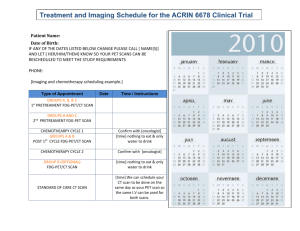
doc - Northeastern University
advertisement

Problem Set - I (Due at the beginning of class on 2/16/11) 2/2/11 CS 4740/6740 Network Security This problem set will be graded out of 240 points. It will count for 8% of your final grade.In this first assignment, you will be forming your teams and preparing your machines for the rest of the upcoming assignments. You will be required to understand and acknowledge the lab rules and you will get your first taste of the Network Security Lab layout. Forming a team Students should form teams with 3 people or less per group and choose a team name. You are responsible for choosing your teammates, so consider your choice carefully. Successful teams are made up of individuals who: Complement each other well in the areas of Unix Systems Administration, Windows Systems Administration, and Cryptography. Get along well with one another under stressful situations and can stay organized in a task-oriented environment. Once you have chosen your teammates, send an email to the TA (with a CC to Professor Ravi Sundaram) with the subject <course number> - Team: <team name> and the body containing the following information: Team name Team member names and email addresses (each line for one member) Your team will be then contacted with information/credentials to remotely access your lab machines at which point, you may begin the setup and scanning sections. Each team will be given two machines which run Ubuntu 10.x and Microsoft Windows Server 2003 respectively, which are a part of the NetSec Lab network. DO NOT install service packs, patches, firewalls, or any other software/service that is not explicitly noted in the assignments. Submitting the assignment. Please submit your assignment in electronic format via email to the TA (Triet Vo-huu) with a cc to the instructor (Ravi Sundaram). The assignment is due before 6 PM on 2/16/2011. Internet 1) Internet – Architecture, Layers [20] a) Explain what is layering giving one advantage and one disadvantage of layering? [4] b) Describe briefly and give one example of each of the following layers - physical, data link, network and transport. [4] c) State and explain the significance of the end-to-end principle? [2] d) What keeps packets from being passed along, router to router, indefinitely? [2] e) Which is better for transferring a large file – UDP or TCP and why? [2] f) What is an ICMP echo-request packet used for? [2] g) Explain how traceroute works? [4] 2) IP/BGP/DNS [20] a) Go to http://whois.arin.net/. Query for “Northeastern University” (quotes not included). List the IP blocks that are registered to Northeastern. [4] b) Go to http://whois.arin.net/ . Query for “a Northeastern University” (quotes not included). List the AS number(s) registered to Northeastern. List the emailid(s) of the tech contact for Northeastern’s Autonomous System(s). [4] c) Go to http://us.mirror.menandmice.com/knowledgehub/tools/dig. Leave the Name Server and Query Type field as is; query www.ccs.neu.edu in the Domain Name field. What is the IP address of www.ccs.neu.edu? [2] d) Go to http://tracert.com. Run a traceroute from SDSC (San Diego Super Computer Center) to www.ccs.neu.edu. List the IP(s) encountered in order. What is the average round trip time? How does it compare to the speed of light? [4] e) Go to any online ping server (e.g. http://tracert.com). Run a ping to www.ccs.neu.edu and to www.rsa.com. Do you see a difference? Why is this? [2] f) Go to http://stat.qwest.net/looking_glass.html. Pick any location; query for type “bgp” the IP address from part c). What is the AS number that CCIS’ website lives in and which organization does this AS belong to? What is the AS number immediately upstream of the AS that CCIS’ website lives in? Use http://whois.arin.net/ to determine the OrgName of the organization that provides connectivity to CCIS’ website. [4] Setup 3) Creating Accounts [25] Each team is provided with a team account for each machine. In order for team members to work more conveniently on the assignments, each member will have to create his/her own account on the team machines. To create an account on your Linux system, use the useradd command. However, you must have permission to execute the command, refer to the man page of sudo command for information. When creating your account, review the command options in the useradd man page to make sure the following requirements are satisfied: o Shell is /bin/bash. o A home directory is created and attached to the new account. o a) b) c) d) Add the account to admin group. By default, a newly created account is disabled. To enable it, login as the team user given to you by the TA, and use the passwd command to set a new password. Log into your Windows machine via Remote Desktop using the Administrator account provided and create your own account which should be added to the Administrators group. Passwords are not necessarily the same on both machines. Remember not to use weak passwords. Create all required accounts for each team member. [10] Explain the purpose of the sudo command. [5] What are the differences between sudo and su? [5] What is the /etc/sudoers file used for? [5] 4) Reviewing Network Settings [20] In order to perform any kind of attack, you will need to understand the network layout. To review your network settings, follow these steps, saving all the information for your report: a) On your Linux machine, determine network interfaces on the machine and their configuration using the ifconfig command. Determine the routing table using the route command. [6] b) On your Windows server, determine the network interfaces and their configuration using the ipconfig command or checking the properties on the Local Area Connection. [6] c) What does the overall topology of NetSec Lab network look like (give a detailed diagram)? [8] Scanning The topic of this section is network reconnaissance and scanning. This is the first step an attacker might use to survey your network and locate potential weaknesses. Therefore, it is imperative that users (especially those who might at one point run their own server) understand these techniques and themselves use scanning tools to discover their own system weaknesses as the first step in improving their defenses. 5) Port Scanning using NMAP [35] NMAP is a popular tool for various types of scanning against hosts on a network. Install NMAP and read its man page. a. Run a discovery scan using -sP against the IP range 10.0.0.64/26. You should have identified two systems in that IP range. Record the output for your report. [5] b. NMAP has an option to determine the operating systems and services running on the identified systems. Find it and record the output for your report [5] c. NMAP has a feature which automates banner-grabbing. Read the man page on the -sV option. Then, run a scan against the two discovered systems using the -sS and -sV options. Record the results of this scan. [5] d. Scan those systems with options -sT and -sS respectively. Record the output. What is the difference between those options? Which one runs faster and why? In general, why would an attacker use TCP SYN scan instead of a full TCP connect scan? [15] e. Review the -p option in the man page. Use this option to scan every UDP port of the two systems in question. Do you notice a difference between the scan rate of the two systems? Record the output of this command. Describe how you could use icmp_ratelimit kernel parameter in Linux to slow down a UDP scan. [5] 6) Stealth Scanning [30] A sneaky method was developed in 1998 to perform spoofed scans through the information leak of IP ID numbers. IP IDs are a field in the IP header of packets which allows a recipient to piece together packets that get fragmented in transit. In order to function properly, these IDs need to be mostly unique, and many IP implementations simply increment a global counter for each packet sent out. However, such an implementation leaks information about how many packets are being sent from a host. Using this leak, one can obtain the results of a spoofed TCP scan. Fyodor describes idle scanning in detail, along with an early post announcing the technique. We will first try this technique manually, then learn how to use nmap's automated idle scan feature. You will use three machines for this experiment. The Windows machine you identified in the previous scan will be called the "zombie" or "zero traffic host". The Linux machine you identified in the previous scan will be known as the victim. Your team's Linux machine will be the attacker. Before you begin the stealth scan, you will be checking to make sure that the zombie is not receiving traffic at the time of your test. If it is, you will have to wait for a later time. Open three seperate shell sessions to your Linux machine. In the first session, setup your Linux machine to listen for ICMP echo reply packets. These packets will be used to check the IP ID on the zombie host. A suggested command line for this is: tcpdump -v -i eth0 icmp[icmptype] == icmp-echoreply In the second session, send a few packets to the zombie machine to determine if it is idle. A suggested command is: ping -c 10 ZOMBIE_IP_ADDRESS Back in the first session, you should see ten lines of output from tcpdump corresponding to the ten echo reply packets. The lines should look something like: 11:37:52.054397 IP (tos 0x0, ttl 128, id 6197, offset 0, flags [DF], proto 1, length: 84) 10.0.0.X > 10.0.0.T: icmp 64: echo reply seq 376 Notice the id field in the IP headers section. This field is the IP ID and it should be incrementing by one for every line. If it is not, the zombie is not idle. Try this lab at another time. Now, in the third session window, scan the victim on a single port, spoofing the source address to point to the zombie server. You can do this with nmap using a command line like: nmap -P0 -sS -p PORT -e eth0 -S ZOMBIE_IP_ADDR VICTIM_IP_ADDR You should first select PORT as a port you know is open on the VICTIM. This scan will send a single SYN packet to an open TCP port on the victim system, made to look like it came from the zombie machine. Send a few more ICMP echo requests to the zombie host with the command: ping -c 3 ZOMBIE_IP_ADDRESS Return to the router session window in which tcpdump is running. Play close attention to the IP ID field. You should see a hole in the sequence between the packets from the first ping command and the last one. You can repeat the experiment several times. If you did everything right, you should notice the sequence skips one number for each time you run the scan. This is because the zombie system will respond with a RST packet to the SYN/ACK received from the victim system, which causes the system-wide ID to increment by one. a) Record a snippet of the tcpdump output when the scan was run. Annotate the output to point-out holes in the IP ID sequence associated with your spoofed scan. [18] NOTE: nmap will report correct results of the scan, even though you didn't give your system's address as the source. Because of the current network configuration, nmap sees the responses even though they aren't technically destined for your Linux router. If you were using an idle host the same interface as the victim, nmap would likely show all ports as filtered, even though the IP IDs would indicate otherwise. Run the experiment again, this time against a port which you know is closed. Watch the IP ID sequence and see if there are any holes. Repeat this several times to be sure; there shouldn't be a hole. This is because the victim will return a RST packet to the zombie host and the zombie host will not respond to a RST packet. b) Fortunately, this labor-intensive scan technique has been automated in nmap. Read the man page's explanation of the -sI scan type. Run an idle scan against the same victim host, once again using the zombie host. Scan at least 5 TCP ports, some known to be open, and some known to be closed. Record the output of this scan. [12] 7) Automated Network Discovery Tools [20] a. Download from the Internet and use an automated network discovery tool like NeoTrace, VisualRoute (try at least one) to form a network map of the target network (choose any target outside of the NetSec Lab network). What information would this would give you? [10] b. Explain how this is useful both for network administrators as well as for potential attackers. [10] 8) Basic UNIX Service Enumeration [25] a. Learn about the netcat tool and what you can do with it. Provide a brief explanation of it’s capabilities, both from an offensive and defensive point of view. [5] b. If you found any Web server or Telnet server on your target network, use netcat for grabbing the available banners. What good does this do and what does it tell a potential intruder about the target host? How might they use this information? [10] c. Check UNIX users/groups on remote targets (or your own if no users are logged in on the target subnet) via finger and report your findings. How could this information be used by an attacker? How can we prevent this sort of information leakage? What if we really needed to run finger for some bizarre reason? [10] 9) Windows NetBIOS/SMB Enumeration [20] a. Use net view (Windows command line) or smbclient (Linux) to enumerate NetBIOS services (Windows port 139, try hosts on your own local network, in particular try host knoxville, assume the investigating user has an unprivileged local account) including Samba shares. Record your output. [10] b. To further simplify the process, try using nbtscan (pre-installed) and scan the entire 10.0.0.0/24 network for shares using Legion (download from http://strawman/scan/). What did you find? Include your output. [10] 10) All-in-one Vulnerability Scanners [25] a. These are really powerful, and really easy to use. You will be using Nessus to scan your own local subnet. Download the software (either Windows or Linux), read installation and user guide, register to the HomeFeed subscription and try using it. Provide a listing of what you have found in the local subnet. Describe how a tool such as Nessus can be an incredibly powerful asset to any system administrator and also how they can be dangerous in the wrong hands. [15] b. Take a quick look at the Nessus architecture and describe how it works. How do they keep their inventory of service vulnerabilities up to date? How does the plugin architecture work, and how can an administrator or developer use this to write custom tools for their own deployments? [10]