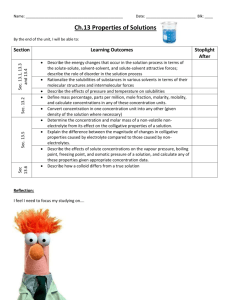
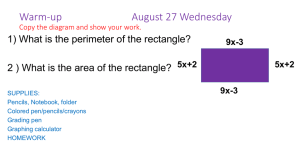
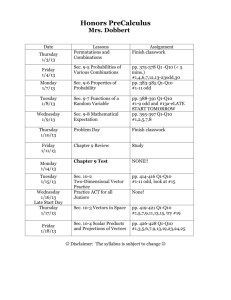
Agenda and Presentation Materials
advertisement

DISCUSS AND DISCOVER BDC Roundtable Thursday, September 11, 2014 Hosted by: Sponsored by: SUTHERL AND ASBILL & BRENNAN LLP www.sutherland.com Agenda RONALD REAGAN BUILDING AND INTERNATIONAL TRADE CENTER 1300 PENNSYLVANIA AVENUE, NW WASHINGTON, DC Thursday, September 11, 2014 GENERAL MEETING AGENDA 8:00 a.m. – 9:00 a.m. Continental Breakfast 9:00 a.m. – 9:15 a.m. Welcome 9:15 a.m. – 10:30 a.m. Regulatory, Legislative and Market Overview Panel Speakers Steve Boehm, Partner, Sutherland Cynthia Krus, Partner, Sutherland Brett Palmer, President, Small Business Investor Alliance Mark Timperman, Managing Director, Wells Fargo 10:30 a.m. – 10:45 a.m. Break 10:45 a.m. – 11:45 a.m. Facing Disclosure: Meet the SEC Reviewers Panel Speakers Jim Curtis, Branch Chief, Division of Investment Management, U.S. Securities and Exchange Commission Christina Fettig, Senior Accountant, Division of Investment Management, U.S. Securities and Exchange Commission John Ganley, Senior Counsel, Division of Investment Management, U.S. Securities and Exchange Commission Matt Giordano, Assistant Chief Accountant, Division of Investment Management, U.S. Securities and Exchange Commission Christian Sandoe, Assistant Director, Division of Investment Management, U.S. Securities and Exchange Commission 11:45 a.m. – 1:00 p.m. Lunch – Table Topics and Networking Join the table(s) of your choice to discuss current developments, challenges and new ideas around these subject areas, or network on your own. CCOs Enforcement Outsourcing Private Funds SBICs RONALD REAGAN BUILDING AND INTERNATIONAL TRADE CENTER 1300 PENNSYLVANIA AVENUE, NW WASHINGTON, DC Thursday, September 11, 2014 1:00 p.m. – 2:15 p.m. Financing Structures and Alternatives: What You Need to Know Panel Speakers Robert Copps, Partner, Sutherland Eric Fenichel, Partner, Sutherland Peter Fozzard, Partner, Sutherland Daphne Frydman, Partner, Sutherland Moderator: Cynthia Krus, Partner, Sutherland 2:15 p.m. – 3:15 p.m. Takedown Lowdown: Trends in Capital Raising Panel Speakers Paul Echausse, Chief Executive Officer and President, Alcentra Capital Corporation Larry Herman, Managing Director, Raymond James Alan Kirshenbaum, Chief Financial Officer, TPG Specialty Lending, Inc. Al Laufenberg, Managing Director, Keefe, Bruyette and Woods, a Stifel Company Rich Petrocelli, Chief Financial Officer, Fifth Street Finance Corp. / Fifth Street Senior Floating Rate Corp. Moderator: Harry Pangas, Partner, Sutherland 3:15 p.m. – 3:30 p.m. Break 3:30 p.m. – 4:30 p.m. OCIE Exams: What to Expect When the SEC Comes Calling Speakers Andrew Bowden, Director of the Office of Compliance Inspections and Examinations, U.S. Securities and Exchange Commission John Walsh, Partner, Sutherland 4:30 p.m. Closing Remarks Speaker Biographies 2014 BDC ROUNDTABLE Thursday, September 11, 2014 SPEAKER BIOGRAPHIES 2014 Regulatory, Legislative and Market Overview Steve Boehm, Partner, Sutherland Asbill & Brennan LLP Nationally recognized as an authority on business development companies (BDCs), Steve Boehm guides his clients in successfully navigating the intricate rules and regulations of the U.S. Securities and Exchange Commission (SEC), especially the Investment Company Act of 1940 and its 1980 amendments. Steve and his team represent many of the nation’s largest BDCs, which he advises on a broad range of legal matters and transactions, including initial public offerings (IPOs), debt financing and structural solutions. In his practice, Steve also represents registered and unregistered investment funds and investment advisers on a broad range of regulatory and transactional matters. Cynthia Krus, Partner, Sutherland Asbill & Brennan LLP Cynthia Krus, who serves as vice chair of Sutherland’s Corporate and Financial Services practices, has been involved in numerous public and private securities offerings and has advised clients in connection with a variety of corporate transactions including mergers and acquisitions, proxy contests, exchange and rights offerings, going-private transactions and reorganizations. She advises companies on the structure and formation of various entities and the establishment and operation of private and public equity, including business development companies (BDCs) and Small Business Investment Companies (SBICs). Cynthia counsels public companies in a broad range of corporate and securities matters, such as the Sarbanes-Oxley Act of 2002, corporate governance, disclosure, executive compensation and shareholder matters. Brett Palmer, President, Small Business Investor Alliance Brett T. Palmer is the president of the Small Business Investor Alliance (SBIA). In this role, Mr. Palmer works to foster a healthy environment for small business investing and a strong and profitable lower middle market. In addition to managing the SBIA organization, he serves as its principal liaison with Congress, the Executive Branch, and other industry organizations. Mr. Palmer brings years of valuable public policy and advocacy experience to SBIA. He served in the executive branch as a Presidential appointee in the Commerce Department as Assistant Secretary for Legislative Affairs and as Deputy Assistant Secretary for Trade Legislation. He served in a number of roles in Congress including as a policy aide for the Speaker of the House. Mr. Palmer graduated from Davidson College with a degree in history. Mark Timperman, Managing Director, Wells Fargo Mark Timperman is a managing director in the Financial Institutions group at Wells Fargo Securities and is head of the Asset Management Investment Banking practice. He is based in Charlotte. Mark joined Wells Fargo in 1997 and helped establish the Asset Management practice in 2003. He has extensive industry knowledge and long-term clients in both asset management and specialty finance. He helped build Wells Fargo’s position in underwriting business development companies and closed-end funds, and he has significant experience advising clients on capital markets and strategic transactions. Mark earned a B.A. from Duke University and an M.B.A. from the Darden School of Business at the University of Virginia. 2014 BDC ROUNDTABLE Thursday, September 11, 2014 SPEAKER BIOGRAPHIES Facing Disclosure: Meet the SEC Reviewers Jim Curtis, Branch Chief, Division of Investment Management, U.S. SEC Mr. Curtis currently is a branch chief in the Office of Chief Counsel of the Division of Investment Management. He has served as an attorney with the Securities and Exchange Commission since 1991 and has worked on various projects for offices within the Division of Investment Management. He is the author of “Special Duties of Closed-End Fund Directors,” a chapter in the treatise Fund Governance: Legal Duties of Investment Company Directors, published by the American Lawyer’s Law Journal Press. Prior to his employment with the SEC, Mr. Curtis was in private practice in New York. Before attending law school, he worked as a product manager for Seagram’s in New York. Mr. Curtis is a graduate of Hamilton College (B.A.), The Amos Tuck School of Business Administration (M.B.A.) and New York University School of Law (J.D.). The Securities and Exchange Commission, as a matter of policy, disclaims responsibility for any private publications or statements by any of its employees. The views expressed here are those of the author and do not necessarily reflect the views of the Commission or the others on the staff of the Commission. Christina Fettig, Senior Staff Accountant, Division of Investment Management, U.S. SEC Christina has a total of 16 years of asset management experience and currently has been with the SEC for 11 years as a Staff Accountant in the Division of Investment Management’s Disclosure Review and Accounting Office. Christina examines and analyzes, from an accounting and auditing perspective, all financial statements and other financial data included in registration statements, prospectuses and amendments filed under the Securities Act of 1933. She examines applications for registration and annual and semi-annual reports filed under the Investment Company Act of 1940. She conducts and participates in conferences with other members of the staff and with the Chief Accountant of the Division with respect to technical accounting and auditing problems arising in the examination and analysis of documents and conducts and participates in conferences with representatives and the accountants of registrants. Prior to joining the Commission, she was a Senior Associate in the Assurance and Business Advisory Services practice of PricewaterhouseCoopers LLP where she spent 5 years. At PricewaterhouseCoopers, Christina was responsible for the planning, execution and completion of audits of clients in the financial services industry, with an emphasis on investment management clients. Her responsibilities as a senior associate included supervising audit teams ranging from two to fifteen team members and accepting overall engagement responsibility as well as communicating with varying levels of client management as well as interacting directly with partners and managers. Christina is a Certified Public Accountant and received her BBA in Accounting from Loyola College in Maryland in 1998. Christina received her MBA with a concentration in Finance from Loyola College in Maryland. John Ganley, Senior Counsel, Division of Investment Management, U.S. SEC John Ganley has served with the SEC since 1990, first serving with the Office of the General Counsel before working with the Office of Disclosure Rulemaking. John currently serves with the Disclosure Review Office and the Division of Investment Management. John received his JD, with honors, from the George Washington University Law School and his B.S. from the University of Rochester. 2014 BDC ROUNDTABLE Thursday, September 11, 2014 SPEAKER BIOGRAPHIES Facing Disclosure: Meet the SEC Reviewers (cont.) Matt Giordano, Assistant Chief Accountant, Division of Investment Management, U.S. SEC Matt Giordano is an Assistant Chief Accountant for the Division of Investment Management at the U.S. Securities and Exchange Commission. Matt assists the Chief Accountant in interpreting new accounting regulations and directing the financial reporting and accounting practices of investment companies in compliance with the federal securities laws. Prior to joining the Commission, Matt was a Senior Manager at KPMG LLP, where he worked for approximately ten years specializing in audit and attest engagements for various investment management clients. As a Senior Manager at KPMG LLP, Matt was also a national instructor focusing on technical accounting and audit methodology topics. Matt received his BBA with a focus in Accounting from the University of Massachusetts and a MSA from Boston College. Matt is a Certified Public Accountant licensed in Massachusetts and New York. Christian Sandoe, Assistant Director, Division of Investment Management, U.S. SEC Christian Sandoe is an 18 year veteran of the SEC. Christian has spent the past 14 years with the Disclosure Review Office, specifically in the Division of Investment Management. Prior to this, Christian spent several years working with the Division of Enforcement in New York. Christian earned his LLM in Securities and Financial Regulation from Georgetown University law Center and received his JD from Suffolk University Law School. 2014 BDC ROUNDTABLE Thursday, September 11, 2014 SPEAKER BIOGRAPHIES Financing Structures and Alternatives: What You Need to Know Robert Copps, Partner, Sutherland Asbill & Brennan LLP Bob Copps is a corporate lawyer focusing on private investment funds and mergers and acquisitions. Bob represents private investment funds in all aspects of their operations, including fund formation, regulatory matters, the management of portfolio investments and exit transactions. Bob handles M&A transactions and general corporate matters for both publicly-traded and private corporate clients. He has worked with very prominent clients on several of the most significant transactions in the timber, water and natural resources industries. Eric Fenichel, Partner, Sutherland Asbill & Brennan LLP Eric Fenichel represents corporate and financial services clients in structured finance transactions. His clients include insurance companies, business development companies, energy dealers, financial services companies, timber investment management firms and commercial and industrial firms. Eric’s experience includes life insurance reserve securitizations, including XXX and AXXX reserve securitization financings; commercial loan portfolio financings, including CLO/CDO transactions; commodity financing arrangements in the energy industry; timber installment note transactions and general corporate finance transactions. Peter Fozzard, Partner, Sutherland Asbill & Brennan LLP Working primarily with generation and transmission cooperatives, renewable energy developers and lenders across the country, Peter Fozzard helps these clients finance utility, telecommunications and other corporate operations and project development. His finance background includes senior, second lien and subordinated commercial financings; private placements and other taxable long-term debt issuances; government-guaranteed financings; project financing; public, pollution control and industrial revenue bond issuances; structured financings of inventories; commercial paper offerings; lines of credit; and letter of credit transactions. Daphne Frydman, Partner, Sutherland Asbill & Brennan LLP Daphne Frydman helps companies in the financial services industry raise capital for their operations through a broad range of financing and other deals including structured finance, life insurance reserve securitizations, including XXX and AXXX reserve securitization financings, and general corporate finance transactions including senior debt financing, private debt placements and retail notes. Daphne also advises asset managers, insurance companies, public and private funds, business development companies and other investment vehicles, in their operations, structure, governance, CFTC registration, public offerings, private placements and compliance with the Dodd-Frank Act and applicable requirements of the U.S. Securities and Exchange Commission (SEC) exchange rules, the Commodity Futures Trading Commission (CFTC), and the National Futures Association (NFA). Cynthia Krus, Partner, Sutherland Asbill & Brennan LLP Cynthia Krus, who serves as vice chair of Sutherland’s Corporate and Financial Services practices, has been involved in numerous public and private securities offerings and has advised clients in connection with a variety of corporate transactions including mergers and acquisitions, proxy contests, exchange and rights offerings, going-private transactions and reorganizations. She advises companies on the structure and formation of various entities and the establishment and operation of private and public equity, including business development companies (BDCs) and Small Business Investment Companies (SBICs). Cynthia counsels public companies in a broad range of corporate and securities matters, such as the Sarbanes-Oxley Act of 2002, corporate governance, disclosure, executive compensation and shareholder matters. 2014 BDC ROUNDTABLE Thursday, September 11, 2014 SPEAKER BIOGRAPHIES Takedown Lowdown: Trends in Capital Raising Paul Echausse, Chief Executive Office and President, Alcentra Capital Corporation Paul is responsible for the overall management and direction of fund investing, including transaction sourcing, deal execution and the monitoring of portfolio companies. Paul is a member of the Investment Committee, serves as the Chairman of the board of directors of Grindmaster Cecilware Corporation and is a member of the board of directors of Emerald Waste Services, EB Brands, FST Technical Services, DRC and Battery Solutions. Paul brings more than 20 years of leveraged finance experience to the origination and management of the Partnership’s investment portfolios. Prior to joining Alcentra, Paul was President of Kisco Capital Corporation, the growth capital Small Business Investment Company affiliate of the Kohlberg family office. Previously, he was Chief Operating Officer of IBJS Capital Corporation, the junior capital investment affiliate of IBJ Schroder Bank. Prior to IBJS, Paul was the Assistant Division Head of Southeast Banking for the Bank of New York. Paul has served as President of the Northeast Regional Association of Small Business Investment Companies and on the national board of the National Association of Small Business Investment Companies. Paul received a B.S. from Fordham University (magna cum laude, Phi Beta Kappa), an M.B.A. from New York University and a J.D. from Fordham Law School and is a member of the New York State Bar. Larry Herman, Managing Director, Raymond James Mr. Herman joined Raymond James in 2012 as part of the merger with Morgan Keegan. Prior to joining Morgan Keegan, he was in the investment banking groups of CIBC World Markets and Alex. Brown and was head of corporate development for Radiant Systems, Inc. Mr. Herman received a B.B.A. with high honors in finance from The University of Texas at Austin and an M.B.A. with honors from the Olin School of Business at Washington University. Alan Kirshenbaum, Chief Financial Officer, TPG Specialty Lending, Inc. Prior to being named Chief Financial Officer in November 2013, Mr. Kirshenbaum was a Vice President of the Company since 2011. From 2011 to 2013, Mr. Kirshenbaum was Chief Financial Officer and Executive Director of TPG Special Situations Partners (“TSSP”). From 2007 to 2011, Mr. Kirshenbaum was the Chief Financial Officer of Natsource, a private investment firm. Mr. Kirshenbaum was a Managing Director, Chief Operating Officer and Chief Financial Officer of MainStay Investments from 2006 to 2007. Mr. Kirshenbaum joined Bear Stearns Asset Management (“BSAM”) in 1999 and was BSAM’s Chief Financial Officer from 2003 to 2006. Prior to working at BSAM, Mr. Kirshenbaum worked in public accounting at KPMG from 1996 to 1999 and J.H. Cohn from 1994 to 1996. Mr. Kirshenbaum received a B.S. from Rutgers University in 1994 and an M.B.A. from New York University’s Stern School of Business in 2003. Allen Laufenberg, Managing Director, Keefe, Bruyette and Woods, a Stifel Company Mr. Laufenberg’s primary responsibilities include advising public and privately-owned business development companies (BDCs) and depositories on a wide range of alternatives. Al has represented numerous financial institutions (buy side and sell side) as well as working for special committees for approximately 20 years. Mr. Laufenberg leads the firm’s BDC investment banking initiative and is also a member of firm’s fairness opinion committee. 2014 BDC ROUNDTABLE Thursday, September 11, 2014 SPEAKER BIOGRAPHIES Takedown Lowdown: Trends in Capital Raising (cont.) Rich Petrocelli, Chief Financial Officer, Fifth Street Finance Corp./Fifth Street Senior Floating Rate Corp. Richard Petrocelli is the Chief Financial Officer of Fifth Street Finance Corp. (NASDAQ:FSC) and Fifth Street Senior Floating Rate Corp. (NASDAQ:FSFR) – both publicly-traded business development companies (BDCs). Mr. Petrocelli joined Fifth Street in March 2014 with over 20 years of experience in investment management, private equity and corporate reorganizations. In addition, he is a member of the Board of Directors of Healthcare Finance Group, LLC. Before joining Fifth Street, Mr. Petrocelli served as Chief Financial Officer, Chief Compliance Officer and Secretary at Saratoga Investment Corp., a publiclytraded BDC, where he was responsible for all accounting, finance, compliance and fund administration functions and had direct involvement in the underwriting of new loans. He was also a Managing Director of the company’s investment adviser, Saratoga Investment Advisors, LLC. Additionally, Mr. Petrocelli was a Managing Director and Chief Financial Officer at Saratoga Partners, a private equity investment firm, where he was involved with originating, structuring, managing and monitoring middle market investments. He has served as a Director of a number of Saratoga Partners’ portfolio companies. Prior to joining Saratoga Partners in 1998, Mr. Petrocelli worked at Gabelli Asset Management in the corporate finance department with a primary focus on the company’s alternative investment business. Before that, he worked at BDO Siedman as an accountant. Mr. Petrocelli received his B.S.B.A. from Georgetown University and earned an M.B.A. from New York University’s Stern School of Business. He is a Certified Public Accountant. Harry Pangas, Partner, Sutherland Asbill & Brennan LLP Harry Pangas represents issuers and investment banking firms in connection with public and private offerings of equity and debt securities, including initial public offerings (IPOs), Rule 144A offerings, shelf offerings, at-the-market offerings, registered direct offerings, high-yield bond offerings, convertible debt offerings and rights offerings. Harry also regularly advises public companies on compliance with ongoing SEC reporting obligations and other securities laws, including Section 16(b) compliance, Rule 10b5-1 plans, the Sarbanes-Oxley Act, Form S-8 and proxy disclosure, as well as the corporate governance listing requirements of the national securities exchanges. In addition, Harry has developed a niche practice representing financial services companies, including business development companies (BDCs), private investment funds, lending cooperatives, banks and insurance companies, in connection with a myriad of securities transactional and regulatory matters. 2014 BDC ROUNDTABLE Thursday, September 11, 2014 SPEAKER BIOGRAPHIES OCIE Exams: What to Expect When the SEC Comes Calling Andrew Bowden, Director of the Office of Compliance Inspections and Examinations, U.S. SEC Drew Bowden was appointed by Chair Mary Jo White as the Director of the Office of Compliance Inspections and Examinations (OCIE) in June 2013. He joined the SEC in November 2011 and initially served as the National Associate for the Investment Adviser and Investment Company Examination Program. In September 2012, Mr. Bowden was named Deputy Director of OCIE. Mr. Bowden began his career as a trial attorney and partner at a major Baltimore law firm, specializing in securities related litigation, arbitration, and regulatory matters. He later worked for seventeen years at Legg Mason in a variety of roles, including legal, compliance, operations, sales, service, marketing, and corporate governance. He has also served on the Board of Governors and Executive Committee of the Investment Adviser Association. He holds a Bachelor of Arts degree, summa cum laude, from Loyola University Maryland and a law degree, cum laude, from The University of Pennsylvania. John Walsh, Partner, Sutherland A 23-year veteran of the Securities and Exchange Commission (SEC), John Walsh joined Sutherland in October 2011. With his deep, insider’s experience and perspective of the SEC, John now represents brokerdealers, hedge funds, investment advisers and other securities firms in compliance and regulatory issues involving the agency. He counsels clients on the full spectrum of securities issues from development and compliance to cooperation in examinations and defense in enforcement proceedings. At the SEC, John played a key role in creating the Office of Compliance Inspections and Examinations (OCIE), which administers examinations of U.S. registered securities entities. He designed and implemented the SEC’s securities compliance examination practices, first as a senior advisor for compliance policy and then, most recently, as associate director-chief counsel. In 2009, he served as OCIE’s acting director and led a massive retraining of examination staff on antifraud techniques. Supplemental Materials Organization of the SEC – Division of Investment Management ©2014 Sutherland Asbill & Brennan LLP DivisionofInvestmentManagement(IM) OrganizationChart Director’s Office Director: Norm Champ Deputy Director: Dave Grim (202) 551‐6720 Senior Advisor: Jennifer McHugh Senior Advisor: Judy Lee Senior Counsel: Marian Fowler Senior Counsel: Aidan O’Connor Confidential Assistant: Ammani Nagesh (202) 551‐6720 The Division of Investment Management works to: protect investors; promote informed investment decisions; and facilitate appropriate innovation in investment products and services through regulating the asset management industry. Chief Counsel’s Office Associate Director and Chief Counsel: Douglas Scheidt (202) 551‐6701 Associate Director and Deputy Chief Counsel: Elizabeth Osterman (202) 551‐6746 Disclosure Review and Accounting Office Associate Director: Barry Miller (202) 551‐6725 Associate Director and Deputy for Disclosure Policy: Susan Nash Rulemaking Office Associate Director: Diane Blizzard Managing Executive’s Office Managing Executive: Eun Ah Choi (202) 551‐6702 (202) 551‐6720 (202) 551‐6742 Chief Counsel's Office #1 (Legal Guidance) Assistant Chief Counsel: Nadya Roytblat (202) 551‐6825 Disclosure Review Office #1 Assistant Director: Brent Fields (202) 551‐6921 Investment Adviser Regulation Office Assistant Director: Daniel Kahl (202) 551‐6999 Administrative Office Business Manager: Denise Green (202) 551‐6720 Chief Counsel's Office #2 (Legal Guidance) Assistant Chief Counsel: Sara Crovitz (202) 551‐6825 Disclosure Review Office #2 Assistant Director: Christian Sandoe (202) 551‐6921 Investment Company Regulation Office Assistant Director: Sarah ten Siethoff (202) 551‐6792 Risk and Examinations Office Assistant Director: Jon Hertzke (202) 551‐6706 Chief Counsel's Office #3 (Legal Guidance) Assistant Chief Counsel: Dalia Blass (202) 551‐6825 Disclosure Review Office #3 (Insured Investments) Assistant Director: William Kotapish (202) 551‐6921 Chief Counsel's Office (Enforcement Liaison) Assistant Director: Janet Grossnickle (202) 551‐6785 Chief Accountant’s Office Chief Accountant: Jaime Eichen (202) 551‐6918 Communications Vacant 202‐551‐6720 Technology Office Senior Technology Officer: Amy Lawson 202‐551‐6720 Updated June 16, 2014 Legal Alert: The Division of Investment Management Clarifies Certain Positions Regarding the Applicability of Rules 3-09 and 4-08(g) of Regulation S-X to BDCs October 23, 2013 Related People/Contributors The U.S. Securities and Exchange Commission (“SEC”) Division of Investment Management recently published written guidance (see link below) on rules that require that certain financial information be included pertaining to unconsolidated subsidiaries to portfolio companies of business development companies (“BDCs”). The relevant provisions are found in Rules 3-09 and 4-08(g) of Regulation S-X. Rule 3-09 generally addresses whether separate financial statements of an unconsolidated subsidiary of an SEC registrant should be included in its SEC filings, while Rule 408(g) generally covers whether summarized annual (and, indirectly, interim) balance sheet and income statement information must be included in a note to an SEC registrant’s financial statements for its unconsolidated subsidiaries. Both rules look to the three significance tests set forth in Rule 102(w) of Regulation S-X, though with different thresholds applied for Rules 3-09 and 4-08(g), respectively. • • • • Steven B. Boehm Cynthia M. Krus John J. Mahon Harry S. Pangas The Division of Investment Management has now clarified, through informal discussions, certain positions relating to the applicability of Rules 3-09 and 4-08(g) to BDCs under certain circumstances. In particular, the Division of Investment Management has clarified the following positions: • For purposes of the definition of “subsidiary” set forth in Rule 1-02(x) of Regulation S-X, “control” should be tested by reference to the definition set forth in the Investment Company Act of 1940, as amended (the “1940 Act”), which includes holding 25% or more of an entity’s voting securities. • Rules 3-09 and 4-08(g) can be applied, as applicable, to any BDC portfolio company, regardless of the nature of its business. • Rule 3-09 should only be applied to majority-owned portfolio companies that are not consolidated. • All three significance tests set forth under Rule 1-02(w), including the investment, asset and income test, should be applied using a 20% threshold when evaluating the applicability of Rule 3-09 to any majority-owned portfolio company. • All three significance tests set forth under Rule 1-02(w), including the investment, asset and income test, should be applied using a 10% threshold when evaluating the applicability of Rule 4-08(g) to any BDC portfolio company that would qualify as a “subsidiary.” • As opposed to Rule 3-09 which applies to majority-owned portfolio companies, Rule 4-08(g) can apply to any BDC portfolio company that would qualify as a “subsidiary” (i.e., where a BDC is deemed to “control” such portfolio company, as that term is defined under the 1940 Act). • It would be inappropriate to utilize investment structures that appear to be designed to ATLANTA AUSTIN GENEVA HOUSTON LONDON NEW YORK SACRAMENTO WASHINGTON, DC Legal Alert: The Division of Investment Management Clarifies Certain Positions Regarding the Applicability of Rules 3-09 and 4-08(g) of Regulation S-X to BDCs continued technically avoid the applicability of either Rule 3-09 or Rule 4-08(g). The original written guidance issued by the Division of Investment Management is provided as a reference. If you have any questions about this Legal Alert, please feel free to contact the attorneys listed under "related people/contributors" above, or the Sutherland attorney with whom you regularly work. ATLANTA AUSTIN GENEVA HOUSTON LONDON NEW YORK SACRAMENTO WASHINGTON, DC Legal Alert: The Volcker Rule: The Rising Appeal of Registered Investment Companies and BDCs January 10, 2014 Related People/Contributors On December 10, 2013, the U.S. Federal Reserve, the Office of the Comptroller of the Currency, the Federal Deposit Insurance Corporation, the Commodity Futures Trading Commission, and the Securities and Exchange Commission issued final rules implementing Section 619 of the DoddFrank Wall Street Reform and Consumer Protection Act of 2010, also known as the “Volcker Rule.” While the final rules clarify a number of important questions regarding implementation of the Volcker Rule, they also serve to distinguish investment companies registered under the Investment Company Act of 1940, as amended (the 1940 Act), as well as closed-end funds that have elected to be treated as a business development company, or BDC, under the 1940 Act, from traditional private funds that rely on exemptions from registration under the 1940 Act. The final rules also exempt small business investment companies, or SBICs, from the definition of covered fund, thus providing BDCs with the possibility of pursuing SBIC licenses either for the BDCs themselves or for their subsidiaries. In doing so, the final rules arguably create incentives for insured depository institutions and their affiliates to seek opportunities to sponsor, invest in, and potentially manage registered investment companies and BDCs. • • • • • Brian Barrett Steven B. Boehm Cynthia M. Krus John J. Mahon Harry S. Pangas The Volcker Rule, which is intended to curb potentially risky bank practices, generally prohibits insured depository institutions and their affiliates, typically referred to as “banking entities,” from: • Engaging in short-term proprietary trading, or • Investing in, or having certain relationships with, hedge funds and private equity funds, referred to as “covered funds” under the Volcker Rule. The Volcker Rule effectively seeks to prohibit banking entities, directly or indirectly, from acquiring or retaining an ownership interest in covered funds. Under the Volcker Rule, covered funds include: • An issuer that would be an investment company under the 1940 Act, but for an exclusion set forth under 3(c)(1) or 3(c)(7) of the 1940 Act, • Certain commodity pools, and • Funds organized outside of the United States that are sponsored by a U.S. banking entity or in which a U.S. banking entity is an investor. However, the final rules specifically exclude registered investment companies, as well as BDCs and SBICs, from the scope of the term “covered fund” for purposes of the Volcker Rule, since Section 619 only references funds that rely on Sections 3(c)(1) or 3(c)(7) of the 1940 Act. In addition, the final rules clarify that neither registered investment companies nor BDCs will be considered “affiliates” of a banking entity so long as that banking entity: • Does not own, control, or hold the power to vote 25% or more of the voting shares of the registered investment company or BDC; and ATLANTA AUSTIN GENEVA HOUSTON LONDON NEW YORK SACRAMENTO WASHINGTON, DC Legal Alert: The Volcker Rule: The Rising Appeal of Registered Investment Companies and BDCs continued • Provides investment advisory, commodity trading advisory, administrative, and other services to the registered investment company or BDC in compliance with the limitations under applicable regulation, order, or other authority. As a result, a banking entity generally may invest in a registered investment company or BDC, including one that potentially engages in activities subject to restriction under the Volcker Rule so long as that banking entity does not hold the power to vote more than 25% of such registered investment company or BDC’s voting shares, provided that it is otherwise permitted to do so under applicable banking law. Likewise, a banking entity may manage such a registered investment company or BDC, so long as it does so in compliance with applicable securities and banking law, including the Bank Holding Company Act of 1956, and the applicable provisions under the 1940 Act and the Investment Advisers Act of 1940, in each case as amended. While registered investment companies and BDCs remain subject to substantial regulation under the 1940 Act, including limits on the use of leverage, the above benefits may provide potential opportunities for banking entities to sponsor, invest in, and manage investment vehicles with attributes and investment objectives similar to the types of hedge funds and private equity funds that would otherwise be subject to restriction under the Volcker Rule. If you have any questions about this Legal Alert, please feel free to contact any of the attorneys listed or the Sutherland attorney with whom you regularly work. ATLANTA AUSTIN GENEVA HOUSTON LONDON NEW YORK SACRAMENTO WASHINGTON, DC Legal Alert: M&A Brokers Exempt from SEC Broker-Dealer Registration Requirements February 7, 2014 Related People/Contributors On January 31, 2014, the U.S. Securities and Exchange Commission’s (SEC) Division of Trading and Markets issued a No-Action Letter (Letter)1 that allows a private business broker (M&A Broker) to receive transaction-based compensation for assisting in effecting sales of privately-held companies without being registered as a broker-dealer under the Securities Exchange Act of 1934 (Exchange Act). It is important to note that the relief granted in the Letter applies only to federal broker-dealer registration requirements. M&A Brokers must still consider registration and licensing requirements under state laws that may apply to M&A Brokers. Background The registration status of private business brokers was the focus of a 2005 report published by the American Bar Association (ABA).2 The ABA report noted that private business brokers, sometimes called M&A Brokers, operate only as “finders,” connecting potential buyers and sellers of private companies, and that the traditional broker-dealer registration model would impose significant costs on these brokers. More recently, the U.S. Congress has introduced legislation, scheduled for consideration in 2014, that would exempt M&A Brokers from SEC registration in certain securities transactions that involve transferring ownership of a privately-held company.3 Importantly, the legislation would be limited to transactions involving companies with annual earnings of less than $25 million and annual gross revenue of less than $250 million. The SEC No-Action Letter The Letter permits M&A Brokers to facilitate certain types of securities transactions, including mergers, acquisitions, business sales and business combinations (collectively, M&A Transactions) without registering as a broker-dealer so long as specified conditions (discussed below) are met by the business being sold, the M&A Transaction, the buyer and the M&A Broker. As explained in the Letter, an M&A Broker is a person engaged in the business of effecting securities transactions solely in connection with the transfer of ownership and control of a privately-held company through the purchase, sale, exchange, issuance, repurchase, or redemption of, or a business combination involving, securities or assets of the company, to a buyer that will actively operate the company or the business conducted with the assets of the company. • • • • • • • • • • • • • • • • • • • • • • • • • Peter J. Anderson Eric A. Arnold Keith J. Barnett Steven B. Boehm Bruce M. Bettigole Patricia A. Gorham Olga Greenberg Cheryl L. Haas Gregory S. Kaufman Clifford E. Kirsch Michael B. Koffler Susan S. Krawczyk Cynthia M. Krus Yasho Lahiri Neil S. Lang John J. Mahon Harry S. Pangas S. Lawrence Polk Brian L. Rubin Amelia Toy Rudolph Holly H. Smith W. Scott Sorrels John H. Walsh Bryan M. Ward Ben Marzouk Conditions for the Business Being Sold. The business being sold must be a privately-held company. A “privately-held company” is a company that does not have any class of securities registered, or required to be registered with the SEC under Section 12 of the Exchange Act, or does not file, and is not required to file, periodic information, documents or reports under Section 15(d) of the Exchange Act. The privately-held company must be a “going concern”4 and not a “shell” company.5 Significantly, the size of the privately-held company is not a consideration. Conditions for the M&A Transaction. The relief is limited to a transaction involving the transfer of ownership and control of a privately-held company through the purchase, sale, exchange, issuance, repurchase, or redemption of, or a business combination involving, securities or assets of the company, to a buyer that will actively operate the company or the business conducted with the assets of the company. Additionally, the M&A Transaction cannot involve a public offering of securities. If the M&A Transaction involves an offering or sale of securities, the offering and sale must be conducted in compliance with an applicable exemption from registration under the Securities Act of 1933 (Securities Act). Moreover, any securities received by the buyer or the M&A ATLANTA AUSTIN GENEVA HOUSTON LONDON NEW YORK SACRAMENTO WASHINGTON, DC Legal Alert: M&A Brokers Exempt from SEC BrokerDealer Registration Requirements continued Broker in connection with the M&A Transaction must be restricted securities within the meaning of Rule 144(a)(3) under the Securities Act. Conditions for the Buyer: Upon completion of the M&A Transaction, the buyer must “control” and “actively operate” the company. The necessary “control” would exist if the buyer has the power, directly or indirectly, to direct the management or policies of the company, and will be presumed to exist if the buyer, upon completion of the M&A Transaction, has the right to vote, sell or direct the sale of at least 25% of a class of voting securities or, in the case of a partnership or limited liability company, has the right to receive upon dissolution or has contributed 25% or more of the capital. The Letter also contemplates that a buyer could “actively operate” the company, among other ways, through the power to elect executive officers and approve the annual budget, or by service as an executive or other executive manager. But the Letter clarifies that the relief would not cover a buyer that is a shell company upon the conclusion of the M&A Transaction (excluding shell companies formed to complete the M&A Transaction or change the corporate domicile). Conditions for the M&A Broker: To rely on the Letter, an M&A Broker cannot take custody, control, or possession, or otherwise handle any funds or securities issued or exchanged in connection with the M&A Transaction. The M&A Broker also cannot provide financing, either directly or indirectly, for the M&A Transaction. Nor can the M&A Broker have the authority to bind a party to the M&A Transaction. In addition, the M&A Broker cannot rely on the Letter if any officer, director or employee thereof has been barred from association with a broker-dealer by the SEC, any state, or any self-regulatory organization, or suspended from association with a broker-dealer. Significantly, the Letter explicitly permits the M&A Broker to provide the following services without being registered as a broker-dealer: • Advertise the privately-held company for sale with information such as the description of the business, general location and price range. • Assess the value of any securities being sold. • Represent both the buyer and seller, so long as the M&A Broker gives both parties clear written disclosure of the joint representation and obtains their written consent. • Participate in negotiations for the M&A Transaction. • Assist buyers in obtaining financing from unaffiliated third parties, so long as the M&A Broker complies with all applicable requirements, including Regulation T, and discloses to the buyer in writing any compensation received by the M&A Broker for such services. • Advise the buyer and seller to issue securities, or otherwise effect the transfer of the privatelyowned company by means of securities. ATLANTA AUSTIN GENEVA HOUSTON LONDON NEW YORK SACRAMENTO WASHINGTON, DC Legal Alert: M&A Brokers Exempt from SEC BrokerDealer Registration Requirements continued Most importantly, the Letter permits the M&A Broker to receive transaction-based compensation without being registered as a broker-dealer. 1 The SEC’s No-Action Letter, dated January 31, 2014, is available at http://www.sec.gov/divisions/marketreg/mrnoaction/2014/ma-brokers-013114.pdf. 2 The ABA Report and Recommendation of the Task Force on Private Placement Broker-Dealers, dated June 20, 2005, is available at http://www.sec.gov/info/smallbus/2009gbforum/abareport062005.pdf. 3 H.R. 2274, 113th Congress, 2d Session (introduced October 6, 2013), “Small Business Mergers, Acquisitions, Sales, and Brokerage Simplification Act,” available at http://docs.house.gov/billsthisweek/20140113/BILLS113hr2274-SUS.pdf. 4 The Letter explains that a “going concern” need not be profitable, and could even be emerging from bankruptcy, so long as it has actually been conducting business, including soliciting or effecting business transactions or engaging in research and development activities. 5 The Letter explains that a “shell” company is a company with no or nominal operations that has (i) no or nominal assets, (ii) assets consisting solely of cash or cash equivalents, or (iii) assets consisting of any amount of cash and cash equivalents and nominal other assets. If you have any questions about this Legal Alert, please feel free to contact any of the attorneys listed under 'Related People/Contributors' or the Sutherland attorney with whom you regularly work. ATLANTA AUSTIN GENEVA HOUSTON LONDON NEW YORK SACRAMENTO WASHINGTON, DC Legal Alert: SEC Awards Whistleblower More Than $14 Million – Largest Award to Date October 4, 2013 Related People/Contributors In a press release issued on October 1, 2013, the U.S. Securities and Exchange Commission (SEC or Commission) announced its largest whistleblower award yet of $14 million. (Click here for the press release.) The recipient of the award is an individual whistleblower who reported information that led to a successful enforcement action for a potential violation of the federal securities laws and ultimately allowed the SEC to recover “substantial” investors’ funds. Because the whistleblower wanted to remain anonymous, the SEC did not disclose any additional information surrounding the grounds for the enforcement action. Although the details of the enforcement action were not disclosed, the Commission’s Order Determining Whistleblower Award Claim (Order) provides some insight into the basis for the size of the award. (Click here for the Order.) According to the Order, the expected dollar amount of the award will exceed $14 million “in light of the monetary sanctions already collected” and after “appropriately recogniz[ing] the significance of the information that the [whistleblower] provided to the Commission, the assistance the [whistleblower] provided in the Commission action, and the law enforcement interest in deterring violations by granting awards.”1 • • • • • • • • • • • Thomas R. Bundy, III Peter N. Farley Cynthia M. Krus Allegra J. Lawrence-Hardy Holly H. Smith W. Scott Sorrels John H. Walsh Gail L. Westover James J. Briody Lee A. Peifer Yvonne M. Williams-Wass To date, the SEC has awarded eligible whistleblowers $25,000 to $14 million as part of the incentivized Whistleblower Program. The recent $14 million award is the fifth award the Commission has awarded since the Whistleblower Program went into effect in July 2010 as part of the Dodd-Frank Wall Street Reform and Consumer Protection Act. Considering factors prescribed by law, the SEC sets whistleblower awards between 10% and 30% of the total monetary sanctions collected as the result of a successful enforcement action. Specific factors considered by the SEC include the significance of the information provided to the SEC, the extent of the whistleblower’s participation in an investigation and successful proceeding, law enforcement interest in deterring violations, and whether the whistleblower was a participant or culpable in the securities laws violations. Employers should know that an individual is eligible for an award under the Whistleblower Program only if the person “voluntarily provides [the SEC] with original information about a possible violation of the federal securities laws that has occurred, is ongoing, or is about to occur [and] [that] information. . . lead[s] to a successful SEC action resulting in an order of monetary sanctions exceeding $1 million.”2 The recent whistleblower award of $14 million should serve as a message to employers given the great monetary incentive driving the Whistleblower Program and possible sanctions that can result from a SEC investigation. Thus, employers subject to federal securities laws should be proactive and look to ATLANTA AUSTIN GENEVA HOUSTON LONDON NEW YORK SACRAMENTO WASHINGTON, DC Legal Alert: SEC Awards Whistleblower More Than $14 Million – Largest Award to Date continued develop appropriate internal reporting procedures. 1Whistleblower Award Proceeding, File No. 2013-4 (SEC Sept. 30, 2013), available at http://www.sec.gov/rules/other/2013/34-70554.pdf. 2SEC Office of the Whistleblower, Frequently Asked Questions and Answers (October 2, 2013), available at http://www.sec.gov/about/offices/owb/owb-faq.shtml#P2_764. If you have any questions about this Legal Alert, please feel free to contact any of the attorneys listed under Related People/Contributors or the Sutherland attorney with whom you regularly work. ATLANTA AUSTIN GENEVA HOUSTON LONDON NEW YORK SACRAMENTO WASHINGTON, DC 2014 BDC ROUNDTABLE BDC CCO COMPENSATION SURVEY RESULTS SUTHERLAND ASBILL & BRENNAN LLP www.sutherland.com BDCCCOCompensationSurvey Q1IsyourBDCinternallyorexternally managed? Answ ered:14 Skipped:0 Internally managed 6 Externally managed 8 0 3 6 9 Sutherland Asbill & Brennan LLP 12 15 BDCCCOCompensationSurvey Q2InadditiontotheChiefCompliance OfficertitlefortheBDC,whatother functionaltitledoestheCCOhold? (chooseallthatapply) Answ ered:14 Skipped:0 Chief Compliance Officerfor... 6 Chief Compliance Officerfor... 5 Chief Financial Officer 4 Chief Operating Officer Corporate Secretary 3 General Counsel 4 Other (please specify) 3 0 3 6 9 Sutherland Asbill & Brennan LLP 12 15 BDCCCOCompensationSurvey Q3IftheCCO'stimeisallocatedamong otherpositionsorentities,approximately whatpercentageofhis/hertimeis allocatedtotheBDCCCOfunction? Answ ered:14 Skipped:0 30.71 Percentage 0 50 Average Percent Allocation of Time to CCO Role Sutherland Asbill & Brennan LLP UNITED STATES SECURITIES AND EXCHANGE COMMISSION WASHINGTON, D.C. 20549 THE CHAIR October 21, 2013 The Honorable Scott Garrett Chairman Subcommittee on Capital Markets and Government Sponsored Enterprises U.S. House of Representatives Washington, DC 20515 The Honorable Carolyn Maloney Ranking Member Subcommittee on Capital Markets and Government Sponsored Enterprises U.S. House of Representatives Washington, DC 20515 Dear Chairman Garrett and Ranking Member Maloney: I understand that the Capital Markets Subcommittee of the House Financial Services Committee will be discussing at an upcoming legislative hearing three bills that would amend provisions of the Investment Company Act of 1940 (Act) concerning business development companies (BDCs): H.R. 31 (the Next Steps for Credit Availability Act); H.R. 1800 (the Small Business Credit Availability Act); and H.R. 1973 (the Business Development Company Modernization Act). I write to briefly provide background on BDCs and to draw your attention to certain features of these bills. Please note that the views expressed in this letter are my own and do not necessarily reflect the views of the full Commission or any Commissioner. As of June 30, 2013, there were 68 active BDCs with aggregate total assets of $53.7 billion. While BDCs account for a small percentage of the assets managed by all regulated investment companies, assets managed by BDCs have grown rapidly over the past decade from net assets ofjust $5 billion at the end of 2003. Much of this growth is from newly organized BDCs sponsored by large private capital managers. Most BDCs sell a fixed number of shares in periodic offerings and most (about 85%) provide investors with liquidity by listing their shares on a stock exchange. Significantly, most securities issued by BDCs, whether traded or not, are held by retail investors. Congress created BDCs in 1980 as a specialized type of closed-end investment company (i.e., a fund that is notrequired to repurchase or redeem its securities) whose principal activities consist of investing in, and providing managerial assistance to, small, growing, or financially troubled domestic businesses. To this end, the Act generally requires a BDC to invest at least 70% of its portfolio assets in cash (or high quality, short-term debt securities), securities issued by financially troubled businesses, orcertain securities issued by domestic companies that: • do not have a security listed on a national securities exchange (i.e., are private companies), or have a security listed on a national securities exchange but have less • than $250 million of common shares outstanding; are not investment companies; and The Honorable Scott Garrett The Honorable Carolyn Maloney Page 2 • would not be investment companies but for an exclusion from the definition of "investment company" in section 3(c) ofthe Act. The remaining 30% of a BDCs portfolio assets are not limited by these investment restrictions and can be invested freely. Under the Act, BDCs enjoy greater operating flexibility than mutual funds or other closed-end funds. A BDC, for example, may issue long term options and warrants, may issue multiple classes of debt securities, and may issue approximately 50% more debt securities as a percentageof capital than other investmentcompanies. As discussed below, H.R. 31 and H.R. 1800 would ease that regulatory structure by permitting a BDC to double its permitted borrowingsand issue an unlimited amount of preferred stock, thereby increasing the risk of loss from such leverage for BDC shareholders and holders of senior securities issued by BDCs. H.R. 31 and H.R. 1800 Both H.R. 31 and H.R. 1800 would amend section 61(a) of the Act to: (a) reduce the asset coverage for senior securities representing indebtedness from 200% to 150%; and (b) make inapplicable the 200% asset coverage requirement for senior securities that are stock, le.t preferred stock, and other provisions ofthe Act intended to protect holders ofpreferred stock.1 In my view, this increase in theability of BDCs to use leverage, and theelimination of provisions of the Actintended to protect holders of preferred stock issued by a BDC, gives rise to investor protection concerns, particularly because most BDC shareholders are retail investors. The Act's asset coverage requirements existfor the protection of both a BDCs shareholders on one hand and investors in its senior securities on the other.2 Leverage amplifies both negative and positive portfolio performance. As the percentage of a BDCs capital from senior securities increases, the greater is theamplification. Increased leverage increases earnings volatility. Atthe same time, the risk increases that the BDC will lack the resources to pay 1 Asset coverage is the ratio oftotal assets less liabilities other than senior securities to senior securities. The asset coverage requirement for senior securities issued by aBDC is 200%. For other closed-end funds, the asset coverage requirement is 300% for debt securities and 200% for preferred stock. An asset coverage of300% is approximately equivalent to adebt to equity ratio of1:2; an asset coverage of200% is approximately equivalent to adebt to equity ratio of 1:1. 2 When Congress enacted the Act, the highly capitalized and simplified capital structure that the Act imposes on investment companies was regarded as being ofcentral importance to the protection ofinvestors. Prior to 1940, the use ofexcessive leverage and complex capital structures by certain closed-end funds led to personal gain for insiders at the expense ofpublic security holders. In some instances, debt and preferred stock sold to the public accounted for adisproportionate amount ofafund's capital, but common stock concentrated in the hands ofinsiders controlled the fund. Although a fund's assets might be insufficient to liquidate the senior securities, insiders could induce the fund to pay distributions with respect to the common stock or repurchase common stock. See Investment Trusts and Investment Companies pt. 3, H.R. Doc. No. 279, 76th Cong., 1st Sess. 1001, 1582-97 (1939). In this regard, section 1(b) ofthe Act identifies "excessive borrowing and the issuance ofexcessive amounts ofsenior securities [i.e., preferred stock or debt securities]" as one ofthe principal abuses the Act was designed to address. The Honorable Scott Garrett The Honorable Carolyn Maloney Page 3 promised interest or dividends, or the principal or liquidation preference, to the holders of its senior securities. The risk that a BDC will be unable to make timely payments to senior security holders is, in my view, of particular concern in view ofthe illiquid types of investments that BDCs make. The asset coverage provisions act as a circuit breaker. If a BDCs asset coverage of its senior securities is less than 200% (after giving effect to the distribution, issuance or repurchase), the BDC may not make cash distributions to shareholders, issue additional senior securities, or repurchase common stock and must retain for the BDCs use cashthat the BDC otherwise would pay to its shareholders as distributions.3 Both H.R. 31 and H.R. 1800 would permit a BDC to significantly increase its leverage in two specific ways. First, the amendments to the Act proposed inthose bills would reduce the asset coverage requirement for debt securities to 150% from 200%, thereby increasing the debt to equity ratio from approximately 1:1 to 2:1. By way of example, under current law, a BDC with $100 in equity could borrow $100 (equal to $200 total assets). If that BDCs assets lost 50% oftheir value, its shareholders wouldexperience a total loss on their equity investment. Reducing the required asset coverage to 150% would permit the same BDC toborrow $200, effectively doubling its leverage. A BDCs assets would only have to lose 33 1/3% oftheir value before exposing shareholders to a total loss oftheir investment. Second, the proposed amendments would allow aBDC to issue an unlimited amount of preferred stock, effectively eliminating the Act's limitations on leverage. Because the proposed amendments would treat the issuance of preferred stock as the equivalent of the issuance of common stock for purposes ofcalculating asset coverage, aBDC could increase its leverage by issuing preferred stock and thereby actually increase its capacity for issuing additional debt securities. Both H.R. 31 and H.R. 1800 also would eliminate all ofthe provisions in the Act specifically intended to protect the holders ofpreferred stock issued by aBDC. A potential 3 Debt securities issued by aBDC also provide that if: (a) asset coverage declines to less than 100% for one year then the holders ofthose securities have the right toelect a majority ofthe BDCsdirectors; or(b) asset coverage declines to less than 100% for 24 consecutive months then a default shall be deemed tohave occurred. Failing to meet the asset coverage requirements, however, is not aviolation ofthe Act, and the BDC is not forced to sell assets. 4The Act provides that holders ofpreferred stock, voting separately as aclass, are entitled to: (a) elect at least two directors at all times; (b) elect amajority ofthe directors ifat any time dividends on the preferred stock have been in arrears for two full years; (c) approve or disapprove any plan ofreorganization adversely affecting their interests; and (d) approve or disapprove certain other major corporate events, such as converting to amutual fund format. These voting rights help balance the sometimes conflicting interests ofthe holders ofthe common stock and the holders ofthe preferred stock issued by the same fund. Under the Act, aBDC may not issue different classes of preferred stock, i.e., classes with different priorities as to the payment ofdividends or liquidation preference. In liquidation, ifthe value ofaBDCs assets is insufficient to satisfy the claims ofall security holders, holders ofa class with ahigher priority have aclear advantage. Absent liquidation, that priority can influence the market value ofasecurity, particularly during times when aparticular BDCs prospects dim. Retail investors might find ajunior class ofpreferred stock with ahigh dividend rate attractive but fail to appreciate the risks in the event that the BDC The Honorable Scott Garrett The Honorable Carolyn Maloney Page 4 consequence is the sale to retail investors of preferred stock with a confusing mix of characteristics and rights. Under the Act, for example, preferred stockhas "complete priority" over the common stock as to payment of dividends, and dividends are cumulative. This provision prohibitsthe sale of participating preferred stock or preferred stock that is preferred only as to assets in liquidation but not as to dividends. But for these provisions, holders of preferred stock could find that dividends not paid during lower earnings periods are never paid, even ifthe BDC subsequently prospers. The two bills also would: (a) amend section 60 of the Act to permit a BDC to purchase securities issued by registered investment advisers; and (b) direct the Commission to revise certain rules under the Securities Act of 1933 to put BDCs on parity with other issuers that are required to file certain reports under the SecuritiesExchangeAct of 1934. In my view, these provisions do not raise significant investor protection concerns. H.R. 1973 By amending the Act's definition of "eligible portfolio company" to include currently excluded financial institutions, H.R. 1973 would change the definition and stated purpose of BDCs. The Act defines "business development company" as a closed-end fund that is "operated for the purpose of making investments in securities" issued by small or financially distressed companies, generally companies that meet the Act'sdefinition of "eligible portfolio company." This definition requires that, with one exception,5 an eligible portfolio company be neither an investment company, as defined inAct, nor a company that is excluded from the definition of investment company solely by section 3(c) ofthe Act, i.e., financial institutions such as hedge funds, private equity funds, brokers and consumer finance companies. The Act, however, does not prohibit a BDC from investing infinancial institutions orother companies that are not eligible portfolio companies; under the Act, a BDC can invest up to 30% ofits portfolio in securities issued by these companies. The explicit exclusion ofinvestment companies and other financial institutions from the definition of"eligible portfolio company" was intended to encourage a BDC to focus its investment activities onoperating companies that directly produce goods orprovide services rather than on other financial institutions that serve primarily as conduits of capital. Congress created BDCs inresponse to"the slowing ofthe flow ofcapital to American enterprise, particularly to smaller, growing businesses."6 To the extent that aBDC concentrates its experiences financial reversals. ABDC in financial distress, for example, might eliminate dividend payments to holders ofajunior class ofpreferred stock but continue dividend payments to holders ofa senior class. 5 The one exception allows an eligible portfolio company to be asmall business investment company (SBIC) licensed by the Small Business Administration that is a wholly owned subsidiary ofa BDC. ASBIC makes investments that are consistent with the purpose of BDCs. 6 H.R. Rep. No. 1341,96th Cong., 2d Sess. 20 (1980). The House Report states that "[t]he importance ofthese businesses tothe American economic system interms ofinnovation, productivity, increased competition and the jobsthey create is,of course, critical." Id The Honorable Scott Garrett The Honorable Carolyn Maloney Page 5 investments in other financial institutions, it would divert capital from small, growing businesses that BDCs were originally created to help. While Congress obviously can choose to change the purpose of BDCs in this manner, of particular concern is the prospect of a BDC concentrating its investments in hedge and other private funds because of the riskier strategies associated with some of these funds. This raises potential investor protection concerns, as it would allow non-accredited investors to invest in a BDC comprised entirely of private funds. As such, BDCs could be used to circumvent the general prohibition on selling interests in private funds to retail investors. 1hope that this information is helpful to you and to the other members of the Subcommittee. Please do not hesitate to contact me at (202) 551-2010, or have your staff contact Tim Henseler, Director of the Office of Legislative and Intergovernmental Affairs, at (202) 5512015, if I can be of any further assistance. Sincerely, 'X-^toUr Mary Jo White Chair cc: Chairman Jeb Hensarling Ranking Member Maxine Waters IM Guidance Update September 2013 | No. 2013-07 business Development Companies—SEPARATE Financial Statements or Summarized Financial Information of Certain Subsidiaries Applicability of Regulation S-X Rules 3-09 and 4-08(g) to Business Development Companies (BDCs). In reviewing registration statements filed by BDCs, the staff has observed that some BDCs that have certain significant subsidiaries do not provide separate financial statements or summarized financial information for those subsidiaries as required by Regulation S-X. This written guidance reflects the comments that the staff has provided to these BDCs. The bases of the staff’s comments are Regulation S-X Rules 3-09 and 4-08(g), which apply to BDCs. Rule 3-09 describes, among other things, the circumstances under which separate financial statements of an unconsolidated majority-owned subsidiary are required to be filed. Rule 4-08(g) describes, among other things, the circumstances under which summarized financial information must be presented in the notes to the financial statements for subsidiaries not consolidated. BDCs register their securities under the Securities Act of 1933 on Form N-2. For purposes of Form N-2, “[a] business development company should comply with the provisions of Regulation S-X generally applicable to registered management investment com­panies. (See . . . Sections 210.6-01 through 210.6-10 of Regulation S-X . . .).” 1 Under Regulation S-X, in turn, “[t]he financial statements filed for persons to which [rules 6-01 to 6-10] are applicable shall be prepared in accordance with the . . . special rules [6-01 to 6-10] in addition to the general rules [1-01 to 4-10] (Articles 1, 2, 3, and 4). Where the requirements of a special rule differ from those prescribed in a general rule, the requirements of the special rule shall be met.” 2 Rules 3-09 and 4-08(g) apply to BDCs because they are general rules and there are no special rules in Rules 6-01 through 6-10 that differ from the requirements in Rules 3-09 and 4-08(g) related to whether, and for what periods, financial statements and financial information are required to be presented. Rule 4-08(g) generally requires registrants to present in the notes to their financial statements summarized financial information for all unconsolidated subsidiaries when any unconsolidated subsidiary, or combination of unconsolidated subsidiaries, meets the definition of a “significant subsidiary” in Regulation S-X Rule 1-02(w). If a BDC is required to present summarized financial information, the Division generally would not US Securities and Exchange Commission Division of Investment Management IM g u i d a n c e u p d a t e 2 object if the BDC presents summarized financial information in the notes to the financial statements only for each unconsolidated subsidiary which individually meets the definition of a “significant subsidiary” in Rule 1-02(w) but does not present summarized financial information in the notes to the financial statements for all unconsolidated subsidiaries. If a BDC believes the application of Rule 3-09 or Rule 4-08(g) results in the presentation of either financial statements or summarized financial information of an unconsolidated subsidiary that is not necessary to reasonably inform investors, the BDC should contact the Division’s Chief Accountant’s Office at 202-551-6918 or imoca@sec.gov. BDCs are also encouraged to contact the Division’s Chief Accountant’s Office with any other questions or concerns about the application of these requirements to their particular situations. Endnotes 1 Instruction 1.a to Item 8.6.c of Form N-2. 2 Regulation S-X Rule 6-03. This IM Guidance Update summarizes the views of the Division of Investment Management regarding various requirements of the federal securities laws. Future changes in laws or regulations may supersede some of the discussion or issues raised herein. This IM Guidance Update is not a rule, regulation or statement of the Commission, and the Commission has neither approved nor disapproved of this IM Guidance Update. The Investment Management Division works to: s protect investors s promote informed investment decisions and s facilitate appropriate innovation in investment products and services through regulating the asset management industry. If you have any questions about this IM Guidance Update, please contact: Chief Accountant’s Office Phone:202.551.6918 Email:IMOCA@sec.gov IM Guidance Update JUNE 2014 | No. 2014-09 BUSINESS DEVELOPMENT COMPANIES WITH WHOLLY-OWNED SBIC SUBSIDIARIES—ASSET COVERAGE REQUIREMENTS The Commission has, from time to time, issued exemptive orders to business development companies (“BDCs”)1 granting limited relief from the asset coverage requirements of sections 18(a) and 61(a) of the 1940 Act.2 Subject to representations and a condition described in the exemptive applications, this relief permits a BDC to treat certain indebtedness issued by its wholly owned subsidiary operating as a small business investment company (“SBIC Subsidiary”) as indebtedness not represented by senior securities for purposes of determining the BDC’s consolidated asset coverage.3 Recently, the staff has become aware that certain BDCs have sought to rely on this limited relief in connection with SBICs that have not issued indebtedness that is held or guaranteed by the Small Business Administration (“SBA”). As discussed further below, the staff does not believe that reliance on the relief for this purpose is consistent with the representations historically included in the exemptive applications. In addition, to make explicit this existing requirement under the orders, the staff requests that all new applications include a modified condition, as described below. Background Section 18(a)(1) of the 1940 Act prohibits a registered closed-end company from issuing any class of senior security representing indebtedness unless the company complies with the asset coverage requirements set forth in that section.4 Section 61(a) of the 1940 Act makes section 18(a) applicable to BDCs, with certain modifications. A BDC may be deemed an indirect issuer of any class of senior security issued by its direct or indirect wholly owned SBIC Subsidiary. As a result, absent exemptive relief, the BDC would also be required to comply with the asset coverage requirements on a consolidated basis, meaning that it would treat as its own the assets and liabilities of its SBIC Subsidiary for purposes of calculating the BDC’s asset coverage.5 US Securities and Exchange Commission Division of Investment Management I M G U I D A N C E U P D AT E 2 The Commission has issued a number of exemptive orders to BDCs granting limited relief from the asset coverage requirements. This relief allows the BDCs to treat certain indebtedness issued by their wholly owned SBIC Subsidiaries as indebtedness not represented by senior securities for purposes of determining the BDC’s consolidated asset coverage. For purposes of the asset coverage calculation, this indebtedness is deducted from the BDC’s total assets and is also excluded from the amount of senior securities representing indebtedness. In support of the request for relief, applicants represent that companies operating under the SBIA, such as the SBIC Subsidiaries, are subject to the SBA’s separate regulation of permissible leverage in their capital structure. Applicants also point to section 18(k) of the 1940 Act, which exempts investment companies operating as SBICs from the asset coverage requirements contained in sections 18(a)(1)(A) and (B) for senior securities representing indebtedness. Applicants contend that because an SBIC Subsidiary would be entitled to rely on section 18(k) if it were a BDC, there is no policy reason to deny the benefit of that exemption to the BDC parent. Existing Orders Existing orders are subject to several representations and a condition described in the exemptive applications. Although in most cases the representations and condition have not explicitly required that the SBIC Subsidiary have issued indebtedness held or guaranteed by the SBA, we believe this requirement is implicit in the rationale for the relief. Specifically, the relief is premised on the SBA’s separate oversight of the SBIC Subsidiary’s indebtedness rendering application of the 1940 Act’s asset coverage requirements unnecessary. However, if the SBIC Subsidiary has not issued indebtedness such that the SBIC Subsidiary is fully subject to that oversight, the application of the 1940 Act’s requirements is not duplicative. Accordingly, where an SBIC Subsidiary has not issued indebtedness that is held or guaranteed by the SBA, the staff does not believe that reliance on the order would be consistent with the representations made in the existing exemptive applications. Potential Applicants for Orders To make explicit this existing requirement under the orders, the staff requests that all new applications include a modified condition. Specifically, the condition should provide that any senior securities representing indebtedness of an SBIC Subsidiary will not be considered senior securities and, for purposes of the definition of “asset coverage” in section 18(h), will be treated as indebtedness not represented by senior securities but only if that SBIC Subsidiary has issued indebtedness that is held or guaranteed by the SBA.6 I M G U I D A N C E U P D AT E 3 Endnotes 1 Section 2(a)(48) of the 1940 Act defines a BDC to be any closed-end investment company that, among other things, is operated for the purpose of making investments in securities described in sections 55(a)(1) through 55(a)(3) of the 1940 Act and makes available significant managerial assistance with respect to the issuers of such securities. 2 For examples of this type of relief, see In the Matter of Medley Capital Corporation, et al., Investment Company Act Release Nos. (30234) (Oct. 16, 2012) (notice) and (30262) (Nov. 14, 2012) (order) and In the Matter of Saratoga Investment Corporation, et al., Investment Company Act Release Nos. (30145) (July 23, 2012) (notice) and (30171) (Aug. 20, 2012) (order). 3 A “small business investment company” or “SBIC” is a company that is licensed by the Small Business Administration (“SBA”) to operate as such under the Small Business Investment Act of 1958 (“SBIA”). 4 Section 18(g) of the 1940 Act provides, in relevant part, that “‘Senior security’ means any bond, debenture, note, or similar obligation or instrument constituting a security and evidencing indebtedness, and any stock of a class having priority over any other class as to distribution of assets or payment of dividends; and ‘senior security representing indebtedness’ means any senior security other than stock.” 5 Section 18(h) of the 1940 Act provides, in relevant part, that, “‘Asset coverage’ of a class of senior security representing an indebtedness of an issuer means the ratio which the value of the total assets of such issuer, less all liabilities and indebtedness not represented by senior securities, bears to the aggregate amount of senior securities representing indebtedness of such issuer.” 6 See In the Matter of OFS Capital Corporation, et al., Investment Company Act Release Nos. (30771) (Oct. 30, 2013) (notice) and (30812) (Nov. 26, 2013) (order). I M G U I D A N C E U P D AT E This IM Guidance Update summarizes the views of the Division of Investment Management regarding various requirements of the federal securities laws. Future changes in laws or regulations may supersede some of the discussion or issues raised herein. This IM Guidance Update is not a rule, regulation or statement of the Commission, and the Commission has neither approved nor disapproved of this IM Guidance Update. The Investment Management Division works to: s protect investors s promote informed investment decisions and s facilitate appropriate innovation in investment products and services through regulating the asset management industry. If you have any questions about this IM Guidance Update, please contact: Chief Counsel’s Office Phone: 202.551.6825 Email: IMOCC@sec.gov 4 IM Guidance Update March 2014 | No. 2014-04 GUIDANCE ON THE TESTIMONIAL RULE AND SOCIAL MEDIA From time to time, we have been asked questions concerning the nature, scope and application of the rule that prohibits investment advisers from using testimonials in their advertisements. In addition, in the past several years, we have been asked a number of questions concerning investment advisers’ use of social media. We are now providing this guidance concerning registered investment advisers’ use of social media and their publication1 of advertisements that feature public commentary about them that appears on independent, third-party social media sites.2 We understand that use of social media has increased the demand by consumers for independent, third-party commentary or review of any manner of service providers, including investment advisers. We recognize that social media has facilitated consumers’ ability to research and conduct their own due diligence on current or prospective service providers. Through this guidance, we seek to clarify application of the testimonial rule as it relates to the dissemination of genuine third-party commentary that could be useful to consumers. Specifically, we seek through this guidance to assist firms in applying section 206(4) of the Investment Advisers Act of 1940 (“Advisers Act”) and rule 206(4)-1(a)(1) thereunder (“testimonial rule”) to their use of social media.3 The guidance, in the form of questions and answers, also seeks to assist investment advisers in developing compliance policies and procedures reasonably designed to address participation in this evolving technology, specifically with respect to the publication of any public commentary that is a testimonial. Consistent with previous staff guidance, we believe that in certain circumstances, as described below, an investment adviser’s or investment advisory representative’s (“IAR’s”) publication of all of the testimonials about the investment adviser or IAR from an independent social media site on the investment adviser’s or IAR’s own social media site or website would not implicate the concern underlying the testimonial rule.4 US Securities and Exchange Commission Division of Investment Management I M G U I D A N C E U P D AT E 2 BACKGROUND Section 206(4) generally prohibits any investment adviser from engaging in any act, practice or course of business that the Commission, by rule, defines as fraudulent, deceptive or manipulative. In particular, rule 206(4)-1(a)(1) states that: [i]t shall constitute a fraudulent, deceptive, or manipulative act, practice, or course of business . . . for any investment adviser registered or required to be registered under [the Advisers Act], directly or indirectly, to publish, circulate, or distribute any advertisement which refers, directly or indirectly, to any testimonial of any kind concerning the investment adviser or concerning any advice, analysis, report or other service rendered by such investment adviser. Rule 206(4)-1(a)(1) was designed to address the nature of testimonials when used in investment advisory advertisements. When it adopted the rule, the Commission stated that, in the context of investment advisers, it found “. . . such advertisements are misleading; by their very nature they emphasize the comments and activities favorable to the investment adviser and ignore those which are unfavorable.” 5 The staff has stated that the rule forbids the use of a testimonial by an investment adviser in advertisements “because the testimonial may give rise to a fraudulent or deceptive implication, or mistaken inference, that the experience of the person giving the testimonial is typical of the experience of the adviser’s clients.”6 Whether public commentary on a social media site is a testimonial depends upon all of the facts and circumstances relating to the statement. The term “testimonial” is not defined in the rule, but the staff has consistently interpreted that term to include a “statement of a client’s experience with, or endorsement of, an investment adviser.” 7 Depending on the facts and circumstances, public commentary made directly by a client about his or her own experience with, or endorsement of, an investment adviser or a statement made by a third party about a client’s experience with, or endorsement of, an investment adviser may be a testimonial.8 The staff also has stated that an investment adviser’s publication of an article by an unbiased third party regarding the adviser’s investment performance is not a testimonial, unless it includes a statement of a client’s experience with or endorsement of the adviser. 9 The staff also has stated that an adviser’s advertisement that includes a partial client list that does no more than identify certain clients of the adviser cannot be viewed either as a statement of a client’s experience with, or endorsement of, the adviser and therefore is not a testimonial.10 Such an advertisement could nonetheless violate section 206(4) and rule 206(4)-1(a)(5) if the advertisement is false or misleading.11 I M G U I D A N C E U P D AT E 3 The staff no longer takes the position, as it did a number of years ago, that an advertisement that contains non-investment related commentary regarding an IAR, such as regarding an IAR’s religious affiliation or community service, may be deemed a testimonial violative of rule 206(4)-1(a)(1).12 The following questions and answers are intended to provide more guidance. Third-party commentary Q1. May an investment adviser or IAR publish public commentary that is an explicit or implicit statement of a client’s experience with or endorsement of the investment adviser or IAR on the investment adviser’s or IAR’s social media site? A1. Generally, staff believes that such public commentary would be a testimonial within the meaning of rule 206(4)-1(a)(1) and its use in an advertisement by an investment adviser or IAR would therefore be prohibited. • For example, if an investment adviser or IAR invited clients to post such public commentary directly on the investment adviser’s own internet site, blog or social media site that served as an advertisement for the investment adviser or IAR’s advisory services, such testimonials would not be permissible. Q2.May an investment adviser or IAR publish the same public commentary on its own internet or social media site if it comes from an independent social media site? A2.When an investment adviser or IAR has no ability to affect which public commentary is included or how the public commentary is presented on an independent social media site; where the commentators’ ability to include the public commentary is not restricted;13 and where the independent social media site allows for the viewing of all public commentary and updating of new commentary on a real-time basis, the concerns underlying the testimonial prohibition may not be implicated. As described in more depth below, publication of public commentary from an independent social media site would not raise any of the dangers that rule 206(4)-1(a) (1) was designed to prevent if: • the independent social media site provides content that is independent of the investment adviser or IAR; • there is no material connection between the independent social media site and the investment adviser or IAR that would call into question the independence of the independent social media site or commentary; and I M G U I D A N C E U P D AT E • 4 the investment adviser or IAR publishes all of the unedited comments appearing on the independent social media site regarding the investment adviser or IAR.14 Under these circumstances, an investment adviser or IAR may include such public commentary in an advertisement without implicating the concerns underlying the testimonial rule. If, however, the investment adviser or IAR drafts or submits commentary that is included on the independent social media site, the testimonial rule generally would be implicated. Also, if the investment adviser or IAR is allowed to suppress the publication of all or a portion of the commentary, edit the commentary or is able to organize or prioritize the order in which the commentary is presented, the testimonial rule generally would be implicated. Q3.What content is not independent of an investment adviser or IAR and what is a material connection that would call into question the independence of a site or commentary? A3.Commentary would not be independent of an investment adviser or IAR if the investment adviser or IAR directly or indirectly authored the commentary on the independent social media site, whether in their own name, a third party’s name, or an alias, assumed or screen name. An investment adviser or IAR would have a material connection with a site or commentary that would call into question the independence of the site or commentary if, for example, the investment adviser or IAR: (1) compensated a social media user for authoring the commentary, including with any product or service of value; or (2) prioritized, removed or edited the commentary.15 • For example, an investment adviser could not have a supervised person submit testimonials about the investment adviser on an independent social media site and use such testimonials in advertisements without implicating the testimonial rule. • An investment adviser or IAR could not compensate a client or prospective client (including with discounts or offers of free services) to post commentary on an independent social media site and use such testimonials in advertisements without implicating the testimonial rule. Q4.May an investment adviser or IAR publish testimonials from an independent social media site in a way that allows social media users to sort the criteria? I M G U I D A N C E U P D AT E 5 A4.An investment adviser or IAR’s publication of testimonials from an independent social media site that directly or indirectly emphasizes commentary favorable to the investment adviser or IAR or de-emphasizes commentary unfavorable to the investment adviser or IAR would implicate the prohibition on testimonials. The investment adviser may publish only the totality of the testimonials from an independent social media site and may not highlight or give prominence to a subset of the testimonials. • Investment adviser or IAR sites may publish the testimonials from an independent social media site in a content-neutral manner, such as by chronological or alphabetical order, which presents positive and negative commentary with equal prominence. • Social media users, however, are free to personally display the commentary and sort by any criteria, including by the lowest or highest rating. Investment adviser and IAR sites may facilitate a user’s viewing of the commentary by providing a sorting mechanism as long as the investment adviser or IAR site does not itself sort the commentary. Q5.May an investment adviser or IAR publish testimonials from an independent social media site that includes a mathematical average of the public commentary? A5.Publication by an investment adviser or IAR of such testimonials from an independent social media site would not raise any of the dangers that rule 206(4)-1(a) (1) was designed to prevent if the independent social media site were designed to make it equally easy for the public to provide negative or positive commentary about an investment adviser or IAR. • Investment advisers or IARs could publish testimonials from an independent social media site that include a mathematical average of the commentary provided that commenters themselves rate the investment advisers or IARs based on a ratings system that is not designed to elicit any pre-determined results that could benefit any investment adviser or IAR. • The independent social media site, the investment adviser and the IAR may not provide a subjective analysis of the commentary.16 Inclusion of on Investment Adviser Advertisements on Independent Social Media Site Q6.May an investment adviser or IAR publish public commentary from an independent site if that site also features the investment adviser or IAR’s advertising? I M G U I D A N C E U P D AT E 6 A6.The existence of an investment adviser or IAR’s advertisement within the architecture of an independent site that also contains independent public commentary does not, in combination, create a prohibited testimonial or otherwise make the advertisement false or misleading, provided that the investment adviser complies with the material connection and independence factors described above and provided that the advertisement is easily recognizable to the public as a sponsored statement. • In other words, an advertisement would not cause the investment adviser or IAR’s publication of the independent social media site’s commentary to violate rule 206(4)-1 where (1) it would be readily apparent to a reader that the investment adviser or IAR’s advertisement is separate from the public commentary featured on the independent social media site and (2) the receipt or non-receipt of advertising revenue did not in any way influence which public commentary is included or excluded from the independent social media site. Reference to Independent Social Media Site Commentary Investment Adviser Non-Social Media Advertisements Q7. May an investment adviser or IAR refer to public commentary from an independent social media site on non-social media advertisements (e.g., newspaper, radio, television)? A7. An investment adviser or IAR could reference the fact that public commentary regarding the investment adviser or IAR may be found on an independent social media site, and may include the logo of the independent social media site on its non-social media advertisements, without implicating the testimonial rule. • For example, an IAR could state in its newspaper ad “see us on [independent social media site],” to signal to clients and prospective clients that they can research public commentary about the investment adviser or IAR on an independent social media site. • In contrast, an investment adviser or IAR may not publish any testimonials from the independent social media site on the newspaper ad without implicating the testimonial rule.17 Client lists Q8.Would a list or photographs of “friends” “or “contacts” on an investment adviser or IAR’s social media site that is viewable by the general public be considered a testimonial or otherwise violate section 206(4) or rule 206(4)-1? I M G U I D A N C E U P D AT E 7 A8.It is common on social media sites to include a communal listing of contacts or friends. The staff has stated that an advertisement that contains a partial client list that does no more than identify certain clients of the adviser cannot be viewed either as a statement of a client’s experience with, or endorsement of, the investment adviser, and therefore is not a testimonial.18 Such an advertisement, however, could be false or misleading under rule 206(4)-1(a)(5) depending on the facts and circumstances. • If the contacts or friends are not grouped or listed so as to be identified as current or past clients of an IAR, but are simply listed by the social media site as accepted contacts or friends of the IAR in the ordinary course, such a listing of contacts or friends generally would not be considered to be in violation of rule 206(4)-1(a)(1). • However, if an IAR attempts to create the inference that the contacts or friends have experienced favorable results from the IAR’s investment advisory services, the advertisement could be considered to be in violation of section 206(4) and rule 206(4)-1. Fan/Community Pages Q9.Individuals unconnected with a particular investment adviser or IAR may establish “community” or “fan” or other third-party sites where the public may comment on a myriad of investment topics, along with commentary regarding an investment adviser firm or individual IARs. Do such sites raise concerns under rule 206(4)-1? A9. In the ordinary course, a third party’s creation and operation of unconnected community or fan pages generally would not implicate rule 206(4)-1. We strongly caution investment advisers and supervised persons when publishing content from or driving user traffic to such sites (including through hyperlinks to such sites), particularly if the site does not meet the material connection and independence conditions described above. The Commission has stated that: any SEC-registered investment adviser (or investment adviser that is required to be SEC registered) that includes, in its web site or in other electronic communications, a hyperlink to postings on third-party web sites, should carefully consider the applicability of the advertising provisions of the [Advisers Act]. Under the Advisers Act, it is a fraudulent act for an investment adviser to, among other things, refer to testimonials in its advertisements.19 I M G U I D A N C E U P D AT E 8 Endnotes 1 For purposes of this guidance, “publication” refers to any form of real-time broadcast through social media or the Internet whether by hyperlinking, posting, livestreaming, tweeting, or forwarding or any similar public dissemination and, does not relate to advertisements on non-Internet or non-social media sites, such as paper, television or radio. Social media allows for instantaneous updating of posted commentary and concurrent viewing of all of the comment history; in contrast, paper, television and radio are static media that reflect public commentary at a particular point in time and are limited media that would typically not reproduce all of the available public commentary simultaneously (often due to cost, space and other considerations). 2 As used herein, “independent social media sites” refers specifically to third-party social media sites that predominantly host user opinions, beliefs, findings or experiences about service providers, including investment advisory representatives or investment advisers (e.g., Angie’s List). An investment adviser’s or IAR’s own social media profile or account that is used for business purposes is not an “independent social media site.” 3This IM Guidance Update only addresses the use by a firm or IARs of social media sites for business purposes. This Update does not address the use by individuals of social media sites for purely personal reasons. This Update does not seek to address any obligations under state law of social media for business use. In addition, this guidance does not seek to address the use of social media sites by broker-dealers. 4 Any such advertisements also must comply with rule 206(4)-1(a)(5). 5 Investment Advisers Act Rel. No. 121 (Nov. 2, 1961) (adopting rule 206(4)-1). 6 See Richard Silverman, Staff No-Action Letter (pub. avail. March 27, 1985). 7 See Cambiar Investors, Inc., Staff No-Action Letter (pub. avail. Aug. 28, 1997) (“Cambiar”). 8 See DALBAR, Inc., Staff No-Action letter (pub. avail. March 24, 1998) (“DALBAR”). 9 See New York Investors Group, Inc., Staff No-Action Letter (pub. avail. Sept. 7, 1982); Stalker Advisory Services, Staff No-Action Letter (pub. avail. Feb. 14, 1994). See also Kurtz Capital Management, Staff No-Action Letter (pub. avail. Jan. 22, 1988). 10 See Cambiar, supra note 7. 11 Id. (“For example, the inclusion of a partial client list in an adviser’s advertisement has the potential to mislead investors if the clients on the list are selected on the basis of performance and this selection bias is not adequately disclosed. A list that includes only advisory clients who have experienced above-average performance could lead an investor who contacts the clients for references to infer something about the adviser’s competence or about the possibility of enjoying a similar investment experience that the investor might not have inferred if criteria unrelated to the client’s performance had been used to select the clients on the list or if the selection bias was fully and fairly disclosed.”). I M G U I D A N C E U P D AT E 9 12 See Dan Gallagher, Staff No-Action Letter (pub. avail. July 10, 1995). Advisers that publish advertisements regarding non-investment related commentary remain subject to the fiduciary responsibilities imposed by section 206(1) and (2) of the Advisers Act. Thus an adviser cannot use social media to perpetrate affinity frauds, which are investment scams that prey upon members of identifiable groups, such as religious or ethnic communities, the elderly, or professional groups. Affinity frauds can target any group of people who take pride in their shared characteristics, whether they are religious, ethnic, or professional. See http://www.sec.gov/investor/ pubs/affinity.htm. 13 Some independent social media sites may have member fees or subscriptions payable by users. An investment adviser or IAR’s publication of public commentary from a site that charges member or subscription fees to public users would not call into question the independence of the independent social media site for purposes of our views herein. 14 Independent social media sites may have editorial policies that edit or remove public commentary violative of the site’s own published content guidelines (e.g., prohibiting defamatory statements; threatening language; materials that infringe on intellectual property rights; materials that contain viruses, spam or other harmful components; racially offensive statements or profanity). An investment adviser or IAR’s publication of public commentary that has been edited according to such an editorial policy would not call into question the independence of the independent social media site for purposes of the staff’s views herein. 15 As explained in Q6 below, any arrangement whereby the investment adviser or IAR compensated the independent social media site, including with advertising or other revenue, in order to publish or suppress the publication of anything less than the totality of the public commentary submitted could render any use by the IAR or investment adviser on its social media site violative of the prohibition on testimonials. 16 See DALBAR, supra note 8. 17 See supra note 1. 18 See Cambiar, supra note 7. 19 See Commission Guidance on the Use of Company Websites at note 83, Investment Company Act Rel. No. 28351 (Aug. 1, 2008). See also SEC Interpretation: Use of Electronic Media, Investment Company Act Rel. No. 24426 (May 4, 2000). I M G U I D A N C E U P D AT E This IM Guidance Update summarizes the views of the Division of Investment Management regarding various requirements of the federal securities laws. Future changes in laws or regulations may supersede some of the discussion or issues raised herein. This IM Guidance Update is not a rule, regulation or statement of the Commission, and the Commission has neither approved nor disapproved of this IM Guidance Update. The Investment Management Division works to: s protect investors s promote informed investment decisions and s facilitate appropriate innovation in investment products and services through regulating the asset management industry. If you have any questions about this IM Guidance Update, please contact: Catherine Courtney Gordon Chief Counsel’s Office/Public Inquiry Phone:202.551.6825 Email:IMOCC@sec.gov 10 Investor Alert: Social Media and Investing -- Stock Rumors Search July 25, 2014 The U.S. Securities and Exchange Commission’s (SEC) Office of Investor Education and Advocacy (“OIEA”) is issuing this Investor Alert to warn investors about fraudsters who may attempt to manipulate share prices by using social media to spread false or misleading information about stocks. Social media and the Internet in general have become important tools for investors. Investors may use social media to research particular stocks, look up background information on a broker-dealer or investment adviser, find guidance on investing strategies, receive up-to-date news, and discuss the markets with others. While social media can provide many benefits for investors, it also presents opportunities for fraudsters. Through social media, fraudsters can spread false or misleading information about a stock to large numbers of people with minimum effort and at a relatively low cost. They can also conceal their true identities by acting anonymously or even impersonating credible sources of market information. One way fraudsters may exploit social media is to engage in a market manipulation, such as spreading false and misleading information about a company to affect the stock’s share price. Wrongdoers may perpetuate stock rumors on social media, as well as on online bulletin boards and in Internet chat rooms. The false or misleading rumors may be positive or negative. For example, in a “pump-and-dump” scheme, promoters “pump” up the stock price by spreading positive rumors that incite a buying frenzy and they quickly “dump” their own shares before the hype ends. Typically, after the promoters profit from their sales, the stock price drops and the remaining investors lose money. In other instances, fraudsters start negative rumors urging investors to sell their shares so that the stock price plummets and the fraudsters take advantage of buying shares at the artificially low price. SEC Enforcement Action Involving Social Media and Market Manipulation The SEC has charged individuals for committing securities fraud through the use of social media. In SEC v. McKeown and Ryan, the SEC obtained judgments against a Canadian couple who used their website (PennyStockChaser), Facebook, and Twitter to pump up the stock of microcap companies, and then profited by selling shares of those companies. The couple allegedly received millions of shares of these companies as compensation and sold the shares around the time that their website predicted the stock price would massively increase (a practice known as “scalping”). The SEC’s complaint alleged that the couple did not fully disclose the compensation they received for touting the stocks. The court ordered the couple and their companies to pay more than $3.7 million in disgorgement for profits gained as a result of the alleged conduct, and ordered the couple to pay $300,000 in civil penalties. Investors should be aware that fraudsters may use social media to impersonate an established source of market information. For example, fraudsters may set up an account name, profile, or handle designed to mimic a particular company or securities research firm. They may go so far as to create a webpage that uses the company’s logo, links to the company’s actual website, or references the name of an actual person who works for the company. When you receive investment information through social media, verify the identity of the underlying source. Look for slight variations or typos in the sender’s account name, profile, email address, screen name, or handle, or other signs that the sender may be an imposter. Determine whether information appearing to be from a particular company or securities research firm is authentic. When contacting a company or attempting to access its website, be sure to use contact information or the website address provided by the company itself, such as in the company’s SEC filings. Carefully type the website’s address into the address bar of your web browser. Some social media operators have systems that may help you to determine whether or not a sender is genuine. For example, Twitter verifies accounts for authenticity by posting a blue verified badge (a solid blue circle containing a white checkmark) on Twitter profiles. While a verified account does not guarantee that the source is genuine, be more skeptical of information from accounts that are not verified. Think twice about investing if you spot any of these red flags of investment fraud: Limited history of posts. Fraudsters can set up new accounts specifically designed to carry out their scam while concealing their true identities. Be skeptical of information from social media accounts that lack a history of prior postings or sending messages. Pressure to buy or sell RIGHT NOW. Take the time to research the stock before you invest. Be skeptical of messages urging you to buy a hot stock before you “miss out” or to sell shares of a stock you own before the price goes down after negative news is announced. Be especially wary if the promoter claims the recommendation is based on “inside” or confidential information. Unsolicited investment information or offers. Fraudsters may look for victims on social media sites, chat rooms, and bulletin boards. Exercise extreme caution regarding information provided in new posts on your wall, tweets, direct messages, e-mails, or other communications that solicit an investment or provide information about a particular stock if you do not personally know the sender (even if the sender appears connected to someone you know). Unlicensed sellers. Federal and state securities laws require investment professionals and their firms who offer and sell investments to be licensed or registered. Many fraudulent investment schemes involve unlicensed individuals or unregistered firms. Check license and registration status by searching the SEC’s Investment Adviser Public Disclosure (IAPD) website or the Financial Industry Regulatory Authority (FINRA)’s BrokerCheck website. Investors who learn of investing opportunities from social media should always be on the lookout for fraud. If you are aware of possible securities fraud, including potential market manipulation, submit a tip or complaint to the SEC. To report a problem or to ask a question, submit a complaint or question to the SEC or call the SEC’s tollfree investor assistance line at (800) 732-0330 (dial 1-202-551-6551 if calling from outside of the United States). Additional Resources: Investor Alert: Investment Newsletters Used as Tools for Fraud Investor Alert: Don’t Trade on Pump-And-Dump Stock Emails Investor Alert: Social Media and Investing – Avoiding Fraud Investor Alert: Social Media and Investing – Understanding Your Accounts NASAA.org: Informed Investor Advisory: Social Networking Receive the latest Investor Alerts and Bulletins from OIEA by email or RSS feed. Visit Investor.gov, the SEC’s website for individual investors. Like OIEA on Facebook at www.facebook.com/secinvestoreducation. Follow OIEA on Twitter @SEC_Investor_Ed. Boards of Directors, Corporate Governance and Cyber-Risks: Sharpening the Focus Search Commissioner Luis A. Aguilar "Cyber Risks and the Boardroom" Conference New York Stock Exchange New York, NY June 10, 2014 Good afternoon. Thank you for that kind introduction. I am glad to be back at the New York Stock Exchange. In anticipating today’s conference, I thought back to an earlier trip to the NYSE where in April 2009, I had the opportunity to ring the closing bell. Before I begin my remarks, let me issue the standard disclaimer that the views I express today are my own, and do not necessarily reflect the views of the U.S. Securities and Exchange Commission (“SEC” or “Commission”), my fellow Commissioners, or members of the staff. I am pleased to be here and to have the opportunity to speak about cyber-risks and the boardroom, a topic that is both timely and extremely important. Over just a relatively short period of time, cybersecurity has become a top concern of American companies, financial institutions, law enforcement, and many regulators. [1] I suspect that not too long ago, we would have been hard-pressed to find many individuals who had even heard of cybersecurity, let alone known what it meant. Yet, in the past few years, there can be no doubt that the focus on this issue has dramatically increased.[2] Cybersecurity has become an important topic in both the private and public sectors, and for good reason. Law enforcement and financial regulators have stated publicly that cyber-attacks are becoming both more frequent and more sophisticated.[3] Indeed, according to one survey, U.S. companies experienced a 42% increase between 2011 and 2012 in the number of successful cyber-attacks they experienced per week.[4] As I am sure you have heard, recently there have also been a series of well-publicized cyber-attacks that have generated considerable media attention and raised public awareness of this issue. A few of the more well-known examples include: The October 2013 cyber-attack on the software company Adobe Systems, Inc., in which data from more than 38 million customer accounts was obtained improperly;[5] The December 2013 cyber-attack on Target Corporation, in which the payment card data of approximately 40 million Target customers and the personal data of up to 70 million Target customers was accessed without authorization;[6] The January 2014 cyber-attack on Snapchat, a mobile messaging service, in which a reported 4.6 million user names and phone numbers were exposed;[7] The sustained and repeated cyber-attacks against several large U.S. banks, in which their public websites have been knocked offline for hours at a time;[8] and The numerous cyber-attacks on the infrastructure underlying the capital markets, including quite a few on securities exchanges.[9] In addition to becoming more frequent, there are reports indicating that cyber-attacks have become increasingly costly to companies that are attacked. According to one 2013 survey, the average annualized cost of cyber-crime to a sample of U.S. companies was $11.6 million per year, representing a 78% increase since 2009.[10] In addition, the aftermath of the 2013 Target data breach demonstrates that the impact of cyber-attacks may extend far beyond the direct costs associated with the immediate response to an attack. [11] Beyond the unacceptable damage to consumers, these secondary effects include reputational harm that significantly affects a company’s bottom line. In sum, the capital markets and their critical participants, including public companies, are under a continuous and serious threat of cyber-attack, and this threat cannot be ignored.[12] As an SEC Commissioner, the threats are a particular concern because of the widespread and severe impact that cyber-attacks could have on the integrity of the capital markets infrastructure and on public companies and investors.[13] The concern is not new. For example, in 2011, staff in the SEC’s Division of Corporation Finance issued guidance to public companies regarding their disclosure obligations with respect to cybersecurity risks and cyber-incidents.[14] More recently, because of the escalation of cyber-attacks, I helped organize the Commission’s March 26, 2014 roundtable to discuss the cyber-risks facing public companies and critical market participants like exchanges, broker-dealers, and transfer agents.[15] Today, I would like to focus my remarks on what boards of directors can, and should, do to ensure that their organizations are appropriately considering and addressing cyber-risks. Effective board oversight of management’s efforts to address these issues is critical to preventing and effectively responding to successful cyber-attacks and, ultimately, to protecting companies and their consumers, as well as protecting investors and the integrity of the capital markets. The Role of the Boards of Directors in Overseeing Cyber-Risk Management Background on the Role of Boards of Directors When considering the board’s role in addressing cybersecurity issues, it is useful to keep in mind the broad duties that the board owes to the corporation and, more specifically, the board’s role in corporate governance and overseeing risk management. It has long been the accepted model, both here and around the world, that corporations are managed under the direction of their boards of directors.[16] This model arises from a central tenet of the modern corporation — the separation of ownership and control of the corporation. Under this structure, those who manage a corporation must answer to the true owners of the company — the shareholders. It would be neither possible nor desirable, however, for the many, widely-dispersed shareholders of any public company to come together and manage, or direct the management of, that company’s business and affairs. Clearly, effective full-time management is essential for public companies to function. But management without accountability can lead to self-interested decision-making that may not benefit the company or its shareholders. As a result, shareholders elect a board of directors to represent their interests, and, in turn, the board of directors, through effective corporate governance, makes sure that management effectively serves the corporation and its shareholders.[17] Corporate Boards and Risk Management Generally Although boards have long been responsible for overseeing multiple aspects of management’s activities, since the financial crisis, there has been an increased focus on what boards of directors are doing to address risk management.[18] Indeed, many have noted that, leading up to the financial crisis, boards of directors may not have been doing enough to oversee risk management within their companies, and that this failure contributed to the unreasonably risky behavior that resulted in the destruction of untold billions in shareholder value and plunged the country and the global economy into recession.[19] Although primary responsibility for risk management has historically belonged to management, the boards are responsible for overseeing that the corporation has established appropriate risk management programs and for overseeing how management implements those programs.[20] The importance of this oversight was highlighted when, in 2009, the Commission amended its rules to require disclosure about, among other things, the board’s role in risk oversight, including a description of whether and how the board administers its oversight function, such as through the whole board, a separate risk committee, or the audit committee.[21] The Commission did not mandate any particular structure, but noted that “risk oversight is a key competence of the board” and that “disclosure about the board’s involvement in the oversight of the risk management process should provide important information to investors about how a company perceives the role of its board and the relationship between the board and senior management in managing the material risks facing the company.”[22] The evidence suggests that boards of directors have begun to assume greater responsibility for overseeing the risk management efforts of their companies.[23] For example, according to a recent survey of 2013 proxy filings by companies comprising the S&P 200, the full boards of these companies are increasingly, and nearly universally, taking responsibility for the risk oversight of the company.[24] Clearly, boards must take seriously their responsibility to ensure that management has implemented effective risk management protocols. Boards of directors are already responsible for overseeing the management of all types of risk, including credit risk, liquidity risk, and operational risk[25] — and there can be little doubt that cyber-risk also must be considered as part of board’s overall risk oversight. The recent announcement that a prominent proxy advisory firm is urging the ouster of most of the Target Corporation directors because of the perceived “failure…to ensure appropriate management of [the] risks” as to Target’s December 2013 cyber-attack is another driver that should put directors on notice to proactively address the risks associated with cyber-attacks.[26] What Boards of Directors Can and Should Be Doing to Oversee Cyber-Risk Given the significant cyber-attacks that are occurring with disturbing frequency, and the mounting evidence that companies of all shapes and sizes are increasingly under a constant threat of potentially disastrous cyber-attacks, ensuring the adequacy of a company’s cybersecurity measures needs to be a critical part of a board of director’s risk oversight responsibilities. [27] In addition to the threat of significant business disruptions, substantial response costs, negative publicity, and lasting reputational harm, there is also the threat of litigation and potential liability for failing to implement adequate steps to protect the company from cyber-threats.[28] Perhaps unsurprisingly, there has recently been a series of derivative lawsuits brought against companies and their officers and directors relating to data breaches resulting from cyber-attacks.[29] Thus, boards that choose to ignore, or minimize, the importance of cybersecurity oversight responsibility, do so at their own peril. Given the known risks posed by cyber-attacks, one would expect that corporate boards and senior management universally would be proactively taking steps to confront these cyber-risks. Yet, evidence suggests that there may be a gap that exists between the magnitude of the exposure presented by cyberrisks and the steps, or lack thereof, that many corporate boards have taken to address these risks. Some have noted that boards are not spending enough time or devoting sufficient corporate resources to addressing cybersecurity issues.[30] According to one survey, boards were not undertaking key oversight activities related to cyber-risks, such as reviewing annual budgets for privacy and IT security programs, assigning roles and responsibilities for privacy and security, and receiving regular reports on breaches and IT risks.[31] Even when boards do pay attention to these risks, some have questioned the extent to which boards rely too much on the very personnel who implement those measures.[32] In light of these observations, directors should be asking themselves what they can, and should, be doing to effectively oversee cyber-risk management. NIST Cybersecurity Framework In considering where to begin to assess a company’s possible cybersecurity measures, one conceptual roadmap boards should consider is the Framework for Improving Critical Infrastructure Cybersecurity, released by the National Institute of Standards and Technology (“NIST”) in February 2014. The NIST Cybersecurity Framework is intended to provide companies with a set of industry standards and best practices for managing their cybersecurity risks.[33] In essence, the Framework encourages companies to be proactive and to think about these difficult issues in advance of the occurrence of a possibly devastating cyber-event. While the Framework is voluntary guidance for any company, some commentators have already suggested that it will likely become a baseline for best practices by companies, including in assessing legal or regulatory exposure to these issues or for insurance purposes.[34] At a minimum, boards should work with management to assess their corporate policies to ensure how they match-up to the Framework’s guidelines — and whether more may be needed. Board Structural Changes to Focus on Appropriate Cyber-Risk Management The NIST Cybersecurity Framework, however, is a bible without a preacher if there is no one at the company who is able to translate its concepts into action plans. Frequently, the board’s risk oversight function lies either with the full board or is delegated to the board’s audit committee. Unfortunately, many boards lack the technical expertise necessary to be able to evaluate whether management is taking appropriate steps to address cybersecurity issues. Moreover, the board’s audit committee may not have the expertise, support, or skills necessary to add oversight of a company’s cyber-risk management to their already full agenda.[35] As a result, some have recommended mandatory cyber-risk education for directors. [36] Others have suggested that boards be at least adequately represented by members with a good understanding of information technology issues that pose risks to the company.[37] Another way that has been identified to help curtail the knowledge gap and focus director attention on known cyber-risks is to create a separate enterprise risk committee on the board. It is believed that such committees can foster a “big picture” approach to company-wide risk that not only may result in improved risk reporting and monitoring for both management and the board, but also can provide a greater focus — at the board level — on the adequacy of resources and overall support provided to company executives responsible for risk management.[38] The Dodd-Frank Act already requires large financial institutions to establish independent risk committees on their boards.[39] Beyond the financial institutions required to do so, some public companies have chosen to proactively create such risk committees on their boards.[40] Research suggests that 48% of corporations currently have board-level risk committees that are responsible for privacy and security risks, which represents a dramatic increase from the 8% that reported having such a committee in 2008.[41] Clearly, there are various mechanisms that boards can employ to close the gap in addressing cybersecurity concerns — but it is equally clear that boards need to be proactive in doing so. Put simply, boards that lack an adequate understanding of cyber-risks are unlikely to be able to effectively oversee cyber-risk management. I commend the boards that are proactively addressing these new risks of the 21st Century. However, while enhancing board knowledge and board involvement is a good business practice, it is not necessarily a panacea to comprehensive cybersecurity oversight. Internal Roles and Responsibilities Focused on Cyber-Risk In addition to proactive boards, a company must also have the appropriate personnel to carry out effective cyber-risk management and to provide regular reports to the board. One 2012 survey reported that less than two-thirds of responding companies had full-time personnel in key roles responsible for privacy and security, in a manner that was consistent with internationally accepted best practices and standards.[42] In addition, a 2013 survey found that the companies that detected more security incidents and reported lower average financial losses per incident shared key attributes, including that they employed a full-time chief information security officer (or equivalent) who reported directly to senior management.[43] At a minimum, boards should have a clear understanding of who at the company has primary responsibility for cybersecurity risk oversight and for ensuring the adequacy of the company’s cyber-risk management practices.[44] In addition, as the evidence shows, devoting full-time personnel to cybersecurity issues may help prevent and mitigate the effects of cyber-attacks. Board Preparedness Although different companies may choose different paths, ultimately, the goal is the same: to prepare the company for the inevitable cyber-attack and the resulting fallout from such an event. As it has been noted, the primary distinction between a cyber-attack and other crises that a company may face is the speed with which the company must respond to contain the rapid spread of damage.[45] Companies need to be prepared to respond within hours, if not minutes, of a cyber-event to detect the cyber-event, analyze the event, prevent further damage from being done, and prepare a response to the event.[46] While there is no “one-size-fits-all” way to properly prepare for the various ways a cyber-attack can unfold, and what responses may be appropriate, it can be just as damaging to have a poorly-implemented response to a cyber-event. As others have observed, an “ill-thought-out response can be far more damaging than the attack itself.”[47] Accordingly, boards should put time and resources into making sure that management has developed a well-constructed and deliberate response plan that is consistent with best practices for a company in the same industry. These plans should include, among other things, whether, and how, the cyber-attack will need to be disclosed internally and externally (both to customers and to investors).[48] In deciding the nature and extent of the disclosures, I would encourage companies to go beyond the impact on the company and to also consider the impact on others. It is possible that a cyber-attack may not have a direct material adverse impact on the company itself, but that a loss of customers’ personal and financial data could have devastating effects on the lives of the company’s customers and many Americans. In such cases, the right thing to do is to give these victims a heads-up so that they can protect themselves.[49] Conclusion Let me conclude my remarks by reaffirming the significance of the role of good corporate governance. Corporate governance performed properly, results in the protection of shareholder assets. Fortunately, many boards take on this difficult and challenging role and perform it well. They do so by, among other things, being active, informed, independent, involved, and focused on the interests of shareholders. Good boards also recognize the need to adapt to new circumstances — such as the increasing risks of cyber-attacks. To that end, board oversight of cyber-risk management is critical to ensuring that companies are taking adequate steps to prevent, and prepare for, the harms that can result from such attacks. There is no substitution for proper preparation, deliberation, and engagement on cybersecurity issues. Given the heightened awareness of these rapidly evolving risks, directors should take seriously their obligation to make sure that companies are appropriately addressing those risks. Those of you who have taken the time and effort to be here today clearly recognize the risks, and I commend you for being proactive in dealing with the issue. Thank you for inviting me to speak to you today. [1] For example, the Director of the Federal Bureau of Investigation (FBI), James Comey, said last November that “resources devoted to cyber-based threats will equal or even eclipse the resources devoted to non-cyber based terrorist threats.” See, Testimony of James B. Comey, Jr., Director, FBI, U.S. Department of Justice, before the Senate Committee on Homeland Security and Governmental Affairs (Nov. 14, 2013), available at http://www.hsgac.senate.gov/hearings/threats-to-the-homeland. See also, Testimony of Jeh C. Johnson, Secretary, U.S. Department of Homeland Security, before the House Committee on Homeland Security (Feb. 26, 2014) (“DHS must continue efforts to address the growing cyber threat to the private sector and the ‘.gov’ networks, illustrated by the real, pervasive, and ongoing series of attacks on public and private infrastructure.”), available at http://docs.house.gov/meetings/HM/HM00/20140226/101722/HHRG-113-HM00-Wstate-JohnsonJ20140226.pdf; Testimony of Ari Baranoff, Assistant Special Agent in Charge, United States Secret Service Criminal Investigative Division, before the House Committee on Homeland Security, Subcommittee on Cybersecurity, Infrastructure Protection, and Security Technologies (Apr. 16, 2014), available at http://docs.house.gov/meetings/HM/HM08/20140416/102141/HHRG-113-HM08-Wstate-BaranoffA- 20140416.pdf (“Advances in computer technology and greater access to personally identifiable information (PII) via the Internet have created online marketplaces for transnational cyber criminals to share stolen information and criminal methodologies. As a result, the Secret Service has observed a marked increase in the quality, quantity, and complexity of cybercrimes targeting private industry and critical infrastructure.”); Remarks by Secretary of Defense Leon E. Panetta to the Business Executives for National Security (Oct. 11, 2012), available at http://www.defense.gov/transcripts/transcript.aspx?transcriptid=5136 (“As director of the CIA and now Secretary of Defense, I have understood that cyber attacks are every bit as real as the more well-known threats like terrorism, nuclear weapons proliferation and the turmoil that we see in the Middle East. And the cyber threats facing this country are growing.”). [2] See, e.g., Martin Lipton, et al., Risk Management and the Board of Directors — An Update for 2014, The Harvard Law School Forum on Corporate Governance and Financial Regulation (Apr. 22, 2014), available at http://blogs.law.harvard.edu/corpgov/2014/04/22/risk-management-and-the-board-of-directors-anupdate-for-2014/ (noting that cybersecurity is a risk management issue that “merits special attention” from the board of directors in 2014); PwC 2012 Annual Corporate Directors Survey, Insights from the Boardroom 2012: Board evolution: Progress made yet challenges persist, available at http://www.pwc.com/en_US/us/corporate-governance/annual-corporate-directors-survey/assets/pdf/pwcannual-corporate-directors-survey.pdf (finding that 72% of directors are engaged with overseeing and understanding data security issues and risks related to compromising customer data); Michael A. Gold, Cyber Risk and the Board of Directors–Closing the Gap, Bloomberg BNA (Oct. 18, 2013) available at http://www.bna.com/cyber-risk-and-the-board-of-directors-closing-the-gap// (“The responsibility of corporate directors to address cyber security is commanding more attention and is obviously a significant issue.”); Deloitte Development LLC, Hot Topics: Cybersecurity … Continued in the boardroom, Corporate Governance Monthly (Aug. 2013), available at http://www.corpgov.deloitte.com/binary/com.epicentric.contentmanagement.servlet.ContentDeliveryServlet /USEng/Documents/Deloitte%20Periodicals/Hot%20Topics/Hot%20Topics%20%20Cybersecurity%20%20%20Continued%20in%20the%20boardroom%20-August%202013%20-Final.pdf (“Not long ago, the term ‘cybersecurity’ was not frequently heard or addressed in the boardroom. Cybersecurity was often referred to as an information technology risk, and management and oversight were the responsibility of the chief information or technology officer, not the board. With the rapid advancement of technology, cybersecurity has become an increasingly challenging risk that boards may need to address.”); Holly J. Gregory, Board Oversight of Cybersecurity Risks, Thomson Reuters Practical Law (Mar. 1, 2014), available at http://us.practicallaw.com/5-558-2825 (“The risk of cybersecurity breaches (and the harm that these breaches pose) is one of increasing significance for most companies and therefore an area for heightened board focus.”). [3] For example, on December 9, 2013, the Financial Stability Oversight Council held a meeting to discuss cybersecurity threats to the financial system. See, U.S. Department of the Treasury Press Release, “Financial Stability Oversight Council to Meet December 9,” available at http://www.treasury.gov/presscenter/press-releases/Pages/jl2228.aspx. During that meeting, Assistant Treasury Secretary Cyrus-AmirMokri said that “[o]ur experience over the last couple of years shows that cyber-threats to financial institutions and markets are growing in both frequency and sophistication.” See, Remarks of Assistant Secretary Cyrus Amir-Mokri on Cybersecurity at a Meeting of the Financial Stability Oversight Council (Dec. 9, 2013), available at http://www.treasury.gov/press-center/press-releases/Pages/jl2234.aspx. In addition, in testimony before the House Financial Services Committee in 2011, the Assistant Director of the FBI’s Cyber Division stated that the number and sophistication of malicious incidents involving financial institutions has increased dramatically over the past several years and offered numerous examples of such attacks, which included fraudulent monetary transfers, unauthorized financial transactions from compromised bank and brokerage accounts, denial of service attacks on U.S. stock exchanges, and hacking incidents in which confidential information was misappropriated. See, Testimony of Gordon M. Snow, Assistant Director, Cyber Division, FBI, U.S. Department of Justice, before the House Financial Services Committee, Subcommittee on Financial Institutions and Consumer Credit (Sept. 14, 2011), available at http://financialservices.house.gov/uploadedfiles/091411snow.pdf. [4] 2012 Cost of Cyber Crime Study: United States, Ponemon Institute LLC and HP Enterprise Security (Oct. 2012), available at http://www.ponemon.org/local/upload/file/2012_US_Cost_of_Cyber_Crime_Study_FINAL6%20.pdf. [5] See, e.g., Jim Finkle, Adobe says customer data, source code accessed in cyber attack, Reuters (Oct. 3, 2013), available at http://www.reuters.com/article/2013/10/03/us-adobe-cyberattackidUSBRE99212Y20131003; Jim Finkle, Adobe data breach more extensive than previously disclosed, Reuters (Oct. 29, 2013), available at http://www.reuters.com/article/2013/10/29/us-adobe-cyberattackidUSBRE99S1DJ20131029; Danny Yadron, Hacker Attack on Adobe Sends Ripples Across Web, Wall Street Journal (Nov. 11, 2013), available at http://online.wsj.com/news/articles/SB10001424052702304644104579192393329283358. [6] See, Testimony of John Mulligan, Executive Vice President and Chief Financial Officer of Target, before the Senate Judiciary Committee (Feb. 4, 2014), available at http://www.judiciary.senate.gov/imo/media/doc/02-04-14MulliganTestimony.pdf; Target Press Release, “Target Confirms Unauthorized Access to Payment Card Data in U.S. Stores” (Dec. 19, 2013), available at http://pressroom.target.com/news/target-confirms-unauthorized-access-to-payment-card-data-in-u-sstores. [7] See, e.g., Andrea Chang and Salvador Rodriguez, Snapchat becomes target of widespread cyberattack, L.A. Times (Jan. 2, 2014), available at http://articles.latimes.com/2014/jan/02/business/la-fi-snapchathack-20140103; Brian Fung, A Snapchat security breach affects 4.6 million users. Did Snapchat drag its feet on a fix? Washington Post (Jan. 1, 2014), available at http://www.washingtonpost.com/blogs/theswitch/wp/2014/01/01/a-snapchat-security-breach-affects-4-6-million-users-did-snapchat-drag-its-feet-ona-fix/. [8] See, e.g., Joseph Menn, Cyber attacks against banks more severe than most realize, Reuters (May 18, 2013), available at http://www.reuters.com/article/2013/05/18/us-cyber-summit-banksidUSBRE94G0ZP20130518; Bob Sullivan, Bank Website Attacks Reach New Highs, CNBC (Apr. 3, 2013), available at http://www.cnbc.com/id/100613270. [9] For example, according to a 2012 global survey of securities exchanges, 53% reported experiencing a cyber-attack in the previous year. See, Rohini Tendulkar, Cyber-crime, securities markets, and systemic risk, Joint Staff Working Paper of the IOSCO Research Department and World Federation of Exchanges (July 16, 2013), available at http://www.iosco.org/research/pdf/swp/Cyber-Crime-Securities-Markets-andSystemic-Risk.pdf. Forty-six securities exchanges responded to the survey. [10] See, HP Press Release, HP Reveals Cost of Cybercrime Escalates 70 Percent, Time to Resolve Attacks More Than Doubles (Oct. 8, 2013), available at http://www8.hp.com/us/en/hp-news/press-release.html? id=1501128. [11] See, Target Financial News Release, Target Reports Fourth Quarter and Full-Year 2013 Earnings (Feb. 26, 2014), available at http://investors.target.com/phoenix.zhtml?c=65828&p=irolnewsArticle&ID=1903678&highlight (including a statement from then-Chairman, President and CEO Gregg Steinhafel that Target’s fourth quarter results “softened meaningfully following our December announcement of a data breach.”); Elizabeth A. Harris, Data Breach Hurts Profit at Target, N.Y. Times (Feb. 26, 2014), available at http://www.nytimes.com/2014/02/27/business/target-reports-on-fourth-quarterearnings.html?_r=0 (noting that “[t]he widespread theft of Target customer data had a significant impact on the company’s profit, which fell more than 40 percent in the fourth quarter” of 2013). [12] I also want to note that at the Investment Company Institute’s (“ICI”) general membership meeting, held just last month, the issue of cybersecurity was front and center. Among the issues raised during the meeting was the “huge risk to brand” for a firm if they have a security failure in the event of a cyber-attack. A separate panel at the ICI conference devoted to cybersecurity also discussed the shift in focus from building “hard walls” to protect against risks from outside the company to cybersecurity focused on “inside” risks, such as ensuring that individuals with mobile applications or other types of flexible applications don’t introduce, intentionally or unintentionally, malware or other kinds of security breaches that could lead to a cyber-attack on the company. See, e.g., Jackie Noblett, Cyber Breach a “Huge Risk to Brand,” Ignites (May 29, 2014), available at http://ignites.com/c/897654/86334/cyber_breach_huge_risk_brand? referrer_module=emailMorningNews&module_order=7. [13] See, Commissioner Luis A. Aguilar, The Commission’s Role in Addressing the Growing Cyber-Threat (Mar. 26, 2014), available at http://www.sec.gov/News/PublicStmt/Detail/PublicStmt/1370541287184. [14] On October 13, 2011, staff in the Commission’s Division of Corporation Finance (Corp Fin) issued guidance on issuers’ disclosure obligations relating to cyber security risks and cyber incidents. See, SEC’s Division of Corporation Finance, CF Disclosure Guidance: Topic No. 2—Cybersecurity (“SEC Guidance”) (Oct. 31, 2011), available at http://www.sec.gov/divisions/corpfin/guidance/cfguidance-topic2.htm. Among other things, this guidance notes that securities laws are designed to elicit disclosure of timely, comprehensive, and accurate information about risks and events that a reasonable investor would consider important to an investment decision, and cybersecurity risks and events are not exempt from these requirements. The guidance identifies six areas where cybersecurity disclosures may be necessary under Regulation S-K: (1) Risk Factors; (2) Management’s Discussion and Analysis of Financial Condition and Results of Operation (MD&A); (3) Description of Business; (4) Legal Proceedings; (5) Financial Statement Disclosures; and (6) Disclosure Controls and Procedures. The SEC Guidance further recommends that material cybersecurity risks should be disclosed and adequately described as Risk Factors. Where cybersecurity risks and incidents that represent a material event, trend or uncertainty reasonably likely to have a material impact on the organization's operations, liquidity, or financial condition — it should be addressed in the MD&A. If cybersecurity risks materially affect the organization’s products, services, relationships with customers or suppliers, or competitive conditions, the organization should disclose such risks in its description of business. Data breaches or other incidents can result in regulatory investigations or private actions that are material and should be discussed in the Legal Proceedings section. Cybersecurity risks and incidents that represent substantial costs in prevention or response should be included in Financial Statement Disclosures where the financial impact is material. Finally, where a cybersecurity risk or incident impairs the organization's ability to record or report information that must be disclosed, Disclosure Controls and Procedures that fail to address cybersecurity concerns may be ineffective and subject to disclosure. Some have suggested that such disclosures fail to fully inform investors about the true costs and benefits of companies’ cybersecurity practices, and argue that the Commission (and not the staff) should issue further guidance regarding issuers’ disclosure obligations. See, Letter from U.S. Senator John D. Rockefeller IV to Chair White (Apr. 9, 2013), available at http://www.commerce.senate.gov/public/? a=Files.Serve&File_id=49ac989b-bd16-4bbd-8d64-8c15ba0e4e51. [15] See SEC Press Release, SEC Announces Agenda, Panelists for Cybersecurity Roundtable (Mar. 24, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370541253749; Cybersecurity Roundtable Webcast (Mar. 26, 2014), available at http://www.sec.gov/news/otherwebcasts/2014/cybersecurity-roundtable-032614.shtml. In addition, the SEC’s National Exam Program has included cybersecurity among its areas of focus in its National Examination Priorities for 2014. See, SEC’s National Exam Priorities for 2014, available at http://www.sec.gov/about/offices/ocie/national-examination-program-priorities-2014.pdf. In addition, it was recently announced that SEC examiners will review whether asset managers have policies to prevent and detect cyber-attacks and are properly safeguarding against security risks that could arise from vendors having access to their systems. See, Sarah N. Lynch, SEC examiners to review how asset managers fend off cyber attacks, Reuters (Jan. 30, 2014), available at http://www.reuters.com/article/2014/01/30/us-seccyber-assetmanagers-idUSBREA0T1PJ20140130. FINRA has also identified cybersecurity as one of its examination priorities for 2014. See, FINRA’s 2014 Regulatory and Examination Priorities Letter (Jan. 2, 2014), available at http://www.finra.org/web/groups/industry/@ip/@reg/@guide/documents/industry/p419710.pdf. To continue the discussion and to allow the public to weigh in on this important topic, the SEC set up a public comment file associated with the Cybersecurity Roundtable. To date, we have received ten comment letters from academics, software companies, and other interested parties, available at http://www.sec.gov/comments/4-673/4-673.shtml. See, e.g., Jodie Kelly, Senior Vice President and General Counsel, BSA| The Software Alliance comment letter (Apr. 30, 2014) (highlighting the importance of strong internal controls related to software assets as a first line of defense against cyber-attacks, and noting that verifying legal use of software is a critical first step in deterring cyber-attacks because the “existence and availability of pirated and counterfeit software exposes corporate information technology networks to significant risks in many ways.”); Tom C.W. Lin, Associate Professor of Law, Temple University Beasley School of Law comment letter (Apr. 29, 2014) (expressing support for the roundtable and the Commission’s attention to cybersecurity and highlighting four broad issues for the Commission’s consideration: (1) cybersecurity threats to the high-speed, electronically connected modern capital markets can create systemic risks; (2) due to technological advances, financial choices are made by both people and machines, which does not comport congruently with many traditional modes of securities regulation; (3) incentives, in addition to penalties, should be designed to encourage firms to upgrade their cybersecurity capabilities; and (4) private regulation of cybersecurity should be vigorously enhanced and leveraged to better complement government regulation); Dave Parsonage, CEO, MitoSystems, Inc. comment letter (Apr. 3, 2014); Gail P. Ricketts, Senior IT Compliance and Risk Analyst, ON Semiconductor comment letter (Mar. 26, 2014) (suggesting future roundtables include speakers from outside the financial services industry, such as manufacturing); Michael Utzig, IT Director, Hefren Tillotson, Inc. comment letter (Mar. 26, 2014) (noting that readily available technologies that can protect email communications are not widely used despite universal understanding that cybersecurity is a high-priority); Cathy Santoro comment letter (Mar. 26, 2014) (raising questions about the interactions between banks and service providers and the measures being undertaken regarding mobile payment cybersecurity risks); Duane Kuroda, Senior Threat Researcher, NetCitadel comment letter (Mar. 25, 2014) (noting that the panel discussion should focus on the process and people involved in responding to breaches and not just their detection); William Pfister, Jr. comment letter (Mar. 25, 2014) (requesting that one of the panels address the potential conflicts between national security and required disclosure). Many of these letters are generally supportive of the Commission’s efforts and focus in this area, and some identify issues and concerns that were not discussed in detail during the roundtable and warrant further attention. For example, one commenter highlighted the need for companies to adopt sound internal controls over the legal use of software, noting that pirated and counterfeit software can expose companies to heightened risk of cyber-attacks and recommending that registrants report on the status of such internal controls.[15] See, e.g., Jodie Kelly, Senior Vice President and General Counsel, BSA| The Software Alliance comment letter (Apr. 30, 2014) (noting, among other things, that unlicensed software eliminates the opportunity for security updates and patches from legitimate vendors when security breaches are identified, and that malware and viruses may be contained within pirated software itself or reside on the networks from which it is downloaded. BSA recommends that registrants report on the status of their internal controls in the area of licensing and legal use of software, and that such controls should, at a minimum, ensure that software is only purchased from authorized vendors and that companies should have procedures to conduct periodic software inventories and limit exposure to malware and viruses brought into their systems by linkage of employees’ personal devices to corporate systems). I encourage others to comment and provide valuable input on this critical issue. [16] See, e.g., Model Bus. Corp. Act § 8.01 (2002); Del. Gen. Corp. Law § 141(a). [17] For additional thoughts on the importance of effective corporate governance, see Commissioner Luis A. Aguilar, Looking at Corporate Governance from the Investor’s Perspective, available at http://www.sec.gov/News/Speech/Detail/Speech/1370541547078. [18] See, e.g., Committee of Sponsoring Organizations of the Treadway Commission, Effective Enterprise Risk Oversight: The Role of the Board of Directors (2009), available at http://www.coso.org/documents/COSOBoardsERM4pager-FINALRELEASEVERSION82409_001.pdf (“Clearly, one result of the financial crisis is an increased focus on the effectiveness of board risk oversight practices.”); Committee of Sponsoring Organizations of the Treadway Commission, Board Risk Oversight: A Progress Report — Where Boards of Directors Currently Stand in Executing Their Risk Oversight Responsibilities (Dec. 2010), available at http://www.coso.org/documents/Board-Risk-Oversight-SurveyCOSO-Protiviti_000.pdf (“Risk oversight is a high priority on the agenda of most boards of directors. Recently, the importance of this responsibility has become more evident in the wake of an historic global financial crisis, which disclosed perceived risk management weaknesses across financial services and other organizations worldwide. Based on numerous legislative and regulatory actions in the United States and other countries as well as initiatives in the private sector, it is clear that expectations for more effective risk oversight are being raised not just for financial services companies, but broadly across all types of businesses.”); David A. Katz, Boards Play A Leading Role in Risk Management Oversight, The Harvard Law School Forum on Corporate Governance and Financial Regulation (Oct. 8, 2009), available at http://blogs.law.harvard.edu/corpgov/2009/10/08/boards-play-a-leading-role-in-risk-managementoversight/ (“Just as the Enron and other high-profile corporate scandals were seen as resulting from a lack of ethics and oversight, the credit market meltdown and resulting financial crisis have been blamed in large part on inadequate risk management by corporations and their boards of directors. As a result, along with the task of implementing corporate governance procedures and guidelines, a company’s board of directors is expected to take a leading role in overseeing risk management structures and policies.”). [19] Nicola Faith Sharpe, Informational Autonomy in the Boardroom, 201 U. Ill. L. Rev. 1089 (2013) (“The financial crisis of 2007-2008 was one of the worst in U.S. history. In a single quarter, the blue chip company Lehman Brothers (who eventually went bankrupt) lost $2.8 billion. While commentators have identified multiple reasons why the crisis occurred, many posit that boards mismanaged risk and failed in their oversight duties, which directly contributed to their firms failing.”); Lawrence J. Trautman and Kara Altenbaumer-Price, The Board’s Responsibility for Information Technology Governance, 28 J. Marshall J. Computer & Info. L. 313 (Spring 2011) (“With accusations that boards of directors of financial institutions were asleep at the wheel while their companies engaged in risky behavior that erased millions of dollars of shareholder value and plunged the country into recession, increasing pressure is now being placed on public company boards to shoulder the burden of risk oversight for the companies they serve.”); William B. Asher, Jr., Michael T. Gass, Erik Skramstad, and Michele Edwards, The Role of Board of Directors in Risk Oversight in a Post-Crisis Economy, Bloomberg Law Reports-Corporate Law Vol. 4, No. 13, available at http://www.choate.com/uploads/113/doc/Asher,%20Gass%20The%20Role%20of%20Board%20of%20Directors%20in%20Risk%20Oversight%20in%20a%20PostCrisis%20Economy.pdf (“Senior management and corporate directors face renewed criticism surrounding risk management practices and apparent failures in oversight that are considered, at least in part, to be at the root of the recent crisis.”). [20] See, e.g., Stephen M. Bainbridge, Caremark and Enterprise Risk Management, 34 Iowa J. Corp. L. 967 (2009) (“Although primary responsibility for risk management rests with the corporation’s top management team, the board of directors is responsible for ensuring that the corporation has established appropriate risk management programs and for overseeing management’s implementation of such programs.”); Martin Lipton, Risk Management and the Board of Directors–An Update for 2014, The Harvard Law School Forum on Corporate Governance and Financial Regulation (Apr. 22, 2014), available at http://blogs.law.harvard.edu/corpgov/2014/04/22/risk-management-and-the-board-of-directors-anupdate-for-2014/ (“. . . the board cannot and should not be involved in actual day-to day risk management. Directors should instead, through their risk oversight role, satisfy themselves that the risk management policies and procedures designed and implemented by the company’s senior executives and risk managers are consistent with the company’s strategy and risk appetite, that these policies and procedures are functioning as directed, and that necessary steps are taken to foster a culture of risk-aware and riskadjusted decision making throughout the organization. The board should establish that the CEO and the senior executives are fully engaged in risk management and should also be aware of the type and magnitude of the company’s principal risks that underlie its risk oversight. Through its oversight role, the board can send a message to management and employees that comprehensive risk management is neither an impediment to the conduct of business nor a mere supplement to a firm’s overall compliance program, but is instead an integral component of strategy, culture and business operations.”). [21] Proxy Disclosure Enhancements, SEC Rel. No. 33-9089 (Dec. 16, 2009), 74 Fed. Reg. 68334, available at http://www.sec.gov/rules/final/2009/33-9089.pdf. [22] Id. That amendment also required disclosure of a company’s compensation policies and practices as they relate to a company’s risk management in order to help investors identify whether the company has established a system of incentives that could lead to excessive or inappropriate risk taking by its employees. [23] Supra note 19, William B. Asher, Jr. et al., The Role of Board of Directors in Risk Oversight in a PostCrisis Economy (“We know today, however, that risk management has indeed forced its way into the boardroom and that there has been a substantial change in the relationship between the overseers of public companies and their shareholders.”). [24] Risk Intelligent Proxy Disclosures — 2013: Trending upward, Deloitte (2013), available at http://deloitte.wsj.com/riskandcompliance/files/2014/01/Risk_Intelligent_Proxy_Disclosures_2013.pdf (noting that 91% of the issuers of proxy disclosures noted that “the full board is responsible for risk.”). [25] See, Proxy Disclosure Enhancements, supra note 21. [26] Paul Ziobro, Target Shareholders Should Oust Directors, ISS Says, Wall St. Journal (May 28, 2014), available at http://online.wsj.com/article/BT-CO-20140528-709863.html; Bruce Carton, ISS Recommends Ouster of Seven Target Directors for Data Breach Failures, ComplianceWeek (May 29, 2014), available at http://www.complianceweek.com/iss-recommends-ouster-of-seven-target-directors-for-data-breachfailures/article/348954/?DCMP=EMC-CW-WeekendEdition. [27] See, e.g., Risk Management and the Board of Directors–An Update for 2014, supra note 2 (noting that cybersecurity is a risk management issue that “merits special attention” from the board of directors in 2014); Alice Hsu, Tracy Crum, Francine E. Friedman, and Karol A. Kepchar, Cybersecurity Update: Are Data Breach Disclosure Requirements On Target?, The Metropolitan Corporate Counsel (Jan. 24, 2014), available at http://www.metrocorpcounsel.com/articles/27148/cybersecurity-update-are-data-breach-disclosurerequirements-target (“As part of a board’s risk management oversight function, directors should assess the adequacy of their company’s data security measures. Among other things, boards should have a clear understanding of the company’s cybersecurity risk profile and who has primary responsibility for cybersecurity risk oversight and should ensure the adequacy of the company’s cyber risk management practices, as well as the company’s insurance coverage for losses and costs associate with data breaches.”). [28] Charles R. Ragan, Information Governance: It’s a Duty and It’s Smart Business, 19 Rich. J.L. & Tech. 12 (2013), available at http://jolt.richmond.edu/v19i4/article12.pdf. (indicating that “[t]he principles thus enunciated raise the specter of potential liability if officers and directors utterly fail to ensure the adequacy of information systems.”); J. Wylie Donald and Jennifer Black Strutt, Cybersecurity: Moving Toward a Standard of Care for the Board, Bloomberg BNA (Nov. 4, 2013), available at http://www.bna.com/cybersecurity-moving-toward-a-standard-of-care-for-the-board/ (quoting from a Delaware Chancery Court decision stating that directors may be liable if “(a) the directors utterly failed to implement any reporting or information system or controls; or (b) having implemented such a system or controls, consciously failed to monitor or oversee its operations thus disabling themselves from being informed of risks or problems requiring their attention.”). [29] See, e.g., Collier v. Steinhafel et al. (D.C. Minn. Jan. 2014), case number 0:14-cv-00266 (alleging that Target's board and top executives harmed the company financially by failing to take adequate steps to prevent the cyber-attack then by subsequently providing customers with misleading information about the extent of the data theft.); Dennis Palkon et al. v. Stephen P. Holmes et al. (D.C.N.J. May 2014), case number 2:14-cv-01234 (alleging that Wyndham's board and top executives harmed the company financially by failing to take adequate steps to safeguard customers' personal and financial information.). [30] Steven P. Blonder, How closely is the board paying attention to cyber risks?, Inside Counsel (formerly Corporate Legal Times) (Apr. 9, 2014), available at http://www.insidecounsel.com/2014/04/09/howclosely-is-the-board-paying-attention-to-cyber. (Indicating that “[i]n all likelihood, absent an incident, it is likely that board members are not spending sufficient time evaluating or analyzing the risks inherent in new technologies, as well as their related cybersecurity risks.”). [31] Jody R. Westby, Governance of Enterprise Security: CyLab 2012 Report — How Boards & Senior Executives Are Managing Cyber Risks, Carnegie Mellon University CyLab (May 16, 2012), at 5. (Hereinafter “CyLab 2012 Report.”). [32] Supra note 30, Steven P. Blonder, How Closely is the Board Paying Attention to Cyber Risks? (stating that “[f]urther, even if a board has evaluated these risks, to what extent is such an evaluation dependent on a company’s IT department — the same group implementing the existing technology protocols?”). [33] The National Institute of Standards and Technology Framework for Improving Critical Infrastructure Cybersecurity (Feb. 12, 2014) (the “NIST Cybersecurity Framework”), available at http://www.nist.gov/cyberframework/upload/cybersecurity-framework-021214.pdf, was released in response to President Obama’s issued Executive Order 13636, titled “Improving Critical Infrastructure Cybersecuity,” dated February 12, 2013. The NIST Cybersecurity Framework sets out five core functions and categories of activities for companies to implement that relate generally to cyber-risk management and oversight, which the NIST helpfully boiled down to five terms: Identify, Protect, Detect, Respond and Recover. This core fundamentally means the following: companies should (i) identify known cybersecurity risks to their infrastructure; (ii) develop safeguards to protect the delivery and maintenance of infrastructure services; (iii) implement methods to detect the occurrence of a cybersecurity event; (iv) develop methods to respond to a detected cybersecurity event; and (v) develop plans to recover and restore the companies’ capabilities that were impaired as a result of a cybersecurity event. See also, Ariel Yehezkel and Thomas Michael, Cybersecurity: Breaching the Boardroom, The Metropolitan Corporate Counsel (Mar. 17, 2014), available at http://www.sheppardmullin.com/media/article/1280_MCCCybersecurity-Breaching%20The%20Boardroom.pdf. [34] Supra note 2, Holly J. Gregory, Board Oversight of Cybersecurity Risks; supra note 33, Ariel Yehezkel and Thomas Michael, Cybersecurity: Breaching the Boardroom (stating that “[w]hile adoption of the Cybersecurity Framework is voluntary, it will likely become a key reference for regulators, insurance companies and the plaintiffs’ bar in assessing whether a company took steps reasonably designed to reduce and manage cybersecurity risks.”). [35] Matteo Tonello, Should Your Board Have a Separate Risk Committee?, The Harvard Law School Forum on Corporate Governance and Financial Regulation (Feb. 12, 2012), available at https://blogs.law.harvard.edu/corpgov/2012/02/12/should-your-board-have-a-separate-risk-committee/ (asking “[d]oes the audit committee have the time, the skills, and the support to do the job, given everything else it is required to do?”). [36] See, e.g., Katie W. Johnson, Publicly Traded Companies Should Prepare To Disclose Cybersecurity Risks, Incidents, Bloomberg BNA (Mar. 17, 2014), available at http://www.bna.com/publicly-tradedcompanies-n17179885721/ (citing Mary Ellen Callahan, Chair of the Privacy and Information Governance Practice at Jenner & Block, LLP at the International Association of Privacy Professionals Global Privacy Summit, held in March 2014); Michael A. Gold, Cyber Risk and the Board of Directors — Closing the Gap, Bloomberg BNA (Oct. 18, 2013), available at http://www.bna.com/cyber-risk-and-the-board-of-directorsclosing-the-gap// (suggesting that companies would do well to have “[m]andatory cyber risk education for directors,” among other things.); see also, The Comprehensive National Cybersecurity Initiative, initially launched by then-President George W. Bush in 2008, referencing “Initiative #8. Expand cyber education,” and available at http://www.whitehouse.gov/issues/foreign-policy/cybersecurity/national-initiative. [37] Supra note 19, Lawrence J. Trautman and Kara Altenbaumer-Price, The Board’s Responsibility for Information Technology Governance. [38] Supra note 35, Matteo Tonello, Should Your Board Have a Separate Risk Committee?; supra note 33, Ariel Yehezkel and Thomas Michael, Cybersecurity: Breaching the Boardroom. [39] Dodd-Frank Act Section 165(h). [40] Supra note 19, Lawrence J. Trautman and Kara Altenbaumer-Price, The Board’s Responsibility for Information Technology Governance. [41] Deloitte Audit Committee Brief, Cybersecurity and the audit committee (Aug. 2013), at 2, available at http://deloitte.wsj.com/cfo/files/2013/08/ACBrief_August2013.pdf. [42] See, supra note 31, CyLab 2012 Report, at 27. [43] PricewaterhouseCoopers LLP, The Global State of Information Security Survey 2014, at 4, available at http://www.pwc.com/gx/en/consulting-services/information-security-survey/download.jhtml (the “PwC IS Survey”). The PwC IS Survey also noted other shared attributes, such as having (i) an overall information security strategy; (ii) measured and reviewed the effectiveness of their security measures within the past year; and (iii) an understanding as to exactly what type of security events have occurred in the past year. See also, supra note 2, Holly Gregory, Board Oversight of Cybersecurity Risks. [44] Supra note 27, Alice Hsu, et al., Cybersecurity Update: Are Data Breach Disclosure Requirements on Target?. [45] See, e.g., Roland L. Trope and Stephen J. Humes, Before Rolling Blackouts Begin: Briefing Boards on Cyber Attacks That Target and Degrade the Grid, 40 Wm. Mitchell L. Rev. 647 (2014), at 656 (stating that “unlike other corporate crises, boards and management must be ready to address severe cyber incidents with response and recovery plans that activate upon discovery of an intrusion and with little or no time for deliberation.”) Some observers have even suggested that companies conduct “cyberwar games” organized around hypothetical business scenarios in order to reenact how a company might respond in a real cybersecurity situation in order to fix what vulnerabilities are teased out from the simulated scenario. Tucker Bailey, James Kaplan, and Allen Weinberg, Playing war games to prepare for a cyberattack, McKinsey & Company Insights & Publications (July 2012). Other observers have suggested that companies implement a response plan that takes into consideration a number of factors, such as (i) how much risk the company can accept if systems or services have to shut down; (ii) for how long the company can sustain operations using limited or backup technology; and (iii) how quickly the company can restore full operations. See, Former FBI Agent Mary Galligan on Preparing for a Cyber Attack, CIO Journal, Deloitte Insights (Mar. 3, 2104), available at http://deloitte.wsj.com/cio/2014/03/03/former-fbi-agent-marygalligan-on-preparing-for-a-cyber-attack/. [46] See, e.g., id., Roland L. Trope and Stephen J. Humes, Before Rolling Blackouts Begin: Briefing Boards on Cyber Attacks That Target and Degrade the Grid, at 656. [47] Supra note 45, Tucker Bailey, James Kaplan, and Allen Weinberg, Playing War Games to Prepare for a Cyberattack. [48] Supra note 33, Ariel Yehezkel and Thomas Michael, Cybersecurity: Breaching the Boardroom, Metropolitan Corporate Counsel (stating that “Boards should prepare for worst-case scenario cybersecurity breaches and help management develop immediate response plans, including public disclosure procedures and economic recovery strategies, to mitigate potential damages.” In addition, “[b]oards should consider disclosing cybersecurity risks and protective measures on relevant SEC filings, as such disclosures can generate confidence in investors rather than fear.”) The U.S. Department of Commerce also has suggested that a company’s cybersecurity preparedness could include cybersecurity insurance, which is specifically designed to mitigate losses from a variety of cyber incidents, including data breaches, business interruption, and network damage. Cybersecurity Insurance, U.S. Department of Homeland Security, available at http://www.dhs.gov/publication/cybersecurity-insurance. Despite the increased threats of cyber-attacks, the cybersecurity insurance market has been slow to develop, and many companies have chosen to forego available policies, citing their perceived high cost, a lack of awareness about what they cover, and their confidence (or ignorance) about their actual risk of a cyber-attack. Id. Moreover, despite the fact that cyber incidents are not covered by general liability policies, one survey noted that 57% of respondents indicated that their boards are not reviewing their existing policies for cyber-related risks. See, supra note 31, CyLab 2012 Report, at 15. [49] The Department of Justice recently unsealed indictments against five Chinese military officials who allegedly conspired to steal information from U.S. companies across different industries. In connection with this indictment, it was recently reported that three U.S. public companies identified as victims of this conspiracy failed to report the theft of trade secrets and other data to their investors, despite the Commission’s disclosure guidance on this topic. Two of the companies, Alcoa Inc. and Allegheny Technologies Inc., said that the thefts were not “material,” and therefore did not have to be disclosed to investors. See, Chris Strohm, Dave Michaels and Sonja Elmquist, U.S. Companies Hacked by Chinese Didn’t Tell Investors, Bloomberg (May 21, 2014), available at http://www.bloomberg.com/news/2014-05-21/u-scompanies-hacked-by-chinese-didn-t-tell-investors.html; See also, supra note 14. Last modified: June 10, 2014 Keynote Address at Compliance Week 2014 Search Andrew Ceresney Director of the Division of Enforcement Washington D.C. May 20, 2014 At the outset, let me give the requisite reminder that the views I express today are my own and do not necessarily represent the views of the Commission or its staff. It is a real pleasure to be here with a group of legal and compliance professionals. In my time in private practice, and now as the Director of Enforcement, I have come to appreciate how your work is invaluable to the SEC’s mission of protecting investors and ensuring the integrity of our markets. You serve as a critical line of defense against securities law violations. I recently reached my one-year anniversary since joining the Commission, and so I want to share with you today my thoughts on some of our accomplishments over the last year, including some of the significant changes we have made, and what lies ahead. As I often like to say, this is a great time to be in the Enforcement Division. Let me first salute the Division staff. I have been truly amazed every day by the talent, ingenuity and commitment of the people in Enforcement. They possess a tremendous wealth of knowledge and experience and are wholly devoted to the mission of the Agency. In all of their actions, they are tough and aggressive but fair. Thanks to their efforts, we achieved a great deal in my first year. I could stand here and give you statistics about the number of enforcement actions brought last year and the amounts of disgorgement and penalties that were ordered as a result of those actions. But you can obtain those numbers from our website, and such quantitative metrics do not fully capture the effectiveness of our enforcement efforts. When measuring our performance, we primarily consider the quality, breadth, and impact of our efforts. And by that standard, it was a banner year, as our cases spanned the full breadth of the securities industry, served as a strong deterrent to misconduct, punished securities violators, returned funds to injured investors, and sent important messages to the market. Those cases included actions against exchanges to ensure they operate fairly and in compliance with applicable rules, actions against investment advisers and broker-dealers for taking undisclosed fees and for disrupting the markets through failures in their automated trading systems, important financial reporting cases against issuers, actions against auditors and others who serve as gatekeepers to our financial system, FCPA cases against large multinational corporations, actions against municipal issuers, and landmark insider trading cases. We covered the proverbial waterfront of securities violations. Specialized Units As you know, pursuing violations related to the financial crisis has been one of our key priorities. But after successfully addressing such misconduct over the last five years, we now have shifted our attention to other areas and redeployed our resources accordingly. Let me touch on some of those areas. My predecessor, Rob Khuzami, created five specialized units relating to areas of significant concern. The idea was to build expertise and knowledge in each of these areas, and to have unit personnel solely focused on making cases in these important areas. As I like to say, these units were designed not just to eat a piece of the “Enforcement pie” – by working on cases that we otherwise would have brought – but to make the pie bigger by creating initiatives to examine practices that may not have in the past received sufficient attention and bringing cases for violations related to those practices. The units have been incredibly successful in accomplishing these goals. Over the last couple of years, the Asset Management Unit has launched a series of innovative initiatives – often in partnership with OCIE – focusing on important regulations like the custody rule and on undisclosed principal transactions and conflicts of interest; identified funds with aberrational returns that engaged in misconduct and investment advisers with deficient compliance programs; and brought cases against boards that did not exercise their responsibilities to determine investment adviser fees or to value their funds’ holdings properly.[1] The Municipal Securities and Public Pensions unit this year brought the first action against a municipal issuer for materially misleading statements made outside of its securities disclosure documents,[2] the first case in which the Commission assessed a financial penalty against a municipal issuer,[3] and helped bring significant cases against individuals, including a City of Miami budget director and several City of Victorville officials.[4] The FCPA Unit has teamed with DOJ to bring significant cases against issuers and individuals this past year, including reaching global settlements with Alcoa for over $380 million,[5] with Weatherford International for over $250 million,[6] and with Hewlett-Packard for over $108 million.[7] The Complex Financial Instruments Unit was incredibly productive in addressing misconduct arising from the financial crisis, bringing CDO and RMBS cases against several prominent financial institutions.[8] The unit has now shifted its attention to the next frontier and I expect it to zero in on the structuring, rating, valuation, sale, and use of other types of complex financial products, such as CMBSs, structured notes, and CDSs, while also preparing to enforce new Dodd-Frank rules like the Volcker Rule. Finally, the Market Abuse Unit has been focused on complex insider trading and market structure cases. Let me spend a few minutes on market structure, since that is an area that has received much attention recently. Market Structure Our markets have been radically transformed over the last five or so years due to the proliferation of sophisticated technological tools and the increased use of high-frequency trading, complex algorithmic trading, and off-exchange trading venues, including so-called “dark pools.” Although other divisions within the Commission handle the policy and rulemaking questions arising out of these developments, Enforcement’s role is to prosecute violations of the law. To ensure fair trading and equal access to information in the securities markets, we have brought significant actions in the past year against exchanges, broker-dealers, and other key market participants relating to failures in controls and the use of manipulative trading strategies. For example, in the last three years, we have pursued a number of cases against national securities exchanges. Most recently, we charged NYSE and two affiliated exchanges with failing to conduct their operations in accordance with Commission-approved exchange rules, which resulted in a $4.5 million penalty.[9] This action comes on the heels of our other recent cases against national exchanges, including charges against NASDAQ for violations in connection with the Facebook IPO[10] and the Chicago Board Options Exchange (CBOE) for breakdowns in its role as a self-regulatory organization, including its failure to oversee compliance with Reg SHO.[11] NASDAQ and CBOE ultimately paid $10 million and $6 million, respectively – the two largest SEC penalties ever levied against exchanges. After many decades of never assessing a single penalty against a securities exchange, we now have had six exchanges collectively pay over $25 million in less than two years. And through these actions, we have sent a strong, unmistakable message that exchanges need to institute appropriate controls and closely monitor trading. Our market structure cases have not been limited to exchanges. A substantial amount of trading—recently reported to be over one-third of all trading—occurs off-exchange, and we are expanding our presence in this realm. Indeed, the Commission has already brought actions against two dark pool operators in recent years[12] and will continue to pursue Reg ATS violations, including the failure to implement safeguards that protect ATS subscribers’ confidential trading information as required by Reg ATS. Considering the volume of trading at these venues, investors must be able to trust that off-exchange trading is fair and reliable. In addition to trading venues like exchanges and dark pools, we also must continue to focus on brokerdealers that route much of the order flow in today’s markets. Rule 15c3-5, known as the “Market Access Rule,” requires brokers-dealers to have reasonably designed controls and supervisory procedures to manage the risks of having market access, including both financial controls to prevent problems like erroneous orders and trades that exceed capital and credit limits, and regulatory controls that ensure compliance with our rules and regulations.[13] Last fall, we brought our first enforcement case under Rule 15c3-5 against Knight Capital related to the firm’s August 2012 trading incident that disrupted the markets. The action included a $12 million penalty and our investigation showed, among other things, that Knight did not have adequate controls for its smart order router.[14] This is an important area for us and you can expect continued scrutiny relating to compliance with the Market Access Rule. We also have been focused on other issues related to high-frequency and automated trading, including potential abuses of order types, net capital rules, and manipulative trading. For example, we have brought cases involving a manipulative trading practice known as “layering,” which involves the use of fictitious orders that a trader intends to cancel before they are executed, to induce others to buy or sell securities at prices that do not represent actual supply and demand. Indeed, the Commission charged the owner of a brokerage firm last month with engaging in layering over a three-year period.[15] As the primary regulator of the securities industry, the SEC remains committed to bringing enforcement actions whenever parties jeopardize the integrity of our markets or otherwise fail to operate within the rules. Through these efforts, we will continue to ensure that our markets remain fair, efficient, and reliable for all investors. Task Forces Over the last year, we also have amplified the division’s focus on other areas of growing concern, beyond the ones covered by the specialized units. We have accomplished this by launching several task forces, which have enabled us to quickly mobilize a core group of attorneys, professionals, and industry experts to concentrate on high-priority areas and share their expertise and promising leads division-wide. For example, we launched the Financial Reporting and Audit Task Force to renew our attention on financial reporting and accounting fraud.[16] The importance of pursuing financial fraud cannot be overstated. Comprehensive, accurate and reliable financial reporting is the bedrock upon which our markets are based because false financial information saps investor confidence and erodes the integrity of the markets. The Task Force’s mandate is to incubate financial reporting cases by finding promising investigations. It brings together an experienced group of attorneys and accountants who are developing state-of-the-art techniques for identifying and uncovering accounting fraud. The team relies on the latest data analytic tools and outside services to identify high-risk companies and potential accounting issues.[17] And it is already off to a great start, having helped generate several promising leads. Meanwhile, we have brought a series of financial reporting cases over the last few months, including significant actions against CVS, Diamond Foods, AgFeed, and Dewey & LeBouf.[18] More such cases will be coming down the pike. In addition to more closely monitoring financial reporting, we also have bolstered our focus on financial reporting “gatekeepers.”[19] In every financial reporting investigation, we evaluate the conduct of the auditors, seeking to determine whether they followed audit procedures and performed their role according to generally accepted auditing standards. We also are more closely monitoring and pursuing misconduct related to microcap securities. Abuses in this area frequently involve entities that use false or misleading marketing campaigns and manipulative trading strategies, largely at the expense of less sophisticated, retail investors. Over time, these abuses have proliferated due to the increased use of the Internet and social media to publicize fraudulent schemes and lure in unsuspecting investors. To stay on top of this, we created a Microcap Fraud Task Force, which is focused on developing proactive initiatives that target executives, gatekeepers and other repeat players who help facilitate these schemes. [20] The Task Force also aims to identify and shut down schemes in their early stages, with tools like trading suspensions and asset freezes. And it has had an immediate impact. We have opened numerous investigations because of their work and brought 15 trading suspensions in recent months. These efforts have enabled us to more quickly halt misconduct and mitigate investor harm, while sending an unmistakable message to the microcap community.[21] We also recently launched a Broker-Dealer Task Force that is focusing on current issues and practices within the broker-dealer community. The group is liaising closely with the broker-dealer program within OCIE, as well as the Division of Trading and Markets, to develop initiatives that can be implemented division-wide. Their early efforts include initiatives relating to anti-money laundering regulations and recidivist brokerage firms that shelter rogue brokers and engage in abusive activities. The Division also is focused on enforcing some of the Commission’s new and upcoming rules. For example, last year we launched the JOBS Act Task Force, a nationwide group dedicated to preparing the Division to enforce the new capital-raising rules under the JOBS Act, including rules related to general solicitation and crowdfunding. The group has created risk-based initiatives to identify parties that are not adhering to the new regulations, including issues related to inadequate efforts to verify accreditation.[22] New Approach to Settlements The changes in the last year have not been limited to substantive areas of focus. One of the first changes implemented after Chair White and I arrived at the SEC last year was to modify the SEC’s longstanding no admit/no deny settlement protocol by requiring admissions in certain types of cases. Our prior practice had been to settle all cases, except those with a guilty plea or criminal conviction, on a no admit/no deny basis. This practice had served the SEC well for many years. When we settle enforcement cases on a no admit/no deny basis, we often are able to get the same – or even higher – penalties than we would have if we litigated and won the case. Such settlements also speed up our ability to reclaim ill-gotten gains and return funds to wronged investors, avoid the delay and uncertainty inherent in trials, and allow us to use our finite resources more efficiently. But there are some cases where the need for accountability and acceptance of responsibility is critical to the success of our program. In such cases, admissions enhance the message and strength of the action, and enable us to achieve a greater measure of public accountability, which, in turn, bolsters the public’s confidence in the safety of our markets. After nearly a year, I am happy to report that the new program is working very well. We have obtained admissions in eight cases under the new approach – with more in the pipeline. And we have obtained them across a broad spectrum of defendants – against firms and individuals; against regulated and unregulated entities; and in scienter-based, as well as non-scienter, controls-based cases. Many originally doubted our ability to implement this new approach. Some expressed concern that we would not be able to obtain admissions because defendants would be overly concerned about collateral consequences. Others wondered whether our new policy would bog down settlements and cause more parties to go to trial. But these dire predictions have not materialized and we have been able to obtain significant admissions in cases where we thought they were appropriate. Now that we have settled a number of cases with admissions, the types of cases where the Division may seek them can be better appreciated. We obtained admissions in the ConvergEx matter, for example, where the defendants were regulated entities and their egregious and fraudulent conduct harmed numerous clients.[23] We obtained admissions from JP Morgan – for conduct related to the so-called “London Whale” trading loss – where the company’s woefully deficient controls created a significant risk to investors.[24] In our action against Philip Falcone and his advisory firm, admissions helped give the public unambiguous information about the defendant’s actions so they would be empowered to make informed decisions about whether to continue investing in companies with which he was involved.[25] In the Scottrade matter, we obtained admissions where the company produced inaccurate blue sheet data over an extended period of time, which impeded the SEC’s ability to investigate misconduct and protect investors.[26] And in Lions Gate, we sent an important message to the market about the perils of misleading investors in the midst of a tender offer battle.[27] The new admissions approach gives us an additional powerful tool to use in appropriate cases and it has undoubtedly strengthened our program. Trials Another area of focus for the Division over the past year has been enhancing our litigation efforts. We have experienced a significant increase in the number of trials this year – in fact, we had more trials in the first half of this fiscal year than we had during all of the last fiscal year. This is hardly a bad development – as Mary Jo has said in the past, trials have lots of benefits, including the public airing and adjudication of the facts. Although it could just be a blip, this uptick in trials means that we must marshal appropriate resources and skills to remain competitive in court against defendants that often have far greater resources at their disposal. And we have been doing just that. We have incredibly talented lawyers at the SEC who I would put up against any defense counsel. We are ensuring that we provide the strongest advocacy possible in every case, preparing relentlessly for any argument that might be raised at trial. This renewed focus does not mean we will win every case – though we have been very successful overall and recently, winning our last five jury trials, including our significant victory last week in the Wyly matter. What it does mean is that defendants know we will not hesitate to go to trial, and that when we are in court, defendants will face skilled, tireless advocates who will present as strong a case as possible on our behalf. Use of Technology We also have been focused on using technology to improve our ability to detect and investigate fraud. With the increased complexity of the markets, and of schemes more generally, as well as the proliferation of big data, we need to better harness technology in order to keep up with wrongdoers. Take insider trading. Over the last five years, we have filed an unprecedented number of insider trading actions against more than 570 individuals and firms. We often have learned of this misconduct through surveillance referrals from FINRA and ORSA. But we also have now developed in-house the Advanced Bluesheet Analysis Program to identify suspicious trading patterns that would suggest relationships among different traders who may be sharing inside information. Identifying these trading relationships allows us to work backwards to find evidence of connections and sources of the inside information. Technology is assisting us in many other areas as well. We developed a program a couple of years ago that identifies aberrant returns in investment funds, which often can signify misconduct. We have brought a number of cases identified through this initiative and continue to expand its application as we receive and process new fund data. Last year, we launched the Center for Quantitative and Risk Analytics, which is helping us develop technologies to analyze trading and other types of data available to us from a wide variety of venues.[28] It is critical that we continue to develop tools that mine these massive data sources for possible violations. This data is a rich source of information for us and we need to take advantage of it. Increased Focus on Compliance Finally, because this is the Compliance Week conference, I thought it would be appropriate to spend a few minutes on compliance programs and compliance officers. I start from the premise that the companies that have done well in avoiding significant regulatory issues typically have prioritized legal and compliance issues, and developed a strong culture of compliance across their business lines and throughout the management chain. This is something I observed firsthand while in private practice and have come to fully appreciate from my perch at the SEC. I have found that you can predict a lot about the likelihood of an enforcement action by asking a few simple questions about the role of the company’s legal and compliance departments in the firm. Are legal and compliance personnel included in critical meetings? Are their views typically sought and followed? Do legal and compliance officers report to the CEO and have significant visibility with the board? Are the legal and compliance departments viewed as an important partner in the business and not simply as support functions or a cost center? Far too often, the answer to these questions is no, and the absence of real legal and compliance involvement in company deliberations can lead to compliance lapses, which, in turn, result in enforcement issues. When I was in private practice, I always could detect a significant difference between companies that prioritized legal and compliance and those that did not. When legal and compliance were not equal partners in the business, and were not consulted as a matter of course, problems were inevitable. I hope to use my current role to further promote a strong, empowered legal and compliance presence at firms, in part by encouraging legal and compliance personnel to engage and become involved when they see an issue that raises a concern. You should not hesitate to provide advice and help remediate when problems arise. And I do not want you to be concerned that by engaging, you will somehow be exposed to liability. As recent SEC staff guidance makes clear, compliance personnel do not become supervisors solely because they provide advice to, or consult with, business line personnel and the staff does not view compliance or legal personnel generally as supervising business personnel.[29] But at the same time, I need to be clear that we have brought – and will continue to bring – actions against legal and compliance officers when appropriate. This typically will occur when the Division believes legal or compliance personnel have affirmatively participated in the misconduct, when they have helped mislead regulators, or when they have clear responsibility to implement compliance programs or policies and wholly failed to carry out that responsibility. A recent case illustrates all three of these situations. Yesterday, the Commission instituted administrative proceedings against the CCO, among others, at what used to be one of the largest independent clearing firms in the country. In the matter, the Division alleged that the firm violated Reg SHO for more than three years and that the CCO not only knew about the firm’s decision to violate the rules, but also affirmatively participated in the violations by, among other things, failing to implement procedures that he was responsible for implementing and that would have brought the firm into compliance, and then concealing those violations from regulators.[30] It also is certainly appropriate to bring actions against compliance officers when they fail to carry out their clearly assigned responsibility to implement necessary policies. For example, we launched the Compliance Program Initiative – a joint effort with OCIE – to identify and bring actions against investment advisers that fail to adopt or implement adequate compliance programs after being notified repeatedly of deficiencies by examination staff.[31] To date, the Commission has brought ten actions as part of this initiative, including charges against compliance personnel when they were clearly responsible for the failure. At the end of the day, though, legal and compliance officers who perform their responsibilities diligently, in good faith, and in compliance with the law are our partners and need not fear enforcement action. In fact, we want to use our enforcement program to support your efforts. Last year, for example, we filed our firstever charge against an individual for misleading and obstructing a compliance officer of an investment adviser. The Commission’s Order was based on factual findings that an assistant portfolio manager had, among other things, attempted to conceal from his firm’s CCO his involvement in more than 600 unauthorized personal trades – many of which involved securities held or acquired by funds that the firm managed.[32] We will look for more cases like this one. Conclusion So you can see that we have been quite busy this past year trying to expand our enforcement footprint. As markets continue to evolve, we must continue to innovate and devise new strategies that enhance our ability to deter wrongdoers, and broaden our reach within the industry. I am confident that this next year will be even better and I hope to return in 2015 to report on another great round of innovations that will help us detect misconduct and bring securities violators to justice. Thanks very much and I look forward to taking your questions. [1] See, e.g., Press Release No. 2013-230, SEC Charges Three Firms With Violating Custody Rule (Oct. 28, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540098359; Press Release No. 2013-250, SEC Announces Charges Against Two-Houston Based Firms for Engaging in Thousands of Undisclosed Principal Transactions (Nov. 26, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540414827; Press Release No. 2012-90, SEC Charges Scotland-Based Firm for Improperly Boosting Hedge Fund Client at Expense of U.S. Fund Investors (May 10, 2012), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1365171489060; Press Release No. 2013-259, SEC Charges London-Based Hedge Fund Adviser and U.S.-Based Holding Company for Internal Control Failures (Dec. 12, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540491613; Press Release No. 2013-226, SEC Sanctions Three Firms Under Compliance Program Initiative (Oct. 23, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540008287; Press Release No. 2013-78, SEC Charges Gatekeepers of Two Mutual Fund Trusts for Inaccurate Disclosures About Decisions on Behalf of Shareholders (May 2, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1365171514096; Press Release No. 2012-259, SEC Charges Eight Mutual Fund Directors for Failure to Properly Oversee Asset Valuation (Dec. 10, 2012), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1365171486708. [2] See Press Release No. 2013-82, SEC Charges City of Harrisburg for Fraudulent Public Statements (May 6, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1365171514194. [3] See Press Release No. 2013-235, SEC Charges Municipal Issuer in Washington’s Wenatchee Valley Region for Misleading Investors (Nov. 5, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540262235. [4] See Press Release No. 2013-130, SEC Charges City of Miami and Former Budget Director with Municipal Bond Offering Fraud (July 19, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370539727618; Press Release No. 2013-75, SEC Charges City of Victorville, Underwriter, and Others with Defrauding Municipal Bond Investors (Apr. 29, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1365171514980. [5] See Press Release No. 2014-3, SEC Charges Alcoa With FCPA Violations (Jan. 9, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540596936. [6] See Press Release No. 2013-252, SEC Charges Weatherford International With FCPA Violations (Nov. 26, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540415694. [7] See Press Release No. 2014-73, SEC Charges Hewlett-Packard With FCPA Violations (Apr. 9, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370541453075. [8] See, e.g., Press Release No. 2011-131, J.P. Morgan to Pay $153.6 Million to Settle SEC Charges of Misleading Investors in CDO Tied to U.S. Housing Market (June 21, 2011), available at http://www.sec.gov/news/press/2011/2011-131.htm; Press Release No. 2013-148, SEC Charges Bank of America With Fraud in RMBS Offering (Aug. 6, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370539751924. [9] See Press Release No. 2014-87, SEC Charges NYSE, NYSE ARCA, and NYSE MKT for Repeated Failures to Operate in Accordance With Exchange Rules (May 1, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370541706507. [10] See Press Release No. 2013-95, SEC Charges NASDAQ for Failures During Facebook IPO (May 29, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1365171575032. [11] See Press Release No. 2013-107, SEC Charges CBOE for Regulatory Failures (June 11, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1365171575348. [12] See Press Release No. 2012-204, SEC Charges Boston-Based Dark Pool Operator for Failing to Protect Confidential Information (Oct. 3, 2012), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1365171485204; Press Release No. 2011-220, Alternative Trading System Agrees to Settle Charges That It Failed to Disclose Trading by an Affiliate (Oct. 24, 2011), available at http://www.sec.gov/news/press/2011/2011-220.htm. [13] See 17 C.F.R. § 240.15c3-5. [14] See Press Release No. 2013-222, SEC Charges Knight Capital With Violations of Market Access Rule (Oct. 16, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370539879795. [15] See Press Release No. 2014-67, SEC Charges Owner of N.J.-Based Brokerage Firm With Manipulative Trading (Apr. 4, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370541406190. [16] See Press Release No. 2013-121, SEC Announces Enforcement Initiatives to Combat Financial Reporting and Microcap Fraud and Enhance Risk Analysis (July 2, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1365171624975. [17] See SEC Spotlight on the Financial Reporting and Audit Task Force, available at http://www.sec.gov/spotlight/finreporting-audittaskforce.shtml. [18] See Press Release No. 2014-69, SEC Charges CVS With Misleading Investors and Committing Accounting Violations (Apr. 8, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370541437806; Press Release No. 2014-4, SEC Charges Diamond Foods and Two Former Executives Following Accounting Scheme to Boost Earnings Growth (Jan. 9, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540598296; Press Release No. 2014-47, SEC Charges Animal Feed Company and Top Executives in China and U.S. With Accounting Fraud (Mar. 11, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370541102314; Press Release No. 2014-45, SEC Charges Five Executives and Finance Professionals Behind Fraudulent Bond Offering by International Law Firm (Mar. 6, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540889964. [19] See Press Release No. 2013-207, SEC Charges Three Auditors in Continuing Crackdown on Violations or Failures By Gatekeepers (Sept. 30, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370539850572. [20] See Press Release No. 2013-121, SEC Announces Enforcement Initiatives to Combat Financial Reporting and Microcap Fraud and Enhance Risk Analysis (July 2, 2013), available at https://www.sec.gov/News/PressRelease/Detail/PressRelease/1365171624975. [21]See SEC Spotlight on Microcap Fraud, available at http://www.sec.gov/spotlight/microcap-fraud.shtml. [22] See SEC Spotlight on Jumpstart Our Business Startups (JOBS) Act, available at http://www.sec.gov/spotlight/jobs-act.shtml. [23] See Press Release No. 2013-266, SEC Charges ConvergEx Subsidiaries With Fraud for Deceiving Customers About Commissions (Dec. 18, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540521484. [24] See Press Release No. 2013-187, JPMorgan Chase Agrees to Pay $200 Million and Admits Wrongdoing to Settle SEC Charges (Sep. 19, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370539819965. [25] See Press Release No. 2013-159, Philip Falcone and Harbinger Capital Agree to Settlement (Aug. 19, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370539780222. [26] See Press Release No. 2014-17, Scottrade Agrees to Pay $2.5 Million and Admits Providing Flawed ‘Blue Sheet’ Trading Data (Jan. 29, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540696906. [27] See Press Release No. 2014-51, SEC Charges Lions Gate With Disclosure Failures While Preventing Hostile Takeover (Mar. 13, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370541123111. [28] See Press Release No. 2013-121, SEC Announces Enforcement Initiatives to Combat Financial Reporting and Microcap Fraud and Enhance Risk Analysis (July 2, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1365171624975. [29] See Frequently Asked Questions about Liability of Compliance and Legal Personnel at Broker-Dealers under Sections 15(b)(4) and 15(b)(6) of the Exchange Act (Sept. 30, 2013), available at http://www.sec.gov/divisions/marketreg/faq-cco-supervision-093013.htm. [30] See Press Release No. 2014-101, SEC Announces Charges Against Four Former Officials at Clearing Firm Penson Financial Services for Regulation SHO Violations (May 19, 2014), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370541860014. [31] See Press Release No. 2013-226, SEC Sanctions Three Firms Under Compliance Program Initiative (Oct. 23, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370540008287. [32] See Press Release No. 2013-165, SEC Sanctions Colorado-Based Portfolio Manager for Forging Documents and Misleading Chief Compliance Officer (Aug. 27, 2013), available at http://www.sec.gov/News/PressRelease/Detail/PressRelease/1370539791420. Last modified: May 21, 2014