D
M
O
H
T
A
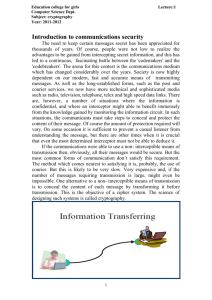
Secret Writing Meeting
(The Art of Cryptology)
Provided by the National Defense Education Program
M
D
A
T
O
H
Topic
The history of cryptology (the complete science of secure communications, including both cryptography
and cryptanalysis) is given and explained in the context of mathematics.
Materials Needed
♦♦ Pairs of rods, of various diameters, that are approximately 10 to 12 inches long (Materials such as PVC
pipe, wooden dowels, broom handles or paper towel rolls can be used. Though the two rods of each
pair must have the same diameter, try to vary the diameters of the different pairs between 0.75 and 2 inches.)
♦♦ Narrow paper strips (one per student) that are 2 to 3 feet long and no more than 0.5 inches wide
♦♦ Copies of The Art of Secret Writing available for download from www.mathcounts.org on the MCP
Members Only page of the Club Program section (Selections from this downloadable history are
provided below.)
♦♦ Pen/pencil
♦♦ Clear tape (optional)
Meeting Plan
Before beginning the hands-on activities with your students, they should be given The Art of Secret Writing
to read (available on mathcounts.org). The necessary vocabulary such as cryptology, cryptography,
cryptanalysis, encryption and decryption is thoroughly explained, and examples of three different encryption techniques (transposition, substitution and modular arithmetic) are given. Students then can
utilize two of these techniques in the activities that follow. Below are selections from The Art of Secret
Writing.
The Art of Secret Writing
Since people first learned to communicate, there has been a need to protect secrets. In early times information that
needed to be kept secret was transmitted by word of mouth only to those who had a need to know. Messengers were
used to secretly transfer information between individuals or groups to protect military information and diplomatic and
trade secrets or to set up clandestine (secret) meetings. As people learned to communicate in a written form, it became
important to find a mechanism to protect the written word in case the message fell into the wrong hands.
Cryptology is the complete science of secure communications and has two parts. The first is cryptography.
Cryptography is the process of writing a message in such a way as to keep the information secret. Cryptographic
methods are also called ciphers. The opposite of cryptography is cryptanalysis. Cryptanalysis is the science of
attacking cryptographic systems to find a weakness that can be used to “crack” a code and reveal the message or to
prove that a specific cryptographic system is secure.
...
Transposition. Transposition ciphers simply rearrange the order of the letters in a message, based on an agreed-upon
pattern (the shared secret). A simple example of a transposition cipher would be to break the message down into pairs
of letters and reverse the letters. Let’s work with the plaintext message, “MEET ME AT LUNCHTIME WE NEED TO
TALK.” Break it down into pairs of letters: ME│ET│ME│AT│LU│NC│HT│IM│EW│EN│EE│DT│OT│AL│K. Reversing
the letters within each pair and keeping the number of letters necessary per word, the plaintext message becomes the
ciphertext message “EMTE EM TA ULCNTHMIW EN EEET DT OLAK.”
...
Substitution. Substitution ciphers replace each letter in a message (plaintext) with a different letter, based on an
agreed-upon pattern to create the ciphertext. The pattern can be a simple shift of the alphabet to the right or left, a
2010–2011 MATHCOUNTS Club Resource Guide
23
...
random assignment of values (A=T, B=O, C=Y, etc.), or the use of math operations (addition or subtraction) to combine
a word, phrase or number sequence with the plaintext.
Modular Arithmetic. Encryption and decryption processes often use modular arithmetic to allow for more complex
methods. So what’s modular arithmetic? Modular arithmetic, sometimes called clock arithmetic, is where the numbers
“wrap around” after they reach a certain value called the modulus. When working with our alphabet, the modulus is
26 for the twenty-six letters in the alphabet. Modular arithmetic was introduced by Carl Friedrich Gauss in his book
Disquisitiones Arithmeticae, published in 1801.
...
Before the modern era of computers, cryptography was concerned solely with message confidentiality, or ensuring that
only the intended recipients of the information would be able to read it. With the advent of high speed computers, the
field of cryptography has created more powerful and secure means of encrypting information. It has also expanded
beyond confidentiality (keeping information secret) to include techniques for message integrity checking (Did anyone
change my message while it was being transmitted?), sender/receiver identity authentication (Is it really who I think it
is or is someone pretending to be my friend?), digital signatures (a process that proves you were the only person who
could have approved/signed a computer transaction) and others.
Once students have read about and discussed the exciting field of cryptology, they are ready for the
following hands-on activities!
The Scytale
The Scytale (rhymes with Italy) was developed by the Greeks to send secret messages and is one of the
oldest systems on record. This transposition cipher is unique in that the key (shared secret) is a physical
object (a rod of a specific diameter). The message is created by wrapping a narrow strip of paper around
the rod. The message is then written along the length of the rod, being careful to write only one letter
on each layer of the paper. When the message is completed, unwrap the paper and you have a secret
message that can be decoded only if you have the correct diameter rod.
Here’s a picture of a scytale showing how the message ATTACK
TOMORROW can be written and read using this specific-sized rod.
A T T A C K
T O M O R RO W
W
O
R
K
R
C
O
A
M
T
O
T
T
A
When unwound, the strip of paper looks like this:
Activity: Have the students pair up. Each pair of students should be given their “keys” (or two rods of
the same diameter or extremely similar diameters). Each partner receives one rod, assembles his or her
scytale (wrapping the paper around the rod) and writes a simple question. Do not let the partners observe
each other’s messages being written. When the messages are complete, the partners will then unwind their
messages and swap messages with each other. Each partner will rewind the message on his or her scytale
and then write the answer to the question. Finally, each partner will give the question and answer to the
original student to see if the whole process worked.
When everyone has had a chance to create and respond to a message, place all of the messages in a
container. Have student pairs randomly draw messages out of the container and see if they can decrypt
the messages by using their scytales.
After the activity, lead a student discussion on the strengths and weaknesses of this approach.
24 2010–2011 MATHCOUNTS Club Resource Guide
The Caesar Cipher
The Caesar cipher was named after Julius Caesar. He developed it to send secret messages to his military
commanders. The Caesar cipher is a very simple substitution cipher. For encrypting the message, each
letter is shifted or rotated three places to the right. A becomes D, B becomes E, and so on. So, you may
ask, “Why was this considered secure since it is a simple three-place rotation called ROT 3?” Most people
were illiterate at the time, including most people in the military. Only the officers were educated. Also, the
messages were time sensitive. Even if the enemy did figure it out, chances were, by the time they could
read the real message, it was too late to do anything about it.
Here is an example:
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V W X
V W X
Y
Z
Y
B
C
Z
A
ATTACK AT DAWN becomes DWWDFN DW GDZQ.
Activity: Form student pairs. Have each of the students create a short message and encrypt it using
the Caesar cipher. Then have the partners swap messages with each other and decrypt each other’s
messages. Each partner then thinks of a response to the message, encrypts the plaintext, and passes only
the ciphertext back to his or her partner who should decrypt the message.
Once students are comfortable with the Caesar cipher (ROT 3), have each pair of students secretly select
a different rotation scheme. For example, they could choose to shift 5 characters to the left or 10 characters
to the right. The shift is the shared secret. Each student can now encrypt a message with his or her new
shared secret cipher, swap messages with his or her partner and decrypt the partner’s message.
Possible Next Steps
Ask each student to write a short paragraph (plaintext) to encrypt. (The paragraph should be only two to
five sentences.) Using either a combination of the methods described here or one of his or her own, each
student should develop his or her own encryption key and encrypt the paragraph. Students then must write
out an explanation of their encryption keys. Once each student is finished (this could be done at home
and shared during the next club meeting), students will then swap work so that each student receives the
encryption key and ciphertext of another student and tries to decrypt the message. Students with the most
original and accurate encryption keys and encryptions could receive prizes!
National Defense Education Program
Pre-Engineering Programs
www.ndep.us/ProgPEP.aspx
2010–2011 MATHCOUNTS Club Resource Guide
25
The Art of Secret Writing
Since people first learned to communicate, there has been a need to protect secrets. In early
times information that needed to be kept secret was transmitted by word of mouth only to those
who had a need to know. Messengers were used to secretly transfer information between individuals or groups to protect military information and diplomatic and trade secrets or to set up
clandestine (secret) meetings. As people learned to communicate in a written form, it became
important to find a mechanism to protect the written word in case the message fell into the
wrong hands.
Cryptology is the complete science of secure communications and has two parts. The first is
cryptography. Cryptography is the process of writing a message in such a way as to keep the
information secret. Cryptographic methods are also called ciphers. The opposite of cryptography is cryptanalysis. Cryptanalysis is the science of attacking cryptographic systems to find a
weakness that can be used to “crack” a code and reveal the message or to prove that a specific
cryptographic system is secure.
Cryptography, derived from the Greek words krypto (hidden or secret) and grapho (I write),
is the study and practice of hiding information. An example of cryptography is the process of
encryption. Encryption is the process of converting messages from a comprehensible or readable form (cryptoanalysts call this plaintext) into incomprehensible gibberish (cryptoanalysts
call this ciphertext) based on a shared secret. The shared secret is called an encryption key.
To encrypt information, you must have an agreed upon method or algorithm. These algorithms
are usually made public so they can be tested to insure they are secure. However, the shared
secret or key is only known to the people transferring the information. The encryption process
can then be reversed using the shared secret to return the ciphertext (gibberish) to plaintext (the
original message) without errors. This reverse process is called decryption.
Encryption techniques usually rely on three mathematical operations. Transposition (changing
the order), substitution (one value replaced with another, e.g. A=T, B=O, C=Y, etc. or two values
added together to form a third) and modular arithmetic.
Transposition. Transposition ciphers simply rearrange the order of the letters in a message,
based on an agreed-upon pattern (the shared secret). A simple example of a transposition
cipher would be to break the message down into pairs of letters and reverse the letters. Let’s
work with the plaintext message, “MEET ME AT LUNCHTIME WE NEED TO TALK.” Break it
down into pairs of letters: ME│ET│ME│AT│LU│NC│HT│IM│EW│EN│EE│DT│OT│AL│K. Reversing the letters within each pair and keeping the number of letters necessary per word, the
plaintext message becomes the ciphertext message “EMTE EM TA ULCNTHMIW EN EEET DT
OLAK.”
Substitution. Substitution ciphers replace each letter in a message (plaintext) with a different
letter, based on an agreed-upon pattern to create the ciphertext. The pattern can be a simple
shift of the alphabet to the right or left, a random assignment of values (A=T, B=O, C=Y, etc.),
or the use of math operations (addition or subtraction) to combine a word, phrase or number
sequence with the plaintext.
© 2010 MATHCOUNTS Foundation. All rights reserved. MATHCOUNTS Club Resource Guide
One of the simplest substitution ciphers was invented by Julius Caesar to communicate with
his commanders. Caesar’s cipher or shift cipher is one of the simplest and most widely known
encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is
replaced by a letter some fixed number of positions down the alphabet. For Caesar, the shift
was always 3 to the right. In other words, A would be replaced by D, B would become E, and so
on. The number of places to shift and the direction of the shift becomes the shared secret. Using the previous transposition example, the plaintext “MEET ME AT LUNCHTIME WE NEED TO
TALK” becomes the ciphertext “PHHW PH DW OXQFKWLPH ZH QHHG WR WDON”. But what
happens if the shift requires a letter beyond Z? What do you do? In this case, you wrap around
to the beginning where X = A, Y = B and Z = C. What happens when you are decrypting and
you have to shift A, B or C back three places? You use the same approach, but in the opposite
direction, and A becomes X, B becomes Y and C becomes Z. This wrapping around technique is
called modular arithmetic.
Modular Arithmetic. Encryption and decryption processes often use modular arithmetic to allow for more complex methods. So what’s modular arithmetic? Modular arithmetic, sometimes
called clock arithmetic, is where the numbers “wrap around” after they reach a certain value
called the modulus. When working with our alphabet, the modulus is 26 for the twenty-six letters
in the alphabet. Modular arithmetic was introduced by Carl Friedrich Gauss in his book Disquisitiones Arithmeticae, published in 1801.
We have discussed the simple shift example where shifting the letters to the right extends beyond Z, and you wrap around like the hands of a clock going past 12. However, there are different definitions for the modulo operation. In our example using the alphabet, our result must be in
the range 0-25 to be a valid letter. Therefore, if the result is greater than 25, you subtract 26 to
get it back in the range of 0-25. If the result is less than zero (a negative number) you add 26.
This technique also can be used when the result may be a very large number. For example, if
your modulus is 26 and result is 64, how do you find the answer? You divide the result by the
modulus and remainder is your answer. In this example, 64 divided 26 equals 2 with a remainder of 12 or 64 = 26 + 26 + 12. Using math notation, 64 mod 26 ≡ 12.
But what if we use an encryption method where we have to add or subtract two letters together?
What? Why would you ever want to add or subtract letters you ask? More sophisticated ciphers,
like the Vigenere Cipher, use a word or phrase (the shared secret) as the key. To create the
secret message (cipher text), you add the letters of the message (plaintext) to the letters in the
key (shared secret) to create the ciphertext. To decrypt the ciphertext, you have to reverse the
process and subtract the letters in the key from the ciphertext to get back to plaintext.
With the advent of modern computers, addition and subtraction have been replaced with a
mathematical operator called the eXclusive OR (XOR). The XOR rules are very simple and
there are only two to remember. If the two values being XORed are the same (equal) the XOR
value is zero (0). If the values are NOT equal, the XOR value is one (1).
(1) 0 XOR 0 = 0
(2) 0 XOR 1 = 1
(3) 1 XOR 0 = 1
(4) 1 XOR 1 = 0
© 2010 MATHCOUNTS Foundation. All rights reserved. MATHCOUNTS Club Resource Guide
Computers only understand 1s and 0s, so all of their information is expressed as strings of 1s
and 0s. Letters of the alphabet can be expressed in this format using the American Standard
Code for Information Interchange (ASCII). By converting the plaintext message and the key to
strings of binary numbers, their values can be XORed together to create the ciphertext. Here is
a quick example:
ENCRYPTION
Plaintext:
Key:
XOR Result (Ciphertext):
10011011
11101001
01110010
00110101
01001001
01111100
DECRYPTION
Ciphertext:
Key:
XOR Result (Plaintext):
01110010
11101001 10011011 01111100
01001001
00110101
Modern encryption algorithms use both substitution (XORing binary numbers together to create
a third value) and transposition (rearranging the 1s and 0s using a specific pattern) many, many
times to create ciphertext. The methods and algorithms are actually published so people can
examine them and look for weaknesses. The strength lies in the length of the key, how well the
algorithm scrambles the message, and keeping the key secret.
Before the modern era of computers, cryptography was concerned solely with message confidentiality, or ensuring that only the intended recipients of the information would be able to read
it. With the advent of high speed computers, the field of cryptography has created more powerful and secure means of encrypting information. It has also expanded beyond confidentiality
(keeping information secret) to include techniques for message integrity checking (Did anyone
change my message while it was being transmitted?), sender/receiver identity authentication (Is
it really who I think it is or is someone pretending to be my friend?), digital signatures (a process
that proves you were the only person who could have approved/signed a computer transaction)
and others.
National Defense Education Program
Pre-Engineering Programs
www.ndep.us/ProgPEP.aspx
© 2010 MATHCOUNTS Foundation. All rights reserved. MATHCOUNTS Club Resource Guide
The Art of Secret Writing Activity Supplement
I. The Scytale
The Scytale (rhymes with Italy) was developed by the Greeks to send secret messages and is
one of the oldest systems on record. This transposition cipher is unique in that the key (shared
secret) is a physical object (a rod of a specific diameter). The message is created by wrapping
a narrow strip of paper around the rod. The message is then written along the length of the
rod, being careful to write only one letter on each layer of the paper. When the message is
completed, unwrap the paper and you have a secret message that can be decoded only if you
have the correct diameter rod.
Here’s a picture of a scytale showing how the message ATTACK TOMORROW can be written
and read using this specific-sized rod.
A T T A C K
T O M O R RO W
W
O
R
K
R
C
O
A
M
T
O
T
T
A
When unwound, the strip of paper looks like this:
II. The Caesar Cipher
The Caesar cipher was named after Julius Caesar. He developed it to send secret messages to
his military commanders. The Caesar cipher is a very simple substitution cipher. For encrypting
the message, each letter is shifted or rotated three places to the right. A becomes D, B
becomes E, and so on. So, you may ask, “Why was this considered secure since it is a simple
three-place rotation called ROT 3?” Most people were illiterate at the time, including most
people in the military. Only the officers were educated. Also, the messages were time sensitive.
Even if the enemy did figure it out, chances were, by the time they could read the real message,
it was too late to do anything about it.
Here is an example:
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V W X
T
U
V W X
Y
Z
Y
B
C
Z
ATTACK AT DAWN becomes DWWDFN DW GDZQ.
National Defense Education Program
Pre-Engineering Programs
www.ndep.us/ProgPEP.aspx
© 2010 MATHCOUNTS Foundation. All rights reserved. MATHCOUNTS Club Resource Guide
A