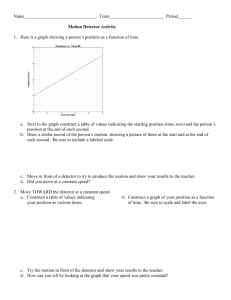
Fast Eliminate-Highest-Error Algorithms for Bit
advertisement

Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
A Family of Likelihood Ascent Search Detectors for CDMA
Multiuser Detection1
Yi Sun
Department of Electrical Engineering
The City College of City University of New York
New York, NY 10031
Phone: (212)650-6621
Fax: (212)650-8249
E-mail: yisun@ee-mail.engr.ccny.cuny.edu
Abstract – Although achieving global maximum likelihood (GML) detection and thus
achieving global minimum error probability, the optimum detector is impractical because
its computational complexity grows exponentially with the increasing number of users. In
this paper, we propose a family of likelihood ascent search (LAS) detectors that achieve
some subset maximum likelihood (SML) detection whereas their expected per-bit
computational complexity is linear in the number of users. It is shown that when only a
subset of hypotheses are allowed to test, the optimum detection is to select the hypothesis
that achieves the maximum likelihood in this subset of hypotheses. A generalized search
rule is proposed for the family of LAS detectors. The LAS detectors monotonically increase
likelihood at every search step, and thus monotonically decrease error probability and
converge with probability one to a fixe point in a finite number of steps. It is proved that
the thresholds set up in the LAS detectors are necessary and sufficient for monotonic
likelihood ascent with probability one. The properties of the fixed points and their
observation regions are studied. The fewer are the bits allowed to be flipped at each step,
then the less the fixed points are, the smaller the fixed regions are, the slower a LAS
detector converges, and the smaller the error probability is. Among the LAS detectors, the
wide-sense sequential LAS (WSLAS) detectors are shown to converge to local maximum
likelihood (LML) points with probability one, and thus each achieves a local minimum
error probability. As side products, some properties of the parallel interference
cancellation (PIC) detector are also obtained. Simulations are carried out and verify
analytical results.
Index Terms – multiaccess communication, maximum likelihood, fixed point, multipath.
1
Part of the material in this paper was presented at the 5th Conference on Information Systems Analysis and
Synthesis / 3rd Conference on Systemics, Cybernetics and Informatics (ISAS´99/SCI'99), Orlando, Florida, July 31 to
August 4, 1999
1
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
I. INTRODUCTION
The multiuser detection of CDMA signals has received considerable attention for over a decade.
A textbook on multiuser detection was written by Verdú [1]. Tutorial references were presented
by Verdú [2], Duel-Hallen et al. [3], and Moshavi [4] with extensive reference lists therein.
Verdú [5] [6] showed that an optimal maximum likelihood multiuser detector can achieve
significant performance improvement over the conventional detector. However, its computational
complexity grows exponentially with the number of active users. Unless the signal correlations
have a special structure as was found for nonpositive correlations by Ulukus and Yates [7], the
optimum detector is impractical when the number of active users is large.
To develop low-complexity suboptimal multiuser detectors, suboptimal tree-type maximumlikelihood sequence detectors were proposed for multiuser systems. Xie, Tushforth, and Short [8]
considered the sequential detector, and later on considered was breadth-first algorithms [9]. Wei
and Schlegel [10] used the M-algorithm tree-search scheme preceded with a decorrelating noise
whitening filter. Wei et al. [11] showed that combined with a decorrelating noise whitening
matched filter, the M- and T- algorithms can provide near optimum performance at a low level of
complexity compared with the optimum detector.
To develop linear suboptimum detector, Lupas and Verdú exploited a linear decorrelating
detector [12] [13], which was initially proposed in [14]. The decorrelating detector has
computational complexity significantly lower than that of the optimum detector while provides
substantial performance gain over the conventional detector. The most significant advantage of
the decorrelating detector is that it achieves optimal performance of near-far resistance. However,
its performance is far from the optimality due to the noise enhancement of the matrix inverse.
Xie, Short and Rushforth [15] applied the minimum mean-square error (MMSE) filter which
compromises both multiple access inference suppression and background noise suppression. The
structure constraint that the detector is linear is too severe.
Viterbi [16] and Yoon, Kohno, and Imai [17] applied the idea of the successive interference
cancellation (SIC). The SIC detector takes a serial approach to canceling interference. DuelHallen [18] [19] used the decorrelating decision-feedback detector (DDFD). Klein, Kaleh, and
Baier [20] proposed the zero-forcing decision-feedback detector. The DDFD performs linear
preprocessing followed by a form of SIC detection. Varanasi [21] developed a systematic
approach to the design of decision feedback detector.
2
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
The likelihood ascent search (LAS) detectors proposed in this paper are mostly comparable with
the parallel interference cancellation (PIC) detector. There has been considerable research on the
multistage PIC detector since Varanasi and Aazhang [22] [23] proposed the structure of it. A
basic one stage PIC structure was proposed by Kohno, Imai and Hatori [24]. In the PIC detector,
the multiple access inference is estimated based on the bit estimate from previous stage and is
subtracted from received signal in parallel. This process can be repeated for multiple stages. It
was observed [22] that the performance of the PIC detector depends heavily on the initial data
estimates. The decorrelating detector was proposed [23] for use as the first stage. It was indicated
in [23] that it is the effect of interference doubling from users that are incorrectly detected at the
penultimate stage, that ultimately limits the performance of the multistage detector. Verdú
demonstrated [1] for a two-user channel that a limit cycle exists in this process of the PIC
detector. A number of variations on the PIC detector have been proposed for improved
performance. Patel and Holtzman [25] indicated that soft-decision PIC is found to be superior in
a well power-controlled channel. Giallorenzi and Wilson [26] proposed the use of the already
detected bits at the output of the current stage to improve detection of the remaining bits in the
same stage. Moshavi [27] considered the linear combination of the soft-decision outputs of
different stages of the PIC detector. Divsalar, Simon, and Raphaeli [28] proposed a partial
multiple access interference cancellation at each stage with the amount of cancellation increasing
for each successive stage. Other studies on the PIC detector can be found in literature such as
Hegarty and Vojcic [29], Gray, Kocic, and Brady [30], Ghazi-Moghadam, Nelson, and Kaveh
[31], Shi, Du, and Driessen [32], Buehrer and Woener [33], Zhang and Brady [34], and Beuhrer
and Nicoloso [35].
Although there have been many studies on the PIC detector in literature, there were drawbacks
in the development of the PIC detector and of the PIC detector itself. These drawbacks can be
more easily seen in the framework of the LAS detectors proposed in this paper. The PIC detector
is fundamentally a search detector. Given one demodulated vector at one stage, the PIC detector
searches out another vector at next stage. The PIC detector was developed mainly based on the
intuition motivated by interference cancellation in parallel rather than aiming at guaranteed
likelihood ascent stage by stage. There is no indication about whether performance is improved
at each stage, probably partly due to the lack of an efficient method for the performance
3
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
evaluation at every stage when the PIC detectors were developed. Nevertheless, it is the
motivation to cancel all interference in parallel simultaneously that yields a greedy and
malfunctioned PIC detector. Specifically, the size of search step in the PIC detector is too large,
larger than the necessary size to guarantee the likelihood ascent at every step with probability
one. Thus, the PIC detector converges to a limit cycle and instability occurs with a nonzero
probability. Once a PIC detector converges to a limit cycle, likelihood descent is inevitable. The
computation time at stages where likelihood does not increase is wasted. In contrast, the family
of the LAS detectors proposed in this paper is developed by aiming at guaranteed likelihood
ascent step by step, thus converging to a fixed point in a finite number of search steps with
probability one.
Among the large number of existing CDMA multiuser detectors, except the optimum detector
that achieves the global maximum likelihood detection and thus achieves global minimum error
probability, none of others aims at and is known to achieve a local maximum likelihood (LML)
detection so as to achieve a local minimum error probability. In this sense, none of the
suboptimal detectors is really suboptimal.
The impracticability of the optimum detection is essentially due to the impracticability of
carrying out a test of all hypotheses. To seek suboptimal solution under certain constraint of
computational complexity, first we need to know the optimal decision if only a subset of
hypotheses are allowed to be tested. Second, we need to know how to design a better subset of
hypotheses. In this paper, it is shown that the optimum decision of a subset hypothesis test is to
select the hypothesis that achieves the maximum likelihood in the subset of hypotheses. Then
presented is a family of likelihood ascent search (LAS) detectors. The LAS detectors achieve the
maximum likelihood detection of some subset hypothesis test. Among them, the wide-sense
sequential LAS detectors achieve LML detection and thus achieve local minimum error
probabilities. All the LAS detectors are shown to have per-bit complexity linear in the number of
users. The properties of the LAS detectors are mainly attributed to a low computationally
complex method for evaluation of likelihood change at every step.
A partial list of notations and abbreviations used in this paper is given below.
A
Diagonal matrix of user energy
Ak
Signal amplitude of the kth user
4
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
CPIC(r)
Set of limit cycle points of the PIC detector with observation r
b
Vector of k bits
b(t)
Vector of a LAS detector at step t
b
Detector or vector detected by detector
b(r)
Fixed point or detected vector by detector with observation r
bf
Fixed point of a LAS detector
ej
jth coordinate vector
f(r | b)
Metric function of b with observation r
g(t)
Wb(t)
h(t)
Negative gradient of metric at step t
K
Number of users
L(t)
Index set of bits that are updated at step t
L(t)
Index set of bits that are updated at step t by a LAS detector
M
Processing gain (number of chips per bit)
n
White Gaussian noise vector
N
Expected total number of additions per demodulated bit
N(b)
Neighborhood of b
Pc(b)
Correct detection probability of b
Pe(b)
Error probability of b
q
Ar
r
Sufficient statistics of b
R
Crosscorrelation matrix of users’ signature waveforms
R
A partition region of observation space of index
S
Signature waveform matrix
t
Search step
t kf
Search step that a LAS detector terminates flip of the kth bit
tf
Search step that a LAS detector reaches a fixed point
t f
Search step that a LAS detector reaches a fixed point
tf
Expected total number of search steps
9/6/99
5
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
tk(t)
Threshold of the kth bit at step t
t k (t )
Threshold of the kth bit of a LAS detector at step t
~t
k
Minimum threshold of the kth bit of a LAS detector after termination of bit flip
VLML(b)
Observation region of LML point b
V(b)
Observation region of fixed point b of a search detector
W
ARA
z
Gaussian noise vector with mean zero and covariance matrix 2R
Z(b)
Decision region of b in R
b(t)
b(t + 1) b(t)
f(t)
f[b(t + 1)] f[b(t)]
Detector
Special set of crosscorrelation matrices of signature waveforms
(r | b)
Likelihood function of b with observation r
Subset of hypotheses of index
(r)
Limit set of search detector with observation r
LML(r)
Set of LML points with observation r
(r)
Set of fixed points of search detector with observation r
GLAS
Generalized likelihood ascent search
GML
Global maximum likelihood – optimum detector
ISML
Identical subset maximum likelihood
LAS
Likelihood ascent search
LML
Local maximum likelihood
PLAS
Parallel likelihood ascent search
SLAS
Sequential likelihood ascent search
SML
Subset maximum likelihood
USML
Uniform random subset maximum likelihood
WPLAS
Wide-sense parallel likelihood ascent search
WSLAS
Wide-sense sequential likelihood ascent search
6
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
The rest of the paper is organized as follows. In Section II, the subset hypothesis test is
discussed. In Section III, preliminary properties of the search detectors are presented. In Section
IV, the generalized LAS detector is presented and its properties are analyzed. In Section V, the
wide-sense sequential LAS detectors and the parallel LAS detectors are studied. Section VI
addresses the observation regions of fixed points. Simulation results are demonstrated in Section
VII. Conclusions are made in Section VIII and some proofs are included in the Appendix.
II. SUBSET HYPOTHESIS TEST
A. Received baseband CDMA signal
In contrast to the conventional CDMA system where a bank of matched filters is applied to the
received continuous-time signal, in this paper we consider the direct sampling of the received
continuous-time signal to obtain sufficient statistics.
Consider a K-user CDMA system. The kth user transmits baseband signal
x k (t )
A s
i
k
k
(t iTb )bk (i ) .
(1)
Ak is the amplitude of the kth user’s signal. Ak2 is referred to as the energy per bit. Throughout
this paper, we assume that Ak > 0 for all k and Ak is time-invariant. sk(t) is the signature waveform
of duration Tb, which is normalized so as to have unit energy. The chip period of sk(t) is denoted
by Tc. bk (i ) {1, 1} is the transmitted bit of period Tb. M Tb/Tc is the processing gain. xk(t)
has bandwidth approximately equal to chip rate 1/Tc.
Consider the following baseband multipath fading channel model for the kth user,
dk
y k (t ) kj (t ) x k (t t k jk ) nk (t ) .
(2)
j 1
In (2), dk is the number of paths. kj(t) is the fading coefficient of the jth path, of which the
magnitude is Rayleigh-distributed and the phase is uniformly distributed. tk is the kth user’s
reference time. nk(t) is additive white Gaussian noise. Without loss of generality, we assume that
tk + jk 0 and max = max (tk + jk) < Tb/2. Assume further that the fading is slow so that the
signal part in y(t) has bandwidth equal to the chip rate 1/Tc. For the up-link transmission, to
obtain the sufficient statistics the received signal is sampled at the chip rate at the receiver.
7
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Assume that the fading coefficients are time-invariant within one bit period. In the Appendix, the
received signal is shown to be rewritten in matrix form as (here t denotes the bit period),
y(t ) C(0) (t )Ab (t ) C(1) (t )Ab (t 1) n(t )
(3)
where y(t) CM1, C(0)(t), C(1)(t) CMK and A = diag(A1, …, AK). b(t), b(t 1) {1, 1}K are
vectors transmitted at the tth and (t 1)th bit periods, respectively. n(t) CM1 is a Gaussian
random vector with zero mean and covariance matrix 2I with 2 equal to the power of n(t)
within the frequency band of bandwidth 1/Tc (we assume that a baseband filter of bandwidth 1/Tc
is applied in front of the sampler to limit the noise power). The signal model (3) is applicable to
multicarrier signals in the environment of multipath channel delays such as OFDM signals with
intersymbol and interchannel interference [37].
Consider an ideal bit-synchronous CDMA system where radio channels for all users are ideal
memoryless Gaussian and all users transmit bits synchronously. Let dk = 1, kj(t) = 1, jk = 0, tk =
0. After omission of time index, a one-shot formulation is obtained
y = SAb + n.
(4)
In (4), all variables are real. In this ideal model, S is the signature matrix of K users. Its lkth
element is Slk = sk(lTc), the lth sample (or the value of the lth chip) of the kth user’s signature
waveform. The transpose of the signature matrix ST is equivalent to a matched-filter bank. By
applying ST to the data of (4), the output of the matched-filter bank is obtained,
r = STy = RAb + z
(5)
where R = STS is the crosscorrelation matrix of signatures with unit diagonal elements Rii = 1, z
= STn is a Gaussian random vector with zero mean and covariance matrix 2R.
In the Appendix, we show that for a data burst of N transmitted vectors b(t) for t = 0, …, N 1,
the asynchronous, multipath-fading CDMA signal (3) also leads to the formulation of (4) and (5)
with the increased dimensions of signal space.
Since the bit-asynchronous multi-path fading channel model (3) with the transmission of a
finite-length data burst is equivalent to the ideal bit-synchronous model (4), the focus of this
paper is on the multiple access detection of the bit-synchronous Gaussian channel. All results are
applicable to the bit-asynchronous multi-path fading channels with increased computational
complexity.
8
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
B. Multiple hypothesis test
Throughout this paper, assume that all users independently transmit bits 1 and 1 with equal
probability. From (4), a likelihood function of b {1, 1}K with observation y is,
( y | b)
|| SAb y || 2
1
.
exp
2
(2 ) K / 2
2
(6)
From (5), a likelihood function equivalent to (6) can be written as
(r | b)
(RAb r)T R 1 (RAb r)
.
exp
(2 ) K / 2 | R |1/ 2
2 2
1
(7)
In (7), if the inverse of R does not exist, R1 denotes its pseudo-inverse and |R| is the product of
nonzero eigenvalues of R. Either (y | b) or (r | b) can be used in our discussion and both y and
r are sufficient statistics. The noise power ratio of y to r is M/K. When M > K, this ratio is greater
than one. In what follows, the statistic r K and likelihood function (7) are used.
Consider 2K hypotheses:
b {1, 1}K.
Hb: r = RAb + z,
(8)
A 2K-hypothesis test is carried out based on observation r and a decision is made on transmitted
vector b. A decision rule of the 2K-hypothesis test divides the observation space K into 2K
decision regions Z(b), b {1, 1}K. If r Z(b), it is decided to say that b was transmitted. Since
all vectors are equiprobable, the error probability of the decision is
Pe
1
2K
(r | a)dr .
(9)
b{1,1}K a b ,a{1,1}K Z ( b )
It is well-known [38] that the minimization of the error probability leads to the optimum detector
that selects the hypothesis bGML maximizing the likelihood function, i.e.
b GML arg max K (r | b) , r K.
(10)
b{ 1,1}
The error probability of the optimum detector is
Pe (b GML ) 1 Pc (b GML ) 1
1
2K
K
max (r | b)dr
b{1,1}K
(11)
where Pc(bGML) is the probability of correct detection of the optimum detector.
From (7), a metric is defined by
9
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
1
f (r | b) (RAb r )T R 1 (RAb r )
2
1
1
b T Wb q T b r T R 1r
2
2
(12)
where W = ARA and q = Ar. Since Rkk = 1, Wkk = Ak2 for k.
Observation 1: For a, b {1, 1}K, iff (r | a) < (r | b), then f(r | a) > f(r | b).
Observation 1 follows the fact that ex is a monotonic function of x. f(r | b) and (r | b) are said
to be equivalent in the sense of Observation 1. Through this paper, when one is used, the other is
always meant to be usable. It follows from Observation 1 that (10) can be written
b GML arg min
b{ 1,1}K
f (r | b) , r K.
(13)
Obviously, to obtain the optimum solution bGML requires the comparison of 2K metric values f(r
| b), b {1, 1}K. Although a tree-search trellis scheme like the Viterbi algorithm can
sometimes achieve efficient comparison of the 2K metric values, the computational complexity
per demodulated bit for the optimum detection still grows exponentially with K, the number of
users. The optimum detector is impractical.
C. Subset hypothesis test
Suppose that a constraint on computational complexity allows only to carry out a test on a
subset of the 2K hypotheses in (8). The question that first arises is what the optimum detection in
terms of minimization of error probability is.
Definition 1: Let the observation space K be partitioned into disjointed regions R for U
where U is a finite index set. Each region R is uniquely assigned a subset {1, 1}K. For
each r R, a subset of hypotheses is tested,
Hb: r = RAb + z,
b .
(14)
This defines a subset hypothesis test.
Observation 2: There are totally at most 22 1 possible regions R.
K
If R = K and = {1, 1}K, the subset hypothesis test becomes the ordinary 2K -hypothesis
test in (8).
10
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
In a different region R, tested can be a different subset of hypotheses out of 2K hypotheses. A
decision rule divides region R into || disjoint decision regions Z(b) R for b . If r
Z(b), it is decided to say that b was transmitted. The decision never says that a vector b
{1, 1}K \ was transmitted. The error probability of this decision is
1
Pe K
U 2
1
(r | a)dr 2 (r | a)dr
K
b a
Z ( b )
b a b ,a
Z ( b )
(15)
A decision region Z(b) can be empty. The error denoted by the first term inside the parenthesis
of (15) is independent of the decision rule because it can be written as
Pe ( )
1
2K
(r | a)dr .
(16)
a R
The probability of correct detection complementary to Pe in (16) is
Pc
1
2K
(r | b)dr .
(17)
U b Z ( b )
If = {1, 1}K for all U, the subset hypothesis test becomes the ordinary hypothesis test and
(15) becomes (9).
Theorem 1: For the subset hypothesis test, the optimum decision that minimizes the error
probability is to select the hypothesis bSML that achieves the maximum likelihood over ,
b SML arg max (r | b) , r R, U,
b
(18)
and the error probability is
Pe (b SML ) 1
1
2K
(r | b)dr .
max
U R
b
(19)
Proof: The error probability Pe( ) of (16) over the region R depends only on the subset of
hypotheses for that are not allowed to be tested, and is independent of the decision rule. When
is given, Pe( ) is fixed. The total error probability varies only with the decision for the
hypotheses allowed to be tested as shown by the second term of (15). Since the partitioned
observation regions are disjointed, the minimization of error probability is to minimize the
decision error (given by the second summation term in parenthesis of (15)) over each observation
11
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
region R. This error over R is || times the error probability for the decision rule of an ordinary
||-hypothesis test for a transmitter that equiprobably transmits b . The minimization of
error probability for this ||-hypothesis test is well-known to select the hypothesis bSML that
maximizes the likelihood function over . Hence, (18) minimizes the total error probability of
(15) for the subset hypothesis test in Definition 1. By placing the maximum likelihood function
in (17), we obtain
Pc (b SML )
1
2K
U b Z ( b )
max (r | a)dr
a
which yields (19).
(20)
(Q.E.D.)
Definition 2: A detector achieving bSML in Theorem 1 is said to be a subset maximum
likelihood (SML) detector.
Observation 3: The optimum detector is an SML detector when = {1, 1}K for U.
From (19), it is easy to see that the error probability of an SML detector is determined by the
hypothesis of maximum likelihood in each subset of hypotheses.
Corollary 1: The probability of correct detection of the SML detector is
Pc (b SML )
| |
Pc (b GML ( ))
K
U 2
(21)
where bGML() is the optimum detector on R when b is equiprobably transmitted.
Theorem 2: Let two subset hypothesis tests A and B have the same partition regions R, U.
If maxB (r | b) maxA (r | b) for r R and U, then
b
b
Pe (b SML ( A)) Pe (b SML ( B)) Pe ( R )
U
Pe (b SML ( B))
(22)
where
Pe ( R )
1
2K
(r | b) max (r | b)]dr ,
[max
R
b
B
b
A
R {r R | maxB (r | b) maxA (r | b)} .
b
b
(23)
(24)
12
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Theorem 2 means that for an SML detector (B) to achieve a smaller error probability, it is not
necessary to test more hypotheses (i.e., | B | | A |), but to test better hypotheses (i.e.,
maxB (r | b) maxA (r | b) ).
b
b
Corollary 2: (a) For any partition R and associated subset , Pe(bSML) Pe(bGML); (b) If bGML
for U, then Pe(bSML) = Pe(bGML).
In terms of Corollary 2, the optimum detector is optimum among the SML detectors. However,
if every subset of hypotheses contains the optimum hypothesis, the SML detector achieves the
optimum performance even though the number of tested hypotheses is much smaller than 2K, the
number required by the optimum detection. Since the optimum hypothesis varies with r, it is
necessary to design subsets of hypothesis adaptive to r.
Corollary 3: Consider two subset hypothesis tests A and B that have the same partition R,
U. If A B for U, then Pe(bSML(A)) Pe(bSML(B)).
D. Examples of SML detectors
As an example, we consider first an SML detector with an identical subset of hypotheses.
ISML detector: Given a set of hypotheses {1, 1}K. Let b ISML arg max (r | b) .
b
Theorem 3: The error probability of the ISML detector for the set of hypotheses is
Pe (b
ISML
2K | | | |
( ))
K Pe (b GML ( ))
K
2
2
(25)
where Pe(bGML()) is the error probability of the optimum solution over K when only b are
equiprobably transmitted.
Since the ISML detector never selects a hypothesis b , the error probability is 1/2K whenever
a vector b is transmitted. All these 2K || vectors contribute the error probability given by
the first term in (25). The performance of the ISML detector is limited by the error probability of
these vectors that are not tested.
Next, we consider the uniform random selection of hypotheses.
USML detector: For r K, equiprobably select a fixed number || of hypotheses to form (r)
{1, 1}K. Let b USML arg max (r | b) .
b ( r )
13
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Since the tested || hypotheses are equiprobably chosen from the 2K hypotheses for r K, the
probability that the GML solution is in the selected hypotheses (r) is
Pr(b GML (r ))
| |
.
2K
(26)
By taking expectation of (26) over K with respect to r, we obtain the following theorem.
Theorem 4: The probability that the USML detector achieves the optimum solution is
Pr(b USML b GML )
| |
.
2K
(27)
The performance of the USML detector is limited by the number of tested hypotheses.
III. PRELIMINARY PROPERTIES OF SEARCH DETECTORS
A. Limit points of search detectors
For r K, a search detector at any search step t is a map from {1, 1}K to {1, 1}K,
(r): {1, 1}K | {1, 1}K.
(28)
Definition 3: If maps from b(t) {1, 1}K to b(t + 1) {1, 1}K in deterministic sense, is a
deterministic search detector; otherwise, if maps from one vector to several vectors each with
certain probability, is a random search detector. If the mapping is independent of t, is timeinvariant; otherwise, is time-variant.
As step t approaches infinity, b(t) converges to some limit point,
(r): b lim b(t ) .
(29)
t
b is the finally demodulated vector of . There can exist many limit points.
Definition 4: For r K, the limit set of (r) is defined as
(r) {b {1,1}K | (r) : b lim b(t ), b(0) {1,1}K } .
t
(30)
(r) contains all limit points of (r) starting from all possible initial vectors. Due to the
dependence on r, (r) is a random set. There are two kinds of limit points – fixed points and
limit cycle points.
14
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Definition 5: For r K, b is a fixed point of if there exists an integer tf 0 such that under
the search rule of (r), b(t) = b for t tf.
Depending on r, tf is a random variable.
Definition 6: For r K, b is a point on a limit cycle of if there exist integers T > 1 and tc
0 such that under the search rule of (r), b(t+T) = b(t) = b for t tc > T. T is called the length
of the limit cycle.
Limit points are detector-dependent. The limit set (set of demodulated vectors) determines
performance of the detector.
Lemma 1: For r K, a deterministic and time-invariant (r) converges to either a fixed point
or enters a limit cycle after at most 2K search steps.
Definition 7: Given r, a sequence {[r | b(t)]} is said to be of monotonic likelihood ascend, or
simply monotonic, if [r | b(t + 1)] > [r | b(t)] for any b(t + 1) b(t).
In this paper, we consider only two kinds of likelihood sequences: (i) {[r | b(t)]} is monotonic
as in Definition 7; or (ii) {[r | b(t)]} is not monotonic. In other words, we do not consider the
monotonic likelihood descent sequence such that [r | b(t + 1)] < [r | b(t)] for any b(t + 1)
b(t) though some results are applicable to this sequence. This is because a monotonic likelihood
descent sequence is always undesired. Hence, through this paper, we consider only the search
detectors that never generate a monotonic likelihood descent sequence at any conditions.
Lemma 2: For an r K, let {b(t)} be a sequence generated by a deterministic (time-variant or
invariant) search detector (r). If {[r | b(t)]} is monotonic, then {b(t)} converges to a fixed
point in a finite number of steps.
Corollary 4: If the condition in Lemma 2 holds for all r K, converges to a fixed point in a
finite number of steps with probability one,
Pr {b(t 1) b(t )} 1 .
t 0 t t
f
f
(31)
Due to Corollary 4, if (31) is not true, there exists a region C K with nonzero probability
measure such that if r C, then [r | b(t + 1)] [r | b(t)] for some b(t + 1) b(t). If a nonzero
15
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
update b(t + 1) b(t) 0 does not increase likelihood, the computation of this update is wasted.
It is desired to design a search detector that monotonically increases likelihood.
In terms of Lemma 2, if {b(t)} does not converge to a fixed point in a finite number of steps,
{[r | b(t)]} is not monotonic. Hence, Lemma 2 yields the following corollary.
Corollary 5: Suppose that {b(t)} is on a limit cycle of a deterministic (time-variant or invariant)
search detector (r). Then {[r | b(t)]} is not monotonic.
B. Local maximum likelihood point
For r K, the optimum detector bGML is well-known to achieve the global maximum
likelihood (GML) point. As we will see in this paper, there exists a class of detectors, the widesense sequential LAS detectors, that achieve local maximum likelihood (LML) points. The GML
detector bGML has been well studied in literature. However, the LML detectors bLML have not
been paid attention in literature.
Definition 8: For b {1, 1}K, the neighborhood of b is defined as the set
N(b) = {a {1, 1}K | ||a b||1 1}.
(32)
||a b||1 denotes the Hamming distance between a and b. For a N(b) and a b, a and b
differ by only one bit. That is a = b 2bkek for some k {1, …, K} where ek is the kth coordinate
vector.
Definition 9: For r K, consider b {1, 1}K and its neighborhood N(b). If
(r | b) (r | a),
a N(b)\{b},
then b is a local maximum likelihood (LML) point.
(33)
Definition 10: For r K, the set of local maximum likelihood (LML) points is defined by
LML(r) = {b {1, 1}K | (r | b) (r | a), a N(b)\{b}}.
(34)
Due to dependence on r, an LML point bLML is random and the set LML(r) of LML points is a
random set. Clearly, if and only if b is a local minimum point of f(r | b), b is an LML point. The
set of local minimum points of f is the set of LML points.
Observation 4: bGML(r) LML(r), r K.
16
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
In addition to bGML(r), LML(r) may contain many other LML points, depending on observation
r, signature crosscorrelation matrix R, and distribution of users’ signal amplitudes Ak. Among all
the LML points in LML(r), the optimum bGML(r) is the global maximum likelihood point.
Lemma 3: For r K, b LML(r) iff
b [r (R I)Ab] 0,
(35)
where denotes the Hadamard product, and the inequality of vector is element-wise.
The region {r K | (r | b) = (r | a), a N(b)\{b}} = {r K | rk = [(R I)Ab]k, k
{1, 1}K} has a zero probability measure. In this paper, for the simplicity of discussion
sometimes this region is ignored.
Observation 5: If a b and a, b LML(r), ||a b||1 2. In particular, ||a bGML||1 2.
Proof: Without loss of generality, consider (r | a) < (r | b). If ||a b||1 = 1, then b N(a),
which contradicts a LML(r). Hence, ||a b||1 2.
(Q.E.D.)
After ignoring the region {r K | rk = [(R I)Ab]k of zero probability measure for k {1,
1}K}, (35) can be equivalently written as
b = sgn[r (R I)Ab]
(36)
where the sign of vector is the vector of signs. We can arbitrarily take sgn(0) = 1 or 1. As
expected, the optimum detector bGML satisfies condition (36) as pointed out in [1] (p. 213).
The definition of LML points depends on the definition of neighborhood. In this paper, only the
neighborhood of size one is considered. An LML point can also be defined based on the
neighborhood of size larger than one. In this case, an algorithm achieving an LML point becomes
more computationally complex. For example, if the entire set {1, 1}K is considered the
neighborhood of any vector, then only the GML point bGML belongs to LML(r). The algorithm
achieving bGML becomes NP-hard.
C. Observation region of limit point
The limit points of a search detector are finally demodulated vectors. It is interesting to see the
observation region of a limit point because this limit region is actually the decision region with
an according initial.
Definition 11: Let b be a limit point of . The limit region of b in the observation space is
defined as V(b) = {r K | b (r)}.
17
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Definition 12: For b {1, 1}K, the LML region of b in the observation space is defined as
VLML(b) = {r K| b LML(r)}.
The following corollary is a dual result of Lemma 3.
Corollary 6: For b {1, 1}K, the LML region of b is VLML(b) = {r K| b [r (R
I)Ab] 0}.
VLML(b) is an open convex hull bounded by K sides. Its kth side is on the hyperplane rk = [(R
I)Ab]k and its vertex is at r = (R I)Ab. Properties of LML points and LML regions are
discussed in [36].
D. Likelihood ascent property
The following lemma will be useful in this paper. As expected, this lemma points out that it is
necessary to achieve higher likelihood in detection in order to reduce error probability.
Lemma 4: For r K, let b(r) and b(r) be demodulated vectors by detectors and ,
respectively. If [b(r)] [b(r)] for r K, then Pe(b) Pe(b) where the equality holds
iff Pr[(b) = (b)] = 1.
Proof: As shown in Fig. 1, suppose that the observation space K is divided into decision
regions Za for a {1, 1}K by , and decision regions Zb for b {1, 1}K by .
Neither nor may necessarily contain all vectors of {1, 1}K. Define D = {r K | (r | b)
> (r | b)} and D = {r K | (r | b) = (r | b)}. Clearly, D D = K. b and b are
random vectors and their realizations are vectors in and , respectively.
If Pr[(b) = (b)] = Pr(r D ) < 1, Pr(r D) = 1 Pr(r D ) > 0. The correct detection
probability of detector is
Pc (b )
Pr(r Z
b
b
| H b ) Pr( H b )
1
2K
b a
1
2K
Pr(r Z
b a
1
2K
(r | b)dr 2 (r | b)dr
Pr(r Z
a
Zb | Hb )
a
Zb D | Hb )
1
2K
Pr(r Z
b a
a
Zb D | Hb )
1
b a
K
Za Zb D
b a
Za Zb D
18
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
1
2K
1
b a
1
2K
(r | a)dr 2 (r | a)dr
b a
1
2K
(r | a)dr 2 (r | a)dr
a b
1
2K
(r | a)dr 2 (r | a)dr
a
1
2K
Pr(r Z
a
1
2K
a
(r | b)dr 2 (r | a)dr
K
Za Zb D
b a
9/6/99
(37)
Za Zb D
1
K
Za Zb D
b a
Za Zb D
1
K
Za Zb D
a b
Za Zb D
1
K
Za D
a
a
D | Ha )
a
| Ha )
Pr(r Z
Za D
1
2K
Pr(r Z
a
a
D | Ha )
Pc (b ) .
(38)
Hence, Pe(b) < Pe(b).
If Pr[(b) = (b)] = 1, then Pr(r D) = 0 and Pr(r D ) 1 . Hence, (37) becomes
Pc (b )
1
2K
1
2K
a Za D
1
2K
a
1
2K
a
(r | a)dr
b a Za Zb D
(r | a)dr
Pr(r Z
a
D | Ha )
Pr(r Z
a
| Ha )
Pc (b ) ,
(39)
and therefore Pe(b) = Pe(b).
(Q.E.D.)
IV. LIKELIHOOD ASCENT SEARCH DETECTORS
A. Generalized likelihood ascent search detector
19
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
The performance of the ISML and USML detectors in Section II is limited by the number || of
tested hypotheses. When || is small, their error probabilities are large. To reduce the error
probabilities, || must be large. However, the computational complexity increases with ||. On the
other hand, Theorem 2 suggests that in order to reduce error probability it be not necessary to test
more hypotheses, but necessary to test better hypotheses. If the subset of hypotheses at every r is
properly designed, the error probability can be considerably reduced with a limited number of
tested hypotheses. The ISML and USML detectors have limited performance due mainly to the
ordinary design of the subsets of hypotheses. Suppose that a is on hand and its likelihood (r | a)
is known. We want to search another vector b that has increased likelihood. If b has lower
likelihood, it has to be discarded and the computation for comparison of two likelihood values
(mainly the computation of (r | b)) is wasted. For arbitrarily given a, if we equiprobably
selected a vector among the other 2K 1 vectors, the probability to increase the likelihood would
be only about ½. There would be a half chance to waste the computation. This explains the
limited performance of the ISML and USML detectors that select tested hypotheses in the similar
way.
With an initial b(0), it is desired to search out a sequence {b(0), b(1), …} with monotonic
likelihood ascent {[b(0)] < [b(1)] < … }. In this search, the information provided by the
vectors on hand must be used in search of the next vector so that the likelihood ascent of the next
vector is guaranteed. Given a vector b(t), the gradient of likelihood function (equivalently the
negative gradient of metric) evaluated at b(t) suggests the direction in which the likelihood
should increase, which forms the main idea of the LAS detectors.
The negative gradient of metric f(r | b) with respect to b, which is evaluated at b(t), is
h(t) = f[b(t)] = Wb(t) + q.
(40)
It is easy to show that the metric f can be expressed by the norm of h as
f (b)
1 T
h (b) W 1h(b) .
2
(41)
The negative gradient of metric must be calculated at every search step t. After b(t + 1) is
accepted, an efficient computation method to update h(t + 1) from h(t) is desired. Assume that
~
b(t + 1) and b(t) differ by the bits whose indices are in L (t ) {1, 1}K,
20
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
b(t 1) b(t ) 2 bi (t )e i
9/6/99
(42)
~
iL ( t )
where bi(t) {1, 1}. It can be shown that h(t) can be efficiently updated by
h(t 1) h(t ) 2 bi (t )Wi
(43)
~
iL ( t )
where Wi is the ith column vector of matrix W. Then the metric change f(t) = f[b(t + 1)]
f[b(t)] due to the bit change b(t) = b(t + 1) b(t) can be written as
f (t ) b T (t )f [b(t )]
b T (t )[ h(t )
1 T
b (t ) 2 f [b(t )]b(t )
2
1
g (t )] ,
2
(44)
where 2f[b(t)] = W is the second derivative of f(r | b) with respect to b and
g(t ) Wb(t ) .
(45)
When b(t) is on hand, h(t) indicates the direction along which the likelihood may increase.
Since vectors are supported by a finite set, the next better vector can only be roughly along the
direction indicated by the negative gradient. Along this direction, a search step may have
different size. That is, the next vector b(t+1) can differ from the current vector by a different
number of bits. However, similarly to ordinary local search optimization algorithms for
parameters of real support, the step size ||b(t+1) b(t)|| in the search of b(t + 1) must be properly
limited so that the likelihood is guaranteed to increase. This is maintained by properly established
thresholds of all bits that are allowed to be updated. There are many choices of bits allowed to be
updated at every search step. To include all the possible choices in a generalized framework, a
generalized likelihood ascent search (GLAS) detector is proposed as follows.
GLAS detector: Given a sequence of bit index subsets L(t) {1, ..., K} for t 0 and an initial
b(0) {1, 1}K, the bits are updated by
if k L(t ), bk (t ) 1 and hk (t ) t k (t ),
1,
bk (t 1) 1,
if k L(t ), bk (t ) 1 and hk (t ) t k (t ),
b (t ), otherwise,
k
(46)
where tk(t) is the threshold of the kth bit at step t,
t k (t )
| W
jL ( t )
kj
| ,
for k L(t).
(47)
21
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
~
h(t + 1) is updated by (43) where L (t ) is the index set of really flipped bits in (46). If b(t) = bf
for all t tf with some tf 0, bf is the finally demodulated vector.
Determined by whether L(t) is deterministic or random and whether L(t) depends on r, the
GLAS detector can be deterministic, random dependent on r, random independent of r, or
random dependent on r and other independent random source. In this paper, for simplicity it is
always assumed that L(t) is deterministic though some results are applicable to other cases. If L(t)
varies with t, the GLAS detector is time-variant; otherwise, time-invariant. In most case, L(t)
varies with t, and thus GLAS detector is time-variant. In general, achieving bf, a fixed point, the
GLAS detector terminates search at step tf. Both bf and tf depend on r and initial b(0), and thus
are random.
L(t) determines the neighborhood of the search at step t, i.e., b(t + 1) Ns(t) {b {1, 1}K | bk
= bk(t), k {1, …, K}\L(t)}. If k L(t), the kth bit is allowed to be updated but may not be
flipped. If further the kth component hk(t) of the negative gradient satisfies one of the flip
conditions with threshold tk(t), the kth bit is flipped at step t. If k L(t), the kth bit is kept
unchanged at step t. L(t) also determines the threshold tk(t) for k L(t). As shown in (47), the
threshold tk(t) depends on the crosscorrelation coefficients and signal amplitude of the users that
are updated at the same step t (whose indices are in L(t)). Threshold tk(t) changes with step t if
L(t) changes.
Specifying an index subset sequence L(t) for t 0 in the GLAS detector, one produces a LAS
detector. The GLAS detector defines a family of LAS detectors. Properties of the GLAS detector
are properties of this family of LAS detectors.
Let (r, t ) 0 t b( ) . From step 0 to t, the GLAS detector carries out a test on the subset
hypothesis,
Hb: r = RAb + z,
b (r, t),
(48)
and selects b(t). It will be proved in the next subsection that b(t) achieves the SML detection
over (r, t) for t 0. In particular, terminating at step tf with decision bf, the GLAS detector
achieves the SML detection over (r, tf). This comes up with the fact that the sequence {b(t)}
generated by the GLAS detector is associated with monotonic likelihood ascent [r | b(t)] [r |
22
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
b(t + 1)] where the equality is true if and only if b(t) = b(t + 1). This is why we call each of the
detector a likelihood ascent search (LAS) detector.
The condition of hk(t) required for the flip of the kth bit in (46) can be concisely written as
bk(t)hk(t) < –tk(t).
(49)
Let t kf 0 be the terminating step of flip of the kth bit such that bk(t + 1) = bk(t) for t t kf . It
is clear that t kf tf for k. In other words, though the GLAS detector terminates search at step tf,
it may have no longer changed a bit before tf. Without loss of generality, in this paper, we assume
that after t kf , the kth bit is updated at least once more, that is
L(t ) {k} {k} , k.
(50)
t t kf
For any such t t kf such that k L(t), due to the search rule of the GLAS detector, the kth
component of negative gradient of metric at the fixed point bf satisfies
bkf hk (b f ) t k (t ) .
(51)
Defining the minimum threshold of the kth bit after its termination of flip by
~
tk min
{t k (t )} ,
f
(52)
then h(bf) at the fixed point satisfies
bkf hk (b f ) ~
tk , k.
(53)
t t k , kL ( t )
The performance of the GLAS detector depends on the initial. For example, if the initial is the
output of the optimum (GML) detector with probability one, as we can see later, the GLAS
detector achieves the optimum detection because the GLAS detector actually never changes this
optimum initial. In order to explore the performance of the GLAS detector in all situations, in the
performance analysis that follows, the initial is always assumed to be arbitrary unless specified.
B. Likelihood ascent and stability of LAS detectors
One of the most important properties of the GLAS detector is described by the following
theorem. From it many other properties can be derived.
Theorem 5: For r K, the GLAS detector guarantees monotonic likelihood ascent,
[r | b(t + 1)] [r | b(t)],
t 0,
where the equality holds if and only if b(t + 1) = b(t).
(54)
23
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Theorem 5 implies that the likelihood function as well as the metric f is a Liapunov function
of the GLAS detector. The family of detectors defined by (46) are indeed likelihood ascent
search (LAS) detectors. The monotonic likelihood ascent property implies the stability of the
LAS detectors.
Theorem 6: For r K, after a finite number tf of search steps, the GLAS detector converges
to a fixed point.
Corollary 7: The GLAS detector converges to a fixed point in a finite number of steps with
probability one.
Convergence with probability one to a fixed point allows the existence of a region of zero
probability measure, on which a detector does not converge to a fixed point. Clearly, the GLAS
detector eliminates the existence of such a region.
Theorem 6 immediately yields that every limit point of the GLAS detector is a fixed point and
there is no limit cycle point for r.
Corollary 8: For r K, let GLAS(r) and GLAS(r) be the limit set and the set of fixed points
of the GLAS detector, respectively. Then GLAS(r) = GLAS(r).
Repeatedly applying Theorem 5 leads to the following corollary. Given an initial, the GLAS
detector can finally obtain a new vector with increased likelihood unless the initial vector is a
fixed point itself.
Corollary 9: For b(0) {1, 1}K and r K, let bf be a fixed point of the GLAS detector
with initial b(0). (i) If b(0) GLAS(r), then bf b(0) and (r | bf) > [r | b(0)]; (ii) if b(0)
GLAS(r), then bf = b(0).
Observation 6: Stopping search at t 0 with b(t) of the demodulated vector, the GLAS
detector is an SML detector over (r, t ) 0 t b( ) .
If the likelihood at a nonzero-update step does not increase, the computation at this step is
wasted in the viewpoint of decreasing error probability (which asks the likelihood to increase
according to Lemma 4). Moreover, the non-increase of likelihood may imply the instability of the
detector. In order to save computation time and ensure stability, the monotonic likelihood ascent
must be guaranteed. This needs larger thresholds. On the other hand, larger thresholds mean the
existence of more unnecessary fixed points, thus implying a larger error probability, too. In what
follows, we show that the thresholds set up in the GLAS detector are necessary and sufficient for
24
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
monotonic likelihood ascent even for the class of “bad” crosscorrelation matrices, which is
defined below.
Definition 13: R if there exists a subset L {1, …, K} with |L| 2 and a vector b {1,
1}K such that Rkj 0 and sgn(Rkj) = dkdj for k, j L.
If the condition of |L| 2 was eliminated from Definition 13, then all R would belong to
because we can always let L = {k}, k {1, …, K}.
Lemma 5: R iff R = I.
Proof: If R I, there exists at least one pair of k and j such that Rkj 0. Consider L = {k, j}. We
can chose a vector b {1, 1}K such that sgn(Rkj) = dkdj. Then R . On the other hand, if R =
I, there is no L {1, …, K} such that |L| 2 and Rkj 0 for k, j L. Hence, I .
As indicated by Lemma 5, almost every crosscorrelation matrix belongs to . On the other
hand, for L| 3, not every R I belongs to . It is clear that for any L {1, …, K}, there are
infinitely many R . For such a large class of crosscorrelation matrices, the GLAS detector
would be unstable if thresholds were smaller than that in (47) as shown by the following two
theorems.
Theorem 7: For arbitrary L(t) {1, …, K} and arbitrary R, the thresholds tk(t) specified in (47)
are necessary and sufficient for the GLAS detector to increase likelihood for nonzero update b(t
+1) b(t) with probability one.
Proof: For the sufficiency, in terms of Theorem 5, for r K the GLAS detector guarantees
monotonic likelihood ascent, i.e., [r | b(t + 1)] > [r | b(t)], t 0 for b(t + 1) b(t). Hence,
Pr{[b(t + 1)] > [b(t)]} = E{I[(r | b(t + 1)) > (r | b(t))} = E(1) = 1
(55)
where I(X) is the indicator function of event X.
In what follows, we prove the necessity. For any L(t), if |L(t)| 2, we consider a matrix R
and b(t) such that bk(t)bj(t) = sgn(Rkj). If |L(t)| = 1, any R can be considered because of sgn(Rkk) =
sgn( Ak2 ) = 1 = bk(t)bk(t). Consider k > 0 such that tk(t) k 0. In the following, we show that
if the threshold tk(t) in the GLAS detector is replaced by a smaller threshold tk(t) k, the
probability that at step t the likelihood change (t) = [r | b(t + 1)] [r | b(t)] is larger than
zero is smaller than one, i.e., Pr((t) > 0) < 1.
We define a region of K by
25
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
= {h K | tk(t) bk(t)hk(t) < tk(t) + k, k L(t)}.
9/6/99
(56)
h(t) of (40) can be rewritten as
h(t) = Wb(t) + Wb + Az.
(57)
Since Az is Gaussian with zero mean and covariance matrix 2W, if 0, the probability that
h(t) is located in is greater than zero, i.e.,
Pr[h(t) ] > 0.
(58)
Consider h(t) . Suppose that the threshold tk(t)’s in the GLAS detector were replaced by the
new threshold tk(t) k (which is strictly smaller than tk(t)). In terms of the GLAS detector, all
bk(t) for k L(t) should be updated such that bk(t) = bk(t+1) bk(t) = 2bk(t) because bk(t)hk(t) <
tk(t) + k (Note that in the original GLAS detector as shown by (49), if bk(t)hk(t) < tk(t), then
bk(t + 1) = bk(t)). Such a b(t) is a nonzero update of the GLAS detector.
Notice that bk(t) = 0 for any k L(t). The metric change according to (44) is
b (t )e
f (t )
k
kL ( t )
2
b (t )e
k
kL ( t )
2
h(t ) W b j (t )e j
jL ( t )
k
k
b (t )b j (t )
jL ( t )
kj k
b (t )h (t ) | W
kL ( t )
2
1
h(t ) W b j (t )e j
2 jL (t )
b (t )h (t ) W
kL ( t )
2
T
k
T
k
k
b
kL ( t )
k
k
jL ( t )
kj
|
(t )hk (t ) t k (t ) 0
(59)
where the last inequality holds due to h(k) . This proves that Pr(f(t) 0 | h(t) ) = 1.
Hence,
Prf (t ) 0 Prf (t ) 0 h(t ) Prh(t )
Prf (t ) 0 h(t ) Prh(t )
Prf (t ) 0 h(t ) Prh(t ) Prh(t ) 0
(60)
which implies
Prf (t ) 0 1 Prf (t ) 0 1 ,
(61)
26
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
or equivalently Pr[(t) > 0] < 1.
9/6/99
(Q.E.D.)
The arbitrary L(t) and arbitrary R in Theorem 7 are in the sense of worst case, i.e. R . For
the sequential LAS detector (defined in Section V) that has |L(t)| = 1, the conclusion of Theorem
7 is in the sense of any R as stated in the following corollary.
Corollary 10: For L(t) = {k} of k {1, …, K} and any R, the thresholds tk(t) specified in (47)
are necessary and sufficient for a sequential LAS detector to increase likelihood for nonzero
update with probability one.
The following theorem further shows that the decrease of the thresholds in the GLAS detector
can result in existence of a limit cycle.
Theorem 8: Consider that a search detector has the same search rule as the GLAS detector but
tk(t) is replaced by tk(t) k > 0 with k > 0 for k L(t) and L(t) = L {1, …, K} is fixed for all t.
Then given any one of L {1, …, K} and R with Rkj = 0 for k or j L there exists the other
as well as a region D = {r K | k/Ak < rk < k/Ak, k L} such that for r D, (r) contains
a limit cycle C = {b(1), …, b(T)} where bk(t + 1) = bk(t) for k L.
Proof: Given L(t) = L {1, …, K} and b(t) {1, 1}K, we consider an R such that
sgn(Rkj) = bk(t)bj(t) for k, j L and Rkj = 0 for k or j L. Define a region by D = {r K |
k/Ak < rk < k/Ak, k L}. For r D,
K
bk (t )hk (t ) bk (t )Wkj b j (t ) bk (t ) Ak rk
j 1
bk (t )
W
jL ( t )
| W
jL ( t )
kj
kj
b j (t ) bk (t ) Ak rk
| bk (t ) Ak rk
t k (t ) bk (t ) Ak rk
t k (t ) Ak | rk |
t k (t ) k , k L(t).
(62)
Hence, all bits whose indices are in L(t) are flipped at step t, i.e. bk(t + 1) = bk(t) for k L(t) =
L. Since L(t + 1) = L(t) = L, at step t + 1 we have
K
bk (t 1)hk (t 1) bk (t 1)Wkj b j (t 1) bk (t 1) Ak rk
j 1
27
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
bk (t 1)
bk (t )
W
jL ( t )
| W
jL ( t )
W
jL ( t 1)
kj
kj
kj
9/6/99
b j (t 1) bk (t 1) Ak rk
b j (t ) bk (t ) Ak rk
| bk (t ) Ak rk
t k (t ) bk (t ) Ak rk
t k (t ) Ak | rk |
t k (t ) k , k L(t + 1).
(63)
Hence, all bits whose indices are in L(t + 1) = L are flipped back at step t + 1, i.e. bk(t + 2) =
bk(t + 1) = bk(t) for k L(t + 1). Obviously, the bits bk for all k L are flipped at every search
step t, and so does not converge to a fixed point. With the fixed L, is deterministic and timeinvariant, and thus converges to a limit cycle according to Lemma 1.
On the other hand, given R , we consider L(t) = L {1, …, K} and b(t) such that sgn(Rkj)
= bk(t)bj(t) for k, j L and Rkj = 0 for k or j L. Similarly, the result can be obtained.
(Q.E.D.)
In Theorem 8, since D has nonzero probability measure, the following corollary is obtained.
Corollary 11: In the condition of Theorem 8, the detector converges to a limit cycle with a
nonzero probability.
The following theorem addresses the conditions under which the second LAS detector improves
the performance of the first LAS detector if they are cascaded.
Theorem 9: Let b be a fixed point of a LAS detector with initial b, a fixed point to which
~
another LAS detector converges with an arbitrary initial. (i) if t k (t ) tk for all t 0 and k
~
L(t), then (r) = (r) for r; (ii) if t k (t ) tk for all t 0 and k L(t), then (r) (r),
~
r; (iii) if the inequality ( t k (t ) < tk ) in condition of (ii) holds for at least one pair of k and t,
then there exists a region D K such that Pr(r D) > 0 and (r) (r) for r D.
Proof: Since starts with an arbitrary initial, b can be any fixed point of .
~
~
(i) Since b (r), according to (53) bkf hk (b ) tk for k. Since t k (t ) tk for all t 0
and k L(t),
28
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
bkf hk (b ) ~
tk t k (t ) , t 0 and k L(t).
9/6/99
(64)
Due to (53), this implies that b (r) and thus (r) (r), r. Since always starts
search from some b (r), (r) = (r), r.
~
~
(ii) Since t k (t ) tk for all t 0 and k L(t), ~tk tk . This means that for b (r), b
(r), r. Hence, (r) (r), r.
~
(iii) Consider the pair of k and t such that t k (t ) < tk . For b , suppose that up to step t,
does not change b, i.e. b(t) = b. Define
{h K | bk hk [~
tk ,t k (t )), bi hi [~
ti , ), i k , i {1,..., K }}
(65)
and let
h(t) = Wb + Ar = Wb + Wb + Az.
(66)
If 0, Pr[h(t) ] > 0. We define a region
D {r K | r A 1h RAb , h }
(67)
where clearly Pr(r D) = Pr[h(t) ] > 0.
~
For r = A1h(t) + RAb D or h(t) , b (r) because of bkf hk (b ) tk , k.
However, the kth bit of b(t) = b must be flipped by due to bk hk (b ) t k (t ) . Hence, b(t + 1)
~
b(t) = b. This implies that b (r). Since (r) (r), (r)\(r) . If t k (t ) < tk is
true for several k at t or for several pairs of k and t, we can show in the same way that there
exists a region D K such that Pr(r D) > 0 and (r)\(r) for r D. (Q.E.D.)
Stated in probability, Theorem 9 leads to the following corollary.
Corollary 12: Let b be a fixed point of a LAS detector with initial b, a fixed point to which
~
another LAS detector converges with an arbitrary initial. (i) if t k (t ) tk for all t 0 and k
~
L(t), then Pr( = ) = 1; (ii) if t k (t ) tk for all t 0 and k L(t), then Pr( ) = 1; (iii)
if the inequality in condition of (ii) holds for at least one pair of k and t, then Pr( ) > 0.
Proof: It is straightforward to obtain (i) and (ii) from Theorem 9 (i) and (ii). For (iii), consider
the b in the proof of (iii) of Theorem 9. Because of Pr( ) = 1 due to (ii), then
Pr(\ ) Pr(b \)
= Pr(b \ | r D)Pr(r D) + Pr(b \ | r D)Pr(r D)
29
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Pr(b \ | r D)Pr(r D)
= Pr(r D) > 0.
(68)
(Q.E.D.)
The following theorem indicates a relationship of fixed point sets of LAS detectors with index
sequences L(t), t 0 via the thresholds. The situation is different from that in Theorem 9 because
with arbitrary initials both (r) and (r) for r contain all possible fixed points of and ,
respectively.
Corollary 13: Consider two LAS detectors and both with arbitrary initials. (i) If
t k (t ) t k (t ) for all k and t 0, then Pr( ) = 1; (ii) if the inequality in condition of (i)
holds for at least one pair of k and t, then Pr( ) > 0.
~
Proof: (i) For r and b (r), according to (53) bk hk (b ) tk for k. Since
~
~
~
t k (t ) t k (t ) for all k and t 0, then tk tk and thus bk hk (b ) tk for k. Hence, b
(r) and thus (r) (r), r. This implies Pr( ) = 1.
(ii) Because the initial b(0) of is arbitrary, Pr[b(0) = b] > 0. By means of (iii) of Corollary
12, Pr[ | b(0) = b] = 1. Hence, Pr( ) = Pr[ | b(0) = b]Pr[b(0) = b] +
Pr[ | b(0) b]Pr[b(0) b] Pr[ | b(0) = b]Pr[b(0) = b] = Pr[b(0) = b]
> 0.
(Q.E.D.)
The more the bits are updated at each step, the larger the thresholds, and then the more the fixed
points, and the easier a LAS detector converges to a fixed point.
C. Performance of LAS detectors
It is of interest to study the performance of the LAS detectors in terms of error probability. As
we will see, the monotonic likelihood ascent of the GLAS detector directly results in the
monotonic descent of error probability.
Theorem 10: The GLAS detector monotonically reduces error probability, i.e.,
Pe[b(t + 1)] Pe[b(t)],
t 0
where the equality holds if and only if Pr[b(t + 1) = b(t)] = 1.
(69)
Proof: In terms of Theorem 5, for r and b(t), the GLAS detector yields b(t + 1) such that [r |
b(t + 1)] [r | b(t)] where the equality holds iff b(t + 1) = b(t). This implies
30
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Pr{[b(t + 1)] = [b(t)]}
= Pr{[b(t + 1)] = [b(t)] | b(t + 1) = b(t)}Pr[b(t + 1) = b(t)]
+ Pr{[b(t + 1)] = [b(t)] | b(t + 1) b(t)}Pr[b(t + 1) b(t)]
= Pr[b(t + 1) = b(t)].
Hence, the result of this theorem follows from Lemma 4.
(70)
(Q.E.D.)
The GLAS detector guarantees monotonic likelihood ascent for any r, thus resulting in the
monotonic descent of error probability. On the other hand, monotonic descent of error probability
does not require monotonic likelihood ascent for all r. The difference is a region of zero
probability measure.
The GLAS detector always decreases error probability unless the initial is its fixed point with
probability one.
Theorem 11: Let bGLAS be a fixed point of the GLAS detector with initial b(0). Then
Pe(bGLAS) Pe[b(0)]
where the equality holds iff Pr[b(0) GLAS] = 1.
(71)
Proof: Due to Corollary 9, for r K, (r | bGLAS) [r | b(0)] where the equality holds iff
b(0) GLAS. Hence,
Pr{(bGLAS) = [b(0)]} = Pr{(bGLAS) = [b(0)] | b(0) GLAS}Pr[b(0) GLAS]
+ Pr{(bGLAS) = [b(0)] | b(0) GLAS}Pr[b(0) GLAS]
= Pr[b(0) GLAS].
The result of this theorem follows from Lemma 4.
(72)
(Q.E.D.)
In Theorem 11, the initial b(0) can be output of any detectors of any kind. If the output of a
detector is not a fixed point of the GLAS detector with probability one, the GLAS detector can
reduce its error probability by giving different vectors for some initials.
Theorem 11 is also applicable to the case when two LAS detectors are cascaded. The following
theorems indicates when one LAS detector improves another LAS detector.
Theorem 12: Let b be a fixed point of a LAS detector with initial b, a fixed point to which
~
another LAS detector converges with an arbitrary initial. If t k (t ) tk for all k and t 0 and
the inequality holds for at least one pair of k and t, then Pe(b) < Pe(b).
31
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Proof: In terms of Corollary 12 (ii) and (iii), Pr(\ ) > 0. Because the initial of is
arbitrary, Pr(b \) > 0. Hence, Pr(b ) < 1. According to Theorem 11, Pe(b) <
Pe(b).
(Q.E.D.)
Theorem 12 is derived from Corollary 12 and Theorem 11. However, if and are not
cascaded (i.e., Pr[b(0) = b] < 1), then the conclusion of Theorem 12 is not necessarily true
because by controlling its initial, may achieve a higher error probability than . This explains
why a result similar to Theorem 12 can not be derived from Corollary 13.
Theorem 13: LML(r) GLAS(r), r K.
Theorem 13 states that any LML point is a fixed point of the GLAS detector. The converse is
true only if the GLAS detector is a wide-sense sequential LAS detector defined in the next
section. Combined with Theorem 11, Theorem 13 implies that a LAS detector can not improve
an LML detector. In particular, achieving GML detection, the optimum detector can not be
improved by a LAS detector.
Corollary 14: If Pr[b(0) LML] = 1, then Pe(bGLAS) = Pe[b(0)]. In particular, if Pr[b(0) =
bGML] = 1, then Pe(bGLAS) = Pe[b(0)].
It is of interest to know how good a fixed point of the GLAS detector is in terms of residuals.
Definition 14: For a fixed point bf of the GLAS detector, bf is said to be bounded if there exists t
t kf and k L(t) such that (a) bkf = 1 and hk (b f ) > tk(t) or (b) bkf = 1 and hk (b f ) < tk(t),
where hk (b f ) is the kth component of h(bf) = Wbf q.
Theorem 14: Let bf be a fixed point of the GLAS detector for r. If bf is not bounded, the
gradient of metric and the metric are upper bounded by,
K
|| h(b f ) ||1 min
{t k (t )}
f
k 1
t t k , kL ( t )
(73)
and
f (b f )
K
1
|| W 1 || min
{t k2 (t )} ,
f
t
t
,
k
L
(
t
)
2
k
k 1
respectively, where ||h(bf)||1 denotes the l1-norm of h(bf).
(74)
32
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
The residuals at a fixed point depend only on W and L(t). The fewer the bits updated at one
step, the smaller the thresholds. As shown by Theorem 14, the fewer are the bits updated at each
step, the lower are the upper bounds of ||h(bf)||1 and f(bf), and the higher is the (bf).
D. Computational complexity of LAS detectors
Computational complexity of the GLAS detector depends on the total number tf of search steps.
tf is a random variable depending on r and b(0). It is necessary that the expected computational
complexity be used to measure the complexity of the GLAS detector. In what follows, the
expected tf is estimated and then the expected number of additions per bit is obtained.
First, we define a function by
g ( x) E ( z | z x)
exp( x 2 / 2)
(75)
2 Q( x)
where z ~ N(0, 1) is a standard Gaussian random variable and Q( x) (1 / 2 ) exp( t 2 / 2)dt .
x
Obviously, g(x) is a monotonically increasing function, g(x) > x for x, g() = 0, and g(x)/x = 1
as x , and g (0) 2 / . For > 0 and x 0, g(x/) g (0) 2 / . The figure of
g(x) is shown in Fig. 2.
In order to estimate the expected tf, the expected initial metric divided by the expected reduced
metric at each search step is considered. For any initial b(0) {1, 1}K, the initial metric in
terms of (12) is
f (r | b(0))
1
(RAb(0) r ) T R 1 (RAb(0) r )
2
1
(RAb(0) RAb z ) T R 1 (RAb(0) RAb z )
2
1
1
(b b(0)) T AR T A(b b(0)) z T A(b b(0)) z T R 1 z
2
2
(76)
where b is the transmitted vector. Assume bk and bk(0) are mutually independent and each
equiprobably takes 1 and 1, i.e., bk bk(0) {2, 0, 2}. Then E(bk bk(0)) = 0,
E[(bk bk(0))(bj bj(0))] = 2(k j)
(77)
and E[(b b(0))(b b(0))T] = 2I. b b(0) is independent of z. The expected initial metric is
33
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
1
1
E[(b b(0)) T ARA(b b(0))] E (z T R 1 z )
2
2
f (b(0)) E[ f (r | b(0))]
9/6/99
1
1
tr{E[ ARA(b b(0))(b b(0)) T ]} tr[ E (R 1 zz T )]
2
2
1
tr ( W) tr (R 1 2 R )
2
K
Ak2
k 1
K 2
.
2
(78)
The negative gradient of metric at step t from (40) is
h(t) = Wb(t) + ARAb +Az
= W(b b(t)) + Az
(79)
~
Suppose that at step t, the bits whose indices belong to L (t ) L(t) are flipped by the GLAS
~
~
detector, i.e., bk(t) = bk(t+1) bk(t) = 2bk(t) for k L (t ) , and bk(t) = 0 for k L (t ) . By
means of (A20), the amount of metric reduced by the GLAS detector at step t is
f (t )
~
kL ( t )
1
bk (t ) hk (t ) g k (t )
2
1
b (t )h (t ) 2 b (t ) g
~
kL ( t )
k
k
k
~
kL ( t )
k
(t ) u(t ) v(t ) .
(80)
Now we need to know the mean and the variance of bk(t)hk(t). Assume bits are equiprobable
and independent. From (79),
bk (t )hk (t ) (bk (t 1) bk (t )) Wkk (bk bk (t ))
2bk (t ) Wkk (bk bk (t ))
K
W
j 1, j k
kj
K
W
j 1, j k
kj
(b j b j (t )) Ak z k
(b j b j (t )) Ak z k
K
2Wkk 2Wkk bk (t )bk 2bk (t ) Wkj (b j b j (t )) Ak z k
j 1, j k
2Wkk 2Wkk bk (t )bk 2bk (t ) k (t )
(81)
where k(t) has zero mean and variance
k2 Var ( k (t )) 2
K
W
j 1, j k
2
kj
2Wkk .
(82)
34
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Assume that K is large so that k(t) can be approximated as a Gaussian random vector, i.e. k(t) ~
~
N(0, k2 ). Note that from (49), bk(t)hk(t) = 2bk(t)hk(t) > 2tk for k L (t ) . Conditioned with
(bk(t), bk) = (1, 1), we have
E bk (t )hk (t ) | bk (t )hk (t ) 2t k , bk (t ) 1, bk 1
E 2Wkk 2Wkk 2 k (t ) | 2Wkk 2Wkk 2 k (t ) 2t k
(t ) k (t ) t k
2 k E k
k
k
k
t
2 k g k
k
.
(83)
Similarly,
E bk (t )hk (t ) | bk (t )hk (t ) 2t k , bk (t ) 1, bk 1
E 2Wkk 2Wkk 2 k (t ) | 2Wkk 2Wkk 2 k (t ) 2t k
(t ) k (t ) t k 2Wkk
4Wkk 2 k E k
k
k k
t 2Wkk
4Wkk 2 k g k
k
,
(84)
E bk (t )hk (t ) | bk (t )hk (t ) 2t k , bk (t ) 1, bk 1
E 2Wkk 2Wkk 2 k (t ) | 2Wkk 2Wkk 2 k (t ) 2t k
(t ) k (t ) t k 2Wkk
4Wkk 2 k E k
k
k
k
t 2Wkk
4Wkk 2 k g k
k
,
(85)
and
E bk (t )hk (t ) | bk (t )hk (t ) 2t k , bk (t ) 1, bk 1
E 2Wkk 2Wkk 2 k (t ) | 2Wkk 2Wkk 2 k (t ) 2t k
(t ) k (t ) t k
2 k E k
k
k
k
35
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
t
2 k g k
k
.
9/6/99
(86)
Then we obtain
E (u (t )) E bk (t )hk (t ) | bk (t )hk (t ) 2t k
kL~ ( t )
Eb (t )h (t ) | b (t )h (t ) 2t
k
~
kL ( t )
k
k
k
k
1
Ebk (t )hk (t ) | bk (t )hk (t ) 2t k , bk (t ) a, bk b
4 kL~ (t ) ( a ,b ){1,1}2 ,
t
2Wkk k g k
~
kL ( t )
k
t 2Wkk
k g k
k
.
(87)
By noticing (A19), we have
v(t )
2
1
Wkj bk (t )b j (t )
2 kL~ (t ) jL~ (t )
W
~
~
kL ( t ) jL ( t )
2
W
~
kL ( t )
kk
b (t )b j (t )
kj k
2
W
~
~
kL ( t ) jL ( t ), j k
b (t )b j (t ) .
(88)
kj k
Its mean is
E (v(t )) 2
W
~
kL ( t )
kk
.
(89)
Then we obtain
E (u (t )) E (v(t ))
t
k g k
~
kL ( t )
k
t 2Wkk
k g k
k
.
(90)
~
Assume that every k L(t) has equal probability to be flipped. That is, Pr(k L (t ) | k L(t)) =
~
| L (t ) |/| L(t)|. Then
E (u (t )) E (v(t ))
~
tk
| L (t ) |
k g
| L(t ) | kL ( t )
k
t 2Wkk
k g k
k
.
(91)
Assume further that |L(t)| = J is fixed and each of the K bits has equal probability to be selected
into L(t). The expected metric reduction from (80) is
36
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
K
f (t ) E (f (t ))
L ( t ){1,..., K } J
1
9/6/99
E (u(t )) E (v(t ))
| L ( t )| J
1
~
t
K
| L (t ) |
k g k
J L (t ){1,..., K } J kL (t )
k
| L ( t )| J
t 2Wkk
k g k
k
.
(92)
The expected number t f of search steps is approximated t f f [b(0)] / f (t ) . In each step, the
computation of the GLAS detector accounts for the update of h(t) by (43). Since 2W can be
stored in memory, if ignoring the change of sign due to multiplication of bi(t) {1, 1}, the flip
of one bit needs K additions (if W has zero elements such as in an asynchronous channel, the
~
number of additions is smaller than K). Since there are | L (t ) | flipped bits in each step, then the
expected total number of additions per demodulated bit is
~
~
t f | L (t ) | K
f [b(0)] | L (t ) |
N
K
f (t )
1
tk
k g
kL ( t )
k
t 2Wkk
k g k
k
K
K 2
J Ak2
2
k 1
K
L ( t ) {1,..., K } J
K 2 K 2
J Ak
2
k
1
t
K
J min k g k
1 k K
L ( t ) {1,..., K } J
k
| L ( t )| J
1
| L ( t )| J
t 2Wkk
k g k
k
K
K 2
Ak2
2
k 1
tk
k g
| L ( t )| J ,1 k K
k
t 2Wkk
k g k
k
K 2 K 2
Ak
2
k
1
t
k g k
| L ( t )| J ,1 k K
k
K
K 2
Ak2
2
k 1
max Ak2 2 / 2
1 k K
min
| L ( t )| J ,1 k K
tk
min
min
min
| L ( t )| J ,1 k K
(93)
tk
K.
(94)
Therefore, we have shown the following proposition.
37
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Proposition 1: With random uniform initial, the expected per-bit computational complexity of
the GLAS detector is linear in the number of users.
The upper bond N b given by (94) shows the linear complexity of the GLAS detector. In what
follows, the approximated N in (93) is considered in the two special cases when the signature
waveforms are random binary and the channel is perfectly power-controlled. It is compared with
simulation results in Section VII.
If the signature waveforms are random binary, k and tk can be estimated by replacing Wkj2 and
|Wkj| with their means. Each chip sik of the random binary signature waveforms si = (si1, si2, …,
siM)T independently takes 1 / M and 1 / M with equal probability. It is easy to show that Rij
= s Ti s j for i j has mean E(Rij) = 0 and variance E ( Rij2 ) 1/M. When the processing gain M is
large, Rij ~ N(0, 1/M) and then E (| Rij |) 2 /( M ) . Hence, Wkj2 = AkAj/M and |Wkj| =
[ 2 /( M )] Ak A j for k j,
t k Ak2
2
M
Ak
t k 2Wkk Ak2
A
jL ( t ), j k
2
M
,
j
Ak
(95)
A
jL ( t ), j k
j
,
(96)
and
k2
2 2 K 2
Ak A j Ak2 2 .
M
j 1, j k
(97)
If further the channel is perfectly power-controlled, i.e. Ak = A, then the index of users can be
removed and
tk ~
t
M ( J 1) 2
M
t k 2Wkk ~
t 2W
k2 ~ 2
A2 ,
M ( J 1) 2
M
2( K 1) M / SNR 2 4
A .
M
(98)
A2 ,
(99)
(100)
38
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
~
t
~
M ( J 1) 2
M 2( K 1) M / SNR 2
,
9/6/99
(101)
and
~
t 2W
~
M ( J 1) 2
.
M 2( K 1) M / SNR 2
(102)
where
SNR
A
.
(103)
It follows from (93) that
K 2 K 2
N J Ak
2
k
1
K
L ( t ){1,..., K } J
1
| L ( t )| J
~
~ ~
t
t 2W
g ~ k g ~
kL ( t )
A 2 1 0.5 / SNR 2 K
= cK.
~ ~ ~
g ( t / ) g (( ~t 2W ) / ~)
(104)
It is easy to see that the constant c with the increasing J. Hence, the more the number of bits
updated at one step, the faster the convergence.
Since each bit flip takes K additions, N is also the expected total number of bit flips in tf steps
and thus the constant c in (104) is the percentage of bits that are expected to be flipped by the
GLAS detector. For example, if M = 1300, K = 1000, SNR = 3 dB, J = 5, then N 0.513K.
That is, only slightly more than a half of the K bits are expected to be flipped. In contrast, for
arbitrarily selected a, b {1, 1}K, E(||b a||1) = ½K. That is, a half of the K bits of a are
expected to be flipped to obtain the perfect demodulation b.
Finally, we mention that at the initial with given W and q, calculation of h(0) may need other
extra K additions per bit with the exception when the initial is an output of another detector and
h(0) is a byproduct.
V. TWO SPECIAL CLASSES OF LAS DETECTORS
The GLAS detector defines the family of LAS detectors, each of which is specified by a
sequence L(t), t 0. There are two special classes of LAS detectors: the wide-sense sequential
39
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
LAS detectors and the parallel LAS detectors. All properties of the GLAS detector in previous
section are applicable to this two classes.
A. Sequential LAS detectors
Before discussing the wide-sense sequential LAS detectors, we define the sequential LAS
detectors first.
Definition 15: If |L(t)| = 1 for t 0, the GLAS detector is said to be a sequential LAS (SLAS)
detector.
From (47), the kth threshold of a SLAS detector is fixed,
t kSLAS (t ) Wkk Ak2 .
(105)
From Theorem 14 and (105), we obtain the following corollary.
Corollary 15: If a SLAS detector converges to a fixed point bf that is not bounded, then
K
|| h(b f ) ||1 Ak2 ,
(106)
k 1
f (b f )
K
1
|| W 1 || Ak4 .
2
k 1
(107)
The thresholds in a SLAS detector are the lowest among all LAS detectors, and thus the upper
bounds of the residual at the fixed points are the lowest. As shown by (104), the SLAS detector is
slowest among all LAS detectors.
There are many choices in specifying L(t) for a SLAS detector. Two common choices are L(t) =
{t modulo K} and L(t) = {an index equiprobably select from {1, …, K}}. Theses two sequences
are statistically equivalent.
B. Wide-sense sequential LAS detectors
The Wide-sense sequential LAS (WSLAS) detectors including the SLAS detectors form a larger
class of LAS detectors. All properties of the WSLAS detectors are applicable to the SLAS
detectors.
Definition 16: If there exists an integer t0 0 such that |L(t)| = 1 for t t0, the GLAS detector
is said to be a wide-sense sequential LAS detector.
40
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Corollary 10 is applicable to the class of WSLAS detectors. One of the most interesting
properties of the WSLAS detectors is as follows.
Theorem 15: WSLAS(r) = LML(r), r K.
Proof: In the wide-sense sequential updating mode, for t t0, the threshold is tk(t) = Wkk for k =
1, …, K. For b WSLAS(r), due to (46),
hk Wkk , if bk 1,
hk Wkk , if bk 1,
bk(hk + bkWkk) 0, k {1, …, K}.
(108)
Since Wkk Ak2 and
K
hk Ak Rkj A j b j rk ,
j 1
(109)
we have
K
bk rk Rkj A j b j 0 ,
j 1, j k
k {1, …, K},
(110)
which implies b LML(r) due to Lemma 3, and therefore WSLAS(r) LML(r).
Since LML(r) WSLAS(r) according to Theorem 13, LML(r) = WSLAS(r).
Corollary 16: Pr(WSLAS = LML) = 1.
(Q.E.D.)
Corollary 10 and Theorem 15 yield the following corollary.
Corollary 17: For t t0 when a WSLAS detector operates as a SLAS detector, the thresholds set
up in (105) are necessary and sufficient for the WSLAS detector to converge to an LML point
with probability one with any W.
Definition 17: Let b(r) be demodulated by a detector with observation r. is said to be an
LML detector if b(r) LML(r) for r K.
Observation 7: (a) An LML detector is an SML detector; (b) the optimum (GML) detector is an
LML detector; (c) all WSLAS detectors including all SLAS detectors are LML detectors;
The LML detectors form a special class of detectors. Except the optimum detector, the class of
LML detectors have not been paid attention in literature. From the following theorem, we see a
key difference between LML and non-LML detectors. This theorem also shows how a non-LML
detector is improved by a WSLAS detector.
41
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Theorem 16: Let bWSLAS be a fixed point of a WSLAS detector with initial b, the output of
another detector. Then Pe(bWSLAS) Pe(b) where the equality holds iff Pr(b LML) = 1.
Proof: For r K, suppose that b LML(r). A WSLAS detector will finally become a
SLAS detector starting at step t0. Because b is not an LML point, starting from b, a WSLAS
detector generates a sequence of vectors b, b1, …, bN (the Hamming distance of two consecutive
vectors of this sequence may not be equal to one) such that bWSLAS = bN LML(r). Moreover, in
terms of Theorem 5, (r | b) < (r | b1) < … < (r | bN) = (r | bWSLAS). On the other hand, if
b LML(r), then b is a fixed point of the WSLAS detector, bWSLAS = b, and (r | bWSLAS) =
(r | b). Hence, (r | bWSLAS) (r | b) for r, and
Pr[(bWSLAS) = (b)] = Pr[(bWSLAS) = (b) | b LML]Pr(b LML)
+ Pr[(bWSLAS) = (b) | b LML]Pr(b LML)
= Pr(b LML).
(111)
Therefore, Pr[(bWSLAS) = (b)] = 1 iff Pr(b LML) = 1. By means of Lemma 4, Pe(bWSLAS)
Pe(b) where the equality holds iff Pr(b LML) = 1.
(Q.E.D.)
Theorem 16 is interesting in that if a detector does not achieve an LML detection with
probability one, the error probability of this detector can be reduced by a followed WSLAS
detector.
To understand better the LML detectors, we introduce the concept of local minimum error
probability. For r K, a detector b selects b(r) {–1, 1}K, which is associated with a
neighborhood N[b(r)]. A detector b is said to be in the neighborhood of the detector b,
denoting by b N(b), if b(r) N[b(r)] for r K except for some observations, of which
the collection has a zero probability measure. The detector b is said to achieve a local minimum
error probability if it achieves the minimum error probability among all detectors in its
neighborhood, i.e. Pe(b) Pe(b) for b N(b)\{b}.
Theorem 17: b achieves a local minimum error probability iff Pr(b LML) = 1.
Proof: Consider any detector b N(b). If Pr(b LML) = 1, then (r | b) (r | b) for all
r except for those observations whose collection has a zero probability measure. Due to Lemma
4, Pe(b) Pe(b) and thus Pe(b) is a local minimum.
42
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Suppose Pr(b LML) < 1. Consider a detector b N(b) such that (i) b(r) = b(r) for r
where b(r) LML(r); and (ii) b(r) N[b(r)]\{b} and (r | b) > (r | b) for r where b(r)
LML(r). Obviously, (r | b) (r | b) for r K, and Pr[(b) = (b)] = Pr(b LML)
< 1. Due to Lemma 4, Pe(b) < Pe(b). Clearly, b N(b), and therefore Pe(b) is not a local
minimum error probability.
(Q.E.D.)
Observation 8: Every LML detector (as well as all WSLAS detectors) achieves a local
minimum error probability, and vice versa.
There are many LML detectors. Not every local minimum error probability achieved by an LML
detector is lower than a non-local minimum error probability achieved by a non-LML detector.
However, for any detector that does not achieve an LML detection with probability one, in terms
of Theorem 16, its error probability can be reduced to a local minimum by a followed WSLAS
detector.
Besides the class of WSLAS detectors, only the optimum (GML) detector is known to achieve
an LML (actually GML) detection with probability one. As expected, the optimum detector
achieves the global minimum error probability. The well-known conventional detector,
decorrelating detector, and PIC detector were not claimed to achieve an LML detection with
probability one, and thus may not achieve a local minimum error probability. As a matter of fact,
as shown in the simulation of this paper, their error probabilities are reduced by followed
WSLAS detectors. Hence, they are not LML detectors in the simulated conditions.
C. An example of WSLAS detector
As we have seen, the more the bits are updated at one step, the faster the LAS detector
converges, but the larger are the error probability and the residual at a fixed point. As suggested
by Theorem 12, in general, we can design L(t) for t 0 such that |L(t)| is large at initial and
gradually diminishes to |L(t)| = 1. With such an index sequence, the LAS detector can converge
faster to better solutions. Clearly, this index sequence specifies a WSLAS detector. An example
is given below.
Suppose that the indices of K users are partitioned into J groups Mj(t) , j = 1, …, J, where
M1(t) + … + MJ(t) = K. If J = 1, there is one group of K users. If J = K, there are K groups of one
43
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
user. The bits are updated group by group in the order of group indices. According to (47), the
thresholds of users in the jth group is
t k (t )
| W
iM j ( t )
ki
| ,
for k Mj(t).
(112)
In order for the threshold to gradually decrease, the sizes of groups decrease whereas the
number of groups increases in general. For example, suppose K = 2N (though this is not
necessary), a LAS detector can operate in the following manner. At initial, let J = 1 and M1(0) =
{1, …, K}. Operate until it converges to a fixed point. Then let J = 2, M1(1) = {1, …, K/2} and
M2(1) = {K/2 + 1, …, K}. Operate until it converges to a fixed point. Repeat this procedure until
the LAS detector finally converges to a fixed point with J = N and Mk(N 1) = {k} for k {1,
…, K}. Clearly, this defines a WSLAS detector.
Each time converging to a fixed point, this WSLAS detector decrease thresholds once, thus
reducing error probability once according to Theorem 12.
The index sequence L(t) for t 0 determines the trajectory along which a LAS detector
converges from an initial to a fixed point. Different index sequence leads to a different fixed
point. Hence, L(t) for t 0 directly determines the performance of the LAS detector. In order to
adaptively find better index sequence, the EHE and FMD criteria are proposed in [39]. It is
demonstrated by simulation that under the EHE and FMD criteria the LAS detectors can
converge to much better solutions in few search steps.
Initial vectors are also important for the LAS detectors to converge to better fixed points. Since
a LAS detectors monotonically increases likelihood, the large the initial likelihood is, the better
the final demodulation is or the faster the LAS detector converges. Any other existing detector
can be used as an initial. The initial can also be randomly selected to meet requirement of low
computational complexity. To increase the chance to converge to a better fixed point, a LAS
detector can start from multiple random initial points. The final demodulation is the one
achieving the largest likelihood among all fixed points. The operation with multiple initials is
equivalent to increasing the number of tested hypotheses along multiple trajectories, thus
improving performance.
D. Parallel LAS detector
44
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
In a parallel LAS detector, all bits are updated at every search step.
Definition 18: If L(t) = {1, …, K} for t 0, the GLAS detector is a parallel LAS (PLAS)
detector.
The thresholds of the PLAS detector are time-invariant
K
t kPLAS(t ) | Wkj | .
(113)
j 1
Theorem 18: GLAS(r) PLAS(r), r K.
Proof: Consider the GLAS detector with any L(t), t 0. For r and b GLAS(r), according
~
to (53) bk hk (b) tk GLAS for k. Since t kGLAS (t ) t kPLAS(t ) for all k and t 0, we have
~ GLAS ~ PLAS
~
tk
tk
and thus bk hk (b) tk PLAS for k. Hence, b PLAS(r) and so GLAS(r)
PLAS(r) for r.
(Q.E.D.)
The following corollary is due to (113) and Theorem 14.
Corollary 18: If a PLAS detector converges to a fixed point bf that is not bounded, then
K
K
|| h(b f ) ||1 | Wkj | ,
(114)
k 1 j 1
K K
1
f (b ) || W 1 || | Wkj
2
k 1 j 1
f
2
| .
(115)
The thresholds in the PLAS detector are the highest among all LAS detectors, and thus the
upper bounds of the residual at the fixed point are also the highest. On the other hand, as shown
by (104), the PLAS detector has lowest computational complexity among all LAS detectors.
Definition 19: If there exists t0 0 such that L(t) = {1, …, K} for t t0, the GLAS detector
becomes a wide-sense parallel LAS (WPLAS) detector.
Corollary 18 is applicable to the class of WPLAS detectors.
E. Comparison with parallel interference cancellation
By comparison with the parallel interference cancellation (PIC) detector, we can further
understand the advantages of the LAS detectors.
45
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
The well-known parallel interference cancellation (PIC) detector [23] has the following
updating equation,
b(t + 1) = sgn[r (R I)Ab(t)]
(116)
which is shown in the Appendix equivalent to
if bk (t ) 1 and hk (t ) Wkk ,
1,
bk (t 1) 1,
if bk (t ) 1 and hk (t ) Wkk , k {1, …, K}.
b (t ), otherwise.
k
(117)
Clearly, compared with (46) and (105), the PIC detector is the same as the PLAS detector except
that the thresholds of the SLAS detector are used. It is because of the lower thresholds, unlike the
GLAS detector, the PIC detector can not avoid limit cycle. Note that
K
Wkk | Wkj | , k {1, …, K},
(118)
j 1
where all equalities are simultaneously true if and only if R = I. The thresholds used in the PIC
detector are lower than those of (113) that are sufficient and necessary for monotonic likelihood
ascent when all bits are allowed to be updated at each step. Hence, from Theorem 7, the
following corollary is obtained.
Corollary 19: For arbitrary R I, the PIC detector decreases likelihood at some stage with a
nonzero probability.
Moreover, the PIC detector suffers from a limit cycle.
Theorem 19: For R with Rkj = 0 for k or j L where L {1, …, K} is associated with R
in definition. Then there exists a region
D r K
| R
jL , j k
kj
|A j rk
| R
jL , j k
kj
|A j , k L
(119)
such that for r D, PIC(r) contains a limit cycle C = {b(1), …, b(T)} where bk(t + 1) = bk(t)
for k L.
Proof: For R with Rkj = 0 for k or j L, consider a vector b(t) {1, 1}K such that
sgn(Rkj) = bk(t)bj(t) for k, j L. For r D, at stage t,
K
bk (t )hk (t ) Wkk bk (t )Wkj b j (t ) bk (t ) Ak rk Wkk
j 1
46
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
bk (t ) Wkj b j (t ) bk (t ) Ak rk Wkk
jL
| W
jL , j k
kj
| bk (t ) Ak rk
Ak | Rkj | A j bk (t )rk
jL, j k
Ak | Rkj | A j | rk
jL, j k
|
< 0, k L.
(120)
In terms of (117), all bits whose indices are in L are flipped at step t, i.e. bk(t + 1) = bk(t) for k
L. At stage t + 1 we have
K
bk (t 1)hk (t 1) Wkk bk (t 1)Wkj b j (t 1) bk (t 1) Ak rk Wkk
j 1
bk (t 1) Wkj b j (t 1) bk (t 1) Ak rk Wkk
jL
bk (t ) Wkj b j (t ) bk (t ) Ak rk Wkk
jL
| W
jL , j k
Ak
kj
| bk (t ) Ak rk
| R
jL , j k
kj
| A j bk (t )rk
Ak | Rkj | A j | rk
jL, j k
|
< 0, k L.
(121)
In terms of (117), all bits whose indices are in L are flipped back at stage t + 1, i.e. bk(t + 2) =
bk(t + 1) = bk(t) for k L. Obviously, the bits bk for all k L are flipped at every stage, and so
the PIC detector does not converge to a fixed point. Being deterministic and time-invariant, the
PIC detector enters a limit cycle according to Lemma 1.
(Q.E.D.)
Corollary 20: For R with Rkj = 0 for k or j L where L {1, …, K} is associated with R
in definition. Then the PIC detector converges to a limit cycle with a nonzero probability.
47
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
The crosscorrelation matrices in Theorem 19 (Corollary 20) form a large class of
crosscorrelation matrices. Moreover, these matrices are not necessary for the PIC to converge to a
limit cycle with nonzero probability. There may exit a larger class of crosscorrelation matrices
such that the PIC converges to a limit cycle. The PIC detector indeed suffers from limit cycles.
Theorem 20: Let PIC(r) and PIC(r) be, respectively, the limit set and the fixed point set of the
PIC detector for r K. Then (i) PIC(r) = LML(r); and (ii) if CPIC(r) = PIC(r)\PIC(r) ,
then CPIC(r) contains only limit cycle points.
Proof: (i) A fixed point of b of the PIC detector satisfies (116) that is equivalent to (35). In
terms of Lemma 3, PIC(r) = LML(r). (ii) Since the PIC detector is deterministic and timeinvariant, by means of Lemma 1, the limit set of the PIC detector contains only either fixed
points or limit cycle points. Hence, CPIC(r) contains only limit cycle points if CPIC(r) .
(Q.E.D.)
Theorem 20 shows that the limit set PIC(r) of the PIC detector contains only LML points and
limit cycle points. Because the limit set of the PIC detector includes all the LML points, if the
initial is an LML point b(0) LML(r), then the PIC detector does not change the initial, i.e. bPIC
= b(0). On the other hand, once entering a limit cycle, the PIC detector keeps on the limit cycle.
Several drawbacks of the PIC detector are resulted from the existence of a limit cycle.
Lemma 6: Let b1 be a vector on a limit cycle of the PIC detector. There must exist a sequence of
mutual different vectors b2, …, bN such that N 2, ||bi bi+1||1 = 1, (r | bi) < (r | bi+1) for i = 1,
…, N1, and bN LML(r).
Lemma 6 indicates that the likelihood of any point on the limit cycle is smaller than that of a
LML point connected with it through a monotonic likelihood ascent sequence. Although such a
sequence exists, the PIC detector is unable to search out the likelihood-increased bN along the
sequence. On the other hand, starting from b1, a SLAS detector is capable of searching out bN
along this likelihood ascent sequence as shown by the following theorem.
Theorem 21: Let bSLAS be demodulated by a SLAS detector with initial bPIC which is
demodulated by the PIC detector. Then Pe(bSLAS) Pe(bPIC) where the equality holds iff Pr(bPIC
CPIC) = 0 where CPIC = PIC\LML.
Proof: By repeatedly applying Theorem 5, we obtain (r | bSLAS) (r | bPIC) for r.
If bPIC LML, then bSLAS = bPIC and (r | bSLAS) = (r | bPIC).
48
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
In what follow, we show that if bPIC CPIC, then (r | bSLAS) > (r | bPIC).
According to Theorem 20, CPIC is the set of limit cycle points of the PIC detector. In terms of
Lemma 6, for r and bPIC CPIC, there exists at least one monotonic likelihood ascent
sequence bPIC, b2, …, bN such that the Hamming distance of any two consecutive vectors is one
and bN LML(r). There may exist several such sequences l1(r), …, lM(r) with their ending
vectors of LML points. Let (r) LML denote the set of these ending vectors. For b (r),
(r | b) > (r | bPIC) because of Lemma 6. A SLAS detector searches only along a monotonic
likelihood ascent sequence, of which any two consecutive vectors have Hamming distance one,
and terminates search at an LML point. Clearly, stating from bPIC, a SLAS detector will search
along one of these sequence l1(r), …, lM(r) and produce the finally demodulated bSLAS (r).
Hence, (r | bSLAS) > (r | bPIC). This implies
Pr[(bSLAS) = (bPIC) | bPIC CPIC] = 0
(122)
Pr[(bSLAS) = (bPIC) | bPIC LML] = 1,
(123)
and
and therefore,
Pr[(bSLAS) = (bPIC)] = Pr[(bSLAS) = (bPIC) | bPIC CPIC]Pr(bPIC CPIC)
+ Pr[(bSLAS) = (bPIC) | bPIC LML]Pr(bPIC LML)
= Pr(bPIC LML) = 1 Pr(bPIC CPIC).
(124)
Hence, Pr[(bSLAS) = (bPIC)] = 1 iff Pr(bPIC CPIC) = 0. By means of Lemma 4, Pe(bSLAS)
Pe(bPIC) where the equality holds iff Pr(bPIC CPIC) = 0.
(Q.E.D.)
The proof of Theorem 21 describes how a SLAS detector can improve the PIC detector. A
SLAS detector can not improve the PIC detector if and only if the probability of the existence of
a limit cycle is equal to zero. This can be true in the following cases (i) when signature
waveforms are orthogonal, i.e. R = I; and (ii) when the initial of the PIC detector is an LML
point with probability one, i.e. Pr(bPIC(0) LML) = 1.
As indicated by Theorem 11, when its initial is an output of another detector, any LAS detector
never increases the error probability of the initial detector and may decrease the error probability
by giving better demodulation. In contrast, however, in the same situation the PIC detector may
deteriorate the performance of this detector by giving a worse demodulation because of the
existence of the limit cycle. The following observation presents a scenario.
49
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Observation 9: Consider R . Let each of sets li’s be the set of vectors on a limit cycle of
the PIC. Let Cmin {b | (b) max ali (a), i} be the set of all vectors that achieve maximum
likelihood on their limit cycles, respectively. Consider a detector b such that Pr(b LML
Cmin) = 1 and Pr(b Cmin) > 0. If bPIC is the demodulated vector of the PIC detector with initial
b where bPIC equiprobably takes a limit cycle point when trapped into a limit cycle, then Pe(bPIC)
> Pe(b).
Proof: In terms of Theorem 19, there exists a region D K such that Pr(r D) > 0, and
PIC(r) contains limit cycle points for r D. If b LML(r), then bPIC = b and so (r | b) =
(r | bPIC). If b Cmin(r), bPIC is a limit cycle point. In this case, Pr(bPIC b) > 0, and (r | b)
> (r | bPIC) when bPIC b. Hence, (r | b) (r | bPIC) for r. Due to Theorem 20, LML
Cmin = . We further have
Pr[(b) = ( bPIC)] = Pr[(b) = (bPIC) | b Cmin]Pr(b Cmin)
+ Pr[(b) = (bPIC) | b LML]Pr(b LML)
= Pr[(b) = (bPIC) | b Cmin]Pr(b Cmin) + Pr(b LML)
= {Pr[(b) = (bPIC) | bPIC = b, b Cmin]Pr(bPIC = b | b Cmin)
+ Pr[(b) = (bPIC) | bPIC b, b Cmin]Pr(bPIC b | b Cmin)}
Pr(b Cmin) + Pr(b LML)
= Pr(bPIC = b | b Cmin)Pr(b Cmin) + Pr(b LML)
½ Pr(b Cmin) + Pr(b LML)
< Pr(b Cmin) + Pr(b LML) = 1.
In terms of Lemma 4, Pe(b) < Pe(bPIC).
(125)
(Q.E.D.)
In contrast, in terms of Theorem 16, the follow observation is true.
Observation 10: Any WSLAS detector reduces the error probability of the non-LML detector b
in Observation 9. Any LAS detector will never increase the error probability of b.
Once the PIC detector converges to a limit cycle, the computation in the stages where likelihood
does not increase is wasted in terms of reduction of error probability because of Lemma 4.
Moreover, trapped into a limit cycle, the PIC detector does not have an adequate criterion to
terminate. Finally, though both operating in a parallel updating mode, a PLAS detector has less
complex computation than the PIC detector because the PIC detector does not use (43) to update
50
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
h(t) to reduce unnecessary computations. Specifically, at each step, the PLAS detector uses ||b(t +
1) b(t)||1K additions but the PIC detector always uses KK additions. Since the average ||b(t +
1) b(t)||1 along a trajectory of a PLAS detector is much smaller than K, the PLAS detector has
much simpler computation at each step in average without saying the possible ceaseless search of
the PIC detector on a limit cycle.
VI. OBSERVATION REGION OF FIXED POINT
A. Duality properties
It is interesting to see the observation region of a fixed point of a LAS detector because the
fixed region is actually the decision region of the LAS detector with accordingly given initials.
Theorem 22: Let bf be a fixed point of the GLAS detector. For r, denote (r) = {b(0) {–1,
1}K | GLAS: r, b(0) bf} the set of vectors that initiate the GLAS detector to converge to bf.
Then the fixed region V(bf) of bf is
V (b f ) {r K | (r ) , bkf rk k , k 1,...K }
(126)
where
k bkf
K
R
j 1, j k
kj
A j b jf max
min
b ( 0 ) ( r ) t t kf [ b ( 0 )], kL ( t )
| R
jL ( t ), j k
kj
(127)
| Aj
and t kf [b(0)] denotes the terminating step of the kth bit associated with initial b(0).
It is clear that for bf {–1, 1}K, V(bf) given in (126) is nonempty. In other words, any vector
can be a fixed point of any LAS detector with a nonzero probability. Like an LML region, the
fixed region V(bf) of a LAS detector is an open convex hull of K sides. Its kth side is on the
hyperplane rk bkf k and its vertex is at r = ( b1f 1, …,
bKf K)T. From Theorem 22, it is
straightforward to obtain the following corollary, which is a dual result of Corollary 13 about
fixed points of LAS detectors.
Corollary 21: Let b be a fixed point of two LAS detectors and with fixed regions V(b) and
V(b), respectively. (i) If t k (t ) t k (t ) for all k and t 0, then V(b) V(b); (ii) if t k (t ) < t k (t )
for all k and t 0, then V(b) V(b).
A fixed region of the PLAS and WSLAS detectors can be concisely given.
Corollary 22: The fixed regions of b of a PLAS detector and a WSLAS detector are
51
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
VPLAS(b) = {r K| b[r (R I)Ab] (|R| I)A1}
(128)
VWSLAS(b) = {r K| b[ r (R I)Ab] 0},
(129)
and
respectively, where the absolute value of matrix is element-wise and 1 is an all-one vector.
Proof: For a PLAS detector, L(t) = {1, …, K} for t 0. (127) becomes
k bk
K
Rkj A j b j
j 1, j k
K
| R
j 1, j k
kj
| Aj
(130)
which implies (128). For a PLAS detector, |L(t)| = 1 for t 0. (127) becomes
k bk
K
R
j 1, j k
kj
Aj b j ,
thus yielding (129).
(131)
(Q.E.D.)
The following theorem is dual with Theorem 15, Theorem 13 and Theorem 18.
Theorem 23: VLML(b) = VWSLAS(b) VGLAS(b) VPLAS(b).
Proof: For r VLML(b), b LML(r) = WSLAS(r) in terms of Theorem 15. Hence, r
VWSLAS(b) and so VLML(b) VWSLAS(b). Conversely, for r VLML(b), b WSLAS(r) =
LML(r). Hence, r VLML(b) and so VWSLAS(b) VLML(b). Therefore, VWSLAS(b) = VLML(b).
For r VLML(b), b LML(r). In terms of Theorem 13, LML(r) GLAS(r). Hence, b
GLAS(r), which implies r VGLAS(b) and thus VLML(b) VGLAS(b).
For r VGLAS(b), b GLAS(r). In terms of Theorem 18, GLAS(r) PLAS(r). Hence, b
PLAS(r), which implies r VPLAS(b) and thus VGLAS(b) VPLAS(b).
(Q.E.D.)
Although proved by applying the duality between the fixed point set and fixed region, Theorem
23 can be proved by comparing k in (127), as applied in the proof of Corollary 22. More
properties of LML points and LML regions are discussed in [36].
As a duality to Theorem 20, the following corollary is yielded from Theorem 20.
Corollary 23: Let VPIC(b) be observation region of a fixed point of the PIC detector. VPIC(b) =
VLML(b).
Similarly, an observation region of limit cycle points of the PIC detector can be defined as the
region where a limit cycle of the PIC exists. The limit cycle region of the PIC detector is
demonstrated in the next subsection for two-user channels.
52
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
B. Examples of two-user channels
In what follows, by two-user channels we demonstrate fixed regions of the PLAS and SLAS
detectors, and limit regions of the PIC detector.
Limit region of PIC detector: According to Theorem 20, the limit set of the PIC detector is
composed of fixed points and limit cycle points. In duality, the limit regions of the PIC detector
include the fixed regions and limit cycle regions. According to (117), the observation region
where b is a fixed point of the PIC detector satisfies bkhk + Wkk 0 for k. When K = 2, let =
R12, then
b1 (r1 A2 b2 ) 0
b2 (r2 A1b1 ) 0
(132)
which defines a fixed region of b of the PIC detector. For any r, the b that satisfies (132) is an
LML point. Hence, (132) is the LML region of b.
For two user systems, the length of a limit cycle can be only equal to two. Consider two points a
and b on a limit cycle of the PIC detector. Suppose that a1 = b1 and a2 = b2. Since the first bit
must be kept unchanged and the second must be flipped on the limit cycle at each step, in terms
of (117)
a1 (r1 A2 a2 ) 0
a2 (r2 A1a1 ) 0
(133)
b1 (r1 A2 b2 ) 0
.
b2 (r2 A1b1 ) 0
(134)
and
Here, (134) is equivalent to
a1 (r1 A2 a2 ) 0
,
a
(
r
A
a
)
0
1 1
2 2
(135)
of which the second inequality contradicts to the second inequality of (133). Similarly, if a1 = b1
and a2 = b2, there is a contradiction. Hence, it is impossible that two vectors differing by one bit
consist of a limit cycle.
If a limit cycle is composed of a and a, in terms of (117),
a1 (r1 A2 a2 ) 0
a2 (r2 A1a1 ) 0
(136)
53
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
and
a1 (r1 A2 a2 ) 0
a2 (r2 A1a1 ) 0
(137)
which gives an observation region defined in the following corollary.
Corollary 24: For two-user channels, iff a1a2 = sgn(), then a and a construct a limit cycle of
the PIC detector with the limit cycle region
| | A2 r1 | | A2
.
| | A1 r2 | | A1
(138)
Corollary 25: For two-user channels, iff = 0, Pr(CPIC = ) = 0.
If and only if = 0, the PIC detector converges to a limit cycle with zero probability.
Fixed region of a PLAS detector: For two-user channels, (128) produces
b1r1 A2 b1b2 | | A2
b2 r2 A1b1b2 | | A1
(139)
which defines the fixed region of b of the PLAS detector. The fixed region of the PLAS detector
is larger than and includes the fixed region of the PIC detector. However, the PLAS detector does
not have a limit cycle region.
Fixe region of a WSLAS detector: For two-user channels, (129) leads to (132). In other words,
for b, the fixed region of a WSLAS detector is the LML region of b, which is also the fixed
region of the PIC detector. However, the WSLAS detector does not have a limit cycle region.
Fig. 3 shows the observation space of the two-user channel with = 0.4, A1 = 1 and A2 = 0.6. As
shown in Fig. 3 (a), the fixed regions of a WSLAS detector, which are the LML regions, are
given by: VLML[(1,1)] = [A2, )[A1, ), VLML[(1,1)] = (, A2][A1, ), VLML[(1,1)] =
(, A2](, A1], and VLML[(1,1)] = [A2, )(, A1]. In the shaded region (A2,
A2)(A1, A1), both (1,1) and (1,1) are LML points, one of which is the GML point. The
line segment dividing the shaded region into two triangles is the boundary between decision
regions of (1,1) and (1,1), which is made by the optimum (GML) detector. In the upper shaded
triangle, (1,1) is the GML point and is assigned (1,1) by the optimum detector. In the lower
shaded triangle, (1,1) is the GML point and is assigned (1,1) by the optimum detector. Outside
54
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
the shaded region, there is only GML point, and therefore a WSLAS detector performs equally
well as the optimum detector. Only inside the shaded region, may a WSLAS detector perform
differently from the optimum detector because of the existence of two LML points.
As shown in Fig. 3 (a), the PIC detector has the same fixed region as that of a WSLAS detector.
However, PIC detector has a limit cycle region exactly given by the shaded region. In this shaded
region, (1,1) and (1,1) construct a limit cycle of length two. On this limit cycle, likelihood of
any point of (1,1) and (1,1) is smaller than the local maximum likelihood of any LML point of
(1,1) and (1,1). In summary, outside the shaded region, the PIC detector performs equally well
as a WSLAS detector (as well as the optimum detector). Inside the shaded region, if the initial is
either (1,1) or (1,1), the PIC detector converges to (actually does not change) the initial, and
thus performs equally well as a WSLAS detector with the same initial. However, if the initial is
either (1,1) or (1,1), the PIC detector is trapped into the limit cycle and performs worse than a
WSLAS detector.
As shown in Fig. 3 (b), the fixed regions of the PLAS detector are given by: VPLAS[(1,1)] = [0,
)[0, ), VPLAS[(1,1)] = (, 2A2][2A1, ), VPLAS[(1,1)] = (, 0](, 0], and
VPLAS[(1,1)] = [2A2, )(, 2A1]. Each of the fixed regions of the PLAS detector includes
the corresponding fixed region (LML region) of a WSLAS detector. Because of the enlargement
of the fixed regions compared with the LML regions, the PLAS detector has more fixed points
than a WSLAS detector in some regions. The two coordinate axes divides the enlarged shaded
region into four shaded rectangles. In the shaded rectangles located in the upper-left and lowerright quadrants, (1,1) and (1,1) are fixed points. In the shaded rectangle located in the upperright quadrant, (1,1), (1,1) and (1,1) are fixed points. In the shaded rectangle located in the
lower-left quadrant, (1,1), (1,1) and (1,1) are fixed points. Because the fixed regions are
enlarged, the area of the overlapped fixed region (i.e. the shaded region) becomes larger.
Moreover, the number of LML points is increased in the enlarged shaded regions in the upperright and lower-left rectangle. The enlargement of shaded region and the increased number of
LML points in the shaded region both increases error probability if initial is equiprobable.
Because the fixed regions are enlarged and the number of fixed points is increased in two shaded
rectangles, the PLAS detector expectedly converges much faster than a SLAS detector. However,
it is because of the enlargement of the fixed regions, the PLAS detector performs worse than a
55
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
WSLAS detector. Compared with the PIC detector, the PLAS detector (actually all LAS
detectors) does not have a limit cycle region.
VII. SIMULATIONS
In all simulations reported in this section, processing gain is M = 15, uniformly random binary
signature waveforms are used, and 10,000 trials are tested unless particularly specified. The
signal-to-noise ratio in decibel of the kth user is defined as
SNR k 10 log 10
Ak2
2
.
Examined is the performance of the SLAS detector, WSLAS detector, and PLAS detector with
comparison to the PIC detector, conventional detector, and decorrelating detector. In the SLAS
detector, bits are visited in the order of their indices, i.e., L(t) = {(t mod K) + 1}. The WSLAS
detector is the one defined in Section V. The conventional detector is defined by bc = sgn(r) and
the decorrelating detector is by bdec = sgn(R1r). If the PIC detector converges to a fixed point
within ten stages, the fixed point is the finally demodulated vector; otherwise, the PIC detector is
forced to stop at the tenth step and its output at the tenth step is the finally demodulated vector.
Whenever the decorrelating detector is used for comparison in a simulation, those sets of
signature waveforms, of which the crosscorrelation matrices are invertible, are eliminated.
A. BER versus number of users
In the following simulations, different initials are considered. Channels are perfectly powercontrolled with SNR of 5 dB.
Fig. 4 shows BER versus number of users. Initials of three LAS detectors and the PIC detectors
are random uniform. Since the PLAS detector has fixed regions larger than the corresponding
LML regions, PLAS detector performs worse than the PIC, SLAS, and WSLAS detectors. Due to
the instability of limit cycles, the PIC detector has a probability less than one to converge to LML
points. Hence, the PIC detector performs worse than the SLAS and WSLAS detectors that
converge to LML points with probability one.
In Fig. 5, initials of three LAS detectors and the PIC detectors are output of the conventional
detector. The PLAS detector neither improves nor worsens the BER of the conventional detector
56
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
for all numbers of users. This implies that the large fixed regions of the PLAS detector cover
corresponding decision regions of the conventional detector. On the other hand, the SLAS and
WSLAS detectors reduce the BER of the conventional detector for all numbers of users. This
means that the conventional detector is not an LML detector. In contrast, however, the PIC
detector decreases the BER of the conventional detector only for K 13, and increases the BER
for K 14. This is due to the existence of limit cycles of the PIC detector. When the number of
users is large, the limit cycle region becomes large and so the probability that the PIC detector
converges to a limit cycle is high even when the initial is output of the conventional detector. The
WSLAS detector performs slightly better than the SLAS detector.
In Fig. 6, initials of three LAS detectors and the PIC detectors are output of the decorrelating
detector. In the simulation, those signature waveforms whose crosscorrelation matrices are
invertible are eliminated. The PLAS detector does not change the output of the decorrelating
detector for all numbers of users. This implies that the fixed regions of the PLAS detector cover
corresponding decision regions of the decorrelating detector. On the other hand, the SLAS and
WSLAS detectors reduce the BER of the decorrelating detector for all numbers of users. This
means that the decorrelating detector is not an LML detector. With the initial of the decorrelating
detector, the PIC detector can decrease the BER of the conventional detector only for K 15.
Fig. 7 shows BER versus number of users. Initials of the PIC detector are uniformly random.
Initials of the three LAS detectors are output of the PIC detector. All the three LAS detectors
improve the performance of the PIC detector. Although the fixed regions of the PLAS detector
cover and are larger than the corresponding limit regions of the PIC detector, the PLAS detector
can improve the output of the PIC detector. The gain of the PLAS detector over the PIC detector
is obtained from the improvement of limit cycle points of the PIC detector. The improvement of
the SLAS and WSLAS detectors upon the output of the PIC detector also is due to the
improvement of the limit cycle points of the PIC detector. Because of the convergence to LML
points with probability one, the SLAS and WSLAS detectors perform better than the PLAS
detector.
In all the cases, the SLAS and WSLAS detectors outperform the PIC detector. This is due to the
fact that the SLAS and WSLAS detectors converge to LML points with probability one while the
PIC detector converges to a limit cycle with a nonzero probability. The regions of limit cycle
57
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
points of the PIC detector become large with the increasing number of users. In other words, the
probability for the PIC detector to converge to a limit cycle increases with the increasing number
of users. Hence, as shown in all Figs. 4-7, the outperformance of the SLAS and WSLAS
detectors over the PIC detector grows with the increasing number of users.
B. Computational complexity versus number of users
In the same conditions as in Figs. 4-7, the average number of additions per demodulated bit is
recorded. The results are shown in Figs. 8-11, respectively. The theoretical estimates of N for
the SLAS and PLAS detectors are also shown, which are given by (104) with |J| = 1 and |J| = K,
respectively. In running of the PIC detector, instead of the original (116), the updating equation
(117) is used and h(t) is updated by (43). Hence, in each stage, ||b(t + 1) b(t)||1K additions
instead of K2 are counted and thus the total number of additions per bit of the PIC detector shown
in Figs. 8-11 is less than what it should be if the original PIC updating equation were used.
As shown in Fig. 8, with random initials, the average additions per demodulated bit for the
SLAS and WSLAS detectors are linear in the number of users, i.e. approximately 0.55K for the
SLAS detector and 0.40K for the WSLAS detector. The average additions per demodulated bit
for the PLAS detector are nonlinear in the number of users with maximum of about 1.2. Both
theoretical estimates for the SLAS and PLAS detectors evaluated from (104) are fairly close to
the simulated results. In the simulation, the PIC detector has the number of additions per
demodulated bit growing with K2, which is close to 0.3K2, where we note that the PIC detector is
forced to terminate at the tenth stage if it does not converge to a fixed point before the tenth
stage.
As shown in Figs. 9, 10, and 11, when initials are outputs of the conventional detector and
decorrelating detector, the numbers of additions per demodulated bit of the three LAS detectors
and the PIC detector are slightly reduced. In both cases, the PLAS detector has the number of
additions per bit close to zero. In Fig. 11 when initials are output of the PIC detector, all three
LAS detectors have computational complexity close to that in the case when initials are random
uniform.
In summary, all the LAS detectors have average computational complexity linear in the number
of users with upper bound of about 0.67K – fewer than two third of bits are flipped.
58
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
C. BER and computational complexity versus SNR
In the following simulation, K = 12 users are considered. Channel is perfectly power-controlled.
Initials of the three LAS detectors and the PIC detector are output of the conventional detector.
Since the decorrelating detector is considered in the simulation, those signature waveforms of
invertible crosscorrelation matrices are eliminated.
Fig. 12 shows BER versus SNR. With the initial of the conventional detector output, the PLAS
detector has the same BER of the conventional detector in all SNR. This implies that for the
perfectly power-controlled channels, fixed regions of the PLAS detector cover corresponding
decision regions of the conventional detector. The PIC detector can slightly improve the
performance of the conventional detector. In contrast, the SLAS and WSLAS detectors, which
converge to LML points with probability one, considerably improve the performance of the
conventional detector. The larger the SNR, the greater the improvement. When SNR is low, due
to noise enhancement of inverse of crosscorrelation matrix R, the decorrelating detector performs
worse than the conventional, PIC, and LAS detectors. The performance of the decorrelating
detector becomes better as SNR increases.
The average additions per demodulated bit versus SNR are shown in Fig. 13. As we can see, the
average computational complexities of the three LAS detectors and the PIC detector are roughly
independent of SNR in the range of simulation.
D. Instant bit error rate
In this simulation, we consider BER at each instant n of bit flip. Note that several bits may be
flipped at one search step in the WSLAS, PLAS and PIC detectors. K = 12 users are considered.
Channels are perfectly power-controlled with SNR of 5 dB. Initials are random uniform. The
instant BER are averaged over 100 trials at each instant n of bit flip. The results are shown in Fig.
14. The short vertical segments on horizontal axis are average total numbers of flips per trial.
As shown in Fig. 14, the three LAS detectors monotonically reduce instant BER – in
expectation, every bit flip in the LAS detectors decreases metric value and increases likelihood,
and thus reducing BER. The average total numbers of bit flips over the 100 trials for the PLAS,
WSLAS, and SLAS are 1.18, 5.69, and 6.78, respectively, all of which are less than 8 – two third
59
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
of K = 12. The largest total numbers of bit flips among the 100 trials are, respectively, 6, 9, and
10, all of which are less than K = 12, the total number of users.
In contrast, the PIC detector does not guarantee the monotonic descent of the instant BER
because of the existence of limit cycles. With the forced termination at the tenth stage once the
PIC detector does not converge to a fixed point before the tenth stage, the average total number
of bit flips over the 100 trials is 35.39. The largest total number of bit flips among the 100 trials
is 109. Both are much larger than those of the LAS detectors.
E. Near-far performance
The performance of the three LAS detectors, PIC detector, conventional detector, and
decorrelating detector in near-far situation is examined by simulation. K = 12 users are
considered. Initials of the three LAS detectors and the PIC detector are random uniform. The
average signal power over all K users for every one trial is normalized such that
10 log 10 [k 1 Ak2 /( K 2 )] 15 (dB), which is produced as follows. First, we generate
K
~
2
) , a Gaussian random variable with mean zero and
Ak2 10SNR k / 10 A2 where SNRk ~ N (0, SNR
~
2
variance SNR
. Clearly, the SNR in dB for a user with energy Ak per bit is a Gaussian random
variable with mean SNR 10 log 10 ( A2 / 2 ) and standard deviation SNR. In the simulation,
SNR 15 dB is chosen. In every trial, the energy Ak per bit of the kth user is normalized such
~
K
that Ak2 A2 KAk2 / k 1 Ak2 . Hence, for every trial, we have exactly constant (rather than mean)
signal power averaged over the K users, i.e. 10 log 10 [k 1 Ak2 /( K 2 )] 15 (dB). Because of the
K
nonlinear normalization, SNR k 10 log 10 ( Ak2 / 2 ) is not a Gaussian random variable and its
standard deviation (SDV) is no longer SNR. In the simulation, the true SDV of SNR is estimated
from 10,000 trials over all K users. When the SDV of SNR is zero dB, the channel is perfectly
power-controlled.
As shown in Fig. 15, BERs of the conventional detector and the decorrelating detector
monotonically increase with the increasing SDV of SNR. In this sense, the conventional detector
and the decorrelating detector suffer from the near-far problem. In particular, with such a high
average signal power of 15 dB, the decorrelating detector performs worse than the SLAS and
60
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
WSLAS detectors when the SDV of SNR is greater than 6.5 dB, and even worse than the PIC
detector when the SDV of SNR is greater than 11 dB.
The BER of the PLAS detector slowly decreases with the increasing SDV of SNR. The BERs of
both the SLAS and WSLAS detectors as well as the PIC detector are convex up functions of the
SDV of SNR. The best operation point for them are far away from the point when the channel is
perfectly power-controlled. This can be explained as follows. When the energies of users deviate
from the point of perfect power control, the users of higher SNR have larger chances to be
correctly demodulated earlier, thus reducing average BER over all users. However, when the
SDV of SNR is too large, though the strong users can be correctly detected with high probability,
the left users of very low SNR will suffer from relatively strong noise, thus resisting the decrease
of the BER averaged over all users. In summary, all these search detectors are near-far resistant.
With a proper deviation of SNR, the SLAS and WSLAS detectors as well as the PIC detectors
can perform better for near-far channels than for the perfectly power-controlled channel.
Because of the convergence to LML points with probability one, the SLAS and WSLAS
detectors outperform the PIC detector in all situations.
VIII. CONCLUSIONS
The optimum detector achieves the global maximum likelihood detection and thus achieves
global minimum error probability. However, the optimum detector is impractical because its
computational complexity grows exponentially with the increasing number of users. Although
there have been many suboptimal detectors, none of them is really suboptimal in the sense of
achieving a local minimum error probability. The family of likelihood ascent search (LAS)
detectors proposed in this paper achieve subset maximum likelihood detection while their
expected per-bit computational complexity is linear in the number of users.
As expected, when only a subset of hypotheses are allowed to be tested due to the constraint on
computational complexity, the optimum detection in terms of minimization of error probability is
to select the hypothesis that achieves the maximum likelihood in each subset of hypotheses
assigned to a partitioned region. A higher likelihood of a nonzero probability measure in
detection implies a lower error probability. All LAS detectors guarantee to monotonically
increase likelihood at every search step, thus guaranteeing monotonic reduction of error
61
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
probability unless all bits reach their terminating step with probability one. Among them, the
wide-sense sequential LAS (WSLAS) detectors achieve local maximum likelihood detection and
thus achieve local minimum error probabilities. When following any detector, a LAS detector
may reduce and never increases the error probability of the detector. A WSLAS detector can
reduce the error probability of any detector to a local minimum if the detector does not achieve
local maximum likelihood detection with probability one. Except the optimum detector, none of
other well-known detectors are known to achieve local maximum likelihood detection with
probability one and thus may be improved by the LAS detector. The conventional detector,
decorrelating detector, and the parallel interference cancellation (PIC) detector are improved by
followed WSLAS detectors in simulations. This implies that they are not local maximum
likelihood detectors.
Because of the guaranteed monotonic likelihood ascent, for arbitrary crosscorrelation matrices
all LAS detectors converge to a fixed point in a finite number of steps with probability one and
they do not have limit cycles. The thresholds set up in the LAS detectors are necessary and
sufficient for monotonic likelihood ascent with probability one. In contrast, it is because of no
guarantee of monotonic likelihood ascent for any set of non-orthogonal signature waveforms, the
PIC detector converges to a limit cycle with a nonzero probability and can not achieve a local
maximum likelihood detection with probability one for a large class of crosscorrelation matrices.
We conjecture that in terms of expected computational complexity, the WSLAS detectors are
the computationally simplest detectors among the detectors that achieve local maximum
likelihood detection for arbitrary crosscorrelation matrices and arbitrary initials.
We conjecture that unless all signature waveforms are mutually orthogonal, the PIC detector
converges to a limit cycle with a nonzero probability.
Since all local maximum likelihood detectors including the optimum detector perform
differently only in the region where multiple local maximum likelihood regions are overlapped, it
is interesting to study the properties of local maximum likelihood points and their observation
regions.
Many signal recovery problems such as image restoration and reconstruction [40], symbol
detection from single carrier single user channels as well as multiple-input multiple-output
62
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
channels, etc. can be formulated same as the problem of CDMA multiuser detection. The results
developed in this paper are potentially applicable to them.
APPENDIX
Derivation of (3):
In terms of (1), (2) can be written
dk
j 1
i
y k (t ) kj (t ) Ak s k (t t k jk iTb )bk (i ) nk (t )
dk
i j 1
kj
(t )s k (t t k jk iTb )Ak bk (i) nk (t )
(A1)
For the up-link transmission, the base station receives the following baseband signal from K
users,
K
K
dk
y (t ) y k (t ) n(t ) kj (t )s k (t t k jk iTb )Ak bk (i) n(t ) .
k 1
(A2)
k 1 i j 1
The mth sample in the lth bit period is taken at time t = mTb + lTc + c with c (0, Tc),
yl (m)
K
dk
i k 1 j 1
kj
(mTb lTc c)s k [( m i)Tb lTc c t k jk ] Ak bk (i) n(mTb lTc c)
nl ( m )
(A3)
for l = 0, …, M 1. Consider the samples in the tth bit period (now t denotes the index of bit),
y l (t )
0
K
t
K
dk
lT c)s [(t i )T
(tT
i t 1 k 1 j 1
kj
b
c
k
b
lTc c t k jk ] Ak bk (i ) nl (t )
kj ( t )
dk
kj (t ) s k (iTb lTc c t k jk ) Ak bk (t i) nl (t )
i 1 k 1 j 1
i)
s (jmk
0
K
dk
kj (t ) s k (iTb lTc c t k jk ) Ak bk (t i) nl (t )
i 1 k 1 j 1
i)
s (jmk
0 K dk
i)
Ak bk (t i ) nl (t )
kj (t )s (jmk
i 1 k 1 j 1
(i )
C mk
(t )
63
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
0
9/6/99
K
(i )
C mk
(t ) Ak bk (t i ) nl (t )
(A4)
i 1 k 1
which in matrix form is (3).
(Q.E.D.)
Proof of equivalence between (3) and (4) or (5)
Let y R (t ) Re( y(t )) ,
y I (t ) Im( y(t )) , C (Ri ) (t ) Re(C (i ) (t )) , C (Ii ) (t ) Im( C (i ) (t )) , nR(t) =
Re(n(t)), and nI(t) = Im(n(t)). Further denote y (t ) [y TR (t ) y TI (t )]T , C ( i ) (t )
[C (Ri )T (t ) C (Ii )T (t )]T , and n(t ) [n TR (t ) n TI (t )]T where the real and imaginary parts of the noise
vector are independent. We have
y (t ) C ( 0) (t ) Ab (t ) C (1) (t ) Ab (t 1) n(t ) ,
t = 0, …, N 1.
(A5)
~
~ [n T (0) ... n T ( N )]T ,
~
b [b T (0) ... b T ( N 1)]T ,
Let
y [y T (0) ... y T ( N )]T ,
n
~
A diag [ A1 AK A1
C ( 0) (0)
0
0
( 0)
(1)
C (1) C (1) 0
~
S
0
0
0
AK ] , and
,
(0)
C ( N )
0
0
then we have
~~~ ~
~
y S Ab n
(A6)
which has the same form of (4).
(Q.E.D.)
Proof of Observation 2:
There are totally 2K hypotheses in {1, 1}K. Consider all possible combinations. There are
= 2K regions each containing one element of {1, 1}K. There are
2K
1
regions each containing two
2K
2
element of {1, 1}K, etc. It is easy to see that the largest possible total number of regions is
2K 2 2K 2K
K
K
(1 1) 2 1 2 2 1 .
m1 m
m 0 m 0
2K
K
(A7)
(Q.E.D.)
64
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Proof of Theorem 2:
From (19), we obtain
Pe (b SML ( A)) Pe (b SML ( B))
1
2K
1
2K
U R \ R
1
2K
(r | b)]dr
[max (r | b) max
B
U R b
b
A
[maxB (r | b) maxA (r | b)]dr
b
b
(r | b)]dr
[max (r | b) max
B
U R b
b
(A8)
A
which implies (22).
(Q.E.D.)
Proof of Corollary 2:
(a) Since {1, 1}K for U, by means of Theorem 2,
Pe (b SML ) Pe (b GML )
1
2K
[ max
K
U R b{1,1}
(r | b) max (r | b)]dr
b
Pe (b GML )
(A9)
where
R {r R | max K (r | b) max (r | b)} .
b{1,1}
(A10)
b
(b) If bGML for U, then
max (r | b) max K (r | b) , r R
b
b{1,1}
and so Pr(r R ) = 0, U. This implies Pe(bSML) = Pe(bGML) by means of (A8). (Q.E.D.)
Proof of Corollary 3:
Since A B implies maxB (r | b) maxA (r | b) , the result follows from Theorem 2.
b
b
(Q.E.D.)
Proof of Theorem 3:
By applying Corollary 1, we note that = is identical for U. We obtain
65
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
| |
Pc (b GML ( ))
K
U 2
Pe (b ISML ) 1
1
| |
Pc (b GML ( ))
K
2
1
| |
[1 Pe (b GML ( ))]
2K
1 | | | |
K Pe (b GML ( )) .
K
2
2
(A11)
(Q.E.D.)
Proof of Lemma 1:
Consider the sequence {b(t )}t0 generated by (r). Since there are totally 2K different vectors in
{1, 1}K, there exist t0 1 and 1 T t0 such that b(t0) = b(t0 T) where t0 2K. According to
the definition of the deterministic time-invariant detectors, the vector b(t0 + 1) generated based
on r and b(t0) is the same as b(t0 T + 1) based on the same r and b(t0 T) = b(t0), i.e., b(t0 + 1)
= b(t0 T + 1). Repeating this procedure, we can easily see that b(t) = b(t T ) for t t0. This
implies that after at most 2K (due to t0 2K) search steps, (r) converges to either a fixed point if
T = 1, or a limit cycle with length 2 T 2K.
(Q.E.D.)
Proof of Lemma 2:
For r, the initial metric f[b(0)] is finite. Since the number of elements of {1, 1}K is finite, the
number of values that f(b) for b {1, 1}K can take is finite and thus f(b) is finite. Hence, for
b(t +1) b(t), f[b(t)] f[b(t + 1)] where > 0 independent of b(t) and b(t + 1) can not be
arbitrarily small.
Suppose that {b(t )}t0 does not converge to a fixed point. That is, there exists a subsequence
{t0, t1, } in {0, 1, } such that b(tj + 1) b(tj) with f[b(tj + 1)] < f[b(tj)], and b(tj + 1) = b(tj + 2)
= = b(tj+1) with f[b(tj + 1)] = f[b(tj + 2)] = = f[b(tj+1)] for j = 0, 1, . For such a sequence,
f [b(0)] f [b(t 0 )]
f [b(t 0 )] f [b(t 0 1)] f [b(t 0 1)]
f [b(t 0 )] f [b(t 0 1)] f [b(t1 )]
66
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
f [b(t 0 )] f [b(t 0 1)] f [b(t1 )] f [b(t1 1)] f [b(t1 1)]
1
{ f [b(t i )] f [b(t i 1)]} f [b(t1 1)]
i 0
n
{ f [b(t i )] f [b(t i 1)]} f [b(t n 1)]
i 0
n f [b(t n 1)] ,
(A12)
as n . This contradicts that both f[b(0)] and f[b(tn + 1)] are finite. Hence, {b(t )}t0 converges
to a fixed point in a finite number of steps.
(Q.E.D.)
Proof of Corollary 4:
Lemma 2 implies,
Pr {b(t 1) b(t )} r 1 , r
te 0 t te
(A13)
and thus
Pr {b(t 1) b(t )} E Pr {b(t 1) b(t )} r 1
t e 0 t t e
te 0 t te
where the expectation is taken over r.
(A14)
(Q.E.D.)
Proof of Lemma 3:
In terms of (40), the negative gradient of f at b is h(b) = Wb + q. Consider bk = b 2bkek
N(b) for k {1, …, K}. Denote bk = bk b = 2bkek. The metric difference from (44) is
f (b k ) f (b) (b k b) T [h(b)
1
W(b k b)]
2
2bk e Tk [h(b) bk We k ]
2bk [hk (b) bk Wkk ] 0
(A15)
where hk(b) is the kth component of h(b). Since W = ARA and q = Ar,
K
hk (b) bkWkk Wkj b j Ak rk bkWkk
j 1
67
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
K
Ak rk Rkj A j b j
j 1, j k
9/6/99
(A16)
which along with (A15) yields (35) in matrix form. The converse is obvious.
(Q.E.D.)
Proof of Theorem 5:
Obviously, if b(t + 1) = b(t), (t + 1) = (t). In what follows, we prove that if b(t + 1) b(t),
(t + 1) > (t) or equivalently f(t) < 0. Assume that L(t) is nonempty. Since only those bits
whose indices are in L(t) are updated at step t, the ith component of b(t) for iL(k) is bi(t) =
bi(t + 1) bi(t) = 0, and therefore
b (t )e
b(t )
j
jL ( t )
.
j
(A17)
where bj(t) {2, 0, 2} depends on whether the condition of (49) is true for the jth bit. From
(45) we have
g(t ) W
b (t )e
j
jL ( t )
b (t )W
i
j
jL ( t )
(A18)
j
and so
W
g k (t )
kj
jL ( t )
b j (t ) , k {1, …, K},
(A19)
where gk(t) is the ith component of g(t) and Wj is the jth column vector of W. The metric change
at step t according to (44) is
b (t )e
f (t )
k
kL ( t )
T
k
1
h(t ) g(t )
2
1
b (t ) h (t ) 2 g
k
kL ( t )
k
k
(t ) .
(A20)
Since the possible values of bj(t) for j L(t) are –2, 0 and 2,
t k (t )
1
2
| w
jL ( t )
| w
jL ( t )
kj
kj
|
1
2
| w
jL ( t )
b j (t ) |
1
|
2
kj
|| b j (t ) |
w
jL ( t )
kj
b j (t ) |
1
| g k (t ) | .
2
(A21)
Therefore, for any k L(t) and bk(t) 0 we have:
68
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
(a) if the kth bit is flipped from bk(t) = 1 to bk(t + 1) = 1, then bk(t) = 2. Since hk(t) + ½ gk(t)
hk(t) + ½ gk(t) hk(t) + tk(t), the inequality hk(t) > tk(t) is sufficient for bk(t)[hk(t) + ½
gk(t)] < 0;
(b) if the kth bit is flipped from bk(t) = 1 to bk(t + 1) = 1, then bk(t) = 2. Since hk(t) + ½
gk(t) hk(t) ½ gk(t) hk(t) tk(t), the inequality hk(t) < tk(t) is sufficient for bk(t)[hk(t) +
½ gk(t)] < 0.
Since any nonzero updatebk(t) 0 in the GLAS detector is either the case (a) or the case (b),
due to (A20), f(t) < 0 if b(t + 1) b(t).
(Q.E.D.)
Proof of Observation 6:
For r K, denote {b(r,t)} the sequence generated by the GLAS detector with a fixed point
bf(r) such that b(r,t) = bf(r) for t tf(r) with some tf(r) 0. Denote (r, t) = {b(r,0), …, b(r,t)}
and define U(t) = {(r, t) | r K}. For (t) U(t), let R(t)(t) = {r K | (r, t) = (t)}.
Clearly, at t 0, K is partitioned by R(t)(t) each associated with a subset (t) of hypotheses.
For r R(t)(t), the demodulated b(r,t) (t) achieves the SML solution of subset (t) due to
Theorem 5. Hence, the GLAS detector is an SML detector over (r, t ) 0 t b( ) at t 0.
(Q.E.D.)
Proof of Theorem 14:
For t t kf and k L(t), in terms of the given conditions, | hk (b f ) | t k (t ) . That is,
| hk (b f ) |
min {t k (t )}
(A22)
t t kf , kL ( t )
which implies (73) for || h(b f ) ||1 k 1| hk (b f ) | .
K
By means of (41) and (A22),
f (b f )
1 T f
h (b ) W 1h(b f )
2
1
|| W 1 |||| h(b f ) || 2
2
K
1
|| W 1 || | hk (b f ) | 2
2
k 1
69
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
K
1
|| W 1 || min
{t k2 (t )} .
f
t
t
,
k
L
(
t
)
2
k
k 1
9/6/99
(A23)
(Q.E.D.)
Proof of Theorem 13:
According to (47), tk(t) Wkk for k L(t). If b LML(r), due to Lemma 3 the term in
parenthesis of (A16) is true for k {1, …, K}, which is equivalent to (A15). From (A15),
if bk 1,
hk (b) Wkk t k ,
hk (b) Wkk t k , if bk 1,
which by means of (46) implies that b GLAS(r). Hence, LML(r) GLAS(r).
(A24)
(Q.E.D.)
Derivation of (117):
It follows from (116) that
b(t+1) = sgn[Ar A(R I)Ab(t)]
= sgn[q Wb(t) + A2b(t)]
= sgn[h(t) + A2b(t)]
(A25)
or equivalently,
bk(t+1)[hk(t) + Wkkb(t)] > 0, k {1, …, K},
which yields (117).
(A26)
(Q.E.D.)
Proof of Lemma 6:
Since LML(r) PIC(r) due to Theorem 20, b1 LML(r) (otherwise the PIC detector would
stop search at b1), which implies that there exists a vector b2 N(b1) such that ||b1 b2||1 = 1 and
(r | b1) < (r | b2). If b2 LML(r), there exists a vector b3 N(b1) such that ||b2 b3||1 = 1 and
(r | b2) < (r | b3). This procedure can be repeated until an LML point bN is reached.
(Q.E.D.)
Proof of Theorem 22:
Consider bf {1, 1}K and r K such that (r) . For b(0) (r), from (52) and
(53) we have
70
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
bkf hk (b f ) min
{t k (t )} 0 .
f
9/6/99
(A27)
t t k , kL ( t )
Since
K
bkf hk (b f ) bkf Wkj b jf qk
j 1
bkf Ak2 bkf Ak
K
R
j 1, j k
Ak2 bkf Ak rk
kj
A j b jf Ak rk
K
R
j 1, j k
kj
A j b jf
(A28)
and
t k (t )
| W
jL ( t )
kj
| | Wkk |
| W
jL ( t ), j k
kj
| Ak2 Ak
| R
jL ( t ), j k
kj
| Aj ,
(A27) can be written as
bkf rk
K
R
j 1, j k
kj
A j b jf min
f
t tk ,kL ( t )
| R
jL ( t ), j k
kj
| Aj
which implies (126).
(A29)
(Q.E.D.)
REFERENCES
[1] S. Verdú, Multiuser detection, Cambridge University Press, New York, 1998.
[2] S. Verdú, “Multiuser detection,” in Advances in Statistical Signal Processing: Signal Detection, H.
V. Poor and J. B. Thomas, Eds. Greenwich, CT: JAI Press, 1993, pp. 369-410.
[3] A. Duel-Hallen, J. Holtzman, and Z. Zvonar, “Multiuser detection for CDMA systems,” IEEE
Personal Commun., pp. 46-58, Apr. 1995.
[4] S. Moshavi, “Multi-user detection for DS-CDMA communications,” IEEE Commun. Mag., pp. 124136, Oct. 1996.
[5] S. Verdú, "Minimum probability of error for asynchronous Gaussian multiple-access channels," IEEE
Trans. Inform. Theory, vol. IT-32, pp.85-96, Jan. 1986.
[6] S. Verdú, "Optimum, multiuser asymptotic efficiency," IEEE Trans. Commun, vol. COM-34, pp.
890-897, Sept. 1986.
[7] S. Ulukus and R. Yates, “Optimum multiuser detection is tractable for synchronous CDMA systems
using M-sequences,” IEEE Commun. Lett., vol. 2, no. 4, pp. 89-91, 1998.
71
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
[8] Z. Xie, C. Rushforthm, and R. Short, "Multiuser signal detection using sequential decoding," IEEE
Trans. Commun., vol. 38, pp. 578-583, May 1990.
[9] Z. Xie, C. Rushforthm, R. Short, and T. K. Moon, "Joint signal detection and parameter estimation in
multiuser communications," IEEE Trans. Commun., vol. 41, pp.1208-1215, Aug. 1993.
[10] L. Wei and C. Schlegel, "Synchronous DS-SSMA with improved decorrelating decision-feedback
multiuser detector," IEEE Trans. Veh. Technol., vol. 43, pp. 767-772, Aug. 1994.
[11] L. Wei, L. K. Rasmussen, and R. Wyrwas, "Near optimum tree-search detection schemes for bitsynchronous multiuser CDMA systems over Gaussian and two-path Rayleigh-fading channels," IEEE
Trans. Commun., vol. 45, pp. 691-700, June 1997.
[12] R. Lupas and S. Verdú, "Linear multiuser detectors for synchronous code-division multiple-access
channels," IEEE Trans. Inform. Theory, vol. 35, pp. 123-136, Jan. 1989.
[13] R. Lupas and S. Verdú, "Near-far resistance of multiuser detectors in asynchronous channels," IEEE
Trans. Commun., vol. 38, pp. 496-508, Apr. 1990.
[14] K. S. Schneider, “Optimum detection of code division multiplexed signals,” IEEE Trans. Aerospece
Elect. Sys., vol. AES-15, no., Jan. 1979, pp. 181-185.
[15] Z. Xie, R. T. Short, and C. K. Rushforth, “A family of suboptimum detectors for coherent multiuser communications,” IEEE JSAC, vol. 8, no. 4, May 1990, pp. 683-690.
[16] A. J. Viterbi, “Very low rate convolutional codes for maximum theoretical performance of spreadspectrum multiple-access channels,” IEEE JSAC, vol. 8, no. 4, May 1990, pp. 641-649.
[17] Y. C. Yoon, R. Hohno, and H. Imai, “Combination of an adaptive array antenna and a canceller of
interference for direct-sequence spread-spectrum multiple-access system,” IEEE J. Select. Areas
Commun., vol. 8, May 1990, pp. 675-682.
[18] A. Duel-Hallen, "Decorrelating decision-feedback multiuser detector for synchronous code-division
multiple-access channel," IEEE Trans. Commun., vol. 41, Feb. 1993, pp. 285-290.
[19] A. Duel-Hallen, “A family of multiuser decision-feedback detectors for asynchronous code-division
multiple access channels,” IEEE Trans. Commun., vol. 43, no.2/3/4, Feb./Mar./Apr., 1995, pp. 421-434.
[20] A. Klein, H. K. Kaleh, and P. W. Baier, “Zero forcing and minimum-mean-square-error equalization
for multiuser detection in code-division multiple-access channels,” IEEE Trans. Vehic. Tech., vol. 45, no.
2, May 1996, pp. 276-287.
[21] M. K. Varanasi, “Decision feedback multiuser detection: a systematic approach,” IEEE Trans.
Inform. Theory, vol. 45, no. 1, Jan. 1999, pp. 219-240.
72
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
[22] M. K. Varanasi and B. Aazhang, "Multistage detection in asynchronous code-division multipleaccess systems," IEEE Trans. Commun., vol. 38, Apr. 1990, pp. 509-519.
[23] M. K. Varanasi and B. Aazhang, "Near-optimum detection in synchronous code-division multiple
access systems," IEEE Trans. Commun., vol. 39, May 1991, pp. 725-736.
[24] R. Kohno et al., “Combination of an adaptive array antenna and a canceller of interference for
direct-sequence spread-spectrum multiple-access system,” IEEE JSAC, vol. 8, no. 4, May 1990, pp. 675682.
[25] P. Patel and J. Holtzman, “Performance comparison of a DS/CDMA system using a successive
interference cancellation (IC) scheme and a parallel IC scheme under fading,” in Proc. ICC’94, New
Orleans, LA, Ma 1994, pp. 510-514.
[26] T. R. Giallorenzi and S. G. Wilson, “Decision feedback multiuser receivers for asynchronous
CDMA systems,” in Proc. IEEE Globecom’93, Houston, TX, Dec. 1993, pp. 1677-1682.
[27] S. Moshavi, “Multistage linear detectors for DS-CDMA communications,” Ph.D. dissertation, Dept.
Elect. Eng., City Univ. New York, NY, Jan. 1996.
[28] D. Divsalar, M. Simon, and D. Raphaeli, “Improved parallel interference cancellation for CDMA,”
IEEE Trans. Commun., vol. 46, pp. 258-268, Feb. 1998.
[29] C. Hegarty and B. Vojcic, “Two-stage multiuser detection for noncoherent CDMA,” in Proc. 33rd
Allerton Conf. Communication, Control and Computing, Monticello, IL, Oct. 1995, pp. 1063-1072.
[30] S. D. Gray, M. Kocic, and D. Brady, “Multiuser detection in mismatched multiple-access channels,”
IEEE Trans. Commun., vol. 43, pp. 3080-3089, Dec. 1995.
[31] V. Ghazi-Moghadam, L. B. Nelson, and M. Kaveh, “Parallel interference cancellation for CDMA
systems,” in Proc. 33rd Annu. Allerton Conf. Communication, Control, and Computing, Oct. 1995, pp.
216-224.
[32] Z. L. Shi, W. Du, and P. F. Driessen, ”A new multistage detector for synchronous CDMA
communications,” IEEE Trans. Commun., vol. 44, pp. 538-541, May 1996.
[33] R. M. Buehrer and B. D. Woener, “Analysis of adaptive multistage interference cancellation for
CDMA using an improved Gaussian approximation,” IEEE Trans. Commun., vol. 44, pp. 1308-1321,
Oct. 1996.
[34] X. Zhang and D. Brady, “Asymptotic multiuser efficiency for decision-directed multiuser
detection,” IEEE Trans. Inform. Theory, vol. 44, pp. 502-515, Mar. 1998.
[35] R. M. Beuhrer and S. P. Nicoloso, “ Comments on ‘partial parallel interference cancellation for
CDMA’,” IEEE Trans. Commun., vol. 47, no. 5, pp. 658-661, May 1999.
73
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
[36] Y. Sun, “Local maximum likelihood points in CDMA multiuser detection,” to be submitted to IEEE
Trans. on Information Theorem.
[37] Y. Sun and L. Tong, “Channel equalization for wireless OFDM systems with ICI and ISI,” in Proc.
IEEE Int. Conf. on Commun., ICC'99, June 6-10, 1999, Vancouver B.C., Canada.
[38] H. L. Van Trees, Detection, Estimation, and Modulation Theory – Part I Detection, Estimation, and
Linear Modulation Theory, John Wiley & Sons, New York, 1968.
[39] Y. Sun, "Eliminating-highest-error and fastest-metric-descent criteria and iterative algorithms for
bit-synchronous CDMA multiuser detection," in Proc. IEEE Int. Conf. on Comm., ICC'98, Atlanta,
Georgia, June 7-11, 1998, pp. 1576-1580.
[40] G. Demoment, "Image reconstruction and restoration: overview of common estimation structures
and problems," IEEE Trans. on Acoust., Speech, Signal Processing, Vol. 37, No. 12, pp. 2024-2036, Dec.
1989.
[41] Y. Sun, "A generalized updating rule for modified Hopfield neural network," in Proc. IEEE Int.
Conf. on Neural Networks, ICNN’97, Houston, Texas, June 9-12, 1997, pp. 1227-1230.
[42] Y. Sun, “A generalized updating rule for modified Hopfield neural network for quadratic
optimization,” Neurocomputing, 19 (1998), pp. 133-143.
74
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
Za2
Za1
9/6/99
Zb1
Za3
Zb4
Zb3
Zb2
Zb5
Fig. 1. Decision regions in observation space K; left: of detector ; right: of detector .
Function g(x)
6
5
4
g(x)
3
2
1
g(x)
x
0
-1
-5
-4
-3
-2
-1
0
x
1
2
3
4
5
Fig. 2. Function g(x).
75
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
r2
9/6/99
r2
++
++
+
+
0
0
r1
+
r1
+
(a)
(b)
Fig. 3. The observation space of the two-user channel with = 0.4, A1 = 1 and A2 = 0.6. (a) Fixed
region (LML region) of a WSLAS detector as well as the PIC detector. In the shaded region, the
PIC detector has a limit cycle composed of (1,1) and (1,1). (b) Fixed region of the PLAS
detector.
Bit error rate vs. number of users
0
10
PLAS
PIC
BER
WSLAS
SLAS
-1
10
-2
10
2
4
6
8
10
12
14
16
18
20
K
Fig. 4. BER versus K. Initials are random uniform. (M = 15; signature waveforms are random
uniform binary; SNR = 5 dB; the system is perfectly power-controlled.)
76
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Bit error rate vs. number of users
0
10
PIC
BER
PLAS = Conv.
-1
10
-x- SLAS
-+- WSLAS
-2
10
2
4
6
8
10
12
14
16
18
20
K
Fig. 5. BER versus K. Initials are output of the conventional detector. (M = 15; signature
waveforms are random uniform binary; SNR = 5 dB; the system is perfectly power-controlled.)
Bit error rate vs. number of users
0
10
PLAS = Decor.
PIC
BER
-x- SLAS
-+- WSLAS
-1
10
-2
10
2
4
6
8
10
12
14
16
18
20
K
Fig. 6. BER versus K. Initials are decorrelating detector. (M = 15; signature waveforms are
random uniform binary; SNR = 5 dB; the system is perfectly power-controlled.)
77
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Bit error rate vs. number of users
0
10
SLAS
PIC
BER
PLAS
WSLAS
-1
10
-2
10
2
4
6
8
10
12
14
16
18
20
K
Fig. 7. BER versus K. Initials are PIC detector. (M = 15; signature waveforms are random
uniform binary; SNR = 5 dB; the system is perfectly power-controlled.)
Computational complexity vs. number of users
80
70
60
Additions/bit
50
40
PIC
-x-+---.-.
-o-
30
20
SLAS
WSLAS
SLAS analytic
PLAS analytic
PLAS
10
0
2
4
6
8
10
12
14
16
18
20
K
Fig. 8. Computational complexity versus K. Same conditions as in Fig. 3.
78
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Computational complexity vs. number of users
80
70
60
Additions/bit
50
40
PIC
30
-x- SLAS
-+- WSLAS
-o- PLAS
20
10
0
2
4
6
8
10
12
14
16
18
20
K
Fig. 9. Computational complexity versus K. Same conditions as in Fig. 4.
Computational complexity vs. number of users
80
70
60
Additions/bit
50
40
PIC
30
-x- SLAS
-+- WSLAS
-o- PLAS
20
10
0
2
4
6
8
10
12
14
16
18
20
K
Fig. 10. Computational complexity versus K. Same conditions as in Fig. 5.
79
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Computational complexity vs. number of users
80
70
60
Additions/bit
50
40
PIC - random initial
30
-x- SLAS
-+- WSLAS
-o- PLAS
20
10
0
2
4
6
8
10
12
14
16
18
20
K
Fig. 11. Computational complexity versus K. Same conditions as in Fig. 6.
Bit error rate vs. SNR
0
10
Decor.
BER
PLAS = Conv.
-1
PIC
10
WSLAS
SLAS
-2
10
0
5
10
15
A/ (dB)
Fig. 12. BER versus SNR. K = 12 users are considered; the system is perfectly power-controlled;
initials of the three LAS detectors and the PIC detector are output of the conventional detector.
80
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Computational Complexity vs. SNR
80
70
-*-x-+-o-
60
Additions/bit
50
PIC
SLAS
WSLAS
PLAS
40
30
20
10
0
0
5
10
15
SNR
Fig. 13. Computational complexity versus SNR. The conditions are the same as in Fig. 11.
Instant bit error rate
0
10
-1
BER( n)
10
-2
10
-*-x-+-o-
PIC
SLAS
WSLAS
PLAS
-3
10
0
10
1
10
n (bit flip)
2
10
Fig. 14. BER versus bit flip. K = 12 users are considered. The system is perfectly powercontrolled with SNR of 5 dB. Initials are random uniform. Vertical segments on horizontal axis
are average total numbers of flips.
81
Y. Sun, A Family of Likelihood Ascent Search Detectors for CDMA Multiuser Detection, submitted to IEEE Trans. on Info. Theory
9/6/99
Near-far performance: BER vs. deviation of SNR
0
10
PLAS
Conv.
BER
PIC
-1
10
WSLAS
SLAS
Decor.
-2
10
0
5
10
15
SDV of SNR(dB)
Fig. 15. Near-far performance. There are K = 12 users. Initials of the three LAS detector and PIC
detector are random uniform. In every trial, the signal power averaged over K users is 15 dB.
82