Homework 3 Solution

EE 5304/EETS7304 Internet Protocols March 8, 2006
Homework #3 Solution
Problem 1. (IP fragmentation)
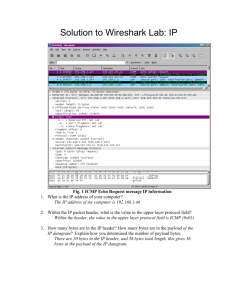
Suppose an IP datagram containing 256 bytes of data is divided into two fragments, each containing 128 bytes of data. Fill in the table for the header fields for the two fragments.
Header field
Header length
Total length
Identification
Datagram Fragment 1
5
276
3
Fragment 2
MF
Fragment offset
0
0
An IP datagram of 256 bytes of data is divided into two fragments, each containing 128 bytes of data. The header length is 20 bytes but measured in units of 4 bytes. Total length is the sum of header and data bytes. Identification number is the same in all fragments to indicate that they belong to the same original datagram. MF flag is always 1 for all fragments except for the last fragment. Fragment offset indicates where the fragment’s data belongs in the original datagram measured in units of 8 bytes.
Header field
Header length
Datagram Fragment 1
5 5
Fragment 2
5
Total length
Identification
MF
Fragment offset
276
3
0
0
148
3
1
0
148
3
0
16
Problem 2. (IP fragmentation)
When the destination router receives an IP fragment, it keeps the fragment in a buffer until the other fragments are 1 received. Does the router know how much buffer space to allocate for the reassembly of the IP datagram?
Usually the destination host does not know the required amount of buffers when an IP fragment arrives, unless it is the last fragment (identified by MF=0).
Problem 4. (IP routers)
Give at least three reasons why an IP router might discard an IP datagram (packet).
Some possible reasons for discarding an IP datagram: checksum error; time-to-live field expires; invalid protocol field value; destination host is unknown or unreachable; datagram cannot be fragmented; buffer overflow.
1
EE 5304/EETS7304 Internet Protocols March 8, 2006
Problem 5. (IP fragmentation)
Suppose that the destination router receives 3 out of 4 fragments, but the reassembly timer expires and the router discards these fragments. Some time later, the last fourth fragment arrives. How does the router treat this fragment?
When the reassembly timer expires, the router will discard the 3 fragments received so far. When the last fourth fragment arrives, the router will treat the fragment as a new datagram and start another reassembly timer. When this timer expires later, this fourth fragment will be discarded also.
Problem 6. (IP header)
Why is the IP header checksum recalculated at every router?
The IP header checksum is recalculated at every router because some of the IP header fields will change, such as the TTL and (if fragmentation occurs) total length, MF flag, and fragment offset.
Problem 7. (IP routing)
(a) What is the source routing option in IP? (b) What is the difference between strict and loose source routing in IP?
(a) In source routing, the sender chooses the route and puts the route in the packet header.
This might be handy for testing specific routes or implementing routing policies (e.g., avoiding certain routes).
(b) Strict source routing means that the IP packet is constrained to follow the exact route specified by a list of routers contained in the IP header (source route option). Loose source routing means that the IP packet is constrained to follow a route that includes the list of routers (maybe including other routers) in the IP header.
Problem 8. (ICMP)
(a) Suppose that a ping (ICMP echo request) fails to get a response (ICMP echo reply) from the pinged host. Does it mean that the host is down? (b) Some utilities send a series of pings and take the average of the response times as a measure of the typical roundtrip delay between the two hosts. Is this a reliable measurement?
(a) No, the pinged host may not have received the ICMP echo request, due to congestion or a problem along the way. Also, some organizations have a policy of blocking ICMP messages such as pings. It is also possible that the pinged host returned an ICMP echo reply that was lost in the network. (b) Pings are always samples of the current roundtrip delay, and a series of pings will also capture the current roundtrip delay. The average of a series of pings will be a "snapshot" measure of the current roundtrip delay, but this could be quite different from the typical roundtrip delay ("typical" over a long period of time).
Problem 9. (ICMP)
Consider a NAT box that forwards an outgoing data packet from a private network host.
The data packet results in an ICMP Destination Unreachable message returned back to
2
EE 5304/EETS7304 Internet Protocols March 8, 2006 the private host. (a) Describe the contents of the Destination Unreachable message including message headers. (b) Suppose the private network host has private address P and public IP address G. Which addresses in the Destination Unreachable message need to be changed by the NAT box? (c) Which three checksums in the Destination
Unreachable message need to be recomputed by the NAT box? a.
An ICMP Destination Unreachable message consists of an IP packet header, followed by the ICMP message header, and then the original data packet header and first 8 bytes of data.
b. The address in the outer IP packet header must be changed from G to P. Also, the original data packet inside the ICMP message will be carrying address G, so that address must also be changed from G to P. (c) Checksums must be changed because the addresses have been changed. First, the checksum in the outer IP packet header must be recomputed. Second, the checksum in the original data packet header must be changed.
Third, the checksum in the ICMP message header must be changed (because the checksum covers the ICMP message).
Problem 10. (subnetting)
Consider a class B address with a subnet mask of 255.255.192.0. How many subnets are possible?
The first byte 255 and second byte 255 correspond to the class B prefix (first 2 address bytes). The third byte 192 is 11000000 in binary, which means two bits in the third address byte are used to identify subnets. With two bits, it is possible to identify 4 subnets.
3