COMMUNICATIONS NETWORKS
advertisement

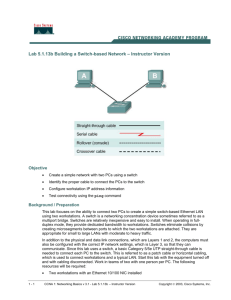
DT008/3 Communications Systems 1 Laboratory 3 Objective This lab will investigate the set up of simple networks based on the Ethernet LAN standard, using the following networking components: Hubs: a device to which can be connected multiple hosts. Frames transmitted by one host are forwarded to all ports of the hub, and therefore to all connected hosts. LAN Switches: a device to which can be connected multiple hosts. Frames transmitted by one host are forwarded to the port of the device to which the host identified by the layer 2 address of the frame is attached. Category 5/5E (Enhanced) Cables: A cable that consists of 4 twisted pair conductors (Unshielded Twisted Pairs, UTP), used for data transmission. Each end of the cable is terminated with an RJ-45 connector. The twisting of the pairs protects to some degree the signals carried by the cable from unwanted interferences. Category 5 cable is typically used for 10 or 100 Mbps Ethernet LANs, with only 2 pairs effectively used. Category 5 E is a higher specs cable designed for higher transmission speeds. In order to connect 2 PCs, or 2 Hubs or 2 Switches, the cable must be a crossover cable rather than a straight through: the receive and transmit pairs are crossed to allow transmission. Ping: the ICMP protocol will be used to test the connectivity between PCs (ping). The ICMP data are encapsulated as follows: Ethernet MAC header IP header ICMP header ICMP Data Ethernet MAC trailer Message capture with Wireshark: some fields in the Ethernet frame are generated in HW in the Network Interface Card just before transmission on line, and are not displayed by the Wireshark analyser. These fields are the FCS, pre-amble and SFD, (and padding, on the transmitter side, if needed in the payload). Page 1/5 During most of the laboratory you will need to interconnect 3 PCs. You should agree to work with 1 or 2 partners at the beginning of the session, and select a group of 3 PCs you will be able to use. There can be a single joint report for the group. Exercise 1: Hub based network In this part of the laboratory, you will need to work with 3 interconnected PCs. You will observe the traffic using the Wireshark network protocol analyser. Build the network with 3 PCs At the beginning of this exercise, you should have 3 PCs, 3 straight through cables and 1 hub (3COM Office Connect Dual Speed 5). Connect the 3 PCs to the hub using the straight through cables. Configure the IP settings For each PC: - from the “Control Panel” select “Network and Internet - View Network Status and Tasks". In the panel on the left, click on "Change Adapter Settings". - Right click on Local Area Connection and select properties. Then, highlight “Internet Protocol Version 4 (TCP/IP)” , and click on “Properties”. - select “Use the following IP address”; set the IP information as follows, then click OK to close the panel. Host IP Address Subnet Mask Default Gateway PC 1 192.168.1.1 255.255.255.0 N/A PC 2 192.168.1.2 255.255.255.0 N/A PC 3 192.168.1.3 255.255.255.0 N/A - open a Command Prompt window and use the ipconfig/all command to check that the values displayed are consistent with the values entered above, and to find the MAC (Physical) address of the PC. List in the Results sheet the 2 addresses for each PC. =>Results Sheet Test Reachability You should start the Network Protocol Analyser “Wireshark” from the desktop of each PC. Enter icmp in the display filter and Apply. In the Wireshark menu click on Capture, and click on start. From one PC, in the command prompt window, try to ping the IP address of the 2 other computers with only one request per ping and 81 bytes of data. Stop the capture after the sending PC has received all replies. Page 2/5 Observe the traffic captured by the analyser on each PC. On one of the PCs, identify a captured message that illustrates the “shared medium” operation of the Hub. Justify the choice, identify the PC on which you are making this observation, and list the source & destination addresses in the message. Results Sheet Observe the packet header details window. Report the number of bytes in the frame (“bytes on wire”) and find the number of Header bytes added by each layer. Show the breakdown of the number of bytes in the frame, by listing the payload and all headers and their length in bytes. Results Sheet Exercise 2: Switch based network Build the network with 3 PCs At the beginning of this exercise, you should have 3 PCs, 3 straight through cables and 1 switch (Cisco Catalyst Switch). Connect the 3 PCs to the switch using the straight through cables. Verify the IP settings Open a Command Prompt window; use the ipconfig command to check the values of addresses are same as entered in exercise 1. Each PC should send a default ping to each of the 2 other PCs to verify the connectivity. Test Reachability You should start the Network Protocol Analyser “Wireshark” from the desktop of each PC. Enter icmp in the display filter and Apply. In the Wireshark menu click on Capture, and click on start. From same PC as in Exercise 1, send a single request ping (1 requests, 32 bytes) to each of the 2 other PCs. Stop the capture when all replies have been received. Observe the traffic captured by the analyser on each PC. Explain the difference between the observed messages in this test and in exercise 1. Results Sheet Effect of payload size In the Wireshark menu, click on Capture, and click on start. For this test clear the icmp filter. From the command prompt window, try to ping from a PC the IP address of one of the 2 other computers, using only 1 request per ping and 1472 bytes. Then ping from a PC the IP address of one of the 2 other computers, using only 1 request per ping and 1473 bytes. Page 3/5 Calculate the size of the total payload that must be carried by the Ethernet LAN in each case, taking into account the IP and ICMP headers. Results Sheet Note: a packet too big for encapsulation in a single Ethernet frame will be fragmented, which leads to the display of packets identified as IP Fragments by Wireshark. Observe the messages captured by Wireshark for each of the 2 requests (ping 1472 and ping 1473), and explain how many frames are used in each case. Give the size of the frames. Results Sheet When a payload is too small, it is “padded” by adding bytes to reach the size of the minimum Ethernet frame. Find an example of such padded frame in the captured results. Explain how much padding has been added to this frame. Results Sheet Exercise 3 Connecting a management PC to the Switch 1. Connect the switch’s console port using a roll-over cable to the serial (COM) port on PC, Rollover cable 2. Open “Hyper terminal” by clicking: Start > Programs > Accessories > Communication > Hyper terminal. 3. Enter connection name, e.g.: Cisco 4. Select the COM port 5. Under “bits per second” select 9600 and leave all other fields. 6. Enter password if prompted (Passwords to be given during lab) Note: When first connecting, the lowest access mode, called the EXEC mode is entered. From this mode, the user can only use a limited numbers of unprivileged commands. It is necessary to enter privileged mode to enable more commands. This is done using the command enable. Privileged mode will usually be password protected. 7. Type enable and enter the password to enter Privileged mode. Page 4/5 From the command prompt, you can enter the command show mac-address-table dynamic, to visualize the MAC address table (forwarding database) created by the switch. First enter the following command to clear the forwarding database. Switch# clear mac-address-table dynamic Then send a ping from PC1 to PC2 only; use the show command to look at the MAC address table. Explain how the switch uses the Source Address and the Destination Address contained in an Ethernet frame. Results Sheet NOTE: AT THE END OF THE LABORATORY, RE-OPEN THE LOCAL AREA CONNECTION PROPERTIES FOR IPV4, AND RE-CHECK THE BOX “OBTAIN AN IP ADDRESS AUTOMATICALLY”. Page 5/5