Virtual Private Networks A Technology Overview
advertisement
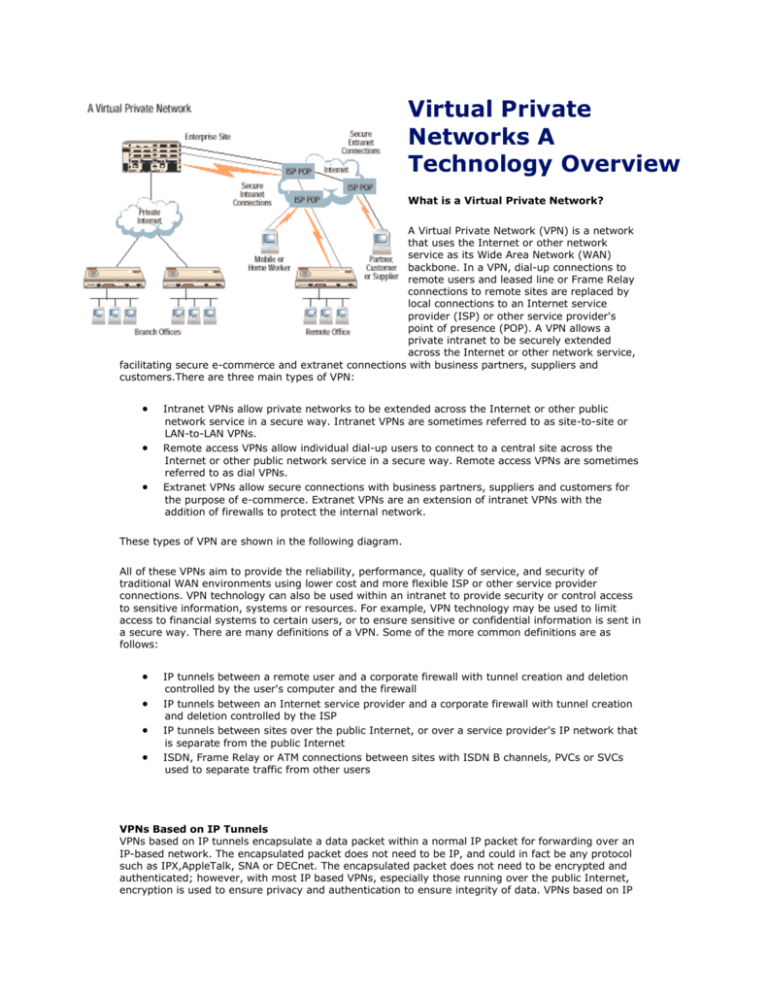
Virtual Private Networks A Technology Overview What is a Virtual Private Network? A Virtual Private Network (VPN) is a network that uses the Internet or other network service as its Wide Area Network (WAN) backbone. In a VPN, dial-up connections to remote users and leased line or Frame Relay connections to remote sites are replaced by local connections to an Internet service provider (ISP) or other service provider's point of presence (POP). A VPN allows a private intranet to be securely extended across the Internet or other network service, facilitating secure e-commerce and extranet connections with business partners, suppliers and customers.There are three main types of VPN: Intranet VPNs allow private networks to be extended across the Internet or other public network service in a secure way. Intranet VPNs are sometimes referred to as site-to-site or LAN-to-LAN VPNs. Remote access VPNs allow individual dial-up users to connect to a central site across the Internet or other public network service in a secure way. Remote access VPNs are sometimes referred to as dial VPNs. Extranet VPNs allow secure connections with business partners, suppliers and customers for the purpose of e-commerce. Extranet VPNs are an extension of intranet VPNs with the addition of firewalls to protect the internal network. These types of VPN are shown in the following diagram. All of these VPNs aim to provide the reliability, performance, quality of service, and security of traditional WAN environments using lower cost and more flexible ISP or other service provider connections. VPN technology can also be used within an intranet to provide security or control access to sensitive information, systems or resources. For example, VPN technology may be used to limit access to financial systems to certain users, or to ensure sensitive or confidential information is sent in a secure way. There are many definitions of a VPN. Some of the more common definitions are as follows: IP tunnels between a remote user and a corporate firewall with tunnel creation and deletion controlled by the user's computer and the firewall IP tunnels between an Internet service provider and a corporate firewall with tunnel creation and deletion controlled by the ISP IP tunnels between sites over the public Internet, or over a service provider's IP network that is separate from the public Internet ISDN, Frame Relay or ATM connections between sites with ISDN B channels, PVCs or SVCs used to separate traffic from other users VPNs Based on IP Tunnels VPNs based on IP tunnels encapsulate a data packet within a normal IP packet for forwarding over an IP-based network. The encapsulated packet does not need to be IP, and could in fact be any protocol such as IPX,AppleTalk, SNA or DECnet. The encapsulated packet does not need to be encrypted and authenticated; however, with most IP based VPNs, especially those running over the public Internet, encryption is used to ensure privacy and authentication to ensure integrity of data. VPNs based on IP tunnels are mainly self deployed; users buy connections from an ISP and install VPN equipment which they configure and manage themselves, relying on the ISP only for the physical connections. VPN services based on IP tunnels are also provided by ISPs, service providers and other carriers. These are usually fully managed services with options such as Service Level Agreements (SLAs) to ensure Quality of Service (QoS). A Ten Point Plan for Building a VPN shows some of the steps taken when deploying an Internetbased VPN. The following diagram shows an Internetbased VPN that uses secure IP tunnels to connect remote clients and devices. VPNs based on IP tunnels provide the following benefits: provided using a single secure connection Reduced telecom costs, as dedicated and long distance connections are replaced with local connections Greater flexibility in deploying mobile computing, telecommuting and branch office networking Easier e-commerce and extranet connections with business partners, suppliers and customers External Internet access, and internal intranet and extranet access can be The main disadvantage of VPNs based on IP tunnels is that QoS levels may be erratic and are not yet as high as alternative solutions. Also, for VPNs based on the public Internet, higher levels of security such as authentication and data encryption are essential to ensure integrity and security of data. Note that ISP connections used for VPNs do not necessarily need to be protected by a firewall as data is protected through tunneling, encryption, etc. Also, you can use separate ISP connections for general Internet access and VPN access, or you can use a single connection with a common router with a VPN device and firewall in parallel behind it. In some cases, you can use devices that integrate one or more of these functions. VPNs Based on ISDN, Frame Relay or ATM VPNs based on ISDN, Frame Relay or ATM connections are very different from VPNs based on IP tunnels. This type of VPN uses public switched data network services and uses ISDN B channels, PVCs, or SVCs to separate traffic from other users. Single or multiple B channels, PVCs, or SVCs may be used between sites with additional features such as backup and bandwidth on demand. Data packets do not need to be IP, nor do they need to be encrypted. Due to more wide-spread awareness about security issues, however, many users now choose to encrypt their data. The following diagram shows a carrierbased VPN that uses ISDN B channels and Frame Relay PVCs to connect remote clients and devices. VPNs based on public switched data networks are usually provided by service providers and other carriers, and may or may not provide fully managed services. In most cases, additional services such as QoS options are available. This type of VPN is likely to become particularly popular in Europe, where public switched data networks are widely available and business use of the Internet is less developed. The main benefits of VPNs based on ISDN, Frame Relay or ATM connecstions include the following: Connections can be used for any type of communication, from PBX connections and video conferences to private data International connections are relatively easy to obtain, especially for Frame Relay, although they can be expensive Extensive billing and accounting information is available, as these services are well established Security is less of a concern, as data is usually carried over the service provider's or carrier's private network The main disadvantages of this type of VPNs are that ISDN, Frame Relay and ATM services may be expensive and are not as widely available as ISP services. Plus, it is often harder to provide extranet and e-commerce connections to business partners, suppliers and customers. A Note About the Term "VPN" The term VPN is used for many different services, including remote access, data, fax, and voice over IP (VoIP). The other sections in this discussion are concerned with just two types of VPN service: remote access and intranet. However, much of the discussion on intranet QoS requirements is relevant to multimedia, including VoIP. VPN Benefits VPNs offer considerable cost savings over traditional solutions. Find out how much you could save. VPNs cost considerably less than traditional leased line, Frame Relay or other services, because longdistance connections are replaced with local connections to an ISP's point of presence (POP), or local connections to a service provider or carrier network. Reduced Costs VPNs offer the network manager a way to reduce the overall operational cost of wide area networking through reduced telecom costs. In the case of a managed VPN service, the savings can be greater as the ISP or service provider manages the WAN equipment, allowing fewer networking staff to manage the security aspects of the VPN. In many cases, implementing a VPN also means that more use is made of an existing dedicated Internet connection. Flexibility VPNs based on IP tunnels, particularly Internet-based VPNs, also allow greater flexibility when deploying mobile computing, telecommuting and branch office networking. Many corporations are continuing to experience explosive growth in the demand for these services. VPNs provide a lowcost and secure method of linking these sites into the enterprise network. Due to the ubiquitous nature of ISP services, it is possible to link even the most remote users or branch offices into the network. Examples The following examples, based on real-life costs, show how you can make significant savings by implementing VPN-based solutions. The first example shows the cost of a dial up VPN service compared to a traditional remote access solution, while the second example shows the cost of an intranet VPN solution compared to a traditional WAN solution. The final example shows the costs of an international VPN service based on an encrypted 128 Kbps Frame Relay connection compared to a 64 Kbps dedicated leased line. Example 1—Dial VPN Versus Traditional Remote Access There are two areas where savings can be made with a dial VPN solution compared to a traditional remote access solution: Telecom costs. Companies can reduce telecom costs as users start dialing into the network through local calls to ISPs rather than through direct longdistance calls to the company.Typically, a company has a dedicated highspeed connection to the Internet and one or more T1/E1 or ISDN PRI connections to support remote dial-up users. Market research of Fortune 1000 companies by Forrester has found that more than 70 percent of company sites had more than one high-speed connection. This multiple-line approach is common even in small branch offices. A VPN can reduce the number of lines, since dial-up traffic terminates at the ISP POP and is delivered via the high-speed Internet link. In many cases, implementing a VPN means that more use is made of an existing dedicated Internet connection. Staffing and equipment costs. Rather than maintaining a remote access server (RAS), modem banks and ISDN terminal adapter pools for remote access as well as a router for Internet access, a VPN can combine all of the traffic over the connection used by the router for Internet access. Instead of the burden of managing multiple RAS devices, modem banks and ISDN terminal adapter pools, network staff now manage a higher-performance router that offers VPN services. In the case of an outsourced VPN service, the router can also be managed by the ISP or carrier, possibly reducing the cost even further. According to Forrester's research, the cost savings of an Internet-based dial VPN solution compared to a traditional RAS approach are staggering as shown in the following table. However to assess the cost justification completely, we must also consider the potential costs of making the switch to a VPN. A VPN may not make sense if, for example, nearly all of a company's remote users need only make a local call to access the network. This is especially true in the US where local calls are free as there are no monthly usage charges. In most European countries, however, this is not the case and a remote access solution based on ISDN may actually be cheaper than a dial VPN solution. In many European countries, ISDN tariffs are low, and extensive use of time cutting, protocol spoofing and filtering can dramatically reduce ISDN costs. See Cabletron's ISDN and Telesaving white paper for more details. Moving to a dial VPN solution means that each remote user requires an ISP account, and the POPs must be local to the majority of the users. The cost benefits might not be as compelling if users are switched to an ISP account with a flat monthly rate but then must incur long distance call charges to connect to the ISP's nearest POP. Example 2—Intranet VPN Versus Leased Line and Frame Relay There are two areas where savings can be made with an intranet VPN solution compared to a traditional WAN solution: Telecom costs. Companies can reduce telecom costs by using leased line or Frame Relay connections to local ISPs and relying on the Internet for long distance connections. Typically, a company implemen ts a private WAN using many long distance T1/E1 leased line or Frame Relay connectio ns. Studies by Cabletron have found that an intranet VPN can reduce the cost of leased line or Frame Relay connections considerably. Staffing and equipment costs. Rather than maintaining multiple routers at many small branch and SOHO sites, companies can use an outsourced VPN service where the routers are managed by the ISP or carrier to reduce costs even further. Based on a study by Cabletron, the following table shows the average annual savings per site on the cost of intranet VPN access compared to the cost of traditional leased line access for different types of site. Note that the costs shown in the table are for bandwidth only. Based on a cost comparison alone, the reasons for moving to an intranet VPN are compelling. However, a traditional WAN based on leased lines or Frame Relay provides guaranteed levels of Quality of Service (QoS). Replacing a traditional WAN between branch offices and central sites with an intranet VPN is unlikely to give the same levels of performance and QoS to users unless the service provider is able to give throughput and latency guarantees as part of a Service Level Agreement (SLA). See Quality of Service for more information about QoS and SLAs. Example 3—International VPN Versus International Connections The savings are particularly evident in the cost of international connections. A 128 Kbps VPN link between London and Tokyo provided by an international ISP costs around $20,000 per year, while a 64-Kbps leased line provided by a traditional carrier can easily cost around $160,000 per year. Even an international VPN service based on Frame Relay provided by a traditional carrier costs around a third of the cost of the 64 Kbps dedicated leased line. Internet VPNs VPNs based on the Internet are becoming widely available, especially as an alternative for dial-up remote access. Generally when people talk about VPNs, they implicitly mean an Internet-based network as an alternative to a private network based on public network services such as T1 leased lines or Frame Relay. The Internet has become so ubiquitous and Internet service providers (ISPs) so numerous that it is now possible to obtain connections in all but the most remote locations. Most counties worldwide now have ISPs offering connections to the Internet, although some countries still restrict access. So it is possible for many organizations, both large and small, to consider the Internet not just for external communication with customers, business partners and suppliers, but for internal communications as well using a VPN. Internet-based VPNs can be used to outsource remote access with significant cost savings and greater flexibility. Modem racks, remote access servers and the other equipment necessary to service the needs of remote and mobile users can be replaced with a managed service provided by an ISP (see Remote Access VPNs). While Internet VPNs are suitable for remote access needs, there are still problems to overcome before moving to a full intranet VPN solution.Although most VPN products now offer adequate levels of security, the issue of Quality of Service (QoS) and Service Level Agreements (SLAs) remains.While most VPN service providers can offer guarantees for connectivity and uptime, few can offer adequate throughput and latency guarantees. In addition, there are few agreements between ISPs, so unless you can use a single ISP's IP backbone for all your connections, you are likely to suffer service degradation where connections cross boundaries between ISPs. Most users will not want to give up the levels of service currently offered by leased lines, Frame Relay or ATM networks for something inferior. However, in the long term these problems will be overcome, and Internet-based VPNs will become much more widespread for intranet as well as remote access. In a few years, global VPN services based on the Internet will become as cost-effective and as highly available as global Frame Relay and other public network services. Public Network VPNs Public networks such as ISDN, Frame Relay and ATM can carry mixed data types including voice, video and data. They can also be used to provide VPN services by using B channels, Permanent Virtual Circuits (PVCs) or Switched Virtual Circuits (SVCs) to separate traffic from other users. Optionally, authentication and encryption can be used where the identity of users and the integrity of data needs to be guaranteed. Using PVCs, SVCs or B channels makes it easier to provide additional bandwidth or backup when needed. The traffic shaping capabilities of Frame Relay and ATM can be used to provide different levels of QoS, and because these services are based on usage, there is significant opportunity to reduce telecom costs even further by using bandwidth optimization features. Frame Relay in particular has become a popular, widespread and relatively low-cost networking technology that is also suitable for VPNs. Running VPNs over a Frame Relay network allows expensive dedicated leased lines to be replaced and makes use of Frame Relay's acknowledged strengths, including bandwidth on demand, support for variable data rates for bursty traffic, and switched as well as permanent virtual circuits for any-to-any connectivity on a per-call basis. Frame Relay's ability to handle bursty traffic and built-in buffering means that it makes optimum use of available bandwidth, something that is important in a VPN environment where latency and performance are concerns. Frame Relay can be used to create a VPN in two ways: By creating a mesh of Frame Relay connections between sites. These connections are essentially point-to- point links and are similar in concept to dedicated leased lines. Data is kept separate from other Frame Relay users as each connection uses a separate virtual circuit. By using IP tunnels over Frame Relay connections between sites. As above, these connections are essentially point-to-point links similar in concept to dedicated leased lines and each connection uses a separate virtual circuit. However, several separate IP tunnels can be run over each connection, and each tunnel can be encrypted and authenticated to provide additional security. Frame Relay is an end-to-end protocol that can be run over a variety of access technologies, such as ISDN, DSL (Digital Subscriber Loop), and even POTS dial-up lines. New access methods such as switched virtual circuits (SVCs), ISDN access and backup mean that Frame Relay is now a much more reliable and costeffective solution. Frame Relay can also run over, and interoperate with,ATM backbones, making it one of the most widely available public data networking services worldwide. As a result, major service providers and carriers have created global Frame Relay networks which are cost-effective and offer high availability. When coupled with tunneling, encryption and authentication, these attributes make Frame Relay an ideal candidate for global VPN services. Remote Access VPNs Remote access VPNs are rapidly replacing traditional remote access solutions as they are more flexible and cost less. Remote access refers to the ability to connect to a network from a distant location. A remote access client system connects to a network access device, such as a network server or access concentrator. When logged in, the client system becomes a host on the network. Typical remote access clients might be: Laptop computers with modems used by mobile workers PCs with modems or ISDN connections used at home by telecommuters Laptop computers on a shared LAN. For example, some hotel chains are now offering LAN connection points in hotel rooms so that Ethernet cards can be used, with no need for a modem card. We can divide remote access connections into two groups: local dial and long-distance dial. For traditional, private, remote access networks, local-area users connect using a variety of telecommunication data services. Remote access long-distance users rarely have a choice other than modem access over telephone networks. The aggregation devices that the clients connect to typically use channelized leased line and primary-rate ISDN, offering dedicated, circuit switched access. With VPNs, local area users typically have a wider range of data services to choose from, regardless of the support at the enterprise or central site VPN equipment. However, long-distance connections are currently via modem access. What VPN carriers currently offer corporations are "Work Globally, Dial Locally" services. The VPN equipment will use high-speed leased lines to the nearest POP of the chosen VPN carrier and all remote access traffic can be aggregated or routed as IP datagrams over this single link. Advantages of Remote Access VPNs over Traditional Direct-Dial Remote Access Cheaper dial-service costs for long-distance users. When a company partners with a VPN carrier to provide global remote access, the employees are issued information on local telephone number access points in each country for which they have support. Since local calls are significantly cheaper than national and international call, this would appear to offer a sizable saving. This saving does of course depend on the throughput achieved and the relative cost of local, national and international calls. In most regions of the world, local calls are not free, and this may mean that real savings are not achieved. For example, if local calls offer a 50% saving over national calls, but the VPN throughput means that it takes twice as long to copy mail from a central office than it would have using a direct-dial call, no telecommunication savings have been made and company time has been wasted. For local users with telephone lines (or ISDN), a VPN offers no dial-in cost savings and a worse service for the user. Better data rates for modems. Because long-distance VPN users can dial a local modem at the VPN carrier's office, the data rate achieved by the modem should be better than for a long-distance or international direct call. Again, partnering with a VPN carrier to provide a service is important. For example, international VPN throughput can deteriorate badly when using the Internet as a carrier. Scalability. Adding 100 users to a modem pool typically presents more problems to the network manager than adding 100 users to an enterprise Security Gateway that only deals with IP datagrams over a high-speed leased line. Less upgrading needed to the equipment at an enterprise or central site. As modem technology improves, and new local loop services become available, new hard-ware would be required at a "modem pool" site. With VPNs, this problem is handled (and paid for) by the VPN carriers. Improved local access services. With a traditional direct-dial remote access network, the data services that can be used by the remote users are dictated by the data services supported by the aggregation device. With a VPN, the user can choose the best local loop service available, for example, cable modems or xDSL. This advantage is only a reality for home workers currently, but may eventually apply to mobile users. Better utilization of bandwidth at the enterprise or central site. With the traditional approach, each user is typically allocated fixed bandwidth, for example, an ISDN B-channel or a 56Kb channel on a T1 circuit. Most remote working sessions have very low overall utilization of the reserved bandwidth allocated. Also, with a circuit switched approach, there is a fixed number of users who can be supported before new users are completely blocked. With a VPN approach, it is possible to fully utilize the available bandwidth; as the number of connected users increases, the service to each user gradually decreases, but is not completely blocked. Users equipped with high-speed local access services may also take advantage of any spare capacity more easily. Using the link for both company and private business. If the connection from a small office/home office (SOHO) to a central site uses the Internet as a carrier, it is possible to use the link for company and private business. It is also possible to send external mail using the ISP's mail servers and other features (e.g. fax, voice-mail, DNS, direct browsing) without burdening the company-owned servers. This does have the downside of raising billing and security issues. Disadvantages of Remote Access VPNs Most of the disadvantages listed here refer to Internet-based VPNs and solutions will be available on VPN-focused carriers. Possible disadvantages of VPN remote access include the following: Quality of Service. Unlike circuit-switched or leased line data services,VPN links (or tunnels) over public routed networks do not typically offer any endto-end throughput guarantees. In addition, packet loss is variable and can be very high, and packets can be delivered out-of-order and fragmented. Because of these QoS issues, data compression performance over a tunnel can be poor (zero-history compression). Security. VPN connections are made by first connecting to a POP of the public network, and then using that network to reach a remote peer to form a private tunnel. Once the connection has been made to the POP, unsolicited data from other users of the public network can be received, and the exposure to "attacks" requires comprehensive and complex security measures. Accounting and billing. If dial-in costs are being incurred on a link that is not directly connected to the company that will pick up the bill, it becomes a neat trick to monitor the budget (although this seems achievable with VPN carrier-based L2TP). Bandwidth reservation or Quality of Service (QoS) at the enterprise or central site. Bandwidth reservation refers to the ability to "reserve" transmission bandwidth on a network connection for particular classes or types of traffic. It is much harder to achieve with VPNs than traditional networks. Some reservation can be done on out-bound traffic, but for inbound reservation to be achieved, the VPN carrier would need to help. Some inbound flow control is available with L2TP. However, controlling incoming data from power users is a problem that requires some way to flow-control input from each remote client. Two-way calling. Small office/home office sites that use ISDN to access a central site directly enjoy the capabilities of two-way calling, e.g. if the link is idle (the inactivity timer has fired and disconnected the call) and traffic needs to flow from the central site to the remote site, the central site can initiate the call. In a VPN network, this is a capability missing from common ISP offerings today. Call-back is a related topic; offering to pick up the dialin costs incurred by partners and customers is also difficult. Again, L2TP does include support for these features at the moment. Centralized telesaving control. Managing cost-effective use of dial links centrally may no longer be possible. Overhead. VPN tunnels impose overhead for dial-in users: encryption algorithms may impact the performance of the user's system, there will be an increased protocol header overhead, authentication latency will increase, PPP and IP compression will perform poorly (compared to a direct link), and modem compression won't work at all. Support issues. Replacing direct-dial links with VPN tunnels may produce some very painful fault-finding missions. Due to the complexity of VPN carrier networks, the opportunities for "hand-washing" are enormous. Reconnection time. Using tunneling may increase the reconnection time for dial users. With the VPN carrier L2TP model, the client has to go through two authentication phases: one on contacting the VPN carrier POP, and another on contact with the enterprise Security Gateway. Although the authentication exchange with the POP may well be trivial, the VPN database look-up can take time. For ISDN SOHO sites that wish to use cost-saving techniques, special features may be needed to cache these look-ups to allow rapid reconnects. Multimedia. Applications such as video conferencing only work acceptably over low latency links that can offer the required minimum throughput. Currently on the Internet, latency and throughput can vary alarmingly. Multichannel data services, such as ISDN and xDSL solve this problem in the short term, allowing the "data" channel to be used for VPN tunneling, and a separate "voice" channel to be used for business telephone calls or video conferencing. Encryption. When using encryption to protect a tunnel, data compression is no longer achievable as encrypted data is not compressible. This means that hardware compression over a modem connection is not possible. Intranet VPNs Intranet VPNs can be used to provide cost-effective branch office networking and offer significant cost savings over traditional leased-line solutions. Intranet, or site-to-site,VPNs apply to several categories of sites, from small office/home office (SOHO) sites to branch sites to central and enterprise sites. SOHO sites could be considered as remote access users where dial services are used, but as SOHO sites often have more than one PC, they are really small LAN sites. In an intranet VPN, expensive long distance leased lines are replaced with local ISP connection to the Internet, or secure Frame Relay or ATM connections as shown in the following diagram. Local ISP connections can be provisioned using many technologies, from dial-up POTS and ISDN for small sites, to leased lines or Frame Relay for larger sites. New emerging "last mile" technologies such as DSL, cable and wireless provide both low-cost and high-speed access. Many ISPs and service providers are now starting to support these emerging technologies for Internet access, particularly for home users and SOHO sites. The intranet market is one where traditional WAN carriers are likely to compete heavily with ISPs.Traditional WAN carriers can offer a VPN service similar to a Frame Relay service with Quality of Service (QoS) based on Committed Information Rate. Traditional WAN carriers are well placed to push their advantage in providing secure, reliable, low-latency, intranet links by adopting their current services to support routed VPN links. Advantages of Intranet VPN Solutions Cheaper line rental. Typically,VPN carriers provide a leased-line feed by contracting with a traditional carrier company. Since leased lines often have a distance-related cost structure, connecting to a local POP will provide savings compared to a direct long-distance or international link. Scalability. Unlike leased lines and Frame Relay PVCs, there is no additional cost for new peer-to-peer links. However, in order to offer Frame Relaystyle Quality of Service,VPN carriers may well need to introduce a pervirtual- link factor to cover costs. Cheaper backup. If a company sticks with traditional-carrier, end-to-end data services for primary intranet links (which is advisable), the VPN carrier service may offer cheap "get what you can, when you can" bandwidth, backup or low-priority data routing. To do this effectively, the tunnels need the support of dynamic tunnel monitoring. For example, how does a CPE router know the effective throughput of a tunnel without an end-to-end reliable data link or intimate knowledge of the higher-layer protocol sessions carried over the link? Without a solution to this problem, path sharing between a VPN tunnel and a private leased line may give worse throughput than using just the private leased line. If the VPN tunnel is used in partnership with a private data service which had a use-based tariff, for example Frame Relay, then this solution could offer considerable savings. Cheaper high bandwidth over last mile. Renting high-bandwidth leased lines—for example,T1/E1 or T3/E3—is expensive, and cheaper options exist for last-mile connections in some areas such as cable, xDSL, wireless and satellite. Cheap global virtual backbone. For companies that do not already have a national/international backbone, there is no cheaper option than setting up a virtual backbone using VPN carrier services. Disadvantages of Intranet VPN Solutions Possible disadvantages of intranet VPN include the following: Denial-of-service attacks. Unlike a private leased line, traffic that is not from the peer remote site (tunnel end-point) can flood down the receive path of a VPN tunnel from anywhere on the public network. This unsolicited traffic may reach such a level that solicited data can no longer be retrieved. To combat this, the VPN carrier could offer to filter non-VPN traffic, or perhaps provide a band-width reservation or QoS service. No end-to-end data link in some cases. For some tunnel technologies, there is no end-to-end data link, so detection of reachability will need to be supported at the routing layer with protocols capable of rapid failure detection and instant re-route. Packet loss. A VPN tunnel can sometimes suffer high packet loss and can reorder packets. Reordering can cause problems for some bridged protocols, and high packet loss may have an impact on the optimal configuration of higher-layer protocols. Latency and multimedia.This is very much a next-generation VPN carrier goal that will require considerable investment to do properly.There are serious doubts as to the chances of the Internet achieving success in this area in the near future. Data-link carrier companies and newly-formed VPNfocus companies offering VPN services have a better chance. Increased downtime. Decreased mean time between failures, longer lasting outages, painful problem solving and downtime compensation claims. Aggregation of functions. Doing business with partners is clearly easier to achieve using the VPN model, but aggregating private tunnels, customer tunnels and web publishing access in a single system is difficult without combined VPN and firewall capability. Separating VPN and non-VPN traffic is a sensible precaution. VPN Issues There are a number of issues, both technological and practical, that need to be overcome before you can implement a VPN. Here are some of these issues. For a VPN to function successfully, it must provide a number of essential features—in particular, features that solve the problems that stem from routing private data across a shared public network. The main features are discussed here. Security Since a VPN is a shared-access, routed network, security is the main area of concern. It will require the use of encryption, secure key exchange/re-keying, session and per-packet authentication, security negotiation, private address space confidentiality, complex filtering, and a host of other precautions. Performance and Quality of Service (QoS) IP datagrams sent across the VPN carrier service may experience packet loss (silent discards) and packet reordering. Packet loss tends to be greatly increased by stateful algorithms designed for pointto-point reliable links, for example, PPP compression and encryption algorithms. Throughput may also vary from POP to POP, country to country, and even hour to hour. Reordering will cause problems for some LAN protocols, for example, when running bridging over a VPN. Monitoring Actual Throughput In the absence of Quality of Service guarantees from the VPN carriers, mechanisms are required to allow performance monitoring of tunnels. Preventing Denial of Service Attacks Being connected to a public network, the VPN receive-data path can be clogged by unsolicited data to such an extent that no useful business can be achieved. Unlike a private leased line, traffic that is not from the peer remote site (tunnel end-point) can flood down the receive path of a VPN tunnel from anywhere on the public network. For client-based tunnels, there are no services currently. In the case where the VPN carrier is providing the tunnel, the VPN carrier could offer to filter non-VPN traffic, or perhaps provide a bandwidth reservation service. For the L2TP VPN carrier-based approach, the client is protected by the fact that it is not reachable via the public network, as no global address is assigned Scalability The term scalability refers to how well a system can adapt to increased demands. A scalable network system is one that can start with just a few nodes but can easily expand to thousands of nodes. Scalability can be a very important feature because it means that you can invest in a system with confidence that you won't outgrow it. If VPN carriers are to succeed in VPN deployment, the technologies they use need to scale easily. The VPN customer will also require this at larger Security Gateway sites. Enterprises will need to consider: The overhead associated with security mechanisms. The overhead associated with encryption and compression, which both require a lot of processing power. Hardware compression and encryption may be needed cope with this load. Key management, including methods of key generation, distribution and exchange. Management Client-based software should be as transparent as possible. VPN carriers will require new management tools in order to simplify the configuration and monitoring of a corporate customer's VPN. Also,VPN customers may well want a privileged management window into their VPN carrier-held database to make changes for themselves! Flexibility To offer a "go anywhere"VPN service,VPN carriers are keen to provide a service that can support all protocols and all data links (e.g. PPP over anything). Telesaving Telesaving means making cost-effective use of WAN data services. Telesaving is appropriate to all WAN links, but is particularly useful for "pay-as-you-use" data services, for example, ISDN. For clients using this type of service to access the VPN carrier network—and from there, a tunnel server—telesaving needs to be performed from a central site (an Enterprise Security Gateway) for data links that are connected indirectly via the VPN carrier network. New, VPN-specific, telesaving features will be needed to take advantage of the possibility of cheap bandwidth via a VPN link, while maintaining some layer of service using more expensive, private data links when needed. Bandwidth Reservation and Quality of Service (QoS) Bandwidth reservation and Quality of Service (QoS) refers to the ability to "reserve" transmission bandwidth on a network connection for particular classes of traffic or particular users. It allocates percentages of total connection bandwidth for specified traffic classes or users, which have given priority levels assigned to them. A bandwidth reservation algorithm is used to decide which packets to drop when there is too much network traffic for the available bandwidth. Given a fixed capacity VPN WAN link (say a T1), it is desirable to reserve bandwidth outbound (and inbound if possible) on a per user (remote access) or per remote LAN basis.There are, however, some questions about how bandwidth reservation can be accomplished over tunnels. For outbound reservation, the Security Gateway could implement transmit priority queues, but inbound reservation requires the assistance of the VPN carrier. Some possibilities for inbound reservation are: The ISP POP access device could apply tunnel/non-tunnel bandwidth reservation and filtering techniques to the client's requirements. The VPN carrier could offer an SVC-style service where each VPN link has some predetermined capacity. L2TP network servers or access concentrators have the option of inbound, dynamic, flow control to help inbound bandwidth reservation. Remote VPN clients can be flow-controlled using L2TP sequence numbers/window size in order to reserve appropriate bandwidth for individual VPN clients and nonVPN traffic. To be effective, the VPN carrier POP would need to support at least a broad VPN/non-VPN queuing priority inbound to the L2TP network server. It would be useful if bandwidth reservation could be managed dynamically. High-Performance Routing Issues With encryption being used from intranet or host-to-host, the nature of IP-switching filters changes. For IP-switching (L3 switching) to function on encrypted data flows, it may need to understand the IPSec and L2TP standards. For example, the definition of a flow may need to make use of the IPSec protocol headers to identify a communication stream. As an example, it may be possible to trigger on the SPI field of the ESP header used in IPSec as a means of identifying a stream. For L3 switches that terminate secure tunnels, no fast forwarding is possible since the encrypted IP packet needs to be reconstituted before being forwarded. There is also the extra load of decrypting/encrypting for these secure tunnels. In time,encryption (and compression) will be present in all hosts and there will be less need for routers to terminate secure tunnels-allowing switching based on tunnel header information and requiring no encryption/decryption horsepower. Work to redefine the TOS field of IP packets as part of DiffServ may deliver the means to reinstate traffic prioritization in L3 switches for secure data flows. Quality of Service What Quality of Service can you expect from your VPN service provider and how can you measure what you are getting? Most data services, such as Frame Relay, provide guarantees for uptime and availability, as well as throughput and response time. These guarantees, or Quality of Service (QoS) metrics, are defined in the Service Level Agreement (SLA) with your service provider. While most managed VPN services provide a certain level of guaranteed uptime and availability, many do not provide comparable performance and latency guarantees, nor do they offer throughput guarantees. There are several different schemes used to provide Quality of Service, some of which have been developed specifically with a particular technology or protocol in mind, such as Ethernet or ATM. Other schemes are specific to the IP protocol and are being developed by the IETF. Examples of different QoS schemes are: ATM and Frame Relay traffic shaping schemes. These bandwidth reservation mechanisms are built into the ATM and Frame Relay standards. Examples are ATM ABR and CBR, and Frame Relay CIR. IEEE 802.1p and 802.1q. IEEE specifications that allow Level 2 switches to provide traffic prioritization over Ethernet and Token Ring LANs. Differentiated Services (DiffServ). An IETF standard that defines ways of assigning specific service levels and priorities to IP traffic using the IP TOS field. Multiprotocol Label Switching (MPLS). A method of encapsulating and tagging IP traffic to improve efficiency and control of routed networks. Resource Reservation Protocol (RSVP). An IETF standard that defines how routers and other network devices should reserve bandwidth across the network on a hop-by-hop basis. If you are considering a managed VPN service, you need to pay particular attention to the QoS metrics specified in the SLA from your service provider. If the service provider is unable to provide adequate SLA guarantees, you may need to reconsider how you deploy VPNs in your environment. Some applications, such as dial-up remote access, are very suited to the VPN approach as users are unaccustomed to guaranteed uptime and availability and are less demanding of the service. However, replacing dedicated leased line or Frame Relay connections between branch offices and central sites with an intranet VPN is unlikely to give the same levels of performance and QoS to users unless the service provider is able to give throughput and latency guarantees. SLA Checklist Here are some things to ask your service provider about SLAs: What QoS scheme is used in the network and what does it cover? What is the level of guarantee of network availability? A typical guarantee is 99.8 percent network availability. What backup options are offered and at what cost? Check to see whether the service provider offers backup connections such as ISDN or Frame Relay SVCs should the main connection fail. Do customers get a credit when there is an outage and if so, what is the level of credit? Many service providers give service credits based on the duration of outages. Is service availability covered in addition to network availability? Simply having a connection to the network is not enough; the VPN service that runs over the network must also be available. Does the SLA cover temporary disconnection, for example when faced with hacker attacks on a firewall? Elective downtime should be part of the service to protect the integrity of your network. SLAs In the Future Over the long term, SLAs for VPN services are likely to improve as the various different QoS schemes are deployed more widely. However, until this time, SLAs may be limited to connections over a single service provider's network. To ensure end-to-end SLAs in the interim time, traffic should stay on the same network. If the connection goes across networks, a service provider has little control over the quality of the other provider's network. This situation is likely to remain until service providers reach agreement on SLA interworking. VPN Futures VPNs are only just starting to be deployed. Once VPNs are in wide use, they provide the opportunity to integrate other types of communication such as multimedia and Voice over IP (VoIP). The primary concern for VPNs will always be security. However, once VPN products are widely available, the focus will fall more and more on delivering quality of service (QoS) and class of service (CoS) over IP networks as part of a VPN. As voice and data services merge into one (voice over IP, IP fax), new network services are being developed to offer the QoS/CoS required for data, telephony and fax. (For more information about QoS see Quality of Service and SLAs.) As products develop to take advantage of this opportunity, all communication devices will become IP addressable, providing voice, fax, video and data to the desktop.All of these services can make use of VPN security protocols. Name servers could become very useful for configuring and reconfiguring VPNs. If the routers in a complex intranet VPN network were to make use of name servers to locate peer routers, then these networks could be reconfigured simply by changing the name-to-address mapping. Work is in progress to extend the use of DNS servers to provide a secure (IP Security-based) mechanism for routers to find peer routers and clients to find servers. Next Generation VPN Carriers New VPN carriers are emerging to take advantage of the new markets, and traditional telecommunications providers see that the aggregation possible with routed networks makes good sense for remote access data, as it reduces the strain on long-haul dial services as well. New 'last-mile' technologies like Digital Subscriber Loop (DSL) deliver a means for the phone companies to provide high bandwidth IP access over existing cabling (twisted-pair copper). Cable companies also offer the potential to deliver high bandwidth IP access over existing and new cable infrastructure. As the phone and cable companies become familiar with delivering IP services, these new last-mile technologies put them in a good position to acquire a significant share of the Internet access and VPN markets. New providers are focussing on providing VPN services. A popular technique is to build an ATM or Frame Relay backbone and then offer VPN links with guarantees on throughput and latency to enable customers to outsource remote access, site-to-site and even interoffice fax and voice.These networks are well placed to offer everything from voice to site-to-site by making use of the quality of service options inherent in ATM and Frame Relay networks. To offer global services to a VPN customer with global data needs, consortiums of VPN carriers are forming to offer a uniform service internationally. Many of these services are based on ATM and Frame Relay, although new IP based services are becoming available. VPNs and Voice/Data Convergence Companies today use different communications infrastructure to provide their voice, data and Internet connectivity needs. On the voice side, components include a PABX, key system or Centrex service with features such as voice mail and automated attendant. Computer Telephony Integration (CTI) applications may also be used to link voice capabilities with data applications. On the data side, LAN infrastructure is typically provided by a stackable or chassis based hub with multiple 10/100 Ethernet segments. WAN connectivity is typically provided by a router using leased lines or Frame Relay, with Internet connections for e-mail and web browsing provided via a separate firewall connection. Companies that use a variety of data and voice services to meet their communication needs will find new alternatives becoming available that offer direct and indirect cost savings. New customerpremises routers are now appearing that act as both Security Gateways and Multimedia Gateways. These Multiservice Routers integrate a number of LAN and WAN capabilities such as hub and routing functions, and also support new applications such as Voice Over IP (VoIP), IP-fax, Internet access (browsing, publishing, e-mail, e-commerce) as well as VPN traffic over a single local-loop link to a service provider POP. An initial investment in web access and web publishing may well be the starting point for a company that wishes to take advantage of VPN services. For the move from web publishing and e-mail to full e-commerce, companies may follow these steps: Web publishi ng. Compani es are already becoming familiar with accessing and publishin g information and exchanging e-mail over a public routed network. Private remote access via VPN carrier networks: out-sourced remote access. Providing a more scalable remote access solution with cheaper access to corporate networks. The existing "modem pool" may be preserved for backup. Partnership access with customers, partners and suppliers (extranets). Rather than arrange for one-off solutions each time a new partner needs to be linked to the corporate network,VPN networks provide a common technology to reduce the complexity and expense of adding new partner network links. An intranet VPN based on carrier networks with outsourced backbone links. Once VPN networks can offer QoS guarantees, corporate backbone links could be outsourced to managed routed networks. These would have builtin failure recovery, and should have a lower cost per month than traditional dedicated leased bandwidth. Full electronic commerce, that is, doing business over public networks. For example, electronic-fax, voice-over-IP and electronic ordering.With the growth in the reach and capacity of the Internet and the IP protocol suit, there is the promise of providing all common communications services over the same communications link-an IP datagram service.