Selected Solutions by Simsam Hijjawi
advertisement

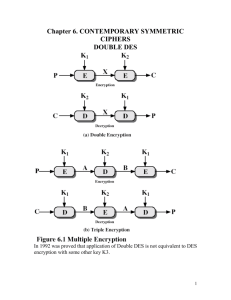
Jordan University of Science and Technology Computer Engineering Department Cryptography & Network Security CPE (541) HW#5 Contemporary Symmetric Ciphers (Double-DES, Triple-DES & Blowfish) Supervised by: Dr Loái Tawalbeh Eng. Sulaiman Al-Basheer Simsam R.Hijjawi 20022171043 Review Problems: 6.1 What is the triple encryption? It is a three-stages encryption with three different keys, to avoid costly requirements arises from using three different keys with total length of 3x56 = 186 bits a triple encryption with two keys maybe used. 6.2 What is the meet in the middle attack? It's that attack doesn't depend on any particular property of the DES, instead, it will work against any type of block ciphers. For the double-DES cipher & a given (P,C) pair, this attack works as follow: 1. Encrypt the plaintext P with all possibilities of K1, store the results in a table, & sort that table by the value of X. 2. Decrypt C with all possible values of K2, check each resulted value with the entries in the table, in case of match, check these two keys against another known pair (P1,C1), if match, accept them as the correct keys. 6.4 Why is the middle portion of 3DES is a decryption rather than an encryption ? 1. It's a decryption process in order to change the traditional nature of the DES, if it's an encryption, it'll stay a DES but with longer key size. 2. In the cryptography, there is no significance of using the decryption in the middle stage, the only advantage of doing so is to allow users of 3DES to decrypt data encrypted by the users of the older single DES C = Ek1[Dk2[Ek1[P]]] = Ek1[P]. Suppose that the middle portion is decryption instead of encryption, C = Ek1[Ek2[Ek1[P]]] The previous assumption in equation 1 will not be ever met. On the other hand 3. If an encryption process is done instead of decryption the meet-in-the-middle attack becomes possible. 6.6 What primitive operations are used in Blowfish? Addition: Addition the words, it is performed modulo 2^32. Bitwise exclusive-OR. Problems: 6.1 For the two design approaches introduced in the textbook, which is the preferred in the followings: Note: the suggested block cipher in my considerations below is DES. - security. The single loop compact approach "single CBC loop" is more secure, this is because the EDE block contains the encryption function C = E k1[D k2[Ek1[P]]] without simplifications, this makes the cryptanalysis like differential attack more difficult than doing it on a simple loop with encryption or decryption process because each loop in the second approach appears like a simple DES that may be attacked alone in a chosen plain-text attack i.e. differential attack. - performance. The second 3 simple approach is the preferred from the performance wise point of view, this is because each block in each loop contains either encryption or decryption processes so it is faster than the first approach. But as I mentioned above, it is more vulnerable to cryptanalysis than the first approach because each loop is a single DES with differential attack possibility. We can also distinguish between the two approaches based on error propagation. 6.2 Can you suggest security improvements to either option, using three DES chips & some number of XOR functions? Assume you are still limited to two keys. Changing the mode sounds a good solution: 1. For the first approach that contain only a single independent loop, using Counter mode seems to be simpler, because we deal with counters that less longer than plain texts & have no linear or statistical relationship, this may increase the performance of the 3DES in this case. 2. For the second approach, the dependency between stages prevents using the counter mode as an enhancement, a more secure mode is required in this case, using the CFB may eliminate the possibility of differential cryptanalysis because chosen plain text attack is not worth. 6.4 Demonstrate that the blowfish decryption is the inverse of the blowfish encryption. Taking in consideration the following: The decryption process is applied in the same direction as the encryption but with reverse order use of the sub keys. Encryption: 1. Assume the following plain text P with E-PL0 & E-PR0 portions. 2. After the ith round, the output of that round will be E-PRi = E-PLi Xor Pi ……… (1) E-PLi = F [E-PRi] Xor E-PRi-1 ……… (2) 3. The cipher text will be: E-PR17 = E-PL16 Xor P18 E-PL17 = E-PR16 Xor P17 C = E-PR17 + E-PL17 "+ sign is a concatenation" It will be the input of the decryption algorithm which is the same as the encryption algorithm but with reverse order key fashion. Decryption: 1. Assume the following cipher text C with D-CL0 & D-CR0 portions. 2. After the ith round, the output of that round will be D-CRi = D-CLi Xor P19-I ………. (3) D-CLi = F [D-CRi] Xor D-CRi-1 ………. (4) 3. the outputs of equation # 1 & equation # 3 and equation # 2 & equation # 4 are the same for each round, this implies the reversibility in the blowfish algorithm between the encryption & the decryption algorithms.