Security Threat and Risk Assessment
advertisement

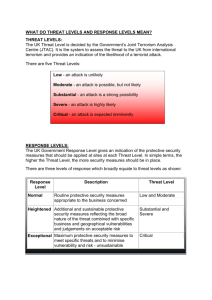
Policy Summary No. 7 Security Threat and Risk Assessment Information Security Branch, Office of the Chief Information Officer Ministry of Technology, Innovation and Citizens’ Services, Province of British Columbia http://www.cio.gov.bc.ca/cio/informationsecurity/index.page Importance of Information Security Protection of information assets is the primary goal of information security. This includes practicing safe computing behaviours to reduce the overall occurrence of theft, loss, or misuse of government information assets. A breach in information security or loss of information assets can have serious consequences, depending on the sensitivity and value of the information and the extent of the breach. The consequences can include: - disclosure of personal information, - interruption in government’s ability to deliver services, - financial losses related to correcting the situation, - threats to public safety or individuals’ health and well-being, - legal actions, and - erosion of the public trust in the government. Personnel action is the KEY to protecting government information assets. Technology and policies are only effective if personnel are aware of their responsibilities to use the processes enforcing the policies. Education and awareness are essential to promote an understanding of the importance of information security. The purpose of this document is to provide guidance about security-related aspects of a subject area of interest to the government community. It outlines the subject area background, related security concerns, responsibilities, and relevant information security policy. Subject Area Description Security Threat and Risk Assessments (STRA) are conducted to evaluate the security threats and risks to government information, programs, systems, services and physical spaces. (PS#16 Protection of Sensitive Information, PS#30 System Security Plan, PS#20 Application Security) A Security Threat and Risk Assessment examines four areas: personnel, physical environment, records/information, and technology. Security Threat and Risk Assessments form a part of the risk management process to ensure responsible management and security of information and information resources. Assessments suggest where to avoid, reduce and accept risk, as well as diminish the impact of threatening events. (PS#9 Information Security Events and Incidents) The Security Threat and Risk Assessment is a structured method for gathering threat profile information. The objective of conducting a Security Threat and Risk Assessment is to determine the adequacy of current safeguards from the point of view of requirements, efficiency and cost. Risk Assessment must be conducted on all information systems. This Policy Summary offers guidance for the use of Security Threat and Risk Assessments. It is intended to guide personnel and help them understand their responsibilities and obligations under the Information Security Policy. Areas of Concern The primary area of concern is that Security Threat and Risk Assessments are not conducted, reviewed or not performed consistently where and when required. Many factors amplify this concern: • When an assessment is not conducted in developing a program, system, service or physical space security controls may be inadequate or missing. • Where security vulnerabilities are not identified and controls put in place as the result of an assessment there may be great cost involved from a successful breach of the vulnerability. • Where risk information from a Security Threat and Risk Assessment is not considered an over expenditure for security controls may be incurred. • Where an assessment is not conducted threats to information and information resources may be unknown. • When an assessment is not conducted to identify threats to information and information resources acceptable risk is unclear. • When an assessment is not conducted to identify threats to information and information resources budgeting efficiencies or deficits may be missed. • Compliance and legislative requirements regarding security and privacy may not be adequate. • Lack of knowledge and experience integrating Security Threat and Risk Assessment findings into project plans and operational processes (e.g., unclear scale of effort, prioritization and resource requirements) may result in security vulnerabilities and lack of protection of information. Intended Outcomes The policies associated with Security Threat and Risk Assessment are intended to enable: • Compliance with legislative and policy objectives; • Cost-effective allocation of resources based on a risk assessment; • Responsible governance of the Province’s information assets; and, • Secure provision of government information and information resources. PS#7: Security Threat and Risk Assessment 1 CIO-SPS-2010-000-V3 Responsibilities of all Personnel Things to do: • Security Threat and Risk Assessments should be done on new, significantly upgraded or breached programs, systems, services and physical spaces. • Know the procedures for obtaining or conducting a Security Threat and Risk Assessment. • Obtain assistance from the Ministry Information Security Officer (MISO). • Regularly assess information security threats and risks to existing applications, systems or services. • Consider information classification and sensitivity levels in risk assessments. Things to avoid: • Not conducting a Security Threat and Risk Assessment on new, significantly upgraded or breached programs, systems, services and physical spaces. Things to pay attention to: • Identification of business and information technology risks, and any factors that will influence the risk assessment. • Changes to the cross-government standards for conducting Security Threat and Risk Assessments. Things to report: • Actual and suspected security incidents and events as required by the Information Incident Management Process. • File a General Incident or Loss Report (GILR) within 24 hours of a security incident. • Risk Management http://gww.fin.gov.bc.ca/gws/pt/rmb/ • Internal Audit and Advisory Services - Risk Assessment Tools http://www.fin.gov.bc.ca/ocg/ias/Risk_Assessment_Tools. htm • Information Incident Reporting - Shared Services BC Service Desk at 250 387-7000 or 1-866 660-0811, Select Option 3 References Document 12 Information Management and Information Technology Management 13.4.2 Risk and Controls Review 14 Risk Management 15 Security Information Security Policy http://www.cio.gov.bc.ca/local/cio/informationsecurity/policy/isp.pdf Responsibilities of Management Things to do: • Identify, plan for, and initiate Security Threat and Risk Assessments where required. • Review existing Security Threat and Risk Assessments to ensure recommended controls have been implemented. • Consult with the Ministry Information Security Officer (MISO) when conducting Security Threat and Risk Assessments. • When a security or privacy breach has occurred, review and revise related policies and processes as needed. Things to pay attention to: • Be aware of the development of new, significantly upgraded or breached programs, systems, services and physical spaces. • Consider security risks prior to granting access to external parties. Things to establish procedures for: • Conducting Security Threat and Risk Assessments by qualified personnel. Things to monitor: • Security Threat and Risk Assessments are being reviewed, performed and updated. Things to report: • Results of the Security Threat and Risk Assessment to the Ministry Information Security Officer (MISO). Things to reinforce with personnel: • Ensure key personnel are familiar with the requirement to conduct Security Threat and Risk Assessments. • Ensure the use of the Information Incident Management Process when required. 2.1.1 Management direction and support for information security 2.1.2 Organizing Information Security – Internal organization 2.1.4 Formal management authorization for new information systems 2.2.1 Assessment of risks from external party access 5.1 Physical and Environmental Security – Secure areas 5.2 Physical and Environmental Security – Equipment security 6.1.2 Controlling changes to information systems 6.3.2 Acceptance criteria for new or upgraded information systems 6.6.1 Security within the government network. 6.7.1 Media handling 7.1.1 Business requirement for access control 7.4.2 Network access control 7.4.5 Network access control 7.6.2 Application and information access control 7.7.1 Mobile computing and teleworking 8.1.1 Security controls for new or modified information systems Standards and Guidelines IM/IT Standards Manual http://www.cio.gov.bc.ca/local/cio/standards/ documents/standards/standards_manual.pdf Information Incident Management Process http://www.cio.gov.bc.ca/local/cio/information_ incident/information_incident_management_process.pdf Key Contacts Resources • Guide for Completing Information Security Threat and Risk Guide Using iSMART https://gww.cio.gov.bc.ca/services/security/compliance/ documents/guide_for_completing_stra_using_ismart.pdf PS#7: Security Threat and Risk Assessment Description Core Policy & Procedures Manual http://www.fin.gov.bc.ca/ocg/fmb/manuals/CPM/CPMtoc.htm 2 Contact Link Office of the Chief Information Officer http://www.cio.gov.bc.ca Information Security Branch, Office of the Chief Information Officer http://www.cio.gov.bc.ca/cio/ informationsecurity/index.page CIO-SPS-2010-000-V3