Operating Systems Security - Chapter 2
advertisement

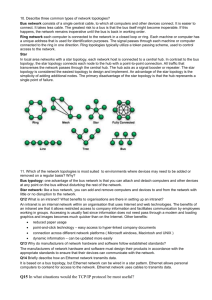
Prof. Michael P. Harris, CCNA CCAI ITNW 1454 – Implementing & Supporting Servers Chapter 1 Logical and Physical Network Topologies Implementing & Supporting Servers - Chapter 1 Logical and Physical Network Topologies Chapter Overview In this chapter, we will discuss the purpose for networking computers and the differences between local area and wide area networks. We also examined the various topologies encountered in network environments. Here are some key points to remember. Learning Objectives Objective 1.1: Recognize the following logical or physical network topologies given a schematic diagram or description: Bus Ring Star (hierarchical) Mesh Wireless Objective 4.10: Given a troubleshooting scenario involving a network with a particular physical topology (i.e., bus, star, ring, mesh, and wireless) —including a network diagram; identify the network area affected and the cause of the problem. Lecture Notes Understanding Network Structure Networking is the process of connecting together two or more devices, such as two computers or a computer and a printer, so that they can share resources. The structure of a network is typically defined by the size of the area it covers. The two most common terms used in describing network structures are local area network (LAN) and wide area network (WAN). LANs is generally limited to a specific geographic area. WANs tie together Local Area Networks. LANs are categorized as peer-to-peer or client-server based. In a peer-to-peer network, all computers (hosts) are considered equal. In a client-server network, security and user access is controlled at the server level. Topologies Bus A bus topology uses a single length of cable (usually coax) to connect the nodes (hosts) together in a daisy-chain fashion. This network requires termination at each end to eliminate signal bounce (reflection). Bus networks are not fault tolerant; a single break in Jerry K. Ainsworth, Kristine A. Kriegel, SYSTEM ADMINISTRATION EMCParadigm ©2004 Page 1 of 3 ISBN: 0-7638-1972-7 Prof. Michael P. Harris, CCNA CCAI ITNW 1454 – Implementing & Supporting Servers Chapter 1 Logical and Physical Network Topologies the cable can bring down the entire network. A logical bus, may not “look” like a physical bus network, but it will act like one. Ring In a ring topology, a cable connects each computer (host) to the next in a continuous loop, or ring. Data travels around the ring, in one direction only, from one computer to the next. Since each computer is wired directly to two others, there are no “ends” on the ring topology requiring termination. Token passing is one common method used to regulate data transmission on a ring network —a token is just a special packet that gives permission to transmit over the network. Since each node (host) is involved in the passing process and maintains the ability to regenerate the token, token passing makes the ring configuration an active topology. A break in the ring or a malfunctioning node can disable a segment or an entire network. These networks tend to get slower as more nodes are added. Ring networks do not generally use a pure ring topology. Instead, they are typically wired in a physical star (star-wired ring) configuration. Star A star topology is commonly used for new network installations. Nodes (hosts) in a star topology network connect to a hub, switch or multistation access unit (MAU). They typically use unshielded twisted pair (UTP) cable. Star topologies are considered fault tolerant, because the failure of a cable or a workstation (host) will not affect the rest of the network. However, the hub, switch, or MAU can be a single point of failure. Mesh In a mesh topology, each computer (host) may be connected directly to some, most, or even all other computer (host) in the network. The redundant/backup connections are used when critical information must be available without interruption (like the Internet). Mesh networks can be quite complex to install and manage, but they are highly fault tolerant. In a full-Mesh network; for every node on the network (n), you will have n(n-1)/2 connections. Wireless Wireless networks usually rely on either radio frequency(RF) or infrared (IR) channels, to connect directly to each other (ad hoc mode) or to access points (APs) (infrastructure mode). Wireless communications devices connect, or network, using either ad hoc mode (point-to-point networking) or infrastructure mode (multipoint networking). Devices such as portable computers, portable digital assistants (PDAs), or smart phones use ad hoc mode by connecting directly to each other without using or needing an AP. In ad hoc mode devices (hosts) send out radio waves that can be intercepted by other wireless devices whenever they move within a certain distance range of each other. The network is created as needed and nodes (hosts) can be moved from this network to another simply by changing their location and proximity to another wireless device (host). Jerry K. Ainsworth, Kristine A. Kriegel, SYSTEM ADMINISTRATION EMCParadigm ©2004 Page 2 of 3 ISBN: 0-7638-1972-7 Prof. Michael P. Harris, CCNA CCAI ITNW 1454 – Implementing & Supporting Servers Chapter 1 Logical and Physical Network Topologies Nodes (hosts) use infrastructure mode, or multipoint networking when connecting to a fixed network. The wireless nodes (host) connect to a wireless bridge functioning as an access point (AP). The AP is generally wired to the network backbone and serves essentially the same purpose as a hub on a wired network. Devices must be within the operating range of the wireless AP in order to access the network. Troubleshooting Problems with Shared Resources Begin by browsing through the shared resources within Network Neighborhood or My Network Places. If you can see the resource (share) but it does not allow you access, check the permissions on the share. If you cannot see the shared resource on the network, try these steps: Check that the computer that hosts the resource is turned on. Check the resource on the host computer to ensure it is still shared. If both of these things check out, determine if you can see other computers on the network. Since a physical connection may be causing the problem, you must determine if the problem is at your computer, the computer hosting the shared resource, or the entire network. If you can see other computers on the network and access their shared resources, check the connectivity at the computer hosting the share. If you cannot see any other computer on the network, check the connection on the computer from which you are trying to access the shared resource. Jerry K. Ainsworth, Kristine A. Kriegel, SYSTEM ADMINISTRATION EMCParadigm ©2004 Page 3 of 3 ISBN: 0-7638-1972-7