Wireless LAN protocols - Why wireless LAN? Convenience and
advertisement

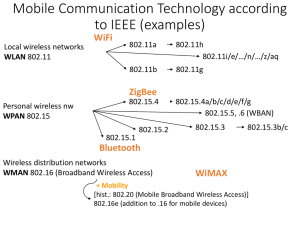
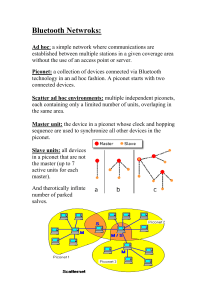
Wireless LAN protocols - Why wireless LAN? o Convenience and flexibility. No need to carry wires or retrofit buildings, (limited) mobility, no connectors (e.g. Macbook Air). - Why not wireless LAN? o Not good if very high bandwidth is required o RF compatibility and other safety issues o Security (?) IEEE 802.15.1 (Bluetooth) - First let’s consider Bluetooth, a very simple wireless LAN protocol – named for King Harald Bluetooth, a 10th century Danish king - Bluetooth connects small devices over a very short range (~1-10m), depending on “class” – though longer ranges are possible – “personal area network” for connecting devices in your immediate vicinity Bluetooth architecture - Hierarchical “master-slave” system - A collection of connected Bluetooth devices is a “piconet” - Piconets consist of four kinds of device: o Master (one per piconet) o Slaves (up to seven per piconet, directly connected to the master, actively transmitting data) o Parked (known to the master but not transmitting data) o Standby (idle) (Fig. 1) - Any device can act as either master or slave; also, piconets can overlap (so it’s maybe not appropriate to think of the master as a “base station”) - Active devices (master + slaves) are assigned a 3-bit active member address (AMA) (this is why there can be at most 7 slaves) - Parked devices are assigned an 8-bit parked member address (can be upgraded to active members as needed or as a slot becomes available) - It is possible for slaves to belong to more than one piconet; it is also possible for a master to be a slave in another piconet – however not simultaneously – the devices jump back and forth (Fig. 2) - it is not possible for a device to be a master in two piconets (in that case the piconets would merge into one) Bluetooth Radio Interface - Bluetooth operates in the 2.4GHz ISM band - Multiple access via frequency hopping spread spectrum (FHSS) o 79 “hop carriers” each with 1 MHz of bandwidth o 1600 hops/s (625 s per “slot”) o so every 625 s, the system occupies a different, pseudo-randomly selected 1 MHz frequency range (Fig. 3) - Why do this? o Devices in the ISM band must tolerate interference from other devices in the same band o By randomly jumping from frequency to frequency, it is unlikely (but not impossible!) that interference will be encountered - When a piconet is formed, the master sets the hopping pattern - All devices have a unique 48-bit device ID, which establishes the hopping pattern (when master) - Time-division duplexing: transmissions proceed as master, slave 1, master, slave 2, master, etc. - It is possible for transmissions to occupy 3 or 5 slots, as needed – in this case no hopping is performed during the block, and intermediate hops are skipped (Fig. 4) - data payload is up to 343 bits for single-slot packets - What is the data rate? – given 1 slave, 2 slaves ... – for the master IEEE 802.11 (WiFi) - The world’s most widely used wireless LAN standard o 802.11 (1997): 1-2 Mbps o 802.11a (1999): 27-54 Mbps (however, limited range – only 802.11 outside of 2.4 GHz) o 802.11b (1999): 11 Mbps o 802.11g (2003): 22-54 Mbps o 802.11n (2010?): 108-600 Mbps - Compare with Ethernet – note – Cat 5 wire is most commonly used with 100 Mbps and is temperamental at higher data rates (e.g., 1 Gbps Ethernet) – with 802.11n, all you need to do is upgrade the terminals