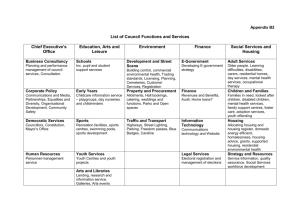
4. Technical Standards
advertisement

e-Government Program (Yesser) YEsser Framework Interoperability (YEFI) YEFI Technical Standards Version 1.1 Date: 27/05/2007 e-Government Program (Yesser) Version 1.1 - Page 2 / 63 Document Description Document Title Document version Document Status YEFI Technical Standards 1.1 Final Versioning Version 0.1 1.0 1.1 Date 01-Apr-07 27-May-07 24-Nov-07 Description of changes made First Draft created Final Update with government agencies’ comments Document Validation Version Author Review by Version Error! Unknown document property name. Date Status Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 3 / 63 Table of Contents 1. Introduction ....................................................................................................................... 7 1.1. Definitions .................................................................................................................... 7 1.1.1. 1.1.2. 1.1.3. 1.2. E-Government in Saudi Arabia ..................................................................................... 7 1.2.1. 1.2.2. 1.2.3. 1.3. 1.4. 1.5. 1.6. The e-Government Concept ................................................................................................................ 7 Yesser ................................................................................................................................................. 7 Yesser Interoperability Framework (YEFI) .......................................................................................... 7 The Program Philosophy ..................................................................................................................... 7 Yesser and ICT in Government ........................................................................................................... 8 Rationale for YEFI ............................................................................................................................... 9 Document Purpose ...................................................................................................... 9 Scope ......................................................................................................................... 10 Target Audience ......................................................................................................... 10 Guiding Principles ...................................................................................................... 10 1.6.1. 1.6.2. 1.6.3. 1.6.4. 1.6.5. 1.6.6. 1.6.7. 1.6.8. 1.6.9. Resolution no. 40, March 2006.......................................................................................................... 10 YEFI is a Living Framework............................................................................................................... 10 Yesser Interoperability Committee .................................................................................................... 10 Use of Open Standards ..................................................................................................................... 11 Publication ......................................................................................................................................... 11 Do not reinvent the wheel .................................................................................................................. 11 Government should not be adversely affected .................................................................................. 11 Reference to Other International Interoperability Frameworks .......................................................... 11 Change Control ................................................................................................................................. 11 1.7. Document Structure ................................................................................................... 12 1.8. Document Assumptions ............................................................................................. 12 1.9. Glossary ..................................................................................................................... 13 2. Summary – Standards Snapshot ................................................................................... 14 2.1. Classification .............................................................................................................. 14 2.2. Approved Standards................................................................................................... 15 2.3. Candidate Standards.................................................................................................. 19 2.4. Emerging Standards................................................................................................... 20 2.5. Deprecated Standards ............................................................................................... 21 3. Policies ............................................................................................................................ 22 3.1. Technical Policies ...................................................................................................... 22 3.1.1. 3.1.2. 3.1.3. 3.1.4. 3.1.5. 3.1.6. 3.1.7. 4. Adoption ............................................................................................................................................ 23 Compliance ....................................................................................................................................... 23 Open Standards ................................................................................................................................ 23 Procurement ...................................................................................................................................... 23 Redesigning Service Delivery............................................................................................................ 23 The Internet is Key ............................................................................................................................ 23 Minimizing the Reliance on Manual Services .................................................................................... 23 Technical Standards ....................................................................................................... 24 4.1. Introduction to Technical Standards ........................................................................... 24 4.2. Presentation and User Interface Standards ................................................................ 24 4.2.1. 4.2.2. 4.2.3. 4.2.4. 4.2.5. 4.2.6. 4.2.7. 4.2.8. 4.2.9. 4.3. HTML ................................................................................................................................................ 24 XHTML .............................................................................................................................................. 25 JPEG ................................................................................................................................................. 25 GIF .................................................................................................................................................... 25 PNG .................................................................................................................................................. 26 TIFF................................................................................................................................................... 26 Ecma Script / Javascript .................................................................................................................... 26 Atom .................................................................................................................................................. 26 WAI ................................................................................................................................................... 27 Multimedia .................................................................................................................. 28 4.3.1. 4.3.2. 4.3.3. MPEG-1/2 Audio Layer 3 .................................................................................................................. 28 AAC ................................................................................................................................................... 28 WMA ................................................................................................................................................. 28 Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 4 / 63 4.3.4. 4.3.5. 4.3.6. 4.3.7. 4.3.8. 4.3.9. 4.3.10. 4.4. Standards for web based and electronic services ....................................................... 32 4.4.1. 4.4.2. 4.4.3. 4.4.4. 4.4.5. 4.4.6. 4.4.7. 4.4.8. 4.4.9. 4.5. 4.6. Unicode ............................................................................................................................................. 35 UTF-16 .............................................................................................................................................. 35 UTF-8 ................................................................................................................................................ 35 RTF ................................................................................................................................................... 35 .txt ..................................................................................................................................................... 36 PDF ................................................................................................................................................... 36 Microsoft Office binary formats .......................................................................................................... 36 ODF ................................................................................................................................................... 37 UML ................................................................................................................................................... 37 XMI .................................................................................................................................................... 37 UBL ................................................................................................................................................... 37 Xpath ................................................................................................................................................. 38 ISO 11179-5 ...................................................................................................................................... 38 Core Component Technical Specification ......................................................................................... 38 DCMI ................................................................................................................................................. 39 XNAL ................................................................................................................................................. 39 ISO 639 - Language Codes ............................................................................................................... 39 ISO 4217 - Currency Codes .............................................................................................................. 40 ISO Country Codes ........................................................................................................................... 40 Connectivity Standards .............................................................................................. 41 4.7.1. 4.7.2. 4.7.3. 4.7.4. 4.7.5. 4.7.6. 4.7.7. 4.7.8. 4.7.9. 4.7.10. 4.7.11. 4.7.12. 4.7.13. 4.7.14. 4.7.15. 4.8. XML ................................................................................................................................................... 32 SOAP ................................................................................................................................................ 32 WSDL ................................................................................................................................................ 32 UDDI ................................................................................................................................................. 32 EbXML .............................................................................................................................................. 33 XML Schema ..................................................................................................................................... 33 XSL ................................................................................................................................................... 33 BPMN ................................................................................................................................................ 34 EDI .................................................................................................................................................... 34 WS - I ......................................................................................................................... 34 Information and Data Exchange Standards ................................................................ 35 4.6.1. 4.6.2. 4.6.3. 4.6.4. 4.6.5. 4.6.6. 4.6.7. 4.6.8. 4.6.9. 4.6.10. 4.6.11. 4.6.12. 4.6.13. 4.6.14. 4.6.15. 4.6.16. 4.6.17. 4.6.18. 4.6.19. 4.7. Real Audio ......................................................................................................................................... 29 MPEG-4 Part 2 .................................................................................................................................. 29 H.264/MPEG-4 part 10/AVC.............................................................................................................. 29 Real Video ......................................................................................................................................... 29 WMV ................................................................................................................................................. 30 MPEG-4 ............................................................................................................................................ 31 ASF ................................................................................................................................................... 30 S/MIME ............................................................................................................................................. 41 POP ................................................................................................................................................... 41 IMAP ................................................................................................................................................. 41 HTTP ................................................................................................................................................. 41 HTTPS .............................................................................................................................................. 42 LDAP ................................................................................................................................................. 42 DNS ................................................................................................................................................... 42 FTP ................................................................................................................................................... 43 FTPS ................................................................................................................................................. 43 IP ....................................................................................................................................................... 43 TCP ................................................................................................................................................... 43 UDP ................................................................................................................................................... 44 IEEE 802.11 ...................................................................................................................................... 44 SMTP ................................................................................................................................................ 44 VPN ................................................................................................................................................... 44 Security Standards ..................................................................................................... 46 4.8.1. 4.8.2. 4.8.3. 4.8.4. 4.8.5. 4.8.6. 4.8.7. 4.8.8. 4.8.9. 4.8.10. PKCS #7 (RFC 2315) ........................................................................................................................ 46 IpSec ................................................................................................................................................. 46 SSL ................................................................................................................................................... 46 TLS.................................................................................................................................................... 46 TDES ................................................................................................................................................. 47 AES ................................................................................................................................................... 47 RSA ................................................................................................................................................... 47 SAML ................................................................................................................................................ 47 WPA .................................................................................................................................................. 48 WS-security ....................................................................................................................................... 48 Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 5 / 63 5. Other standards............................................................................................................... 49 5.1. Candidate Standards.................................................................................................. 49 5.1.1. 5.1.2. 5.1.3. 5.1.4. 5.1.5. 5.1.6. 5.1.7. 5.2. Emerging Standards................................................................................................... 52 5.2.1. 5.3. Pending YIC Approval ....................................................................................................................... 49 XBRL ................................................................................................................................................. 49 XHTML Mobile Profile ....................................................................................................................... 49 MPLS ................................................................................................................................................ 49 Saudi Post National Address Profile.................................................................................................. 50 XML Encryption ................................................................................................................................. 50 XML Signature................................................................................................................................... 50 Office Open XML ............................................................................................................................... 52 Deprecated standards ................................................................................................ 53 5.3.1. 5.3.2. 5.3.3. 5.3.4. 5.3.5. 5.3.6. 5.3.7. 5.3.8. 5.3.9. 5.3.10. 5.3.11. 5.3.12. WML .................................................................................................................................................. 53 EPS ................................................................................................................................................... 53 ISO/IEC 8859-1:1998 ........................................................................................................................ 53 ASCII ................................................................................................................................................. 54 WAP .................................................................................................................................................. 54 DES ................................................................................................................................................... 54 RSS ................................................................................................................................................... 54 DTD ................................................................................................................................................... 55 MPEG-1 ............................................................................................................................................ 55 MPEG-2 ............................................................................................................................................ 30 AVI .................................................................................................................................................... 55 Quicktime .......................................................................................................................................... 56 6. Choosing Standards ....................................................................................................... 57 6.1. International Standards Bodies .................................................................................. 57 6.2. Standards per International body ............................................................................... 59 7. Acknowledgements......................................................................................................... 63 7.1. Copyright Notices ....................................................................................................... 63 Copyright Notice This document is a working draft or committee draft and is copyright-protected by MCIT. While the reproduction of working drafts or committee drafts in any form for use by participants in the YEFI standards development process is permitted without prior permission from MCIT, neither this document nor any extract from it may be reproduced, stored or transmitted in any form for any other purpose without prior written permission from MCIT. Reproduction for sales purposes may be subject to royalty payments or a licensing agreement. Violators may be prosecuted. List of Tables Table 1: Document Structure .................................................................................................... 12 Table 2: Glossary ..................................................................................................................... 13 Table 3: Presentation & User Interface approved standards ..................................................... 15 Table 3: Presentation & User Interface approved standards..................................................... 15 Table 4: Web Based & Electronic Services approved standards ............................................. 16 Table 5: Information & Data Exchange approved standards ..................................................... 17 Table 6: Connectivity approved standards ................................................................................ 17 Table 7: Security approved standards ...................................................................................... 18 Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 6 / 63 Table 8: Candidate Application Integration Standards .............................................................. 19 Table 9: Information Access and Interchange candidate standards .......................................... 19 Table 10: Interconnectivity candidate standards ....................................................................... 19 Table 11: Security candidate standards .................................................................................... 19 Table 12: Emerging Standards ................................................................................................. 20 Table 13: Deprecated Standards .............................................................................................. 21 Table 14: SSO list .................................................................................................................... 59 Table 15: OpenGIS and Ecma standrads ................................................................................. 59 Table 16: W3C & OASIS standards .......................................................................................... 60 Table 17: W3C standards ......................................................................................................... 62 List of Figures Figure 1 Yesser Program ........................................................................................................... 8 Figure 2 YEFI, YESSER and outside interactions....................................................................... 9 Figure 3 YEFI High Level Architecture...................................................................................... 24 Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 7 / 63 1. 1.1. Introduction Definitions 1.1.1.The e-Government Concept1 E-Government may be defined as the effective, integrated utilization of all information and communication technologies to ease and speed up transactions in government organizations (G2G), between government organizations and customers (G2C), between government organizations and their employees (G2E) and between government organizations and business organizations (G2B). 1.1.2.Yesser The e-Government Program - Yesser - was launched with the following objectives: o Raising the public sector's productivity and efficiency o Providing better and more easy-to-use services for individual and business customers o Increasing return on investment (ROI) o Providing the required information in a timely and highly accurate fashion. 1.1.3.Yesser Interoperability Framework (YEFI)2 It’s a unified framework to implement e-government. It includes cross – governmental specifications and policies, to enable cross – governmental integration and facilitate G2G transactions and data sharing. 1.2. E-Government in Saudi Arabia The Government of Saudi Arabia attaches high significance to the e-government concept and the transformation process that leads to its realization. It strongly believes in the huge benefits such concept of e-government entails for the national economy. Transformation to an information society cannot be achieved without comprehensive collaboration and concerted efforts to realize the set objectives. 1.2.1. The Program Philosophy Yesser plays the role of enabling the implementation of e-government. It reduces, as much as possible, centralization in e-government implementation while ensuring the minimum level of coordination between government departments. The program's work methodology is based on the following main principles: 1 2 Principle 1 Unified vision, priorities, standards and frameworks Principle 2 Not only technology, but much more Principle 3 Reduce centralization as much as possible Referenced from the YESSER website: http://www.yesser.gov.sa/english/what_is_gov.asp?id=item2 Referenced from the YESSER website: http://www.yesser.gov.sa/english/YEFI.asp?id=item4 Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 8 / 63 Principle 4 Develop once, use many times 1.2.2.Yesser and ICT in Government ICT applications in government organizations have three categories: 1. Applications common to all government organizations (common applications) such as personnel systems, financial systems, document management systems, etc. 2. Applications that are jointly used by multiple government organizations such as recruitment applications 3. Applications that are specifically used by one government organization. Internet E-Services YEFI GSB YIC GRP Portal YESSER Agency Agency Agency Agency Agency Agency Agency Figure 1 Yesser Program Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 9 / 63 1.2.3. Rationale for YEFI o o o Enable electronic cross – governmental integration. Facilitate cross – governmental data sharing. Facilitate cross – governmental transactions. It is clear that in order to achieve cross-governmental integration and data sharing, a standards framework defining common technical policies and standards is necessary. In the context of e-Government, the standards framework will be encompassed and delivered by the YESSER Framework for Interoperability (YEFI) which will provide the necessary standards required to guarantee interoperability, integration, portability and reusability of systems. YEFI shall be a foundation framework for achieving the overall e-Government strategy and help to ensure that all government systems, processes and electronic services (i.e. eServices) are fit for their purpose. YEFI GSB YESSER Security / Firewalls Figure 2 YEFI, YESSER and outside interactions 1.3. Document Purpose The purpose of this document is to present Version 1.0 of the Technical Standards for YEFI. The intention of this document is that it should be used for consultation purposes within the Yesser Interoperability Committee (YIC) and for consultation purposes across the government agencies in Saudi Arabia. The technical standards document aims to inform which technology and engineering standards will be applicable for cross-governmental integration and data sharing. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 10 / 63 It is expected that the next version of this document, once consultation is complete, will form the basis for the first publicly available YEFI documentation. 1.4. Scope This document provides Technical standards for the following areas: 1.5. Presentation and User interface Multimedia Web based and Electronic service Information and Data Exchange Connectivity Security Target Audience This document is aimed at the prospective users of the YEFI framework, namely, Ministries and other government entities Decision makers and policy analysts ICT managers and Business analysts Businesses and Vendors Other stakeholders involved in interoperability projects or strategies 1.6. Guiding Principles 1.6.1.Resolution no. 40, March 2006 Resolution no. 40 of the Council of Ministers, dated March 2006, provides the baseline mandate for how agencies should approach information and data management to secure an interoperability solution for the delivery of electronic services to the users of government. 1.6.2.YEFI is a Living Framework YEFI is a living framework subject to formal review cycles. To minimize impacts brought about by changes to YEFI, all reasonable efforts will be taken to provide agencies with upfront communications about changes and requisite responses. 1.6.3.Yesser Interoperability Committee YEFI and any recommended changes are subject to approval by the members of the Yesser Interoperability Committee (YIC). Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 11 / 63 1.6.4.Use of Open Standards Wherever possible, YEFI will build upon international open standards. Where these standards do not exist or do not meet the needs for KSA, existing best practices and local industry standards may be adopted. The intention of this principle is that YEFI does not “re-invent the wheel”. 1.6.5.Publication All materials, which constitute the latest version of YEFI, will be published on the Internet and will be freely available to the public including stakeholders involved in interoperability projects or strategies. 1.6.6.Do not reinvent the wheel Any experiences relating to Interoperability standards and/or policies relevant to YEFI and arising from work that a government agency has already conducted will be reviewed and incorporated where possible. The intention of this principle is to not re-invent the wheel. 1.6.7.Government should not be adversely affected Where an organization is negatively affected by the adoption of YEFI, a Working Group may be appointed to work directly to resolve any issues. 1.6.8.Reference to Other International Interoperability Frameworks Interoperability frameworks from other countries will be used as reference where applicable. Regular checks for compatibility with other countries' interoperability frameworks should be part of the revision cycle for YEFI 1.6.9.Change Control All major changes to YEFI shall be subject to a change management and consultation process with all stakeholders, businesses and YIC members. Minor changes shall be subject to change management process and consultation with YIC members. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 12 / 63 1.7. Document Structure This document has the following structure: Section 1. Introduction 2. Summary 3. Policies 4. Technical Standards 5. Other Standards 6. Choosing Standards 7. Acknowledgements Description This section provides information about the purpose and background to the YEFI In this section, the classification of the standards is explained and the Approved and Candidate Standards are provided in a simple tabular form for visual reference. ICT policies relevant to the development and delivery of YEFI as a foundation framework for YESSER In this section, all the recommended standards for YEFI 1.0 are described. This section includes commentaries about the use of the Standards In this section, the Candidate, Emerging and Deprecated standards. This section provides a small discussion primer on what each Standards Body brings to the table and the focus area for each body / organization. The expectation is that this section will be removed from later versions of the Technical Standards. Acknowledgements, copyright notices etc. Table 1: Document Structure 1.8. Document Assumptions This document makes the following assumptions: Assumption 1 MCIT and YIC have people available to review and critique this document before it is distributed for wider review across government. Assumption 2 Delivery of this document is part of the consultation phase for Version 1.0. It is expected that the consultation phase may take up to 4 months to complete pending the amount of feedback and revisions needed to formalize the final version. Assumption 3 YIC is the body that formally accepts the YEFI as delivered. Assumption 4 This document will be replaced by a web-based HTML and/or PDF version available via either the Yesser website or the new, yet to be developed, YEFI portal. Assumption 5 Delivery of this document to MCIT and YIC signals the end of the Technical Standards stream for the current YEFI project. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 13 / 63 1.9. Glossary Abbreviation Description YIC YEFI Interoperability Committee YEFI YEsser Framework for Interoperability Table 2: Glossary Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 14 / 63 2. Summary – Standards Snapshot It is clear that in order to achieve cross-governmental integration and data sharing, a standards framework defining common technical policies and standards is necessary. In the context of e-Government, the standards framework will be encompassed and delivered by the YESSER Framework for Interoperability (YEFI) which will provide the necessary standards required to guarantee interoperability, integration, portability and reusability of systems. YEFI shall be a foundation framework for achieving the overall e-Government strategy and help to ensure that all government systems, processes and electronic services (i.e. eServices) are fit for their purpose. Snapshots The remainder of this section provides a snapshot list of the proposed Technical Standards for YEFI. The standards are described in detail in Section 3 and have hyperlinks to the respective authoritative sources for each standard. 2.1. Classification The standards are grouped in to four categories: Approved Those Standards (International or De Facto) agreed by YIC for inclusion in the YEFI Candidate Standards waiting YIC approval for inclusion as Approved Standards in the YEFI Emerging Standards and/or protocols coming through either the standardization process or are market driven and that bear watching by the YEFI team Deprecated Those standards and/or protocols that should not now be used Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 15 / 63 2.2. Approved Standards Presentation & User Interface Acronym and Version Hypertext Mark-up Language HTML 4.01 Extensible Hypertext Mark-up Language XHTML 1.0 Joint Photographic Experts Group JPEG Graphics Interchange Format GIF Portable Network Graphics PNG Tag Image File Format TIFF ECMA Script ECMA 262 Script 3rd Ed Atom Atom 1.0 Web Accessibility Initiative WAI Table 3: Presentation & User Interface approved standards Multimedia Acronym and Version MPEG-1/2 Audio Layer 3 MP3 Advanced Audio Codec AAC Windows Media Audio WMA 9.0 Real Audio Real Audio MPEG-4 Part 2 MPEG-4 Part 2 H.264/MPEG-4 part 10/AVC H.264/MPEG-4 part 10/AVC Real Video Real Video Windows Media Video WMV 9.0 Moving Picture Experts Group 4 MPEG-4 Advanced Systems Format ASF Table 4: Multimedia approved standards Web Based & Electronic Services Version Error! Unknown document property name. Acronym and Version Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 16 / 63 Extensible markup language XML 1.1 Simple Object Access Protocol SOAP 1.1 Web Services Definition Language WSDL 2.0 Universal Description, Discovery and Integration UDDI 2.0 E-business Extensible Mark-up Language EbXML 1.0 Extensible Mark-up Language Schema XML Schema 1.0 Extensible Stylesheet Language XSL Business Process Modeling Notation BPMN Electronic Document Interchange EDI Web Services Interoperability WS-I Table 5: Web Based & Electronic Services approved standards Information & Data Exchange Acronym and Version Unicode UNICODE ISO/IEC 106461:2000 5.0 Unicode Transformation Format 16 bit UTF-16 Unicode Transformation Format 8 bit UTF-8 Rich Text Format RTF 1.6 Text .txt Portable Document Format PDF Microsoft Office 1997 MS Office 97 binary formats OpenDocument Format ODF 1.1 Unified Modeling Language UML Extensible Metadata Interchange XMI Universal Business Language UBL XML Path Language Xpath ISO 11179-5 ISO 11179-5 Core Component Technical Specification Core Component Technical Specification Dublin Core Metadata Initiative DCMI Extensible Name and Address mark-up Language ISO 639 - Language Codes ISO 4217 - Currency Codes Version Error! Unknown document property name. XNAL ISO 639 ISO 4217 Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 17 / 63 ISO Country Codes ISO 3166-1, 3166-2 Table 6: Information & Data Exchange approved standards Connectivity Acronym and Version Secure / Multipurpose Internet Mail Extensions Post Office Protocol S/MIME 3.0 POP 3.0 Internet Message Access Protocol Hypertext Transfer Protocol Secure Hypertext Transfer Protocol Lightweight Directory Access Protocol Domain Name Server IMAP 4.0 HTTP 1.1 HTTPS LDAP v3 DNS File Transfer Protocol FTP File Transfer Protocol over Secure Socket Layer Internet Protocol FTPS IP v4 Transmission Control Protocol User Datagram Format TCP UDP Wireless Channel G IEEE 802.11g Simple Mail Transfer Protocol Virtual Private Network SMTP VPN Table 7: Connectivity approved standards Security Acronym and Version Public-Key Cryptography Standard Internet Protocol Security Secure Socket Layer Transport Layer Security Triple Data Encryption Standard Advanced Encryption Standard RSA Algorithm Version Error! Unknown document property name. PKCS #7 (RFC 2315) 1.5 IPsec SSL 3.0 TLS 1.1 TDES AES RSA Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 18 / 63 Security Assertion Mark-up Language Wi-Fi Protected Access SAML 2.0 WPA 2 Web Services Security WS-security Table 8: Security approved standards Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 19 / 63 2.3. Candidate Standards Application Integration candidate Standards Acronym and Version Extensible Business Reporting Language XBRL Table 9: Application Integration candidate Standard Information Access and Interchange Acronym and Version Extensible Hypertext Mark-up Language for Mobile Profile XHTML Mobile Profile 1.1 Saudi Post National Address File Table 10: Information Access and Interchange candidate standards Interconnectivity Acronym and Version Multi-protocol Label Switching MPLS Table 11: Interconnectivity candidate standard Security Acronym and Version Extensible Mark-up Language Encryption XML Encryption Extensible Mark-up Language Signature XML Signature Table 12: Security candidate standards Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 20 / 63 2.4. Emerging Standards Emerging Standards Acronym and Version Office Open XML OOXML Table 13: Emerging Standard Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 21 / 63 2.5. Deprecated Standards Deprecated standards Acronym and Version Wireless Markup Language WML Encapsulated PostScript EPS ISO/IEC 8859-1:1998 ISO/IEC 8859-1:1998 American Standard Code for Information Interchange ASCII Wireless Application Protocol WAP Data Encryption Standard DES Really Simple Syndication / Rich Site Summary RSS Document Type Definition DTD Moving Picture Experts Group 1 MPEG 1 Moving Picture Experts Group 2 MPEG 2 Audio Video Interleave AVI Table 14: Deprecated Standards Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 22 / 63 3. Policies The key policy decisions that will serve to shape YEFI include: 1. Alignment with the Internet: the universal adoption of common specifications used on the Internet and World Wide Web for all public sector information systems; 2. Adoption of XML as the primary standard for data integration and data management for all public sector systems; 3. Adoption of the browser as the key interface: all public sector information systems are to be accessible through browser-based technology; other interfaces are permitted but only in addition to browser-based ones; 4. The development and adoption of the metadata standards, based on the international Dublin Core model (ISO 15836) as well as direct experiences from benchmarking studies from other country e-Government experiences; 5. Interfaces between government information systems and intermediaries providing eGovernment services shall conform to the standards in YEFI; 6. Interfaces between intermediaries and the public are outside the scope of YEFI. Adherence to YEFI standards and technical policies shall be mandatory for each Ministry. Other government agencies are strongly encouraged to adopt the YEFI. Full compliance with YEFI is required within 18 months of publication of YEFI version 1.1. 3.1. Technical Policies All Technical Standards will use either “Shall”, “Should”, “May” and “Can” as defined by the IEEE when describing expected behaviors with regard to the utilization and usage of technical standards.3 The use of the terms “Must” and “Will” is not permitted. Rationale The word shall is used to indicate mandatory requirements strictly to be followed in order to conform to the standard and from which no deviation is permitted (shall equals is required to). The use of the word must is deprecated and shall not be used when stating mandatory requirements; must is used only to describe unavoidable situations. The use of the word will is deprecated and shall not be used when stating mandatory requirements; will is only used in statements of fact. 3 http://standards.ieee.org/guides/style/section5.html Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 23 / 63 The word should is used to indicate that among several possibilities one is recommended as particularly suitable, without mentioning or excluding others; or that a certain course of action is preferred but not necessarily required; or that (in the negative form) a certain course of action is deprecated but not prohibited (should equals is recommended that). The word may is used to indicate a course of action permissible within the limits of the standard (may equals is permitted to). The word can is used for statements of possibility and capability, whether material, physical, or causal (can equals is able to). 3.1.1. Adoption The adoption of the Yesser Framework for Interoperability (YEFI) shall allow for a sensible transition. 3.1.2. Compliance Any new information system, software application, or electronic data/information resource (or current instances of these being redeveloped or replaced), or systems for interfacing with these, shall comply with YEFI 3.1.3. Open Standards YEFI will employ Open Standards wherever possible; where Open Standards do not meet the needs of the Saudi government, preference should be given to industry best practice then Saudi Government approved protocols 3.1.4. Procurement All tenders / procurement of new systems (hardware and/or software) shall specify the need for compliance with YEFI 3.1.5. Redesigning Service Delivery All government entities shall redesign their services for delivery using telecommunications and information technology applications4 3.1.6. The Internet is Key Each government entity shall use the Internet eg e-mail and ecommunication media in performing its activities 5 3.1.7. Minimizing the Reliance on Manual Services Each government entity shall minimize reliance on traditional manual and/or paper based methods in providing government services6 4 5 6 Taken from Resolution 40, March 2006 Taken from Resolution 40, March 2006 Taken form Resolution 40, March 2006 Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 24 / 63 4. Technical Standards 4.1. Introduction to Technical Standards This paper provides for a common overview of the technical infrastructure and standards recommended for the establishment of interoperability between ICT systems in the SaudiArabian public sector. The establishment of an interoperability framework provides a platform for agencies to select products that comply with open standards and interoperability. In turn, the adoption of interoperable products provides for improved connections between agencies, allows better data sharing practices and makes it easier to commence the process of standardization across agencies, with the purpose of providing better service to agencies and citizens. YESSER Interoperability Committee (YIC) Security Web Services E-Service Models XSD Registry User Interface Data Exchange Repository Connectivity Policies Governance YEFI Figure 3 YEFI High Level Architecture 4.2. Presentation and User Interface Standards 4.2.1. HTML Name: Hypertext Markup Language Version Error! Unknown document property name. Abbreviation: HTML Version: 4.01 Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 25 / 63 Owner: W3C Alternatives: XHTML 1.0 Status: Approved Usage areas: Publishing web content Link: http://www.w3.org/TR/html401/ Description: HTML is used to display web content Explanation for status: HTML is the basis of a lot of communication over the internet and the preferred way to display content in many applications, including browsers. It is compatible with many different kinds of software. In development of new applications, specifying XHTML as a standard should be considered 4.2.2. XHTML Name: Extensible HyperText Markup Language Abbreviation: XHTML Version: 1.0 Owner: W3C Alternatives: HTML 4.01 Status: Approved Usage areas: Publishing web content Link: http://www.w3.org/TR/xhtml1/ Description: For displaying structured web content in a human and machine-readable format. XHTML is the next generation of HTML, using stricter syntax to make it machine-readable Explanation for status: XHTML is recommended as a standard for delivering web content, since its strict format makes it easier to use on different platforms, with different software and devices. 4.2.3. JPEG Name: Joint Photographic Experts Group Abbreviation: JPEG Version: - Owner: ISO Alternatives: PNG Status: Approved Usage areas: Graphics Link: http://www.w3.org/Graphics/JPEG/itu-t81.pdf Description: JPEG is an image format, well suited for displaying pictures that will tolerate information loss Explanation for status: JPEG is a patented format, where the patent has expired in the US. For Europe the patent status remains unclear. The format is widely used and most applications recognize JPEG images 4.2.4. GIF Name: Graphics Interchange Format Abbreviation: GIF Version: - Owner: - Alternatives: PNG Status: Approved Usage areas: Graphics Link: http://www.w3.org/Graphics/GIF/spec-gif89a.txt Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 26 / 63 Description: GIF is an image format, useful for web purposes because of its small size. It supports animation. Explanation for status: GIF used to be patented, but patents have now expired. This means that the format can be used royalty-free. 4.2.5. PNG Name: Portable Network Graphics Abbreviation: PNG Version: - Owner: W3C Alternatives: GIF Status: Approved Usage areas: Graphics Link: http://www.w3.org/Graphics/PNG/ Description: PNG is an image format, developed as an open alternative to GIF. It does not have the same adoption rate and support though. PNG is suited for displaying graphics, less so for displaying photographic content on the internet because of substantially larger file size Explanation for status: Does not support animation, like GIF does. If this functionality is needed, consider using the GIF image format 4.2.6. TIFF Name: Tagged Image File Format Abbreviation: TIFF Version: 6.0 Owner: - Alternatives: JPEG Status: Approved Usage areas: Graphics Link: http://partners.adobe.com/public/developer/tiff/index.html Description: TIFF is an image format with a wide range of options, well-suited for exchanging images between professional image editing applications Explanation for status: TIFF has a complicated specification that makes it difficult to use in web applications. For applications in this category, alternatives should be considered. 4.2.7.Ecma Script / Javascript Name: ECMA 262 Script Abbreviation: - Version: 3rd edition Owner: ECMA Alternatives: Status: Approved Usage areas: Building dynamic web pages Link: http://www.ecma-international.org/publications/standards/Ecma-262.htm Description: ECMA is the standardized version of JavaScript, a scripting language that makes it possible to construct dynamic web pages Explanation for status: Dynamic functionality in web pages can make them more user-friendly. JavaScript is a good way of building dynamic functionality and the scripting language is recognized on most modern platforms. 4.2.8. Atom Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 27 / 63 Name: Atom Abbreviation: - Version: 1.0 Owner: IETF Alternatives: RSS Status: Approved Usage areas: Content publishing Link: http://tools.ietf.org/html/rfc4287 Description: The Atom standard, like RSS, is used to publish and syndicate web content. The Atom standard has been developed as a more open and XML-compliant alternative to the RSSstandard. Explanation for status: The Atom standard has a more open change process than the RSS standards and is more focused on complying with existing XML-standards. It is not yet as widely used as RSS though. 4.2.9. WAI Name: Web accessibility initiative Abbreviation: -WAI Version: 2.0 Owner: W3C Alternatives: Status: Approved Usage areas: Usability, accessibility Link: http://www.w3.org/TR/WCAG20/ Description: WAI is a set of guidelines to make web content more accessible to people who have difficulties using normal interfaces, e.g. disabled users. The guidelines are also used to ensure that content can be delivered on a number of different platforms, for example mobile devices with limited screen resolution and bandwidth. There are also guidelines for accessibility in developer tools (such as HTML editors) and guidelines for user agents (such as browsers or media players) Explanation for status: WAI is standardized through W3C and is the most widely used set of guidelines for accessibility, ensuring that vendors and developers are familiar with the standard. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 28 / 63 4.3. Multimedia 4.3.1. MPEG-1/2 Audio Layer 3 Name: MPEG-1/2 Audio Layer 3 Abbreviation: MP3 Version: - Owner: ISO/IEC Alternatives: AAC Status: Approved Usage areas: Audio codec Link: http://www.mp3licensing.com/ Description: MPEG-1/2 Audio Layer 3 is an audio lossy compression format. It uses an advanced type of audio compression, which reduces the file size with little reduction in audio quality. Explanation for status: The MP3 format has been an ISO standard since 1993. MP3 is backward and forward compatible ensuring that every mp3-file created in the past can be played on all current and future digital audio players. 4.3.2. AAC Name: Advanced Audio Codec Abbreviation: AAC Version: - Owner: ISO/IEC Alternatives: Status: Approved Usage areas: Audio codec Link: http://www.iso.org/iso/iso_catalogue/catalogue_tc/catalogue_detail.htm?csnumber=43026 Description: AAC is a standardized, lossy compression and encoding scheme for digital audio. AAC audio is placed in a MP4 container, but raw AAC files is also an option, although not advised Explanation for status: AAC is specified both as Part 7 of the MPEG-2 standard, and Part 3 of the MPEG-4 standard. It is a successor format of MP3 for audio coding at medium to high bit rates. It has a number of improvements over MP3, in coding efficiency and frequency handling. 4.3.3. WMA Name: Windows Media Audio Abbreviation: WMA Version: 9 Owner: Microsoft Alternatives: AAC Status: Approved Usage areas: Audio codec Link: http://www.microsoft.com/windows/windowsmedia/forpros/codecs/audio.aspx Description: WMA is a proprietary audio compression technology. WMA can refer to the audio file format or the audio codec. Explanation for status: WMA is one of the most popular codecs. WMA Lossless codec compresses audio data without loss of audio fidelity. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 29 / 63 4.3.4. Real Audio Name: Real Audio Abbreviation: RA Version: 10 Owner: RealNetworks Alternatives: AAC Status: Approved Usage areas: Audio codec Link: http://www.realnetworks.com/products/index.html Description: RealAudio codec is a proprietary audio format developed by RealNetworks. It can be used as a streaming media format over HTTP. Real Audio can be played from a Real Media container. Explanation for status: Real Audio is RealNetworks proprietary audio format. It is possible to obtain the source code to Reals codecs. There exist both a free player for Windows and an open source player for Linux/UNIX. 4.3.5. MPEG-4 Part 2 Name: MPEG-4 Part 2 Abbreviation: MPEG-4 Part2 Version: - Owner: ISO/IEC Alternatives: MPEG-4 Part 10 Status: Approved Usage areas: Video codec Link: http://www.iso.org/iso/fr/iso_catalogue/catalogue_tc/catalogue_detail.htm?csnumber=39259 Description: Mpeg-4 part 2 is a DCT (Discrete Cosine Transform) video compression standard. Explanation for status: Several popular codecs including DivX, Xvid and Nero Digital are implementations of Mpeg-4 part 2 standard. 4.3.6. H.264/MPEG-4 part 10/AVC Name: Advanced Audio Codec Abbreviation: H.264 Version: - Owner: ISO/IEC, ITU-T Alternatives: Status: Approved Usage areas: Video codec Link: http://www.itu.int/rec/T-REC-H.264/en Description: H.264, MPEG-4 Part 10, or AVC is a standard for video compression. allowing to compress video much more effectively and to provide more flexibility for application to a wide variety of network environments Explanation for status: H.264 experienced widespread adoption within a few years of the completion of the standard. It is employed widely in applications ranging from television broadcast to video for mobile devices 4.3.7. Real Video Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 30 / 63 Name: Real Video Abbreviation: Real Video Version: 10 Owner: RealNetworks Alternatives: H.264 Status: Approved Usage areas: Video codec Link: http://www.realnetworks.com/products/index.html Description: Real Video codec is a proprietary video format developed by RealNetworks. Real Video can be played from a Real Media container. Explanation for status: RealVideo uses a proprietary video format making it difficult to use with other player or server software 4.3.8. WMV Name: Windows Media Video Abbreviation: WMV Version: 9 Owner: Microsoft Alternatives: Status: Approved Usage areas: Audio/Video file container Link: http://www.microsoft.com/windows/windowsmedia/forpros/codecs/video.aspx Description: WMV is a compressed video file format for several proprietary codecs developed by Microsoft. Explanation for status: Windows Media Video is a proprietary and closed codec from Microsoft. The codec is normally used in Advanced Systems Format file. 4.3.9. ASF Name: Advanced Systems Format Abbreviation: ASF Version: - Owner: Microsoft Alternatives: MP4 Status: Approved Usage areas: Audio/Video file container Link: http://www.microsoft.com/windows/windowsmedia/forpros/format/asfspec.aspx Description: ASF is Microsoft's proprietary digital audio/video container format, especially meant for streaming media. Explanation for status: ASF container format can technically include any codec. 4.3.10. MPEG-2 Name: MPEG-2 Abbreviation: MPEG-2 Version: - Owner: ISO/IEC Alternatives: MPEG-4 Status: Approved Usage areas: Audio/Video Link: http://www.chiariglione.org/mpeg/standards/mpeg-2/mpeg-2.htm Description: MPEG-2 is a set of audio/video coding and compression standards. MPEG-2 is the core of most digital television and DVD format. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 31 / 63 Explanation for status: MPEG-2 enhances many features of the MPEG-1 standard. MPEG-2 Audio Layer-3 is the standard for the popular MP3 format. Part 7 of the MPEG-2 standard is referred to as MPEG-2 AAC or AAC. 4.3.11. MPEG-4 Name: MPEG-4 Abbreviation: MP4 Version: - Owner: ISO/IEC Alternatives: Status: Approved Usage areas: Audio/Video file container Link: http://www.chiariglione.org/mpeg/standards/mpeg-4/mpeg-4.htm Description: MPEG-4 is a set of standards used primarily to compress audio and visual (AV) digital data. MP4 is the official container for MPEG-4 multimedia. Explanation for status: MPEG-4 absorbs many of the features of MPEG-1 and MPEG-2 and other related standards, adding new features such as (extended) VRML support for 3D rendering, objectoriented composite files (including audio, video and VRML objects), support for externally-specified Digital Rights Management and various types of interactivity. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 32 / 63 4.4. Standards for web based and electronic services 4.4.1. XML Name: Extensible markup language Abbreviation: XML Version: 1.1 Owner: W3C Alternatives: Status: Approved Usage areas: Building web applications, establishing a service-oriented architecture Link: http://www.w3.org/TR/xml11/ Description: XML is a markup language designed to describe data. It uses a Document Type Definition (DTD) or an XML Schema. XML tags are not predefined. Explanation for status: XML is an internationally approved W3C standard and is widely used and supported. 4.4.2. SOAP Name: Simple Object Access Protocol Abbreviation: SOAP Version: 1.1 Owner: W3C Alternatives: Status: Approved Usage areas: Building web applications, establishing a service-oriented architecture, XML Link: http://www.w3.org/TR/soap/ Description: For remote service invocation and XML data exchange. It uses SMTP and HTTP and is therefore widely deployable Explanation for status: SOAP is a widely used standard for XML data exchange. It is an open standard, standardized by W3C and uses HTTP or SMTP as transport protocol, making it compatible with existing infrastructure 4.4.3. WSDL Name: Web Services Description Language Abbreviation: WSDL Version: 2.0 Owner: W3C Alternatives: Status: Approved Usage areas: Building web applications, establishing a service-oriented architecture, XML Link: http://www.w3.org/TR/wsdl20/ Description: For remote service description. Describes what functions are available in a service. WSDL is often used in conjunction with SOAP when building web services. It describes how to use web services available on a server. Explanation for status: The World Wide Web Consortium (W3C) has not endorsed Version 1.1. Version 2.0, for which several drafts have been released, become a W3C recommendation. 4.4.4. UDDI Name: Universal Description, Discovery and Integration Abbreviation: UDDI Version: 3 Owner: OASIS Alternatives: ebXML Status: Approved Usage areas: Building web applications, establishing a service-oriented architecture, XML Link: http://www.uddi.org/specification.html Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 33 / 63 Description: For the publication and discovery of remote service descriptions, UDDI works as a directory of web services, allowing organizations to connect to each other’s web services. UDDI is vendor-driven, being developed by Microsoft, IBM etc. The focus is on helping large organizations manage their network of customers. Explanation for status: UDDI is one of the core web services standards. It is designed to work with SOAP and WSDL. UDDI is an OASIS standard 4.4.5. EbXML Name: Electronic Business using eXtensible Markup Language Abbreviation: EbXML Version: 1 Owner: OASIS / UNCEFACT Alternatives: UDDI Status: Approved Usage areas: Building web applications, establishing a service-oriented architecture, XML Link: http://www.ebxml.org/specs/ Description: Similar to UDDI, EbXML is a set of specifications for the publication and discovery of remote service descriptions. EbXML is more focused on building a universal solution than UDDI, focusing on establishing general B2B XML integration. It is supported by many of the same vendors that are behind UDDI. Explanation for status: EbXML is widely adopted and is standardized by OASIS/UNCEFACT. It is able to use a number of different application-level transport protocols, including SMTP, HTTP etc. The header is XML, but the body of the document may be XML, MIME or other formats. 4.4.6. XML Schema Name: Extensible markup language schema Abbreviation: XML Schema Version: 1 Owner: W3C Alternatives: Status: Approved Usage areas: Building web applications, establishing a service-oriented architecture, XML Link: http://www.w3.org/XML/Schema Description: For data-oriented message DTD as defined in the corresponding XML specification – for textual document-oriented applications Explanation for status: XML Schema is an internationally approved W3C standard and is widely used and supported. 4.4.7. XSL Name: Extensible Stylesheet Language Abbreviation: XSL Version: Owner: W3C Alternatives: Status: Approved Usage areas: Building web applications, establishing a service-oriented architecture, XML Link: http://www.w3.org/Style/XSL/ Description: XSL is a collection of ways to transform and format XML. It consists of XML transformations, XSL formatting objects and XML path language. Explanation for status: XSL is W3C standardized, making it widely applicable Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 34 / 63 4.4.8. BPMN Name: Business Process Modeling Notation Abbreviation: BPMN Version: 1.0 Owner: OMG Alternatives: Status: Approved Usage areas: Process modeling Link: http://www.bpmn.org/ Description: BPMN is a standardized way for graphically displaying business processes in a workflow. The purpose of the standard is to establish one common way of describing business processes, understood by both people on the design side and on the development side, on both the business side and the IT side. Explanation for status: Using a standardized way of describing processes can make it easier to integrate processes between different agencies. BPMN is a well-suited candidate for a common way of describing business processes because of its wide use and open status. 4.4.9. EDI Name: Electronic Data Interchange Abbreviation: EDI Version: Owner: XBRL consortium Alternatives: Status: Approved Usage areas: Building web applications, establishing a service-oriented architecture, XML Link: http://www.xbrl.org/Home/ Description: EDI is a widely used standard for exchanging electronic information between businesses. It is the predecessor of XML Explanation for status: The standard is maintained and developed by the international XBRL consortium and is not subject to license restrictions. It is widely used 4.5. WS - I Name: Web Services Interoperability Abbreviation: WS-I Version: Owner: Web Organization Alternatives: Status: Approved Services Interoperability Usage areas: Building web applications, establishing a service-oriented architecture, XML Link: http://www.ws-i.org/ Description: WS-I is a consortium of vendors, working to promote interoperability between web services. This is done by developing a set of profiles that specify how web services are used (for example WS-I basic profile that provides interoperability guidelines for standards such as SOAP, WSDL and UDDI) Explanation for status: WS-I has the backing and participation of the key vendors of web services solutions, such as Microsoft, IBM, BEA, SAP and Sun, ensuring that the profiles will be implemented in a wide number of solutions. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 35 / 63 4.6. Information and Data Exchange Standards 4.6.1. Unicode Name: Unicode Abbreviation: UNICODE ISO/IEC 10646-1:2000 Version: 5.0 Owner: Unicode Consortium Alternatives: Status: Approved Usage areas: Character encoding Link: http://unicode.org/ Description: Unicode is a standard describing how to represent characters in computer systems. It covers nearly all writing systems, including Arabic. Explanation for status: Unicode is the continuation of the work started on ISO/IEC 8859-1. Unicode includes support for all languages, not just the Latin alphabet 4.6.2. UTF-16 Name: Unicode Transformation Format 16 Abbreviation: UTF-16 Version: Owner: Unicode Consortium Alternatives: UTF-8 Status: Approved Usage areas: Character encoding Link: http://tools.ietf.org/html/rfc2781 Description: UTF-16 is a subset of Unicode. It uses variable length character encoding and can be used to represent any character in Unicode. UTF-16 is used by Windows and Java Explanation for status: UTF-16 is widely used and is the native encoding in the Windows operating system 4.6.3. UTF-8 Name: Unicode Transformation Format 8 Abbreviation: UTF-8 Version: Owner: Unicode Consortium Alternatives: UTF-16 Status: Approved Usage areas: Character encoding Link: http://tools.ietf.org/html/rfc3629 Description: UTF-8 is a subset of Unicode. It uses variable length character encoding and can be used to represent any character in Unicode. Explanation for status: UTF-8 is a byte-oriented encoding, capable of error-handling if the byte stream is corrupted. UTF-8 is commonly used on the web 4.6.4.RTF Name: Rich Text Format Abbreviation: RTF Version: 1.6 Owner: Microsoft Alternatives: .txt, OpenXML, ODF, binary formats Status: Approved Usage areas: Office productivity Link: http://msdn2.microsoft.com/en-us/library/aa140277(office.10).aspx Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 36 / 63 Description: Proprietary document format, developed by Microsoft. It is cross-platform and is being used on most systems Explanation for status: The format can be used on many different systems, and is well-suited for exchanging documents. Basic formatting options are possible, but advanced functionality is not available 4.6.5. .txt Name: Text format Abbreviation: .txt Owner: - Alternatives: OpenXML, ODF, formats Version: RTF, binary Status: Approved Usage areas: Office productivity Link: Description: Open format for basic data exchange Explanation for status: Data in .txt format is basic and unformatted, and can not contain for example formulas from spreadsheets 4.6.6. PDF Name: Portable Document Format Abbreviation: PDF Owner: Adobe Alternatives: OpenXML, ODF, formats, .txt Version: RTF, binary Status: Approved Usage areas: Office productivity Link: http://partners.adobe.com/public/developer/pdf/index_reference.html Description: The "de facto" standard for printable documents, PDF is a format capable of generating self-contained documents, containing fonts and layout Explanation for status: PDF can be generated and read on all platforms, which makes it a very useful format for sharing documents. A PDF document is not editable; other formats must be used if this is a requirement. 4.6.7. Microsoft Office binary formats Name: Microsoft Office binary formats Abbreviation: - Owner: Microsoft Alternatives: OpenXML, ODF, .txt Version: RTF, Status: Approved Usage areas: Office productivity Link: Description: The binary formats are used in Microsoft Office, making them the "de facto" standard for the majority of office documents. They include presentation documents (PowerPoint), word processing (Word) and spreadsheet functionality (Excel). Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 37 / 63 Explanation for status: The binary format specifications are made and owned by Microsoft, and are used everywhere due to the widespread use of Microsoft Office. Other XML-based formats are taking the place of the binary formats as productivity software is upgraded, but a large number of legacy documents will remain in this format and backwards compatibility with this format is important. 4.6.8. ODF Name: OpenDocumentFormat Abbreviation: ODF Owner: OASIS Alternatives: OpenXML, PDF, .txt Version: 1.1 RTF, Status: Approved Usage areas: Office productivity Link: v1.1.html http://docs.oasis-open.org/office/v1.1/OS/OpenDocument-v1.1-html/OpenDocument- Description: OpenDocument format is used in the OpenOffice software package. It has uses similar to Microsoft Office in presentation (Impress), word processing (Writer), spreadsheet functionality (Calc) etc. Explanation for status: The OpenDocument format is XML-based. It is released under GPLlicense terms. This makes it a very interoperable format that is beyond vendor control. 4.6.9. UML Name: Unified Modeling Language Abbreviation: UML Version: 2.0 Owner: OMG Alternatives: Status: Approved Usage areas: Software modeling, business process modeling Link: http://www.omg.org/docs/ad/97-08-11.pdf Description: UML is a standardized language for modeling software artifacts, describing business processes, modeling organizational structures and many other things. It is extensible in different ways, to suit custom purposes. Explanation for status: UML is widely used in the described areas, and is widely supported in many different kinds of software. 4.6.10. XMI Name: XML Metadata Interchange Abbreviation: XMI Version: 2.1 Owner: OMG Alternatives: Status: Approved Usage areas: Metadata Link: http://www.omg.org/technology/documents/formal/xmi.htm Description: XMI is an XML-based standard that allows developers to exchange UML models and other metadata. Explanation for status: XMI used other standards, such as UML and MOF to handle metadata, making it an open and easily implementable standard. 4.6.11. UBL Name: Universal Business Language Version Error! Unknown document property name. Abbreviation: UBL Version: - Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 38 / 63 Owner: OASIS Alternatives: Status: Approved Usage areas: XML, web services Link: http://www.oasis-open.org/committees/tc_home.php?wg_abbrev=ubl Description: UBL is a standard developed by an OASIS committee, aimed at making exchange of purchase orders and invoices easier and more standardized. Explanation for status: The standard is developed by OASIS in an open process. It is based on normal XML, making it widely applicable. It is possible to develop a country-specific subset of UBL (done in Denmark) or a region-specific subset (currently being done in Scandinavia and in Spain). 4.6.12. Xpath Name: XML Path Language Abbreviation: Xpath Version: 2.0 Owner: W3C Alternatives: Status: Approved Usage areas: XML, web services Link: http://www.w3.org/TR/xpath Description: Xpath is an expression language for navigating XML documents, describing a way to locate and process items in the document. Explanation for status: Xpath makes it easier for developers to navigate XML documents in a standardized way, without knowing the specifics of each XML implementation. It is a W3C recommendation and use of Xpath is increasing. 4.6.13. ISO 11179-5 Name: ISO 11179-5 Abbreviation: ISO 11179-5 Version: - Owner: ISO Alternatives: Status: Approved Usage areas: Metadata, web services Link: http://metadata-standards.org/11179 Description: ISO 11179-5 is a standard for representing metadata for an organization in a Metadata Registry Explanation for status: Currently the only ISO standard in this area, ISO 11179-5 is the best approach to use when organizing metadata in a common repository. It is used by some American government agencies and is supported by some vendor solutions. 4.6.14. Core Component Technical Specification Name: Core Component Technical Specification Abbreviation: CCTS Version: 2.01 Owner: UN/CEFACT Alternatives: Status: Approved Usage areas: Metadata, web services Link: http://www.unece.org/cefact/ebxml/CCTS_V2-01_Final.pdf Description: The CCTS standard is the result of UN/CEFACT’s work to establish a common set of business semantics, meaning a common set of expressions used in business. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 39 / 63 Explanation for status: Using CCTS can help systems using different syntaxes (like ebXML and UN/CEFACT) communicate better with each other by bridging some inconsistencies and highlighting others. 4.6.15. DCMI Name: Dublin Core Metadata Initiative Abbreviation: DCMI Version: - Owner: DCMI Alternatives: Status: Approved Usage areas: Metadata Link: http://dublincore.org/documents/usageguide/ Description: Dublin Core is a collection of metadata definitions, a defined set of metadata that can be used to describe various types of data, such as video, text, sound or images. Explanation for status: Dublin Core is an open standard that is flexible, expandable and widely accepted. 4.6.16. XNAL Name: eXtensible Name and Address markup Language Abbreviation: XNAL Version: 2.0 Owner: OASIS Alternatives: Status: Approved Usage areas: XML, web services, metadata, data standardization Link: http://www.oasis-open.org/committees/ciq/ciq.html#4 Description: XNAL are two different standards: one for describing names in a standardized way, and one for doing the same with addresses. The standards are XML-based and are built to accommodate a large number of different international ways of handling names and addresses. Explanation for status: While XNAL is not yet widely used, the use of a standardized address and name format is increasingly seen as an important prerequisite for data exchange. XNAL is the most well-known international standard in this area. 4.6.17. ISO 639 - Language Codes Name: ISO 639 - Language Codes Abbreviation: ISO 639 Version: ISO 6393 Owner: ISO Alternatives: Status: Approved Usage areas: Metadata, data standardization Link: http://www.iso.org/iso/en/CatalogueDetailPage.CatalogueDetail?CSNUMBER=39534&ICS1=1&IC S2=140&ICS3=20 Description: ISO 639 is a standardized way of representing language codes, consisting of three letters from the Latin alphabet (e.g. Arabic is “arb”). ISO 639 can be used to describe dialects as well (“arb” is standard Arabic) Explanation for status: ISO 639 is used widely in applications and on the web Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 40 / 63 4.6.18. ISO 4217 - Currency Codes Name: ISO 4217 - Currency Codes Abbreviation: ISO 4217 Version: Owner: ISO Alternatives: Status: Approved Usage areas: Metadata, data standardization Link: http://www.iso.org/iso/en/prods-services/popstds/currencycodeslist.html Description: ISO 4217 is an international standard for representing currency codes. It consists of three letters, the first two letters of a countries ISO 3166-1 alpha-2 country code and the letter of the country’s currency (Saudi Arabian Riyals become “SAR”). Explanation for status: The currency codes are ISO standardized and are widely used. No standardized alternatives exist. 4.6.19. ISO Country Codes Name: ISO Country Codes Abbreviation: ISO 3166-1 Version: Alpha-2, alpha-3 Owner: ISO Alternatives: Status: Approved Usage areas: Metadata, data standardization Link: http://www.iso.org/iso/en/prods-services/iso3166ma/index.html Description: The ISO country codes are used to uniquely identify different countries. The ISO 3166-1 alpha 2 version is a two-letter country code that is used, for example, for internet top-level domains. Alpha 3 is a three-letter code, used in passports, among other places. Explanation for status: Both the two-letter and the three-letter country codes are widely used, the two-letter version in currency codes, bank SWIFT codes etc., the three-letter version in machinereadable passports etc. This means that most IT-systems already support this way of representing a country. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 41 / 63 4.7. Connectivity Standards 4.7.1. S/MIME Name: Secure/Multipurpose Internet Mail Extensions Owner: IETF Abbreviation: S/MIME Version: 3.0 Alternatives: Status: Approved Usage areas: E-mail, connectivity, character encoding Link: http://www.faqs.org/rfcs/rfc2633.html Description: MIME is an extension of the basic SMTP e-mail protocol. The extension allows for sending text in languages other than English and file types such as images and sound. S/MIME is the secure version of the MIME standard, using public key encryption to sign e-mails. Explanation for status: Not all e-mail applications are compatible with S/MIME. Especially webbased e-mail is incompatible, resulting in error messages. 4.7.2. POP Name: Post Office Protocol Abbreviation: POP Version: 3 Owner: IETF Alternatives: IMAP Status: Approved Usage areas: E-mail, connectivity Link: http://tools.ietf.org/html/rfc1939 Description: POP is an application layer internet standard protocol that specifies how e-mail clients retrieve e-mail from servers. Explanation for status: Using POP downloads e-mails to a local client. If more people or clients access the same mailbox, it is preferable to leave e-mails on the server, using IMAP. 4.7.3. IMAP Name: Internet Message Access Protocol Abbreviation: IMAP Version: 4 Owner: IETF Alternatives: POP Status: Approved Usage areas: E-mail, connectivity Link: http://tools.ietf.org/html/rfc3501 Description: IMAP is an application layer internet standard protocol that specifies how e-mail clients retrieve e-mail from servers. Explanation for status: Using IMAP retrieves messages stored on a server, but does not download them. This makes it possible for multiple users or clients to use the same mailbox. Multiple users make IMAP a more complicated protocol to implement than POP3 4.7.4. HTTP Name: Hypertext Transfer Protocol Abbreviation: HTTP Version: 1.1 Owner: W3C / IETF Alternatives: Status: Approved Usage areas: Connectivity, web Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 42 / 63 Link: http://tools.ietf.org/html/rfc2616 Description: HTTP is a transport protocol for sending information via the web Explanation for status: HTTP is used as the basis for the modern internet, and is therefore extremely pervasive. HTTP traffic is allowed to pass through most routers and firewalls, making it a good protocol for making connections that would otherwise be blocked or require specialized setups. 4.7.5. HTTPS Name: Hypertext Transfer Protocol secure Abbreviation: HTTPS Version: - Owner: - Alternatives: Status: Approved Usage areas: Connectivity, web, security, encryption Link: Description: HTTPS is the method of securing HTTP traffic using SSL or TLS. It works by using a public key certificate on the accessed web server that is recognized by the user’s browser. Explanation for status: HTTPS is an easy-to-implement way of securing sensitive traffic, like users signing in on a website. It is not flawless however, and the effectiveness of the method relies on the security of the server, as HTTPS only encrypts traffic and does nothing to secure data stored on a server. 4.7.6. LDAP Name: Lightweight Directory Access Protocol Abbreviation: LDAP Version: 3 Owner: IETF Alternatives: Status: Approved Usage areas: User management Link: http://tools.ietf.org/html/rfc4510 Description: LDAP is a network protocol for accessing and modifying a directory, for example an employee directory Explanation for status: LDAP is widely supported, making it a good choice for directory networking. It is standardized through IETF. 4.7.7. DNS Name: Domain Name System Abbreviation: DNS Version: Owner: IETF Alternatives: Status: Approved Usage areas: Connectivity, web Link: http://tools.ietf.org/html/rfc1035 (and more) Description: DNS is the system that handles the mapping between IP-addresses and domain names on the internet Explanation for status: The de-facto (and only) standard for handling the mapping between IPaddresses and domain names, using DNS is essentially unavoidable Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 43 / 63 4.7.8. FTP Name: File Transfer Protocol Abbreviation: FTP Version: Owner: IETF Alternatives: HTTP Status: Approved Usage areas: Connectivity, web Link: http://tools.ietf.org/html/rfc959 Description: FTP is a file transfer protocol, used for uploading and downloading files from a server. Explanation for status: FTP is an open standard and is supported by most operating systems. It is not an especially secure protocol though, therefore FTPS is recommended for secure purposes 4.7.9. FTPS Name: Abbreviation: FTPS Version: Owner: IETF Alternatives: Status: Approved Usage areas: Connectivity, web Link: http://tools.ietf.org/html/rfc4217 Description: FTPS is the secure version of FTP, using the SSL/TLS layer to ensure security Explanation for status: FTPS is a fairly easy way to secure FTP using public key certificates 4.7.10. IP Name: Internet Protocol Abbreviation: IP Version: 4 Owner: Alternatives: Status: Approved Usage areas: Connectivity, web Link: http://www.faqs.org/rfcs/rfc791.html Description: The internet protocol (IP) is the standard used to assign IP-addresses to devices connected to the internet. Explanation for status: Version 4 of the internet protocol is being replaced by version 6 that has a larger number of addresses. It is recommended that new solutions be specified to support both version 6 and 4, since version 4 is going to be needed for a long time because of legacy solutions. 4.7.11. TCP Name: Transmission Control Protocol Abbreviation: TCP Version: Owner: IETF Alternatives: UDP Status: Approved Usage areas: Connectivity, web Link: http://tools.ietf.org/html/rfc793 Description: TCP is the layer between IP and an application. It controls how connections are made. It adds a layer of reliability to a connection, making sure that all packets arrive. This is important for loading web pages for example and web browsers use TCP for fetching web pages. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 44 / 63 Explanation for status: TCP is not suited for streaming applications, since a lost packet has to be re-sent before the following packets can be transmitted. For streaming applications like VoIP, UDP is better suited. 4.7.12. UDP Name: User Datagram Protocol Abbreviation: UDP Version: Owner: IETF Alternatives: TCP Status: Approved Usage areas: Connectivity, web Link: http://tools.ietf.org/html/rfc768 Description: UDP is a transport layer, like TCP. It is not as reliable, but more lightweight and more fault tolerant, making it suitable for streaming applications Explanation for status: If reliability and correct ordering of data packages is an important requirement, TCP might be the better choice. 4.7.13. IEEE 802.11 Name: - Abbreviation: IEEE 802.11 Version: g Owner: IEEE Alternatives: IEEE 802.11g / IEEE 802.11n Status: Approved Usage areas: Networking, connectivity, web Link: http://standards.ieee.org/getieee802/802.11.html Description: IEEE 802.11g is a networking protocol, used for establishing a wireless network between a computer and a router. It has a theoretical maximum speed of 54 mbps. Explanation for status: IEEE 802.11g is currently the most-used standard for wireless networking. Its predecessor 802.11b is being phased out. Eventually 802.11g will be replaced with 802.11n, with a theoretical maximum speed of over 100 mbps. Compatibility with this standard would be a good thing to take into consideration when choosing routers and other networking hardware. 4.7.14. SMTP Name: Simple Mail Transfer Protocol Abbreviation: SMTP Version: Owner: IETF Alternatives: Status: Approved Usage areas: Networking, connectivity, web, e-mail Link: http://tools.ietf.org/html/rfc821 Description: SMTP is a text-based protocol for exchanging mail messages Explanation for status: SMTP is the commonly used standard for transmitting e-mail over the internet. A wide range of software supports it. 4.7.15. VPN Name: Virtual Private Network Abbreviation: VPN Version: Owner: IETF Alternatives: Status: Approved Usage areas: Networking, connectivity, web Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 45 / 63 Link: http://tools.ietf.org/html/rfc2764 Description: VPN is a way of using the open Internet to establish a connection to a private network. This allows a person to access the intranet of a company from the outside for example. Explanation for status: VPN is not standardized through an official standardization organization, but is widely used and I supported by many different tools and many different kinds of software Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 46 / 63 4.8. Security Standards 4.8.1. PKCS #7 (RFC 2315) Name: Public Key Cryptography Standards Abbreviation: PKCS #7 Version: 1.5 Owner: RSA Security Alternatives: Status: Approved Usage areas: Security, encryption Link: http://www.rsasecurity.com/rsalabs/node.asp?id=2124 Description: One of several cryptography standards in PKCS, PKCS #7 is used to encrypt messages under a PKI. Explanation for status: The PKC standards are not, despite the name, standardized through a standardization body, but are owned by the company RSA. 4.8.2. IpSec Name: IP security Abbreviation: Ipsec Version: Owner: IETF Alternatives: TLS Status: Approved Usage areas: Security, encryption, connectivity Link: http://tools.ietf.org/html/rfc4301 Description: IPsec provides a way to encrypt or authenticate IP packets in a data stream Explanation for status: The use of IPsec is optional in IP version 4, but is mandatory in IP version 6. This must be taken into consideration when choosing IP standards. For transversing NATs and firewalls, IPsec might not be the best choice. TLS should be considered instead. 4.8.3. SSL Name: Secure Sockets Layer Abbreviation: SSL Version: 3.0 Owner: IETF Alternatives: TLS Status: Approved Usage areas: Security, encryption, connectivity Link: http://wp.netscape.com/eng/ssl3/ Description: SSL is the predecessor of TLS. It is a cryptographic protocol. An industry standard for encrypting TCP traffic. SSL is commonly used to encrypt HTTP data before it is delivered over TCP. Explanation for status: SSL is widely supported, but has been super-seeded by TLS version 1.0. 4.8.4. TLS Name: Transport Layer Security Abbreviation: TLS Owner: IETF Alternatives: Encryption Version: 1.1 XML Status: Approved Usage areas: Security, encryption, connectivity Link: http://tools.ietf.org/html/rfc4346 Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 47 / 63 Description: TLS is a cryptographic protocol, securing applications using HTTP, FTP etc. when communicating over IP (e.g. HTTPS) Explanation for status: TLS is best suited for establishing connections between two parties (for example client/server). For web services, that require multiple connections, XML encryption should be considered. 4.8.5. TDES Name: Triple Data Encryption Standard Abbreviation: TDES Version: - Owner: - Alternatives: AES Status: Approved Usage areas: Security, encryption Link: Description: TDES is a non-standard implementation of the DES encryption, using the DES algorithm with three keys. Explanation for status: TDES is practically secure, since the effort to break the encryption requires substantial resources. It is still widely used and will probably remain in use for a while, even though it is inferior to AES performance-wise. 4.8.6. AES Name: Advanced Encryption Standard Abbreviation: AES Version: Owner: National Institute of Science and Technology Alternatives: Status: Approved Usage areas: Security, encryption Link: Security, encryption Description: AES is the successor of the DES encryption algorithm Explanation for status: AES is the current encryption standard in the US public sector, making it widely used. No successful attacks on the AES encryption currently exist. 4.8.7. RSA Name: RSA Abbreviation: RSA Version: Owner: RSA Laboratories Alternatives: Status: Approved Usage areas: Security, encryption Link: http://www.rsa.com/rsalabs/node.asp?id=2125 Description: RSA is an encryption algorithm, used for public-key encryption. Explanation for status: RSA is currently believed to be secure, due to the infeasibility of breaking the encryption. It is not however impossible that RSA can be broken in the future. 4.8.8. SAML Name: Security Assertion Markup Language Abbreviation: SAML Version: 2.0 Owner: OASIS Alternatives: Status: Approved Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 48 / 63 Usage areas: Security, user management Link: http://www.oasis-open.org/committees/download.php/22553/sstc-saml-tech-overview2%200-draft-13.pdf Description: SAML is an XML-based standard for exchanging information on authentication and authorization Explanation for status: SAML is an open standard, and part of OASIS. It is a widely used standard for identity management. 4.8.9. WPA Name: Wi-fi protected access Abbreviation: WPA Version: 2 Owner: Wi-fi Alliance Alternatives: Status: Approved Usage areas: Security, encryption, connectivity, networking Link: http://www.wi-fi.org/knowledge_center/wpa/ Description: WPA is the successor of the WEP wireless encryption standard. WPA is used to encrypt data sent over a wireless connection. Explanation for status: WPA version 2 implements IEEE 802.11i, a standard specifying security for wireless networks. WPA2 is widely used and most modern wireless networking equipment supports it. 4.8.10. WS-security Name: Web Services Security Abbreviation: WS-Security Version: 1.1 Owner: OASIS Alternatives: Status: Approved Usage areas: Security, networking, building web applications Link: http://www.oasis-open.org/committees/tc_home.php?wg_abbrev=wss Description: WS-security is a communications protocol, describing how to implement security when using web services Explanation for status: WS-security describes enhancements to the SOAP protocol, a standardized way of using open standards to implement web services security, such as SAML and TLS. Using WS-security can ensure interoperability with other solutions using the same specifications Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 49 / 63 5. Other standards 5.1. Candidate Standards 5.1.1. Pending YIC Approval These standards are in use as international standards. Their use in the Kingdom of Saudi Arabia requires some discussion before adoption regarding the practicality of setting these as standards that shall be complied with. 5.1.2. XBRL Name: Extensible Business Reporting Language Abbreviation: XBRL Version: Owner: XBRL consortium Alternatives: Status: Candidate Usage areas: Building web applications, establishing a service-oriented architecture, XML Link: http://www.xbrl.org/Home/ Description: XBRL is an XML-based standard for describing and exchanging financial and business information. Explanation for status: The standard is maintained and developed by the international XBRL consortium and is not subject to license restrictions. It is widely used 5.1.3. XHTML Mobile Profile Name: XHTML Mobile Profile Abbreviation: - Version: 1.1 Owner: W3C Alternatives: XHTML Status: Candidate Usage areas: Publishing mobile web content Link: http://www.w3.org/TR/xhtml11/ Description: XHTML Mobile Profile is used to present XHTML on devices with limited bandwidth and screen resolution Explanation for status: XHTML MP is useful for delivering content to mobile devices, but due to increasing bandwidth and processing power of mobile devices, it might not be necessary. Normal XHTML or HTML might be useable instead. 5.1.4. MPLS Name: MultiProtocol Label Switching Abbreviation: MPLS Version: Owner: IETF Alternatives: Status: Candidate Usage areas: Networking, connectivity, web Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 50 / 63 Link: http://tools.ietf.org/html/rfc3031 Description: MPLS is a way of routing data packages from the network in a more efficient way than normal. The increased efficiency is achieved by adding labels to the packets, making it easier to route the through the network. Explanation for status: MPLS is an open standard and can be used by anyone without licensing costs. It has advantages in multiple areas compared to similar standards like frame relay and ATM and is therefore becoming the preferred standard in this area. 5.1.5. Saudi Post National Address Profile Name: Saudi Post National Address Profile Abbreviation: SP NAF Version: Owner: Saudi Post Alternatives: Status: Candidate Usage areas: Link: Description: The way of representing an address, as specified by Saudi Post Explanation for status: Saudi Post is the governing body on address in Saudi Arabia, this way of representing an address can be used as the national address standard. 5.1.6. XML Encryption Name: XML Encryption Abbreviation: - Owner: W3C Alternatives: signature Version: XML Status: Candidate Usage areas: Security, encryption, xml Link: http://www.w3.org/TR/xmlenc-core/ Description: XML encryption is a W3C specification on how to encrypt XML data. W3C recommends that XML encryption and XML not be used at the same time, as that might make it easier to perform guessing attacks. Explanation for status: XML encryption is useful in web services, where the interaction is between multiple parties and not just client/server. It is also useful because it has the ability to encrypt only part of a message, something SSL/TLS cannot do. W3C recommends that XML encryption and XML signature not be used at the same time, as it might make it easier to perform guessing attacks. 5.1.7. XML Signature Name: XML signature Abbreviation: Owner: W3C Alternatives: encryption Version: XML Status: Candidate Usage areas: Security, encryption, xml Link: http://www.w3.org/TR/xmldsig-core/ Description: XML is the W3C standard for digital signatures in XML format Explanation for status: W3C recommends that XML encryption and XML signature not be used at the same time, as it might make it easier to perform guessing attacks. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 51 / 63 Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 52 / 63 5.2. Emerging Standards Standards and/or protocols coming through either the standardization process or are market driven and that bear watching by the YEFI team 5.2.1. Office Open XML Name: Office Open XML Abbreviation: OOXML Version: Owner: Microsoft Alternatives: RTF, ODF, PDF, .txt, binary formats Status: Emerging Usage areas: Office productivity Link: Description: Office Open XML is the format used in the new version of Microsoft 2007, Office 2007. It is XML-based. Explanation for status: Under pressure from the competition from OpenOffice, Microsoft has decided to have the formats in Office 07 standardized through the standardization body ECMA. Despite this, it is still uncertain if Microsoft really has relinquished control of the format or if it is still able to make its own proprietary extensions to the formats. Compared to the ODF specification, OOXML is very complicated, weighing in a more than 6000 pages, making it difficult for nonMicrosoft developers to use. OOXML is currently being evaluated by ISO as a standard. Its status will be decided later in 2007. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 53 / 63 5.3. Deprecated standards The following standards should no longer be used: 5.3.1. WML Name: Wireless Markup Language Abbreviation: WML Version: 1.3 Owner: - Alternatives: XHTML Status: Deprecated Usage areas: Publishing mobile web content Link: Description: WML is a markup language, designed to deliver content to devices that use WAP Explanation for status: Due to increases in bandwidth and processing power of mobile devices, WML (and WAP) is being phased out, giving way to XHTML and HTML 5.3.2. EPS Name: Encapsulated PostScript Abbreviation: EPS Version: - Owner: - Alternatives: PDF Status: Deprecated Usage areas: Graphics Link: http://partners.adobe.com/public/developer/tiff/index.html Description: EPS is a way to encapsulate PostScript data, to make it readable as an image format. The format is not platform-independent, but has different implementations for Mac and PC (EPSF and EPSI). Explanation for status: EPS is not recommended, due to its platform dependent specifications. Alternatives should be used where available 5.3.3. ISO/IEC 8859-1:1998 Name: - Abbreviation: ISO/IEC 8859-1:1998 Version: Owner: - Alternatives: Unicode Status: Deprecated Usage areas: Character encoding Link: Description: The standard way to encode characters in the Latin alphabet Explanation for status: This encoding is no longer under active development and has been replaced by Unicode encoding. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 54 / 63 5.3.4. ASCII Name: American Standard Code for Information Interchange Abbreviation: ASCII Version: Owner: Unicode Consortium Alternatives: UTF-8 Status: Deprecated UTF-16 and Usage areas: Character encoding Link: http://www.unicode.org/charts/PDF/U0000.pdf Description: ASCII is the original encoding for encoding content in English. Explanation for status: ASCII has not been updated since 1986, and has been replaced by Unicode and UTF-8. 5.3.5. WAP Name: Wireless Application Protocol Abbreviation: WAP Version: 2.0 Owner: Alternatives: XHTML Mobile profile Status: Deprecated Usage areas: Publishing mobile web content Link: Description: WAP is a standard for web access for wireless devices. It is designed to present content in a way that fits the limited screen resolution and bandwidth of wireless/portable devices. Explanation for status: The WAP protocol has never been especially successful, but is offered by a number of content providers. New solutions are expected to be in other formats, due to an increase of resolution and bandwidth in wireless/portable devices. 5.3.6. DES Name: Data Encryption Standard Abbreviation: DES Version: Owner: National Institute of Science and Technology Alternatives: AES Status: Deprecated Usage areas: Security, encryption Link: http://csrc.nist.gov/publications/fips/fips46-3/fips46-3.pdf Description: DES is an encryption algorithm, used to encrypt data. It was widely used in the 1970's and 1980's before being deemed insecure. Explanation for status: The DES encryption has been broken and is not recommended. Alternatives include the AES cipher. 5.3.7. RSS Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 55 / 63 Name: Really Simple Syndication / Rich Site Summary Abbreviation: RSS Version: 1.0/2.0 Owner: - Alternatives: Atom Status: Deprecated Usage areas: Content publishing Link: Description: RSS is an XML-based format, used publish and syndicate web content. It is developed in two different branches (1.x and 2.x). Explanation for status: The different branches of development of the RSS standard and the fact that a standards body does not undertake the development should be taken into consideration when choosing RSS. Version 2.0 had diverged from being an update of Version 1.0 causing some interoperability issues for systems. It is recommended that the Atom standard is used instead. 5.3.8. DTD Name: Document Type Definition Abbreviation: DTD Version: 1.0/2.0 Owner: W3C Alternatives: XSD Status: Deprecated Usage areas: XML Link: http://www.w3.org/TR/REC-xml/#dt-doctype Description: DTD is used to describe an XML schema via a set of declaration that conforms to particular markup syntax. Explanation for status: DTD faced many criticisms such as using none XML syntax and no support for newer XML features (i.e. Namespaces). 5.3.9. MPEG-1 Name: MPEG-1 Abbreviation: MPEG-1 Version: - Owner: ISO/IEC Alternatives: MPEG-4 Status: Deprecated Usage areas: Audio/Video Link: http://www.chiariglione.org/mpeg/standards/mpeg-1/mpeg-1.htm Description: Mpeg-1 is a set of audio/video compression standards. MPEG-1 video part is used by the Video CD (VCD format) and less commonly by DVD-Video format. MPEG-1 Audio layer 3 is the popular MP3 audio format. Explanation for status: MPEG-1 has been outdated by much advanced standards such as MPEG-2 and MPEG-4. 5.3.10. AVI Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 56 / 63 Name: Audio Video Interleave Abbreviation: AVI Version: - Owner: Microsoft Alternatives: MP4 Status: Deprecated Usage areas: Audio/Video Link: http://msdn2.microsoft.com/en-us/library/ms779631.aspx Description: AVI stands for Audio Video Interleave and is a container file format for audio and video content. While it does not define how the audio and video information itself is encoded, it defines how the video and the audio are saved next to each other. Explanation for status: AVI is considered by some to be an outdated container format. There is significant overhead when used with popular MPEG-4 codecs (Xvid and DivX, for example), increasing file size more than necessary. 5.3.11. Quicktime Name: Quicktime Abbreviation: MOV Version: - Owner: Apple Alternatives: MP4 Status: Deprecated Usage areas: Audio/Video Link: http://developer.apple.com/documentation/QuickTime/QTFF/index.html Description: QuickTime (.mov) file format functions as a multimedia container file capable of handling various formats of digital video, media clips, sound, text, animation, music, and several types of interactive panoramic images. Explanation for status: Quicktime is Apple’s proprietary format Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 57 / 63 6. Choosing Standards This section is provided as a discussion reader about the various standards setting bodies apparent in the ICT environment. 6.1. International Standards Bodies There are a number of reasons for proliferation of standards setting bodies or organizations for ICT; the main reason though has been the dissatisfaction by many vendors with slow, bureaucratic processes. The ICT environment is by nature, a fast moving environment with new protocols and products reaching the market each month. In comparison, developing international standards through a Standards Development Organization (e.g. ISO) often takes a 3-6 year timeframe. During the 1990s, ISO gained a reputation for being slow, bureaucratic, congested, and insensitive to feedback from both vendors and their customers. Attention then turned to the volunteer-based, open-process and non-profit Internet Engineering Task Force (IETF), which develops a number of the standards necessary for the Internet to function. When IETF also appeared too slow for some vendors, they began funding more focused, agile consortia like the W3C and OASIS. This gap between market driven need and the bureaucratic standards development process is a main reason for the emergence and differentiation of the new Standard Setting Organizations (SSO). There are now five (5) main groupings of ICT SSO’s: 1) trade associations, 2) Standards Developing Organizations (SDOs), 3) consortia, 4) alliances, and 5) the Open Source software movement. From a big picture perspective, the main players today for setting standards for ICT (and particularly web services) are: International Organization for Standardization (ISO) / International Electrotechnical Commission (IEC) Institute of Electrical and Electronics Engineers (IEEE) Internet Engineering Task Force (IETF) Organization for the Advancement of Structured Information Systems (OASIS) World Wide Web Consortium (W3C) Open Geospatial Consortium (OGC) Open Liberty Alliance Ecma International A good background paper on the history of the emerging complexity of the Standards Setting Organizations environment can be found at: http://www.ftc.gov/opp/intellect/020418cargill.pdf (Carl Cargill, Sun Microsystems, 27 March 2002). NOTE: the purpose of this paper is to explore the ICT standards environment in terms of intellectual property rights. It does not describe the emergence of each separate SSO. The table on the following page provides a brief synopsis for each of the main standards setting bodies and shows where each body focuses their attention: Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 58 / 63 SSO Year Focus Mission International Organization for Standardization (ISO) 1947 International Trade To be the leading value adding platform and partner for the production of global and market relevant International Standards covering products, services, good conformity assessment, management and organizational practices International Electro technical Commission (IEC) 1906 International Trade To be recognized as the leader in the development of globally accepted standards for products and services in the fields of electricity, electronics and associated technologies that are market relevant and in the best interests of the industry and the users of its products and services. Institute of Electrical Engineers (IEEE) 1963 Engineering The IEEE promotes the engineering process of creating, developing, integrating, sharing, and applying knowledge about electro and information technologies and sciences for the benefit of humanity and the profession. 1986 Internet connectivity To produce high quality, relevant technical and engineering documents that influence the way people design, use, and manage the Internet in such a way as to make the Internet work better. 1993 E-business To drive the development, convergence, and adoption of ebusiness standards. and Electronics Internet Engineering Task Force (IETF) Organization for the Advancement Structured Information Systems (OASIS) of E-commerce World Wide Web Consortium (W3C) 1994 Internet Open Geospatial Consortium (OGC) 1994 Geospatial Location Ecma International 1994 Software Languages To develop, in co-operation with the appropriate National, European and International organizations Standards and Technical Reports in order to facilitate and standardize the use of Information Communication Technology (ICT) and Consumer Electronics (CE). 2001 Federated Identity The Liberty Alliance is committed to creating technical standards that solve ECMA (1961) Open Liberty Alliance Version Error! Unknown document property name. To lead the World Wide Web to its full potential by developing protocols and guidelines that ensures long-term growth for the Web. and To serve as a global forum for the collaboration of developers and users of spatial data products and services, and to advance the development of international standards for geospatial interoperability. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 59 / 63 Management global identity management needs and can be easily implemented by the widest possible audience. Table 15: SSO list 6.2. Standards per International body The following tables provide a listing of 161 standards from 4 of the main SSO’s. This information is provided purely to show the richness of the standards environment – noting that this is the first version of the KSA Interoperability Framework (YEFI) and it only draws on a small subset of the following standards AT THIS POINT IN TIME. OpenGIS® Specifications 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 Catalogue Service Coordinate Transformation Filter Encoding Geographic Objects Geography Markup Language GML in JPEG 2000 Grid Coverage Service Location Services (OpenLS) Simple Feature Access 1 Simple Feature Access 2 Simple Features CORBA Simple Features OLE/COM Styled Layer Descriptor Symbology Encoding Web Coverage Service Web Feature Service Web Map Context Web Map Service Web Service Common Ecma International standards 1 2 3 4 5 6 7 8 C# Language Specification C++/CLI Language Specification Common Language Infrastructure (CLI) ECMAScript Language Specification Eiffel: Analysis, design and programming Language Environmental design considerations for electronic products Universal 3D File Format Microsoft Office Open XML Table 16: OpenGIS & Ecma standards W3C Standards OASIS Standards 1 2 3 4 Architecture of the World Wide Web, Volume One Associating Style Sheets with XML documents Authoring Tool Accessibility Guidelines 1.0 Canonical XML Version 1.0 1 2 3 4 Directory Services Markup Language (DSML) v2.0 DocBook v4.1 DocBook v4.5 ebXML Business Process Specification Schema Technical Specification v2.0.4 5 Cascading Style Sheets (CSS1) Level 1 Specification 5 6 7 Cascading Style Sheets, level 2 (CSS2) Specification Character Model for the World Wide Web 1.0: Fundamentals Composite Capability/Preference Profiles (CC/PP): Structure and Vocabularies 1.0 6 7 ebXML Collaborative Partner Profile Agreement (CPPA) v2 ebXML Message Service Specification v2.0 ebXML Registry Information Model (RIM) v2.0 8 ebXML Registry Information Model (RIM) v3.0 Decryption Transform for XML Signature Document Object Model (DOM) Level 1 Document Object Model (DOM) Level 2 Core Specification Document Object Model (DOM) Level 2 Events Specification 9 10 11 ebXML Registry Services Specification (RS) v2.0 ebXML Registry Services Specification (RS) v3.0 Extensible Access Control Markup Language (XACML) v1.0 eXtensible Access Control Markup Language (XACML) v2.0 Version Error! Unknown document property name. Confidential e-Government Program (YESSER) 8 9 10 11 12 12 This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 60 / 63 13 Document Object Model (DOM) Level 2 HTML Specification Document Object Model (DOM) Level 2 Style Specification Document Object Model (DOM) Level 2 Traversal and Range Specification 13 16 Security Assertion Markup Language (SAML) v1.0 17 Security Assertion Markup Language (SAML) v1.1 18 Security Assertion Markup Language (SAML) V2.0 19 Universal Business Language (UBL) v1.0 20 21 23 Document Object Model (DOM) Level 2 Views Specification Document Object Model (DOM) Level 3 Core Specification Document Object Model (DOM) Level 3 Load and Save Specification Document Object Model (DOM) Level 3 Validation Specification Exclusive XML Canonicalization Version 1.0 Extensible Markup Language (XML) 1.0 (Fourth Edition) Extensible Markup Language (XML) 1.1 (Second Edition) Extensible Stylesheet Language (XSL) Version 1.0 24 25 Extensible Stylesheet Language (XSL) Version 1.1 HTML 3.2 Reference Specification 24 25 Universal Business Language (UBL) v2.0 Universal Business Language Naming & Design Rules (UBL NDR) v1.0 Universal Description, Discovery and Integration (UDDI) v2.0 Universal Description, Discovery and Integration (UDDI) v3.0.2 Web Services for Remote Portlets (WSRP) v1.0 Web Services Security SAML Token Profile v 1.0 and REL Token Profile v1.0 26 27 28 HTML 4.01 Specification Internationalization Tag Set (ITS) Version 1.0 Mathematical Markup Language (MathML) 1.01 Specification Mathematical Markup Language (MathML) Version 2.0 (Second Edition) 26 27 28 Web Services Security v1.0 (WS-Security 2004) Web Services Security v1.1 WS-Reliability (WS-R) v1.1 29 WS-Trust v1.3 14 15 16 17 18 19 20 21 22 29 14 15 22 23 OpenDocument Format for Office Applications (OpenDocument) v1.0 OpenDocument Format for Office Applications (OpenDocument) v1.1 Reference Model for Service Oriented Architecture v1.0 Table 17: W3C & OASIS standards W3C Standards 30 31 32 33 34 35 36 37 38 39 Mobile SVG Profiles: SVG Tiny and SVG Basic Namespaces in XML 1.0 (Second Edition) Namespaces in XML 1.1 (Second Edition) OWL Web Ontology Language Guide OWL Web Ontology Language Overview OWL Web Ontology Language Reference OWL Web Ontology Language Semantics and Abstract Syntax OWL Web Ontology Language Test Cases OWL Web Ontology Language Use Cases and Requirements PICS 1.1 Label Distribution -- Label Syntax and Communication Protocols 40 PICS 1.1 Rating Services and Rating Systems -- and Their Machine Readable Descriptions 41 42 43 44 45 46 47 48 49 50 51 PICS Signed Labels (DSig) 1.0 Specification PICSRules 1.1 Specification Portable Network Graphics (PNG) Specification (Second Edition) QA Framework: Specification Guidelines RDF Primer RDF Semantics RDF Test Cases RDF Vocabulary Description Language 1.0: RDF Schema RDF/XML Syntax Specification (Revised) Resource Description Framework (RDF): Concepts and Abstract Syntax Resource Representation SOAP Header Block Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 61 / 63 52 53 54 55 56 Ruby Annotation Scalable Vector Graphics (SVG) 1.1 Specification Semantic Interpretation for Speech Recognition (SISR) Version 1.0 SMIL Animation SOAP Message Transmission Optimization Mechanism W3C Standards 57 58 59 60 SOAP Version 1.2 Part 0: Primer (Second Edition) SOAP Version 1.2 Part 1: Messaging Framework (Second Edition) SOAP Version 1.2 Part 2: Adjuncts (Second Edition) SOAP Version 1.2 Specification Assertions and Test Collection (Second Edition) 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 Speech Recognition Grammar Specification Version 1.0 Speech Synthesis Markup Language (SSML) Version 1.0 Synchronized Multimedia Integration Language (SMIL 2.1) Synchronized Multimedia Integration Language (SMIL) 1.0 Specification The Platform for Privacy Preferences 1.0 (P3P1.0) Specification User Agent Accessibility Guidelines 1.0 Voice Extensible Markup Language (VoiceXML) Version 2.0 Web Content Accessibility Guidelines 1.0 Web Services Addressing 1.0 - Core Web Services Addressing 1.0 - SOAP Binding WebCGM 1.0 Second Release WebCGM 2.0 XForms 1.0 (Second Edition) XHTML-Print XHTML™ 1.0 The Extensible HyperText Markup Language (Second Edition) 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 XHTML™ 1.1 - Module-based XHTML XHTML™ Basic XML Base XML Encryption Syntax and Processing XML Events XML Inclusions (XInclude) Version 1.0 (Second Edition) XML Information Set (Second Edition) XML Key Management Specification (XKMS 2.0) XML Key Management Specification (XKMS 2.0) Bindings XML Linking Language (XLink) Version 1.0 XML Path Language (XPath) 2.0 XML Path Language (XPath) Version 1.0 XML Schema Part 0: Primer Second Edition XML Schema Part 1: Structures Second Edition XML Schema Part 2: Datatypes Second Edition XML Syntax for XQuery 1.0 (XQueryX) xml:id Version 1.0 XML-binary Optimized Packaging XML-Signature Syntax and Processing XML-Signature XPath Filter 2.0 XPointer element() Scheme XPointer Framework XPointer xmlns() Scheme XQuery 1.0 and XPath 2.0 Data Model (XDM) XQuery 1.0 and XPath 2.0 Formal Semantics XQuery 1.0 and XPath 2.0 Functions and Operators XQuery 1.0: An XML Query Language XSL Transformations (XSLT) Version 1.0 XSL Transformations (XSLT) Version 2.0 Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 62 / 63 105 XSLT 2.0 and XQuery 1.0 Serialization Table 18: W3C standards Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER) e-Government Program (Yesser) Version 1.1 - Page 63 / 63 7. 7.1. Acknowledgements Copyright Notices The YEFI team acknowledges the current document is based on the work published through a number of leading international efforts. In particular, the YEFI has drawn on material from the following documents and acknowledges the rights of these publishers: United Kingdom Interoperability Framework United Kingdom GovTalk New Zealand e-Government Interoperability Framework Danish Interoperability Framework Western Australia E-government Interoperability Framework Ireland REACH Program Malaysian e-Government Initiative In the interests of international cooperation, the Kingdom of Saudi Arabia allows all parties to use the materials in this document so long as reference is acknowledged and published. Version Error! Unknown document property name. Confidential e-Government Program (YESSER) This document (either in whole or in part) cannot be modified or reproduced without the prior written permission of the e-Government Program (YESSER)