Chap 15
advertisement

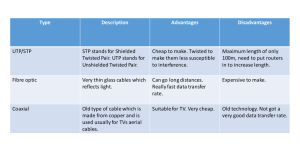
Chapter 15 Wireless LANs Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. Chapter6: Outline 15.1 INTRODUCTION 15.2 IEEE 802.11 PROJECT 15.3 BLUETOOTH 15-1 INTRODUCTION Wireless communication is one of the fastestgrowing technologies. The demand for connecting devices without the use of cables is increasing everywhere. 15.3 Figure 15.1: Isolated LANs: wired versus wireless 15.4 Figure 15.2: Connection of a wired LAN and a wireless LAN to other networks 15.5 15.15.3 Access Control An important issue concerning a wireless LAN is access control— Answering the question of how the wireless host can get access to the shared medium. The shared medium is free space for a wireless LAN. 15.6 15.15.3 Access Control The CSMA/CD algorithm does not work in wireless LANs for many reasons including these: 1.Wireless signal amplitude degrades proportional to the inverse square of the distance. This makes relative amplitudes somewhat meaningless with wireless communication. 1.The hidden station problem prevents collision detection. 15.7 Figure 15.3: Hidden station problem 15.8 15-2 IEEE 802.11 PROJECT IEEE has defined the specifications for a wireless LAN, called IEEE 802.11, which covers the physical and data-link layers. It is sometimes called wireless Ethernet. 15.9 15.2.1 Architecture The standard defines two kinds of services: BSS, the basic service set, and • ESS, the extended service set (ESS). • 15.10 Figure 15.4: Basic service sets (BSSs) 15.11 Figure 15.6: Extended service set (ESS) 15.12 15.2.2 MAC Sublayer Like wired Ethernet, IEEE 802.11 defines two sublayers within the data-link layer: LLC (logical link control) handles framing, error control, flow control. MAC (media access control) physical addressing 15.13 15.2.2 MAC Sublayer IEEE 802.11 defines two sublayers withing the MAC sublayer: DCF the distributed coordination function, and PCF and point coordination function. 15.14 15.2.2 MAC Sublayer DCF the distributed coordination function, and •Uses CSMA/CA as the access method •Implements a persistence strategy with expbackoff •Implements a DIFS after the media is idle. 15.15 15.2.2 MAC Sublayer DCF the distributed coordination function, and PCF and point coordination function. 15.16 Figure 15.6: MAC layers in IEEE 802.11 standard 15.17 DIFS & SIFS DIFS SIFS <= 50 microseconds <= 10 microseconds Figure 15.7: Distributed Coordination Funcion: DCF NAV 15.19 PCF Point Coordination Function, optional layer to allow for transmissions needing higher priority (quality of service) Figure 15.8: Example of repetition interval 15.21 Figure 15.9: The frame format has 9 fields 15.22 Frame Format FC = Frame control D = duration SC = sequence control used for “fragmentation” Frame body up to 2312 bytes. FCS = CRC error detection Table 15.1: Subfields in FC field 15.24 Figure 15.10: Control frames 15.25 Table 15.2: Values of subfields in control frames 15.26 15.2.3 Addressing Mechanism The IEEE 802.11 addressing mechanism specifies four cases, defined by the value of the two flags in the FC field. Each flag can be either 0 or 1, resulting in four different situations. 15.27 Table 15.3: Addresses 15.28 Figure 15.11: Addressing mechanisms 15.29 Figure 15.12: Exposed station problem 15.30 802.11-Physical Layer The unlicensed frequency bands in these three ranges 902–928 MHz, 2.400–4.835 GHz, and 5.725–5.850 GHz. Are known as the ISM bands, Industrial, Scientific and Medical. 15.31 Table 15.4: Specifications (DSSS = Direct Sequence...) 15.32 OFDM Orthogonal Frequency Division Multiplexing OFDM uses QAM for modulation. 15-3 BLUETOOTH Bluetooth is yet another wireless LAN technology requiring short distances between stations. 15.34 15-3 BLUETOOTH A Bluetooth LAN is an ad hoc network. The devices, (aka gadgets), find each other and make a network called a piconet. 15.35 15.3.1 Architecture Bluetooth defines two types of networks: piconet and ● scatternet. ● 15.36 Bluetooth Piconet Up to 8* stations One station is designated the primary The other stations are secondary Bluetooth Piconet The secondary stations synchronize their clocks with the primary station. The secondary stations receive their hopping sequence from the primary station. Bluetooth Piconet Communication is one-to-one or One-to-many. Bluetooth Piconet While limited to seven “active” secondary stations. It is possible to put a station in a “parked state” to allow another station on the piconet. Figure 6.17: Piconet 15.41 Figure 15.18: Scatternet 15.42 Bluetooth V1 1 Mbps bandwidth 2.4-2.483GHz (overlaps with 802.11b & g) FHSS – 1600 hops per second 79 frequency channels of 1MHz each FSK modulation Bluetooth V2 3 Mbps bandwidth Bluetooth V3 24 Mbps bandwidth Bluetooth establishes the link and uses 802.11 to achieve the 24Mbps data rate. Bluetooth Range Power Class 1 Power Class 2 Power Class 3 20db 4 db ~100 m ~10 m ~1 m 15.3.2 Bluetooth Layers Bluetooth uses several layers that do not exactly match those of the Internet model defined in the text book. Figure 15.19 shows these layers. 15.47 Figure 15.19: Bluetooth layers 15.48 Bluetooth Access Method Polling-select The primary poles the secondary stations on even clock cycles. If a secondary is polled, it transmits on the next odd clock cycle. Figure 6.21: Single-secondary communication (diagram error!) microseconds, not milliseconds 15.50 Figure 6.22: Multiple-secondary communication 15.51 Figure 6.23: Frame format types 15.52 Bluetooth V1 Throughput 1-slot frames, 192-Kbps 3-slot frames, 596-Kbps 5-slot frames, 730.484 Kbps