Information on this syllabus is subject to change by the

Welcome to Computer Forensics CNIT 121-Section 831
August 17, 2015 – December 18, 2015
Online, 3 units
Instructor: Miao-Chuan(Mercy) Ho
Required Text:
Guide to Computer Forensics & Investigations- Processing Digital Evidence
By: Bill Nelson, Amelia Phillips & Chris Steuart, 5th Edition, ISBN #13-978-1-285-06003-3
Course Overview:
This course is designed for students that would like to learn about the emerging field of
Computer Forensics. With high tech crime on the rise, students will be able to acquire skills to become proficient in conducting investigations and analyzing cybercrime cases.
Forensics tools, methods and procedures for investigating computers. Data recovery techniques and evidence collection, protection of evidence, expert witness skills and computer crime investigation techniques. Analysis of various file systems and specialized diagnostic software to retrieve data. Prepares in part for CompTIA Security+ and maps to
Computer Investigation Specialists exam. CSU transferrable.
Advisory:
CNIT 120
Mandatory Orientation:
Saturday, 8/22 at 2:00-3:30pm at S214(Science Building at Ocean Campus)
Email me for the waiver if you live outside of Bay Area.
Policy on participation:
Students are expected to participate and complete weekly assignments in a timely manner. Students may be dropped by the instructor for failure to attend class in the following circumstances:
1) Absence from three consecutive weeks of instruction.
2) At any point when it is concluded that absences have irretrievably affected the student’s progress in his/her coursework...”
It is the responsibility of the student to withdrawal if you are no longer interested in attending class. This can be done through the Admissions office.
Contact Information for Instructor:
Feel free to e-mail me at: mcho@ccsf.edu
for questions regarding projects or homework assignments. Online office hours are Wednesday evenings 6-8pm or by arrangement.
Method of Instruction:
Completion of weekly assessments, discussion forums, videos, hands-on and case studies are important in order to master the material and successfully learn Computer Forensic theories and techniques.
Accommodations:
Students with documented learning and/or physical disabilities may receive reasonable testing accommodations. Please make these arrangements with the instructor at the beginning of the semester or as soon as possible after documentation has been determined.
Transfer Information:
This class is transferable to the CSU system.
Important dates to remember:
8/28/2015 Last day to drop Full-Term course work to qualify for 100% full refund
9/4/2015 Last day to add credit courses in person & online using Web4.
9/5-9/7/2015 Holiday- Labor Day Weekend- no classes held
9/10/2015 Last day to drop credit class with no “W”
9/10/2015 Last day to drop Full-Term course work to qualify for 50% refund
9/25/2015 Indigenous People’s Day- College open, no classes held
11/11/2015 Holiday- Veterans Day- no classes held
11/26-11/29 Thanksgiving Holiday-College closed, no classes held
12/11-12/18 Final examinations for day and evening classes
12/19-12/20 Final examinations for Saturday & Sunday classes
1/7/2016 Final grades available on Web4 at www.ccsf.edu
Grading :
100-90% = A
89-80% =
79-70% =
B
C
69-60% = D
59-50% = F
Weekly assessments, projects, mid-term, research paper and final exam will determine the students final grade based upon percentage points listed to the left. You can track your grades anytime in Desire 2 Learn (D2L).
Weekly Hands-on Projects
Weekly Case Projects
Weekly Assessments
Research Paper
Mid-Term
Final Exam
Discussion Forums
160 pts. (10 pts. max per assignment)
160 pts. (10 pts. max per assignment)
140 pts. (10 pts. max per week)
100 pts.
100 pts.
100 pts.
75pts. (5 pts. max per week)
Total 835 pts.
Plagiarism:
Plagiarism is unacceptable in any form in any college courses. This is stealing other people’s academic intellectual property. This includes forms such as: deliberately copying another student’s work, copying directly from the textbooks or other sources without using quotation marks, failure to acknowledge sources you have used in your work (i.e., you must cite all references) and cheating on exams.
Course Policies:
Late postings such as case and hands-on projects will not be accepted. Assignments are posted weekly in the Assignments tab are due by 11pm Saturday, so start early and don’t procrastinate. We will also explore actual Computer Forensics cases that have been investigated and are awaiting prosecution.
Student Learning Outcomes:
1.
Conduct a Computer Forensics investigation using problem solving techniques and strategic planning to identify sources that are infiltrating personal and corporate computers.
2.
Utilize computer forensic tools software to extract and analyze data in accordance with established chain of custody protocols for the organization.
3.
Decipher and recover data from e-mail, graphic files, cell phones and mobile devices by documenting forensic evidence for corporate personnel and law enforcement officials for future testimony.
Coursework:
Weekly Assessment tests are administered each week and are due by 11pm Saturday evening.
Research Paper:
Compile a seven page paper on how we can secure our nations computer infrastructure in our society. It could be related to the financial system, health care, energy grid, id theft, government intrusions etc. Use the Library Assignment handout and locate seven credible sources. Your paper should not have cited material from wikipedia.com. Explore the online databases such as academic search premiere, newsbanks and CQ researcher for relevant articles.
Your paper should have a cover sheet, five or more pages of documentation completed in
MLA style and a Works Cited page. Here is a link that will assist you with citing: http://owl.english.purdue.edu/owl/resource/747/02/ .
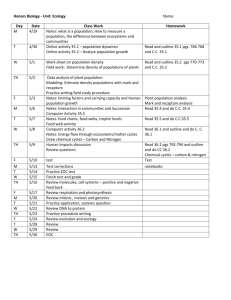
Week 1
Week 2
Week 6
Week 7
~Submit projects by 11pm Saturday evening, no late submissions~
Pick one Hands-On Project for Chapter 1 from pgs. 54-62; then pick one
Case Project from pg. 62
Complete Hands-On Project 2-1 – 2-5 (5 projects) on pages 87-88
Complete Case Project 2-2 from pg. 88
Week 3 Complete Hands-On Project 3-1 on page 129
Complete Case Project 3-2 and 3-4 on pgs. 132-133
Week 4 Complete Case Projects 4-2 and 4-4 on pgs.180-181
Week 5 Complete Hands-On Project’s 5-1 on page 244
Complete Case Project 5-2 on page 250
Complete Case Projects 6-1 & 6-3 on pgs. 282-283.
Complete Hands-On Project 7-1 & 7-2 on pgs. 314-315
Week 8
Week 9
Week 10
Complete Case Project’s 8-1 & 8-3 on pgs. 357-358
Mid-term
Complete Case Projects 9-2 & 9-3 on page 387
Week 11 Complete Case Projects 10-2 & 10-4 on page 422
Week 12 Complete Hands-On Project 11-3 on pgs 453-454 & Case Project 11-2 on page 455
Week 13 Complete Hands-On Projects 12-3 & 12-4 on pgs.478-479
Week 14 Complete Hands-On Project 13-1 on page 505 & Case Project 13-2 from page 510
Week 15 Complete Case Projects 14-1 -14-4 on pgs. 531-534
Week 16 Complete Case Projects 15-2 & 15-3 on page 565
Week 17 Complete Case Projects 16-1 - 16-3 (3 cases) on page 598
Week 18 Final Exam, December 18, 2015 available to login from 9am-5pm.
Week 10
Week 11
Forensics
Week 12
Week 13
Week 15
Week 16
Week 17
Week 18
Lecture Series
Week 1 Chapter 1: Understanding Digital Forensics Profession and Investigations
Week 2 Chapter 2: The Investigator’s Office and Laboratory
Chapter 3: Data Acquisition Week 3
Week 4 Chapter 4: Processing Crime and Incident Scenes
Chapter 5: Working with Windows and CLI Systems Week 5
Week 6
Week 7
Week 8
Week 9
Chapter 6: Current Digital Forensic Tools
Chapter 7: Linux and Macintosh Systems
Chapter 8- Recovering Graphics Files
Prepare for Mid-Term (Chapters 1-8, available 10/16/16 from 9am-5pm)
Chapter 9: Digital Forensics Analysis & Validation
Chapter 10: Virtual Machine Forensics, Live Acquisitions/Network
Chapter 11: E-Mail and Social Media Investigations
Chapter 12: Mobile Device Forensics
Chapter 13: Cloud Forensics
Chapter 14: Report Writing for High-Tech Investigations
Chapter 15: Expert Testimony in High-Tech Investigations
Chapter 16: Ethics for the Expert Witness
Prepare for Final Exam (Chapters 9-16, 12/18/15 from 9am-5pm)
Information on this syllabus is subject to change by the Instructor…