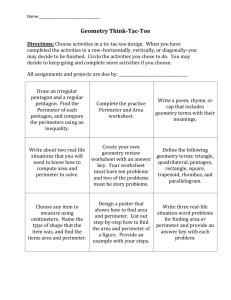
Security Perimeter - MnSCU Information Technology Services
advertisement

<name here> Security Domain Definition (DRAFT) Developed by: Your name Your organization Date DRAFT 11/12/02 Approvals Approver Title Date Revision Record Rev. # Date Description of Changes <name here> Security Domain Definition Revised By DRAFT 11/12/02 Table of Contents INTRODUCTION 1 SECURITY PERIMETER 2 PHYSICAL PERIMETER 2 LOGICAL PERIMETER 2 ASSETS 3 DATA 3 APPLICATIONS 3 HOSTS 3 NETWORK DEVICES 4 NETWORK PERIPHERALS 4 TELECOMMUNICATIONS DEVICES 4 STRUCTURES 4 FUNCTIONAL ROLES 4 GOODWILL 5 OWNERSHIP AND REVIEW CONTACT INFORMATION 6 6 <name here> Security Domain Definition DRAFT 11/12/02 Introduction The Security Domain defines limits of organizational control. The Security Domain: Is defined by physical and logical perimeter boundaries Includes assets that are by definition controllable Establishes scope of threat analysis <name here> Security Domain Definition Introduction 1 DRAFT 11/12//02 Security Perimeter Physical Perimeter The physical perimeter is defined as follows: Floor, ceiling, and external walls of: (Enter physical description or address) Logical Perimeter ( Insert visio drawing of logical network. Logical drawing should show logical placement of all assets tabulated on following pages ) The logical perimeter is defined as the external interfaces of the ( border device name(s) ). <name here> Security Domain Definition Security Perimeter 2 DRAFT 11/12//02 Assets Data The following data is included within the security perimeter. (List data types contained within the security perimeter) UNRESTRICTED WWW RESTRICTED Student data PROTECTED ISRS Credit card info Financial records Employee data Applications The following applications are included within the security perimeter: (List applications hosted within the security perimeter. All data types should have a corresponding application) ADMINISTRATIVE Groupwise client ISRS client MAPS client SEMA4 client Warehouse client Brio client ACADEMIC Faculty WEB Server App name NETWORK DNS SMTP WWW LDAP NDS RADIUS Terminal Services NTP Anti-virus DESKTOP Standard build Hosts The following hosts are included within the security perimeter: (Enter logical names and categorize by type. All applications should have a corresponding host here) Administrative Application Academic Application Network Service Client Computers (DNS logical name) Admin desktops User desktops App server logical name laptops PDA’s Library desktops <name here> Security Domain Definition Assets 3 DRAFT 11/12//02 Network Devices The following network devices are included within the security perimeter: (Enter logical names and categorize by type) Routers Switches/Hubs Firewalls Remote Access Cabling Room 234 Network Peripherals The following network peripherals are included within the security perimeter: (enter logical names and categorize by type) Printers IP Phones Telecommunications Devices The following telecommunications devices are included within the security perimeter: (be especially vigilant in identifying modems) PBX Modems FAX Structures The following Structures are included within the security perimeter: (Enter address of structure(s) containing security perimeter. The previously defined physical security perimeter boundaries may be a subset of this. For example, the structure entered here may be 123 Main St, and the physical security perimeter previously defined may be room 101 of 123 Main St. This section is used to evaluate environmental hazards such as flood and fire. Risks that transcend the previously defined physical security perimeter) Functional Roles The following functional roles are included within the security perimeter: (Identify functional roles performed within the security perimeter here) WWW support Data Base Analysts <name here> Security Domain Definition Assets 4 DRAFT 11/12//02 System Analysts WAN services LAN services System Developers Help Desk Data warehouse Security Administrators Management System Managers Administrative support Business Analysts Quality Control Training Technical writers Add or delete more as required Goodwill The following elements of goodwill are included within the security perimeter: Reputation: confidence in the ability of MnSCU to fulfill its mission Image: public perception of MnSCU Note: 1. At this point all assets should be identified and categorized. 2. Identified assets should be contained within the defined physical and logical security perimeters. 3. Hard assets should be identifiable on the logical diagram 4. An institution may choose to segment itself by using multiple domain definitions to address multiple levels of risk and risk tolerance. Distinct Security Domain definitions may include data centers, administrative areas, faculty offices, and student computer labs. 5. This document defines the scope for the actual performance of the security risk assessment. 6. All assets identified here will be accounted for in the Security risk assessment spreadsheet. 7. Assets may be grouped together if they have a common threat profile. For example, one entry can be made for administrative desktops if they are all the same and on the same LAN segment. <name here> Security Domain Definition 5 DRAFT 11/12//02 Ownership and Review This Domain definition is owned by the Information Security Manager. This Domain definition shall be reviewed on a yearly basis. Change to this Domain definition shall be in accordance with the MnSCU document control process. Contact Information Include contact info here <name here> Security Domain Definition Ownership and Review 6