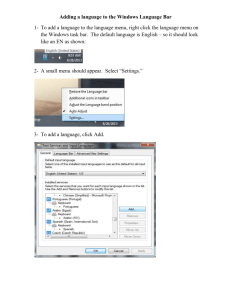
Lotus Development Corporation v. Borland International: The United
advertisement

1349 LOTUS DEVELOPMENT CORPORATION v. BORLAND INTERNATIONAL: THE UNITED STATES COURT OF APPEALS FOR THE FIRST CIRCUIT TAKES A STEP BACKWARD FOR THE COPYRIGHT PROTECTION OF COMPUTER PROGRAMS Since Congress has elected to grant certain exclusive rights to the owner of a copyright in a protected work, it is virtually axiomatic that the public interest can only be served by upholding copyright protections and, correspondingly, preventing the misappropriation of the skills, creative energies, and resources which are invested in the protected work.' INTRODUCTION Article I, section 8 of the United States Constitution gives Congress the power to provide copyright protection for the works of inventors and authors. 2 The economic philosophy underlying this provision is that the public welfare will be promoted best by encouraging individual effort.3 Thus, copyright protection extends to the expression of an idea and not to the idea itself.4 Copyright law seeks to balance the advancement of individual incentive through safeguarding one's work with a limited scope of protection, so that the stagnation of monopolies may be avoided. 5 Typically, courts faced with a copyright infringement action involving a computer program will initially identify the elements of the copyrighted work that are the proper subject matter for copyright protection. 6 Next, courts will determine whether these elements are sub1. Apple Computer, Inc. v. Franklin Computer Corp., 714 F.2d 1240, 1255 (3d Cir. 1983) (quoting Klitzner Indus., Inc. v. H.K James & Co., 535 F. Supp. 1249, 1259-60 (E.D. Pa. 1982)). 2. U.S. CoNsT. art. I, § 8, cl. 8. This clause grants Congress the power "to promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries." Id. 3. Computer Assocs. Intl, Inc. v. Altai, Inc., 982 F.2d 693, 696 (2nd Cir. 1992). 4. Ashton-Tate Corp. v. Ross, 728 F. Supp. 597, 601 (N.D. Cal. 1989), affd, 916 F.2d 516 (9th Cir. 1990). 5. Computer Assocs. Int'l, Inc., 982 F.2d at 696. 6. Autoskill, Inc. v. National Educ. Support Sys., Inc., 994 F.2d 1476, 1497 (10th Cir. 1993); MiTek Holdings, Inc. v. Arce Eng'g Co., Inc., 864 F. Supp. 1568, 1575 (S.D. Fla. 1994), affd 89 F.3d 1548 (11th Cir. 1996); Digital Communications Assocs., Inc. v. Softklone Distrib. Corp., 659 F. Supp. 449, 464 (N.D. Ga. 1987). 1350 CREIGHTON LAW REVIEW [Vol. 30 stantially similar to portions of the allegedly infringing work. 7 When faced with the protectable elements of two computer programs that are substantially similar, courts have determined that copyright infringement has occurred.8 In Lotus Development Corporationv. Borland International,Inc. 9 the United States Court of Appeals for the First Circuit held that the menu command hierarchy of the Lotus 1-2-3 spreadsheet computer program ("Lotus 1-2-3"), a part of the user interface, could not be protected by copyright. 10 The First Circuit found that the menu command hierarchy was a "method of operation" for which copyright protection is not available.1 1 As a result, the court ruled that no copyright infringement occurred when Borland International, Inc. placed "'a virtually identical copy" of the Lotus 1-2-3 menu tree in its Quat12 tro and Quattro Pro spreadsheet programs. Initially, this Note will address the First Circuit's conclusion that the Lotus 1-2-3 menu command hierarchy is a "method of operation" and not entitled to copyright protection. 13 This Note will then briefly discuss computers, computer programs, and copyright law.' 4 Next, this Note will review other cases involving the copyright protection afforded computer programs and discuss the elements of a copyright infringement claim, noting the tests currently applied by the courts to 7. Autoskill, Inc., 994 F.2d at 1496-98; MiTek Holdings, Inc., 864 F. Supp. at 1579-80; Digital Communications Assocs., Inc., 659 F. Supp. at 464-65. 8. DigitalCommunicationsAssocs., Inc., 659 F. Supp. at 465; Whelan Assocs., Inc. v. Jaslow Dental Lab., Inc., 797 F.2d 1222, 1248 (3d Cir. 1986); E.F. Johnson Co. v. Uniden Corp. of Am., 623 F. Supp 1485, 1493 (D. Minn. 1985). For a complete discussion of the doctrines that may preclude copyright protection despite a finding of substantial similarity, see infra notes 75-79 and accompanying text. 9. 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). 10. Lotus Dev. Corp. v. Borland Intl, Inc., 49 F.3d 807, 813, 819 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). A user interface: involves a system of menus, each menu consisting of less than a dozen commands, arranged hierarchically, forming a tree in which the main menu is the root/trunk of the tree and submenus branch off from higher menus, each submenu being linked to a higher menu by operation of a command, so that all the specific spreadsheet operations available in Lotus 1-2-3 are accessible through the paths of the menu command hierarchy. Lotus Dev. Corp. v. Borland Intl, Inc., 799 F. Supp. 203, 216 (D. Mass 1992), rev'd, 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). Author's note: hereinafter this case will be referred to as Borland II. Computer programs are subject to copyright protection as literary works. Lotus Dev. Corp. v. Paperback Software Int'l, 740 F. Supp. 37, 49 (D. Mass. 1990) (citing 17 U.S.C. § 101 (1988)). 11. Lotus Dev. Corp., 49 F.3d at 815. Title 17 of the United States Code section 102(b) prohibits the copyright protection of methods of operation. 17 U.S.C. § 102(b) (1994). See infra notes 30, 39-43, 94-98 and accompanying text. 12. Lotus Dev. Corp., 49 F.3d at 810, 819. 13. See infra notes 17-43 and accompanying text. 14. See infra notes 44-98 and accompanying text. 1997] COPYRIGHT PROTECTION 1351 resolve these claims. 15 Finally, this Note will then demonstrate that a computer program's user interface, which includes16 the menu command hierarchy, is properly protected by copyright. FACTS AND HOLDING The idea of an electronic spreadsheet first took form in the late 1970's when Daniel Bricklin, a student at Harvard's Business School, created VisiCalc, the first commercially available electronic spreadsheet.1 7 Mitchell Kapor and Jonathan Sachs, the original authors of the Lotus 1-2-3 spreadsheet computer program ("Lotus 1-2-3"), built upon Bricklin's idea and developed Lotus 1-2-3, which could operate on IBM personal computers. 18 Developed in the early 1980s, Lotus 12-3 was recognized as a leader in the field of spreadsheet programs, which allow users to execute accounting functions. 19 Lotus 1-2-3 is controlled through a variety of menu commands that are selected on the screen or typing the first either by highlighting the command 20 letter of the desired command. In 1987, Borland International ("Borland") released its first Quattro spreadsheet computer program ("Quattro"). 21 Included in the Quattro and subsequent Quattro Pro version 1.0 programs was "a virtually identical copy of the entire [Lotus] 1-2-3 menu tree," one portion of the Lotus 1-2-3 program in which Lotus Development Corporation ("Lotus") possessed a valid copyright. 22 While the Borland programs included their own commands and menu tree, the Lotus 1-2-3 menu tree was included so that users of that program would not have to 23 learn new commands when switching to Quattro or Quattro Pro. Thus, by incorporating the Lotus 1-2-3 menu command hierarchy into the Quattro programs, Borland could offer users of its electronic spreadsheet programs a choice of communicating with the program 15. See infra notes 107-356 and accompanying text. 16. See infra notes 357-494 and accompanying text. 17. Lotus Dev. Corp. v. Paperback Software Int'l, 740 F. Supp. 37, 65 (D. Mass. 1990). 18. Paperback Software Int'l, 740 F. Supp. at 66. 19. Lotus Dev. Corp. v. Borland Intl, Inc., 49 F.3d 807, 809 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision); Dale M. Cendali and Martin Glenn, In Lotus, the 1st CircuitDeparted from Precedent,Narrowing Protection for Developed Software and Giving Crafty Litigators a Blank Disk on Which to Write 17 NAT'L L.J. B7 (May 15, 1995). 20. Lotus Dev. Corp., 49 F.3d at 809. 21. Id. at 810. 22. Id. at 810, 813. Borland modified the Lotus 1-2-3 menu tree by inserting "some new menu commands." Lotus Dev. Corp. v. Borland Int'l, Inc., 831 F. Supp. 202, 212 (D. Mass. 1993), rev'd, 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). Author's note: hereinafter this case will be referred to as Borland III. 23. Lotus Dev. Corp., 49 F.3d at 810. 1352 CREIGHTON LAW REVIEW [Vol. 30 through commands designed by Borland or the Lotus 1-2-3 menu 24 tree. As a result, Lotus fied a copyright infringement action against Borland in the United States District Court for the District of Massachusetts. 25 Lotus maintained that it possessed a copyright in Lotus 12-3 which was infringed upon by Borland. 26 Borland countered Lotus' claim, stating that its products are not the same as Lotus 1-2-3, or alternatively, that the portions of Lotus 1-2-3 at issue were not subject to copyright protection because they are a "system, process, procedure, or method" for which 17 U.S.C. § 102(b) ("section 102(b)") prohibits copyright protection. 2 7 Borland contended that any portion of its Quattro and Quattro Pro programs which were similar to Lotus 1-2-3 concerned only the way in which the program functioned and did not constitute copyrightable expression. 28 The court noted that Borland "appear[ed] to be asserting more - that if some part of a computer program is a 'system, process, procedure, or method,' 17 U.S.C. § 102(b), no copyright of any aspect of that part of the program is possible." 2 9 Section 102(b) effectively prohibits the copyright of an "idea, procedure, process, system, [or] method of operation . . .," thus Borland maintained that the Lotus 1-2-3 program was a method of operation and, pursuant to section 102(b), outside the protection of copyright law. 30 The district court, however, found that "the Lotus menu struc- ture, organization, and first letters of the command names [were] not within the definition of the 'idea,' 'system,' 'process,' 'procedure,' or 24. 25. Id. Lotus Dev. Corp. v. Borland Intl, Inc., 788 F. Supp. 78, 80 (D. Mass. 1992), rev'd, 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). Author's note: hereinafter this case will be referred to as Borland I. Only days before Lotus filed suit, Borland commenced a declaratory judgment action in United States District Court for the Northern District of California in order to obtain a ruling that Borland had not infringed upon the Lotus copyright. Lotus Dev. Corp, 49 F.3d at 810. The suit filed in California was dismissed in favor of the litigation commenced in Massachusetts. Id. This, however, was not the first occasion in which Lotus had filed a copyright infringement action. See Paperback Software Int'l, 740 F. Supp. at 42; infra notes 201-17 and accompanying text. 26. Borland I, 788 F. Supp. at 80. 27. Id. at 80, 90-91. In 1990, Lotus obtained relief in the United States District Court for the District of Massachusetts for infringement of the same copyright by Paperback Software International. Id. at 80. Borland also maintained that its products were not the same as those created by Paperback Software International. Id. 28. Borland 1, 788 F. Supp. at 85-86. 29. Id. at 91. 30. 17 U.S.C. § 102(b) (1994); Borland I, 788 F. Supp. at 90-91. Title 17 of the United States Code section 102(b) provides in pertinent part that "in no case does copyright protection for an original work of authorship extend to any idea, procedure, process, system, method of operation, concept, principle, or discovery, regardless of the form in which it is described, explained, illustrated, or embodied in such work." 17 U.S.C. § 102(b). 1997] COPYRIGHT PROTECTION 1353 'method' of the Lotus 1-2-3 program and constitute[d] part of the protectable expression found in the program."3 1 The court stated that Borland's argument was "fundamentally inconsistent" with the bal32 ance struck in the Copyright Act. The district court determined that, because there were several different ways to produce a user interface, the Lotus 1-2-3 user interface was an expression, and thus copyrightable. 33 Specifically, the court stated that functional aspects of the program, such as a print command, came within the idea of the program while copyrightability was dependent upon the author's expression. 34 The court indicated that Borland failed to demonstrate that the menu tree was a functional aspect of the program. 35 Thus, the district court determined that Borland's incorporation of the Lotus 1-2-3 menu command hierarchy in its own program constituted infringement. 36 Due to the infringement, the district court issued a permanent injunction prohibiting Borland from further distribution of the Quattro or Quattro Pro computer programs which contained "a copy of the Lotus 1-2-3 37 menu commands and/or menu structure, in any form." 31. Lotus Dev. Corp. v. Borland Intl, Inc., 831 F. Supp. 223, 233 (D. Mass. 1993), rev'd, 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). Author's note: hereinafter this case will be referred to as Borland IV. 32. Borland I, 788 F. Supp. at 92. Copyright law seeks to balance the "protection [afforded] to authors as an incentive to create" with "limit[ing] the extent of that protection so as to avoid the effects of monopolistic stagnation." Computer Assocs. Int'l, Inc. v. Altai, Inc., 982 F.2d 693, 696 (2nd Cir. 1992). 33. Lotus Dev. Corp. v. Borland Int'l, Inc., 799 F. Supp. 203, 217 (D. Mass. 1992), rev'd, 49 F.3d 807 (1st Cir. 1995), afld nem., 116 S. Ct. 804 (1996) (4-4 decision). Author's note: hereinafter this case will be referred to as Borland I. See also Lotus Dev. Corp. v. Borland Intl, Inc., 831 F. Supp. 202, 213 (D. Mass. 1992) (stating that Lotus 12-3 menu tree copyrightable because it is one of a variety of potential expressions), rev'd, 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). Author's note: hereinafter this case will be referred to as Borland III. 34. Borland 11, 799 F. Supp. at 217. 35. Borland III, 831 F. Supp. at 213. 36. Borland IV, 799 F. Supp. at 221. The trial court also noted that Lotus alleged copying of the "'menu commands,' 'menu structure,' 'long prompts,' and 'keystroke sequences.'" Borland 11, 799 F. Supp. at 205. The district court defined "menu command" as being an abbreviated description of a direction within the menu a user may invoke to cause the program to perform a function; the "menu structure" as relating to the arrangement of menu commands and menus; the "long prompts" as being a displayed "description of a 'highlighted' menu command;" and a "keystroke sequence" as a series of keystroke entries which can be entered by a user. Id. at 206. Borland admitted to copying all of these items, save for the long prompts. Id. at 209. The court determined that the issue of whether the long prompts were copied was a jury question. Id. As for the keystroke sequences, the district court found this to be functional and not subject to copyright protection. Id. at 207 (citing 17 U.S.C. § 102(b) (1988)). The court addressed the copying of the menu commands and structure, collectively referring to these items as the "menu tree." Borland III, 831 F. Supp. at 211-12. The trial court held that the menu tree was copyrightable because the arrangement of operations within the tree contained expression. Id. at 211. 37. Borland IV, 831 F. Supp at 245-46. 1354 CREIGHTON LAW REVIEW [Vol. 30 The only issue on appeal to the United States Court of Appeal for the First Circuit was whether the menu command hierarchy present in Lotus 1-2-3 came within the purview of copyright protection. 38 The First Circuit held that the menu command hierarchy could not be protected by copyright because, the court noted, copyright protection does not extend to a "method of operation."3 9 The court determined that "method of operation" refers to "the means by which a person operates "40 The Lotus 1-2-3 menu command hierarchy, the something ... was merely the manner by which the user tells the comcourt noted, 41 puter what to do. Because the court determined that the Lotus 1-2-3 menu command hierarchy was a method of operation and thus not copyrightable, the court did not address whether Borland had copied protectable expression found within the Lotus 1-2-3 spreadsheet program. 42 As the First Circuit stated: Concluding, as we do, that users operate Lotus 1-2-3 by using the Lotus menu command hierarchy, and that the entire Lotus menu command hierarchy is essential to operating Lotus 1-2-3, we do not inquire further whether that method of operation could have been designed differently. The "expressive" choices of what to name the command terms and how to arrange them do not magically change the uncopyrightable menu command hierarchy into copyrightable subject 43 matter. BACKGROUND THE NATURE OF COMPUTERS AND COMPUTER PROGRAMS Modern computers consist of hardware and software which, when combined, allow the computer to process data. 44 The hardware consists of a central processing unit, keyboard, memory, disk drives, and other mechanisms for conveying data to and from the computer's memory. 45 Computer software, on the other hand, can be divided into 38. Lotus Dev. Corp., 49 F,3d at 812. Borland conceded the validity of Lotus' copyright in Lotus 1-2-3 and to copying the menu command hierarchy. Id. at 813. 39. Lotus Dev. Corp., 49 F.3d at 815. The First Circuit stated "the Lotus menu command hierarchy is an uncopyrightable 'method of operation'" as that term is used in 17 U.S.C. § 102(b). Id. For the full text of section 102(b), see supra note 30. 40. Lotus Dev. Corp., 49 F.3d at 815. 41. Id. The First Circuit compared the Lotus menu command hierarchy to the buttons of a VCR. Id. at 817. 42. Lotus Dev. Corp., 49 F.3d at 816. 43. Id. 44. Peter S. Menell, An Analysis of the Scope of Copyright Protection for Application Programs,41 STAN. L. REV. 1045, 1050-51 (1989). 45. Menell, 41 STAN. L. REV. at 1051. 1997] COPYRIGHT PROTECTION 1355 two types: operating systems and application programs. 4 6 Operating systems "manage the internal functions of the computer or facilitate the use of application programs."4 7 In contrast, application programs, such as bookkeeping and financial analysis programs, execute specific 48 data processing assignments for the computer operator. A computer program is assembled in several steps which create a group of commands for the computer. 49 First, a programmer will identify the particular obstacle which the program is to resolve. 50 Next, an outline of the proposed program may be created, often in the form of a flowchart. 5 1 The flowchart will further break down the proposed program into "'subroutines"' or "'modules'" whose arrangement determines the program's efficiency. 52 Once a detailed design has been achieved, the third process, known as coding, begins. 53 In coding, the programmer will draft the program in "source code," which may be in one of several programming languages. 54 The "source code" is then transformed into "object code" by a "compiler," a computer program whose specific purpose it is to ensure that this conversion takes place. 5 5 The "object code" is a binary code consisting of a conglomera56 tion of "O"s and "I"s which the computer uses to perform functions. Source and object code are known as the "literal elements" of a computer program, while the program's structure, organization, and user interface are "nonliteral elements." 57 Courts have held that the literal elements of a computer program may be copyrighted, as can the nonliteral elements, but that a copyright in the nonliteral elements 58 may only be obtained if they contain original expression. 46. Apple Computer, Inc. v. Franklin Computer Corp., 714 F. 2d 1240, 1243 (3d Cir. 1983). 47. Apple Computer, Inc., 714 F.2d at 1243. 48. Id. 49. Whelan Assocs., Inc. v. Jaslow Dental Lab, Inc., 797 F.2d 1222, 1229 (3d Cir. 1986); Steven R. Englund, Note, Idea, Process, or Protected Expression?: Determining the Scope of Copyright Protection of the Structure of Computer Programs, 88 MIcH. L. REV. 866, 870-71 (1990) (explaining the steps necessary to create a computer program). 50. Whelan Assocs., Inc., 797 F.2d at 1229. 51. Id. at 1230. 52. Id. 53. Id. 54. Id. Examples of different programming languages are BASIC, EDL, FORTRAN, and COBOL. Id. For those who have been properly trained, a programming language is easily comprehensible. SAS Inst., Inc. v. S & H Computer Sys., Inc., 605 F. Supp. 816, 818 (M.D. Tenn. 1985). 55. SAS Inst., Inc., 605 F. Supp. at 818. 56. Whelan Assocs., Inc., 797 F.2d at 1230-31. See also id. at 1231 n.21 (addressing additional aspects of completing a computer program). 57. MiTek Holdings, Inc. v. Arce Eng'g Co., Inc., 864 F. Supp. 1568, 1576-77 (S.D. Fla. 1994), aftd, 89 F.3d 1548 (11th Cir. 1996). 58. Engineering Dynamics, Inc. v. Structural Software, Inc., 26 F.3d 1335, 1341 (5th Cir. 1994) (holding that most courts have found that copyright protection extends 1356 CREIGHTON LAW REVIEW [Vol. 30 COPYRIGHT LAW Article I, section 8 of the United States Constitution vests Congress with the power to provide copyright protection for the works of inventors and authors. 5 9 Congress passed the first legislation pursuant to this constitutional grant in 1790.60 Numerous revisions and amendments followed, and then in 1976, influenced largely by chang61 ing technology, Congress completely revised the law of copyrights. Four years later, in 1980, Congress amended the Copyright Act of 1976 (the "Copyright Act") to provide the owners of copyrights in computer programs protection akin to that received by the holders of copy62 rights in literary works. The 1980 amendments came in response to the recommendations of the National Commission on New Technological Uses of Copyrighted Works ("CONTU"), an organization created in 1974 to formulate policy concerning copyrights and computers. 6 3 CONTU recommended that the then-existing Copyright Act be amended to: (1) allow computer programs which reflect original expression to be copyrighted, (2) ensure that copyright law applies to all computer uses, and (3) allow for the rightful copying of computer programs. 64 Accordingly, federal copyright law now defines a "computer program" as a "set of statements or instructions to be used directly or indirectly in a 65 computer in order to bring about a certain result." Copyrights function to protect the expression of ideas, not the ideas themselves. 66 In order for an item to be protected by copyright it must be: (1) an original work of authorship that is (2) manifested in to literal and nonliteral elements), opinion supp. by 46 F.3d 408 (5th Cir. 1995); Johnson Controls, Inc. v. Phoenix Control Sys., Inc., 886 F.2d 1173, 1175, 1177 (9th Cir. 1989) (finding the literal components of a computer program are protected by copyright as are the nonliteral components when they contain expression); Whelan Assocs., Inc., 797 F.2d at 1248 (concluding that copyright protection extends beyond a program's literal code to its structure, sequence, and organization). 59. U.S. CONST. art. I, § 8, cl. 8. 60. M. Kramer Mfg. Co., Inc. v. Andrews, 783 F.2d 421, 432 (4th Cir. 1986). 61. M. Kramer Mfg. Co., Inc., 783 F.2d at 432. 62. Englund, 88 MICH. L. REV. at 873-74. 63. Id. at 873. 64. M.Kramer Mfg. Co., Inc., 793 F.2d at 432 n.8; Arthur R. Miller, Copyright Protection for Computer Programs, Databases, and Computer-Generated Works: Is Anything New Since CONTU?, 106 HARv. L. REv. 978, 979 (1993). 65. 17 U.S.C. § 101 (1994). 66. Computer Assocs. Intl, Inc. v. Altai, Inc., 982 F.2d 693, 703 (2nd Cir. 1992) (emphasis added). See also Q-Co Indus., Inc. v. Hoffman, 625 F. Supp. 608, 616 (S.D.N.Y. 1985) (holding that a claim of copyright infringement was not established because only an idea was copied); Apple Computer, Inc. v. Microsoft Corp., 799 F. Supp. 1006, 1026, 1047 (N.D. Cal. 1992) (finding that common aspects between Apple and Microsoft programs were "ideas," therefore there was no copyright infringement), clarified by 1993 WL 207982 (N.D. Cal. 1992), affd, 35 F.3d 1435 (9th Cir. 1994), cert. denied, 115 S.Ct. 1176 (1995). 1997] COPYRIGHT PROTECTION 1357 a "tangible medium of expression" and (3) capable of communication either directly or with the assistance of a machine. 6 7 The "two fundaFor a case maintaining that the level of sophistication found in a computer program is an indicator of expression which may be protected by copyright, see Johnson Controls, Inc. v. Phoenix Control Sys., Inc., 886 F.2d 1173, 1176 (9th Cir. 1989). In Johnson Controls, the United States Court of Appeals for the Ninth Circuit held that the nonliteral portions of a computer program "may be protected by copyright where they constitute expression, rather than ideas." Johnson Controls, 886 F.2d at 1177. In this case, Johnson Controls, Inc. ("Johnson") alleged that Phoenix Control Systems ("Phoenix") infringed on its copyright in a computer program to control wastewater treatment plants. Id. at 1174. Johnson filed suit in the United States District Court for the District of Arizona and obtained a preliminary injunction against Phoenix precluding it from copying, distributing, publishing, or representing to others that it had the ability to use Johnson's computer program. Id. The district court found the "structure, sequence, and organization" of Johnson's program was expression entitled to copyright protection. Id. at 1175. Phoenix appealed the district court's decision to the United States Court of Appeals for the Ninth Circuit. Id. at 1174. On appeal, the Ninth Circuit discussed the elements of a copyright infringement action. Id. at 1175. The court identified these elements as being ownership of a copyright and copying, the latter of which can be satisfied by showing "access to the copyrighted work, and substantial similarity between the copyrighted work and the infringer's work." Id. at 1175-76 (citations omitted). First, the court noted that Johnson's registration of its copyright was prima facie evidence of originality creating a presumption Phoenix was unable to rebut. Id. at 1175. Next, the court noted that Phoenix had access to the Johnson program since many of Phoenix's employees had formerly worked for Johnson and worked on several versions of Johnson's program. Id. at 1176. Then, the Ninth Circuit discussed the issue of substantial similarity, and deferred to the district court's determination that, in fact, the two programs appeared to be substantially similar. Id. The court stated that examination of these similarities was such that a reasonable person would find the infringing program developed by Phoenix contained the "'total concept and feel'" of Johnson's computer program. Id. Finally, the Ninth Circuit addressed the degree of protection afforded non-literal elements of a computer program. Id. at 1175. The court indicated that the non-literal elements of a computer program include its "structure, sequence and organization and user interface." Id. The protection afforded to such non-literal elements, the court noted, turns on whether such an element is an expression of an idea, rather than being an idea itself. Id. The court noted that Johnson's program was extremely sophisticated, requiring its applications to be individually tailored for each user. Id. at 1175-76. The court maintained that this sophistication indicated a leeway for expression within the program in order for it to execute certain functions. Id. at 1176. Thus, the court found Johnson's computer program to be expression and therefore protectable by copyright. Id. at 1177. 67. 17 U.S.C. § 102(a) (1994). This statute states in pertinent part: Copyright protection subsists, in accordance with this title, in original works of authorship fixed in any tangible medium of expression, now known or later developed, from which they can be perceived, reproduced, or otherwise communicated, either directly or with the aid of a machine or device. Works of authorship include the following categories: (1) literary works; (2) musical works, including any accompanying words; (3) dramatic works, including any accompanying music; (4) pantomimes and choreographic works; (5) pictorial, graphic, and sculptural works; (6) motion pictures and other audiovisual works; (7) sound recordings; and (8) architectural works. 1358 CREIGHTON LAW REVIEW [Vol. 30 mental criteria of copyright protection" are originality and fixation. 68 Originality, although not defined in the Copyright Act, has been interpreted by the United States Supreme Court as "mean[ing] only that the work was independently created by the author... and... possesses at least some minimal degree of creativity." 6 9 Because "originality is not a stringent standard," authors must do little more than create something that may be recognized as their own. 70 Fixation, on the other hand, is defined in the Copyright Act. 7 1 A work is "fixed" if it is permanent such that it can be "perceived, reproduced, or other72 wise communicated for a period of more than a transitory duration." When a work possesses both originality and fixation it may be pro73 tected by copyright. Fulfilling these criteria, however, does not guarantee that a party will prevail in a copyright infringement action. 74 For example, even if a work possesses originality and fixation, the "merger" doctrine will deny copyright protection when the expression of an idea is indistinguishable, or cannot be separated, from the idea itself.7 5 Similarly, the "scenes a faire" doctrine precludes copyright protection where material "is 'standard,' 'stock,' or 'common' to a particular topic, or that 'necessarily follows[s] from a common theme or setting."76 "Scenes a faire" may also nullify copyright protection when elements of a work 68. M. KramerMfg. Co., Inc., 793 F.2d at 433 (quoting H.R. REP. No. 94-1476, at 51 (1976), reprinted in 1976 U.S.C.C.A.N. 5659, 5664). 69. Id. at 433 (stating that the term "originality" is not defined in the Copyright Act); Feist Publications, Inc. v. Rural Tel. Serv. Co., Inc., 499 U.S. 340, 345 (1991). 70. M. Kramer Mfg. Co., Inc., 783 F.2d at 438; FeistPublications,Inc., 499 U.S. at 362 (stating that "originality is not a stringent standard."). 71. M. Kramer Mfg. Co., Inc., 783 F.2d at 433. 72. 17 U.S.C. § 101 (1994). This statute maintains in pertinent part that: A work is "fixed" in a tangible medium of expression when its embodiment in a copy or phonorecord, by or under the authority of the author, is sufficiently permanent or stable to permit it to be perceived, reproduced, or otherwise communicated for a period of more than transitory duration. A work consisting of sounds, images, or both, that are being transmitted, is "fixed" for the purposes of this title if a fixation of the work is being made simultaneously with its transmission. Id. In M. Kramer Mfg. Co., Inc. the United States Court of Appeals for the Fourth Circuit employed this statute to define "fixation." M. Kramer Mfg. Co., Inc., 783 F.2d at 433. 73. M. Kramer Mfg. Co., Inc., 783 F.2d at 433. 74. See infra notes 75-79 and accompanying text. 75. Telemarketing Resources v. Symantec Corp., No. C88-20352 RPA, 1989 WL 200350, at *3 (N.D. Cal. 1989), affd in part sub nom. Brown Bag Software v. Symantec Corp., 960 F.2d 1465 (9th Cir. 1992). See Autoskill, Inc. v. National Educ. Support Sys., Inc., 994 F.2d 1476, 1494 (10th Cir. 1993) (holding that the merger doctrine prohibited the copyright of a program's use of certain categories of vowels and consonants because they are dictated by the idea of the program, which was to teach reading in English). 76. Autoskill, Inc., 994 F.2d at 1494 (citing 3 MELVILLE B. NneMER & DAVID NimMER, NIM4MER ON COPYRIGHT § 13.03[B][4] (1993)). In Autoskill, the scenes a faire doctrine prevented the "silent sentence" and "silent paragraph" components of a reading 1997] COPYRIGHT PROTECTION 1359 "have been dictated by external factors," such as software compatibility requirements. 7 7 Furthermore, a copyright cannot be obtained for a "useful article," defined in the Copyright Act as "an article having an intrinsic utilitarian function that is not merely to portray the appearance of the article or to convey information." 78 Lastly, the fair use doctrine allows a court to avoid a finding of copyright infringement if a copyrighted work is being used for "criticism, comment, news reporting, teaching,... scholarship, or research . . .79 If these doctrines do not operate to preclude copyright protection, then a copyright secures exclusive rights for the owner in his or her work.8 0 A copyright extends during the author's lifetime, plus fifty years or seventy-five to one hundred years depending upon whether the copyrighted work is authored anonymously, through a pseudonym, or was a work for hire. 8 1 During this time, only the owner of the copyright may reproduce the copyrighted work, distribute copies, dis82 play, or prepare derivative works based on the copyrighted material. Anyone who violates these exclusive rights will be deemed an "infringer of the copyright," entitling the copyright owner to bring an infringement action seeking injunctive relief, as well as actual or 83 statutory damages. program from being copyrighted because they were "'so standard to the field that they cannot be afforded protection."' Id. 77. Gates Rubber Co. v. Bando Chem. Indus., Ltd., 9 F.3d 823, 838 (10th Cir. 1993). The "external factors" applicable to a computer program one seeks to copyright include "hardware standards and mechanical specifications ... software standards and compatibility requirements... computer manufacturer design standards, target industry practices and demands... and computer industry programming practices .... " Id. (citations omitted). Another court has denied copyright protection under the "scenes a faire" because the alleged infringer was merely attempting to comply with industry standards. EngineeringDynamics, Inc., 26 F.3d at 1347 n.13. 78. Lotus Dev. Corp. v. Paperback Software Intl, 740 F. Supp. 37, 52 (D. Mass. 1990) (quoting 17 U.S.C. § 101 (1988)). 79. 17 U.S.C. § 107 (1994). When applying the fair use doctrine four criteria must be considered: (1) the purpose and character of the use, including whether such use is of a commercial nature or is for nonprofit educational purposes; (2) the nature of the copyrighted work; (3) the amount and substantiality of the portion used in relation to the copyrighted work as a whole; and (4) the effect of the use upon the potential market for or value of the copyrighted work. Id. 80. 17 U.S.C. § 106 (1994). 81. 17 U.S.C. § 302(c) (1994). 82. 17 U.S.C. § 106. 83. 17 U.S.C. § 501 (1994) (defining infringers of copyright); 17 U.S.C. § 502 (1994) (providing that injunctive relief is available "to prevent or restrain infringement of a copyright"); 17 U.S.C. § 504 (1994) (stating that one who infringes another's copyright is liable for actual damages or statutory damages). CREIGHTON LAW REVIEW 1360 [Vol. 30 Actual damages available to the copyright owner are computed based on the actual damage caused by the infringement, plus the profits obtained by the infringer attributable to the violation of the copyright.8 4 Alternatively, an aggrieved party may recover statutory damages in lieu of actual damages.8 5 Statutory damages range from $200 to $100,000, depending on whether the infringement was willful.8 6 Further, if a copyright has been willfully infringed "for purposes of commercial advantage or.private personal gain," criminal sanctions may be imposed upon the infringing party, consisting of a sentence of imprisonment not exceeding five years, a fine, or both.8 7 Moreover, costs and attorney's fees may also be awarded at the court's discretion.8 8 A copyright infringement suit must commence within three years of the claim's accrual.8 9 TITLE 17, UNITED STATES CODE, SECTION 102 Title 17 of the United States Code section 102(a) ("section 102(a)") lists the subject matter which may be protected by copyright. 90 For example, section 102(a) provides copyright protection for musical and dramatic works, motion pictures, sound recordings and music, architectural works, literary works, pantomimes, choreography, pictures, graphics, and sculptures. 9 1 Literary works are defined in section 101 as "works ...expressed in words, numbers, or other verbal or numerical symbols ... "92 The legislative history of the Copyright Act indicates that computer programs are to be considered within the purview of "literary works" as defined under section 101. 93 Title 17 of the United States Code section 102(b) ("section 102(b)"), however, acts to restrict copyright protection by preventing a copyright from protecting any "idea, procedure, process, system, method of operation,concept, principle, or discovery, regardless of the form in which it is described, explained, illustrated, or embodied in 84. 17 U.S.C. § 504(b) (1994). 85. 17 U.S.C. § 504(a). 86. 17 U.S.C. § 504(c). 87. 17 U.S.C. § 506(a) (1994). 88. 17 U.S.C. § 505 (1994). 89. 17 U.S.C. § 507(a)(b) (1994). 90. 17 U.S.C. § 102(a) (1994). 91. Id. 92. 17 U.S.C. § 101 (1994). This section states in pertinent part that "literary works' are works, other than audiovisual works, expressed in words, numbers, or other verbal or numerical symbols or indicia, regardless of the nature of the material objects, such as books, periodicals, manuscripts, phonorecords, film, tapes, disks, or cards, in which they are embodied." Id. 93. H.R. REP. No. 94-1476, at 54 (1976), reprinted in 1976 U.S.C.C.A.N. 5659, 5667. 1997] COPYRIGHT PROTECTION 1361 such work."94 Section 102(b) reflects the dichotomy between idea and expression. 95 Congress enacted section 102(b) to ensure that the expression chosen by a computer programmer was subject to copyright protection, but that the processes or methods with which the program operated were not.9 6 Section 102(b) does not prohibit the copyrightability of computer programs. 9 7 The relevant House report states: Section 102(b) is intended, among other things, to make clear that the expression adopted by the programmer is the copyrightable element in a computer program, and that the actual processes or methods embodied in the program are not within the scope of the copyright law. Section 102(b) in no way enlarges or contracts the scope of copyright protection under the present law. Its purpose is to restate, in the context of the new single Federal system of copyright, that the basic 98dichotomy between expression and idea remains unchanged. THE UNITED STATES SUPREME COURT'S INTERPRETATION OF THE DICHOTOMY BETWEEN IDEA AND EXPRESSION The United States Supreme Court's decision in Baker v. Selden 99 is the seminal case in the area of the copyright protection afforded utilitarian works. 10 0 In Baker, the Supreme Court held that the holder of a copyright for a book which explained a unique method of bookkeeping was not entitled to copyright protection of the illustrative forms contained in the book. 1° 1 The holder of the copyright, Charles Selden, alleged that Baker infringed upon Selden's copyright of the bookkeeping method when Baker created accounting books developed from substantially the same system.102 Baker denied that any infringement occurred and argued that Selden's book was not a proper subject for copyright. 10 3 The Court stated that a description of "the art," which in this case was bookkeeping, could be copyrighted, but copyright protection was not available for the bookkeeping procedure 94. 95. 17 U.S.C. § 102(b) (emphasis added). Englund, 88 MICH. L. REv. at 875. H.R. REP. No. 94-1476, at 57 (1976), reprinted in 1976 U.S.C.A.A.N. at 5670 96. (emphasis added). 97. M. Kramer Mfg. Co., Inc., 783 F.2d at 435. 98. H.R. REP. No. 94-1476, at 57 (1976), reprinted in 1976 U.S.C.A.A.N. at 5670 (emphasis added). 99. 101 U.S. 99 (1879). 100. Computer Assocs. Int'l, Inc., 982 F.2d at 704. 101. Baker v. Selden, 101 U.S. 99, 104 (1879). 102. Baker, 101 U.S. at 99-100. 103. Id. at 100. 1362 CREIGHTON LAW REVIEW [Vol. 30 itself.10 4 Therefore, the Court held that Selden's copyright did not confer upon him the exclusive right to create and make use of accounting books with the forms he designed.' 0 5 Instead, the Court determined that Selden's forms were necessary for practical application of his method of bookkeeping and should be made available to the public.106 THE SCOPE OF COPYRIGHT PROTECTION FOR COMPUTER PROGRAMS Copyrightabilityof the Structure of a Computer Program The United States Court of Appeals for the Third Circuit's deci07 sion in Whelan Associates, Inc. v. Jaslow Dental Laboratory, Inc. 1 has been identified as the "leading case" defining the extent to which l0 8 aspects of a computer program are subject to copyright protection. In Whelan, the Third Circuit held that copyright protection extended past the literal computer code to the "structure, sequence, and organization" of a computer program.' 0 9 In Whelan, a custom-made computer program was developed by Elaine Whelan for the Jaslow Dental Laboratory, Inc. (the "Jaslow Lab"). 1 10 Elaine Whelan's program was written in a language that allowed it to be operated on IBM Series One machines, but was not compatible with many of the computers used by smaller dental firms."' Three years after this program was completed, Rand Jaslow, an officer and shareholder in the Jaslow Lab, began working on a pro112 gram which would operate on the computers used by smaller firms. Once completed, Whelan Associates, Inc. ("Whelan") brought suit in the United States District Court for the Eastern District of Penn3 sylvania alleging copyright infringement."1 104. Id. at 104-05. The term "art" as used by the Supreme Court has been construed to denote the "idea" of the work. Autoskill, Inc. v. Nat'l Educ. Support Sys. Inc., 793 F. Supp. 1557, 1564 (D.N.M. 1992) (citing Baker v. Selden, 101 U.S. 99 (1879)), affd, 994 F.2d 1476 (10th Cir. 1993). 105. Baker, 101 U.S. at 107. 106. Id. at 103. 107. 797 F.2d 1222 (3d Cir. 1986). 108. Digital Communications Assocs., Inc. v. Softklone Distrib. Corp., 659 F. Supp. 449, 455 (N.D. Ga. 1987). 109. Whelan Assocs., Inc. v. Jaslow Dental Lab., Inc., 797 F.2d 1222, 1248 (3rd Cir. 1986). 110. Whelan Assocs., Inc., 797 F.2d at 1225. At the time Elaine Whelan wrote the program she was associated with Strohl Systems Group, Inc. ("Stroh"). Id. at 1225-26. After the program was completed for Jaslow, Elaine Whelan formed her own business, Whelan Associates, Inc., and acquired Stroh's interest in the program she created for Jaslow. Id. at 1226. 111. Whelan Assocs., Inc., 797 F.2d at 1226. 112. Id. 113. Id. at 1227. 1997] COPYRIGHT PROTECTION 1363 The Jaslow Lab argued that Whelan's copyright registration was defective for two reasons; first, that Rand Jaslow owned the first program, and second, that Rand Jaslow independently developed the second program. 1 4 Guided by expert testimony, the district court examined the file structures, screen outputs, and five subroutines. 1 15 The district court then held that Rand Jaslow's access to Whelan's program, combined with the substantial similarity between the two 116 programs, violated Whelan's copyright. On appeal, the United States Court of Appeals for the Third Circuit focused on whether Rand Jaslow, in developing the second program, copied the first program designed and copyrighted by Whelan. 117 The court noted that copying may be proven by demonstrating that a defendant had access to the copyrighted work and that the copyrighted and allegedly infringing work are substantially similar. 118 Because it was undisputed that Rand Jaslow had access to the copyrighted program, the Third Circuit addressed the issue of the similarity between the two programs and whether the copyright protection afforded a computer program extends beyond the literal computer code.119 After reviewing the district court's decision, the Third Circuit concluded that a substantial similarity existed between the two programs and affirmed the district court's judgment. 120 The Third Circuit examined the scope of copyright infringement to determine whether the Whelan copyright protected more than just the program's literal source and object codes. 12 1 The court noted that a showing of substantial similarity is not required in order to find infringement of the literal elements of a literary work. 12 2 Likewise, the Third Circuit 114. Id. 115. Id. at 1242-46. A file structure is "a storage place for data." Id. at 1242. A subroutine represents one portion of the solution for the problem that the program is designed to solve. Id. at 1230. 116. Whelan Assocs., Inc., 797 F.2d at 1228-29. 117. Id. at 1231-32. Rand Jaslow did not contest Whelan's copyright ownership before the Third Circuit. Id. at 1231. 118. Whelan Assocs., Inc., 797 F.2d at 1231-32. 119. Id. at 1232-34. The Jaslow Lab supported their position by arguing that the National Commission on New Technological Uses of Copyrighted Works ("CONTU") report suggested that the copyright protection afforded to computer programs be limited to a program's literal elements. Id. at 1241. The Third Circuit, however, pointed out that CONTU never made such a recommendation. Id. The court indicated that CONTUs report actually states that copyright protection may extend beyond the source and object codes to flowcharts. Id. The court stated further that the only statutory provision relevant was section 102(b). Id. Because the CONTU report did not instigate any changes in section 102(b), that report cannot be used as legislative history. Id. at 1241-42. 120. Whelan Assocs., Inc., 797 F.2d at 1248. 121. Id. at 1233-42. 122. Id. at 1234. 1364 CREIGHTON LAW REVIEW [Vol. 30 maintained, a computer program's copyright may be infringed "absent copying of the literal elements of the program."123 In discussing section 102(b), the Third Circuit stated the "clear" purpose of section 102(b) was to set forth "the idea-expression dichotomy." 12 4 The court noted that when examining a utilitarian work, the purpose or function of the work is the idea. 125 Thus, every element that is not essential for the purpose or function of the program is considered "part of the expression of the idea."1 2 6 In this case, the court determined that the idea was the "efficient organization of a dental lab."12 7 Because such organization may be achieved in many different ways, the court found that the program's structure was not essential to that idea, and therefore concluded that the program's structure was expression. 128 Accordingly, the court held that the structure, sequence, and organization of a computer program may be protected by 29 copyright. 1 123. Id. 124. Id. at 1234. 125. Id. at 1236. 126. Id. 127. Id. at 1240. 128. Id. at 1239-40. 129. Id. at 1248. For another case citing the proposition that copyright protection extends to one among several alternatives available to accomplish a task, see Pearl Sys., Inc. v. Competition Elecs., Inc., No. 87-6278-CIV-MARCUS, 1988 WL 146047 (S.D. Fla. 1988). In Pearl Systems the United States District Court for the Southern District of Florida held that copyright infringement occurred where two program subroutines, which could have been designed differently, were both activated "by the same sequence of buttons." PearlSys., Inc., 1988 WL 146047, at *6. The programs at issue were present on microprocessors inside shot timers, a devise used in competitive pistol shooting. Id. at *1-2. Competition Electronics, Inc. ("Competition") developed its shot timer in 1983 and subsequently registered a copyright for the software associated with this device. Id. at *1-2. The shot timer created by Pearl Systems, Inc. ("Pearl Systems") was produced after one of the individuals instrumental in its development acquired and operated one of Competition's shot timers. Id. at *2. Pearl Systems then brought a declaratory judgment action seeking a decree that it did not infringe upon the Competition copyright. Id. at *1. At issue before the district court was whether Pearl Systems copied an idea or the expression of an idea. Id. at *6. One subroutine in the shot timer allowed a user to set a "par time," which is a function that measures the number of shots fired in a specific time period. Id. at *1, 6. The other subroutine allowed a user to review the shots fired and discover the elapsed time between each shot. Id. at *6. Since the subroutines could have been designed in any number of ways the court maintained their structure was not dictated by function. Id. Thus, the court found these subroutines to be the expression of ideas and, accordingly, found that Pearl Systems infringed on Competition's copyright. Id. The district court enjoined Pearl Systems from further infringing on the copyright. Id. 1997] COPYRIGHT PROTECTION 1365 Copyrightabilityof a Main Menu Screen In Digital CommunicationsAssociates, Inc. v. Softklone Distributing Corporation,130 the United States District Court for the Northern District of Georgia specifically addressed whether the main menu screen of a computer program could be protected by copyright. 13 1 In Digital, Microstuff, Inc. ("Microstuff") developed and copyrighted a communications program that allowed information to be conveyed between computers. 132 This program had a unique main menu that contributed to its success. 13 3 ForeTec Development Corporation ("ForeTec"), after being advised by counsel that the main menu of the Microstuff program could not be protected by copyright, developed a "clone" of the Microstuff program. 134 After the clone program was created, Microstuff brought suit in the district court, alleging that ForTec 35 violated the Microstuff copyright.1 Distinguishing between idea and expression, the court stated the "'idea"' involved was the process or manner through which the main menu operated and the "'expression'" was the way the main menu was comprehended by the user.13 6 The court noted the grouping of commands on Microstuff's main menu contained "considerable stylistic 37 creativity" which could have been depicted in any number of ways. 1 Moreover, the court stated that the main menu and manner in which commands were selected had no relationship to the function of the status screen or program.' 38 Because the expression adopted by Microstuff was not dictated by the idea of a main menu, the court concluded that the main menu both expressed and conveyed information and could be protected by copyright. 139 130. 659 F. Supp. 449 (N.D. Ga. 1987). 131. Digital Communications Assocs., Inc. v. Softklone Distrib. Corp., 659 F. Supp. 449, 462 (N.D. Ga. 1987). The trial court identified the "main menu" as a "status screen." Id. at 452. 132. Digital CommunicationsAssocs., Inc., 659 F. Supp. at 452. Microstuff obtained a copyright for the main menu of the program in addition to a copyright for the program as a whole. Id. at 453. Digital Communications Associates, Inc. was substituted as plaintiff in this action after it purchased Microstuff. Id. 133. Digital CommunicationsAssocs.,.Inc., 659 F. Supp. at 452. 134. Id. at 453. ForeTec obtained a copy of Microstufi's program before creating its own program. Id. Softklone Distributing Corporation is a wholly owned subsidiary ForeTec created to market and distribute this "clone" program. Id. 135. Digital CommunicationsAssocs., Inc., 659 F. Supp. at 454. 136. Id. at 459. 137. Id. at 460. 138. Id. 139. Id. at 460, 462. 1366 CREIGHTON LAW REVIEW [Vol. 30 Copyrightabilityof Input and Output Formats Input and output formats have also been held to come within the purview of copyright protection.140 In Engineering Dynamics, Inc. v. Structural Software, Inc.,141 the United States Court of Appeals for the Fifth Circuit held that the nonliteral portion of a computer program may be protected by copyright. 142 In this case, Engineering Dynamics, Inc. ("EDI") developed a computer program designed to solve structural analysis engineering problems. 143 EDI's program was limited to operation on a mainframe computer. 144 Subsequently, when a competitor known as Structural Software, Inc. ("SSI") developed a similar program compatible with a personal computer, EDI claimed that its copyright had been infringed. 14 5 EDI then brought a copyright infringement action in the United States District Court for the Eastern District of Louisiana, seeking damages and equitable relief.14 6 Specifically, EDI alleged that SSI had infringed on EDI's copyright by copying fifty-six input formats, as well as various output formats, present in the EDI program. 147 The district court held that EDI's copyright did not protect the input and output formats because this aspect of the EDI program only communicated "standardized information to the user" and was therefore outside the scope of copyright protection.148 EDI appealed the court's decision to the United States 149 Court of Appeals for the Fifth Circuit. On appeal, the Fifth Circuit addressed three arguments presented by SSI: (1) user input formats could not be copyrighted, (2) EDI's input and output formats "represent unoriginal facts and lists of facts that are not copyrightable," and (3) input and output formats are "idea[s], process[es], or method[s]" which cannot be copyrighted. 150 In order to address the arguments presented by SSI, the Fifth Circuit applied the "abstraction-filtration-comparison" test to determine 140. Engineering Dynamics, Inc. v. Structural Software, Inc., 26 F.3d 1335, 1351 (5th Cir. 1994), opinion supp. by 46 F.3d 408 (5th Cir. 1995). 141. 26 F.3d 1335 (5th Cir. 1994), opinion supp. by 46 F.3d 408 (5th Cir. 1995). 142. EngineeringDynamics, Inc., 26 F.3d at 1342. The literal portion of a computer program is the source and object code. Id. at 1341. 143. EngineeringDynamics, Inc., 26 F.3d at 1338. 144. Id. 145. Id. at 1339. 146. Id. at 1340. 147. Id. at 1339. 148. Engineering Dynamics, Inc. v. Structural Software, Inc., 785 F. Supp. 576, 582 (E.D. La. 1991), affd & rev'd in part, 26 F.3d 1335 (5th Cir. 1994), opinion supp. by 46 F.3d 408 (5th Cir. 1995). 149. Engineering Dynamics, Inc., 26 F.3d at 1340. 150. Id. at 1341. COPYRIGHT PROTECTION 1997] 1367 whether the EDI program could be copyrighted. 15 1 The court outlined the "abstraction-fitration-comparison" test as follows: First, in order to provide a framework for analysis, . . a court should dissect the program according to its varying levels of generality... Second, poised with this framework, the court should examine each level of abstraction in order to filter out those elements of the program which are unprotectable. Filtration should eliminate from comparison the unprotectable elements of ideas, processes, facts, public domain information, merger material, scenes a faire material, and other unprotectable elements suggested by the particular facts of the program under examination. Third, the court should then compare the remaining protectable elements with the allegedly infringing program to determine whether the defendants have misappropriated substantial elements of the plaintiffs program. 152 In addressing SSI's first argument, the court discussed the abstraction portion of the test, and determined that both the input and output formats were expressions rather than ideas.1 5 3 Because a variety of ways existed for these formats to be constructed in order to accomplish the program's purpose, the court found that the formats constituted expression which could be protected by copyright. 154 The court then analyzed the filtration portion of the test in order to resolve SSI's second argument and determine whether the input and output formats were unprotectable facts or original expression.' 5 5 Because facts cannot be copyrighted, the court indicated that any input and output formats which consisted completely of facts could not be protected by the EDI copyright. 156 The court found that facts do not appear on the input and output formats, but that the formats were 1 7 "organized, descriptive tables for [the] entry of data...."5 The court found that the data chosen by EDI and its placement in the program was both original and unique. 158 Accordingly, the court determined that the input and output formats consisted of more than "facts," and therefore, were copyrightable. 159 In its fitration analysis, the court addressed SSI's third argument, in which it characterized the input data formats as being "a 151. Id. at 1342-1348. For a further discussion of the abstraction-filtration-comparison test, see supra notes 297-303 and accompanying text. 152. EngineeringDynamics, Inc., 26 F.3d at 1342-43. 153. Id. at 1344. 154. 155. 156. 157. 158. 159. Id. Id. at 1345. Id. Id. Id. at 1346. Id. at 1345. 1368 CREIGHTON LAW REVIEW [Vol. 30 template or tool used by the engineer." 160 The court identified the issue as being whether copyright protection was prohibited because of the utilitarian nature of the input formats. 16 1 The court determined that copyright protection was available because the input formats possess "original expressive content in... selection, sequence, and coordination .... "162 The Fifth Circuit then remanded the case to the district court to determine if industry standards prohibit copyright protection and whether or not SSI infringed on EDI's copyright in the 16 3 user interface of its program. The propriety of applying the "abstraction-ifitration-comparison" test to a copyright infringement case was also addressed by the United States Court of Appeals for the Tenth Circuit in Gates Rubber Co. v. Bando Chemical Industries, Ltd.,164 in which the Tenth Circuit applied the test to determine which elements of a computer program were protectable by copyright. 16 5 In GatesRubber Co., the Tenth Circuit held that the United States District Court for the District of Colorado failed to properly apply the "abstraction-ifitration-comparison" test. 16 6 Consequentially, the Tenth Circuit remanded the case to the district court to determine whether a copyright in the protectable ele16 7 ments of the program at issue had been infringed. At that time, Gates Rubber Company ("Gates") was a leader in the sale of industrial machine belts, and had developed the program for use by its sales personnel. 168 Gates obtained a certificate of copyright registration for its program which was designed to aid in the determination of the proper size of a rubber belt used on a particular 170 machine. 16 9 Bando American ("Bando") was a competitor of Gates. A Bando employee, Steven R. Piderit, who previously worked for Gates, aided Bando in developing a similar program.171 Gates subsequently brought suit for copyright infringement in the United States District Court for the District of Colorado. 172 The district court found 160. 161. 162. 163. 164. 165. 1993). 166. 167. 168. 169. Id. Id. at 1346. Id. Id. at 1351. 9 F.3d 823 (10th Cir. 1993). Gates Rubber Co. v. Bando Chem. Indus., Ltd., 9 F.3d 823, 833-34 (10th Cir. Gates Rubber Co., 9 F.3d at 848. Id. Id. at 830. Id. 170. Id. Bando American is actually a division of the a Japanese corporation that was in competition with Gates Rubber Co. Id. 171. Gates Rubber Co., 9 F.3d at 830-31. 172. Id. at 831. COPYRIGHT PROTECTION 1997] 1369 that Bando infringed on the copyright Gates had in its computer 73 program.' The district court initially determined that portions of the Gates program, such as the data and control flow, as well as the mathematical constants used, were all protectable by copyright. 17 4 After analyzing the substantial similarities between the two programs, the court held that there was "but one outcome: Defendants [Bando] infringed on Plaintiffs [Gates'] copyright." 175 Bando appealed this ruling to the United States Court of Appeals for the Tenth Circuit, contending that the district court erred in affording copyright protection to facts and 176 ideas present within Gates' program. On appeal, the Tenth Circuit found the former Gates employee who aided Bando in creating its program had access to the Gates program. 177 The appellate court then attempted to determine whether 178 any "probative similarities" existed between the two programs. The court indicated that even if copying did occur, infringement may not result unless protectable elements were copied and those protectable elements compromise a significant portion of the Gates' program. 179 In addressing whether any "probative similarities" existed between the two programs, the Tenth Circuit applied the "abstractionfiltration-comparison" test.180 Through the abstraction portion of the test, the court indicated that a computer program can be segregated into six different levels: "(i) the main purpose, (ii) the program structure or architecture, (iii) modules, (iv) algorithms and data structures, (v) source code, and (vi) object code."' 1 Once a level of abstraction is identified, the court stated, the filtration step "filter[s] out" those portions of the computer program which cannot be protected by copyright.' 8 2 The Tenth Circuit pointed out that filtration involves section 102(b), which prohibits the copyright protection of "ideas, concepts, and principles."' 8 3 The court maintained that the legislative history of section 102(b) clarified the proposition that a computer programmer's expression is to be protected, but that "actual processes or meth173. Id. 174. Gates Rubber Co. v. Bando Am., Inc., 798 F. Supp. 1499, 1518-19 (D. Colo. 1992), affd & vacated in part, 9 F.3d 823 (10th Cir. 1993). 175. Gates Rubber Co., 798 F. Supp. at 1519. 176. Gates Rubber Co., 9 F.3d at 831. 177. Id. at 830. 178. Id. at 832. 179. Id. at 833. 180. Id. at 834-46. 181. Id. at 835. 182. Id. at 836. 183. Id. (citing 17 U.S.C. § 102(b)). 1370 CREIGHTON LAW REVIEW [Vol. 30 ods" are outside the scope of copyright law.184 The court found that ideas within expression cannot be copyrighted.' 8 5 A program's purpose is an idea and is at one end of the spectrum, the court maintained, while a program's source and object code, which are literal elements of the program, are at the other end and will usually be considered protected expression.' 8 6 The court explained that generalization about what lies in between is more difficult.' 8 7 The Tenth Circuit remanded the case to the district court for reapplication of the "abstraction-filtration-comparison" test and a further examination of several aspects of the Gates and Bando programs. 188 ELEMENTS OF A COPYRIGHT INFRINGEMENT CLAIM In order to prevail on a copyright infringement claim, aggrieved plaintiffs must prove that: (1) they own a valid copyright, and (2) that the alleged infringer has copied elements of the copyrighted work which are original.' 8 9 A valid copyright is established by a certificate reflecting the registration of a copyright and is considered "prima facie 184. Id. at 836-37 (citing H.R. REP. No. 94-1476, at 57 (1976), reprinted in 1976 U.S.C.A.A.N. 5659, 5670). 185. Id. at 836. 186. Id. 187. Id. One program's structure may be considered an idea, while another's is found to be protectable expression. Id. 188. Gates Rubber Co., 9 F.3d at 830. On remand, the Tenth Circuit instructed the trial court to re-examine seven aspects of the Gates and Bando programs: constants, menus and sorting criteria, control and data flow, engineering calculation and design modules, common errors, fundamental tasks, and install files. Id. at 842-46. Constants are a part of the formulas used in the Gates program to perform calculations necessary to determine the load that a certain belt can bear. Id. at 842-43. The Tenth Circuit found these constants to be scientific observations of facts and therefore not subject to copyright protection. Id. Since the record on appeal required clarification of exactly what the trial court meant by "menu and sorting criteria" and "control and data flow" the appellate court had to remand the case without resolving whether these elements of the program could be copyrighted. Id. at 843-44. As for the engineering and design modules, the Tenth Circuit found that the trial court failed to determine if this could be an uncopyrightable process. Id. at 845. Further, the Tenth Circuit stated that the trial court did not consider the doctrines of merger or scenes a faire. Id. Accordingly, the appellate court was precluded from reviewing the engineering and design modules of the program. Id. Gates also argued to the Tenth Circuit that common errors could be protected. Id. Common errors refer to the incident of two programs performing incorrectly. Id. The Tenth Circuit maintained that this could be used as evidence of copying, but the errors themselves could not be protected. Id. Further, like "menu and sorting criteria" and "control and data flow," the Tenth Circuit was unsure of what meaning the district court accorded to "fundamental tasks." Id. at 846. This also required remand. Id. The last element considered by the Tenth Circuit, install files, was part of the Disk Operating System and may not have been subject to the Gates copyright. Id. An operating system is an assortment of programs that direct the computer's internal functions and serve as a bridge between hardware, application programs, and the user. Menell, 41 STAN. L. REV. at 1051. The appellate court remanded the case to determine this issue as well. Gates Rubber Co., 9 F.3d at 846. 189. Feist Publications,Inc., 499 U.S. at 361. 19971 COPYRIGHT PROTECTION 1371 evidence of the validity of the copyright and of the facts stated in the certificate." 190 The second element, copying, may be proven by direct evidence or by demonstrating that an infringer had access to the copyrighted work and that the infringer's work is "substantially similar to the . . . copyrighted material." 19 1 Because no physical proof is typi- cally available, copying is generally established by proving that an infringer had access to the copyrighted work and that a substantial similarity exists between the copyrighted work and the infringing must be "of such importance that the appropriawork. 1 92 The copying 19 3 tion is actionable." Ownership of a Valid Copyright If one does not have a valid copyright in a computer program, then suit may not be brought against an alleged infringer.' 9 4 In Bull 195 HN Information Systems, Inc. v. American Express Bank Limited, the United States District Court for the Southern District of New York dismissed a copyright infringement claim because the party bringing suit, Bull HN Information Systems, Inc. ("Bull EN"), did not have a copyright registered for the computer programing language at issue.' 9 6 Bull HN had developed a computer program with its own pro197 prietary language and obtained a copyright only in the program. Bull IN argued that a similar program developed by American Express Bank Limited ("American Express") infringed on Bull HN's copyright in both the computer programming language and the program created with that language. 198 Bull HN claimed American Express copied the "overall structure, sequence and organization" of the Bull HN program, as well as the way the program "look[s] and feel[s]." 19 9 When Bull HN failed to produce evidence of a valid copyright in the proprietary language, the district court dismissed Bull 190. Autoskill, Inc., 994 F.2d at 1487 (citing 17 U.S.C. § 410(c)). This presumption of validity may be rebutted. Folio Impressions, Inc. v. Byer California, 937 F.2d 759, 763 (2nd Cir. 1991). In effect, the burden is shifted onto the party who wishes to prove the invalidity of a copyright. Bibbero Sys., Inc. v. Colwell Sys., Inc., 893 F.2d 1104, 1106 (9th Cir. 1990). Any immaterial or inadvertent mistake present in the application for the copyright will not threaten the validity of the copyright registration. Data Gen. Corp. v. Grumman Sys. Support Corp., 36 F.3d 1147, 1161 (1st Cir. 1994). 191. Computer Assocs. Int'l, Inc., 982 F.2d at 701. 192. Concrete Mach. Co., Inc. v. Classic Lawn Ornaments, Inc., 843 F.2d 600, 606 (1st Cir. 1988). 193. Gates Rubber Co., 9 F.3d at 832. 194. Bull HN Info. Sys., Inc. v. American Exp. Bank Ltd., No. 88 CIV 2103 (SWK), 1990 WL 48098, *2 (S.D.N.Y. 1990). 195. 1990 WL 48098 (S.D.N.Y. 1990). 196. Bull HN Info. Sys., Inc., 1990 WL 48098, at *2. 197. Id. at *2. 198. Id. at *1-2. 199. Id. 1372 CREIGHTON LAW REVIEW [Vol. 30 HN's claim of infringement because Bull HN had never obtained a 20 0 copyright in the programming language. Proofof Copying: Direct Evidence One method for an owner of a valid copyright to prove copying is by direct evidence. 20 1 For example, in Lotus Development Corp. v. Paperback Software International,20 2 the United States District Court for the District of Massachusetts had direct evidence of the copying of a computer program's user interface and found that such an interface, which includes the menu command structure, may be protected by 20 3 copyright. In Paperback, a company known as Paperback Software International ("Paperback") sought to develop a computer spreadsheet program that was compatible with Lotus 1-2-3.204 The result was a program, called VP-Planner, which contained the same menu command hierarchy as Lotus 1-2-3.205 Paperback admitted that they directly incorporated the Lotus 1-2-3 menu command hierarchy into their program, thus providing Lotus Development Corp. ("Lotus") with direct evidence of copying.20 6 Paperback argued before the district court, however, that the copyright protection afforded a computer program extends only to the literal portions of the program, including the program's source code and object code, and therefore Lotus' direct evidence was not relevant. 20 7 Lotus countered this claim, stating that copyright protection encompasses both the literal and nonliteral elements of a computer program that possess original expression, including its menu command hierarchy. 20 8 Whether an original element of a program was literal or nonliteral, Lotus argued, was irrelevant to a search for original expression, which could be found in a program's 200. Id. at *2. Bull HN did register a copyright in the program written from the programming language at issue. Id. at *1-2. 201. See supra note 191 and accompanying text. 202. 740 F. Supp. 37 (D. Mass. 1990). 203. Lotus Dev. Corp. v. Paperback Software Int'l, 740 F. Supp. 37, 63, 68 (D. Mass. 1990). The district court, in summarizing its holding as to the copyrightability of the user interface, appears to use the terms "user interface" and "menu command system" interchangeably. Paperback Software Int'l, 740 F. Supp. at 68. 204. PaperbackSoftware Int'l, 740 F. Supp. at 69. Paperback contended that their program must be compatible with Lotus 1-2-3 in order for it to become a commercial success. Id. 205. PaperbackSoftware Int'l, 740 F. Supp. at 70. 206. Id. at 68. 207. Id. at 45-46. 208. Id. 1997] COPYRIGHT PROTECTION 1373 user interface. 20 9 The district court set forth the legal test for copyrightability as consisting of three parts: FIRST, in making the determination of "copyrightability," the decisionmaker must focus upon alternatives that counsel may suggest, or the court may conceive, along the scale from the most generalized conception to the most particularized, and choose some formulation - some conception or definition of the "idea" - for the purpose of distinguishing between the idea and its expression... SECOND, the decision maker must focus upon whether an alleged expression of the idea is limited to elements essential to expression of that idea (or is one of only a few ways of expressing the idea) or instead includes identifiable elements of expression not essential to every expression of that idea. THIRD, having identified elements of expression not essential to every expression of the idea, the decisionmaker must focus on whether those elements2 10are a substantial part of the allegedly copyrightable "work." Initially, the court determined that the mere idea of an electronic spreadsheet was not copyrightable. 2 1 1 However, the court noted that the general idea of an electronic spreadsheet could manifest itself through a variety of expressions. 2 12 If those expressions are found not to be essential to an electronic spreadsheet, the court then concluded, the expression would be copyrightable. 2 13 The court examined the menu command system and determined that the particular system designed by Lotus was not essential to the electronic spreadsheet and 2 14 was thus copyrightable. 209. Id. Paperback also maintained that the user interface of Lotus 1-2-3 was a "useful article," that is, an article having an "intrinsic utilitarian function." Id. at 54. The district court found that a "useful article," or rather the utilitarian aspect of a useful article, is not entitled to copyright protection. Id. at 52. This does not have the effect, the district court noted, of precluding a copyright simply because an intellectual work is practical and functional. Id. at 58. Expression in a useful article may be copyrighted, the court stated, provided such expression exists independently "of the functional ideas that make the article useful." Id. Indeed, the district court noted that expression is part of the test of copyrightability. Id. at 59-60. More than expression of an idea is necessary; in order to be copyrighted the work must express the idea in an original way. Id. 210. Paperback Software Intl, 740 F. Supp. at 60-61. 211. Id. at 65. 212. Id. 213. Id. at 67-68. The court found that the rotated "L"appearance of the spreadsheet on the screen, the designation of a particular key that will activate the menu command system, and the use of certain keys as symbols for mathematical functions are found "in most expressions of ... electronic spreadsheet computer programs," and are therefore not copyrightable. Id. 214. PaperbackSoftware Int'l, 740 F. Supp. at 67-68. 1374 CREIGHTON LAW REVIEW [Vol. 30 Having found the menu command system to be a mode of expression, the court then determined the command structure of Lotus 1-2-3 constituted original expression because other electronic spreadsheet programs incorporate different command structures. 2 1 5 Finally, the court determined that the Lotus 1-2-3 user interface was a substantial portion of the program, accounting for the program's overall popularity.2 16 Because Paperback's program copied a substantial portion of Lotus 1-2-3, the district court concluded that Paperback Software was 2 17 liable to Lotus for copyright infringement. Proof of Copying:Access and Substantial Similarity A second way to prove copying is by demonstrating that the infringing party had both access to the copyrighted material and that the infringing material bears a substantial similarity to the protected material. 2 18 In E.F. Johnson Co. v. Uniden Corporation of America, 2 19 the United States District Court for the District of Minnesota issued a preliminary injunction against Uniden Corporation of America ("Uniden") because E.F. Johnson Co. ("EFJ") demonstrated that it was likely to succeed on the merits of the copyright infringement action, namely copyright ownership, access, and the substantial similarity. 2 20 At issue in E.F. Johnson was software used in EFJ's mobile radios. 2 2 1 After EFJ examined other mobile radios containing similar software which were marketed by Uniden, EFJ commenced the instant copyright infringement action seeking to obtain the 2 22 injunction. The court recognized Uniden's admission that it had obtained and examined the EFJ programs while developing software for its own radio, proving that it had access to EFJ's programs. 2 23 Next, the court dealt with the issue of substantial similarity by requiring EFJ to demonstrate both that Uniden used EFJ's copyrighted work to develop its own software and, in doing so, precisely duplicated substantial por215. Id. 216. Id. at 68. 217. Id. at 84. 218. See supra note 191 and accompanying text. 219. 623 F. Supp. 1485 (D. Minn. 1985). 220. E.F. Johnson Co. v. Uniden Corp. of Am., 623 F. Supp. 1485, 1491-93, 1504 (D. Minn. 1985). In discussing the likelihood of EFJ's success on the merits, the court first noted that EFJ produced a copyright certificate. E.F. Johnson, 623 F. Supp. at 1492. The court stated that such a certificate was prima facie evidence of EFJ's ownership of the copyright and its validity. Id. 221. E.F. Johnson Co., 623 F. Supp. at 1487. 222. Id. 223. Id. at 1490. 1997] COPYRIGHT PROTECTION 1375 tions of EFJ's programs. 224 The district court satisfied this requirement by showing that the program's Barker Codes and H-Matrices, which are required in order for the radio to operate, were copied "verbatim" by Uniden. 2 25 Further proof of copying, the court indicated, could be found in the fact that superfluous instructions and errors present in the EFJ program were also found in the Uniden program. 22 6 Thus, the district court concluded that EFJ was likely to copyright infringement claim and granted a preliminary succeed in its 2 27 injunction. That same year SAS Institute, Inc. v. S & H Computer Systems, Inc.228 was decided by the United States District Court for the Middle District of Tennessee. 2 2 9 This case concerned the copyright infringement of a computer program, designed by SAS Institute, Inc. ("SAS"), which was designed to execute statistical analysis. 2 30 The district court held that copyright infringement occurred when the organizational and structural details of the copyrighted work were copied into another program. 23 1 While the SAS program could be operated only on IBM-compatible computers, SAS was attempting to adapt the pro- 224. Id. at 1492-93. The district court noted that in the Eighth Circuit, courts are required to resolve the issue of substantial similarity by determining "'whether the work is recognizable by an ordinary observer as having been taken from the copyrighted source'" unless the copyrighted material renders the test difficult to apply. Id. at 149293. In this case the district court noted that the software at issue was on computer chips fixed within mobile radios, making the software virtually indistinguishable by the ordinary observer. Id. at 1487, 1493. Thus, the district court followed what is known as the iterative test, which requires the author to demonstrate (1) that the infringer used the copyrighted work to prepare the copy and (2) that the infringing copy precisely duplicated substantial portions of the work protected by copyright. Id. at 1493. 225. E.F.Johnson Co., 623 F. Supp. at 1493-95. A Barker Code is a series of zeros and ones in a prepatterned sequence which must be identified by the radio in order for communication to occur. Id. at 1494. An H-Matrix is a series of ones and zeroes arranged in a matrix format that is used to detect transmission errors. Id. at 1495. 226. E.F. Johnson Co., 623 F. Supp. at 1495. 227. Id. at 1504. Uniden also proffered a 17 U.S.C. § 102(b) argument, which the court rejected. Id. at 1501. Uniden maintained that it copied the idea behind the EFJ radios, and any similarity was necessary in order to achieve compatibility. Id. The court stated this argument had been addressed before by other circuits, which looked to see if there were other ways to accomplish the same functions as the copyrighted program. Id. at 1501-02. If the copyrighted program is the only way to achieve the desired ends, then no infringement occurs. Id. at 1502. The court found that the software could have been designed several different ways. Id. Thus, the court rejected Uniden's section 102(b) argument. Id. at 1501. 228. 605 F. Supp. 816 (M.D. Tenn. 1985). 229. SAS Inst., Inc. v. S & H Computer Sys., Inc., 605 F. Supp. 816 (M.D. Tenn. 1985). 230. SAS Inst., Inc., 605 F. Supp. at 817. 231. Id. at 830. 1376 CREIGHTON LAW REVIEW [Vol. 30 gram so that it could be operated on other computers. 2 32 S & H Computer Systems, Inc. ("S & H") had obtained a license from SAS to operate its program on one IBM computer. 2 33 The court concluded that S & H then obtained the source code of the SAS program in order 2 34 to modify the SAS program so that it would run on VAX computers. Further, the court found that S & H used the SAS source code to prepare the S & H program. 23 5 Later, as the district court noted, S & H 2 36 attempted "to mask and disguise evidence of copying." The district court indicated that similarities existed between the two programs. 2 37 S & H argued, however, that these similarities were uncopyrightable ideas and that any copying which may have occurred 8 23 was insignificant when compared to the SAS program as a whole. S & H also argued that significant portions of its program were origi- nal. 23 9 The court rejected S & H's initial argument, stating that S & H copied expression and cited forty-four specific examples of copying which were deemed by the court to be substantial. 240 Therefore, the court found the two programs to be substantially similar. 2 41 Further, the court indicated that S & H's originality argument was irrelevant, noting that the S & H program was obviously based upon the SAS work. 2 42 The court therefore concluded that SAS' copyright was in2 43 fringed upon by S & H. 232. Id. at 818. VAX computers are manufactured by the Digital Equipment Corpo- ration. Id. The IBM-compatible program developed by SAS could not be run on VAX computers. Id. at 819. 233. SAS Inst., Inc., 605 F. Supp. at 821. 234. Id. at 820. 235. Id. at 822-23. Evidence of copying by S & H included an attempt to change the caption of the output label, alteration of the term "SAS" in the source code which resulted in incoherent statements, selection of "'driver routine' names" which closely resembled that chosen by SAS, the lack of design documentation for the S & H product, the presence of non-functional features in the S & H product that can only be discovered through the SAS source code, and a lack of organizational. patterns utilized by S & H. Id. at 823-25. Further, the court indicated that S & H could not overcome the presumption of validity attached to the SAS copyright registration. Id. at 826-27. Therefore, the court found the SAS copyright to be "valid and fully enforceable." Id. at 827. 236. SAS Inst., Inc., 605 F. Supp. at 822-23. 237. Id. at 829. Similarities between the two programs were corroborated by S & H's expert witness. Id. 238. SAS Inst., Inc., 605 F. Supp. at 829. 239. Id. at 830. 240. Id. at 829-30. 241. Id. at 830. 242. Id. S & H also argued that any infringement could be remedied by "simple excision." Id. at 831. The court likened this to S & H misappropriating every feature of a building and then "changing the tint of the windows and the color of the siding" in order to resolve the impropriety if its actions. Id. The court stated that this argument 'must be rejected." Id. 243. SAS Inst., Inc., 605 F. Supp. at 831. 1997] COPYRIGHT PROTECTION 1377 The overall structure of a computer program may be protected by copyright when a variety of methods of expression are available to the author. 2 44 In BroderbundSoftware, Inc. v. Unison World, Inc.,245 the United States District Court for the Northern District of California found that two computer programs were substantially similar, and thus, the creation of the subsequent program infringed upon the copyright of the original work. 2 46 In Broderbund, Pixellite Software ("Pixellite") developed and obtained a copyright for a computer program entitled "The Print Shop," which with the aid of audiovisual displays produced customized banners, greeting cards, and posters. 2 47 In 1984, Broderbund Software, Inc ("Broderbund") began distributing Print Shop. 248 At that time, the program was compatible only with Apple computers. 24 9 Subsequently, Broderbund and Unison World, Inc. ("Unison World") began negotiations to alter the program and make it operable on IBM computers. 250 An agreement, however, was never reached between the two companies and the negotiations ended. 25 1 Before the negotiations terminated, however, Unison had already begun to develop the IBM-compatible software using the Apple software supplied by Broderbund. 252 During the next year Unison completed work on the allegedly infringing program, entitled "Printmaster," and began to market it in March 1985.253 Shortly thereafter, Broderbund and Pixellite then brought a copyright in25 4 fringement against Unison in the district court. The district court emphasized that a variety of existing methods of expression were available to a programmer which would achieve the same function as Print Shop. 2 55 Although the court found adequate direct evidence that copying had taken place, the court, "in the interest of creating a comprehensive record," addressed the issues of access and substantial similarity. 2 56 Initially, the court found that Unison 244. See infra notes 255-66 and accompanying text. 245. 648 F. Supp. 1127 (N.D. Cal. 1986). 246. Broderbund Software, Inc. v. Unison World, Inc., 648 F. Supp. 1127, 1129, (N.D. Cal. 1986). Broderbund Software, Inc. was the exclusive licensee of the copyrighted software. Broderbund Software, Inc., 648 F. Supp. at 1129-30. 247. Broderbund Software, Inc., 648 F. Supp. at 1131. 248. Id. at 1130. 249. Id. 250. Id. 251. Id. at 1131. 252. Id. at 1130-31. 253. Id. 254. Id. at 1131. 255. Id. at 1134. 256. Id. at 1135-36. The court stated that direct evidence of copying consisted in part of the uncontradicted testimony that Unison World's president, Hong Lu, and products manager, David Lodge, instructed their programmers to copy the Broderbund program. Id. at 1130-31, 1135. 1378 CREIGHTON LAW REVIEW [Vol. 30 had access to several copies of the copyrighted Pixellite program. 2 57 While Unison did not have access to the source or object code of the copyrighted work, the court indicated that copying could be accomplished without such access. 25 s In order to determine substantial sim25 9 ilarity, the court applied an "extrinsic" test and an "intrinsic" test. The court explained that the extrinsic test was used to determine if any substantial similarities were present in the underlying ideas of the two works at issue. 260 The intrinsic test, on the other hand, was used to determine if any substantial similarity existed with regard to 26 1 the underlying idea's expression. The district court's application of the extrinsic test showed that the two programs were substantially similar. 2 62 The court found that the banner, greeting cards, and posters a user could achieve with the programs, as well as the printers used by each, were identical. 2 6 3 The court also found substantial similarity when applying the intrinsic test. 264 The court stated that the screens of the two programs possessed an "eerie resemblance," as well as finding that the screen sequence, layout, choices offered, and mode of feedback were all substantially similar. 26 5 Accordingly, the court concluded Unison in26 6 fringed on the copyright held by Pixellite. 257. Broderbund Software, Inc., 648 F. Supp. at 1136. 258. Id. 259. Id. 260. Id. The district court stated that expert testimony may be received for the extrinsic test only. Id. 261. Broderbund Software, Inc., 648 F. Supp. at 1136. 262. Id. at 1136-37. 263. Id. at 1136. 264. Id. at 1137. 265. Id. The court stated that "no ordinary observer could reasonably conclude that the expression of the ideas underlying these two programs were not substantially similar." Id. 266. BroderbundSoftware, Inc., 648 F. Supp. at 1138. For a case declining to find copyright infringement despite there being substantial similarity between two programs, see Plains Cotton Co-op. Ass'n v. Goodpasture Computer Serv., Inc., 807 F.2d 1256 (5th Cir. 1987). This matter was a copyright infringement case involving computer programs that were designed by the Plains Cotton Cooperative Association ("Plains Cotton") to allow users to obtain information regarding the cotton market. PlainsCotton Co-op. Ass'n, 807 F.2d at 1258. The individuals instrumental in creating the Plains Cotton software subsequently went to work for Goodpasture Computer Service ("Goodpasture"). Id. at 1258. One of these former Plains Cotton employees, Richard R. Fisher, brought with him the program designs of the Plains Cotton software when he went to work for Goodpasture. Id. at 1259. Shortly thereafter, Goodpasture developed its own program which was similar to the program produced and copyrighted by Plains Cotton. Id. Plains Cotton commenced a copyright infringement action in the United States District Court for the Northern District of Texas seeking a preliminary injunction. Id. at 1257. The district court, however, determined the authors of the Goodpasture program relied on their experience and knowledge of the cotton industry and did not copy the 1997] COPYRIGHT PROTECTION 1379 While Broderbund addressed the audiovisual displays of a computer program, the United States District Court for the District of Connecticut concluded that copyright infringement occurred when the screen displays of two separate programs were found to be substantially similar. 2 67 In ManufacturersTechnologies, Inc. v. Cams, Inc.,268 the district court held that a copyright owned by Manufacturers Technologies, Inc.'s ("MTI") was infringed by Cams, Inc. ("Cams") when Cams willfully copied the screen displays associated with MTI's copyrighted computer program. 26 9 In 1982, MTI created a program that allowed a user to predetermine the cost of producing certain manufactured parts. 2 70 With the assistance of two former MTI sales associates and photographs of seven screen displays created by the MTI 271 program, Cams developed a program that achieved the same end. Soon thereafter, MTI filed suit in district court alleging that Cams infringed upon MTI's copyrights when Cams created its own program.272 Cams did not contest MTI's ownership of the copyrights in question, but instead argued that functional considerations severely limited the manner in which Cams could express the idea of costestimating.2 73 Therefore, Cams argued, any cost-estimation program would be similar, perhaps even identical, to the program created by MTI. 2 74 The district court rejected this argument, stating that the sePlains Cotton work when they created the Goodpasture program. Id. at 1260-61. Thus, the district court denied the injunction sought by Plains Cotton. Id. at 1259. On appeal to the United States Court of Appeals for the Fifth Circuit, the court noted that, but for an abuse of discretion by the district court, the Fifth Circuit was required to affirm the judgment of the district court. Id. The Fifth Circuit declined to find that the district court had abused its discretion, noting that the district court was entitled to rely on the testimony of several witness who collectively maintained the Goodpasture program was the result of the authors' experience and knowledge of the cotton industry and was not created by copying the. Plains Cotton program. Id. at 126061. Thus, the Fifth Circuit affirmed the district court's denial of the injunction sought by Plains Cotton. Id. at 1262. 267. Broderbund Software, Inc., 648 F. Supp. at 1138. See infra notes 277-81 and accompanying text. 268. 706 F. Supp. 984 (1989). 269. Manufacturers Tech., Inc. v. Cams, Inc., 706 F. Supp. 984, 1002 (D. Conn. 1989). The court found that copyrights which had been registered for the screen displays and the program itself had both been infringed. Id. The United States Copyright Office decided that copyright registration for a computer program extends to the screen display and no longer accepts separate registrations. Id. at 990-91. The court in Manufacturers Technologies specifically found that a single copyright registration of a computer program would register the program itself and the screen displays or user interface of that program. Id. at 993. 270. Manufacturers Tech., Inc., 706 F. Supp. at 988. 271. Id. at 988, 990. 272. Id. at 987, 990. 273. Id. at 993.2 274. Id. 1380 CREIGHTON LAW REVIEW [Vol. 30 quence and flow of screen displays present in the MTI program were unique to the user operating the program and not dictated by functional considerations. 2 75 The screen display of the MTI program provided the user with a status report as the program operated, and the court found the selection of what was reflected in the status report 27 6 was copyrightable expression. The district court stated that in order to prevail on its claim of copyright infringement MTI had to prove that its program and the one produced by Cams were substantially similar. 27 7 In its substantial similarity analysis, the court applied a two-part test, which first addressed whether the non-protected aspects of the programs were so analogous that copying was indicated, and secondly, examined the similarities between any of the protected elements of copyrighted program and the allegedly infringing work to discover if infringement had occurred. 2 78 In applying the first part of this test, the court noted that MTI offered testimony from several witnesses which indicated that the independent development of the screen pages present in these programs was impossible. 2 79 As for the second part, the court found that the sequencing and flow of the screen displays in both programs paralleled each other. 28 0 Given the similarity present between these two programs, the court held that Cams' "illicit copying" of the protected 28 screen displays constituted copyright infringement. ' In Telemarketing Resources v. Symantec Corporation,28 2 however, the United States District Court for the Northern District of California found that portions of two computer outlining programs were sufficiently different to preclude a finding of infringement. 28 3 In Telemarketing Resources, the programmer, John L. Friend, developed both programs; the first he sold to Brown Bag Software ("Brown Bag"), and the second, a later version, he sold to the Symantec Corporation ("Symantec").2 84 Brown Bag maintained that the subsequent pro275. Id. at 994. 276. Id. at 996. 277. Id. at 990. The district court also stated that MTI had to prove that Cams had access to the MTI screen displays which was clearly established from the facts of the case. Id. at 1000. 278. ManufacturersTech., Inc., 706 F. Supp. at 1000. The district court stated that expert testimony may be received in order to make the first determination. Id. 279. Manufacturers Tech., Inc., 706 F. Supp. at 1000. 280. Id. at 1001. 281. Id. at 1001-02. 282. 1989 WL 200350 (N.D. Cal. 1989), affd in partsub nom. Brown Bag Software v. Symantec Corp., 960 F.2d 1465 (9th Cir. 1992). 283. Telemarketing Resources, v. Symantec Corp., No. C88-20352 RPA, 1989 WL 200350, at *6-7 (N.D. Cal. 1989), affd in part sub noa. Brown Bag Software v. Symantec Corp., 960 F.2d 1465 (9th Cir. 1992). 284. Telemarketing Resources, 1989 WL 200350, at *1. 1997] COPYRIGHT PROTECTION 1381 gram infringed upon its copyright of the earlier program. 28 5 Symantec responded that the features it28 6purportedly copied were unprotectable ideas and not expressions. The district court applied both the "extrinsic" and "intrinsic" analyses to determine whether the two programs were substantially similar. 2 8 7 The court noted that aesthetic differences existed between the programs, such as the pull down menus and color schemes used in the screen displays. 288 Additionally, the court determined that different functions were offered by each program and those functions were not similarly accessed. 28 9 Thus, the district court concluded that Brown Bag failed to establish that substantial similarity existed between the two programs. 290 Accordingly, the district court entered2 9summary 1 judgment for Symantec, from which Brown Bag appealed. On appeal, the United States Court of Appeals for the Ninth Circuit upheld the district court's grant of summary judgment. 2 92 The Ninth Circuit addressed Brown Bag's contention that the district court erred in its substantial similarity analysis. 29 3 Specifically, Brown Bag argued that the district court erred when it compared "specific screens, menus, and keystrokes" and did not adequately evaluate the "overall look and feel" of the two programs in its analysis of substantial similarity. 2 94 The Ninth Circuit disagreed, noting that it was proper for the district court to compare the expression present within the two programs, a comparison that was performed at the request of Brown Bag, who had never requested that the district court 285. Id. at *2. 286. Id. 287. Id. at *3. 288. Id. at *6. 289. Id. at *5. 290. Id. at *6-7. Brown Bag maintained that printing, editing, and accessing work being done with either program showed substantial similarity. Id. at *4-5. The court rejected this assertion, stating that these concepts are inherent to any computer outlining program. Id. at *4.Brown Bag also pointed out that nine functions offered on both programs were similar. Id. at *5. The court agreed, but pointed out that these functions were extremely different in their corresponding features. Id. Brown Bag argued further that similarity was shown by the pull down menus and main editing screens of the two programs. Id. This argument similarly failed before the district court, since the pull down menus of the two programs looked different. Id. As for the main editing screens, the court found that such a devise was essential to the idea of the program. Id. The court indicated that while some of the colors present in the two screens were similar, the limited number of colors from which to choose prevented copyright protection for a choice of colors. Id. Lastly, Brown Bag directed the court's attention to the similarities in the opening menus of the two programs. Id. at *6. The court noted that each program's opening menu offered a different number of options, distinct descriptions of the functions, and different access to the functions. Id. 291. Brown Bag Software v. Symantec Corp., 960 F.2d 1465, 1468 (9th Cir. 1992). 292. Brown Bag Software, 960 F.2d at 1478. 293. Id. at 1473. 294. Id. at 1475. 1382 CREIGHTON LAW REVIEW [Vol. 30 measure the "overall look and feel" of the programs at issue. 29 5 Accordingly, the Ninth Circuit affirmed the judgment of the district court. 2 96 Subsequently, in 1992, the United States Court of Appeals for the Second Circuit fashioned the abstraction-fitration-comparison test, a three-step analysis to determine whether a computer program's nonliteral elements were substantially similar. 29 7 In the first step of the analysis, the abstraction phase, a court disassembles the copied program's structure and identifies the elements present within it. 298 The starting point of the abstraction analysis is an examination of the program's code, and the inquiry ends with an explanation of the program's function. 2 99 The second step, filtration, scrutinizes the structural components of the program. 300 The purpose of filtration is to determine whether each component is (1) an "idea," (2) is incidental to the idea because of concerns for efficiency, (3) is a component required by factors other than the program, or (4) is nonprotectable expression obtained from the public domain. 30 1 The final step in the analysis is comparison.3 0 2 The comparison phase determines whether the protected expression has been duplicated; if so, the court must also evaluate the significance of the copied expression as it relates to the 303 copyrighted program as a whole. In Computer Associates International, Inc. v. Altai, Inc.,304 the United States Court of Appeals for the Second Circuit first announced the abstraction-fitration-comparison test for substantial similarity. 30 5 In Altai, a job scheduling program was created by Computer Associates International ("CA") which allowed the user to operate 295. Id. at 1476. 296. Id. at 1478. 297. See infra notes 298-303, 318 and accompanying text. 298. Computer Assocs. Int'l, Inc. v. Altai, Inc., 982 F.2d 693, 707 (2nd Cir. 1992). The United States Court of Appeals for the Tenth Circuit identified the "elements" to include the program's main purpose, structure and architecture, modules, algorithms and data structures, source code, and object code. Gates Rubber Co., 9 F.3d at 835. 299. Computer Assocs. Int'l, Inc., 982 F.2d at 707. 300. Id. 301. Id. For example, an "idea" would be a general statement concerning what the work is about. Id. at 705. An example of a component essential to the idea because of concerns for efficiency would be if there was only one or two subroutines possible for a given program that could achieve a particular option. Id. at 708. Similarly, the mechanical specifications of a computer is a factor other than the program which could restrict a programmer's freedom of choice. Id. at 709-10. Further, an example of nonprotectable expression present in the public domain are works created in antiquity. Concrete Mach. Co., Inc., 843 F.2d at 610. 302. Computer Assocs. Int'l, Inc., 982 F.2d at 710. 303. Id. 304. 982 F.2d 693 (2nd Cir. 1992). 305. MiTek Holdings, Inc. v. Arce Eng'g Co., Inc., 864 F. Supp. 1568, 1577 (S.D. Fla. 1994), aftd, 89 F.3d 1548 (11th Cir. 1996). COPYRIGHT PROTECTION 1997] 1383 multiple operating systems while maintaining the same software on a computer.3 0 6 Altai created its own job scheduling program (the "first Altai program"), with the assistance of a former CA programmer, Claude F. Arney, III, and a copy of the source code for the CA program. 30 7 Mr. Arney incorporated thirty percent of this source code in the first Altai Program.3 0S Once Altai discovered what Mr. Arney had done, its president, James P. Williams, arranged to have the Altai program rewritten so that any portion obtained from the CA program would not be retained, which resulted in yet another Altai program (the "second Altai program"). 30 9 After discovering that Altai may have appropriated a portion of its program, CA obtained a copyright in its program and filed a copyright infringement action in the United 3 10 States District Court for the District of New Jersey. The district court held that Altai was liable to CA only for the copyright infringement that led to the first Altai program. 31 1 The district court did not find that CA's copyright was infringed when the second Altai program was created because a comparison of the two programs revealed that copied portions of the CA program either could not be protected by copyright or that the two programs were not substantially similar. 312 In concluding that the two programs were not substantially similar, the district court separated the second Altai program by levels of abstraction, excluded any expression which was not protectable by copyright, and then addressed the similarities remaining in elements of the two programs. 3 13 The remaining elements, the court noted, were either not protectable by copyright or not substantially similar.3 14 Accordingly, the district court denied CA re306. 307. 308. Computer Assocs. Int'l, 982 F.2d at 699. Id. at 699-700. Id. at 700. 309. Id. 310. Eastern 311. 312. 313. Id. The case was later transferred to the United States District Court for the District of New York. Id. Computer Assocs. Int'l, 982 F.2d at 701. Id. at 714-15. Id. at 714. 314. Id. at 714-15. The district court found that the second Altai program contained "virtually no lines of code" from the CA program. Id. at 714. With regard to the parameter lists and macros of the two programs, the district court found any elements copied were minimal, taken from the public domain, or imposed by the programs' functional demands. Id. Further, the district court found the similarities present between the "list of services" present in the two programs were imposed by the other programs with which the CA and second Altai programs were designed to interact, and therefore were not grounds for copyright infringement. Id. Lastly, the district court determined similarities between the program's organizational charts "follow naturally from the work's theme" rendering them unprotectable due to the scene a faire doctrine. Id. at 715. 1384 CREIGHTON LAW REVIEW [Vol. 30 to lief on this portion of its copyright infringement claim; CA appealed 3 15 the United States Court of Appeals for the Second Circuit. On appeal, CA contended that the district court had erred in its substantial similarity analysis in not concluding that the second Altai program infringed on CA's copyright in its program. 3 16 The Second Circuit pointed out that copyright protection extends to the literal and nonliteral portions of a computer program. 3 17 In determining the scope of this protection, the Ninth Circuit stated that district courts would be "well-advised" to apply the abstraction-fitration-comparison test "in order to determine whether the nonliteral elements of two or more computer programs are substantially similar."3 18 Because the Second Circuit accepted the district court's "overly thorough" substantial similarity analysis, the district court's denial of CA's copyright infringement claim was affirmed. 3 19 The following year the United States Court of Appeals for the Tenth Circuit applied the abstraction-filtration-comparison test in Autoskill, Inc. v. NationalEducationalSupport Systems, Inc.,320 in order to determine whether any portion of a copyrighted computer program designed to assist students with their reading skills was protectable by copyright and, if so, whether these protectable elements were substantially similar to an allegedly infringing work. 3 2 1 In Autoskill, a Canadian software development company, Autoskill, Inc. ("Autoskill"), developed and copyrighted an educational computer program and then negotiated with National Educational Support Systems, Inc. ("NESS") to market the program. 3 22 After failing to obtain the marketing rights to the Autoskill program, NESS enlisted the 3 23 services of a programmer to assist it in developing its own program. Less than two years after the NESS program was completed, Autoskill brought a copyright infringement action seeking to enjoin NESS from manufacturing or distributing any portion of its program containing 32 4 elements of the Autoskill program. Granting the requested injunction, the United States District Court for the District of New Mexico found that Autoskill would likely 315. Computer Assocs. Int'l, 982 F.2d at 701, 715. 316. Id. at 701. 317. Id. at 702. This protection is similar to that afforded to literary works. Id. at 701. 318. Computer Assocs. Int'l, 982 F.2d at 706. 319. Id. at 714-15. 320. 994 F.2d 1476 (10th Cir. 1993). 321. Autoskill, Inc. v. National Educ. Support Sys., Inc., 994 F.2d 1476, 1481, 1490 (10th Cir. 1993). 322. Autoskill, Inc., 994 F.2d at 1481. 323. Id. at 1481-82. NESS provided its programmers with an Autoskill sales brochure in order to assist their development of the new program. Id. at 1482. 324. Autoskill, Inc., 994 F.2d at 1482. 1997] COPYRIGHT PROTECTION 1385 succeed on the merits of its infringement claim. 3 25 The district court identified numerous similarities between the NESS program and the "most important protectable aspects of Autoskill's Program," which included the reading test protocols, word choices, feedback provided to the user, and the user's progression through the tests. 3 26 NESS appealed the district court's ruling to the United States Court of Appeals 3 27 for the Tenth Circuit. The Tenth Circuit initially determined that NESS failed to rebut the presumption of ownership created by Autoskill's copyright registration certificate, the first element of a copyright infringement claim. 3 28 The court then addressed the issue of whether NESS had copied the Autoskill program. 32 9 To circumstantially satisfy this element, the court noted, Autoskill must show that the alleged infringer had access to the copyrighted work and developed a program substantially similar to its own. 330 The Tenth Circuit found there to be "no question that NESS had access to the Autoskill Program" and agreed with the district court that the NESS founders were "'thoroughly familiar with the Autoskill Program.'" 33 1 The court's inquiry then sought to identify whether the two programs were substantially 332 similar. The Tenth Circuit noted that the district court used a variation of the abstraction-fitration-comparison test set forth in the Second Circuit's Altai decision. 33 3 The Tenth Circuit affirmed the district court's findings regarding the abstraction phase, noting that the concept of the program-to teach reading skills-could not be copyrighted because it was an idea. 33 4 Moreover, the Tenth Circuit affirmed the dis- trict court's conclusions that the portion of the Autoskill program which placed students into special categories according to their respective reading difficulties was public information and could not be copyrighted. 33 5 Prior to concluding the abstraction portion of its anal325. Autoskill, Inc. v. National Educ. Support Sys., Inc., 793 F. Supp. 1557, 1573 (D.N.M. 1992), afftd, 994 F.2d 1476 (10th Cir. 1993). The district court also found that Autoskill owned a valid copyright and, with regard to access, "there is no question that NESS had access to the Autoskill program." Autoskil, Inc., 793 F. Supp. at 1563. 326. Autoskill, Inc., 793 F. Supp. at 1569. 327. AutoskilU, Inc., 994 F.2d at 1481. 328. Id. at 1487-88. 329. Id. at 1489. 330. Id. 331. Id. at 1489-90. One of the NESS founders had sold computers which contained the Autoskill program. Id. at 1490. 332. Autoskill, Inc., 994 F.2d at 1490-91. 333. Id. at 1490. For a complete discussion of the Computer Assocs. Int'l, Inc. case, see supra notes 297-319 and accompanying text. 334. Autoskill, Inc., 994 F.2d at 1492-93. 335. Id. at 1492. 1386 CREIGHTON LAW REVIEW [Vol. 30 ysis, the Tenth Circuit addressed a section 102(b) argument made by NESS. 33 6 NESS maintained that copyright protection would deny others the "educational processes, methods and procedures . . ." con- tained in the Autoskill program. 33 7 The Tenth Circuit disagreed with NESS' argument and concurred with the trial court's statement that "more than a literal application of the statute is required."3 38 The Tenth Circuit also affirmed the district court's findings throughout its filtration analysis. 339 The program's mode of testing and diagnosis of reading disabilities survived the Tenth Circuit's filtration analysis, despite NESS' argument that the entire Autoskill program had been obtained from the public domain and could not be copyrighted.3 40 The Tenth Circuit noted that the elements remaining after fitration revealed numerous similarities; for example, the tests given as well as the types of words used by each program were identical. 34 1 Thus, the Tenth Circuit affirmed the district court's findings 34 2 and resolution of Autoskill's copyright infringement claim. At least one court has applied the abstraction-filtration-comparison test and concluded that a computer program's menu command structure is not subject to copyright protection. 34 3 In MiTek Holdings, Inc. v. Arce EngineeringCo., Inc.,344 the United States District Court for the Southern District of Florida concluded that the menu used by a program designed to produce architectural blueprints was "a process that is not entitled to copyright protection."3 45 In MiTek, the copyrighted program was owned by MiTek Holdings, Inc. ("MiTek") and was written by its then-employee Emilio Sotolongo. 34 6 Sotolongo left MiTek's employ to work for Arce Engineering Co., Inc. ("Arce"), where he was instructed to develop a similar program "'from scratch."' 3 4 7 Shortly after completion of the Arce program, MiTek filed a copyright 336. Id. at 1493. 337. Id. 338. Id. 339. Id. at 1496. 340. Id. 341. Id. at 1497. It is doubtful that NESS was aided by its concession that there were "many similarities" between the two programs and the testimony of a lead NESS witness that elements of the Autoskill program that were arguably protectable were present in the NESS program. Id. 342. Autoskill, Inc., 994 F.2d at 1498. 343. MiTek Holdings, Inc. v. Arce Eng'g Co., Inc., 864 F. Supp. 1568, 1580 (S.D. Fla. 1994), affd, 89 F.3d 1548 (11th Cir. 1996). 344. 864 F. Supp. 1568 (S.D. Fla. 1994), aftd, 89 F.3d 1548 (11th Cir. 1996). 345. MiTek Holdings, Inc., 864 F. Supp. at 1580. The program at issue was a "layout program" whose purpose it was to determine the size and location of wood trusses within a structure. Id. at 1572. Wood trusses are a group of beams that support a roof. Id. 346. MiTek Holdings, Inc., 864 F. Supp. at 1572-73. 347. Id. at 1574. 1997] COPYRIGHT PROTECTION 1387 infringement action, alleging that eighteen nonliteral elements of its program were protected by copyright and infringed upon when Arce 3 48 developed its own program. The district court analyzed these eighteen nonliteral elements using the widely accepted abstraction-filtration-comparison test.34 9 Because the parties identified the nonliteral elements of the program at issue, the court's analysis was confined to the filtration and comparison portions of the test. 5 0° During application of the fitration analysis, the district court "'flter[ed] out' the unprotectable elements [of the program] to obtain a core of protectable expression." 35 1 One of the elements fitered out by the district court was the MiTek program's "main menu command system" because the court determined it was an unprotectable process.3 52 Despite testimony that the menus of the two programs operated "in an almost identical manner," the district court denied MiTek protection for its menu because the menu's operation was similar to that of a draftsman attempting to complete the same task manually. 353 The district court then examined the visual appearance of each menu and found they were not substantially similar.3 5 4 This filtration analysis did not render unprotectable the entirety of the MiTek program, as the district court found that four out of five protectable elements of the MiTek program were substantially similar to portions of the Arce program.3 5 5 The district court determined, however, that the elements which were substantially similar were "de minimis" and, accordingly, denied MiTek's request for a pre3 56 liminary injunction. ANALYSIS In Lotus Development Corp. v. Borland International,Inc. ,357 the United States Court of Appeals for the First Circuit held that a menu command hierarchy was a "method of operation" as defined in Title 17 348. Id. at 1574-75. 349. Id. at 1577, 1579-84. The district court found that MiTek held a valid copyright in its program and that Arces had access to the MiTek program since both were authored by Emilio Sotolongo. Id. at 1579. This left the court's consideration only whether the MiTek and Arces programs were substantially similar. Id. 350. MiTek Holdings, Inc., 864 F. Supp. at 1579. 351. Id. at 1578. 352. Id. at 1579-80. 353. Id. at 1580. 354. Id. 355. Id. at 1584. These were the "shorthand method of entering distances with the mouse," the "expression of work planes without reference to real walls," the "use of reference lines," the "entry of walls in free form," and the "expression of three dimensional views by the entry of two angles." Id. at 1583-84. 356. MiTek Holdings, Inc., 864 F. Supp. at 1584-85. 357. 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). 1388 CREIGHTON LAW REVIEW [Vol. 30 of the United States Code section 102(b) ("section 102(b)") and, accordingly, was not subject to copyright protection. 358 Although a computer's menu command hierarchy is arguably subject to copyright protection given its originality and expression, the First Circuit relied instead on section 102(b) to deny copyright protection. 3 59 Despite contrary holdings by other federal courts that similar user interfaces may be protected by copyright, the court in Borland disagreed, stating that "the initial inquiry should not be whether individual components of a menu command hierarchy are expressive, but rather whether the menu command hierarchy as a whole can be copyrighted." 360 The First Circuit's holding has the potential to severely restrict copyright protection for user interfaces. 36 1 Indeed, such an overinclusive view of section 102(b) could have broad reaching consequences, such as precluding copyright protection for many menus and user interfaces. 3 62 In Borland, the United States District Court for the District of Massachusetts found that the copyright possessed by Lotus Development Co. ("Lotus") in the spreadsheet program Lotus 1-2-3 was infringed by Borland International ("Borland") when Borland incorporated the Lotus 1-2-3 menu into its Quattro and Quattro Pro programs. 3 6 3 The district court found the Lotus 1-2-3 menu was an original work and contained expression, noting that several different methods were available to Lotus in order to achieve the desired menu. 3 64 It was the definition, arrangement, and identification of the commands within the menu, the court found, that allowed the menu to 358. Lotus Dev. Corp. v. Borland Intl, Inc., 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). For the full text of section 102(b), see supranote 30. 359. Lotus Dev. Corp. v. Paperback Software Int'l, 740 F. Supp. 37, 68 (D. Mass. 1990) (holding that the Lotus 1-2-3 menu command structure is an "original and nonobvious" mode of expression); Lotus Dev. Corp. v. Borland Int'l, Inc., 799 F. Supp. 203, 209 (D. Mass. 1992), rev'd, 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision) (stating that "a menu command hierarchy is copyrightable subject matter"). Author's note: hereinafter this case will be referred to as Borland II. 360. Lotus Dev. Corp., 49 F.3d at 815; Manufacturers Tech., Inc. v. Cams, Inc., 706 F. Supp. 984, 1002 (D. Conn. 1989) (finding that "screen pages" could be protected by copyright); Digital Communications Assocs., Inc. v. Softklone Distrib. Corp., 659 F. Supp. 449, 463 (N.D. Ga. 1987) (holding that the "arrangement and design of parameter/command terms" within a "status screen" can be protected by copyright); Broderbund Software, Inc. v. Unison World, Inc., 648 F. Supp. 1127, 1138 (N.D. Cal. 1986) (concluding that "audiovisual displays" may be protected by copyright). 361. Dale M. Cendali & Martin Glenn, In Lotus, the 1st Circuit Departedfrom Precedent, Narrowing Protection for Developed Software and Giving Crafty Litigators a Blank Disk on Which to Write, 17 NAT'L L.J. B7 (May 15, 1995). 362. Arthur R. Miller, Copyright Protectionfor Computer Programs,Databases,and Computer-GeneratedWorks: Is Anything New Since CONTU?, 106 HARv. L. REV.978, 1008 (1993). 363. Borland 11, 799 F. Supp. at 223. 364. Id. at 218. 1997] COPYRIGHT PROTECTION 1389 be protected by copyright.3 6 5 Accordingly, the district court granted the permanent injunction requested by Lotus prohibiting Borland from manufacturing or distributing its Quattro or Quattro Pro computer programs containing any form of the Lotus 1-2-3 menu com3 66 mands or structure. The United States Court of Appeals for the First Circuit reversed, holding that section 102(b) precluded copyright protection for the menu command hierarchy of Lotus 1-2-3.367 Noting that section 102(b) does not allow a method of operation to be copyrighted, and that a method of operation "refers to the means by which a person operates something," the First Circuit concluded that the Lotus 1-2-3 menu was an unprotectable method of operation. 3 68 Moreover, the First Circuit declined to apply the abstraction-fitration-comparison analysis typically undertaken by courts addressing copyright infringement claims involving computer software. 3 6 9 The First Circuit found this test "to be of little help in assessing whether the literal copying of 3 70 a menu command hierarchy constitutes copyright infringement." Thus, the First Circuit relied solely on section 102(b), finding that Borland did not commit copyright infringement when it placed an identi371 cal copy of the Lotus menu in its own computer program. THE CONGRESSIONAL INTENT BEHIND SECTION 102(B) AND THE JUDICIAL INTERPRETATIONS THAT FOLLOWED As part of the Copyright Act of 1976, Congress enacted section 102(b), intending to codify the idea-expression dichotomy.3 7 2 That intent is reflected in the legislative history, specifically in House Report No. 94-1476 ("House Report"), which states that section 102(b) was intended "to make clear that the expression adopted by the program365. Lotus Dev. Corp. v. Borland Intl, Inc., 831 F. Supp. 202, 211 (D. Mass. 1992), reu'd, 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). Author's note: hereinafter this case will be referred to as Borland III. 366. Lotus Dev. Corp. v. Borland Intl, Inc., 831 F. Supp. 223, 245-46 (D. Mass. 1993), rev'd, 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). Author's note: hereinafter this case will be referred to as Borland IV. 367. Lotus Dev. Corp., 49 F.3d at 815. 368. Id. 369. Id. at 815; MiTek Holdings, Inc. v. Arce Eng'g Co., Inc., 864 F. Supp. 1568, 1577 (S.D. Fla. 1994) (stating that the approach for determining the copyrightability of the nonliteral elements of a computer program is the widely accepted "abstraction-filtration-comparison"test), affd, 89 F.3d 1548 (11th Cir. 1996). 370. Lotus Dev. Corp., 49 F.3d at 815. 371. Id. at 819. 372. The Copyright Act of 1976, Pub. L. No. 94-553, § 102(b), 90 Stat. 2541, 2545; Steven R. Englund, Note, Idea, Process, or Protected Expression?: Determining the Scope of Copyright Protection of the Structure of Computer Programs,88 MICH. L. REV. 866, 875 (1990). 1390 CREIGHTON LAW REVIEW [Vol. 30 mer is the copyrightable element in a computer program, and that the actual processes or methods embodied in the program are not within the scope of the copyright law."3 73 The House Report further main- tained that section 102(b) "in no way enlarges or contracts the scope of dichotomy between exprescopyright protection" and that "the3 basic 74 sion and idea remains unchanged." While the First Circuit maintained that it was "navigating in unchartered waters," other courts have addressed section 102(b) as it applies to the copyright infringement of a computer program. 3 75 In fact, the Congressional intent behind section 102(b) has been addressed by several federal courts. 3 76 For example, in Autoskill, Inc. v. National Educational Support Systems, Inc.,3 77 the United States District Court for the District of New Mexico noted that Congress had no intention of affecting the scope of copyright protection by enacting section 102(b).3 7 8 Indeed, when applying section 102(b), the district court stated that "more is required, however, than a literal application of the language of the statute."3 79 The district court in Autoskill determined that, when applying section 102(b), a comparison of the computer program at issue with relevant case law addressing the dichotomy between idea and expression was a "must."3 0 Further, in Gates Rubber Co. v. Bando Chemical Industries, Ltd.,381 the United States Court of Appeals for the Tenth Circuit determined that section 102(b) codified the "fundamental tenet" of copyright law that original expression may be protected by copyright, while the same protection is 373. H.R. REP. No. 94-1476, at 57 (1976), reprinted in 1976 U.S.C.C.A.N. 5659, 5670. 374. Id. 375. Lotus Dev. Corp., 49 F.3d at 813 (stating that "we know of no cases that deal with the copyrightability of a menu command hierarchy standing on its own (i.e., without other elements of the user interface, such as the screen displays, in issue)."). See infra notes 377-87 and accompanying text. 376. See infra notes 377-87 and accompanying text. 377. 793 F. Supp. 1557 (D.N.M. 1992), affd, 994 F.2d 1476 (10th Cir. 1993). 378. Autoskill, Inc. v. National Educ. Support Sys., Inc., 793 F. Supp. 1557, 1564 (D.N.M. 1992), affd, 994 F.2d 1476 (10th Cir. 1993). See also Computer Assocs. Intl, Inc. v. Altai, Inc., 982 F.2d 693, 703 (2d Cir. 1992) (stating that Congress intended the copyright in a computer program to protect the "'programmer's expression of original ideas, as distinguished from the ideas themselves"'); Whelan Assocs., Inc. v. Jaslow Dental Lab., Inc., 797 F.2d 1222, 1234 (3d Cir. 1986) (finding that Congress aimed to codify the idea-expression dichotomy when it adopted § 102(b)); M. Kramer Mfg. Co., Inc. v. Andrews, 783 F.2d 421, 434-35 (4th Cir. 1986) (stating the "legislative purpose" of § 102(b) was to allow the "expression" found within a computer program to be copyrighted). 379. Autoskill, Inc., 793 F. Supp. at 1564. 380. Id. 381. 9 F.3d 823 (10th Cir. 1993). COPYRIGHT PROTECTION 1997] 1391 not available to the ideas found within that expression.38 2 The Tenth Circuit also construed the legislative history behind section 102(b) as clarifying any ambiguity concerning the state of the copyright of processes.3 8 3 Although section 102(b) prohibits processes from being copyrighted, the Tenth Circuit noted that an author's description of a process can be protected by copyright so long as it contains some originality. 38 4 Similarly, in Lotus Development Corporation v. Paperback 3 8 5 the United States District Court for the Software International, District of Massachusetts found that Congress intended to use the idea-expression dichotomy "as part of the test of copyrightability for computer programs." 38 6 The district court in Paperback determined that Congress "extend[ed] copyright protection to original expression embodied in computer programs .... ." and that such a "conclusion is consistent with the treatment of other kinds of intellectual works "387 In Borland, however, the First Circuit chose to define a section 102(b) "method of operation" as "the means by which a person operates something, whether it be a car, a food processor, or a computer."38 8 Citing no precedent to support this definition, or its conclusion that the "Lotus menu command hierarchy is a method of operation," the First Circuit held the Lotus menu command hierarchy was "uncopyrightable." 38 9 Despite Gates Rubber and Paperback, which collectively stand for the proposition that original expression present in a computer program may be protected by copyright, and the admonition of Autoskill that more than a literal application of section 102(b) was required, the First Circuit denied copyright protection to the Lotus menu command hierarchy. 390 Construing the First Circuit's conclusion as an overinclusive view of section 102(b), copyright protection would, arguably, no longer be available for a computer pro391 gram's menu and user interface. 382. Gates Rubber Co. v. Bando Chemical Indus., Ltd., 9 F.3d 823, 836 (10th Cir. 1993). 383. Gates Rubber Co., 9 F.3d at 836. 384. Id. at 837. 385. 740 F. Supp. 37 (D. Mass. 1990). 386. Paperback Software Int, 740 F. Supp. at 54. 387. Id. 388. Lotus Dev. Corp., 49 F.3d at 815. 389. Id. 390. Lotus Dev. Corp., 49 F.3d at 819; Gates Rubber Co., 9 F.3d at 836-37; Autoskill, 793 F. Supp. at 1564; PaperbackSoftware Int'l, 740 F. Supp. at 54. 391. Miller, 106 HARv. L. REv. at 1008. 1392 CREIGHTON LAW REVIEW [Vol. 30 JUDICIAL OPINIONS ADDRESSING MENUS, SCREEN DISPLAYS, AND PROGRAM STRUCTURE In Borland, the First Circuit initially addressed whether the Lotus menu command hierarchy could be copyrighted.3 9 2 The First Circuit resolved this inquiry, determining that the Lotus menu command 393 hierarchy was, pursuant to section 102(b), a method of operation. Because a method of operation cannot be copyrighted, the First Circuit reasoned, Borland did not infringe on the Lotus copyright when it and placed it into its Quattro copied the menu command 3 hierarchy 94 and Quattro Pro programs. However, the First Circuit in Borland was not the first federal court to address the copyrightability of a menu present in a computer program. 39 5 In Digital Communications Associates v. Softklone Distributing Corporation,39 6 the United States District Court for the Northern District of Georgia found that the arrangement of terms 397 within the main menu of a computer program could be copyrighted. In Digital Communications, the computer program at issue enabled computers to "'communicate' with other computers," and did so through the use of a "main menu," which specifically contributed to the program's success.3 98 In identifying exactly what portion of the main menu was "idea" and what portion was "expression," the district court stated that the "'idea' is the process or manner by which the status screen [or main menu],.. . operates and the 'expression is the method by which the idea is communicated to the user." 39 9 Because the main menu had previously been copyrighted, the district court concluded that the reproduction of the main menu constituted copy40 0 right infringement. Likewise, in Manufacturers Technologies, Inc. v. Cams, Inc.,401 the United States District Court for the District of Connecticut determined that the copying of a computer program's screen displays constituted copyright infringement. 40 2 The district court found that 392. Lotus Dev. Corp., 49 F.3d at 815. 393. Id. 394. Id. at 819. 395. See infra notes 396-410 and accompanying text. 396. 659 F. Supp. 449 (N.D. Ga. 1987). 397. Digital Communications Assocs., Inc. v. Softklone Distrib. Corp., 659 F. Supp. 449, 463 (N.D. Ga. 1987). 398. Digital Communications Assoc., Inc., 659 F. Supp. at 452. 399. Id. at 458. The district court in Digital apparently found that § 102(b) was inapplicable to this case, as the court cited this statute for the proposition that ideas cannot be copyrighted. Id. at 457 (citing 17 U.S.C. § 102(b) (1982)). 400. Digital Communications Assocs., Inc., 659 F. Supp. at 465. 401. 706 F. Supp. 984 (D. Conn. 1989). 402. Manufacturers Tech., Inc., 706 F. Supp. at 1002. 1997] COPYRIGHT PROTECTION 1393 copyright protection extended to the arrangement of words in the screen display and the manner in which the display communicated information to a user. 40 3 When such copyrighted material was copied, the court determined that the copyright at issue had been 40 4 infringed. Moreover, in SAS Institute, Inc. v. S & H Computer Systems, Inc.,405 and Whelan Associates, Inc. v. Jaslow Dental Laboratory, Inc.,406 the structure and organization of computer programs were found to be protected by copyright. 40 7 In SAS Institute, the United States District Court for the Middle District of Tennessee determined that the expression of the "functional abilities, ideas, methods, and 40 8 processes" of the program at issue were not restricted in any way. Instead, the court characterized the duplication of the organizational structure of the copyrighted work as being "unnecessary" and "intentional" on the part of the infringer. 40 9 The United States Court of Appeals for the Third Circuit took a similar approach in Whelan, finding that because a "variety of program structures" existed through which the idea of the program could be expressed, such structure was not a necessity and could therefore be copyrighted. 4 10 The First Circuit in Borland reached the opposite conclusion, however, and held that the menu command hierarchy of Lotus 1-2-3, part of the program's user interface, was uncopyrightable subject matter. 4 11 Because this aspect of the Lotus 1-2-3 user interface was not subject to copyright protection, the First Circuit concluded that Borland's copying did not consti4 12 tute copyright infringement. Other federal courts have found that the alleged similarities between two computer programs do not rise to the level of copyright infringement, yet, these courts maintain that copyright protection is available for several aspects of a computer program. 4 13 For example, the United States District Court for the Northern District of California supported this proposition in Telemarketing Resources v. Symantec Corp.,4 14 where it found that the "overall structure and 403. 404. 405. 406. Id. at 996. Id. at 1002. 605 F. Supp. 816 (M.D. Tenn. 1985). 797 F.2d 1222 (3d Cir. 1986). 407. SAS Inst., Inc. v. S & H Computer Sys., Inc., 605 F. Supp. 816, 830 (M.D. Tenn. 1985); Whelan Assocs., Inc. v. Jaslow Dental Lab., Inc., 797 F.2d 1222, 1248 (3d Cir. 1986). 408. SAS Inst., Inc., 605 F. Supp. at 825. 409. Id. 410. Whelan Assocs., Inc., 797 F.2d at 1240, 1248. 411. 412. 413. 414. Lotus Dev. Corp., 49 F.3d at 819. Id. See infra notes 414-19 and accompanying text. 1989 WL 200350 (N.D. Cal. 1989), affd, 960 F.2d 1465 (9th Cir. 1992). 1394 CREIGHTON LAW REVIEW [Vol. 30 organization of a computer program, including its audiovisual displays, or screen.. ." could be protected by copyright. 4 15 The district court held, however, that since the two screens at issue were not substantially similar there was no infringement of the copyrighted com4 16 puter screen. Similarly, in MiTek Holdings, Inc. v. Arce Engineering Co., Inc. ,417 the United States District Court for the Southern District of Florida found that the owner of a copyright in a computer program is entitled to protection not only for the way in which the program interacts with the user, but also for the commands a programmer selects to obtain a certain result. 4 18 Without citing section 102(b), however, the district court determined that copyright protection was not available, because the way in which the menu at issue operated was a "process" which mimicked what a human would do if attempting to complete the same task by hand.4 19 In Borland, however, the First Circuit found that selecting commands in Lotus 1-2-3 was comparable to using the function buttons on a VCR. 4 20 Like the menu command hierarchy, these VCR buttons were, according to the court, a method of operation 42 1 and therefore not subject to copyright protection. In Telemarketing Resources, the district court concluded that no copyright infringement occurred because the programs at issue were not substantially similar.4 22 A similar determination was made by the district court in MiTek Holdings, despite evidence that the programs at issue operated "in an almost identical manner."4 23 However, the First Circuit in Borland never addressed substantial similarity and instead relied on section 102(b) and a VCR analogy to determine that the Lotus 1-2-3 menu command hierarchy could not be protected by copyright. 42 4 Unfortunately, in the rapidly expanding world of technology, perhaps "something more than an analogy to VCR buttons 425 [was] needed to support such an important decision." 415. Telemarketing Resources v. Symantec Corp., No. C88-20352 RPA, 1989 WL 200350, at *2 (N.D. Cal. 1989), affd sub nom. Brown Bag Software v. Symantec Corp. 960 F.2d 1465 (9th Cir. 1992). In Telemarketing Resources, however, the lack of substantial similarity between the programs at issue was the district court's reason for denying copyright protection, a conclusion that was affirmed by the United States Court of Appeals for the Ninth Circuit. Telernarketing Resources, 1989 WL 200350, at *7. 416. Telemarketing Resources, 1989 WL 200350, at *7. 417. 864 F. Supp. 1568 (S.D. Fla. 1994). 418. MiTek Holdings, Inc., 864 F. Supp. at 1577. 419. Id. at 1580. 420. Lotus Dev. Corp., 49 F.3d at 817. 421. Id. 422. Telemarketing Resources, 1989 WL 200350, at *6. 423. MiTek Holdings, Inc., 864 F. Supp. at 1580. 424. Lotus Dev. Corp., 49 F.3d at 815, 817. 425. Cendali & Glen, 17 NAT'L L.J. at B7. COPYRIGHT PROTECTION 1997] 1395 ORIGINALITY AND EXPRESSION The district court in Borland found that the Lotus 1-2-3 menu contained expression. 426 Indeed, in Paperback, the Lotus 1-2-3 menu had been found by the same district court to be an "original and nonobvious" mode of expression.4 27 The district court determined that alternative methods of design were available for the menus present within the Borland program. 428 Borland itself, as the court noted, designed an alternate menu tree for use in its program. 4 29 The district court determined that it was possible to produce millions of different menu trees. 4 30 However, the United States Court of Appeals for the First Circuit held that different design options and expressions were irrelevant. 43 1 Thus, any inquiry into originality or expression was precluded because, the First Circuit determined, the menu command hierarchy was an uncopyrightable "method of operation" under 43 section 102(b). 2 The United States Supreme Court has maintained that the "principal focus" of section 102 the Copyright Act of 1976 is to determine whether the originality requirement has been sufficiently met to merit copyright protection. 4 33 While originality is a relatively low standard to meet, it requires that a work possess some creativity and be an independent creation of the author.4 3 4 In Gates Rubber, the United States Court of Appeals for the Tenth Circuit determined that it is "one of the fundamental tenets of copyright law that protection extends only to the author's original expression ....,,435 In fact, prior to the First Circuit's decision in Borland, the United States District Court for the District of Massachusetts addressed originality, expression, and the Lotus 1-2-3 copyright in Paperback.43 6 To the district court in Paperback, the existence of numerous methods in which to express an idea allowed one of those expressions to be protected by 426. Borland III, 831 F. Supp. at 211. 427. PaperbackSoftware Int'l, 740 F. Supp. at 68. The Honorable Robert Keeton of the United States District Court for the District of Massachusetts was the trial judge in both Paperback Software Int'l and Borland. Miller, 106 HARv. L. REV.at 998, 1011. 428. Borland 1I, 799 F. Supp. at 217. 429. Id. 430. Id. 431. Lotus Dev. Corp., 49 F.3d at 816. 432. Id. at 815-16. 433. Feist Publications, Inc. v. Rural Tel. Serv. Co., Inc., 499 U.S. 340, 358 (1991). The Court was discussing the originality requirement as it related to the extent of copyright protection afforded to a telephone book. Id. at 342. The Court referred to originality as the "sine qua non of copyright." Id. at 348. A sine qua non is an indispensable requisite. BLAcK's LAw DICTIONARY 1385 (6th ed. 1990). 434. See supra notes 69-70 and accompanying text 435. Gates Rubber Co., 9 F.3d at 836. 436. Paperback Software Int'l, 740 F. Supp. at 59-60. CREIGHTON LAW REVIEW 1396 [Vol. 30 copyright. 43 7 The district court in Paperback determined that the Lotus 1-2-3 menu structure could be expressed in an unlimited number of ways. 4 3 8 In Digital Communications, the United States District Court for the Northern District of Georgia found the arrangement and design of the "parameter/command terms" within a computer program's status screen could be copyrighted. 4 39 The court found that this aspect of the program could have been expressed in an infinite number of ways. 4 4 0 Further, in Pearl Systems, Inc. v. Competition Electronics,Inc. ,441 the United States District Court for the Southern District of Florida made a similar finding when considering the subroutines of a computer program. 4 42 The existence of several alternatives for the design of the subroutines was determined by the court to 44 3 reveal the existence of many forms of expression. In addressing a computer program's input formats, the United States Court of Appeals for the Fifth Circuit found in EngineeringDynamics, Inc. v. StructuralSoftware, Inc. 4 4 4 that the placement of data within a computer program could be "unique and original." 4 45 The Fifth Circuit determined that the computer program's creativity was 4 46 reflected by the existence of other programs in the same market. The existence of alternatives in E.F. Johnson Co. v. Uniden Corporation ofAmerica 4 4 7 led the United States District Court for the District of Minnesota to find that the expression which existed within a computer program had been copied. 448 The district court maintained that the program at issue could have been independently created, thereby avoiding the reproduction of a copyrighted work. 44 9 Similarly, the differences present in two programs' user interfaces in Broderbund Software Inc. v. Unison World, Inc.45 0 led the United States District Court for the Northern District of California to reject a contention that the idea behind the program, and the expression of that idea, were 437. 438. Id. at 59. Id. at 68. 439. Digital Communications Assocs., Inc., 659 F. Supp. at 463. 440. Id. at 460. 441. 1988 WL 146047 (S.D. Fla. 1988). 442. PearlSys. Inc. v. Competition Elecs., Inc., No. 87-6278-CIV-MARCUS, 1988 WL 146047, at *6 (S.D. Fla. 1988). 443. Pearl Sys., Inc., 1988 WL 146047, at *6. 444. 26 F.3d 1335 (5th Cir. 1994). 445. Engineering Dynamics, Inc. v. Structural Software, Inc., 26 F.3d 1335, 1346 (5th Cir. 1994), opinion supp. by 46 F.3d 408 (5th Cir. 1988). 446. EngineeringDynamics, Inc., 26 F.3d at 1346. 447. 623 F. Supp. 1485 (D. Minn. 1985). 448. E.F. Johnson Co. v. Uniden Co. of Am., 623 F. Supp. 1485, 1503 (D. Minn. 1985). 449. E.F. Johnson Co., 623 F. Supp. at 1503. 450. 648 F. Supp. 1127 (N.D. Cal. 1986). 1997] COPYRIGHT PROTECTION 1397 indistinguishable. 4 5 1 Where the menu screens are different, the court multiple modes of expression available to a found, there4 5 are 2 programmer. Of these cases, Paperback, Digital Communications, Pearl Systems, E.F. Johnson, and Broderbund all resulted in decisions of copyright infringement or a finding that there was a substantial likelihood of success on such a claim. 45 3 While neither court in Gates Rubber or EngineeringDynamics reached a similar conclusion, in Gates Rubber the Tenth Circuit remanded the case so that the trial court could determine exactly which elements of the computer program at issue were protectable by copyright. 4 54 Likewise, in EngineeringDynamics, the Fifth Circuit remanded the case to the trial court in order to determine if similarities between the programs at issue were imposed by 4 55 the engineering industry. In Borland, the United States District Court for the District of Massachusetts addressed originality and expression. 4 56 The court found that functional considerations do not control the configuration of the Lotus 1-2-3 menu. 45 7 The existence of different menu trees in other spreadsheet programs, the court stated, established that the Lotus 1-2-3 menu was but one of many forms of expression that could be adopted. 458 Indeed, other spreadsheet programs, such as Microsoft Excel, achieved commercial success without being perfectly compatible with Lotus 1-2-3. 45 9 The district court determined that originality was present in the Lotus 1-2-3 menu because a "wide variety of expression [was] possible." 46 0 On appeal, the United States Court of Appeals for the First Circuit determined that the existence of alternative designs was irrelevant. 46 1 According to the First Circuit, "if specific words are essential to operating something, then they are part of a 'method of operation' and, as such, are unprotectable (by copy451. Broderbund Software, Inc. v. Unison World, Inc., 648 F. Supp. 1127, 1132 (N.D. Cal. 1986). 452. BroderbundSoftware, Inc., 648 F. Supp. at 1132. See also id. at 1134 (stating the programmer "had available a wide range of expression."). 453. Digital CommunicationsAssocs., Inc., 659 F. Supp. at 465; PaperbackSoftware Int'l, 740 F. Supp. at 70, 84; PearlSys., Inc., 1988 WL 146047 at *7; E.F. Johnson Co., 623 F. Supp. at 1504; BroderbundSoftware, Inc., 648 F. Supp. at 1138. 454. Gates Rubber Co., 9 F.3d at 842; Engineering Dynamics, Inc., 26 F.3d at 1351. 455. EngineeringDynamics, 26 F.3d at 1347. 456. Borland III, 831 F. Supp. at 211, 216. 457. Id. at 213. 458. Id. at 214. 459. Paperback Software Int', 740 F. Supp. at 69. 460. Borland III, 831 F. Supp. at 216-17. 461. Lotus Dev. Corp., 49 F.3d at 816. CREIGHTON LAW REVIEW 1398 right]." 46 2 [Vol. 30 As correctly noted by the district court, however, specific 4 63 words are not essential in order to operate the Lotus 1-2-3 menu. THE FIRST CIRCUIT'S DISCUSSION OF THE ALTA/ TEST In Borland,the First Circuit determined that the Altai test would "be of little help in assessing whether the literal copying of a menu command hierarchy constitutes copyright infringement."4 64 The First Circuit characterized the Altai test as having been developed by the United States Court of Appeals for the Second Circuit "to deal with the fact that computer programs, copyrighted as literary works, can be infringed by what is known as 'nonliteral' copying, which is copying that is paraphrased or loosely paraphrased rather than word for word."4 65 The First Circuit continued, stating that: [W]e are not confronted with alleged nonliteral copying of computer code. Rather, we are faced with Borland's deliberate, literal copying of the Lotus menu command hierarchy.... ... [the Altai test] obscures the more fundamental question of whether a menu command hierarchy can be copyrighted at all. The initial inquiry should not be whether individual components of a menu command hierarchy are expressive, but menu command hierarchy as a whole can rather whether 4the 66 be copyrighted. Despite the First Circuit's description of the test developed by the United States Court of Appeals for the Second Circuit in Altai as having been developed to deal with the "'nonliteral' copying" of computer programs, the test developed by the Second Circuit was not concerned with "'nonliteral' copying."4 67 The issue before the Second Circuit was whether "the scope of copyright protection . . . extend[ed] to a com- puter program's non-literal structure."4 68 In order to make this determination, the Second Circuit recommended "a three-step procedure ...in order to determine whether the non-literal elements of two or more computer programs are substantially similar."4 6 9 This threestep procedure consists of (1) abstraction, where a court identifies the individual elements of the program, (2) filtration, the determination of whether or not the identified elements can be protected by copyright, 462. Id. 463. Borland I, 799 F. Supp. at 217. 464. Lotus Dev. Corp., 49 F.3d at 815. 465. Id. at 814 (citing Computer Assocs. Int'l, Inc. v. Altai, Inc., 982 F.2d 693, 701 (2nd Cir. 1992)). 466. Id. at 814-15. 467. Lotus Dev. Corp., 49 F.3d at 814; Computer Assocs. Int'l, Inc., 982 F.2d at 706. 468. Computer Assocs. Int'l, Inc., 982 F.2d at 703. 469. Id. at 706. 1997] COPYRIGHT PROTECTION 1399 and (3) comparison, which is to determine if the protected work was copied. 4 70 The Second Circuit provided examples of the non-literal elements of a computer program, indicating that "general flow charts as well as the more specific organization of inter-modular relationships, parameter lists, and macros . . ." were all non-literal elements of a computer program. 47 1 The court noted that Congress intended for computer programs to be treated as literary works and, generally speaking, the non-literal elements of literary works could be protected by copyright. 47 2 However, the Second Circuit also emphasized "that, like all copyright infringement cases, those that involve computer programs are highly fact specific" and "the amount of protection due... will vary according to the protectable expression found to exist within 473 the program at issue." The Altai test for substantial similarity was not needed to determine if the menu command hierarchy in Lotus 1-2-3 was substantially similar to the Lotus 1-2-3 menu command hierarchy found in Borland's programs because Borland admitted that it placed "'a virtually identical copy of the entire 1-2-3 menu tree"' in its Quattro and Quattro Pro programs. 4 74 Accordingly, while the First Circuit correctly chose not to use the Altai test, its reasoning for not making use of this test was incorrect. 4 75 This test was designed to determine if the nonliteral elements of two computer programs were substantially similar, and not, as the First Circuit maintained, to determine if a copyright 4 76 has been infringed by "'nonliteral' copying." INFRINGEMENT OF THE COPYRIGHT OF LOTUS 1-2-3 In Borland, the First Circuit recognized that there are two elements of a copyright infringement claim: (1) that one own a valid copy470. Id. at 706-11. For further discussion of the Altai test, see supra notes 297-303 and accompanying text. 471. 472. 473. 474. 475. Computer Assoc. Int'l, Inc., 982 F.2d at 702. Id. Id. at 715. Lotus Dev. Corp., 49 F.3d at 810. See infra note 476 and accompanying text. 476. EngineeringDynamics, Inc., 26 F.3d at 1342 (endorsing the "abstraction-filtration-comparison method of determining copyright protection for computer programs."); Gates Rubber Co., 9 F.3d at 834 (adopting the "Abstraction-Filtration-Comparison" test in order to ascertain those portions of a computer program that can be protected); MiTek Holdings, Inc., 864 F. Supp. at 1577 (stating that the approach for determining the copyrightability of the nonliteral elements of a computer program is the widely accepted "abstraction-filtration-comparison"test). Compare Computer Assocs. Int'l, Inc., 982 F.2d at 706 (stating "that district courts would be well-advised to undertake... [this] test... in order to determine whether the non-literal elements of two or more computer programs are substantially similar.") with Lotus Dev. Corp., 49 F.3d at 815 (holding that "the Altai test may provide a useful framework for assessing the alleged nonliteral copying of computer code .... ). 1400 CREIGHTON LAW REVIEW [Vol. 30 right, and (2) the copying of elements of the copyrighted work which are original. 4 77 The First Circuit indicated that both of these elements were satisfied, "for Borland concedes that Lotus has a valid copyright in Lotus 1-2-3 as a whole and admits to factually copying the Lotus menu command hierarchy." 478 Borland copied the Lotus 12-3 menu command hierarchy so that users accustomed to the Lotus 12-3 program could easily adapt to the Borland program. 47 9 Borland contended that such copying was lawful because it only "copied the unprotectable menus of Lotus 1-2-3."480 Therefore, the First Circuit computer stated, the issue that needed to be resolved was "whether a 48 1 menu command hierarchy is copyrightable subject matter." The United States Constitution grants Congress the power to promote science by providing an author or inventor with exclusive rights to their work for a specific period of time. 48 2 In fact, the economic philosophy which serves as the foundation of this constitutional provision maintains that the public welfare can best be achieved by promoting individual effort. 488 The policy behind copyright law is to create 48 4 incentives for development by guaranteeing inventors a fair return. This incentive must be balanced, however,485with dissemination, so that learning and progress may be promoted. A large degree of individuality goes into computer programming.48 6 A majority of the work that goes into the creation of a com- puter program is found in conceptualizing the program and its user interface.48 7 A computer program's menu is one portion of the user interface, the creation of which is a difficult intellectual task.48 8 The creativity and investment necessary in order to design a user interface 477. Lotus Serv. Co., 499 478. Id. at 479. Id. at 480. Id. at Dev. Corp., 49 F.3d at 813 (citing Feist Publications, Inc. v. Rural Tel. U.S. 340, 361 (1991)). 813. 810. 812. 481. Id. at 809. U.S. CONST. art. I, § 8, cl. 8. 483. Peter S. Menell, An Analysis of the Scope of Copyright Protection for Application Programs, 41 STAN. L. REv. 1045, 1058 (1989). 484. Gates Rubber Co., 9 F.3d at 839. 485. Id. 486. Miller, 106 HARV. L. REv. at 984. 487. Paperback Software Int'l, 740 F. Supp. at 56. 488. Miller, 106 HARv. L. REV. at 984 n. 25 (stating that a "user interface includes the keyboard, mouse, and screen, as well as the program-specific user interface, such as menus, commands, prompts, and displays,"); Paperback Software Int'l, 740 F. Supp. at 56 (finding that the development of a computer program's user interface "is a more difficult intellectual task" than the program's encoding). 482. 1997] COPYRIGHT PROTECTION 1401 are enormous. 48 9 Many times,490it is the user interface which makes a computer program successful. In Borland, however, the First Circuit did not protect the Lotus copyright, instead ruling that the Lotus 1-2-3 menu command hierarchy was uncopyrightable subject matter. 49 1 The First Circuit reached this conclusion despite the fact that the Lotus 1-2-3 menu was not required in order to operate the Borland programs. 4 92 Borland designed its own menu commands for Quattro and Quattro Pro, incorporating the Lotus 1-2-3 menu only to give users a choice of how to operate the Borland programs. 4 93 Despite the individuality, creativity, and investment present in a computer program's user interface, the court in Borland denied copyright protection to the menu command hierarchy 4 94 of Lotus 1-2-3. CONCLUSION 4 95 In Lotus Development Corporation v. Borland International, the United States Court of Appeals for the First Circuit held that the Lotus 1-2-3 "menu command hierarchy [was] an uncopyrightable 'method of operation'" as that term is used in Title 17 of the United States Code section 102(b). 4 9 6 Therefore, the First Circuit reasoned, Borland International ("Borland") did not infringe on the copyright that Lotus Development Corp. ("Lotus") had in Lotus 1-2-3 when Borland placed a "'virtually identical copy of the entire 1-2-3 menu tree'" 49 7 in its Quattro and Quattro Pro computer programs. The Borland decision provides an enormous disincentive for those who create computer programs, especially the user interfaces associated with many programs. According to Professor Arthur R. Miller, a computer program's: [ulser interface design is extremely resource-intensive, and a well-composed user interface is frequently the precise feature that renders a computer program successful .... [Piromoting the unauthorized copying of interfaces penalizes the creative effort of the original designer, something that runs directly counter to the core purposes of copyright law because it may 489. Miller, 106 HARv. L. REv. at 984. 490. Id. at 1033-34. 491. Lotus Dev. Corp., 49 F.3d at 819. 492. Id. at 810. 493. Id. 494. See infra notes 496-98 and accompanying text. 495. 49 F.3d 807 (1st Cir. 1995), affd mem., 116 S. Ct. 804 (1996) (4-4 decision). 496. Lotus Dev. Corp. v. Borland Intl, Inc., 49 F.3d 807, 815 (1st Cir. 1995), affd mem, 116 S. Ct. 804 (1996) (4-4 decision). 497. Lotus Dev. Corp., 49 F.3d at 810, 819. CREIGHTON LAW REVIEW 1402 [Vol. 30 freeze or substantially impede human innovation and techno4 98 logical growth. Although the First Circuit declared the menu of the Lotus 1-2-3 spreadsheet program to be a "method of operation" as that term is used in section 102(b), the court was unable to cite any precedent which defined or rendered insight into exactly what Congress meant by "method of operation."4 99 It is clear that Congress did not intend for section 102(b) to "enlarge or contract the scope of copyright protection . -so0In fact, Congress specifically provided that criminal penalties were to be imposed against "any person who infringes a copyright willfully and for the purposes of commercial advantage "501 Despite the legislative history and abundant case law in various circuits discussing section 102(b), the First Circuit held that a very important and creative aspect of the Lotus 1-2-3 spreadsheet-the 50 2 menu command hierarchy-could not be protected by copyright. This denial of copyright protection for the Lotus 1-2-3 menu, which is arguably a critical aspect of the program that Lotus expended considerable time, money, and resources to develop, strikes at the very heart of copyright law-the creation of incentives for development by guar50 3 anteeing inventors a fair return. The decision by the First Circuit leaves Lotus without any incentive to improve the Lotus 1-2-3 user interface. The Borland decision sends a clear message to Lotus, and any other computer programmer, that innovation will be penalized. Should an author expend the time, effort, and creative energies necessary in order to express their ideas in a form that can be classified as a "means by which a person operates something," the Borland decision effectively prohibits that individual from securing a copyright.5 0 4 Every element that succumbs to such a classification can be freely copied, even by competitors such as Borland, who here blatantly copied a menu from a popular computer program into their own program simply to "ease" the transition from the competitor's product to their own. Microsoft Excel achieved com498. Arthur R. Miller, Copyright Protectionfor Computer Programs,Databases,and Computer-GeneratedWorks: Is Anything New Since CONTU?, 106 HARv. L. REv.977, 1033-34 (1993). 499. Dale M. Cendali & Martin Glenn, In Lotus, the 1st Circuit Departedfrom Precedent, NarrowingProtectionfor Developed Software and Giving Crafty Litigatorsa Blank Disk on Which to Write, 17 NAT'L L.J. B7 (May 15, 1995). 500. H.R. REP. No. 94-1476, at 57 (1976), reprinted in 1976 U.S.C.C.A.N. 5659, 5670. 501. 17 U.S.C. § 506(a) (1994). 502. See supra notes 94-98, 372-87 and accompanying text. 503. Gates Rubber Co. v. Bando Chem. Indus., Ltd., 9 F.3d 823, 839 (10th Cir. 1993). 504. Lotus Dev. Corp., 49 F.3d at 815. 1997] COPYRIGHT PROTECTION 1403 mercial success without being perfectly compatible with Lotus 1-2-3, 50 5 and there was nothing preventing Borland from doing the same. While Borland was free to create a spreadsheet on a computer using its own software, Borland was not free to do so by pirating the creative 50 6 effort expended by Lotus. The United States Court of Appeals for the First Circuit recognized that its holding in Borland was in conflict with the decision of the United States Court of Appeals for the Tenth Circuit in Autoskill, Inc. v. National Education Support Systems, Inc.50 7 While a memorandum opinion from an equally divided United States Supreme Court effectively affirmed the First Circuit's decision, computer software developers, such as Lotus, eagerly await a Congressional response to the First Circuit's misapplication of section 102(b). 508 It is vital that any such response provide clear, effective copyright protection to what may be the most critical element of a computer program the user interface. Jeffrey M. Gott-'97 505. Lotus Dev. Corp. v. Paperback Software Intl, 740 F. Supp. 37, 69 (D. Mass. 1990). 506. E.F. Johnson Co. v. Uniden Corp. of Am., 623 F. Supp. 1485, 1504 (D. Minn. 1985). 507. Lotus Dev. Corp., 49 F.3d at 818. 508. Lotus Development Corp. v. Borland Intl, Inc., 116 S. Ct. 804 (1996) (mem.); Miller, 106 HAlv. L. REv. at 1033. 1404 CREIGHTON LAW REVIEW [Vol. 30