BlackHole Exploit Kit, Banking Trojans and ACH
advertisement

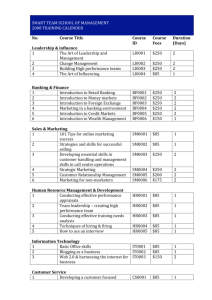
SERT Awareness Report BlackHole Exploit Kit, Banking Trojans and ACH Transfers Table of Contents INTRODUCTION 3 EXPLOIT KITS AND BANKING TROJANS 3 BlackHole Exploit Kit 3 Banking Trojans 4 RECOMMENDATIONS 5 APPENDIX 6 Domains 6 Keywords 10 2 Introduction The Solutionary Security Engineering Research Team (SERT) prepared this report to provide awareness and additional details about the use of exploit kits and banking Trojans to gather information that is used to perform fraudulent Automated Clearing House (ACH) transactions. The report also provides a brief description of how Distributed Denial of Service (DDoS) attacks are used to hide transactions or prevent the stoppage of transactions. SERT has also provided some common recommendations for identifying and possibly preventing malicious attackers from deploying the first stages of attacks as well as preventative measures that can be taken to prevent or reduce the effects of DDoS attacks. Exploit Kits and Banking Trojans BlackHole Exploit Kit While there are numerous exploit kits available and they all functionally work the same way, BlackHole Exploit Kit has been the most popular exploit kit among cybercriminals since 2011. BlackHole is a web application that ® allows an attacker to take advantage of the most known vulnerabilities in popular applications such as Adobe ® ® Reader , Adobe Flash and Java™. Its first version, v.1.0.0, was released in 2010. Version 1.2.3 was released on March 25, 2012. While there were no significant version changes, there were several updates to v.1.2.3 to add additional exploits. The most recent update to the exploit kit came with BlackHole Exploit Kit v2.0, which was released on September 12, 2012. This version marked a significant upgrade to the exploit kit. The majority of the changes were done to prevent research efforts by anti-virus vendors and other security researchers. BlackHole leverages vulnerabilities across a wide range of software to exploit victim hosts. Exploitation of these vulnerabilities leads to infection of an equally wide range of malware. These infections have often resulted in the theft of victims' financial information. BlackHole uses a couple of techniques to direct victims to the exploit site— compromised web pages and spam messages. Often, combinations of the two techniques are also used. The compromised web pages are typically injected with malicious JavaScript™. The injected scripts are normally heavily obfuscated, and use a variety of techniques to evade detection. Most commonly, criminals lure victims to BlackHole Exploit Kit landing pages using of phishing emails. The following list contains some of the more common tactics used to lure victims: • • • • • • • ® ® UPS or FedEx delivery confirmation Scanned documents Flight tickets Amazon order tracking Credit card issues Better Business Bureau (BBB) complaints ACH wire transfer problems The phishing email message typically contains a link to a compromised web page or contains an HTML attachment with the same obfuscated code. The webpage will typically contain an iframe in the HTML code that directs the victim to the BlackHole Exploit Kit landing page. The landing page will capture a parameter included in the URL, fingerprint the victim machine and load the files that target the exploits relevant to fingerprint of the victim’s machine. The landing page will load one or more exploits specifically targeting the victim’s browser and version. The vulnerabilities are targeted based on the potential vulnerabilities that may be present. BlackHole attempts to exploit the victim based on the fingerprint of the machine and install malicious software payloads such as ZeuS, Gameover ZeuS, SpyEye, Cridex, ZeroAccess or any other variant of banking Trojans. 3 Banking Trojans Banking Trojans are typical payloads of exploit kits deployed in the wild. The banking Trojan is effectively what is known as a Trojan (Trojan horse). A Trojan is type of malware that masquerades as a legitimate file or helpful program possibly with the purpose of granting the attacker unauthorized access to a computer. In the case of a banking Trojan, the purpose is to harvest banking information from the victim to initiate fraudulent transactions on the victims’ behalf. For the purpose of this report, the Cridex banking Trojan was used to illustrate how banking Trojans are used in fraudulent transactions. Cridex is just one of the many payloads associated with BlackHole Exploit Kit and other exploit kits available. Once the Cridex malware is dropped onto the victim machine, it executes a copy of itself and injects itself into running processes. From here, the malware deletes the initially executed copy and then tries to connect to a command-and-control (C&C) server. Once the malware finds and successfully connects to a live C&C server, it downloads a customized configuration file that is then saved as a registry entry. As with many of the other banking Trojans, Cridex monitors Internet traffic between remote servers and the victim’s web browser, capturing the credentials entered in certain sites. Banking Trojans are also known to target social media credentials such as those used for Facebook and Twitter. The configuration data associated with the malware contain the sites targeted by the banking Trojans. The malware variant determines how the data is stored on the local system. Cridex, for example, contains a list of targeted websites stored in the affected computer's registry. The configuration information in the registry not only contains domains for the malware to watch for but specific “keywords” related to online banking to watch for as well. There is also complete webpage HTML code to mimic banking sites for the purpose of harvesting banking credentials by manipulating the way the page is displayed to the victim, a technique known as “web injects”. The registry key that has been observed is similar to the following: HKCU\Software\Microsoft\WSH\4F923C43 The key is different on each computer that the malware infects. A complete list of the domains and the keywords parsed from the registry key is included in the Appendix. Once the Trojan is in place, the malware logs keystrokes for login information related to bank accounts listed in the configuration data. Criminals use this information to login and make purchases or transfer funds out of larger accounts through ACH transfers. The criminals also use social engineering techniques to gather additional authorization credentials or even social engineer the release of the fraudulent transaction. Many larger schemes use “money mules” to either knowingly or unknowingly move funds on the behalf of the criminals to move the funds to their overseas accounts. A common trend has been to use a Distributed Denial of Service (DDoS) attack in conjunction with fraudulent ACH transfers. Upon execution of the money transfer, a DDoS attack is launched from multiple points around the globe to prevent legitimate customers from logging on to the banking system and observing the transfer, as well as distracting the financial institution from recognizing the fraud. 4 Recommendations SERT makes the following recommendations related to the initial phishing emails that often lead to the installation of malicious banking Trojans on the victims systems: • Don't respond to suspicious e-mails. • Don't click links in suspicious e-mails. • Delete suspicious e-mails and move on. • Don’t give authorization information over the phone. • Use strong credentials and change them frequently, especially when compromise of credentials is suspected. • Provide frequent (at least annual) security awareness training for an employee that includes phishing and social engineering techniques. Detection is really the key with ACH transaction fraud. System monitoring is a critical component in the detection of fraudulent activity. Solutionary makes the following recommendations to aid in the detection and prevention of DDoS attacks associated with fraudulent ACH transactions: • Understand ISP Options for DoS/DDoS Defense. • Implement appropriate blocking/shunning rules on the IDS/IPS and firewall to address volume-based and packet-based DoS/DDoS attacks. • Limit traffic by implementing access control lists on border routers. • Limit Internet-facing services and protocols. • Harden configuration settings for firewalls and routers. • Deploy purpose-built DDoS and web application protection solutions. • Monitor and retain device logs pertaining to ACH transactions and the security systems protecting them. Recommendations for the banking customer base to prevent fraudulent ACH transactions include: • Process improvements such as daily review of the credits and debits by the business can be essential in detecting fraudulent activity. • Encouraging businesses to invest in additional services such as: ACH debit blocks, ACH debit filters or similar services. 5 Appendix Domains The following is a list of domains that have been identified by parsing the configuration information in the registry key data of Cridex banking Trojan malware. 6 ablv.com bizcurrency.com acbtz.com blilk.com access.jpmorgan.com bmoharrisprivatebankingonline.com access.rbsm.com bmomutualfunds.com access.usbank.com bnycash.bankofny.com accessbankplc.com bob.sovereignbank.com account.authorize.net bobibanking.com achieveaccess.citizensbank.com bolb-east.associatedbank.com achworks.com bolb-west.associatedbank.com alphabank.com.cy boveda.banamex.com.mx ameritrade.com bscincky.com anb.portalvault.com business-eb.ibanking-services.com associatedbank.com business.macu.com auth.umb.com business.netbankerplus.com authmaster.nationalcity.com businessaccess.citibank.citigroup.com azaniabank.co.tz businessbanking.cibc.com baltikums.com businessclassonline.compassbank.com baltikums.eu businesslogins.asp banesco.com.pa businessmanager.com bankaustria.at businessonline.huntington.com banking.calbanktrust.com businessonline.tdbank.com banking.firsttennessee.biz businessportal.mibank.com bankm.co.tz butterfieldonline.ky banknet.lv bxs.com bankofamerica.com cashanalyzer.com bankofbermuda.com cashman.arvest.com bankofcyprus.com cashmanager.mizuhoe-treasurer.com bankonline.sboff.com cashproonline.bankofamerica.com bankonline.umpquabank.com cbbusinessonline.com bbo.1stsource.com cbs.firstcitizens.com bib.lv cencorpcu.com billmelater.com cfgbusinessaccess.com 7 chase.com etrade.com chaseonline.chase.com eurobankefg.com checkgateway eurobankefg.com.cy cib.bankofthewest.com exness.com cibconline.cibc.com express.53.com cimbanque.net fbmedirect.com cm.netteller.com ffinonline.com cmol.bbt.com firstbanks.com comerica.com fnfgbusinessonline.enterprisebanker.com commercebusinessdirect.com geonline.lv commercial.wachovia.com global-ebanking.com commercialservices.mandtbank.com global1.onlinebank.com constitutioncorp.org globalink.leumiusa.com corporate.epfc.com handelsbanken.lv corporatebankingweb hblibank.com cs.directnet.com hellenicnetbanking.com cu.com hillsbank.com cu.org hiponet.lv danskebanka.lv hsbc.co.uk directline4biz.com hsbc.com.mx directnet.com i-linija.lt dtbafrica.com ib.baltikums.com e-moneyger.com ib.dnb.lv e-norvik.lv ib.snoras.com easywebcpo.td.com ibanka.seb.lv ebank.laiki.com ibanking-services.com ebank.rcbcy.com ibbpowerlink.com ebanking-services.com ibbusinessnet.com ebemo.bemobank.com ibs.secure-banking ebill.highmark.com ibs5.secure-banking ecash.fsbnm.com ifxmanager.bankofny.com ecash.mbvtonline.com ifxmanager.bnymellon.com efirstbank.com internet-ebanking.com ekp.lv internetbanker.cc enternetbank.com itinternet.net enterprise2.openbank.com itreasury.amsouth.com epd.uscentral.org ktt.key.com 8 lakecitybank.webcashmgmt.com online.dollarbank.com lakelandbank.com online.ibl.com.lb lasallebank.com online.lkb.lv libertymutualbusinessdirect.com online.ovcb.com lionbank.com online.usb.com.cy login_business.asp online.wilberbank.com loyalbank.com onlineaccess1.com lv.unicreditbanking.net onlinebank.wesbanco.com marfinbank.com.cy onlinebanker.usbank.com mbachexpress.com onlinebanking.banksterling.com mcb-home.com onlinebanking.tdbank.com merchantsbk.inetbanker.com onlinencr.com metrobankdirect.com onlineserv midatlanticcorp.org otm.suntrust.com moneymanagergps.com pacificenterprisebank.com multinetbank.eu parex.lv my.statestreet.com passport.texascapitalbank.com mybankfirstunited.wblnk.com pastabanka.lv mycorporate.org paylinks.cunet.org nab.com.au paypal.com nashvillecitizensbank.com piraeusbank.com nationalcity.com pnc.com nbarizona.com portfolioonline.metavante.com ncms-inc.com premierview.alloyacorp.org netteller.com premierview.membersunited.org nfbconnect.com privatbank.lv nordea.com rbs.com northbaybancorp.com rbscoutts.com northerntrust.com rbsidigital.com norvik.lv rbsiibanking.com nsbank.com rbsm.com ntrs.com rbworld.lv online-offshore.lloydstsb.com rcbcy.com online.1stnb.com rietumu.lv online.alphabank.com.cy royalbank.com online.citadele.lv s2b.standardchartered.com online.citibank.com sampopank.ee 9 sandyspringbank.com sterlingwires.com santander.co.uk suncorpbank.com.au schwab.com sunshinestatefederal.wblnk.com scotiaconnect.scotiabank.com suntrust.com scotiaonline.scotiabank.com svbconnect.com scottvalleybank.com swedbank.lv seb.ee tbb.ee seb.lt tdbank.com seb.lv tdcommercialbanking secure-eccu.org tdcommercialbanking.com secure.1stfedbank.com telepc.net secure.accurint.com top.capitalonebank.com secure.ally.com towernet.capitalonebank.com secure.bancinternetgroup.com trast.net secure.currency.lloydstsb-offshore.com trastnet.tkb.com.cy secure.dalhartfederal.com treas-mgt.frostbank.com secure.fnbhutch.com treasury.pncbank.com secure.fsbperkasie.com treasury.wamu.com secure.fundsxpress.com treasurydirect.tdbank.com secure.ltbbank.com treasurylinkweb.com secure.ltblv.com treasurypathways.com secure2.umb.com trustmark.openbank.com secure7.onlineaccess1.com trustweb.com securebanking.cbtks.com trz.tranzact.org securentry.calbanktrust.com ub.lt securentrycorp.amegybank.com ubs.com secureport.texascapitalbank.com unitedbankwi.com server14.cey-ebanking.com us.hsbc.com singlepoint.usbank.com usgateway.rbs.com site-secure.com usgateway2.rbs.com snoras.com valartis.at solutions-corporate.com valartis.li springbankconnect.com vectrabank.com ssl.selectpayment.com vpbank.com sso.uboc.com wblnk.com sso.unionbank.com wbsavings.wblnk.com statebanktx.com web-access.com web.accessor.com westernbankcash.com webbankingforbusiness.mandtbank.com westernetbank.com webcashmgmt.com westfield.accounts-in-view.com webcmpr.bancopopular.com wirexchange.goxroads.com webinfocus.mandtbank.com wtdirect.com weblink.websterbank.com www.amegybank.com wellsfargo.com www.enternetbank.com wellsoffice.wellsfargo.com www8.comerica.com Keywords The following is a list of keywords that have been identified by parsing the configuration information in the registry key data of Cridex banking Trojan malware. 10 *.com/K1/* *BusinessAppsHome* */Authentication/zbf/k* *CLKCCM* */Authentication/zbf/k/* *CorporateAccounts* */BB/LOGON/* *PassmarkChallenge* */CASHplus/* *Pres_WA_Wires* */CLKCCM/* *RBS_Commercial* */Common/SignOn/* *bankbyweb* */Common/SignOn/Start.asp* *blilk* */IBWS/* *business_solutions* */Web_Bank* *businesslogin* */ach/* *cashman* */cashman/* *cashplus* */cmserver/* *checkgateway* */ebc_ebc1961/* *cmserver* */ibs.* *cnbsec1.* */inets/* *commercialservices* */livewire/* *corpACH* */netbnx/* *corporatebankingweb* */olbb/* *createCorpWire* */sbuser/* *createWire* */webcm/* *cu.com* */wire/* *cu.org* */wires/* *e-moneyger* *BalanceHome* *ebc_ebc1961* *ecash.* *phcp/servlet* *goldleaf* *pub/html* *hbcash.exe* *s2b.* *hbproxy.exe* *securentry* *inetbanker* *servlet/teller* *jqueryaddonsv2.js* *sso.uboc* *login_business.asp* *svbconnect* *netteller* *vpn1.* *nubi* *wcmfd/wcmpw* *onlinebanker* *webcash* *onlineserv/CM* *webexpress* About Solutionary Solutionary is the leading pure-play managed security services provider. Solutionary reduces the information security and compliance burden, delivering flexible managed security services that align with client goals, enhancing organizations’ existing security program, infrastructure and personnel. The company’s services are based on experienced security professionals, global threat intelligence from the Solutionary Security Engineering Research Team (SERT) and the patented ActiveGuard service platform. Solutionary works as an extension of clients’ internal teams, providing industry-leading customer service, patented technology, thought leadership, years of innovation and proprietary certifications that exceed industry standards. This client focus and dedication to customer service has enabled Solutionary to boast a client retention rate of over 98%. Solutionary provides 24/7 services to mid-market and global, enterprise clients through multiple security operations centers (SOCs) in North America. For additional information: info@solutionary.com | 866-333-2133 | www.solutionary.com. ActiveGuard® US Patent Numbers: 7,168,093; 7,424,743; 6,988,208; 7,370,359; 7,673,049; 7,954,159. Solutionary, the Solutionary logo, ActiveGuard, the ActiveGuard logo, are registered trademarks or service marks of Solutionary, Inc. or its subsidiaries in the United States. Other marks and brands may be claimed as the property of others. The product plans, specifications, and descriptions herein are provided for information only and subject to change without notice, and are provided without warranty of any kind, express or implied. Copyright ©2012 Solutionary, Inc. 11