the other. Based on these findings, we develop an integrative process model that explains how offshoring project managers make adjustments to the control configuration periodically to allow the ISD offshoring project and relationship to progress, yielding the iterative use of different three-dimensional control configurations that we conceptualize in the paper. Our process model of control balancing may trigger new ways of looking at control phenomena in temporary inter-firm organizations such as client-vendor ISD offshoring projects. Implications for research on organizational control and 1 An earlier version of this paper appeared in the Proceedings of the International Conference of Information Systems (ICIS). The full citation is Beck, R.; Gregory R.W.; Prifling, M. (2008) Cultural Intelligence and Project Management Interplay in IT Offshore Outsourcing Projects. ICIS; Paris, France. The ‘cultural intelligence’ aspect of the ICIS paper was further developed and appeared in Information Technology & People (IT&P). The full citation is Gregory, R.W.; Prifling, M.; Beck, R. (2009) The Role of Cultural Intelligence for the Emergence of Negotiated Culture in IT Offshore Outsourcing Projects. IT&P, Vol. 22, No. 3, pp. 223-241. 3 ISD offshoring are discussed. In addition, guidelines for ISD offshoring practitioners are presented. Keywords: Control Balancing, Control Dynamics, Organizational Control, Information Systems Development, Offshoring Projects, Outsourcing Relationships, Longitudinal Case Study, Grounded Theory, Process Model, Project Management 4 Control Balancing in Information Systems Development Offshoring Projects INTRODUCTION Information systems development (ISD) offshoring continues to grow in importance as a means to exploit differences (e.g., labor costs, time zone, available expertise) across countries (Ghemawat 2007; Sarker and Sarker 2009). Offshoring is a subset of the broader global information systems (IS) outsourcing industry, which was estimated by Gartner in 2012 to be worth $309 billion. The challenges associated with ISD outsourcing are well documented, and statistics suggest that only 63 percent of IS outsourcing projects are successful (Lacity and Willcocks 2012). Critical for achieving IS outsourcing success is effectively controlling projects and relationships, which is extremely difficult in this context (Tiwana and Keil 2009) due to outsourcing-specific challenges, such as developing client-vendor shared understanding (Rai et al. 2009). These challenges are arguably even greater when the outsourcing involves an offshore vendor. Thus, more research is needed on how to exercise control effectively in such projects. Prior IS research on control has largely focused on why and under which circumstances specific controls (e.g., monitoring an ISD task), control modes (e.g., behavior control), or control types (e.g., formal control) are selected and used (e.g., Kirsch 1996), how controls are combined into a portfolio (e.g., Kirsch 1997), how different control types interact at the portfolio level (e.g., Maruping et al. 2009; Tiwana 2010), and how the use of controls impacts performance (e.g., Henderson and Lee 1992; Tiwana 2008). Comparatively less research attention has been placed on the dynamics of control, although there has been some work on how portfolios of control change over time across different phases of an IS project (e.g., Kirsch 2004). 5 In general, prior research on control can be characterized as having a one-dimensional focus on the construction of control portfolios and a unidirectional perspective on the relationship between project- or relationship-related events and the triggering of changes in the control portfolio. Indeed, in one of the few studies to examine control dynamics in outsourced software development projects, Choudhury and Sabherwal (2003) focused on how certain events trigger changes in the portfolio of controls and not on the dimensions of control use or the interrelationship between control behavior and the client-vendor relationship. Accordingly, there is a theoretical gap regarding the dimensions of control that must be managed over time and the reciprocal nature of the relationship between control use and the client-vendor relationship. To address this theoretical gap, we studied control behavior in a large offshore outsourced ISD project for several years. Our data directed us toward the notion of ‘control balancing,’ which we define as making adjustments to the control configuration periodically in terms of control types, control degree, and control style, to allow the ISD offshoring project and relationship to progress. The image of balancing is used as a metaphor for finding the appropriate configurations along these three control dimensions that will allow the ISD offshoring project and relationship to progress without toppling over. We identified three control configurations from our data: (1) authoritative control, which is based on a traditional outsourcing perspective with clear boundaries between ‘client’ and ‘vendor,’ (2) coordinated control, in which client and vendor work toward shared goals, and (3) trust-based control, grounded in shared understanding. Just as a gymnast on a balance beam must recurrently shift her weight in order to keep from falling while executing her performance, a project manager must make adjustments to the control configuration periodically and shift between these three control configurations in order to maintain the delicate balance that allows the project and relationship to move forward. Based on the dynamics observed in our case study, we developed a process model of control balancing that 6 explains the dimensions of control use and the dynamic interaction between control configurations and the ISD offshoring relationship. We construct a theory of control balancing in ISD offshoring that explains what needs to be balanced (i.e., what factors should be considered for explaining control balancing?), how control balancing occurs (i.e., how are the factors related and what are the dynamics over time?), and why control balancing matters (i.e., why is this an important phenomena and what are the implications?). We begin with the theoretical background in which we present what is known about control portfolios, their evolution, and control balancing in organizational and IS management. In the methods section that follows, we describe our research design. Following this, we present our case analysis and the theory that emerged therefrom. We conclude with a discussion of findings in the light of existing literature, present practical and theoretical implications, and provide directions for future research. THEORETICAL BACKGROUND Control in IS Outsourcing and Offshoring In order for organizations, including temporary organizations such as projects, to achieve their objectives, some type of strategy must be implemented that “effectively controls members’ activities in a manner functional for the organization” (Barker 1993, p. 409). Ouchi (1977; 1979; 1975) proposed one of the most widely adopted control frameworks, which focuses on formal behavioral and outcome controls as well as informal clan controls. An extension of this framework to the context of IS projects was proposed by Kirsch (1996; 1997), who built upon this work as well as related studies (e.g., Henderson and Lee 1992). More recently, controlling IS outsourcing and offshoring projects has become an important area of inquiry for IS researchers. Table 1 summarizes this stream of research. 7 Study Context Focus Findings (Choudhury and Sabherwal 2003) Outsourced ISD projects Evolution of portfolios of formal and informal controls and factors influencing the choice and evolution of controls At the start of the project, control portfolios are dominated by formal outcome controls, influenced by the client’s perception of the controllee’s knowledge, the consequent role expectations, and perceptions of difficulty in monitoring vendor behavior. Later in the project, formal behavior controls and informal controls are added to the portfolio, influenced by vendor performance. (Gopal and Gosain 2010) Outsourced ISD projects The role of boundary spanning between the vendor and client for the performance effects of formal and informal controls Both formal and informal controls have positive performance impacts. In addition, boundary spanning moderates the impacts of outcome controls on software quality and project efficiency and the impacts of behavior controls on project efficiency, such that as the level of boundary spanning increases, the relationship between outcome/behavior controls and the respective outcomes is strengthened. (Heiskanen et al. 2008) Public-sector outsourced ISD projects Co-evolution of control and trust during relationship development The public sector client’s actions oscillate between trust and control during the course of relationship development in three areas: performance, price level, and observed behavior. (Rustagi et al. 2008) Outsourced IS projects (i.e., applications, infrastructure, or business processes) Amount of formal control Clients with technical or relationship management knowledge or who highly trust their vendors, use lower amounts of formal control. However, the amount of formal control generally increases with higher levels of task uncertainty. (Tiwana and Keil 2007) Outsourced ISD projects The role of specialized knowledge in the domain of outsourced activities, i.e., ‘peripheral’ knowledge, for control execution Peripheral knowledge increases the positive performance impacts of formal outcome controls, but not formal process controls. (Tiwana 2008) Outsourced ISD projects The role of intentional decoupling of interoperating subsystems of a larger system, i.e., technological modularity, for control execution Technological modularity lowers the positive performance impacts of formal process controls, but not formal outcome controls. (Tiwana and Keil 2009) Internal and outsourced ISD projects Differences in the use and effectiveness of control mechanisms in internal versus outsourced ISD projects Control mechanisms are used to a greater extent in outsourced projects relative to internal projects. However, formal controls do not enhance outsourced ISD project performance and the positive impact of informal controls depends upon the level of requirements volatility. (Tiwana 2010) Outsourced ISD projects Relationship and interactions between formal and informal control mechanisms in a project’s control portfolio The combination of informal controls with formal process-based controls simultaneously enhances the fulfillment of project goals and development flexibility. However, combining informal controls with formal outcome-based controls can impair these objectives. Table 1: Overview of existing research on control in IS outsourcing and offshoring In summary, prior research on control in IS outsourcing and offshoring contexts has focused on formal and informal controls, including their choice, amount, interactions, performance impacts, factors that moderate the relationship between control and performance, and the evolution of control portfolios over time. In contrast, what is lacking is research on the different dimensions of control use and the reciprocal effects of control behavior on the client vendor relationship in an 8 ISD offshoring project. Furthermore, our understanding of the dynamics and evolution of organizational control in general is limited. Control Balancing in Organizations In organizational management research, Barker’s (1993) analysis of self-managed teams was one of the first studies to examine the evolution of control. His study illustrated the dynamic nature of organizational control, which motivated further longitudinal research in this area. Choudhury and Sabherwal (2003) investigated the dynamics of control in offshore outsourced ISD projects and found that during the course of such projects, portfolios of formal and informal controls change over time (see Table 1). Kirsch (2004) investigated the dynamics of control in IS projects where common systems are deployed globally. She found that control choices in such projects change across project phases due to changes in in the project context (e.g., poor project performance), the stakeholder context (e.g., changing role expectations), and the global context (e.g., challenges arising from cultural differences). More recently, Heiskanen et al. (2008) examined the evolution of trust and control during the process of client-vendor relationship development in the context of public sector ISD outsourcing. They found that the public sector client’s actions oscillated between trust and control during the course of relationship development (see Table 1). A relatively underexplored, yet highly relevant concept that has found its way into the organizational control literature is the notion of ‘balance.’ The basic idea is that different combinations of controls are needed depending upon the context and that a control portfolio that is balanced to suit a particular context is going to be more effective than one that is not (Bradach and Eccles 1989). Within organizations, the need for balancing results from an increasingly turbulent and dynamic business environment (Eisenhardt et al. 2010; Smith and Lewis 2011). Applying the notion of balance to organizational control, Cardinal et al. (2004) examined the evolution of control and found evidence for a repetitive balance-imbalance-rebalance sequence in 9 which balance is defined as “a state where an organization exhibits a harmonious use of multiple forms of control” (Cardinal et al. 2004, p. 412). Despite these important theoretical advancements, research on control balancing in organizations is still in its infancy (Long and Sitkin 2006; Sitkin et al. 2010). Thus, we have only very limited understanding about the nature and characteristics of control balancing in temporary organizations (e.g., IS projects) and clientvendor relationship contexts. RESEARCH METHODOLOGY We conducted a longitudinal single-case study to analyze the management and control of an ISD offshoring project. Given the scarcity of research on the dynamics of control in ISD offshoring (King and Torkzadeh 2008), our goal was to build grounded theory with case study research (Urquhart et al. 2010). The case we studied involved a German bank that was offshoring development work to India. This case was particularly suitable for investigating the phenomenon of interest because it afforded an opportunity to conduct a longitudinal analysis of the management of the project including both client and vendor perspectives. Primary and Secondary Data Primary data collection consisted of 56 interviews conducted between April 2007 and August 2011, with both client and vendor representatives in Germany and India respectively. For the interviews in Germany, we took extensive notes and transcribed them immediately after each interview session (Walsham and Sahay 1999). The interviews conducted in India were taperecorded and transcribed. A typical interview lasted 1.5 hours, although we also had ‘long interviews’ in the very beginning of the research process that lasted up to three hours and short follow-up interviews of less than an hour in later stages of our research. Interviews were conducted in an open-ended and unstructured manner initially and became semi-structured over 10 time in accordance with the development of our grounded theory. Similarly, data sampling was closely aligned with our analysis and emergence of theory (Urquhart et al. 2010). Our primary data collection was complemented by observations and informal face-to-face discussions during our field research in Germany and India (see Table 2). Type of primary data Description of primary data 56 interviews Role of interviewee # of interviews with client employees # of interviews with vendor employees # of interviews in total Project manager/leader 21 11 32 Project team member 6 11 17 Business/functional management 3 2 5 Top IT management 2 0 2 Total # of people interviewed 22 22 44 Total # of interviews (some people were interviewed more than once) 32 24 56 >300 pages of notes and memos based on fieldwork Extensive notes were taken during field visits to capture observations, impressions, results of informal discussions and meetings. Analytic memos were also crafted based on our reading of the data. These captured joint reflections that were made within the research team as we combed through the interview notes and transcripts and discussed the data. In total, more than 300 pages of notes and memos were created during the analysis process from 2007 to 2011. Table 2: Primary Data Consisting of Interviews and Fieldwork In addition, for triangulation purposes, secondary data was collected and analyzed (see Table 3). Type of secondary data Description of secondary data 21 steering committee meeting presentation slides, each consisting of 20-50 slides Contained information that was reported on a quarterly basis from the IT department to the business and IT top management stakeholders. This information included among other things status reports about the project and the relationship as well as critical issues that required top management attention. This information helped in reconstructing the evolution of events and activities in the project. 8 sets of project management slides, including 5-30 slides each Project management slides included information on escalation paths, client-vendor communication plans, project reviews, kick-off presentation slides, business case presentation slides, and project member matrices. This project documentation helped in understanding the context and the characteristics of the project and the nature of the client-vendor relationship. Table 3: Secondary Data that was Collected and Analyzed for Comparisons with Primary Data Data Analysis and Research Process Our methodology for investigating the case was ‘pluralist,’ meaning that we engaged in a variety of interrelated research activities which are summarized in Table A1 in the Appendix (Mingers 2001, p. 245). We adopted a critical realist stance in the sense that ontologically we assumed the existence of an independent reality and from an epistemological perspective we sought to “posit 11 descriptions of reality based on an analysis of the experiences observed and interpreted by the participants, along with other types of data” (Wynn and Williams 2012). Our approach was also consistent with Mingers (2004) who advocates a pragmatic approach in which researchers embrace different research perspectives with the aim of generating “a useful model of reality” (Van de Ven 2007, p. 59). We also followed the principle of ‘emergence’ from grounded theory: grounded theory must ‘fit,’ the data under study, and it must meaningfully explain the behavior under study (Glaser and Strauss 1967, p. 3). In addition, techniques were selected and used that helped us increase the theory’s scope and the degree of conceptualization (Urquhart et al. 2010). Our research process started with formulating the problem (Van de Ven 2007), designing the case study (Yin 2003), and engaging in intertwined data collection and analysis for building grounded theory, i.e., theorizing from our data by developing abstract categories and specifying the relations between them (Bryant and Charmaz 2007). In coding for theory generation, an important technique in grounded theory (Urquhart 2001; Urquhart 2007), we were guided primarily by Glaser’s approach to the Grounded Theory Method (Glaser 1978; Glaser 1992). The table in Appendix A illustrates in detail the coding and data analysis process. For pragmatic reasons, i.e., “in order to participate in the current theoretical conversation” (Lempert 2007, p. 254) and for “relating the theory to other theories in the same or similar field” (Urquhart et al. 2010, p. 369), we gradually conducted an extensive literature review (see Table 4). Type of Literature Review Criterion for Literature Selection and Examples Scope of Literature Review and Extant Knowledge Engagement Goals of Literature Review Problem domain literature review Literature related to the problem domain of our study, i.e., managing ISD outsourcing/ offshoring projects and relationships (e.g., Dibbern et al. 2008; Koh et al. 2004; Levina and Vaast 2008; Rai et al. 2009) Identification of >200 and careful reading of approx. 40 works Presentations at >10 workshops (e.g., Global Sourcing Workshops and IS conferences (e.g., ICIS)) Identification of domain literature gaps Selection of case study Domain literature integration Theoretical domain literature review Literature related to the theoretical domain of our study, i.e., organizational control (e.g., Cardinal et al. 2004; Choudhury and Sabherwal 2003; Kirsch 1997; Kirsch 2004; Tiwana 2010; Tiwana and Keil 2007) Identification of >300 and careful reading of approx. 60 works Participation in related research projects operating in the same theoretical domain Identification of theoretical gaps Definition of research question(s) Theoretical integration Meta- Non IS conceptual literature that increases Identification and screening of ~10 Scaling up grounded 12 theoretical literature review theoretical sensitivity and supports theorization, i.e., the notion of balancing in organizations (e.g., Bradach and Eccles 1989; Eisenhardt et al. 2010; Smith and Lewis 2011; Sundaramurthy and Lewis 2003) potentially interesting metatheoretical concepts and lenses prior to the selection of ‘balancing’ as core lens to conceptualize data theory Increasing theory’s scope and facilitating conceptualization Table 4: Role and Use of Theory or Extant Literature in our Study During our research and analysis process, we also gave special attention to the sequencing of events and delineating control phases (stable states of a particular control configuration) from triggering conditions (i.e., the conditions that led to a change in the control configuration) (Langley 1999; Mohr 1982; Van de Ven 2007). Finally, we integrated our theoretical results into the theory and problem domain literatures. BRIEF CASE DESCRIPTION Our case involved a 5-year-long project between a German client and an Indian vendor in the financial services industry. The project involved the technical reengineering and integration of a core banking system used for daily financial transactions worth billions of Euros. This system consisted of two distinct transaction processing systems (TPS) with overlapping functionality, i.e., a 25-year-old TPS focused on checking accounts with 1.3 million lines of code operating on a batch-processing architecture, and a 7-year-old TPS focused on payment with 4.5 million lines of code operating on a real-time processing architecture. Specific goals of the project included the elimination of function and data redundancy, the reduction of system complexity, and avoiding further dependency on key knowledge (e.g., about old programming languages) for which it would be difficult to recruit new people to replace retiring specialists. The endeavor required more than 170 project members and the overall project manager compared it to a heart surgery due to its high level of risk and criticality to the business. To accomplish it, the bank outsourced approximately 60% of the project work to a Capability Maturity Model Integration (CMMI)-5 certified offshore service provider from India which was contracted on a fixed-price basis. CASE ANALYSIS RESULTS: CONTROL BALANCING IN ISD OFFSHORING 13 Gradually, the research process summarized above directed us toward the notion of ‘control balancing.’ As a result, we decided to embark on a journey to develop a grounded theory of control balancing in ISD offshoring, which we present in this paper. We start our theory development by discussing key assumptions and boundary conditions. Assumptions and Boundary Conditions Our examination of control balancing in ISD offshoring was based upon certain assumptions that both guided our theory development and set the boundary conditions for the application of our theory (Bacharach 1989). One of our assumptions was that there cannot be a single best control configuration that holds across all phases of a project and that control configurations must change over time. Another assumption was that offshoring relationships evolve over time due to differences in work practices, barriers to knowledge transfer, and cross cultural challenges. Finally, we focused on inter-organizational control as opposed to intra-organizational control under the assumption that in the offshore outsourcing context, it is the client-vendor dyad that shapes the context for control. The boundary conditions of our theory are set by the above assumptions as well as both the organizational and project context of our study. Specifically, our theory is grounded in a 5-yearlong project between a German client and an Indian vendor in the financial services industry. The project involved the technical reengineering of a core banking system and the task required more than 170 project members. A Capability Maturity Model Integration (CMMI)-5 certified offshore service provider from India was contracted on a fixed-priced basis to outsource approximately 60% of the project work. Particular organizational characteristics that need to be considered when applying our theory to new contexts include the large size of the project, the long duration of the project, the complexity and risk of the core banking system reengineering task, the German- 14 Indian offshoring relationship context, the selective outsourcing arrangement in which client and vendor distributed the workload almost evenly, the fixed-priced contract, and the special commitment of the vendor to enter into the German market. Core Category and Related Concepts To develop a shared vocabulary for the subsequent process analysis of our case, we start the development of our grounded theory by introducing and defining the core category ‘control balancing’ that we developed from our data. This category explains what needs to be balanced in terms of control in ISD offshoring projects and depicts along which dimensions control configurations are changed over time in ISD offshoring projects. Accordingly, we define control balancing as making adjustments to the control configuration periodically in terms of control types, control degree, and control style, to allow the ISD offshoring project and relationship to progress. The three dimensions of control balancing decisions that emerged from our data are explained and defined in Table 5, together with codes and indicators that illustrate their emergence from our data as well as properties and associated ranges of each dimension. Dimension Definition / Meaning Properties / Ranges (control configuration level) Control types Refers to the selection of control mechanisms for the control portfolio, which can be of a procedural type, i.e., oriented toward improving efficiency and effectiveness, social type, i.e., oriented toward developing shared understanding, or hybrid, i.e., serving both goals simultaneously - goal orientation (relatively procedural – relatively social) - Procedural controls (e.g., status reviews, definition of roles and responsibilities, tracking project milestones) - Social controls (e.g., information exchange, socialization activities, intercultural workshops) - Hybrid controls (e.g., site visits, reflection-in-action sessions, common understanding workshops) Control degree Refers to the degree of control use, which can vary from tight, i.e., high amount of control in terms of a large overall number of controls used simultaneously and/or a high frequency of control execution, usually paired with a high intensity of control use, to relaxed, i.e., low amount of control in terms of a small number of controls used simultaneously and a low frequency of control execution, usually paired with a low intensity of control use - amount: number (large – small) - - amount: frequency (high – low) - intensity (high – low) Codes / Indicators (Selection) Multiple control use Amount of control Control desire Control completeness Ability to let go Excessive control Frequency of control use Relaxed control attitude Exerting pressure with control Intensity of control Focus on control 15 Control style Refers to the style of control use, which can vary from unilateral, i.e., focus on one party (typically the client) controlling the other party (typically the vendor) in a onesided manner without emphasizing mutual agreement and with a clear separation of controller/controllee roles, to bilateral, i.e., focus on the client and the vendor using control mechanisms jointly with an emphasis on mutual agreement of control selection and use, resulting in blurring boundaries between controller/controllee roles - role ambiguity (high – low) - use of controls (jointly – one-sided) - mutual agreement (strong – weak) - Agreement with control Controller vs. controllee roles Mutual control use Control direction Control harmony Control coordination Perceived control necessity Joint control use One-sided control use Control perception Table 5: Dimensions of the Core Category Control Balancing By examining the changing three-dimensional control configurations and recurrent control balancing decisions over time in our case, we realized that control balancing decisions in ISD offshoring drive and are driven by shared understanding in the client-vendor relationship. In Table 6, the four areas of shared understanding that emerged from our data when examining control balancing behavior over time are defined and explained, together with codes and indicators from our data. Areas of Shared Understanding (SU) Definition / Meaning Codes / Indicators (Selection) Project processes (SU1) Shared understanding about project processes refers to mutual agreement about project goals, objectives, and tasks, as well as operational approaches, processes, and procedures for achieving them - Business-functional knowledge (SU2) Shared understanding about business-functional knowledge refers to joint knowledge about the client’s business application domain, the client’s systems, IT infrastructure, and the functional requirements - Mutual expectations (SU3) Shared understanding about mutual expectations refers to negotiated views and consensus about mutual expectations, roles and responsibilities, as well as their fulfillment - Roles and responsibilities residing with the client and the vendor - Distribution of workload between client and vendor in each phase and task area - Expectations fulfillment or nonfulfillment - Unrealistic expectations - Clarifying and communicating expectations - Adaptation of expectations - Clear separation of client and vendor responsibilities - Shared client and vendor responsibilities Reengineering goals and objectives Project milestones and timelines Project phases, sub-projects, and work streams ISD approaches Project methodology Initial requirements gathering Functional specifications Technical specifications Coding Unit test / component integration test / quality control test / integration test / user acceptance test - Configuration / rollout Financial services industry domain knowledge Understanding of client’s business and processes Functionality of client’s systems Functional requirements Business consequences of systems failure Understanding risk of core banking reengineering Client-specific and banking-specific terminology Implications of systems shutdown 16 - Development of shared expectations Social practices (SU4) Shared understanding about social practices refers to shared views and compromises about social communication and work practices, resulting from mutual behavioral adaptation - Openness / frankness / transparency of communication Discussion and consensus finding Communication of problems and issues Handling of software documentations Motivation to learn new social practices Style of asking questions Punctuality / time attitude Perfectionism Role of family Respect Aloofness Accommodation and avoiding disagreement Planning / risk averseness Hierarchy and status boundaries Negotiated culture Mutual learning and adaptation Table 6: Areas of Shared Understanding Relevant to Control Balancing in ISD Offshoring The introduction of these foundational definitions and conceptualizations provides the necessary vocabulary to explain the process of control balancing in ISD offshoring projects, based on our longitudinal case analysis. In the case presentation and analysis that follows, we characterize the evolution of control balancing as proceeding through four phases involving three distinct control configurations. While the particular phases and trajectory that we observed may be case specific, we believe that the three control configurations can be generalized to other contexts. Control Balancing Phase 1: Coordinated Control Client and vendor in our case initially implemented a control configuration that we call coordinated control (summarized in Table 7). Phase Triggering Conditions Control Balancing Decisions Consequences Phase 1: Coordinated control Gaps in shared understanding Need to reach an agreement on joint project processes (SU1) Need to transfer businessfunctional knowledge (SU2) Need to clarify mutual expectations (SU3) Need to deal with differences in social practices (SU4) Combination of procedural controls (operational process documents, formal communication plan, mirror structure), social controls (socialization activities outside of work, intercultural workshops), and hybrid controls (common understanding workshops), resulting in a hybrid control portfolio Tight control degree: High amount of control Bilateral control style: Focus on Development of good working relationships in various client-vendor work streams and sub-projects based upon mutual agreement about joint project processes (SU1), negotiated mutual expectations (SU3), and a perceived good level of shared social practices (SU4), as well as joint business-functional 17 joint control based on mutual agreement of control selection and use knowledge (SU2) Table 7: First Phase of Control Balancing in Our Case When the project started in late November 2004, client and vendor faced a situation of sharing only a minor relationship history with significant gaps in shared understanding. Joint processes for working together in the project had to be established (SU1) and mutual expectations had to be clarified (SU3) as this project was the first major engagement between the client and the vendor. A fixed-price contract had been negotiated during the 9 months prior to project kick-off in which high-level expectations had been already clarified, but they had to be translated into operational roles and responsibilities on the project timeline. In addition, the vendor program manager explained the need to deal with differences in social practices (SU4): “What I recognized as one of the major challenges, which we had to handle upfront…this was one of the units in [name of client], which had not been exposed to outsourcing at this scale before…and all of a sudden so many Indians arrive [laughs] and you [the Germans] don’t know how to deal with them.” While the vendor did have prior experiences in the U.S. and European financial services industry, working together with German clients was relatively new for them. More importantly, the task of reengineering a 25-year-old legacy and core banking system of this magnitude and size was also new to the vendor and business-functional knowledge had to be transferred (SU2). These antecedent conditions triggered coordinated control: “We [client and vendor] realized early on that we both had a strong interest in this project and that the complexity of the project, requiring deep technical and business-functional knowledge, required intensive cooperation…we knew we could only do this together…the first thing we did was to decide jointly on a number of mechanisms to get the relationship going.” [client program manager] Even before the first vendor team members arrived in Germany, the client and the vendor planned and coordinated the first coordinated control configuration: 18 “We asked ourselves the question: How can we bring the team up to speed early on, clarify and explicate mutual expectations, and create an effective shared operational plan? We coordinated our first actions closely with [name of vendor]-management. One of the things we discussed was that we needed joint workshops in the beginning to establish common understanding, a joint working model, and deal with cultural differences.” [client chief architect] Accordingly, the above explained gaps in shared understanding triggered client and vendor to implement both procedural controls (e.g., formal communication plan involving regular project status meetings, sub-project reviews, steering committee meetings and operational process documents documenting and tracking goals, roles, and responsibilities), social controls (e.g., socialization activities outside of work and ‘intercultural’ workshops to foster shared understanding about mutual social practices), and hybrid controls (e.g., ‘common understanding’ workshops involving discussions about project methodology, templates, coordination tools, as well as configuration and release management), resulting in a hybrid control portfolio. Furthermore, all control mechanisms were planned, coordinated, and implemented jointly, which was the consequence of the bilateral control style decision to foster mutual cooperation early on in the relationship. Finally, the control degree was relatively tight. This is illustrated by the relatively high amount of control in this first phase, particularly in terms of the overall number of controls used simultaneously. The main effect of coordinated control was the “development of good working relationships between client and vendor personnel” [excerpt from the steering committee meeting slides after 3 months of cooperation], which was based mainly upon mutual agreement about joint project processes (SU1) and negotiated mutual expectations (SU3). In addition, both client and vendor thought they had reached a fairly good level of shared understanding about social practices (SU4) and business-functional knowledge (SU2). However, what both client and vendor senior 19 management did not realize at that point in time were the persistent business-functional knowledge gaps (SU2): “They [client members] gave us unimaginable amounts of raw software code and related documentation … they expected us to analyze the old software to derive functional requirements and translate them into technical requirements for the new software which from our point of view was simply not possible.” [vendor project manager] While knowledge gaps (i.e., about the client’s business application domain, the client’s systems, IT infrastructure, and the functional requirements) were the main reasons for the challenges that were to follow, persistent differences in social practices (SU4), especially those relating to communication, exacerbated the situation. For example, the vendor preferred agreement over conflict while client project members emphasized open and frank communication, even if conflictive discussions would result. As a result of these and other differences, there were misunderstandings and subsequent heated discussions to clarify them which hampered further shared understanding development. When the first software deliveries and test results were produced, it became clear that things were not developing as expected and the client sensed that their initial expectations had been somewhat unrealistic. Control Balancing Phase 2: Authoritative Control The challenges explained above relating to shared understanding in the client-vendor relationship, which occurred in spite of careful control balancing decisions and a coordinated control configuration, culminated in unmet expectations (SU3). The client architecture lead commented on his experiences from the time when the project approached its first deadlines in mid-2005: “Something was always delivered to a certain deadline, even if they [vendor developers] had to work throughout the whole night. But what was delivered usually did not meet our expectations. We had to invest a lot of additional resources to rework what was delivered.” 20 Mutual expectations also remained unfulfilled from the vendor’s point of view who had expected more efforts on behalf of the client to help build up the necessary business-functional knowledge. For example, parts of software code had German language comments and many banking-specific or even client-specific concepts that were difficult to understand for an external vendor. Unfulfilled expectations brought significant shortcomings in shared understanding to the surface and triggered control balancing decisions, resulting in an authoritative control phase (Table 8). Phase Triggering Conditions Control Balancing Decisions Consequences Phase 2: Authoritative control Unfulfilled expectations (SU3) Project goals and timeline threatened Need to emphasize more procedural efficiency and effectiveness Need to increase the pressure on the vendor Control portfolio dominated by procedural controls (status reviews, inspection of documentations and reports, testing deliverables, tracking goals and milestones) Tight control degree: high amount of control paired with a high intensity of control use Unilateral control style: focus on the client controlling the vendor without emphasizing agreement Increase in project effectiveness at the expense of shared understanding deterioration (SU3) Conflicts and communication breakdown Shared understanding in the offshoring relationship deteriorates, leading to further unfulfilled expectations => vicious cycle Table 8: Second Phase of Control Balancing in Our Case The reasoning behind this shift to authoritative control was explained to us by a senior client project manager: “The use of this sort of authoritative control approach was triggered by quality or time issues. Sometimes we were still on time, but the quality was miserable which is when we got disappointed with the vendor who delivered just ‘something’ to the deadline. Then our status light turned red which alarmed us and so we needed to change something. Our reaction was: we need to control the vendor more tightly. We consciously sent out a signal that there were unacceptable issues with the deliverables.” Accordingly, gaps in shared understanding could not be closed on a consistent basis, leading to vendor deliverables that did not fulfill the client’s expectations and that posed a threat to the ontime achievement of the project’s goals and objectives with the expected quality. This further alarmed the client and led to the perception that an even tighter degree of control was needed and that the pressure on the vendor needed to be increased. This was done by emphasizing procedural efficiency and reminding the vendor that they were responsible for delivering results. As a 21 consequence, the control degree was tightened by increasing further the amount of control (in particular the frequency with which controls were used) as well as by focusing even more attention and resources to rigorous and intensive control as illustrated by the following quotes: “You need to control everything yourself, even a test document. Nothing, but really nothing can be accepted without control.” [client architecture lead] “Very detailed control was the important thing. At the end of the day you needed to inspect every single thing…that was more important than anything else.” [client project manager] The client program manager even explained that at times certain control mechanisms such as status reviews were used on a daily basis to control more tightly. In addition, consciously sending out a signal to the vendor by controlling deliverables more intensively illustrates the decision for a more unilateral control style, which is also a characteristic of authoritative control. Finally, with the decision to control the vendor more tightly and to increase the efficiency and effectiveness in the project, the overall control portfolio became relatively procedural. As a consequence of these control balancing decisions, the vendor clearly realized that something had to be changed and improved, which triggered the search for higher degrees of project effectiveness. The vendor program manager explained: “It was after around one year of working together that in one of the sub-projects we faced an issue. The level of detail expected by the client project managers turned out to be completely different than what we had been delivering ... We established extra ‘focus teams’ in [offshore location] to address performance issues.” However, authoritative control also caused a further deterioration in shared understanding. In particular, as illustrated by the following quote, there was a breakdown in communication: “This [referring to the change in client control behavior] initiated multiple rounds of discussions. The question raised in our team was ‘why are they doing this?’ Yes, details are important, but results are also equally important. The situation escalated…somewhere that element of discussion was lost, people were not talking to each other anymore. Yes, if I talk to you, I can hopefully explain to you why I think this is sufficient and you can explain to me your 22 views on why you think it is not sufficient. That discussion thread had started to break down.” [vendor program manager] This breakdown of communication hampered the accumulation of shared business-functional knowledge (SU2) and ultimately led to further unfulfilled expectations (SU3) and a vicious cycle. After the problems were escalated to the top management level, the client was on the verge of “pulling out the contract” [client program manager] and the project was headed toward failure. Control Balancing Phase 3: Coordinated Control Both the client and the vendor were driven by a strong mutual commitment toward project success. As the client program manager commented: “Failure was no option.” In a series of joint reflections between key client and vendor project members, gaps in shared understanding in all four above mentioned areas (SU1-4) were identified. Realizing and reflecting upon these gaps led to control balancing decisions and a new phase of coordinated control (see Table 9). Phase Triggering Conditions Control Balancing Decisions Consequences Phase 3: Coordinated control Gaps in shared understanding Need to renegotiate joint project processes (SU1) Need to close businessfunctional knowledge gaps (SU2) Need to renegotiate mutual expectations (SU3) Need to foster negotiation of shared social practices (SU4) Combination of procedural controls (redefinition of roles and responsibilities, joint parallel testing approach), social controls (workshops, feedback-driven communication, lessons learned sessions) and hybrid controls (offshore site visits, reflection-inaction sessions, replay sessions), resulting in a hybrid control portfolio Tight control degree: High amount of control paired with a high intensity of control use Bilateral control style: Focus on joint control based on mutual agreement of control selection and use Shared understanding development (SU1-4) Collaborative working relationships Shared understanding development and learning in the offshoring relationship fosters the use of coordinated control => virtuous cycle based on shared experiences and learning Occasional setbacks to authoritative control Client and vendor cycled several times back and forth between authoritative and coordinated control Table 9: Third Phase of Control Balancing in Our Case While the control degree remained tight in this phase of coordinated control, a conscious decision was made to adapt the control style. The following quote by a senior client project manager illustrates the control balancing decision toward a bilateral control style: 23 “At some point in time we arrived at the conclusion that we could not continue to simply control the performance of the vendor… rather, we realized, in fact both we and the vendor realized that we could only master the challenges in the project by working together very closely.” A senior vendor project manager, who was involved in most of these critical joint reflections, explained: “It was in one of these quarterly meetings, the project reviews that we usually conducted iteratively in [client location in Germany] or [vendor location in India]. It was a gradual process of joint reflections, but… the key tipping point was probably this meeting where we discussed the gaps and decided [on] a change in methodology and mutual expectations” From this point forward the distribution of workload changed and new role expectations were negotiated (SU3). In the end, client and vendor agreed that they both had to invest additional resources and that the client would have to take over more responsibility concerning key issues such as cooperating with the vendor to build up business-functional knowledge in the relationship (SU2). The vendor assigned a very senior banking expert to the project who worked closely with the client in Germany for one year. One of his achievements was producing a 22-page long ‘vocabulary list’ with key banking- and client-specific concepts and their explanations as a learning document for the project teams. New social and hybrid controls were added to the control portfolio and the degree of control remained tight, reflecting the shift from authoritative control back to coordinated control. An example is the decision (that was taken jointly by client and vendor) to initiate offshore site visits in which client project managers were sent in small groups for one to two weeks to the offshore vendor location. One of the client project managers commented on this experience: “The site visits to India were helpful …to talk to them [vendor offshore personnel]…all of us [project leaders] went to [vendor location in India] at some point in time…now we [client and vendor staff] feel much more comfortable to communicate with each other. Afterwards, the cooperation was totally different. Personal contact is extremely important. People now have the heart to call each other and talk openly about the issues.” 24 The site visits helped to close the gaps in shared understanding with regards to social practices (SU4) as well as business-functional knowledge (SU2). They also facilitated joint problem solving by client and vendor project members, a key implication of coordinated control. The client program manager commented: “Always when they [client project managers] were there, the project status was on a green light! When you get to know the people there locally, then this helps to build up a good project climate.” As a further example of coordinated control in this phase of cooperation, a client project manager commented on the use of joint ‘reflection-in-action’ in client-vendor face-to-face meetings as well as extensive coaching of less experienced team members. “I had regular meetings with my counterpart from the Indian organization. We discussed different perceptions, misunderstandings, cultural and communication issues, and reflected jointly on the experiences (positive and negative) we gained from working together in the project. Afterward we carried out extensive coaching with our project members on both sides… That way, we were able to solve many conflicts and misunderstandings in the project and motivate our project workers.” [client project manager] With coordinated control in place, client and vendor groups started to understand each other better and started to learn more intensively about the social practices that were deeply embedded in client and vendor work teams (SU4). For example, vendor personnel started to communicate more openly concerning any critical issues or problems they faced. Client personnel also started to learn and adapt. For example, after learning about the Indians’ feelings in situations of disagreement and conflict and their desire for accommodation, they started to develop new communication techniques. A client project manager explained: “What I do in such situations is [I] ask my communication counterpart actively whether he really meant ‘yes’ or ‘no’ when I realize that he is not being totally serious with his statement. Basically, you have to ask: ‘What other options are there?’ and somehow try to stimulate the communication through open instead of closed ‘yes’ or ‘no’ questions. In such situations you have to communicate ‘the Indian way’.” 25 Client and vendor also identified the need to renegotiate joint project processes and made an adaptation to the testing approach (SU1): “We implemented a joint parallel testing approach. Basically, we introduced one more phase and let old and new programs run in parallel both in Germany and India. Recurrently, we would compare results and output and if it was different, then we analyzed why and asked ourselves whether we missed something and if yes where…in the requirements stage or some other phase? The new testing approach proved to be so effective that we adopted this as standard practice for subsequent sub-projects and work streams.” [senior vendor project manager] As a result of the shift toward coordinated control, client and vendor began to cooperate more intensively with each other and started to make significant improvements in the areas of shared understanding about business-functional knowledge (SU2) and mutual expectations (SU3), which gradually also led to better deliverables. Based on the joint experiences in the project, a virtuous cycle of continued shared learning and understanding and coordinated control developed. However, the shift from authoritative control to coordinated control was anything but smooth and linear: “We cycled back and forth several times… But the key thing was that we were always able to sit together with [name of vendor] at the table, identify the gaps, and decide jointly the necessary changes. That’s what I liked about [name of vendor], this constructive cooperation.” [client program manager] Over time, the virtuous cycle mentioned above led to the selection and use of all kinds of new mechanisms that were instantiations of coordinated control. Project managers started to experiment with regular telephone calls to India, the placement of client and vendor onsite teams in joint open plan offices, and the use of shared blackboards for status tracking in onsite teams. Client and vendor members would also meet regularly to discuss open issues and solve problems jointly which was an implication of coordinated control. Gradually, the deliverables in the project improved significantly. A critical roll-out of the most important sub-project was successfully 26 completed in June 2007 and the deliverables of the vendor had improved to a level that the client was satisfied with the results. Control Balancing Phase 4: Trust-Based Control Fulfilled mutual expectations (SU3) triggered control balancing decisions, resulting in trustbased control (Table 10). Phase Triggering Conditions Control Balancing Decisions Consequences Phase 4: Trust-based control Fulfilled expectations (SU3): Need to decrease the amount of resources dedicated to control Need to foster trust and increase the maturity of the relationship Control portfolio dominated by social controls (spontaneous phone calls, brainstorming sessions, informal exchange of ideas, direct and pragmatic communication) Relaxed control degree: low amount of control paired with a low intensity of control use Bilateral control style: Focus on joint control based on mutual agreement of control selection and use Shared understanding became established (SU1-4) and paved the way for a trustbased client-vendor relationship Occasional setbacks to coordinated control The relaxation of control degree gave room for new issues to emerge that challenged client-vendor shared understanding, caused issues in the project, and triggered more coordinated control from time to time Table 10: Fourth Phase of Control Balancing in Our Case The following quotes by the client program manager and two project managers illustrate why the control balancing decision toward a relaxed control degree was eventually taken, a key characteristic of trust-based control: “Our project managers went through a steep learning curve, both with regards to social and procedural aspects. This learning in the offshoring relationship gradually led to shared understanding and trust… you don’t have to control every single thing…after five successful deliverables the sixth will also be fine…project managers then relaxed the reins.” [client program manager] “The moment in which three spot tests in a row meet your requirements, that’s when you start trusting each other [referring to client and vendor project members]. Trust starts replacing the need for controlling tightly.” [client project manager] “Trust made a dense nexus of control obsolete.” [client project manager] When our participants used the word ‘trust,’ they referred to the fulfillment of expectations (SU3) and the essential consequential belief that they could rely on the vendor’s capability to deliver 27 high quality results within an agreed upon timeframe without having to be tracked and controlled intensively. In this phase of trust-based control, the selection and use of control mechanisms changed. Many control mechanisms were of a social type, focusing on improving further shared understanding in the relationship: “In the beginning we had many discussions [referring to conflicts over the quality of deliverables and related issues], but today conversations are more toward optimizing performance; our relationship matured, we now talk about more advanced topics, not day-to-day disagreements.” [senior vendor project manager] Client and vendor participants in our study commented on the use of frequent spontaneous communication, the exchange of ideas, and joint brainstorming sessions. Communication also became more direct (not following always the previously defined formal pathways) and pragmatic. Furthermore, trust-based control led to a reverse situation in comparison with authoritative control: now it was frequently the vendor who was in the ‘lead’ and providing direction for where to go and how. A senior client project manager explained: “For me a key experience was the moment when a problem could not be solved internally in our organization anymore and [name of vendor] took over full responsibility. Then I realized that something fundamentally had changed. I didn’t have to be the one anymore who knows everything.” A vendor project manager gave us a few illustrative examples which made clear that the vendor was taking over the lead gradually and the client continuously reduced the size of its managerial work force assigned to the project. Also, the client program manager commented on this: “It was at the end of 2008 when I began to realize something. The interest calculations for many customers had defects. Everybody was on vacation except myself and then we had a crisis meeting. That was the first crisis meeting of such kind where [name of vendor] was at the table. They analyzed the situation and came up with a solution to the problem already the next day. They basically solved the entire bandwidth of problems all by themselves. It became clear to me: They had understood.” 28 Gradually, trust-based control fostered the establishment of shared understanding (SU1-4) and the development of a truly trust-based relationship, as illustrated by the following quotes: “The element of success comes from trust…whether you trust me, that what I will do is something which is good for you. That trust developed in our relationship and bound us together…that really helped in making it happen.” [vendor program manager] “There are no boundaries between the two teams. We always work together for the project. So, whenever we interact … we always talk about the project; we never talk about the individuals. We constantly ask ourselves how to improve things together… I talked to them as my colleagues, working for the same project, working for the same goal. That was the very best thing.” [vendor architecture lead]. However, similar to the transition from authoritative control to coordinated control, the transition from collaboration control to trust-based control was not entirely smooth and linear: “It was a balancing act. Controlling tightly and coordinating control actions intensively with the vendor cost us a lot of resources, I call it ‘energy modus operandi.’ A lot of overhead and time…of course you cannot manage in such a modus operandi completely, you need to try to get to the next stage [referring to the shift to trust-based control which required less managerial resources]. But then you recurrently get into a new situation where you need to grab the reins more tightly again and so you jump back into energy modus operandi for some time.” [senior client project manager] A Process Model of Control Balancing in ISD Offshoring The process model in Figure 1 synthesizes our case analysis results and abstracts the most important findings. 29 Control Balancing and Evolution in ISD Offshoring Authoritative Control Multiple iterations possible Unfulfilled expectations Shared Understanding Deterioration Coordinated Control Multiple iterations possible Gaps in shared understanding Trust-based Control Fulfilled expectations Shared Understanding Development Shared Understanding Establishment Evolution of ISD Offshoring Client-Vendor Shared Understanding Legend: Changes in shared understanding triggering control balancing Control balancing affecting shared understanding Evolution and dynamics of control balancing Figure 1: Process Model of Control Balancing in ISD Offshoring Accordingly, we find from our case analysis that gaps in client-vendor shared understanding trigger the use of coordinated control with the consequence of shared understanding development (see Tables 7 and 9). Unfulfilled expectations trigger the use of authoritative control with the consequence of shared understanding deterioration (see Table 8). Finally, fulfilled expectations trigger the use of trust-based control, leading eventually to the establishment of shared understanding (see Table 10). As explained in our case analysis, multiple iterations between coordinated control and authoritative control as well as between trust-based control and coordinated control are possible. However, we did not find case-based evidence for a setback all the way from trust-based control back to authoritative control. Control Configurations and Balancing States in ISD Offshoring Control balancing resulted in our case in three different control configurations, which are defined and explained in Table 11. The assignment of control mechanisms to one particular control 30 configuration state (last column) is a simplified view. Mechanisms such as ‘status reviews’ have been naturally used throughout the project. However, the mapping of control mechanisms to the three different control configurations illustrates which control mechanisms were particularly important in which phase. Control Configuration Definition Meaning and Implication Typical Examples of Control Mechanisms from our Case Authoritative control - Procedural control portfolio - Tight control degree - Unilateral control style An approach to control based on a traditional client-vendor perspective Client-vendor perspective: - Means that exchange parties see themselves as ‘client’ and ‘vendor’ with clearly separated roles and responsibilities - Implies that the client specifies requirements, the vendor delivers upon them, and control selection and use is driven by the client - Results in situations in which the client dominates the relationship from a managerial perspective - - Status reviews Detailed examination of deliverables Tracking of project goals Definition of client/vendor roles and responsibilities Operational process documents Coordinated control - Hybrid control portfolio - Tight control degree - Bilateral control style An approach to control based on a coordination perspective Coordination perspective: - Means that exchange parties see themselves as partners that need to closely coordinate activities - Implies that client and vendor work toward coordinated, shared goals, search jointly for problem solutions, and select and use control mechanisms accordingly - Results in situations in which neither the client nor the vendor dominates - Joint parallel testing approach Site visits Workshops Reflection-in-action sessions Coaching of team members Joint communication plan Lessons learned sessions Feedback mechanisms Trust-based control - Social control portfolio - Relaxed control degree - Bilateral control style An approach to control based on a trust-based perspective Trust-based perspective: - Means that exchange parties see themselves as part of the same team based upon mutual trust and shared understanding - Implies that the vendor delivers without the client getting deeply involved in the process and less resources are dedicated to controlling the vendor - Results in situations in which problems get solved instantly, new ideas for improvements are generated, and the vendor takes over more responsibility in the relationship - Direct and pragmatic coordination Brainstorming sessions Spontaneous communication (e.g., facilitated through open plan offices) Informal exchange of ideas - - - Table 11: Control Configurations and Balancing States in ISD Offshoring Figure 2 depicts the three dimensions of control balancing decisions, illustrating that controllers in ISD offshoring need to make recurrent decisions with regards to the appropriate control configuration. The arrows in the figure depict the stylized non-deterministic evolution of control balancing observed in our case study. 31 control type c) social a) Authoritative control (procedural; tight; unilateral) b) Coordinated control (hybrid; tight; bilateral) b) hybrid control degree c) Trust-based control (social; relaxed; bilateral) relaxed procedural a) tight unilateral bilateral control style Figure 2: The Three Dimensions of Control Balancing DISCUSSION AND THEORETICAL INTEGRATION In studying the dynamics of control associated with a 5-year long ISD offshoring project, our data prompted us to examine the related phenomenon of ‘control balancing,’ which became the basis for our theory development. Our grounded theory of control balancing in ISD offshoring explains what needs to be balanced (see Figure 2, Table 5, and Table 11), how control balancing occurs (see Figure 1 and Tables 7 to 10), and why control balancing matters (illustrated by the dynamic interplay of control balancing decisions with shared understanding in Figure 1 and Tables 7 to 10). In the following, we discuss our theory and integrate it into the literature. Control Balancing We conceptualized control balancing as making targeted adjustments to the control configuration periodically along three different dimensions, i.e., control types, control degree, and control style. This departs significantly from prior research, which has focused solely on one dimension, i.e., 32 control types (Cardinal et al. 2004), acknowledging the need for control balancing (Gopal and Gosain 2010, p. 978), without examining in detail what needs to be balanced, how control balancing occurs, and why control balancing matters. Thus, the grounded theory of control balancing in ISD offshoring developed in this paper represents the first systematic attempt to explain organizational control balancing. With ‘balancing,’ we specifically refer to recurrently and intentionally tuning and directing control actions toward key objectives (in our case, ISD offshoring project and relationship progress), by finding the appropriate configurations along the three identified control dimensions. Our findings, summarized in the integrative process model in Figure 1, suggest that the process of control balancing is much more multifaceted, dynamic, and iterative than assumed in existing literature, which basically has focused on linear shifts in the creation of control portfolios over time (Cardinal et al. 2004; Choudhury and Sabherwal 2003; Kirsch 2004). Control types is one dimension of control balancing that emerged from our data. We found that control mechanisms can be of a procedural type, i.e., oriented toward the goal of improving efficiency and effectiveness (e.g., status reviews), social type, i.e., oriented toward the goal of developing shared understanding (e.g., socialization activities), or hybrid type, i.e., oriented toward both goals simultaneously (e.g., common understanding workshops). This goal-oriented typology of control mechanisms fits our notion of control balancing, which emphasizes making adjustments to facilitate both project and relationship progress. However, it also represents a departure from past organizational and IS control theory that has focused on explaining control mechanisms in terms of their degree of formality (Kirsch 1996; Ouchi 1979). Control degree, is the second dimension of control balancing that emerged from our data, and depicts how firmly control is exercised, ranging from tight to relaxed. We found that the amount of control (measured in terms of both the frequency of control use and the number of controls 33 used simultaneously), and the intensity of control are useful properties to depict the degree of control at any given point in time. Thus, our conceptualization of control degree significantly extends and refines prior theorizing, which speaks only to the notion of ‘amount of control’ (Henderson and Lee 1992; Rustagi et al. 2008). To provide an illustrative example of the added explanatory value, conducting frequent project status reviews is not necessarily sufficient for the control degree to be tight. One must also consider the intensity with which the status reviews are performed, i.e., the level of scrutiny to which project is exposed in terms of questioning details and challenging results. Control style is the third dimension of control balancing that we identified, and depicts how control is enacted in the client-vendor relationship, i.e., from relatively unilateral to bilateral. In particular, our findings provide evidence that in an inter-organizational relationship, such as an ISD client-vendor offshoring relationship, ambiguity can arise as to who actually controls whom. Our study illustrates that such ambiguity may result from applying different approaches to control selection, implementation, and use (i.e., unilateral vs. bilateral) and that this aspect of control balancing is not captured under existing control theory. In the unilateral control style, ambiguity concerning the role of controller and controllee in the inter-organizational relationship is relatively low, as control is exercised mainly in a one-way direction (typically the client controlling the vendor). Further, in the unilateral control style, controllers do not emphasize mutuality with respect to control selection and use. On the other hand, in a bilateral control style ambiguity concerning the role of controller and controllee is relatively high and boundaries can begin to blur. In the bilateral control style, exchange parties engage in mutual coordination of control actions and exercise control jointly. As illustrated by our case study, there can be mutual agreement with regards to control, though this finding is not one that would be predicted based on prior literature in which the client is typically viewed as the controller and the vendor as 34 controllee (e.g., Tiwana and Keil 2007). Thus, in surfacing the bilateral control style, we have a counterintuitive finding that extends prior theorizing and allows us to conceptualize situations in which client and vendor may be viewed simultaneously as controllers. The Dynamics of Controlling IS Outsourcing and Offshoring Relationships By analyzing recurrent control balancing decisions in our longitudinal case study of an ISD offshoring project, we were able to identify and conceptualize three control configurations that are relevant to this context (see Table 11): authoritative control (procedural; tight; unilateral), coordinated control (hybrid; tight; bilateral), and trust-based control (social; relaxed; bilateral). In our particular case study, the exchange parties started with coordinated control, which rests upon viewing each other as partners who need to closely coordinate work activities. This results in a hybrid control portfolio with simultaneous emphasis on procedural efficiency and effectiveness as well as the development of shared understanding, a relatively tight control degree, and a bilateral control style. While good working relationships were initially developed through this control configuration, contextual challenges related to shared understanding (e.g., business-functional knowledge gaps, and differences in communication and work practices) created problems that are documented in prior IS offshoring research (e.g., Dibbern et al. 2008; Levina and Vaast 2008). These challenges ultimately led to an unsatisfying vendor performance and unfulfilled mutual expectations, which has also been observed in past IS research (e.g., Sabherwal 1999). Choudhury and Sabherwal (2003) found that under such circumstances changes are made to the control portfolio. We extend their findings by explaining that this can trigger the use of authoritative control. This control configuration rests upon the traditional client-vendor relationship perspective in which control selection and use is driven by the client. Our findings suggest that the use of authoritative control may improve project efficiency, but at 35 the cost of a potential deterioration in client-vendor shared understanding. These findings are related to the known challenge of vicious cycles between control and relationship quality in interorganizational contexts (Das and Teng 1998). In our case study, the identification of gaps in shared understanding by key client and vendor project leaders and respective actions to address them eventually triggered the repeated use of coordinated control (with occasional setbacks to authoritative control), with an even tighter control degree than before and enabled by accumulated shared experiences and learning. While the role of shared learning and understanding development between client and vendor is recognized in the IS outsourcing literature (e.g., Vlaar et al. 2008), its role in facilitating control balancing had not been previously explored. In our case study, vendor performance improved gradually, mutual expectations were fulfilled, and the use of trust-based control was triggered (with occasional setbacks to coordinated control). This led to a situation in which client and vendor employees started to view themselves as part of the same team, thus fostering further establishment of shared understanding. Several important insights emerge from our detailed longitudinal analysis of control balancing. First, contextual factors such as vendor (non-)performance and (un)fulfilled expectations not only trigger changes to the control portfolio as suggested in prior research (Choudhury and Sabherwal 2003) but also may lead to significant changes in control degree and style. Thus, one important contribution of our work is to refocus the discussion from constructing portfolios of control to the idea of control balancing and to recognize that in this broader, more dynamic view there are multiple dimensions that must be considered (i.e., control types, control degree, and control style) and that these dimensions can be combined into specific control configurations. Second, we find strong evidence for the reciprocal effects of control balancing decisions and shared understanding development in an IS outsourcing relationship. In other words, control behavior is not only triggered by project- and relationship-related events as suggested in past research, but control 36 behavior itself has a significant impact on the evolution of the project and relationship. These reciprocal effects offer new insight into the dynamics of control balancing and add to our understanding of the impacts of organizational control behavior. Specifically, we provide evidence for multiple iterations and vicious/virtuous cycles in the process of control balancing based on a dynamic interaction between control balancing decisions and the evolution of clientvendor shared understanding. Guidelines for Managing ISD Offshoring Projects and Relationships Based on the theoretical findings discussed, summarized, and integrated above, we derive the following guidelines for managing ISD offshoring projects and relationships (Table 12). Guideline Challenge Recommendation #1) Make conscious control balancing decisions Project and relationship challenges (e.g., performance is bad, expectations are not fulfilled) oftentimes lead to ad-hoc control change responses (e.g., quickly increase the degree of control in the belief that more control will lead to better outcomes) which may not yield the expected benefits (e.g., shared understanding deterioration, leading to a vicious cycle). We recommend that client and vendor project managers recurrently assess control balance and ask the question: ‘How good is my control configuration in terms of the three dimensions, i.e., control types, degree, and style, given the current situational requirements for achieving both project-related and relationship-related goals and objectives?’ Ideally, such ‘reflectionin-action’ leads to conscious control balancing decisions that proactively tackle project and relationship challenges. #2) Leverage the advantages of a bilateral control style Usually, the client in an outsourcing relationship is viewed as the ‘controller’ and the vendor is viewed as the ‘controllee’. This leads to a unilateral control style which in combination with a tight control degree and relatively procedural control portfolio (i.e., authoritative control) can be detrimental for developing shared understanding in the relationship, an essential success factor in offshore outsourcing. We recommend that client and vendor project managers sit together and think about control jointly, thereby compensating for the natural drift of (hierarchical, bureaucratic) organizations toward efficiency, traditional project success criteria, and authoritative control. The implication is that project managers should try to move as early as possible toward the right in our process model (see Figure 1) in which control configurations are characterized, among other things, by a bilateral control style. #3) Balance project and relationship requirements Strategies for project management (e.g., status reporting and tracking) sometimes may be at odds with strategies for relationship management (e.g., development of shared understanding), producing tensions and undesirable reactions (e.g., the vendor asking the question why s/he is being treated as a subordinate instead of a partner). We recommend that client and vendor project managers establish and maintain the delicate balance between achieving short-term goals of project success and achieving long-term goals of relationship development which are equally needed for ISD offshoring success. #4) Develop shared understanding in the Control balancing decisions in ISD offshoring are driven by shared understanding in the We recommend that client and vendor project managers view critical offshoring issues such 37 relationship relationship and the sooner such understanding is created, the better. However, critical offshoring issues (e.g., business-functional knowledge) are frequently viewed in outsourcing from a one-sided perspective (e.g., knowledge transfer / absorptive capacity), which may limit shared understanding development. as project processes, business-functional knowledge, mutual expectations, and social practices from a shared understanding perspective. For example, client and vendor need to accumulate joint knowledge that is embedded in the relationship; both client and vendor need to learn and adapt to one another to develop negotiated social practices. Table 12: Practical Guidelines for Control Balancing in ISD Offshoring Projects Limitations and Future Research Our study is naturally not without limitations. While a single case study design affords the opportunity to generalize to a theory (Lee and Baskerville 2003, p. 232), which we have strived to achieve here, further research is needed to replicate our findings across different contexts (Eisenhardt 1989; Eisenhardt and Graebner 2007; Yin 2003). Additional research is also needed to determine what other control configurations, besides the three that we identified, may be feasible and under what circumstances. Another direction for future research would be to explore whether individual control modes and mechanisms vary on the dimensions of control degree and style within the context of a particular control configuration. We suspect that for any given control configuration, the individual control modes and mechanisms will tend to have a high level of correlation with respect to control degree and style, but additional research is needed in order to confirm this. Another avenue for future research would be to explore whether control balancing is contingent upon the choice of systems development methodology, which in our case was a waterfall ISD approach and might have affected the dynamics of control balancing due to the associated structuring of the project and manner in which personnel were deployed. Furthermore, we did not examine the role of technologies in promoting or inhibiting the balancing of control, e.g., by facilitating the enforcement of controls. Thus, future research should examine more explicitly the interactions between the use of information and communication technologies and control balancing. Another limitation of our study is that we 38 focused on examining inter-organizational control transmission, while in reality, the use of interorganizational (e.g., client-vendor) controls could potentially interact with the use of intraorganizational controls (e.g., vendors controlling their offshore teams). This, too, deserves further research attention. Finally, our theory is also constrained to some extent by temporal restrictions. In particular, researchers applying and extending our findings to new contexts need to consider that our examination of control balancing is based on the early phases of an IS offshoring relationship. In our particular case, the client and the vendor cooperated for the first time in a joint multi-year project and prior to this project had only cooperated by filling individual resource gaps on a one-off basis. Thus, they shared only a minor relationship history. The phenomenon of control balancing might look differently during later and more mature stages of such a relationship. Finally, we particularly call for more research on the process of control balancing. We hope that our study will trigger more empirical research on control balancing in related contexts, including domestic IS outsourcing projects and internal IS projects, in which different stakeholders may also need to explore various control configurations and adapt them over time as a project unfolds. Such exploration may provide insights into how controllers can acquire the skills needed to enable effective control balancing across a variety of project contexts, thus improving the chances of achieving successful project outcomes. CONCLUSION Our study elucidates the dynamic, reciprocal, and multifaceted nature of control balancing in ISD offshoring projects. This perspective challenges the assumptions and addresses some of the shortcomings of prior research, namely the one-dimensional focus on types of control in the construction of control portfolios and the unidirectional focus on triggers affecting changes in 39 control portfolios. In summary, our grounded theory of control balancing in ISD offshoring projects holds the potential to trigger new ways of looking at control phenomena in temporary inter-firm organizations such as client-vendor ISD offshoring projects. ACKNOWLEDGEMENTS This work was developed as part of a research project of the E-Finance Lab at Goethe University Frankfurt. Any opinions, findings, conclusions, or recommendations expressed in this paper are those of the authors and do not necessarily reflect the views of the E-Finance Lab or its supporting partners. The authors are indebted to the participating universities and gratefully acknowledge the financial support of their industry partners. In addition, we would like to thank Michael Prifling who has supported the data collection. Finally, we acknowledge the truly developmental review process that this paper has gone through under the guidance of the SE and AE and we appreciate the contribution of the entire review team in helping us to improve upon the ideas presented in the paper. REFERENCES Bacharach, S.B. 1989. "Organizational Theories: Some Criteria for Evaluation," The Academy of Management Review (14:4), pp. 496-515. Barker, J.R. 1993. "Tightening the Iron Cage: Concertive Control in Self-Managing Teams," Administrative Science Quarterly (38:3), pp. 408-437. Bradach, J.L., and Eccles, R.G. 1989. "Price, Authority, and Trust: From Ideal Types to Plural Forms," Annual Review of Sociology (15:1), pp. 97-118. Bryant, A., and Charmaz, K. 2007. The Sage Handbook of Grounded Theory, Thousand Oaks: SAGE Publications. Cardinal, L.B., Sitkin, S.B., and Long, C.P. 2004. "Balancing and Rebalancing in the Creation and Evolution of Organizational Control," Organization Science (15:4), pp. 411-431. Charmaz, K. 2006. Constructing Grounded Theory: A Practical Guide through Qualitative Analysis Choudhury, V., and Sabherwal, R. 2003. "Portfolios of Control in Outsourced Software Development Projects," Information Systems Research (14:3), pp. 291-314. Das, T.K., and Teng, B.-S. 1998. "Between Trust and Control: Developing Confidence in Partner Cooperation in Alliances," Academy of Management Review (23:3), pp. 491-512. Dibbern, J., Winkler, J., and Heinzl, A. 2008. "Explaining Variations in Client Extra Costs between Software Projects Offshored to India," MIS Quarterly (32:2), pp. 333-366. Eisenhardt, K.M. 1989. "Building Theories from Case Study Research," Academy of Management Review (14:4), pp. 532-550. Eisenhardt, K.M., Furr, N.R., and Bingham, C.B. 2010. "Microfoundations of Performance: Balancing Efficiency and Flexibility in Dynamic Environments," Organization Science (21:6), pp. 1263-1273. Eisenhardt, K.M., and Graebner, M.E. 2007. "Theory Building from Cases: Opportunities and Challenges," Academy of Management Journal (50:1), pp. 25-32. 40 Ghemawat, P. 2007. "Managing Differences," Harvard Business Review (85:3), pp. 58-68. Glaser, B.G. 1978. Theoretical Sensitivity, Mill Valley: The Sociology Press. Glaser, B.G. 1992. Emergence Vs. Forcing: Basics of Grounded Theory Analysis, Mill Valley, CA: Sociology Press. Glaser, B.G., and Strauss, A. 1967. The Discovery of Grounded Theory: Strategies for Qualitative Research, Chicago: Aldine Publishing Company. Gopal, A., and Gosain, S. 2010. "The Role of Organizational Controls and Boundary Spanning in Software Development Outsourcing: Implications for Project Performance," Information Systems Research (21:4), pp. 960-982. Heiskanen, A., Newman, M., and Eklin, M. 2008. "Control, Trust, Power, and the Dynamics of Information System Outsourcing Relationships: A Process Study of Contractual Software Development," Journal of Strategic Information Systems (17:4), pp. 268-286. Henderson, J.C., and Lee, S. 1992. "Managing I/S Design Teams: A Control Theories Perspective," Management Science (38:6), pp. 757-777. Kelle, U. 2007. "The Development of Categories: Different Approaches in Grounded Theory," in The Sage Handbook of Grounded Theory, A. Bryant and K. Charmaz (eds.). London: SAGE Publications, pp. 191213. King, W.R., and Torkzadeh, G. 2008. "Information Systems Offshoring: Research Status and Issues," Management Information Systems Quarterly (32:2), pp. 205-225. Kirsch, L.J. 1996. "The Management of Complex Tasks in Organizations: Controlling the Systems Development Process," Organization Science (7:1), pp. 1-21. Kirsch, L.J. 1997. "Portfolios of Control Modes and Is Project Management," Information Systems Research (8:3), pp. 215-239. Kirsch, L.J. 2004. "Deploying Common Systems Globally: The Dynamics of Control," Information Systems Research (15:4), pp. 374-395. Koh, C., Ang, S., and Straub, D. 2004. "It Outsourcing Success: A Psychological Contract Perspective," Information Systems Research (15:4), pp. 356-373. Lacity, M., and Willcocks, L. 2012. "Outsourcing Business and I.T. Services: The Evidence of Success, Robust Practices and Contractual Challenges," Legal Information Management (12:01), pp. 2-8. Langley, A. 1999. "Strategies for Theorizing from Process Data," Academy of Management Review (24:4), pp. 691710. Lee, A.S., and Baskerville, R.L. 2003. "Generalizing Generalizability in Information Systems Research," Information Systems Research (14:3), pp. 221-243. Lempert, L.B. 2007. "Asking Questions of the Data: Memo Writing in the Grounded Theory Tradition," in The Sage Handbook of Grounded Theory, A. Bryant and K. Charmaz (eds.). London: SAGE Publications, pp. 245264. Levina, N., and Vaast, E. 2008. "Innovating or Doing as Told? Status Differences and Overlapping Boundaries in Offshore Collaboration," MIS Quarterly (32:2), pp. 307-332. Long, C.P., and Sitkin, S.B. 2006. "Trust in the Balance: How Managers Integrate Trust-Building and Task Control," in Handbook of Trust Research, R. Bachmann and A. Zaheer (eds.). Cheltenham: Edward Elgar, pp. 87– 106. Mähring, M., and Keil, M. 2008. "Information Technology Project Escalation: A Process Model," Decision Sciences (39:2), pp. 239-272. Maruping, L.M., Venkatesh, V., and Agarwal, R. 2009. "A Control Theory Perspective on Agile Methodology Use and Changing User Requirements," Information Systems Research (20:3), pp. 377-399. Mingers, J. 2001. "Combining Is Research Methods: Towards a Pluralist Methodology," Information Systems Research (12:3), pp. 240-259. Mingers, J. 2004. "Real-Izing Information Systems: Critical Realism as an Underpinning Philosophy for Information Systems," Information and Organization (14:2), pp. 87-103. Mohr, L.B. 1982. Explaining Organizational Behavior, San Francisco: Jossey-Bass. Ouchi, W.G. 1977. "The Relationship between Organizational Structure and Organizational Control," Administrative Science Quarterly (22:1), pp. 95-113. Ouchi, W.G. 1979. "A Conceptual Framework for the Design of Organizational Control Mechanisms," Management Science (25:9), pp. 833-848. Ouchi, W.G., and Maguire, M.A. 1975. "Organizational Control: Two Functions," Administrative Science Quarterly (20:4), pp. 559-569. Pan, S.L., and Tan, B. 2011. "Demystifying Case Research: A Structured-Pragmatic-Situational (Sps) Approach to Conducting Case Studies," Information and Organization (21:3), pp. 161-176. 41 Rai, A., Maruping, L.M., and Venkatesh, V. 2009. "Offshore Information Systems Project Success: The Role of Social Embeddedness and Cultural Characteristics," MIS Quarterly (33:3), pp. 617-641. Rustagi, S., King, W.R., and Kirsch, L.J. 2008. "Predictors of Formal Control Usage in It Outsourcing Partnerships," Information Systems Research (19:2), pp. 126-143. Sabherwal, R. 1999. "The Role of Trust in Outsourced Is Development Projects," Communications of the ACM (42:2), pp. 80-86. Sarker, S., and Sarker, S. 2009. "Exploring Agility in Distributed Information Systems Development Teams: An Interpretive Study in an Offshoring Context," Information Systems Research (20:3), pp. 440-461. Sitkin, S.B., Cardinal, L.B., and Bijlsma-Frankema, K. 2010. Organizational Control, New York: Cambridge University Press. Smith, W.K., and Lewis, M.W. 2011. "Toward a Theory of Paradox: A Dynamic Equilibrium Model of Organizing," Academy of Management Review (36:2), pp. 381-403. Sundaramurthy, C., and Lewis, M. 2003. "Control and Collaboration: Paradoxes of Governance," The Academy of Management Review (28:3), pp. 397-415. Tiwana, A. 2008. "Does Technological Modularity Substitute for Control? A Study of Alliance Performance in Software Outsourcing," Strategic Management Journal (29:7), pp. 769-780. Tiwana, A. 2010. "Systems Development Ambidexterity: Explaining the Complementary and Substitutive Roles of Formal and Informal Controls," Journal of Management Information Systems (27:2), pp. 87-126. Tiwana, A., and Keil, M. 2007. "Does Peripheral Knowledge Complement Control? An Empirical Test in Technology Outsourcing Alliances," Strategic Management Journal (28:6), pp. 623-634. Tiwana, A., and Keil, M. 2009. "Control in Internal and Outsourced Software Projects," Journal of Management Information Systems (26:3), pp. 9-44. Urquhart, C. 2001. "An Encounter with Grounded Theory: Tackling the Practical and Philosophical Issues," in Qualitative Research in Is: Issues and Trends, E. Trauth (ed.). Idea Group Publishing, pp. 104-140. Urquhart, C. 2007. "The Evolving Nature of Grounded Theory Method: The Case of the Information Systems Discipline," in The Sage Handbook of Grounded Theory, A. Bryant and K. Charmaz (eds.). London: SAGE Publications, pp. 339-359. Urquhart, C., Lehmann, H., and Myers, M. 2010. "Putting the ‘Theory’ Back into Grounded Theory: Guidelines for Grounded Theory Studies in Information Systems," Information Systems Journal (20:4), pp. 357–381. Van de Ven, A.H. 2007. Engaged Scholarship: A Guide for Organizational and Social Research, New York: Oxford University Press Inc. Vlaar, P.W.L., van Fenema, P.C., and Tiwari, V. 2008. "Cocreating Understanding and Value in Distributed Work: How Members of Onsite and Offshore Vendor Teams Give, Make, Demand, and Break Sense," MIS Quarterly (32:2), pp. 227-255. Walsham, G., and Sahay, S. 1999. "Gis for District-Level Administration in India: Problems and Opportunities," MIS Quarterly (23:1), pp. 39-65. Wynn, D.J., and Williams, C.K. 2012. "Principles for Conducting Critical Realist Case Study Research in Information Systems," MIS Quarterly (36:3), pp. 787-810. Yin, R. 2003. Case Study Research - Design and Methods, Thousand Oaks, California, USA: Sage Publications. 42 Appendix A: Research Process Table A1 depicts our research process, including the main steps as well as associated tasks and outcomes. While the table depicts a linear process, we adhered to grounded theory practice and were highly iterative in our approach. For example, the process analysis was conducted in parallel with substantive and theoretical coding. Furthermore, data collection and analysis tasks were highly intertwined with each other and each influenced the other over time. Therefore, we do not clearly differentiate between data collection and data analysis tasks. Research Step Tasks Outcomes Problem formulation Establishing the phenomenon in terms of its practical relevance as a prerequisite to produce grounded theory that has ‘grab’ (Glaser and Strauss 1967) State what the problem is from a practice and theory perspective and why it is important (Van de Ven 2007) Screening prior research to identify gaps in the literature (Urquhart 2007) Single case study design Establishing engaged relationship with practitioners and negotiating access to data (Pan and Tan 2011; Van de Ven 2007) Selecting a case study site and motivating the rationale for conducting a single case study, e.g., the main criterion for a revelatory case is “when an investigator has an opportunity to observe and analyze a phenomenon previously inaccessible to scientific investigation” (Yin 2003, p. 42) Open coding & data collection Gathering rich primary and secondary data, including intensive interviewing (Charmaz 2006) Coding the data and understanding what it is about by going through interview transcripts line by line, assigning conceptual labels to data segments, and identifying core categories (Glaser 1978) Adhering to the principle of emergence of grounded theory: categories should emerge from the data in the sense that they must ‘fit’ (they must be readily, not forcibly, applicable to and indicated by the data under study) and ‘work’ (they must be meaningfully relevant to and be able to explain the behavior under study) (Glaser and Strauss 1967) Triangulating and comparing different slices of data to find similarities and differences (Charmaz 2006) Delimiting further coding to only those concepts and variables that relate to the emerged categories (Glaser 1978) Making constant comparisons between instances of data labeled as a particular category and other instances of data in the same category to substantiate categories (Urquhart et al. 2010) Further data collection guided by the principle of theoretical sampling, i.e., deciding on analytic Identified the management of ISD offshoring projects as a practically relevant problem that many managers are struggling with Problem identified as developing a relationship with an offshore vendor and managing an ISD offshoring project which is important due to the rapid growth of ISD offshoring and the associated well-known challenges (King and Torkzadeh 2008) Identified gaps in the literature on controlling ISD offshoring projects Reached an agreement with a banking company to conduct a longitudinal multi-year case study of an ISD offshoring project and to obtain data from both the client and the vendor Selected a ‘revelatory case’: longitudinal analysis of an ISD offshoring project including both client and vendor perspectives, which has been inaccessible to scientific investigation before (Choudhury and Sabherwal 2003, p. 313; Dibbern et al. 2008, p. 359) Conducted multiple interviews, observed meetings, and obtained project documentation Generated more than 300 initial codes and more than 300 pages of notes and analytical memos Identified categories related to the simultaneous use of multiple controls throughout the ISD offshoring project without forcing existing concepts from the literature onto the data. Insured that the categories were relevant the understanding of control in offshore ISD projects Compared multiple perspectives, including client and vendor’s, and compared multiple sources of data Selective coding & data collection Delimited further coding to a set of tentative core categories which evolved into control types, control degree, and control style Followed the constant comparisons technique of grounded theory research, focusing on the development of categories and concepts by constantly comparing data to data (e.g., primary interview data to secondary data such as project documentation, data from Germany to data from 43 grounds where to sample from next (Glaser and Strauss 1967, p. 45) Process analysis & data collection Theoretical coding & data collection Scaling up Theoretical integration Mapping of key events (e.g., decisions, actions, outcomes) against a timeline with a focus on depicting the exact sequencing of events with respect to control behavior and decisions in the case study (Mähring and Keil 2008) Delineation of states / phases from triggering mechanisms (Langley 1999; Van de Ven 2007) Analysis and specification of theoretical relationships between core concepts and categories (Bryant and Charmaz 2007, p. 25). This theoretical coding (Glaser 1978), also referred to as iterative conceptualization (Urquhart et al. 2010), is aimed at increasing the level of abstraction, relating categories to each other, and clarifying which categories may be properties of others Engaging with other theories for theory building: To raise the level of conceptualization and scale up the emerging theory, existing theories or concepts should be used for comparisons (Urquhart 2007). Thereby, meta theories and theoretical categories with limited empirical content and general scope are particularly suitable as heuristic or sensitizing devices (Kelle 2007) Grouping higher level categories into broader themes with the goal of increasing the generalizability of the theory and being able to relate the theory to the broader literature (Urquhart et al. 2010) Relating the theory to other theories in the same or similar field by comparing the substantive theory generated with other, previously developed theories (Glaser 1978; Urquhart et al. 2010) Table A1: Research steps, tasks, and outcomes India, data from early data collection to later data collection) as well as data to theoretical concepts outside the domain of study Collected and analyzed additional data as needed to develop our emerging theory. As an example, when our theorizing became focused on control types, degrees, and styles, we decided to conduct additional interviews to flesh out their properties in more detail Constructed a detailed case narrative and process model describing sequences of events and evolution of the project and the relationship over time Identified three different control configurations which form the phases of our process model Identified triggers and consequences of control balancing decisions which evolved into four types of shared understanding in the client-vendor relationship Analyzed relationships between the tentative categories control type, degree, and style. Conceptualized control types, degree, and style as three different dimensions of control, each with associated properties and ranges Engaged with literature on balancing in organizational contexts (e.g., Bradach and Eccles 1989) Conceptualized control balancing as a higher level category. Defined it as making adjustments to the control configuration periodically in terms of control types, control degree, and control style, to allow the ISD offshoring project and relationship to progress Conceptualized three different combinations of control types, degree, and style (i.e., control configurations): authoritative control, coordinated control, trust-based control Compared our core category of control balancing with the notion of ‘a portfolio of control modes’ (Kirsch 1997), the literature on control dynamics (Choudhury and Sabherwal 2003; Kirsch 2004), and the literature on control evolution (Cardinal et al. 2004) Compared our findings on controlling ISD offshoring projects with prior literature on managing and controlling ISD offshoring projects and relationships (e.g., Choudhury and Sabherwal 2003; Dibbern et al. 2008; Levina and Vaast 2008; Rai et al. 2009; Sabherwal 1999)