Lab exercises
advertisement

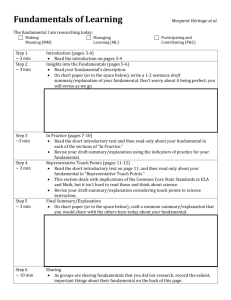
Workplace delivery of ICA50405 – Diploma of Information Technology (Networking) Security fundamentals – Lab 12 Assessment cover sheet Security fundamentals – Lab 12 Student’s name Student’s ID Qualification ICA50405 – Diploma of Information Technology (Networking) Assessment Security fundamentals Unit of competency National ID Title ICAS5118C Manage system security Assessment description This assessment covers the performance criteria for managing system security. Due date Date submitted Student’s declaration Yes No I/We have read and understood the details of the assessment. I/We have been informed of the conditions of the assessment and the appeals process. I/We agree to participate in this assessment. I/We certify that the attached is my/our own work. Student’s signature Date Assessment results Not yet competent Competent Comments/Feedback from assessor to student Comments/Feedback from student to assessor Assessor’s name Date Assessor’s signature Student’s name Date Student’s signature Page 1 of 7 © Department of Training and Workforce Development 2010 Version 1, June 2010 Workplace delivery of ICA50405 – Diploma of Information Technology (Networking) Security fundamentals – Lab 12 Instructions for students 1. In order to meet the criteria, you will need to complete all parts of this assessment. 2. This assessment can be done during class time or outside of class time. 3. Discussion with other team members is encouraged however all work submitted must be substantially your own. 4. You may be required to explain or demonstrate your understanding of any component of this assessment. 5. If you are quoting work that is not your own it must be appropriately referenced. 6. Submitted work must meet presentation standards appropriate to the workplace or your registered training organisation, eg header/footer, consistent formatting, spelling, grammar. 7. All work must be submitted by the due date. 8. If you have any questions please see your trainer. Performance measurement 1. You will need to complete all components without errors. 2. All files are to be correctly saved with appropriate names or as instructed. 3. Failure to do either of these tasks will result in a non-submission of assessment. Date <RTO to enter date> Assessment Security fundamentals – Lab 12 Assessment tasks Multiple tasks. These exercises and labs can be found in: Chapter 12 – ‘Maintaining Organisational Security’ of the Textbook Chapter 12 – ‘Maintaining Organisational Security’ of the Lab Manual. Submission checklist Please make sure that you have the following documents ready for submission. 8 Review answers 2 Case scenarios 5 Lab exercises Lab challenge 6 Lab review answers © Department of Training and Workforce Development 2010 Version 1, June 2010 Page 2 of 7 Workplace delivery of ICA50405 – Diploma of Information Technology (Networking) Security fundamentals – Lab 12 Security fundamentals – Lab 12 Recommended texts Wettern, J 2005, Security + Certification Textbook, Microsoft Press, Redmond, WA Grasdal, M 2005, Security + Certification Lab Manual, Microsoft Press, Redmond, WA Questions The questions and case scenarios for this lab can be found in Chapter 12 of the textbook. Review answers 1. 2. 3. 4. 5. 6. 7. 8. ___________________________________________________________________________ ___________________________________________________________________________ ___________________________________________________________________________ ___________________________________________________________________________ ___________________________________________________________________________ ___________________________________________________________________________ ___________________________________________________________________________ ___________________________________________________________________________ Case scenarios 12.1 Policies and procedures 12.2 Ethical dilemmas Page 3 of 7 © Department of Training and Workforce Development 2010 Version 1, June 2010 Workplace delivery of ICA50405 – Diploma of Information Technology (Networking) Security fundamentals – Lab 12 Lab work Set up You need to have completed the set-up instructions for the ‘instructor’ and ‘student’ computers, and the Contoso Domain as described in Security fundamentals – Lab 2 and the lab set-up guide available form your trainer. Lab exercises Complete the following exercises from the Lab Manual. An answer sheet is provided at the end of this document. Exercise 12.1 Creating an acceptable e-mail use policy Exercise 12.2 Enforcing a software restriction policy Exercise 12.3 Using Windows File Protection to enhance system stability Exercise 12.4 Enforcing an Internet acceptable use policy Exercise 12.5 Using Windows Tools to document system information Lab challenge 12.1 Enforcing security policies by using group policy Trainer sign off The following exercises will need to be sighted for evidence. Exercise 12.1 Exercise 12.2 Exercise 12.3 Exercise 12.4 Exercise 12.5 Lab challenge 12.1 Trainer’s name Date © Department of Training and Workforce Development 2010 Version 1, June 2010 Page 4 of 7 Workplace delivery of ICA50405 – Diploma of Information Technology (Networking) Security fundamentals – Lab 12 Investigation Using your preferred search engine do a search for ‘Cisco Security Policy Builder’. Use the Policy Builder wizard to generate a security policy for an organisation with the following attributes: has 200 users is in health care has wireless and VPN services requires remote access for doctors only. Page 5 of 7 © Department of Training and Workforce Development 2010 Version 1, June 2010 Workplace delivery of ICA50405 – Diploma of Information Technology (Networking) Security fundamentals – Lab 12 Lab review answers Question 1 Question 2 Question 3 Question 4 Question 5 © Department of Training and Workforce Development 2010 Version 1, June 2010 Page 6 of 7 Workplace delivery of ICA50405 – Diploma of Information Technology (Networking) Security fundamentals – Lab 12 Question 6 [End of document] Page 7 of 7 © Department of Training and Workforce Development 2010 Version 1, June 2010