Retainer Template Start
advertisement

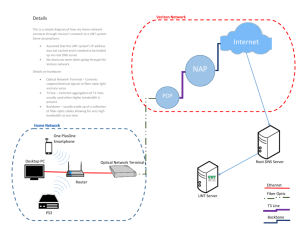
OnDemand Forensic & Incident Response Service Description OnDemand Forensic & Incident Response Service Description Forensic Investigation & Investigative Response Services The goal of the Verizon Investigative Response service offering is to assist our customers in responding rapidly and effectively to perceived threats to sensitive information, customer data, and network quality of service. Verizon is a registered and assessed provider of incident response services under the CREST cyber incident response scheme, a scheme led by CREST and endorsed by GCHQ and CPNI, which focuses on appropriate standards for incident response aligned to demand from all sectors of industry, the wider public sector and academia. Overview The Investigative Response process follows the following process which is described in the next section of the document. Figure 1 – Investigative Response Process This document contains Verizon proprietary and confidential material that shall not be disclosed, duplicated, or used for any purpose other than to evaluate this proposal. 07 March 2016 1 OnDemand Forensic & Incident Response Service Description Investigation steps The following tasks are to be performed by our specialists: 1. Initial Incident Response Phase a. Introduction The Initial Incident Response Phase begins when a potentially harmful incident is first suspected. The goal of this phase is to mobilize quickly to identify the source of the unwanted activity and contain it. The primary objective of the Initial Incident Response phase is to identify the breach take appropriate steps to contain the compromise, while at the same time, taking steps to maintain the integrity of the environment. b. Approach During the Initial Incident Response phase, Verizon will coordinate with Customer IT security personnel to identify the source of the unwanted activity for the purposes of analysis, documentation, and potential reporting / disclosure. c. Methodology The following elements are critical components of the Verizon Initial Incident Response process: i.Identify the Source: Verizon will work in close coordination with Customer IT Security personnel to analyze network and application activity, in addition to the impacts of any internal analysis, to identify the source of any perceived unwanted activity. ii.Containment: Once the source of the unwanted activity has been conclusively identified, the next critical objectives of the phase are to contain the breach and take appropriate steps to contain the compromise. This component of the process may involve network and/or system-level modifications to Customer systems. All modifications should be carried out by Customer under the direction of Verizon. iii.Evidence Preservation: In situations involving the theft of sensitive information, Customer must provide Verizon all necessary approvals so that Verizon may clearly understand the cause and full extent of the breach. Verizon will make best efforts to maintain the quality and integrity of the crime scene. At the conclusion of the phase, relevant forensics data sources identified will be transitioned to the Investigative Response team for further analysis, regardless of whether that role is fulfilled by Verizon, Customer, or law enforcement. d. Customer Responsibilities During the Initial Incident Response phase of the Investigative Response engagement, Customer agrees to: This document contains Verizon proprietary and confidential material that shall not be disclosed, duplicated, or used for any purpose other than to evaluate this proposal. 07 March 2016 2 OnDemand Forensic & Incident Response Service Description i.Provide Verizon with copies of all configuration information, log files, network and connectivity diagrams, intrusion detection events, and other forensic data deemed relevant to the Incident and its analysis; ii.Manage the collection and dissemination of all information regarding an Incident with Customer technical and managerial personnel, legal and public relations departments, others within Customer enterprise, and other involved companies; iii.Be responsible for and facilitate all communications between the Investigative Response Team and any third-party vendors, including Internet service providers and content-hosting firms, utilized by Customer; iv.Provide a secure office or work area equipped with desks, chairs, telephones, and laptop computer connections (or analog telephone lines, as Verizon specifies) for use by the Investigative Response Team while working onsite at Customer premises; v.Provide the Investigative Response Team with supervised access to computer systems and computer networks during the agreed upon timeframe; vi.Be responsible for the decision and authority to implement (or not to implement) any recommendations, the actions taken to do so, and the results achieved from such implementation; and vii.Be responsible for the actual content of any data file, selection, and implementation of controls and use, and security of stored data. e. Verizon Responsibilities Verizon will provide consulting services and support in the following areas of Initial Incident Response: i.Threat Identification: Personnel interviews and analysis of forensics data sources to clearly identify the source of the perceived unwanted activity; ii.Containment: Coordinate with Customer to identify the unwanted activity, and take appropriate steps to contain the compromise; and iii.Evidence Preservation: Identify and maintain the integrity of relevant forensic data sources that may be necessary for the purposes of forensic analysis and transition that information to the Investigative Response team. f. Deliverables Upon completion, Verizon will provide Customer with documentation outlining the specific impacts and findings relative to the Initial Incident Response phase of the engagement. Depending upon the requirements of Customer, this report may either be in the form of an Incident Report Short Form or Statement of Preliminary Findings. This document contains Verizon proprietary and confidential material that shall not be disclosed, duplicated, or used for any purpose other than to evaluate this proposal. 07 March 2016 3 OnDemand Forensic & Incident Response Service Description 2. Computer Forensic Analysis Phase a. Introduction Computer Forensic Analysis commences only after the Initial Incident Response phase has completed and the perceived unwanted activity has been identified and contained. This second stage of the Investigative Response engagement is intended to document the source and full extent of the breach for the purposes of the Incident Post-mortem process as well as to support criminal prosecution or other litigation support relative to a civil matter. b. Approach The Verizon Investigative Response Team utilizes a combination of open-source, commercially available, and proprietary forensic tools in efforts to gain multiple analysis vantage points. c. Methodology During the Computer Forensic Analysis phase of the Investigative Response engagement, Verizon will make efforts to clearly establish the full extent of the security breach or data compromise event. The full extent of the breach may include the source, the initial point of entry, the tools and methods employed by the intruder(s), and a listing of the systems, accounts, and third-parties exposed. More importantly, in situations involving the theft of sensitive information, the full extent may include the quantities and types of information compromised as a result of the breach. To support the Computer Forensic Analysis phase, Verizon may use a number of forensic, network, and/or application analysis tools. These tools may include, but are not limited to, the following: i.FTK: An over-the-counter forensic tool that features powerful file filtering and search functionality, allowing the user to search through thousands of files to find evidence quickly; ii.EnCase: A versatile over-the-counter Windows-based forensic analysis tool supporting data acquisition, data recovery, and de-duplication. ; iii.IDA Pro: A Freeware multi-platform disassembly and debugger; iv.iLook: A non-commercially-available tool. ILook is commonly used to capture and analyze images from computer drives and other external storage media; and v.Coroner’s Toolkit (TCT): A Freeware tool used for Post-mortem analysis of a UNIX system. Notable TCT components are the Grave-Robber tool that captures information, the ILS and MACTIME tools that display access patterns of files, dead or alive, the UNRM and LAZARUS tools that recover deleted files, and the FINDKEY tool that recovers cryptographic keys from a running process or from files. This document contains Verizon proprietary and confidential material that shall not be disclosed, duplicated, or used for any purpose other than to evaluate this proposal. 07 March 2016 4 OnDemand Forensic & Incident Response Service Description Also during the Computer Forensic Analysis phase, Verizon may use several techniques to identify relevant data: i.Time line of file, application, network, and system event activity; ii.Analysis of allocated disk sectors, files, and directories for the purposes of recovering deleted data; iii.Analysis of unallocated file system space for relevant information that may have been deleted; iv.In-depth analysis of file system binaries and executables for evidence of tampering or misuse; v.Recovery of relevant data stored on damaged or otherwise unusable media; and vi.Analysis of tapes, optical media, and other backup related mediums for evidence of relevant information. The specific results of this type of file recovery analysis may restore the target data files to their original locations on the disk or media they were recovered from. In many cases, Verizon may be able to recover most of the files and individual file versions that have existed on a given target system. Note: due to the variables encountered when attempting to recover deleted, destroyed, or otherwise unrecoverable data, results cannot be guaranteed. d. Customer Responsibilities During the Computer Forensic Analysis phase of the Investigative Response engagement, Customer agrees to: i.Provide Verizon with copies of all configuration information, log files, network and connectivity diagrams, intrusion detection events, and other forensic data sources deemed relevant to the Incident and its analysis; ii.Manage the collection and dissemination of all information regarding an Incident with Customer technical and managerial personnel, legal and public relations departments, others within Customer enterprise, and other involved companies; iii.Be responsible for and facilitate all communications between the Analysis Team and any third-party vendors, including Internet service providers and content-hosting firms, utilized by Customer; iv.Provide a secure office or work area equipped with desks, chairs, telephones, and laptop computer connections (or analog telephone lines, as Verizon specifies) for use by the Analysis Team while working on-site at Customer premises; v.Provide the Analysis Team with supervised access to computer systems and computer networks during the hours agreed upon; This document contains Verizon proprietary and confidential material that shall not be disclosed, duplicated, or used for any purpose other than to evaluate this proposal. 07 March 2016 5 OnDemand Forensic & Incident Response Service Description vi.Be responsible for the decision and approval to implement (or not to implement) our recommendations, the actions taken to do so, and the results achieved from such implementation; vii.Be responsible for the actual content of any data file, selection and implementation of controls on its access and use, and security of stored data; and viii.Be responsible for the decision to notify any outside parties, including law enforcement, of the findings. e. Verizon Responsibilities Verizon will provide consulting services and support in the following areas of Computer Forensic Analysis: i.Evidence Acquisition and Analysis: Verizon will utilize a combination of opensource, proprietary, and commercially available forensic and network analysis tools to acquire and analyze relevant evidence. ii.Maintaining Chain of Custody: All evidence acquired for the purposes of the investigation, including electronic media, forensic images, and paperbased reports, will be handled in accordance with industry-practices in relation to maintaining chain of custody. Verizon will securely transport and store all acquired evidence to maintain the confidentiality and integrity of the data; iii.Achieving Informational Objectives: Data acquisition and analysis will be performed specifically for the purposes of understanding the source and extent of the breach. Achieving the informational objectives of the investigation, as stated above, will set up the litigation and/or prosecution phase and serve to minimize any potential fraud losses or impact to consumers. f. Deliverables At the conclusion of the Computer Forensics Analysis phase, Verizon will provide Customer with an Investigative Management Report. This report will detail the specific findings of the investigation and the extent of the breach. This document contains Verizon proprietary and confidential material that shall not be disclosed, duplicated, or used for any purpose other than to evaluate this proposal. 07 March 2016 6 OnDemand Forensic & Incident Response Service Description 3. Litigation Support Phase a. Introduction Successfully pursuing the prosecution of the intruders, or achieving any successes in civil proceedings, will be in reliance of Customer meeting Customer obligations, as defined herein so that Verizon may achieve the informational and milestone objectives outlined in the Initial Incident Response and Computer Forensic Analysis phases. Litigation Support activities commence at the conclusion of the first two phases of the Incident Response lifecycle and may involve electronic data recovery, case evidence preparation, transitioning of case evidence to law enforcement, and expert witness testimony. b. Approach The Verizon Investigative Response team uses a very careful and detailed approach to the first two phases of the Investigative Response lifecycle that assists in the Litigation Support Phase. Verizon can assist if Customer chooses to pursue the prosecution of the intruder(s), notify outside parties of the Incident, or engage law enforcement officials. c. Methodology The Verizon Investigative Response includes both assisting customers in public disclosure following a data compromise event and working in coordination with law enforcement to assist in the capture and successful prosecution of the intruder(s). Verizon may also provide expert witness as needed by Customer. Note: the Litigation Support phase does not always come into play following an Incident. Given the background and facts of the case, the requirement for Litigation Support may be very clear at the onset of an Investigative Response engagement. If not, services in this regard are not scoped or priced as part of the initial engagement. In these circumstances, Litigation Support services are priced and scoped separately if deemed necessary by Customer. d. Customer Responsibilities During the Litigation Support phase of the Investigative Response engagement, Customer agrees to: i.Provide Verizon with copies of all configuration information, log files, network and connectivity diagrams, intrusion detection events, and other forensic data sources deemed relevant to the Litigation Support activity; ii.Manage the collection and dissemination of all information regarding an Incident with Customer technical and managerial personnel, legal, and public relations departments, as well as any others individuals deemed necessary by Customer; iii.Be responsible for and facilitating and arranging all necessary court time, evidence discovery, and other trial related requirements; This document contains Verizon proprietary and confidential material that shall not be disclosed, duplicated, or used for any purpose other than to evaluate this proposal. 07 March 2016 7 OnDemand Forensic & Incident Response Service Description iv.Provide a secure office or work area equipped with desks, chairs, telephones, and laptop computer connections (or analog telephone lines, as Verizon specifies) for use by the Litigation Support Team while working on-site at Customer premises; v.Be responsible for the decision and proper approval to implement (or not to implement) any recommendations, the actions taken to do so, and the results achieved from such implementation; and vi.Be responsible for the actual content of any data file, selection, and implementation of controls on its access and use, and security of stored data. e. Deliverables Unlike situations involving Initial Incident Response and advanced Computer Forensic Analysis, Litigation Support activities can vary greatly depending upon the circumstances and the specific Customer needs. At the onset of any Litigation Support engagement, Verizon will agree to a suitable documentation format that will satisfy reporting needs. Note - engagement deliverables will be formatted in accordance with payment industry guidelines. Also note - as an approved QFI - Verizon is required to provide the Associations (MasterCard and Visa) with copies of all engagement deliverables upon request unless there is a national law preventing this or there is a previous contract with an NDA in place between Verizon and the customer prior to this investigation. Always check with your legal department or your legal advisor if these investigative steps can be taken or if additional requirements are necessary. Verizon does NOT provide legal services but is well experienced in liaising with legal advisors. Customers are advised to store the original investigative items themselves in a secure location. Any evidentiary items that are processed by the IR lab in the course of an investigation are retained for 18 months. After the investigation they are securely deleted or can handed over to the customer or the party of your choice upon request. This document contains Verizon proprietary and confidential material that shall not be disclosed, duplicated, or used for any purpose other than to evaluate this proposal. 07 March 2016 8