Sample
advertisement

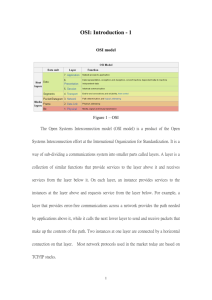
Lesson 2: The OSI Model Multiple Choice 1. Which standardization model describes the steps that data must go through to be transmitted across a data network? a) SOHO model b) UAC model c) Proprietary model d) OSI model Answer: d Difficulty: Easy Section Reference: Introduction to the OSI Model Explanation: The Open Systems Interconnection (OSI) model was created by the International Standards Organization to describe the steps that data must go through in order to be transmitted across a data network. The OSI model was never intended to define how data moves across networks; instead, it was intended to describe how data is created and defined so that it could be sent over a network. 2. What is the process of taking data from a higher layer of the OSI model and carrying it down into the next layer? a) embedment b) fixation c) encapsulation d) segmentation Answer: c Difficulty: Medium Section Reference: Introduction to the OSI Model Explanation: In networking, encapsulation is the process of taking data from a higher layer of the OSI model and carrying it down into the next layer. The reverse of this process is called deencapsulation. 3. In what format is data sent at the Physical layer of the OSI model? a) bits b) segments c) packets d) frames Answer: a Difficulty: Medium Section Reference: Introduction to the OSI Model Explanation: When the data frame reaches the bottom of the OSI model and enters the Physical layer, it is converted into bits, which are then passed down the network media to its destination computer. 4. In what format is data sent at the Transport layer of the OSI model? a) bits b) segments c) packets d) frames Answer: b Difficulty: Medium Section Reference: Introduction to the OSI Model Explanation: When data enters the Transport layer, it then becomes known as a segment. 5. In what format is data sent at the Data-Link layer of the OSI model? a) bits b) segments c) packets d) frames Answer: d Difficulty: Medium Section Reference: Introduction to the OSI Model Explanation: In the Data-Link layer, data packets are turned into frames. 6. In what format is data sent at the Network layer of the OSI model? a) bits b) segments c) packets d) frames Answer: c Difficulty: Medium Section Reference: Introduction to the OSI Model Explanation: As the segment is passed further down the OSI Model to the Networking layer, the segment becomes known as a packet. 7. Which OSI layer is the lowest layer that sends data over a cable or wireless medium? a) Physical b) Data-Link c) Network d) Transport Answer: a Difficulty: Easy Section Reference: Physical Layer Explanation: The Physical layer, as can be expected from its name, deals with all aspects of physically moving data from one computer to the next. The encapsulation units on this layer are called bits because this layer is concerned with converting data from the upper layers into 1s and 0s that can be transmitted over various types of transmission, called media. 8. Which layer includes the cables, wireless cards, and hubs? a) Physical b) Data-Link c) Network d) Transport Answer: a Difficulty: Easy Section Reference: Physical Layer Explanation: Because the Physical layer deals with all aspects of physically moving data from one computer to the next, it includes physical devices such as cables, wireless cards, and hubs. 9. Which layer includes the Logical Link Control and Media Access Control sublayers? a) Physical b) Data-Link c) Network d) Transport Answer: b Difficulty: Easy Section Reference: Data-Link Layer Explanation: The Data-Link layer is unique because it is divided into two sublayers to properly describe its full functionality. These two sublayers are called Logical Link Control (LLC)and Media Access Control. The LLC standard was created to facilitate communications between the upper Network Layer of the OSI Model and the Lower Physical Layer. The Media Access Control Sub Layer is used to determine which computer has access to the network media at any given time. 10. Which layer includes the MAC address? a) Physical b) Data-Link c) Network d) Transport Answer: b Difficulty: Easy Section Reference: Data-Link Layer Explanation: The Data-Link layer is concerned with moving data (in frames) from one computer or node to another. In this layer, computers communicate by using a physical address called the MAC address. 11. What method is used by a specific frame type or protocol to delineate to the computer the beginning and ending of any given frame? a) period counting b) signal threading c) frame synchronization d) clock threading Answer: c Difficulty: Medium Section Reference: MAC Sublayer Explanation: The Media Access Control sublayer determines where one frame ends and the next one starts. This method is known as frame synchronization. 12. Which of the following is not a form of frame synchronization? a) time-based frame synchronization b) character counting c) byte stuffing d) clock threading Answer: d Difficulty: Medium Section Reference: MAC Sublayer Explanation: In frame synchronization, a specific frame type or protocol delineates to the computer the beginning and ending of any given frame. The four methods of frame synchronization are time-based frame synchronization, character counting, byte stuffing, and bit stuffing. 13. At which OSI layer are logical addresses, such as IP addresses, defined? a) Physical b) Data-Link c) Network d) Transport Answer: c Difficulty: Easy Section Reference: Network Layer Explanation: Logical addresses, such as IP addresses, need to be assigned manually to every computer on a network. These addresses are assigned at the Network layer. 14. Which OSI layer is responsible for routing between networks? a) Physical b) Data-Link c) Network d) Transport Answer: c Difficulty: Easy Section Reference: Network Layer Explanation: Whereas the Data-Link layer is responsible for moving data from one computer or node to another, the Network layer is responsible for routing data in the form of packets from one end of the network to the other. 15. Which type of network communications protocol does not ask for verification that a data packet has successfully reached its destination? a) connectionless protocol b) connection-oriented protocol c) end-to-end protocol d) terminating protocol Answer: a Difficulty: Medium Section Reference: Network Layer Explanation: A connectionless protocol does not ask for verification that a data packet has successfully reached its destination. If a connectionless protocol is being used, the data packet is thrown out on the network and is just “assumed” that it successfully reached its destination. This “best-effort” delivery will usually suffice on most environments without problems. 16. TCP is an example of a ___________ protocol a) connectionless protocol b) connection-oriented protocol c) end-to-end protocol d) terminating protocol Answer: b Difficulty: Medium Section Reference: Network Layer Explanation: Connection-oriented protocols ask for verification that a packet has successfully reached its destination before sending another packet out. Most Network layer protocols used in modern networks, such as IP, are of the connectionless variety. However, TCP, one of the most widely used protocols at the Transport layer, is actually a connection-oriented protocol. 17. Which OSI layer ensures that the data gets delivered safely to its destination? a) Transport b) Data-Link c) Network d) Physical Answer: a Difficulty: Medium Section Reference: Network Layer Explanation: Aside from breaking the data into segments or reassembling segments back into data, the Transport Layer is also concerned with the reliability of the transport of the data sent. What this means is that the one of the jobs of the Transport Layer is to ensure that the data that has been sent safely arrived at its destination. 18. A/An ___________ is a unique address inside the computer that is associated with a specific protocol, service, or application. a) IP address b) TCP address c) ICMP port d) port address Answer: d Difficulty: Easy Section Reference: Port Addressing Explanation: The Transport layer needs to ensure that the data it has sent can get to the proper destination applications, services, or protocols. To do this, the Transport layer uses port addressing. A port address is a unique address inside the computer that is associated with a specific protocol, service, or application. 19. What port addresses range from 0 through 1,023? a) well-known ports b) registered ports c) dynamic ports d) recognized ports Answer: a Difficulty: Easy Section Reference: Port Addressing Explanation: Port addresses especially apply to the TCP and UDP protocols and are divided into three categories or ranges: well-known ports, registered ports, and dynamic ports. Well-known ports range from 0 through 1,023 and are pre-assigned by the Internet Corporation for Assigned Names and Numbers (ICANN) for the use of major networking protocols. Well-known ports do not change, no matter what computer or operating system you use. 20. Which address ports range between 1,024 and 49,151? a) well-known ports b) registered ports c) dynamic ports d) recognized ports Answer: b Difficulty: Easy Section Reference: Port Addressing Registered ports range from 1,024 through 49,151 and are registered with ICANN for specific uses, usually for a specific company, vendor, application, or operating system for proprietary use. 21. Which address ports range from 49,152 through 65,535 and are available for any application to use to communicate with any other application? a) well-known ports b) registered ports c) dynamic ports d) recognized ports Answer: c Difficulty: Easy Section Reference: Port Addressing Dynamic ports range from 49,152 through 65,535 and are available for any application to use to communicate with any other application. Dynamic ports are also sometimes known as private ports and ephemeral ports. 22. Which OSI layer is responsible for managing the dialog between networked devices? a) Transport b) Session c) Presentation d) Application Answer: b Difficulty: Easy Section Reference: Session Layer Explanation: The Session layer manages the dialog between networked devices. It can establish, manage, and terminate connections between local and remote computers or applications. 23. Which communication method is a true two-way communication between devices? a) full-duplex b) half-duplex c) simplex d) half-simplex Answer: a Difficulty: Easy Section Reference: Session Layer Explanation: Duplex or full-duplex means true two-way communications between devices. Either end of the connection can transmit or receive at the same time the other end is doing the same thing. 24. Which communication method is a pure one-way communication? a) full-duplex b) half-duplex c) simplex d) half-simplex Answer: c Difficulty: Easy Section Reference: Session Layer Explanation: Simplex communication is purely one way. Think of a radio or TV: All such a device can do is either send or receive; it cannot do both. 25. Which OSI layer is concerned with translation, compression, and encryption? a) Transport b) Session c) Presentation d) Application Answer: c Difficulty: Easy Section Reference: Presentation Layer Explanation: The Presentation layer is concerned with how data is presented to the network. To properly present data to the network, the Presentation layer is primarily concerned with three tasks: translation, compression, and encryption. 26. Which OSI layer includes SSL? a) Transport b) Session c) Presentation d) Application Answer: c Difficulty: Easy Section Reference: Presentation Layer Explanation: The Presentation layer is concerned with encryption, among other tasks. One of the most well-known uses of network encryption is something called Secure Sockets Layer (SSL), which is used to encrypt web pages. 27. Which layer of the OSI model discusses network services? a) Transport b) Session c) Presentation d) Application Answer: d Difficulty: Easy Section Reference: Application Layer Explanation: The top layer of the OSI model is the Application layer, which contains all the services and protocols needed by application software or the operating system to communicate on the network. 28. Which layer of the TCP/IP model corresponds to the OSI Network layer? a) Application b) Transport c) Internet d) Network Access Answer: c Difficulty Medium Section Reference: TCP/IP Model Explanation: Whereas the OSI model is based on an idealized network environment and does not match any real protocol suites, the TCP/IP model is built around the TCP/IP protocol suite. 29. At which OSI layer would a hub operate? a) Physical b) Data-Link c) Network d) Transport Answer: a Difficulty: Easy Section Reference: Physical Layer Explanation: The Physical layer deals with all aspects of physically moving data from one computer to the next, including cables and hubs. 29. At which OSI layer would a switch operate? a) Physical b) Data-Link c) Network d) Transport Answer: b Difficulty: Easy Section Reference: Data-Link Layer Explanation: The Data-Link layer is concerned with moving data from one computer to another. Because switches forward traffic based on the MAC address, it operates at the Data-Link layer. 30. At which OSI layer do routers operate? a) Physical b) Data-Link c) Network d) Transport Answer: c Difficulty: Easy Section Reference: Network Layer Explanation: The Network layer routes data in the form of packets from one end of the network to the other. 31. At which OSI layer do HTTP and FTP operate? a) Transport b) Session c) Presentation d) Application Answer: d Difficulty: Easy Section Reference: Application Layer Explanation: The Application layer contains all the services and protocols, including HTTP and FTP, needed by application software or the operating system to communicate on the network. 32. Which layer is the fourth layer of the OSI model? a) Transport b) Data-Link c) Physical d) Application Answer: a Difficulty: Easy Section Reference: Transport Layer Explanation: The next layer up from Network is Transport. The Transport layer takes data from higher levels of the OSI model and breaks it down into smaller pieces, called segments, which are sent to lower level layers for actual transmission. 33. Which OSI layer is responsible for reliable delivery of sent data? a) Transport b) Data-Link c) Physical d) Application Answer: a Difficulty: Easy Section Reference: Transport Layer Explanation: The Transport layer ensures that sent data safely arrives at its destination. 34. At which OSI layer are port addresses used? a) Transport b) Data-Link c) Physical d) Application Answer: a Difficulty: Easy Section Reference: Transport Layer Explanation: The Transport layer uses port addressing to ensure that data reaches its proper destination applications, services, or protocols. 35. OSI was created by __________. a) Adobe b) the ISO b) Microsoft d) Intel Answer: b Difficulty: Easy Section Reference: Introduction to the OSI Model Explanation: The OSI model was created by the International Organization for Standardization.to describe the steps that data must go through to be transmitted across a data network. 36. What TCP/IP model layer contains Ethernet and 802.11 wireless network device protocols? a) Application b) Transport c) Internet d) Network Access Answer: d Difficulty Medium Section Reference: TCP/IP Model Explanation: The TCP/IP protocol suite relies on standards created by various standards organizations concerning different media. These standards explain how to encode bits onto them to do the work on this layer of the TCP/IP model. Ethernet, the 802.11 wireless standards, and various WAN media standards make up the protocols found on lowest the TCP/IP model, the Network Access layer. 37. What TCP/IP model layer defines HTTP and FTP? a) Application b) Transport c) Internet d) Network Access Answer: a Difficulty: Medium Section Reference: TCP/IP Model Explanation: The top layer of the TCP/IP model is the Application layer, which simply deals with providing the protocols and/or services needed by the operating system and application software to communicate with the network. 38. At which OSI layer do the CSMA/CD and CSMA/CA operate? a) Physical b) Data-Link c) Network d) Transport Answer: b Difficulty: Easy Section Reference: Data-Link Layer Explanation: One of the primary functions of the MAC sublayer (part of the Data-Link layer) is to determine which computer has access to network media at any given time. In a LAN environment, the MAC sublayer makes this determination by using Carrier Sensing Media Access/Collision Detection (CSMA/CD) in the wired world and Carrier Sensing Media Access/Collision Avoidance (CSMA/CA) in the wireless world. 39. At which OSI layer do POP3 and Telnet operate? a) Transport b) Session c) Presentation d) Application Answer: d Difficulty: Easy Section Reference: Application Layer Explanation: The Application layer contains all the services and protocols, including POP3 and Telnet, needed by application software or the operating system to communicate on the network. Fill in the Blank 40. What is the physical address known as on a host or device? Answer: MAC address Difficulty: Medium Section Reference: Data-Link Layer Explanation: To move data around a network, a computer must know the address of the computer it is trying to communicate with. As such, the Data-Link layer contains an addressing mechanism for finding that computer, called a MAC address or a physical address. This address is referred to as a physical address because it is hard coded into the network device. Each device to be communicated with on a network segment must have a unique physical address. 41. A __________ is a predefined and widely accepted set of rules that describe exactly how a specific task is to work in a network environment. Answer: protocol Difficulty: Medium Section Reference: Data-Link Layer Explanation: A protocol is a predefined and widely accepted set of rules that describe exactly how a specific task is to work in a network environment. For communication to occur, both hosts must agree on the same protocol. 42. The _____________ protocol asks for verification that a packet has successfully reached its destination. Answer: connection-oriented Difficulty: Hard Section Reference: Network Layer Explanation: Connection-oriented protocols ask for verification that a packet has successfully reached its destination before sending another packet out. Most Network layer protocols used in modern networks, such as IP, are of the connectionless variety. However, TCP, one of the most widely used protocols at the Transport layer, is actually a connection-oriented protocol. Short Answer 43. How many well-known ports are there? Answer: 1,024 Difficulty: Easy Section Reference: Port Addressing Explanation: Port addresses apply to the TCP and UDP protocols and are divided into three categories or ranges: well-known, registered, and dynamic. Well-known ports range from 0 through 1,023 and are preassigned by the Internet Corporation for Assigned Names and Numbers (ICANN) for the use of major networking protocols. Well-known ports do not change, no matter what computer or operating system you use. 44. What protocol defines the LLC and MAC sublayers? Answer: 802.2 Difficulty: Hard Section Reference: Data-Link Layer Explanation: The protocol that defines these two sublayers in the Data-Link layer is known as IEEE 802.2, defined in the greater IEEE 802 protocol set. The IEEE 802 protocols are written this way because they were first proposed by a standards organization known as the Institute of Electrical and Electronic Engineers. 45. What are dynamic address ports also known as? Answer: Private ports or ephemeral ports Difficulty: Medium Section Reference: Port Addressing Explanation: Dynamic ports range from 49,152 through 65,535 and are available for any application to use to communicate with any other application. Dynamic ports are also sometimes known as private ports and emphemeral ports 46. List the four layers of the TCP/IP model. Answer: Application, Transport, Internet, and Network Access Difficulty: Hard Section Reference: TCP/IP Model Explanation: Whereas the OSI model is based on an idealized network environment and does not match any real protocol suites, the TCP/IP model is built around the TCP/IP protocol suite. It includes the Application, Transport, Internet, and Network Access layers. 47. What is the opposite of encapsulation? Answer: decapsulation Difficulty: Easy Section Reference: Encapsulation Explanation: In networking, encapsulation is the process of taking data from a higher layer of the OSI model and carrying it down into the next layer. The reverse of this process is called de-encapsulation. 48. When data is encapsulated, what is added at the beginning of data before it is sent to the next layer? Answer: A header Difficulty: Easy Section Reference: Encapsulation Explanation: Each layer adds its own header in front of the header from the previous layer. This header contains information that describes what each layer of the OSI model is to do with the data. 49. List at least one mnemonic used to describe the OSI model and match the corresponding OSI layers. Answers: All People Seem to Need Data Processing (Application Presentation Session Transport Network DataLink Physical) or Please Do Not Throw Sausage Pizza Away (Physical Data-Link Network Transport Session Presentation Application) Difficulty: Hard Section Reference: Introduction to the OSI model Explanation: Mnemonics are used as a way to remember not-so-easy lists. In this case, each letter of the phase is the same letter for layer in the OSI model Essay 50. Explain what the OSI model is designed for. Answer: The Open Systems Interconnection (OSI) model was created by the International Standards Organization to describe the steps that data must go through to be transmitted across a data network. The OSI model was never intended to define how data moves across networks; instead the OSI model was intended to describe how data is formatted and processed. It is used to define and classify the various technologies and protocols that make a network operate. Difficulty: Medium Section Reference: Introduction to the OSI Model Explanation: The OSI Model was created as a framework and reference model for understanding how different networking technologies work together and interact. In this capacity, the OSI Model is an excellent place to start when trying to understand all the processes that are necessary for data to be moved around a data network.