09_Lim Poh Meng Nicholas
advertisement

SIM UNIVERSITY
SCHOOL OF SCIENCE AND TECHNOLOGY
ROAMING TRAFFIC (DATA) MONITORING
SYSTEM IN THE GSM NETWORK
STUDENT
: LIM POH MENG, NICHOLAS (N0605681)
SUPERVISOR
: MR. NAVA SELVARATNAM
A project report submitted to SIM University
in partial fulfilment of the requirements for the degree of
Bachelor of Engineering (or Bachelor of 2009)
Nov 2009
ABSTRACT
The mobile system has been a major success for the global telecommunication industry in
providing seamless roaming service to mobile subscribers all over the world. At this point
of time, the mobile market is almost at its saturation and therefore it is important for
mobile operators to provide the best network quality to sustain customer loyalty.
The purpose of my project is to design a roaming data system using a software
application called Wireshark. It has the capability to analyse and monitor the roaming
traffic of global system for mobile communication subscribers and solve problems that
occur at early stages.
I have installed Wireshark into my laptop to be used as a simulator. Upon collecting and
categorising the data into different groups, I will be presenting the data in graphical forms
for better comparison on the kind of data that is being transmitted and received.
Through this project, I have gained valuable experience and have learned to appreciate
the way mobile system functions. It has also allowed me to have a better understanding of
what telecommunication is about.
ACKNOWLEDGEMENTS
First and foremost, I will like to express my sincere gratitude to my supervisor Mr. Nava
Selvaratnam, for making this project a fulfilling experience. His invaluable guidance,
advice and encouragement during this crucial period have definitely contributed to the
success of this project. His careful analysis of my initial and final reports, together with
his detailed and perceptive comments, has also play an integral part in completing this
report.
I would also like to thank my wife, Angeline, and my family members for their
understanding on what I have been going through during my past 3 years of studies in
UNISIM. Without their love, affection, motivation and support, the completion of project
would not have been possible.
Finally, I would like to thank my colleagues at iFocus Pte Ltd for supporting me in terms
of covering my duties at work during this critical phase of my educational roadmap.
The experience and knowledge I have gained from this project is invaluable and
enriching, and I would like to dedicate this project to all the above people who this
possible.
LIST OF ABBREVIATIONS
Symbols
Definition
ACK
Acknowledgement
ANSI
American National Standards Institute
BS
Base Station
CCBS
Call to Busy Subscribers
DCP
Destination Point Code
FTP
File Transfer Protocol
GSM
Global System of Mobile Communications
GT
Global Title
GTT
Global Title Translation
GUI
Graphical User Interface
HTTP
Hypertext Transfer Protocol
IN
Intelligence Network
ISP
Internet Service Provider
LCP
Local Number Portability
MAC
Media Access Control
MTP
Message Transfer Part
NSAP
Network Service Access Point
NSP
Network Service Part
OPC
Originating Point Code
OSI
Open System Interconnection
PCS
Personal Communication Services
POP3
Post Office Protocol Version 3
PSTN
Public Switch Telephone Network
RAT
Remote Admin Trojan
RST
Reset
SCCP
Signalling Connection Control Part
SCMG
SCCP Management
Symbols
Definition
SCRC
SCCP Routing Control
SLS
Signalling Link Selection
SMS
Short Messaging System
SMTP
Simple Mail Transfer Program
SMMP
Simple Network Management Protocol
SSN
Subsystem Number
SSP
Service Switching Point
STP
System Time Protocol
SYN
Synchronize
TAP
Test Access Points
TCAP
Transfer Capabilities Application Part
TC
Transaction Capacity
TCP
Transmission Control Protocol
TTL
Time To Live
UDP
User Datagram Protocol
5
TABLE OF CONTENTS
ABSTRACT ...................................................................................................................................................2
ACKNOWLEDGEMENTS ..........................................................................................................................3
LIST OF ABBREVIATIONS .......................................................................................................................4
1
INTRODUCTION ...........................................................................................................................8
1.1
SIGNALLING CONNECTION CONTROL PART ...................................................................................... 8
1.2
GLOBAL SYSTEM FOR MOBILE COMMUNICATIONS (GSM) ............................................................... 9
1.3
OBJECTIVE .......................................................................................................................................11
1.4
SCOPE ..............................................................................................................................................11
2
LITERATURE REVIEW AND PREVIOUS WORK ................................................................ 12
2.1
THE BEGINNING OF GLOBAL SYSTEM FOR MOBILE COMMUNICATION ............................................12
2.1.1
First Generation ................................................................................................................13
2.1.2
Second Generation ............................................................................................................13
2.1.3
Interim Generation ............................................................................................................13
2.1.4
Third Generation ...............................................................................................................13
2.2
SCOPE OF THE GLOBAL SYSTEM FOR MOBILE COMMUNICATIONS STANDARD ................................14
2.3
SIGNALLING CONNECTION CONTROL PART ROUTING AND CONGESTION CONTROL ........................17
2.3.1
Signalling Connection Control Part Routing ....................................................................17
2.3.2
Congestion Control in the Connection-Oriented Class .....................................................18
2.4
RELATED JOURNALS ........................................................................................................................19
2.4.1
J1: Performance Evaluation of GSM handover Traffic in a GPRS/GSM Network ..........19
2.4.2
J2: Analysis of Congestion Control for SCCP Traffic and the Impact on Intelligent
Network Service...................................................................................................................................20
2.4.3
J3: Congestion and Flow Control in Signalling System No. 7-Impacts of Intelligent
Networks and New Services ................................................................................................................20
2.4.4
J4: Dynamic Traffic Grooming in Optical Networks with Wavelength Conversion ........21
2.4.5
J5: IDAMN: an Intrusion Detection Architecture for Mobile Networks ..........................21
2.4.6
J6: Routing and Congestion Control in Common Channel Signalling System No. 7 .......22
3
OVERVIEW OF THE PROJECT............................................................................................... 24
3.1
PROJECT MANAGEMENT ..................................................................................................................24
3.2
GANTT CHART..................................................................................................................................25
3.3
DETAILS OF GANTT CHART ..............................................................................................................26
3.3.1
Getting Started ..................................................................................................................26
3.3.2
Review on Project Flow ....................................................................................................26
6
3.3.3
Development of Software .................................................................................................26
3.3.4
Evaluation and Begin of Thesis Writing ...........................................................................27
3.3.5
Oral and Poster Presentation .............................................................................................27
4
METHODOLOGY ........................................................................................................................ 28
4.1
DESIGN STRATEGY ..........................................................................................................................28
4.2
SOFTWARE COMPARISONS ...............................................................................................................29
4.3
TECHNOLOGY BEING USED ..............................................................................................................30
5
EXPERIMENTAL PROCEDURE .............................................................................................. 32
5.1
CAPTURE OF DATA ..........................................................................................................................32
5.2
ANALYSE OF DATA ..........................................................................................................................34
5.2.1
Packet List Pane ................................................................................................................35
5.2.2
Packet Details Pane ...........................................................................................................35
5.2.3
Packet Byte Pane ..............................................................................................................35
5.3
6
FLOW CHART ...................................................................................................................................36
RESULTS AND DISCUSSIONS .................................................................................................37
6.1
DATA COLLECTED ...........................................................................................................................37
6.1.1
6.2
7
Graphs ...............................................................................................................................38
TEST RESULTS .................................................................................................................................38
LIMITATION AND CONCLUSION .......................................................................................... 41
7.1
LIMITATION .....................................................................................................................................41
7.2
RISK ASSESSMENT ...........................................................................................................................41
7.3
FUTURE DISCUSSION ........................................................................................................................41
7.4
CONCLUSION....................................................................................................................................42
8
CRITICAL REFLECTIONS .......................................................................................................43
9
REFERENCES .............................................................................................................................. 44
9.1
APPENDIXES.....................................................................................................................................45
9.1.1
9.2
Test Results Data from Wireshark ....................................................................................45
SOURCE CODE..................................................................................................................................47
9.2.1
Capture Data .....................................................................................................................47
9.2.2
Start Capture .....................................................................................................................51
9.2.3
Filter Data .........................................................................................................................53
9.2.4
Read Data ..........................................................................................................................54
7
1
INTRODUCTION
1.1 Signalling Connection Control Part
Signalling Connection Control Part (SCCP) is a routing protocol in the SS7 protocol suite in
layer 3. It gives an end to end routing for TCAP messages to the correct database. It is also a
network layer that provides extended routing, flow control, segmentation, connection orientation
and error correction facilities in the Signalling System 7 telecommunication networks.
SCCP allows an STP to perform global title translation (GTT), a procedure whereby the
destination signalling point and subsystem number (SSN) is determined with digits. Global title,
which is in the signalling message, is pertinent to the service requested. The diagram below
shows where SCCP is located in the SS7/C7 protocol suite:
Figure 1a: SS7/C7 Protocol Suite
SCCP provides better capabilities then MTP:
1.
It enhances MTP to meet OSI layer 3.
2.
It is a powerful and flexible routing mechanism.
3.
It enhances transfer capabilities when message is too large to fit into one message signal
unit (MSU).
SCCP also provides connectionless and connection oriented network service above MTP level 3.
SCCP relies on the service of MTP for basic routing and error detection. MTP level 3 provide
point codes to allow messages to be addressed to a particular signalling point. SCCP on the other
hand, gives subsystems at these signalling points. SCCP is also used as the transport layer for the
transfer capabilities application part (TCAP) based services such as the free phone (800/888),
calling card, local number portability (LCP), wireless roaming, personal communication services
(PCS) and complete of calls to busy subscribers (CCBS) in intelligent networks and mobility,
roaming and SMS in cellular systems.
SCCP is widely used in major cellular networks like the Base Station Subsystem Mobile
Application Part (BSSMAP) and Direct Transfer Applicationice Part (DTAP). They are used to
transfer radio related message in Global System for Mobile communication (GSM). In
combination with TCAP, SCCP is used throughout the GSM Network Switching Subsystem
(NSS) to transport Mobile Application Part (MAP) signalling between the core GSM
components to allow subscriber mobility and text messaging (SMS), among other items.
1.2 Global System for Mobile Communications (GSM)
Originally from Groupe Speciale Mobile, GSM is the most popular standard for mobile phones
in the world. Its promoter, the GSM Association, predicts that 80% of the global mobile market
uses the standard. GSM is used by over 3 billion people across more than 212 countries and
territories. Its ubiquity makes international roaming very common between mobile phone
operators, enabling subscribers to use the phones in many parts of the world. GSM differs from
its predecessors in that both signalling and speech channels are digital. It is considered a second
generation mobile phone system. This also meant that data communication was easy to build into
the system.
The ubiquity of the GSM standards has been an advantage to both consumers and network
operators. GSM is also a low cost alternative to video calls and the short messaging system
(SMS), which is now supported on other mobiles standards as well. Another advantage is that the
standard includes one worldwide emergency telephone number, 112. This makes it easier for
9
international travellers to connect to emergency services without having to know the local
emergency number.
A GSM system consists of a fixed installation infrastructure and the mobile subscribers. The
fixed installation GSM network can be subdivided into 3 subsystems. They are:
1.
Base Station Subsystem (BSS)
2.
Network
3.
Switching Subsystem (NSS)
4.
Operation and Support subsystem (OSS)
To provide service to the mobile subscribers, a network operator has to install a complete and
separate network that is able to interface with the Public Switched Telephone Network (PSTN).
The diagram below shows the layout of the GSM network:
Figure 1b: Structure of the GSM network
10
The network seen by the computer is huge and complicated. In order to provide all the services
that are needed, the network is divided into a number of sections:
1. The base station subsystem (the base stations and the controllers).
2. The network and switching subsystem (the part of the network that is almost similar to a
fixed network. It is also known as core network.)
3. The GPRS core network (the optional part that allows packet based internet connections).
4. All of the elements in the system combine to produce many GSM services such as voice
calls and Short Message System (SMS).
1.3 Objective
The objective of my project is to design a roaming data system that is able to analyse and
monitor the roaming traffic of the GSM (Global System for Mobile Communication) subscribers.
1.4 Scope
Specifically, the scope of this project includes the following:
1. To perform literature study into the Layer 3 of the SCCP (Signalling Connection Control
Part) messages of the GSM (Global System for Mobile Communication) roaming
subscribers.
2. To develop software for the system that is able to extract the desire data from the raw
SCCP messages from GSM network.
3. To analyse the extracted SCCP data and categorise them into specific groups.
4. To modify and optimise the monitoring system.
11
2
LITERATURE REVIEW AND PREVIOUS WORK
2.1 The Beginning of Global System for Mobile Communication
In the year of 1887 and 1888, Hertz found out that invisible waves were originated from electric
spark. It was able to transport information through the air. This phenomenon was then further
researched and developed until it was possible to transmit and receive signals over a distance of
several kilometres. Mr. Guglielmo Marconi performed an out of this world demonstration of this
several years later. This experiment was served as a basic of cellular radio and many other
transmission systems.
In the year 1920, radio broadcasting was slowly introduced. Soon after which, Amplitude
Modulation (AM) and Frequency Modulation (FM) transmission came in 1929. During that year,
early FM receivers had good quality reception but unfortunately, the application was limited by
the transmitter size and large amount of power consumed. Even the cellular concept such as the
spread spectrum technique, digital modulation, trunking techniques and other modern radio
technologies were made known, mobile telephone services did not appear to be user friendly
until the early 1960s.
The convenience of these early mobile services was severely limited and their capacity was
extremely limited compared to today’s standards. At last, analog cellular mobile phone systems
with full FM duplex and trunked access appeared in the 1980s. By the end of 1980, it was clear
that the analog cellular system would not be able to meet the continuing demand into the next
century. The solution was to time multiplex the traffic and signalling functions be realised with
digital techniques.
These practical considerations together with political pressure in Europe created the Groupe
Speciale Mobile (GSM) system in the late 1980s. The GSM system included specific features
such as the international roaming and wide variety of auxiliary services. The first official
commercial GSM service was launched in Europe in 1992. On the global scale, the GSM
standard received a very fast recognition. By the end of 1993, several commercials GSM
networks commenced operation outside Europe.
12
2.1.1 First Generation
The Frequency Division Multiple Access (FDMA) technique was used in first generation
systems. These systems used analog modulation techniques as FM modulation. An example of a
first generation cellular system is Advance Mobile Telephone System (AMPS). First generation
systems suffered from limitations such as low service quality, long call setup time, inefficient use
of bandwidth, susceptibility to interface bulky and expensive equipments and only support for
speech.
2.1.2 Second Generation
GSM falls in the category of second generation cellular systems. Second generation cellular
systems apply better digital modulation and advanced call procedure techniques. Code Division
Multiple Access (CDMA) also falls in that category of second generation systems. These
systems provide better service quality than those of the first generation cellular systems and use
bandwidth more efficiently. Second generation cellular systems support data, speech and
facsimile service. In addition, the second generation systems use encryption mechanism to
protect data and speech and use advanced mobility management and support power control.
2.1.3 Interim Generation
As technology improved, it has become very costly for the service providers to replace the whole
infrastructure. Therefore, incremental improvements to existing networks provided an interim
step with significant benefit to users. GPRS provided a data delivery mechanism on the GSM
network with bigger bandwidth. Enhanced data rate for Global Evolution (EDGE) was the
enhancement provided by GPRS with even higher data rates.
2.1.4 Third Generation
The third generation achieves very high data rates for transmission of data and speech. The third
generation system is to integrate all types of services such as speech, data, audio and video
through the mobile handsets. The users of third generation systems are billed according to the
utilization of the channel rather than time in use. Thus, a third generation system provides faster
service than lower billing rates. The collective name of third generation technologies throughout
13
the world is Universal Telecommunication System (UTMS). The figure below shows the
different stages of Wireless technology:
Figure 2a: Different Stages of Wireless Technology
2.2 Scope of the Global System for Mobile Communications Standard
The first generation of analog cellular systems was designed for basic voice service. Data
services for fax or circuit switch data transmission using a voice band modem were classified as
‘overlay’ services that run on top of the voice service. The second generation GSM cellular
system was designed to be an integrated wireless voice data service network that offered several
other services beyond just voice telephone service.
The first type is Teleservices. It provides standard voice communication and the additional
communications between two end users applications according to standard protocol.
The second type is Bearer Services. It provides the user with the ability to transmit data between
user network interfaces.
14
The additional type is Supplementary Services. They are services that enhance or support a teleservice provided by the network.
The planning of GSM system development and deployment called for the implementation of
system services to be carried out in 2 phases. In the first phase, the GSM services offered were
shown in the table: Phase 1 GSM Service. In the second phase of GSM implementation, the
service offerings would be expanded to include those shown in the table: Phase 2 GSM Service.
Types of Services
Service Provided
Additional Details
GSM Teleservices
Telephone
Full rate at 13 kbps voice
Emergency Calls
“112” is GSM wide emergency
Short Message Systems
number
Videotext Access
Point to point (between two
Tele-tax
users) and cell broadcast types
Fax
GSM Bearer Services
Asynchronous Data
300 - 9600 bps (transparent/non
Synchronous Data
transparent)
Synchronous Packet Data
2400 – 9600 bps (transparent)
Others
Supplementary Services
Call Forwarding
All calls when the subscriber is
Call Barring
not available
Outgoing call with
specifications
Figure 2b: Phase 1 GSM Services
15
Types of Services
Service Provided
Additional Details
GSM Teleservices
Half-Rate Speech Coder
Optional implementation
Enhanced Full Rate
Supplementary Services
Calling Line Identification
Presentation or restriction
Connected Line Identification
of displaying the caller’s
Call Waiting
ID
Call Hold
Presentation or restriction
Multiparty Communication
of displaying the caller ID
Closed User Loop
incoming
Advice of Change
current conversation
Operator Call Barring
Put current call on hold to
call
during
answer another call
Up to five outgoing calls
can be included in one
conversation
Restriction
of
certain
features from individual
subscribers by operator
Figure 2c: Phase 2 GSM Services
16
2.3 Signalling Connection Control Part Routing and Congestion Control
The SCCP enhances the functionality of the MTP by providing connection oriented services. An
example is the logical signalling connection. It gives additional features in the wireless control,
routing and management. The SCCP is used as a transfer of circuit related and non-circuit related
information. The SCCP, together with the MTP, provide the layer 3 of the OSI system’s
functionality. The SCCP provides the following services: basic connectionless class sequenced
(MTP) connectionless class, basic connection-oriented class and flow control connection
oriented class. Theses services are referred as class 0 to 3. A notable application of the SCCP
function is implementing the STP gateway which interconnects two signalling networks. [1]
An important routing function, in both the connectionless and connection-oriented services of
SCCP is GT routing, which includes a translation mapping on the SCCP address parameter from
a GT. An example is a point code and a SSN. The SSN is a sub address which identifies a SCCP
user function. This function is in the OSI model.
2.3.1 Signalling Connection Control Part Routing
The routing function of the SCCP is performed by the SCRC (SCCP Routing Control) for
messages received from the MTP. The SCCP is either using the MTP routing (i.e. is the DPC)
plus a SSN (i.e. the SCCP user address), or a GT routing. The previous is used in direct routing
but will require translation subsequently.
Global address routing is used when the original node does not have the network address of the
destination point. Thus, the function is needed in a vase amount of applications to date (for
instance 800 services). Let us take a look at one example of a GT routing - the signalling
message comprises of a DPC and a GT is routed to an STP. At the STP, the GT address is
translated into a DPC and a SSN. This DPC is used for network routing and the SSN is
identifying the service database at that signalling point. Another option is that the translation of a
GT results in a new GT that is routed to another STP for further translation.
17
There are 4 types of GT routing designated by the GT indicator that are different from one
another based on numbering and encoding schemes. The SCCP global routing is table driven,
using its own table for translating the GT into a DPC and SSN. The translation may be
performed either in a centralised or distributed fashion.
SCMG provides route and traffic management when failures occur. An important capacity of
SCMG is the rerouting of packets to a backup SP when the primary destination of logical address
has failed. This is useful in accessing the SCP for IN service by routing the messages to an
application backup SP when the primary application is unavailable. There is an overhead linking
with processing the GT routing, in the form of additional delay introduced in delivering the
packet to its destination.
2.3.2 Congestion Control in the Connection-Oriented Class
The class 3 of the SCCP protocol has flow control. To perform flow control, a window is
negotiated during the connection establishment that is not changed during the data transfer phase.
The size of the window is shown by a credit field in the SCCP connection establishment
primitives. During the call establishment, the SCCP user proposes a certain value for the quality
of service parameter set as part of the primitives. The window size at the beginning, intermediate
or terminating nodes may be altered by the SCCP to match the quality of service for the
signalling connection.
18
2.4 Related Journals
I have done some research on related journals which are of some assistance to this project.
2.4.1 J1: Performance Evaluation of GSM handover Traffic in a GPRS/GSM
Network
Their intention is to evaluate the performance degradation of GSM handover traffic due to the
introduction of GPRS in a GPRS/GSM network when various priority schemes for handover
traffic over new call traffic are applied. This case study is simulated by using an event driven
simulator. This event simulator has been implemented using simulation library develop in C++.
The GPRS/GSM is simulated in 2 scenarios: a basic microcell scenario and an overlaid
microcell/macro cell scenario. Different handover priority based channel allocation is to enhance
the handover performance. [2]
What I have gained after reading it: The GPRS/GSM can be simulated into 2 scenarios: basic
microcell and overlaid microcell/macro cell. Both can be implemented using an event simulator
using simulation library develop in C++.
19
2.4.2 J2: Analysis of Congestion Control for SCCP Traffic and the Impact on
Intelligent Network Service
It investigates the impact on CCS link overload and SCCP overload control for links supporting
Intelligence Network (IN) service, one of the major users of the SCCP signalling layer. It also
examines a number of network congestion network scenarios involving IN services and the
impact of CCS overload for those links supporting a mixture of IN traffic and PSTN (ISUP)
traffic. [3]
What I have gained after reading it: More knowledge on what is an intelligence network (IN).
The service it provides for the SCCP signalling layer.
2.4.3 J3: Congestion and Flow Control in Signalling System No. 7-Impacts of
Intelligent Networks and New Services
Analyses of the congestion and flow control mechanisms in CCITT Signalling System No7. We
show that signalling traffic characteristics like signalling scenarios or signalling message length
as well as end-to-end signalling capabilities have a significant influence on the congestion and
flow control and, therefore, on the real-time signalling performance. If the intelligent services are
introduced, the SS7 congestion and flow control does not work correctly. To solve this problem,
some reinvestigations into these mechanisms would be necessary. Usage of the SCCP relay
function, or a redesign of the MTP flow control procedures are discussed in order to guarantee
the efficacy of the congestion and flow control mechanisms also in the future. [4]
What I have gained after reading it: When intelligence services are introduced, the congestion
and flow control of the SS7 will not work properly. Therefore, usage of SCCP relay function or
change in the MTP flow control procedure may solve the problem.
20
2.4.4 J4: Dynamic Traffic Grooming in Optical Networks with Wavelength
Conversion
Traffic grooming in WDM (wavelength division multiplexing) optical networks refer to routing
and aggregating low rate client onto wavelength granularity light paths. Dynamic traffic
grooming is when the client randomly arrives/departs. The paper focus on the dynamic traffic
grooming when the optical network has sparse wavelength conversion, also aims to look into
impact of wavelength conversion and converter placement on dynamic traffic grooming. [5]
What I have gained after reading it: I have learnt about dynamic traffic grooming in optical
networks with wavelength conversion, with particular interest in the impact of wavelength
conversion on dynamic traffic grooming.
2.4.5 J5: IDAMN: an Intrusion Detection Architecture for Mobile Networks
IDAMN is a distributed system whose main functionality is to track and detect mobile intruders
in real-time. IDAMN includes two algorithms which model the behaviours of users in terms of
both telephony activity and migration pattern. The main novelty of our architecture is its ability
to perform intrusion detection in the visited location and within the duration of a typical call as
opposed to existing designs that require the reporting of all call data to the home location in
order to perform the actual detection. The algorithms and the components of IDAMN have been
designed in order to minimise the overhead incurred in the fixed part of the cellular network.
What I have gained after reading it: IDAMN is a distributed intrusion detection system for
cellular networks. IDAMN is able to have a complete overview on the mobile user telephony
activity and mobility behaviour. The main novelty of our architecture is its ability to transfer a
small user profile near the location of the serving MSC as opposed to existing systems which
require the reporting of large amount of audit data to a central monitoring entity. [6]
21
2.4.6 J6: Routing and Congestion Control in Common Channel Signalling System
No. 7
Signalling networks based on the Common Channel Signalling System No. 7 (SS7) protocol
provide a specialised packet switching network for transporting call control messages of
telecommunications networks. Two major differences distinguish these specialised packet
networks from classical packet switched networks: high performance for large volume of offered
traffic and high degree of reliability. The journal look into major and in most cases unique
traffic and route handling and management aspects of this protocol based on the International
Telegraph and Telephone Consultative Committee (CCITT), but highlighting the differences in
ANSI (American National Standards Institute that specifies the domestic version of the standard
for North America), to the extent possible. [7]
What I have gained after reading it: Look at the two important functions of routing and
congestion in signalling networks based on SS7. The procedures recommended to perform these
functions have taken into account the required reliability and performance of the signalling
networks.
J7: A Multiple Representation Entity-Based Approach to Hybrid Traffic
Simulation Model
Traffic simulation is a widely used tool to analyse dynamic traffic system. In traffic simulation
field, microscopic simulation offers detailed representation of traffic system, but it is difficult to
model large traffic network; Macroscopic and mesoscopic simulations can capture the dynamics
of large network, but only on a low level of details. These limitations of mono-resolution traffic
simulation emerge more clearly, as the development of its application. Multi-resolution traffic
simulation, which uses hybrid traffic simulation model, can overcome those limitations by
integrating traffic simulation models on different levels into a hybrid model, which combines
advantages of all composing models. [8]
22
What I have gained after reading it: Introduced UNIFY framework into traffic simulation and
developed UNITRANS, a Multiple Representation Entity-based (MRE-based) framework, to
integrate traffic simulation models on different resolution levels and maintain the consistency
among their jointly executing. A hybrid model was built using UNITRANS and a three-legged
intersection was modelled with it. The results showed that UNITRANS was feasible and
effective.
How can I implement into my project: UNIFY framework supplies an effective and flexible
approach to building HTSM and MRTSS. In our concise case study, UNITRANS works well.
Furthermore, there are still problems which are not fully considered in this paper, such as the
Dynamic Traffic Assignment or route choice.
23
3
OVERVIEW OF THE PROJECT
3.1 Project Management
Good project management plays a significant role in the completion of this project. This involves
proper planning and effective time management. Hence I have created a Gantt chart to help me
plan and keep track of my progress for the entire year. These are the 5 main stages of my project:
.
Stage 1: Getting Started
Stage 2: Review on Project Flow
Stage 3: Development of Software
Stage 4: Evaluation and Begin of Theses Writing
Stage 5: Oral and Poster Presentation
This is to ensure that the project works is done in a systematic and structured way as to ensure
project is developed smoothly. I have also set goals within my personal timetable to prevent any
clashes in my work and study time.
24
3.2 Gantt chart
The table below shows my Gantt chart:
25
3.3 Details of Gantt chart
3.3.1 Getting Started
This section is the first stage of my project, it is important to have a clear understanding of the
project background, the scope of my project, set objectives and goals, derive my design
strategies and lay out procedures to perform my testing.
3.3.2 Review on Project Flow
This section is the second stage of my project. The project preliminary task was to perform
research, gathered relevant research materials, deliberated with my supervisor and source for the
suitable type of program/ software to ensure that I am on the right track. Hence, the second stage
was research on the following items:
1. The Background of the GSM network
2. The Generation of the GSM network
3. The SCCP Routing and Congestion Control
4. Related Journals
3.3.3 Development of Software
This is the third stage of my project. I have to understand the concept of the open system
interconnection model whereby the module looks at the fundamentals of data communications,
inclusive of OSI layer modelling, the principles of operation of high speed broad band networks
and the rudiments of data network design. I had to apply the basic fundamental on wireless
communication technology that I had learnt during my polytechnic days. In addition to that, I
have to grasp on more depths about GSM network, introduce the general concepts of wireless
communication systems design and applications, and include Maxwell's equations and related
applications in wireless transmissions - radio propagation in different wireless mediums and
in/around buildings and performance/design issues related to wireless systems and media of
propagation.
26
3.3.4 Evaluation and Begin of Thesis Writing
This is the fourth stage of my project. After developing the software, I started consolidating all
the literature review, project management details, testing results and conclusions into my thesis.
Comments from my supervisor on the project, the solution implemented and whether it is
successful according to its intended design and layout objectives.
3.3.5 Oral and Poster Presentation
This is the final stage of my project where I summarise the entire project I will be presenting to
the public and examiner to demonstrate my understanding of the project.
27
4
METHODOLOGY
In this chapter, I will discuss on what is my design strategy. I have provided a brief comparison
among some of the software that I have researched from the internet and telecommunication
magazines. After careful consideration, I have selected the ideal software for my project.
4.1 Design Strategy
I have used a software application called Wireshark [9] for packet sniffers. It is appropriate
because looking at my project title: Roaming Traffic (Data) Monitoring System in the GSM
Network, it is almost impossible to come out with a hardware prototype.
Using software application, not only is it tidier and cleaner as compared to hardware, but it also
saves space since I only need a laptop to perform my testing. By connecting to the internet using
a router or a modem, there is basically no GSM network function to transmit data which my
project requires me to perform. Hence, to allow me to have GSM capability, I need to use a
mobile broadband device. Why do I need to have a mobile broadband device? As we all know,
most mobile broadband devices require a SIM card. All SIM cards have GSM network capability
and are also be able to connect to the internet. Sometimes, it is difficult to tap on wireless
network when I am in a public place. Having equipped with a mobile broadband device, I do not
have to worry about connecting to the internet and this allows me to do my project anytime,
anyplace.
Having said all the valid reasons of having a mobile broadband device, but where am I able to
get it from? Well, telecommunication service providers such as SingTel, M1 and Starhub do
provide mobile broadband devices. As I have mentioned earlier, with a mobile broadband device,
I am able to access to the GSM network. With that, I’m able to connect to the internet to perform
my data collection through the GSM network. I can retrieve and analyse the data that I have
collected and classified them to different categories for discussion.
Next, from the data that I have collected, I have updated them in a graph and listed them to
review what the GSM network is actually doing during transmitting and receiving. This project
enabled me to apply data communication for packet analysing during my testing of data, giving
28
me a better understanding in different protocol structures and its operation. During this process, I
have recapped on a lot of fundamentals and it helped me to complete data capturing.
4.2 Software Comparisons
I did some research on various software related applications through the internet and magazines
on telecommunications. I have shortlisted some and made comparison based on the supported
protocols, program support, user friendliness the operating system support and finally the cost. In
the next section, I gave my final software decision for my project. The table below shows the list
of software that I found suitable for my project:
Software
NTOP
Colasoft Packet Analyzer
Wireshark
Purchase of Software
Yes
Yes
No (Open Source)
Download
Yes (Trial)
Yes (Trial)
Yes (Full Version)
Supported Protocols
Limited
Some
Yes
Program Support
Limited
Some
Yes
Yes
Yes
Yes
User-Friendly
No
No
Yes
Level of Difficulty
High
High
Medium
License Required
Yes
Yes
No
Renewal of Software
Yes
Yes
No
Limitation of Users
1 User
1 User
Unlimited Users
Maintenance
Unknown
Unknown
Actively Maintained
Source Code Viewing
No
No
Yes
Operating System
Support
29
4.3 Technology Being Used
After looking at the different software pro and cons, I have chosen Wireshark to be my ideal
software application.
Wireshark is a network analyser. It reads packets from the network, decodes and presents them
in an easy to understand format. One of the most important aspects of Wireshark is that it is an
open source - actively maintained and free. The following lists below are some of the other
important aspects of Wireshark:
It is distributed under the Gnu’s Not UNIX (GNU) General Public License (GPL) open
source license.
It works in promiscuous and non promiscuous modes.
It can capture data from the network or read from a capture file.
It has an easy to read and configurable GUI.
It has rich display capabilities.
It supports tcpdump format captures filters. It has a feature that reconstructs a
Transmission Control Protocol (TCP) session and displays it in American Standard Code
for Information Interchange (ASCII), Extended Binary Coded Decimal Interchange Code
(EBCDIC), hexadecimal (hex) dump or D arrays.
It is available in precompiled binaries and source code.
It supports over 750 protocols and as it is an open source, new ones are contributed
frequently.
It can save capture files in a variety of formats (e.g. libpcap, Network Associates Sniffer,
Microsoft Network Monitor (NetMon) and Sun snoop.
It includes a command line version of the network analyzer called tshark.
It includes a variety of supporting programs such as editcap, mergecap and text2pcap.
30
A brief history on how Wireshark came about. N 1997, Gerald Combs first developed Ethereal;
why did he want to do this? The reason was because he was expanding his knowledge of
networking and needed a tool for network troubleshooting. The first version (0.2.0) was released
in July 1998. A development team which includes Gilbert Rameirez, Guy Harris and Richard
Sharpe, quickly formed to provide patches, enhancements and additional dissectors. Dissectors
are what allow Wireshark to decode individual’s protocols and present them in readable format.
Since then, a large number of individuals have contributed specific protocols dissectors and other
enhancement to Wireshark.
31
5
EXPERIMENTAL PROCEDURE
5.1 Capture of Data
Firstly, I connected the mobile broadband device to my laptop as shown in the diagram below:
Step 1: Open the Wireshark application.
32
Step 2: Begin to capture data through the GSM network.
Step 3: Stop the capturing of data.
33
5.2 Analyse of Data
Basically, I spent most of my time in the Wireshark main window. This is where all of the
captured packets are displayed and broken down into a more understandable format. Using the
packet that I just made, let’s take a look at the Wireshark main window which contains three
panes.
The three panes in the main window depend on one another as shown in the diagram below:
Packet List Pane
Packet Details Pane
Packet Byte Pane
34
5.2.1 Packet List Pane
It displays a table containing all the packets in the current capture file. It contains the total packet
number, the relative time the packet was captured, the source and destination, the protocol and
other general information.
5.2.2 Packet Details Pane
It displays a hierarchical of information about a single packet. It can be collapsed and expanded
to show all the information collected about an individual packet.
5.2.3 Packet Byte Pane
It displays its raw and unprocessed form. It shows what the packet looks like when it travels
across the wire. This is raw information with nothing warm or fuzzy to make it easier to follow.
35
5.3 Flow Chart
Start
Capture of Data
No
Correct Data?
Yes
Filter of Required Data
No
Correct Data?
Yes
Display Data to Graph
End
36
6
RESULTS AND DISCUSSIONS
6.1 Data Collected
This is the data which I had collected when opening up Wikipedia website (www.wikipedia.org):
Figure 6a: Data Collected Using Wireshark
The status shows the total numbers of different protocols which have been transmitted from the
source to the destination and the number of packets that are sent and received from the
destination back to the source.
37
6.1.1 Graphs
6b: Graph for Data Collected
6.2 Test Results
The test results can be found in the Appendix section.
From the data that I have collected, I noticed that TCP, HTTP and DNS have the most of volume
of data being captured. Just by clicking into the internet, I received hundreds of packets in just a
few seconds. It is one of the important protocols for data transmission. I like to discuss the most
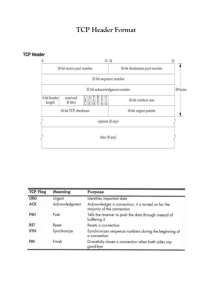
packets that had been capture: TCP. It uses a sequence number to identify each byte of data. The
sequence number identifies the order of the bytes sent from each computer so that the data can be
reconstructed in order, regardless of any fragmentation, disordering, or packet loss that may
occur during transmission.
38
For every payload byte transmitted the sequence number must be incremented. In the first two
steps of the 3-way handshake, both computers exchange an initial sequence number (ISN). This
number can be arbitrary, and should in fact be unpredictable, in order to avoid a TCP Sequence
Prediction Attack.
TCP primarily uses a cumulative acknowledgment scheme, where the receiver sends an
acknowledgment signifying that the receiver has received all data preceding the acknowledged
sequence number. Essentially, the first byte in a segment's data field is assigned a sequence
number, which is inserted in the sequence number field, and the receiver sends an
acknowledgment specifying the sequence number of the next byte they expect to receive.
TCP Header
Bit
offse
t
0
0
1
2
3
4
5
6
7
8
9
1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
Source port
Sequence number
64
Acknowledgment number
128
160
...
C
W
R
E
C
E
2
2
2
3
2
4
2
5
2
6
Destination port
32
96 Data offset Reserved
2
1
U
R
G
A
C
K
P
S
H
R
S
T
S
Y
N
F
I
N
Checksum
Window Size
Urgent pointer
Options (if Data Offset > 5)
...
Figure 6a: Layout of TCP [10]
39
2
7
2
8
2
9
3
0
3
1
Figure 6b: The Function of TCP
40
7
LIMITATION AND CONCLUSION
7.1 Limitation
Due to insufficient support of proper tooling and equipments, I was unable to have a real live
demonstration of collecting precise data through the GSM network. Therefore, I’m only able to
perform a simulation with my laptop. As not being software proficient, performing software
testing is a major obstacle in completing my project where I had to commit a lot of time to
ensure that I could finish my project in time.
7.2 Risk Assessment
Since Wireshark is an open source application, it is frequently maintained by different
developers who are using this application. Therefore, there is basically no risk involved for the
application to be unstable. It is safe to use and there is also a question and answer section to help
new users who are interested in Wireshark to use the program and perform without any difficulty.
7.3 Future Discussion
I like to suggest that for future mobile developers, they may like to focus more on TCP
transmission. As observed from the data captured in the appendix section, there are quite a
number of TCP packets that were either lost or had not been transmitted. This causes mobile
subscribers have to wait to be able to serve the GSM network which much precious time had
been wasted.
41
7.4 Conclusion
In this project, I have gained a lot in terms of project management as well and software
knowledge. Being weak in software, I have spent a majority of my time to understand Wireshark
application. With diligence and perseverance, I finally manage to grasp the gist on how to
capture the data used in this application. It was a breakthrough for me.
In the world today, there is hardly any hardware being invented for network system. Hence, I
appreciate how the data can be transmitted through the GSM network. As I had mention under
the Analysing of Data section, accessing a webpage requires the usage of quite a huge amount of
packets and protocols. As I am not in the telecommunication industry, it is a big challenge for me
to handle this project. I am delighted to be able to achieve my objectives for my project.
42
8
CRITICAL REFLECTIONS
In the beginning of my project, I am totally clueless on how to start. For the first half of the year,
I had been searching for answers. This is where my supervisor, Mr Nava offered me some
pointers on how to kick start my project. I have learnt a lot on time management skills and
researched on journals. Looking for correct materials have been very crucial as it determines
whether I am on the right track and able to progress further. Besides that, I had learnt a great deal
on how to read and analyse on the different packets of data which were sent through the GSM
network. Unfortunately due to time constrain, I am only able to collect and interpret the data on
the fundamental stage. If I were given another opportunity, I am confident that I can progress to
a higher level.
Compared with the goals set in TMA01, I have met my targeted goals and am able to complete
my project in time. The biggest breakthrough is able to come out with the appropriate software
for my project. As not being software proficient, I had a hard time understanding on what I am
going to do for my project. Nevertheless, with a great interest in the telecommunication
technology, I have spent most of my time in understanding the terms and solutions on how to
complete my project through sources from the internet as well as from the libraries in NTU and
NUS.
Another major obstacle is without the correct equipment and tooling, I am not able to collect the
precise data. Therefore, as an alternative, I had to use my laptop as a simulation for data
collection through the GSM network.
43
9
REFERENCES
[1] R. Goldberg and D. Shrader, “Common channel signaling interface for local exchange carrier
to interexchange carrier interconnection”, IEEE Communication Magazine, volume 28, July
1990
[2] Juan Ventura Agustina, Peng Zhang and Raimo Kantola, “IEEE Journal”, Proceedings of the
Eighth IEEE International Symposium on Computers and Communication (ISCC’03), 2003
[3] David McMillian and Michael Rumsewwicz, “IEEE Journal”, 1996
[4] Joachim Zepf and Gerhard Rufa, “IEEE Journal”, IEEE JOURNAL ON SELECTED AREAS
IN COMMUNICATIONS, VOL. 12, NO. 3, APRIL 1994
[5] Chunsheng Xin, “IEEE Journal”, IEEE JOURNAL ON SELECTED AREAS IN
COMMUNICATIONS, VOL. 25, NO. 9, DECEMBER 2007
[6] Didier Samfat, Refik Molva, “INSTITUT EURÉCOM”, INSTITUT EURÉCOM 2229, route
des Crêtes, BP 193 06904 Sophia Antipolis, FRANCE
[7] Bijan Jabbari, “IEEE Journal”, PROCEEDINGS OF THE IEEE. VOL.80.NO. 4, APRIL
1992
[8] Huang Weinan, Sun Jian and Li Keping, “IEEE Journal”, 2008 International Conference on
Information Management, Innovation Management and Industrial Engineering, 2003
[9] www.wireshark.org
[10] www.wikipedia.org
44
9.1 Appendixes
9.1.1 Test Results Data from Wireshark
No.
Source
Destination
Protocol
Info
1
Time
0:00:00
113.10.120.132
203.116.1.78
DNS
Standard query A www.google.com.sg
2
0:00:00
113.10.120.132
203.116.1.78
DNS
Standard query A www.google.com.sg
3
9:22:30
113.10.120.132
203.116.1.78
DNS
Standard query A www.google.com.sg
4
9:45:00
113.10.120.132
203.116.1.78
DNS
Standard query A www.pipi.cn
5
16:30:00
203.116.1.78
113.10.120.132
DNS
Standard query response CNAME www.google.com CNAME www.l.google.com A 216.239.61.104
6
16:30:00
203.116.1.78
113.10.120.132
DNS
Standard query response CNAME www.google.com CNAME www.l.google.com A 216.239.61.104
7
16:30:00
203.116.1.78
113.10.120.132
DNS
Standard query response A 121.12.120.14 A 122.225.100.84 A 121.12.120.6 A 121.12.120.9 A 121.12.120.10 A 121.12.
8
16:52:30
203.116.1.78
113.10.120.132
DNS
Standard query response CNAME www.google.com CNAME www.l.google.com A 216.239.61.104
9
18:00:00
113.10.120.132
121.12.120.14
TCP
autonoc > http [SYN] Seq=0 Win=64380 Len=0 MSS=1460 WS=0 TSV=0 TSER=0
10
19:52:30
113.10.120.132
216.239.61.104
TCP
mxomss > http [SYN] Seq=0 Win=64380 Len=0 MSS=1460 WS=0 TSV=0 TSER=0
11
22:30:00
216.239.61.104
113.10.120.132
TCP
http > mxomss [SYN, ACK] Seq=0 Ack=1 Win=5720 Len=0 MSS=1430 WS=6
12
22:30:00
113.10.120.132
216.239.61.104
TCP
mxomss > http [ACK] Seq=1 Ack=1 Win=64380 Len=0
13
22:30:00
113.10.120.132
216.239.61.104
HTTP
GET / HTTP/1.1
14
3:22:30
121.12.120.14
113.10.120.132
TCP
http > autonoc [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS=1460 WS=3
15
3:22:30
113.10.120.132
121.12.120.14
TCP
autonoc > http [ACK] Seq=1 Ack=1 Win=64380 Len=0
16
3:22:30
113.10.120.132
121.12.120.14
HTTP
GET /pfup/jfcheck/jfcheck.conf HTTP/1.1
17
5:37:30
216.239.61.104
113.10.120.132
TCP
http > mxomss [ACK] Seq=1 Ack=290 Win=6848 Len=0
18
7:30:00
216.239.61.104
113.10.120.132
TCP
[TCP Previous segment lost] [TCP segment of a reassembled PDU]
19
7:30:00
113.10.120.132
216.239.61.104
TCP
[TCP Dup ACK 13#1] mxomss > http [ACK] Seq=290 Ack=1 Win=64380 Len=0 SLE=2861 SRE=4291
20
7:30:00
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
21
7:30:00
113.10.120.132
216.239.61.104
TCP
[TCP Dup ACK 13#2] mxomss > http [ACK] Seq=290 Ack=1 Win=64380 Len=0 SLE=2861 SRE=4554
22
7:52:30
216.239.61.104
113.10.120.132
TCP
[TCP Retransmission] [TCP segment of a reassembled PDU]
23
7:52:30
113.10.120.132
216.239.61.104
TCP
[TCP Dup ACK 13#3] mxomss > http [ACK] Seq=290 Ack=1 Win=64380 Len=0 SLE=1431 SRE=4554
24
8:15:00
216.239.61.104
113.10.120.132
TCP
[TCP Fast Retransmission] [TCP segment of a reassembled PDU]
25
8:15:00
113.10.120.132
216.239.61.104
TCP
mxomss > http [ACK] Seq=290 Ack=4554 Win=64380 Len=0
26
10:30:00
216.239.61.104
113.10.120.132
TCP
[TCP Retransmission] [TCP segment of a reassembled PDU]
27
10:30:00
113.10.120.132
216.239.61.104
TCP
[TCP Dup ACK 25#1] mxomss > http [ACK] Seq=290 Ack=4554 Win=64380 Len=0
28
14:37:30
121.12.120.14
113.10.120.132
TCP
http > autonoc [ACK] Seq=1 Ack=422 Win=6912 Len=0
29
16:07:30
121.12.120.14
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
30
20:15:00
113.10.120.132
121.12.120.14
TCP
autonoc > http [ACK] Seq=422 Ack=1461 Win=64380 Len=0
31
3:45:00
113.10.120.132
216.239.61.104
HTTP
GET /images/close_sm.gif HTTP/1.1
32
4:07:30
113.10.120.132
216.239.61.104
TCP
imyx > http [SYN] Seq=0 Win=64380 Len=0 MSS=1460 WS=0 TSV=0 TSER=0
33
5:15:00
121.12.120.14
113.10.120.132
TCP
[TCP Previous segment lost] [TCP segment of a reassembled PDU]
34
5:15:00
113.10.120.132
121.12.120.14
TCP
[TCP Dup ACK 30#1] autonoc > http [ACK] Seq=422 Ack=1461 Win=64380 Len=0 SLE=2921 SRE=3433
35
8:15:00
216.239.61.104
113.10.120.132
TCP
http > mxomss [ACK] Seq=4554 Ack=852 Win=7936 Len=0
36
8:15:00
216.239.61.104
113.10.120.132
TCP
http > imyx [SYN, ACK] Seq=0 Ack=1 Win=5720 Len=0 MSS=1430 WS=6
37
8:15:00
113.10.120.132
216.239.61.104
TCP
imyx > http [ACK] Seq=1 Ack=1 Win=64380 Len=0
38
8:15:00
113.10.120.132
216.239.61.104
HTTP
GET /images/chrome_48.gif HTTP/1.1
39
9:00:00
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
40
9:00:00
216.239.61.104
113.10.120.132
HTTP
HTTP/1.1 200 OK (GIF89a)
41
9:00:00
113.10.120.132
216.239.61.104
TCP
mxomss > http [ACK] Seq=852 Ack=4902 Win=64032 Len=0
42
12:45:00
216.239.61.104
113.10.120.132
TCP
http > imyx [ACK] Seq=1 Ack=564 Win=6848 Len=0
43
13:07:30
216.239.61.104
113.10.120.132
TCP
[TCP Previous segment lost] [TCP segment of a reassembled PDU]
44
13:07:30
113.10.120.132
216.239.61.104
TCP
[TCP Dup ACK 38#1] imyx > http [ACK] Seq=564 Ack=1 Win=64380 Len=0 SLE=276 SRE=1706
45
45
13:07:30
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
46
13:07:30
113.10.120.132
216.239.61.104
TCP
[TCP Dup ACK 38#2] imyx > http [ACK] Seq=564 Ack=1 Win=64380 Len=0 SLE=276 SRE=2726
47
13:07:30
216.239.61.104
113.10.120.132
TCP
[TCP Fast Retransmission] [TCP segment of a reassembled PDU]
48
13:07:30
113.10.120.132
216.239.61.104
TCP
imyx > http [ACK] Seq=564 Ack=2726 Win=64380 Len=0
49
15:00:00
113.10.120.132
216.239.61.104
HTTP
GET /images/modules/buttons/g-button-chocobo-basic-1.gif HTTP/1.1
50
18:45:00
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
51
19:07:30
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
52
19:07:30
113.10.120.132
216.239.61.104
TCP
mxomss > http [ACK] Seq=1446 Ack=6608 Win=64380 Len=0
53
19:30:00
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
54
20:37:30
113.10.120.132
203.116.1.78
DNS
Standard query A g.microsoft.com
55
21:22:30
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
56
21:22:30
113.10.120.132
216.239.61.104
TCP
mxomss > http [ACK] Seq=1446 Ack=9468 Win=64380 Len=0
57
21:45:00
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
58
23:15:00
203.116.1.78
113.10.120.132
DNS
Standard query response CNAME g.msn.com CNAME g.msn.com.nsatc.net A 207.46.216.54
59
23:15:00
113.10.120.132
207.46.216.54
TCP
x9-icue > http [SYN] Seq=0 Win=64380 Len=0 MSS=1460 WS=0 TSV=0 TSER=0
60
0:22:30
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
61
0:22:30
113.10.120.132
216.239.61.104
TCP
mxomss > http [ACK] Seq=1446 Ack=12328 Win=64380 Len=0
62
0:22:30
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
63
1:07:30
113.10.120.132
216.239.61.104
HTTP
GET /images/modules/buttons/g-button-chocobo-basic-2.gif HTTP/1.1
64
3:00:00
216.239.61.104
113.10.120.132
HTTP
HTTP/1.1 200 OK (GIF89a)
65
3:00:00
113.10.120.132
216.239.61.104
TCP
mxomss > http [ACK] Seq=1446 Ack=14165 Win=64380 Len=0
66
3:00:00
113.10.120.132
216.239.61.104
HTTP
GET /intl/en_com/images/logo_plain.png HTTP/1.1
67
4:52:30
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
68
4:52:30
216.239.61.104
113.10.120.132
HTTP
HTTP/1.1 200 OK (GIF89a)
69
4:52:30
113.10.120.132
216.239.61.104
TCP
imyx > http [ACK] Seq=1158 Ack=3314 Win=63792 Len=0
70
6:45:00
207.46.216.54
113.10.120.132
TCP
http > x9-icue [SYN, ACK] Seq=0 Ack=1 Win=8190 Len=0 MSS=1460
71
6:45:00
113.10.120.132
207.46.216.54
TCP
x9-icue > http [ACK] Seq=1 Ack=1 Win=64380 Len=0
72
6:45:00
113.10.120.132
207.46.216.54
HTTP
GET /_0sfdata/1?CG={2CEDBFBC-DBA8-43AA-B1FD-CC8E6316E3E2}&DV=8.0.6001.9&OS=5.1.2600.3.0&BL=en-us&
73
7:07:30
113.10.120.132
216.239.61.104
HTTP
GET /extern_js/f/CgJlbhICc2crMAo4NiwrMA44BywrMBY4ECwrMBc4AywrMBg4BCwrMBk4CywrMCU4yYgBLCswJjgFLC
74
7:52:30
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
75
8:37:30
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
76
8:37:30
113.10.120.132
216.239.61.104
TCP
mxomss > http [ACK] Seq=2022 Ack=15870 Win=64380 Len=0
77
8:37:30
216.239.61.104
113.10.120.132
TCP
[TCP Previous segment lost] [TCP segment of a reassembled PDU]
78
8:37:30
113.10.120.132
216.239.61.104
TCP
[TCP Dup ACK 76#1] mxomss > http [ACK] Seq=2022 Ack=15870 Win=64380 Len=0 SLE=17300 SRE=18536
79
9:00:00
216.239.61.104
113.10.120.132
TCP
[TCP Retransmission] [TCP segment of a reassembled PDU]
80
9:00:00
113.10.120.132
216.239.61.104
TCP
mxomss > http [ACK] Seq=2022 Ack=18536 Win=64380 Len=0
81
13:30:00
216.239.61.104
113.10.120.132
TCP
[TCP Previous segment lost] [TCP segment of a reassembled PDU]
82
13:30:00
113.10.120.132
216.239.61.104
TCP
[TCP Dup ACK 80#1] mxomss > http [ACK] Seq=2022 Ack=18536 Win=64380 Len=0 SLE=19966 SRE=21396
83
13:30:00
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
84
13:30:00
113.10.120.132
216.239.61.104
TCP
[TCP Dup ACK 80#2] mxomss > http [ACK] Seq=2022 Ack=18536 Win=64380 Len=0 SLE=19966 SRE=22022
85
13:52:30
216.239.61.104
113.10.120.132
HTTP
[TCP Fast Retransmission] HTTP/1.1 200 OK (PNG)
86
13:52:30
113.10.120.132
216.239.61.104
TCP
mxomss > http [ACK] Seq=2022 Ack=22022 Win=64380 Len=0
87
13:52:30
216.239.61.104
113.10.120.132
TCP
http > imyx [ACK] Seq=3314 Ack=1822 Win=9408 Len=0
88
14:37:30
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
89
14:37:30
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
90
14:37:30
113.10.120.132
216.239.61.104
TCP
imyx > http [ACK] Seq=1822 Ack=6174 Win=64380 Len=0
91
14:37:30
121.12.120.14
113.10.120.132
TCP
http > autonoc [FIN, ACK] Seq=3433 Ack=422 Win=6912 Len=0
92
14:37:30
113.10.120.132
121.12.120.14
TCP
[TCP Dup ACK 30#2] autonoc > http [ACK] Seq=422 Ack=1461 Win=64380 Len=0 SLE=2921 SRE=3434
93
14:37:30
216.239.61.104
113.10.120.132
TCP
[TCP segment of a reassembled PDU]
94
16:30:00
207.46.216.54
113.10.120.132
HTTP
HTTP/1.1 204 No Content
46
9.2 Source Code
These sources codes are complied for the application of Wireshark.
9.2.1 Capture Data
/* capture.c
* Routines for packet capture
#ifdef HAVE_CONFIG_H
# include "config.h"
#endif
#ifdef HAVE_LIBPCAP
#ifdef HAVE_UNISTD_H
#include <unistd.h>
#endif
#include <stdlib.h>
#include <string.h>
#include <ctype.h>
#ifdef HAVE_FCNTL_H
#include <fcntl.h>
#endif
#ifdef HAVE_SYS_TYPES_H
#include <sys/types.h>
#endif
#ifdef HAVE_NETINET_IN_H
#include <netinet/in.h>
#endif
#ifdef HAVE_NETDB_H
#include <netdb.h>
#endif
#ifdef HAVE_ARPA_INET_H
#include <arpa/inet.h>
#endif
47
#ifdef HAVE_SYS_SOCKET_H
#include <sys/socket.h>
/* needed to define AF_ values on UNIX */
#endif
#ifdef HAVE_WINSOCK2_H
#include <winsock2.h>
/* needed to define AF_ values on Windows */
#endif
#ifdef NEED_INET_V6DEFS_H
# include "inet_v6defs.h"
#endif
#include <signal.h>
#include <errno.h>
#include <glib.h>
#include <epan/packet.h>
#include <epan/dfilter/dfilter.h>
#include "file.h"
#include "capture.h"
#include "capture_sync.h"
#include "capture_info.h"
#include "capture_ui_utils.h"
#include "util.h"
#include "capture-pcap-util.h"
#include "alert_box.h"
#include "simple_dialog.h"
#include <epan/prefs.h>
#ifdef _WIN32
#include "capture-wpcap.h"
#endif
#include "ui_util.h"
#include "wsutil/file_util.h"
#include "log.h"
48
typedef struct if_stat_cache_item_s {
char *name;
struct pcap_stat ps;
} if_stat_cache_item_t;
struct if_stat_cache_s {
int stat_fd;
int fork_child;
GList *cache_list; /* List of if_stat_chache_entry_t */
};
/* this callback mechanism should possibly be replaced by the g_signal_...() stuff (if I only
would know how :-) */
typedef struct {
capture_callback_t cb_fct;
gpointer user_data;
} capture_callback_data_t;
static GList *capture_callbacks = NULL;
static void
capture_callback_invoke(int event, capture_options *capture_opts)
{
capture_callback_data_t *cb;
GList *cb_item = capture_callbacks;
/* there should be at least one interested */
g_assert(cb_item != NULL);
while(cb_item != NULL) {
cb = cb_item->data;
cb->cb_fct(event, capture_opts, cb->user_data);
cb_item = g_list_next(cb_item);
}
}
void
49
capture_callback_add(capture_callback_t func, gpointer user_data)
{
capture_callback_data_t *cb;
cb = g_malloc(sizeof(capture_callback_data_t));
cb->cb_fct = func;
cb->user_data = user_data;
capture_callbacks = g_list_append(capture_callbacks, cb);
}
void
capture_callback_remove(capture_callback_t func)
{
capture_callback_data_t *cb;
GList *cb_item = capture_callbacks;
while(cb_item != NULL) {
cb = cb_item->data;
if(cb->cb_fct == func) {
capture_callbacks = g_list_remove(capture_callbacks, cb);
g_free(cb);
return;
}
cb_item = g_list_next(cb_item);
}
g_assert_not_reached();
}
50
9.2.2 Start Capture
/**
* Start a capture.
*
* @return TRUE if the capture starts successfully, FALSE otherwise.
*/
gboolean
capture_start(capture_options *capture_opts)
{
gboolean ret;
/* close the currently loaded capture file */
cf_close(capture_opts->cf);
g_assert(capture_opts->state == CAPTURE_STOPPED);
capture_opts->state = CAPTURE_PREPARING;
g_log(LOG_DOMAIN_CAPTURE, G_LOG_LEVEL_MESSAGE, "Capture Start ...");
/* try to start the capture child process */
ret = sync_pipe_start(capture_opts);
if(!ret) {
if(capture_opts->save_file != NULL) {
g_free(capture_opts->save_file);
capture_opts->save_file = NULL;
}
g_log(LOG_DOMAIN_CAPTURE, G_LOG_LEVEL_MESSAGE, "Capture Start failed!");
capture_opts->state = CAPTURE_STOPPED;
} else {
/* the capture child might not respond shortly after bringing it up */
/* (for example: it will block if no input arrives from an input capture pipe (e.g. mkfifo)) */
/* to prevent problems, bring the main GUI into "capture mode" right after a successful */
/* spawn/exec of the capture child, without waiting for any response from it */
51
capture_callback_invoke(capture_cb_capture_prepared, capture_opts);
if(capture_opts->show_info)
capture_info_open(capture_opts);
}
return ret;
}
void
capture_stop(capture_options *capture_opts)
{
g_log(LOG_DOMAIN_CAPTURE, G_LOG_LEVEL_MESSAGE, "Capture Stop ...");
capture_callback_invoke(capture_cb_capture_stopping, capture_opts);
/* stop the capture child gracefully */
sync_pipe_stop(capture_opts);
}
void
capture_restart(capture_options *capture_opts)
{
g_log(LOG_DOMAIN_CAPTURE, G_LOG_LEVEL_MESSAGE, "Capture Restart");
capture_opts->restart = TRUE;
capture_stop(capture_opts);
}
void
capture_kill_child(capture_options *capture_opts)
{
g_log(LOG_DOMAIN_CAPTURE, G_LOG_LEVEL_INFO, "Capture Kill");
/* kill the capture child */
sync_pipe_kill(capture_opts->fork_child);
}
/* We've succeeded in doing a (non real-time) capture; try to read it into a new capture file */
static gboolean
52
capture_input_read_all(capture_options
*capture_opts,
gboolean
is_tempfile,
gboolean
drops_known,
guint32 drops)
{
int err;
/* Capture succeeded; attempt to open the capture file. */
if (cf_open(capture_opts->cf, capture_opts->save_file, is_tempfile, &err) != CF_OK) {
/* We're not doing a capture any more, so we don't have a save file. */
return FALSE;
}
9.2.3 Filter Data
/* Set the read filter to NULL. */
/* XXX - this is odd here; try to put it somewhere where it fits better */
cf_set_rfcode(capture_opts->cf, NULL);
/* Get the packet-drop statistics.
XXX - there are currently no packet-drop statistics stored
in libpcap captures, and that's what we're reading.
At some point, we will add support in Wiretap to return
packet-drop statistics for capture file formats that store it,
and will make "cf_read()" get those statistics from Wiretap.
We clear the statistics (marking them as "not known") in
"cf_open()", and "cf_read()" will only fetch them and mark
them as known if Wiretap supplies them, so if we get the
statistics now, after calling "cf_open()" but before calling
"cf_read()", the values we store will be used by "cf_read()".
If a future libpcap capture file format stores the statistics,
we'll put them into the capture file that we write, and will
thus not have to set them here - "cf_read()" will get them from
the file and use them. */
53
if (drops_known) {
cf_set_drops_known(capture_opts->cf, TRUE);
/* XXX - on some systems, libpcap doesn't bother filling in
"ps_ifdrop" - it doesn't even set it to zero - so we don't
bother looking at it.
Ideally, libpcap would have an interface that gave us
several statistics - perhaps including various interface
error statistics - and would tell us which of them it
supplies, allowing us to display only the ones it does. */
cf_set_drops(capture_opts->cf, drops);
}
9.2.4 Read Data
/* read in the packet data */
switch (cf_read(capture_opts->cf)) {
case CF_READ_OK:
case CF_READ_ERROR:
/* Just because we got an error, that doesn't mean we were unable
to read any of the file; we handle what we could get from the
file. */
break;
case CF_READ_ABORTED:
/* User wants to quit program. Exit by leaving the main loop,
so that any quit functions we registered get called. */
main_window_nested_quit();
return FALSE;
}
/* if we didn't capture even a single packet, close the file again */
if(cf_get_packet_count(capture_opts->cf) == 0 && !capture_opts->restart) {
simple_dialog(ESD_TYPE_INFO, ESD_BTN_OK,
54
"%sNo packets captured!%s\n"
"\n"
"As no data was captured, closing the %scapture file!\n"
"\n"
"\n"
"Help about capturing can be found at:\n"
"\n"
"
http://wiki.wireshark.org/CaptureSetup"
#ifdef _WIN32
"\n\n"
"Wireless (Wi-Fi/WLAN):\n"
"Try to switch off promiscuous mode in the Capture Options!"
#endif
"",
simple_dialog_primary_start(), simple_dialog_primary_end(),
(cf_is_tempfile(capture_opts->cf)) ? "temporary " : "");
cf_close(capture_opts->cf);
}
return TRUE;
}
55