Review for Final Exam
advertisement
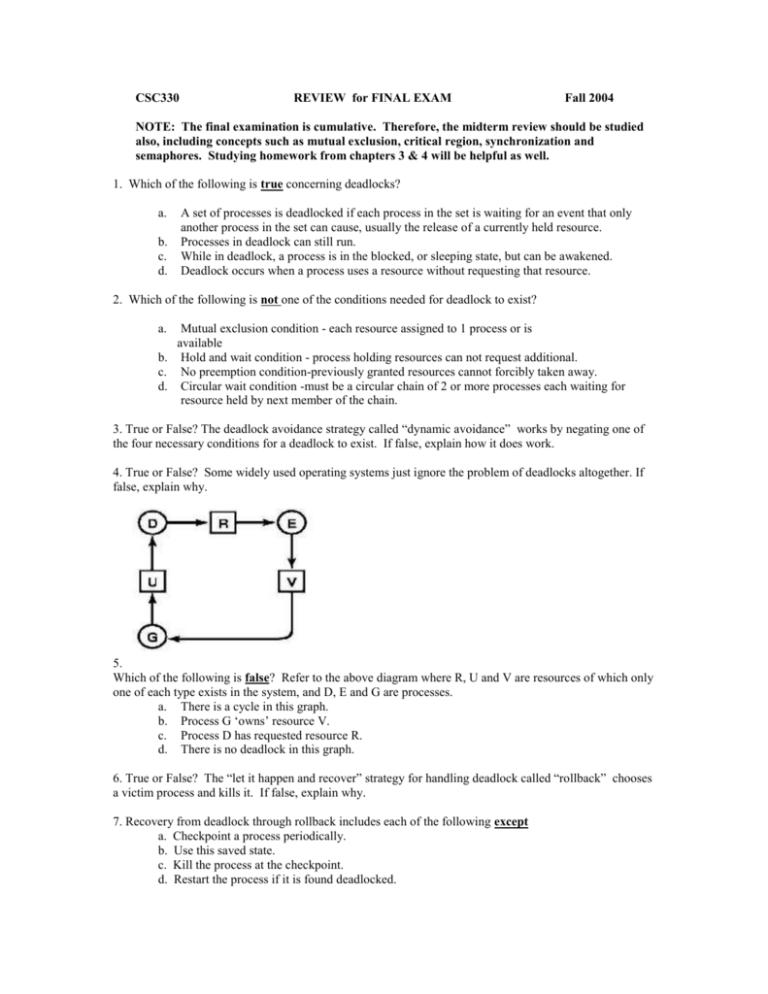
CSC330 REVIEW for FINAL EXAM Fall 2004 NOTE: The final examination is cumulative. Therefore, the midterm review should be studied also, including concepts such as mutual exclusion, critical region, synchronization and semaphores. Studying homework from chapters 3 & 4 will be helpful as well. 1. Which of the following is true concerning deadlocks? a. b. c. d. A set of processes is deadlocked if each process in the set is waiting for an event that only another process in the set can cause, usually the release of a currently held resource. Processes in deadlock can still run. While in deadlock, a process is in the blocked, or sleeping state, but can be awakened. Deadlock occurs when a process uses a resource without requesting that resource. 2. Which of the following is not one of the conditions needed for deadlock to exist? a. Mutual exclusion condition - each resource assigned to 1 process or is available b. Hold and wait condition - process holding resources can not request additional. c. No preemption condition-previously granted resources cannot forcibly taken away. d. Circular wait condition -must be a circular chain of 2 or more processes each waiting for resource held by next member of the chain. 3. True or False? The deadlock avoidance strategy called “dynamic avoidance” works by negating one of the four necessary conditions for a deadlock to exist. If false, explain how it does work. 4. True or False? Some widely used operating systems just ignore the problem of deadlocks altogether. If false, explain why. 5. Which of the following is false? Refer to the above diagram where R, U and V are resources of which only one of each type exists in the system, and D, E and G are processes. a. There is a cycle in this graph. b. Process G ‘owns’ resource V. c. Process D has requested resource R. d. There is no deadlock in this graph. 6. True or False? The “let it happen and recover” strategy for handling deadlock called “rollback” chooses a victim process and kills it. If false, explain why. 7. Recovery from deadlock through rollback includes each of the following except a. Checkpoint a process periodically. b. Use this saved state. c. Kill the process at the checkpoint. d. Restart the process if it is found deadlocked. 8.Using the information in the above matrices and vector, E, complete the P vector showing the total resources of each type assigned, and the A vector, showing the resources still available. The E vector shows the total number of each type resource in the system. Then, use the Banker’s Algorithm for multiple resources, to determine whether the system is safe or not. Show your work and explain your answer. 9. True or False: It is better to prevent deadlocks than to try to avoid them. If false, explain why. 10. Which of the following is false, or impossible, when an operating system uses the strategy of “prevention” to deal with deadlocks? a. Require all processes to request resources before starting, in a system where all processes know all resources that will be needed. b. Impose a numbering sequence on all resources in the system, and require processes to request resources in that order. c. Require processes to give up all resources held, before requesting additional resources and then request all immediately needed. d. It is impossible to prevent deadlocks. 11. True or False: A "file system" is part of an operating system. If false, explain why. 12. Each of the following is a reason for files except: a. to allow multiple processes access to data at the same time. b. to provide disk space for processes too large for main memory. c. to store large amounts of information. d. to provide persistent data. 13. In Unix and Linux all files are arranged in _________________________________. 14. Which of the following serves to attach a file system on a device to a specific directory? a. mnt /dev/fd0 /floppy b. umnt /dev/fd0 /floppy c. mount /dev/fd0 /mnt/floppy d. umount /dev/fd0 /mnt/floppy 15. Explain the use of the command: mount dev dir 16. When a file is opened, the directory entry provides information needed to find the file. This may be any one of the following, depending on the method used, except: a. The disk address of the entire file. b. The number of the first block of the file. c. The number of the i-node. d. The address of the FAT. 17. True or False: The main function of the directory system is to map the ASCII name of a file onto the information needed to locate the data. If false, explain why. 18. True or False: While the virtual address space of a process may be paged, file storage is always in contiguous blocks of disk space. If false, explain why. 19. Contiguous allocation of disk space for files is efficient for devices such as CD-ROMS because a. They are cheap, and can be replaced easily when severe fragmentation occurs. b. The file size and number of blocks needed are known in advance. c. A seek operation will be done for each block of a file stored on such a device. d. Keeping track of a file stored on such a device, does not require knowing the disk address of the first block of the file or the number of blocks in the file. 20. True or False: One advantage of storing files in a linked list of disk blocks is that no disk space is lost to external fragmentation. If false, explain why. 21. Linked list allocation of files is efficient for a. Random access of data in a file. b. Storing an amount of data that is a power of two in a block. c. Sequential access of data in a file. d. Internal fragmentation but not for external fragmentation. 22. True or False: Files may be stored in blocks on a disk without a pointer in each block that holds the address of the next block of the file. If false, explain why. 23. Which of the following is false for a File Allocation Table? a. A FAT eliminates the need for part of a block of a file to be a pointer to the next block of the file. b. As disks grow larger, a FAT grows linearly with them. c. The entire FAT does not need to be in memory all of the time and therefore, does not need to be paged. d. If the first block of a file is stored in physical block number 5 of the disk, the value stored in cell 5 of the FAT is the physical block number of the second block of the file. 24. True or False: The value stored in cell 'x' of a File Allocation Table is the physical location of the next logical block of the file. 25. Suppose a disk holds 20-GB of data in 1-KB size blocks. If each entry in a FAT for this disk takes 4 bytes, how much main memory does the FAT need? 26. True or False: Random access of data in a file stored in non-contiguous blocks on a device is NOT improved when a FAT is used. If false, explain why. 27. True or False: An i-node, or index node, is a data structure which stores the attributes of a file and the disk addresses of all the blocks of the file. If false, explain why. 28. An array of i-nodes a. is stored in main memory. b. is usually bigger than a FAT. c. is proportional to the size of the disk. d. has room for a variable number of disk addresses in each node. 29. A problem with using an array of i-nodes to hold file information is a. the size of the array is proportional to the maximum number of files that the system permits to be open at one time. b. an i-node need be in memory only when the file whose information the i-node holds, is open. c. the array is usually far smaller than the space needed by a FAT. d. a file may grow larger than the number of disk block addresses each i-node holds. 30. Which of the following is true? A directory entry may contain: a. a file name, attributes of the file and disk addresses. b. only a reference to an i-node. c. a file name and the attributes and disk addresses as well as a reference to an i-node. d. a file name alone. 31. True or False: A directory requirement is that all file names are the same length. If false, explain why. 32. Which of the following is false: a. A directory is held in main memory. b. When a file is opened, the operating system finds the file's directory entry by a user-supplied path name. c. A directory entry contains the information needed to find the blocks on a disk in which a file is stored. d. A directory entry does not contain such information as the file's owner or time of creation. 33. True or False: It is possible for a file to appear in multiple directories at the same time. If false, explain why. 34. CPU scheduling decisions may take place when a process does each of the following except: a. Switches from running to waiting state. b. Switches from running to ready state. c. Switches from ready to waiting. d. Terminates. 35. The dispatcher module does each of the following except: a. Switching context. b. Switching to user mode. c. Jumping to the proper location in the user program to restart that program. d. Selecting another process to use the CPU. 36. In batch systems each of the following are important considerations except: a. Throughput - maximize jobs per hour. b. Response time - respond to requests quickly. c. Turnaround time - minimize time between submission and termination. d. CPU utilization - keep the CPU busy all the time. 37. True or False: In some operating systems a process retains control of the CPU until the process blocks for I/O, or other reason, or terminates. If false, explain why. 38. Suppose a system uses the Shortest Job First scheduling algorithm (non-preemptive version). Given the following circumstances, complete the Gantt Chart. Process Arrival Time Burst Time P1 0.0 7 P2 2.0 5 P3 4.0 1 P4 5.0 3 Process Arrival Time P1 0.0 P2 2.0 P3 4.0 P4 5.0 Burst Time 7 4 1 4 39. Complete the following Gantt Chart for the above circumstances when the preemptive version of the SJF scheduling algorithm is used. 40. True or False: In priority scheduling the priority number assigned to each process by the user or administrator must be static and cannot change during execution. If false, explain why. 41. True or False: An advantage of priority scheduling is that starvation never occurs. If false, explain why. 42. The following is true for which scheduling algorithm? "Each process gets a small unit of CPU time (time quantum), usually 10-100 milliseconds. After this time has elapsed, the interval timer generates an interrupt and the process is preempted and added to the end of a queue." a. First Come First Served b. Round Robin c. Priority d. Banker's Algorithm 43. Which of the following is false with respect to the use of Multi-Level Feedback Queues for scheduling processes? a. This algorithm basically treats all jobs the same. b. This algorithm customizes the scheduling of processes based on the process’ performance characteristics. c. Each queue gets a certain amount of CPU time, which it can schedule amongst its processes. d. A process can move between the various queues and aging, implemented this way, avoids starvation. 44. True or False: A process may be swapped in and out of main memory in its entirety, or a process may be broken up into pieces that do not need to be located contiguously in main memory nor do all pieces of the process need to be loaded into main memory during execution. If false, explain why. 45. True or False: When an operating system brings into main memory only a few pieces of a program at a time, an interrupt is generated when an address is needed that is not in main memory. If false, explain why. 46. When an address that is needed is not in main memory, what is the order in which the following actions occur? a. The operating system issues a disk I/O Read request. b. Another process is dispatched to run while the disk I/O takes place. c. An interrupt is issued when disk I/O complete which causes the operating system to place the affected process in the Ready state. d. The operating system places the process in a blocked state. 47. When a processor spends most of its time swapping pieces rather than executing user instructions, it is said that the processor is __________________. a. paging. b. thrashing. c. under-utilized. d. using the principle of Locality. 48. True or False: When each process has its own page table, it is not necessary to have a bit to indicate whether a page is in main memory or not. If false, explain why. 49. Which of the following is true? a. A modify bit is used to indicate if a page has been altered since it was last loaded into main memory. b. If no change has been made to a page, that page must be written to the disk when the page is to be swapped out. c. When a process is running, its entire page table must be in main memory. d. A page table is usually stored in the memory cache. 50. True or False: When an instruction requires a specific virtual address, the processor examines the TLB, and if the page table entry is present (a hit), the frame number is retrieved and the real address is formed. If false, explain why. 51. A high-speed cache that contains page table entries that have been most recently used is called a(n) _____________________________. a. Working Set. b. Inverted Page Table. c. Page Fault Handler. d. Translation Lookaside Buffer. 52. Which of the following is false? a. The smaller page size, the less the amount of internal fragmentation. b. With small page size, there are more pages required per process and page tables are small. c. Larger page tables means a large portion of the table will be in virtual memory. d. Secondary memory is designed to efficiently transfer large blocks of data, so a large page size is usually better. 53. True or False: Multiprogramming is possible with management that divides main memory into fixed sized partitions. If false, explain why. 54. Binding of instructions and data to memory may be done at __________________time, if the process can be moved during its execution from one memory segment to another and hardware (e.g., base and limit registers) support for address maps is available. 55. In compile-time and load-time address binding schemes _________________ are the same but not in execution-time address binding. a. virtual and logical addresses b. logical and physical addresses c. page numbers and frame numbers d. page numbers and segment numbers 56. Addresses that are calculated at load time are called ________________________. 57. Multiprogramming introduced 2 problems into memory management: a. base and limit registers. b. wait time and turnaround time. c. overloading and overriding. d. relocation and protection. 58. True or False: The compiler and linker must know where in physical memory a program will be stored. If false, explain why. 59. The goal of multiprogramming is a. better turnaround time. b. no page faults. c. continuous CPU utilization. d. small page tables. 60. True or False: In both interactive systems and batch systems, processes often spend 80% of their execution time waiting for I/O, and it is possible for all processes to block at the same time. If false, explain why. 61. How many processes, whose fraction of time spent waiting for I/O is p=4/5, should be kept in memory at a time to achieve 99% CPU utilization? SHOW WORK. 62. True or False: timesharing systems and graphically oriented pc’s often have more concurrent processes than main memory can hold, at which time the system will freeze. If false, explain why. 63. ___________________ refers to bringing a process in its entirely into memory, running it for a while, the returning it to a disk. a. paging b. segmentation c. swapping d. relocation 64. True or False: When a process is brought into memory again, all addresses may be relocated. If false, explain why. 65. When processes are moved out of memory, holes of various sizes are left. When there is enough memory available to satisfy a process' space requirement, but that memory is not contiguous (so the process cannot be brought into memory), the condition called _______________________________ has developed. a. dynamic memory allocation b. random access c. external fragmentation d. memory mapping 66. True or False: Multiprogramming requires keeping track of free memory space. If false, explain why. 67. Which of the following is true about bitmaps? a. A '1' means a bit of memory is allocated and a '0' means that bit is free. b. A bitmap does not need to be in memory and does not take up memory space. c. All sequential '0' bits are in the same memory allocation unit. d. The size of a bitmap depends on the size of the memory allocation unit. 68. True or False: Free memory space may be kept track of by a linked list nodes. If false, explain why. 69. Each node in a linked list being used to keep track of memory usage contains all of the following data except: a. The starting address of the allocation unit. b. A 'dirty' bit that indicates whether that data has been modified. c. The number of allocation units in the process or hole. d. A field indicating whether that segment of memory contains a process or not. 70. The __________________algorithm for allocating memory when linked list management is used, chooses the largest available hole, breaking off a hole that is large enough to be useful( i.e. hold another process). a. Worst Fit b. Best Fit c. Next Fit d. First Fit 71. True or False: 'Paging' and 'swapping' are synonyms. If false, explain why. 72. True or False: Paging is a memory management scheme that permits a physical address space to be noncontiguous. If false, explain why. 73. Program, or compiler, generated addresses begin with 0 and are called: a. physical addresses b. page numbers c. virtual addresses d. frame numbers 74. A virtual address space is divided into _________________ and the physical address space is divided into corresponding ________________. a. frames, pages b. pages, blocks c. frames, offsets d. pages, frames 75. The hardware that supports paging includes a(n) ______________________ to keep track of whether a page is in physical memory or not. a. reference bit b. present/absent bit c. base register d. limit register 76. An address of size 'm', coming into the MMU (where page size is given by 2n ) is split into 2 parts, where the high order m - n bits is for the page number and the n low order bits for the ___________, which tells where the address lies on the page. a. modification bit b. page fault c. offset d. frame number 77. Suppose a page size of 212 = 4,096 addressable bytes is being used by a memory management system. Also, 16 bit addresses are used for the virtual address space. How many bits in each address are needed for the offset? 78. Suppose a page size of 212 = 4,096 addressable bytes is being used by a memory management system. Also, 16 bit addresses are used for the virtual address space. Given virtual address: 20500, determine the page on which this address is found and its offset. 79. Suppose a page size of 212 = 4,096 addressable bytes is being used by a memory management system. Also, 16 bit addresses are used for the virtual address space. Given virtual address: 20500, if this page is in memory, how far from the beginning of its frame is it found? 80. True or False: Each process needs its own page table. If false, explain why. 81. 32 bit addresses give a virtual address space of more than ____ gigabytes. 82. In a traditional page table with 16 bit addressing and 4KB pages, the index corresponds to the page number and the table entry contains a. the offset of the physical address. b. the frame number, if the page is in physical memory. c. the virtual address of the page. d. the physical address of the frame. 83. To avoid keeping huge page tables in memory all at once, two-level tables work well with 32 bit addressing for a virtual address space. Which of the following is false? a. The page table is paged. b. The first 10 bits of an address gives the index into the top level page table. c. There are 1024 possible entries in the top level page table. d. Each entry in the top level page table represents 4 gigabytes of addressable memory found in the second level table. 84. True or False: With Paging we have no external fragmentation: any free frame can be allocated to a process that needs it. If false, explain why. 85. Which of the following is false? a. For each process, a pointer to the page table is stored with the other register values in the PCB (process control block). b. When the dispatcher starts a process, it must reload all registers and copy the stored page table values into the "hardware page table" in the MMU, consisting of dedicated registers with high-speed logic, but that design is only satisfactory if the page table is small. c. Today’s computers allow page tables with 1 million or more entries, which fast registers can handle efficiently. d. With 32 bit addressing and 4K pages, where each entry takes 4 bytes, each process may need 4 megabytes of physical address space for its page table, . 86. Place the following into the order they would occur. (List 1 - 10 and write letter of action next to no.) a. Determine that the interrupt was a page fault. b. Trap to the operating system ( also called page fault interrupt). c. Correct the page table /other tables to show that the desired page is now in memory. d. While waiting, allocate the CPU to some other user. e. Take process out of waiting queue and put in ready queue to wait for the CPU again. f. Save the user registers and process state; i.e. process goes into waiting state. g. Check that the page reference was legal and, if so, determine the location of the page on the disk. h. Issue a read from the disk to a free frame and wait in a queue for this device until the read request is serviced. After the device seek completes, the disk controller begins the transfer of the page to the frame. i. Interrupt from the disk occurs when the I/O is complete. Must determine that the interrupt was from the disk. j. Restore the user registers, process state and new page table, then resume the interrupted instruction. 87. Which of the following is false concerning a Translation Lookaside Buffer? a. This is a small hardware device for mapping virtual addresses to physical addresses without going through the page table. b. A TLB is sometimes called "associative memory". c. This works because most programs make a small number of references to a large number of pages. d. When the MMU is presented a virtual address, the hardware checks to see if its page is present in the TLB, which is called a "hit". 88. When a program tries to access an address whose page is not in memory, ______________ occurs. a. demand paging. b. locality of reference. c. aging. d. page fault. 89. The method of an "inverted page table" a. is appropriate for very large virtual address spaces such as 64-bit. b. uses one entry per page of virtual address space. c. requires searching the entire table. d. uses one entry per page frame in physical memory. 90. True or False: An inverted page table saves a great deal of memory, but searching the table would be prohibitively slow without a TLB and hashing. If false, explain why. 91. True or False: In the "not recently used" page replacement algorithm, the combination: not referenced, modified is not possible. If false, explain why. 92. True or False: The most commonly used page replacement algorithm is FIFO. If false, explain why. 93. When a process is created an area the size of the process is reserved on the disk is the ________area. 94. True or False: When a process is created, the entire process image is immediately copied to the backing store. If false, explain why. 95. An alternate method to paging, which uses multiple separate address spaces, each of which begins with zero, is ____________________. 96. True or False: Once a process is created, its size never changes. If false, explain why. 97. Which of the following is false concerning segmentation? a. A separate address space is allocated to only logical parts of a program that can grow. b. Procedures and data can be distinguished and protected separately. c. Segmentation allows sharing of procedures and data among multiple processes. d. Large graphical libraries can be used by several processes without having the library inside the process' virtual address space. 98. True or False: In 'memory-mapped files', 'mapping' means associating an ASCII file name with a virtual address in a process' virtual address space. If false, explain why. 99. Which of the following is false concerning memory-mapped files? a. Mapping is carried out by page faults: when the machine instruction attempts to read from an address that has been memory mapped, page 0 of the file is brought into memory. b. When multiple processes are accessing a file through memory-mapping, inconsistent versions may result. c. 'Unmapping' removes files from the backing store. d. Mapping works best in systems that support segmentation, because byte 'k' of a file is mapped onto byte 'k' of its segment. ANSWERS 1.a 2.b 3.f 4.t 5.d 6.f 7.c 8. P= 5 3 2 2 A=1 0 2 0 Safe (D can be satisfied completely) 9.f 10.d 11.t 12.b 13. a large tree structure 14.c 15. Used to attach device dev at location of dir in tree. 16.d 17.t 18.f 19.b 20.t 21.c 22.t 23.c 26.f 27.t 28.a 29.d 30.a 31.f 32.d 33.t 36.b 37.t 38. at time 7 P3 executes and completes at time 8 P4 executes and completes at time 11 P2 executes and completes 39. at time 2 P2 executes at time 4 P3 executes and completes at time 5 P2 executes and completes at time 7 P4 executes and completes at time 11 P1 executes and completes 40.f 41.f 42.b 43.a 47.b 48.f 49.a 50t 55.b 56. absolute addresses 61. 21 62.f 63.c 64.t 69.b 70.a 71.f 72.t 79. 20bytes 80.t 81. 4 86. 1b 2f 3a 4g 87. c 88.d 89b 90t 95. segmentation 96.f 97.a 44.t 51.d 57.d 65.c 73.c 82. b 5h 91.f 98t 45.t 52.b 58.f 66.t 74.d 83. d 6d 92.f 99c 24.t 34.c 46. d, a, b, c 53.t 54. run time 59.c 60.t 67.d 68.t 75.b 76.c 77. 12 84. t 85. c 7i 8c 9e 93. swap 94.f 25. 80mb 35.d 78.page=5, offset=20 10j








