Bluetooth Report
advertisement

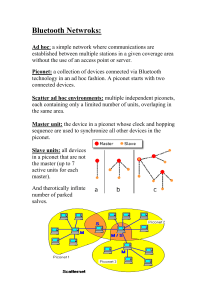
BLUETOOTH AND ITS APPLICATION IN MOBILE PHONES INTRODUCTION Bluetooth is a short range wireless technology intended to replace the cables connecting portable and/or fixed devices while maintaining high levels of security. Ericsson Mobile Communication started this technology in 1994. This technology operates in the unlicensed industrial, scientific and medical (ISM) band at 2.4 to 2.485 GHz using a spread spectrum, frequency hopping full duplex signal at a nominal rate of 1600 hops/sec. Bluetooth enabled electronic devices connect and communicate wirelessly through short-range adhoc networks known as piconets. The main draws of this technology are its low cost, low power and robustness. Compared to other systems operating in the same frequency band, Bluetooth radio typically hops faster and uses shorter packets, which helps it to minimize unauthorized interruption or jamming of telecommunication.. It also uses forward error correction (FEC) which limits the impact of random noise on long-distance links. The ability to simultaneously handle both data and voice transmissions is the fundamental strength of this technology, which gives a variety of innovative solutions such as hands-free headset for voice calls, printing and fax capabilities and synchronizing PDA (Personal Digital Assistance), laptop and mobile phone applications. VARIOUS TECHNICAL ASPECTS OF THIS TECHNOLOGY ARE GIVEN BELOW OPERATING RANGE Class 3 Radios 1 meter or 3 feet Class 2 Radios (For Mobile phones) 10 meters or 30 feet Class 1 Radios (For Industrial Use) 100 meters or 300 feet. CORE SYSTEM RF transceiver, baseband and protocol stack. 3 Core protocols The logical link control and adaptation protocol (L2CAP) : Provides data services to the high layer protocols with protocol multiplexing capability,segmantation and reassembly operations and group abstractions. 1 Service discovery protocols (SDP) : Provides device information, services and the characteristics of the services. RFCOMM protocol : Provides transport capabilities for high level services that use serial line as the transport mechanism. BLUETOOTH CHANNELS 79 RF-Channels, on individual frequencies of 1 MHz apart. Communication channels, consisting of a psuedo-random hopping sequence through these 79 RF channels. 5 logic channels, used for control purposes. PHYSICAL LINKS SCO (Synchronous Connection – Oriented) –This link is point –to-point between master and slave. Master maintains the link by using reserved time slots at regular intervals. Packet retransmission is not allowed in this. ACL (Asynchronous Connection-Less) - This provides packet-switched connections between the master and all active slaves. Packet retransmissions are usually applied to assure data integrity. TRANSMISSION POWER LEVELS A lower power level that covers the shorter personal area within a room A higher power level that can cover a medium range, such as within a home. OTHER RELEVANT INFORMATION The baseband protocol is a combination of circuit and packet switching. Time slots can be reserved for synchronous packets. A frequency hop is done for each packet that is transmitted. A packet nominally covers a single time slot, but can be extended to cover up to five slots. Bluetooth can support An asynchronous data channel Up to 3 simultaneous synchronous voice channels A channel, which simultaneously supports asynchronous data and synchronous Or voice. 2 HOW NETWORKS ARE FORMED AND CONTROLLED? The technology uses frequency hopping in time slots. All communication is done through the master unit. There is no direct communication between the slave units. If the slave units want to talk directly, they will form a new piconet, with one of them acting as Master. They will be parked in the old net, unless they decide to quit the old net altogether. To establish a connection two procedures are used Inquiry – This enables a unit to discover which units are in range and what their device addresses and clocks are. Paging- An actual connection can be established. Ideally, only bluetooth device address is required to set up a connection. Knowledge about the clock will accelerate the setup procedures. A unit that establishes a connection will carry out a page procedure and will automatically become the master of the connection. After the paging procedure, the master must poll the slave by sending POLL or NULL packets to which the slaves will respond. LMP (Link Manager Protocol) procedures that do not require any interaction between the Link Manager (LM) and the host at the paged unit’s side can then be carried out. When the paging device wishes to create a connection involving layers above LM, it sends LMP_host_ connection_req. When the other side receives this message, the host is informed about the incoming connection. The remote device can accept or reject the connection request by sending LMP_accepted or LMP_not_accepted. When a device does not require any further link set_up procedures, it will send LMP_setup_complete. The device will still respond to requests from the other device. When the other device is also ready with link_set_up, it 3 will send LMP_setup_complete. After this, the first packet on a logical channel different from LMP can be transmitted. Various states of bluetooth units Standby mode: Initially all devices are in this mode. An unconnected unit periodically ‘listens’ for messages every 1.28 seconds. A connection is made by a page message, if the address is already known or by an inquiry message followed by a subsequent page message if address is unknown. Hold mode: In this mode only an internal timer is running. Data transfer restarts instantly when units transition out of hold mode. It is used when connecting several piconets or managing a low power device such as a temperature sensor. Sniff mode: A slave device listens to the piconet at reduced rate, thus reducing its duty cycle. Park mode: A device is still synchronized to the piconet but does not participate in the traffic. BLUETOOTH’S SECURITY Bluetooth has built in sufficient encryption and authentication and is thus very secure in any environment. In addition to this, a frequency-hopping scheme with 1600 hops/sec. is employed. This is far quicker than any other competing system. This, together with an automatic output power adaption to reduce the range exactly to requirement, makes the system extremely difficult to eavesdrop. ERROR CORRECTION SCHEME Bluetooth units often have to contend with electro-magnetically noisy environments. Thus, the need for some kind of error-detection and -correction.3 error-correction schemes defined for Bluetooth are : 1. 1/3 rate FEC (Forward Error Correction) 2. 2/3 rate FEC 3. ARQ unnumbered scheme (Automatic Repeat Request). The purpose of the FEC scheme on the data payload is to reduce the number of retransmissions 4 The ARQ-scheme is shown in the figure below. On two occasions, the transmitted data blocks get corrupted, which is detected by the recipient. So the next time that recipient get a chance to communicate with that sender (i.e. at the next appropriate timeslot), the recipient sends a Negative Acknowledgement (a NAK, depicted in red), which prompts the other party to re-transmit that data block. APPLICATION OF BLUETOOTH IS MOBILE PHONES A Serendipity server and Bluetooth activated mobile phone interact using the Connected Limited Device Configuration (CLDC) combined with the Mobile Information Device Profile (MIDP).The CLDC and MIDP together make up the Java Runtime Environment (JRE) for modern resources-constrained mobile information devices such as phones and entry level PDAs.In mobile devices , the JRE must be embedded in ROM at manufacturing time. EXAMPLE: The Serendipity server is located within the room where the meeting takes place. This server acts as the master server within the Bluetooth piconet. The Serendipity server has a predefined mobile phone profile stored in it. The predefined profile contains values for settings such as ring tones, caller tunes, message tones, message alerts, silent mode, vibrating mode, ringing mode, time/date settings, alarm settings, ringing volume, and so on. For example, before entering a meeting room, the user might want to change his mobile settings to silent and vibrating mode, change the time and date to the GMT time zone, turn the alarm off, and establish 5 that no message tones should be issued. The preconfigured mobile phone profile in the Serendipity server contains all of this information. At the start of a gathering, the Serendipity server is ready to register slave devices. Whenever a meeting attendee enters the room with a Bluetooth-enabled mobile phone, service discovery occurs and the device joins the piconet. After the piconet has been formed, the Serendipity server inquires for device profile settings from each of the slave devices. The server checks to see if each device profile matches with the predefined profile it has stored. If this doesn't match, a profile change request is sent to that particular user. The user has the option to either accept this profile change request or deny it. When the user accepts the request, the server increases a weighted count against the predefined profile. If the user denies this profile update request, the weighted count against the user's device profile is increased. The Serendipity server determines the most widely used device profile setting based on these weighted counts. At regular intervals, the Serendipity server transmits the most widely used device profile setting to those devices that have a profile setting different than the one most widely used. The Serendipity server can sense the user's inclination to go with the profile settings as directed by it, after looking at the history of rejection/acceptance of the previous profile update requests. If the user has rejected any of the previous profile update requests, it can exclude those users from the updates. This comes in handy: users can say that they do not want to be bothered with profile change requests any more. 6 7 TERMINOLOGY Piconet: These networks allow one master device to interconnect with up to 7 active slave devices[because a 3 bit MAC(Media Access Control) address is used] Up to 255 slave devices can be inactive or parked, which the master device can bring into active status at any time.Piconets are established dynamically and automatically as bluetooth enabled devices enter and leave radio proximity. Master unit: The device in a piconet whose clock and hopping sequence are used to synchronize all other devices in the piconet. The master also numbers the communication channels Slave units: All devices in a piconet that are not the master (up to 7 active units for each master). Mac address: A 3-bit Media Access Control address used to distinguish between units participating in the piconet Parked units: Devices in a piconet which are regularly synchronized but do not have MAC addresses. The Master with a “beacon signal” wakes them up. Sniff mode and hold mode: Devices that are synchronized to a piconet, and which have temporarily entered power-saving modes in which device activity is lowered. They keep their MAC-addresses. Serendipity: Tool that lets two different devices within the range of bluetooth server communicate with each other. CLDC: Defines the base set of application programming interfaces and a virtual machine for the resource-constrained devices like mobile phones, pagers and mainstream personal digital assistants. MIDP: Provides core application functions required by mobile applications -- including user interface, network connectivity, local data storage, and application life cycle management -- packaged as a standardized JRE and a set of Java technology APIs 8 REFERENCES: http://www.swedetrack.com/images/bluet00.htm http://www-128.ibm.com/developerworks/library/wi-bluetooth/ 9