Instruction Set Architecture: Operand Addressing & RISC vs CISC
advertisement

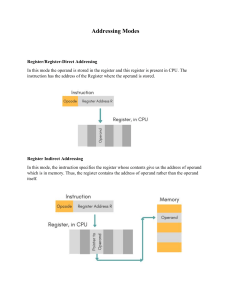
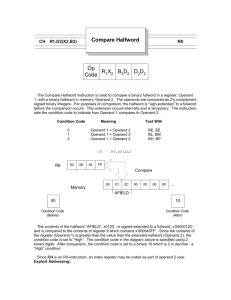
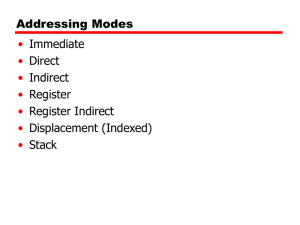
Mano, Chapter 11: Instruction Set Architecture (sections 11-1 through 11-4) Operand Addressing Addresses can be implied (e.g. Mythsim JUMP affects PC) or explicit (e.g. MOVE r1,r3) Number of operands per instruction can differ by architecture. To illustrate, consider the statement: X = (A+B) (C+D); for instructions with 3,2,1, and 0 operands (see accompanying sheet) Addressing Architectures: Memory-to-memory, vs. register-to-register (a.k.a. load/store) Memory-to-memory Typically CISC architectures allow instructions to operate directly on memory addresses. However, memory access is slower than CPU register access. Consider the 3-instruction solution, where each of the 3 instructions is of the form: M[T1] <- M[A] + M[B] A memory reference may need to retrieve 2 words (or 2 bytes in a byte-addressable machine). If each of 3 memory addresses requires an additional memory reference, this gives a total of 6, plus the 1 reference to fetch the instruction, giving a total of 7 memory accesses per each of the 3 instructions. 7 * 3 instructions = 21 memory accesses. Even though there are few instructions, execution time could be slower, and the instructions set larger and much more complex. Register-to-register (a.k.a. load/store) In comparison, the load/store architecture has only a single operation for reading and writing to memory. All other operations must use registers, which are much faster. The resulting 3-operand code for X = (A+B) (C+D) would look like: LOAD R1, A; LOAD R2, B; ADD R3,R1,R2; LOAD R1, C; LOAD R2, D; ADD R1,R1,R2; MUL R1,R1,R3; STORE X,R1; // // // // // // // // R1 <- Mem[A] R2 <- Mem[B] R3 <- R1 + R2 R1 <- Mem[C] R2 <- Mem[D] R1 <- R1 + R2 R1 <- R1 * R3 Mem[X] <- R1 This code now has 8, rather than 3 instructions, but has only 5 memory accesses, just like the stack-machine (0-operand) code. Addressing Modes Addressing modes are interpreted to give the effective address. Addressing modes may be different for each operand within an instruction. Implied Operand is defined implicitly in the opcode. E.g. JAL affects PC and the stack, though they are not specified as part of the instruction. Similarly ADD on a stack machine. Immediate The operand value to be used is embedded in the instruction. This is used in loading a constant or a specific memory address. Sometimes the ‘#’ is used to denote immediate mode. E.g. the second operand in: MOVE r1, #13; // r1 <- 13 Register An operand that uses a CPU register. E.g. the first operand in: MOVE r1, 13; // r1 <- 13 Indirect Addressing An operand that is the address of the value to be used. Indirection is usually indicated using parenthesis. E.g. the second operand in: MOVE r1, (20); // r1 <- Mem[ 20] Register Indirect An operand that is a register, where the register specifies the memory address to be used. E.g. the second operand in: MOVE r1, (r3); // r1 <- Mem[ r3] Relative Addressing An operand that is an offset to be added to the current pc, typically used in a branch. E.g. BR_IF_ZERO rj, ir_const4; // if (rj ==0) then PC <- PC + ir_const4 Indexed Addressing A register is used as an offset to an address. This could be used to traverse an array beginning at some fixed location. E.g. LOAD_INDEXED ri, n(rj); // ri <- Mem[ rj + n] Direct Addressing An operand that represents an actual memory address. A compiler may resolve a symbolic variable (e.g. x) to a direct address (on a machine where programs are loaded into fixed addresses) E.g. in the last line of the pseudo-assembler program segment: 1: .word 0:10 2: … … 17: la $a0, 1; // array of ten 0’s // $a0 <- 1 We don’t have any direct addressing in Mythsim. See also table 11-1 in Mano together with Figure 11-6 for more examples, though the syntax of a few of them is unfamiliar. Instruction Set Architectures There are the two major types of instruction sets, as mentioned at the beginning of the semester. Revisiting the characteristics of these should now make a bit more sense. They are: Complex Instruction Set Computers (CISC), and Reduced Instruction Set Computers (RISC) A RISC (e.g. SPIM, Mythsim) has the following properties: 1. Memory accesses are restricted to load and store instructions, and data manipulation instructions are register to register. 2. Addressing modes are limited in number. 3. Instruction formats are all of the same length 4. Instructions perform elementary operations. A CISC (e.g. Intel) has the following properties: 1. Memory access is directly available to most types of instruction 2. Addressing modes are substantial in number. 3. Instruction formats are of different lengths. 4. Instructions perform both elementary and complex operations.