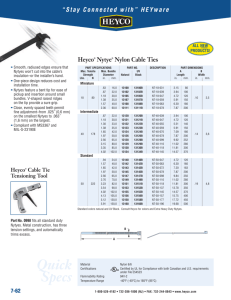
Lesson 1-2: Connectivity and Internetworking Devices
advertisement
COSC 406 Spring 2005 FINAL EXAM – Study Guide Covered Materials: Chapters 1 to 21, TEST 1, TEST 2, Test 1 and Test 2 Study Guides, Class Quizzes, and specific Netknowledge Study Documents There will be following Five categories of questions. Part 1: Repeat questions from Test 1 & Test 2: 20% of total score Part 2: You will expect at least 5 acronyms and their definitions - 10% Chapters 1 to 21 FDM TDM DWDM FDDI MAC LLC/SNAP OUI AUI FOIRL DST PCM DSU/CSU SONET ISDN DSL ADSL HDSL CATV FTTC FTTH HFC CCITT SMDS CIDR ARP ICMP MTU TCP/IP Part 3: 5 to 7 short questions (40%) Chapters 15, 16, and 17 - Write the differences between delay and throughput with examples and their relationship. What is an effective throughput? What a delay-throughput product signifies? - What is the network’s jitter? How the telephone system and data networks handle jitter? - Explain the differences among Sequencing Out-of-order delivery of packets and Sequencing to eliminate Duplicate packets. - What is the main difference between the Data Overrun and the Network Congestion? - What techniques are used to resolve Data overrun (stop-and-go and Sliding Window techniques, their advantages and disadvantages)? - What techniques are used to resolve Network Congestion? chapter 18) What are the main commercial protocol stacks and their vendor names other than the TCP/IP? - Explain the differences between a class-full IP address and CIDR address schemes. What are the main advantages of CIDR address scheme over a class-full address scheme? What are the natural (address) masks for Class A, B, and C? Explain why subnetting is necessary. Briefly describe how a subnet is created. Chapters 19, 20, 21 What is ARP? Describe one of the three Address Resolution Techniques (read each one). The relative advantages and disadvantages of three techniques (Figure 19.4). How ARP message is delivered? (Figure 19.5)? How an ARP packet look like (Figure 19.7)? How an ARP frame is identified (Figure 19.8)? What’s your understanding of Caching ARP responses? In which protocol layer(s) the address is resolved? What are the Virtual Packets and IP datagram? What is Best-Effort Delivery? Examine the Header format of an IP datagram (Figure 20.4) and explain the sections “IDENTIFICATION”, “FLAGS”, “FRAGMENT OFFSET” (consult Chapter 21) Why fragmentation of a packet is required and it is handled in the network? Part 4. Multiple Choices – 20 questions (20%) To Answer these questions, consult Lesson 2-2 of NetKnowledge and your textbook 1. Which type of signaling scheme represents data sent as discrete signals? a. Digital signaling b. Analog signaling c. Asynchronous d. Synchronous 2. Which type of signaling scheme represents continuously changing data? a. Digital signaling b. Analog signaling c. Asynchronous d. Synchronous 3. Which type of bit synchronization transmission requires both a start bit and a stop bit for clocking purposes? a. Digital signaling b. Analog signaling c. Asynchronous d. Synchronous 4. Group of bits, including data and control signals, arranged in a specific format and transmitted as a whole, are called what? a. Clocking b. Sequencing c. Synchronization d. Packets To Answer these questions, consult Lesson 2-3 of NetKnowledge and your textbook 5. Which type of transmission do all devices on the shared network hear and accept? a. Unicast b. Multicast c. Broadcast d. Baseband 6. Which type of signaling uses the entire bandwidth of a cable for a single transmission and allows only one signal at a time? a. Unicast b. Multicast c. Broadcast d. Baseband 7. When all devices have equal access to the network and no one device has priority over another device, what is this called? a. Carrier Sense b. Multiple Access c. Collision Detection d. Collision Domain 8. What is the term used to describe the ability of a device to sense simultaneous transmission attempts and wait a random amount of time before retransmitting data? a. Carrier Sense b. Multiple Access c. Collision Detection d. Collision Domain 9. What is the ability to listen for a jam signal before transmitting data called? a. Carrier Sense b. Multiple Access c. Collision Detection d. Collision Domain 10. Ethernet standards include specifications for which of the following? a. Cabling b. Frame format c. Network access conventions d. All of the above To Answer these questions, consult Lesson 2-4 of NetKnowledge and your textbook 11. In 10BASE5 Ethernet networks, what type of cable is specified? a. 500-ohm thick coaxial cable b. 50-ohm thick coaxial cable c. 500-ohm thin coaxial cable d. 50-ohm thin coaxial cable 12. In 10BASE2 Ethernet networks, what type of cable is specified? a. 500-ohm thick coaxial cable b. 50-ohm thick coaxial cable c. 500-ohm thin coaxial cable d. 50-ohm thin coaxial cable 13. A BNC-T connector is used with which Ethernet type? a. 10BASE5 b. 10BASE2 c. 10BASE_T d. 100BASE-T e. 10BASE-F 14. The maximum number of devices on a 10BASE-T network is what? a. 30 b. 100 c. 500 d. 1,024 15. The maximum number of devices on a 10BASE5 network is what? a. 30 b. 100 c. 500 d. 1,024 16. What is an AUI connector? a. A 15-pin connector used with an external transceiver b. Device used only with a fan-out unit c. The standard connector used for 100BASE-T connections d. Device used for all Ethernet connections 17. The maximum cable length for each segment in 10BASE-T networks is what? a. 100 meters b. 185 meters c. 285 meters d. 500 meters 18. A 10Base-T network may use which cable types? a. Category 3 b. Category 4 c. Category 5 d. All of the above 19. The maximum number of devices per segment on a 10BASE-F network is what? a. 30 devices b. 1,024 devices c. 2 devices d. 500 devices 20. What is the difference between a physical bus and a logical bus/physical star topology? a. The physical bus uses a hub b. The logical bus, physical star is always used for Ethernet networks c. The logical bus, physical star uses a hub d. There is no difference 21. What is the topology of 10BASE-T networks? a. Physical bus/logical star b. Physical/logical star c. Physical/logical bus d. Physical star/logical bus 22. Which type of cabling is used to connect devices in a 10BASE-F network? a. Category 5 b. UTP c. STP d. Fiber optic 23. The maximum number of repeaters/hubs per LAN allowed on a 10BASE-T segment is: a. 4 b. 100 c. 30 d. 925 24. Maximum fiber cable distances are: a. 550 meters b. 250 meters c. 2,000 feet d. 2,000 meters 25. What is an AUI? a. An external transceiver b. An internal transceiver c. A transceiver cable d. An N-type connector 26. Which cable type is used in LANs over 1,000 meters in length? a. UTS b. STP c. Category 5 d. Fiber Optic 27. Which type of copper cable is most useful when EMI and distances of more than 1,000 meters are a concern? a. UTP b. STP c. Thick coaxial d. Thin coaxial To Answer these questions, consult Lesson 2-5 of NetKnowledge and your textbook 28. Token Ring networks operate at a. 10, 100 or 1000 Mbps b. 4, 16, 100 or 128 Mbps c. 1 Gbps d. 10, 16 or 1000 Mbps e. 4 or 10 Mbps 29. The Token Ring token frame size is a. 16 bits b. 24 bits c. 32 bits d. 48 bits e. 64 bits 30. After copying data from the token frame, a receiving device a. Releases the token b. Reads error control information from the frame c. Uses the token frame to send new data d. Destroys the token frame e. Send the frame back to the sending device 31. Token Ring networks a. Fail more often than Ethernet networks b. Fail more gracefully than Ethernet networks c. Never fail d. Cannot accept priority assignments e. Must use fiber optic cabling 32. To detect and correct errors a. Every device on a Token Ring network is an active monitor b. Each device on a Token Ring network diagnoses its own errors c. Each device gives control to its nearest active upstream neighbor d. One device is designated as the active monitor e. All devices send out a Claim Token 33. FDDI operates at a. 10 Mbps b. 4 or 16 Mbps c. 100 Mbps d. 1000 Mbps e. 4.5 Mbps 34. To transport streaming media data, FDDI a. Opens a switched circuit b. Can synchronize data with a clocking field c. Can only transmit one frame when the token has been captured d. Uses fiber optic cabling 35. When an FDDI sending device has captured a token a. It can only transmit one frame b. It can transmit as many frames as it wants c. It can only transmit error diagnostics d. It can transmit frames until a time limit expires e. It releases the token 36. A secondary ring in FDDI a. Automatically steps in if the primary ring fails b. Allows priority communication to select devices c. Doubles communication speed d. Connects to Token Ring networks 37. Which computer manufacturer uses LocalTalk? a. IBM b. Digital Equipment Corporation c. Intel Corporation d. Motorola e. Apple Computer 38. LocalTalk operates at a. 230 Kbps b. 1 Mbps c. 10 Mbps d. 100 Mbps e. 1 Gbps 39. LocalTalk connects using a. Fiber optic cable b. Coaxial cable c. Twisted pair cable d. Microwave radio e. Photonic switches To Answer these questions, consult Lesson 3-2 of NetKnowledge and your textbook 40. Which type of switching provides lowest delays? a. ATM b. Packet switching c. Circuit switching d. Open circuit leased line 41. Which type of switching introduces the greatest delays? a. ATM b. Packet switching c. Circuit switching d. Open circuit leased line 42. Which application requires the highest quality of service? a. Electronic mail b. Video conferencing c. Audio broadcasting d. Web browsing 43. Which application requires the least quality of service? a. Electronic mail b. Video conferencing c. Audio broadcasting d. Web browsing 44. Which switching method provides a flexible quality of service based on need? a. ATM b. Packet switching c. Circuit switching d. Open circuit leased line 45. Network error rates are measured as a. The number of good bits divided by the number bad bits b. The number of good packets added to the number of bad packets c. The number of bad bits divided by the number of good bits d. The number of bad bits subtracted from the number of good bits 46. Which technique detects more kinds of errors? a. Checksum b. Cyclical redundancy check c. Circuit switching d. Authentication 47. X.25 networks detect and correct errors by a. Checking the CRC and requesting a new copy of a bad packet from the sending switch b. Using a checksum and discarding bad packets c. Allowing the routers and devices on the sending an receiving LANs to detect and handle errors d. Using the lowest level of the protocol stack 48. Frame relay networks detect and correct errors by a. Checking the CRC and requesting a new copy of a bad packet from the sending switch b. Using a checksum and discarding bad packets c. Allowing the routers and devices on the sending and receiving LANs to detect and handle errors d. Using the lowest level of the protocol stack 49. A virtual private network (VPN) a. Requires a private leased line b. Uses encryption to make private network connections across the Internet c. Requires users to connect to a dial-up server d. Can only transport TCP/IP protocols Part 5 Matching – 10 questons (10%) To Answer these questions, consult Lesson 1-2 of NetKnowledge and your textbook B. Identify which layer of the OSI model each device is assigned. 1. Bridge 2. Repeater 3. Network Interface Card 4. Router 5. Transceiver 6. Multistation Access Unit (MAU) 7. Hub 8. Switch D. Match the OSI layer with the appropriate function from the list below. Layer Function 7 – Application ____ A. Routes and addresses messages 6 – Presentation ____ B. Translates data so software applications can read it 5 – Session ____ C. Allows user software to access network services 4 – Transport ____ D. Enables network logins 3 – Network ____ E. Frames and controls data flow 2 – Data Link ____ F. Provides reliable transmission and confirmation 1 – Physical ____ G. Defines media specifications E. Label network hardware elements and functions with the appropriate OSI layer. Layer Device and Function Physical (as an example) Repeater.a connector that filters, amplifies and retransmits information to allow signals to travel further along a network. Bridge.connects small numbers of similar LANs into an internetwork or splits an overloaded network into smaller parts without translation. Router.connects different networks together and directs information by best route (using algorithms) to destinations. NIC.provides connection of computer to transmission medium on the network. Gateway.links different network types together. Can be hardware or software that allows different protocols to exchange information. Hub.provides central location with ports where cables on a network come together for connection Modem.allows computers on a network to exchange information by translating into binary form for transmission over telephone lines. Cable.wires used to connect devices on a network. To Answer these questions, consult Lesson 2-3 of NetKnowledge and your textbook F. Matching: Match the part of the frame with its definition. 1. ___ Preamble A One byte code in the LLC field used to identify the protocol that will encapsulate the data field 2. ____ Start of Frame B Hardware address of the destination device 3. ___ Destination Address C Actual information being transmitted 4. ___ Source Address D Specifies the protocol used for sending the frame 5. ___ Type Field E Specifies the length of the data within the frame 6. ___ Length Field F Type of frame check that detects errors that occur in the frame during transmission 7. ___ Pad G Added to the data field of IEEE 802.3 when the data is less than 46 bytes 8. ___ Data H Establishes synchronization and transceiver conditions 9. ___ DSAP I Field with 10101011 sequence separate 10. __ CRC J Hardware address of the sending device To Answer these questions, consult Lesson 3-1 of NetKnowledge and your textbook G. Matching 1. ____ The speed of the least expensive kind of leased line. 2. ____ A digital telephone line likely to be used by an Internet Service Provider. 3. ____ A digital telephone line that can carry data at 1.544 Mbps. 4. ____ The speed of a single channel on a T1 line. A. 8 B. T1 C. T3 D. 64 Kbps E. 7 F. 6 G. 128 Kbps H. 56 Kbps