Hw2 solutions - Network Penetration and Security
advertisement
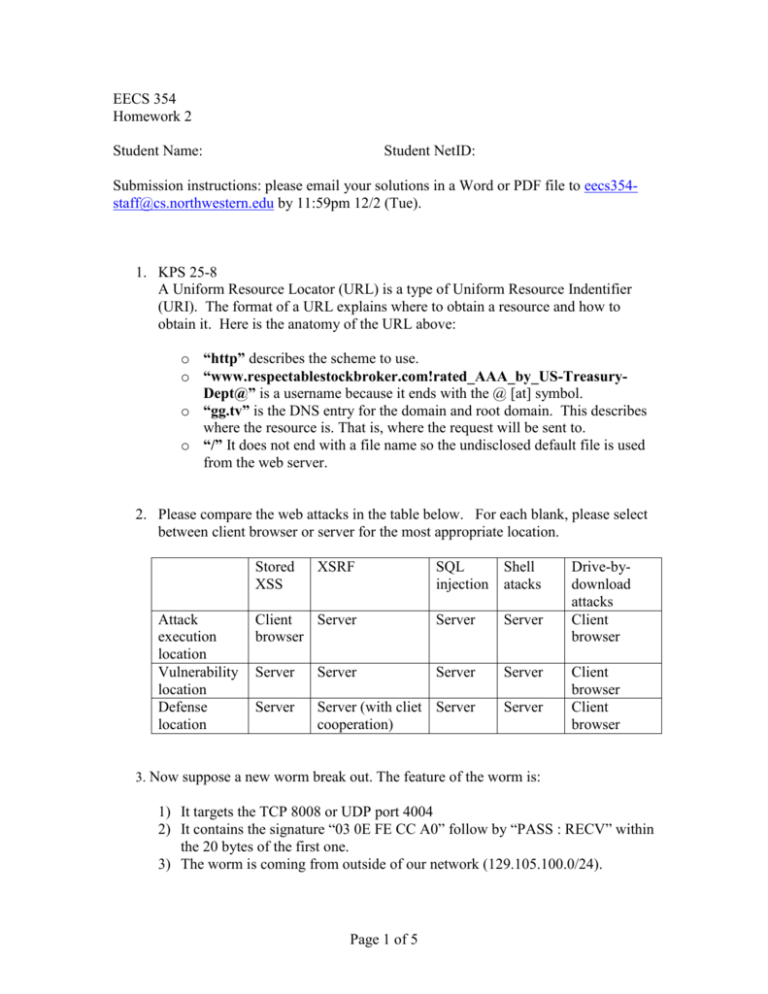
EECS 354 Homework 2 Student Name: Student NetID: Submission instructions: please email your solutions in a Word or PDF file to eecs354staff@cs.northwestern.edu by 11:59pm 12/2 (Tue). 1. KPS 25-8 A Uniform Resource Locator (URL) is a type of Uniform Resource Indentifier (URI). The format of a URL explains where to obtain a resource and how to obtain it. Here is the anatomy of the URL above: o “http” describes the scheme to use. o “www.respectablestockbroker.com!rated_AAA_by_US-TreasuryDept@” is a username because it ends with the @ [at] symbol. o “gg.tv” is the DNS entry for the domain and root domain. This describes where the resource is. That is, where the request will be sent to. o “/” It does not end with a file name so the undisclosed default file is used from the web server. 2. Please compare the web attacks in the table below. For each blank, please select between client browser or server for the most appropriate location. Stored XSS Attack execution location Vulnerability location Defense location XSRF SQL injection Shell atacks Client Server browser Server Server Server Server Server Server Server Server (with cliet Server cooperation) Server Drive-bydownload attacks Client browser Client browser Client browser 3. Now suppose a new worm break out. The feature of the worm is: 1) It targets the TCP 8008 or UDP port 4004 2) It contains the signature “03 0E FE CC A0” follow by “PASS : RECV” within the 20 bytes of the first one. 3) The worm is coming from outside of our network (129.105.100.0/24). Page 1 of 5 Add a firewall rule to block that worm. Suppose the firewall use this kind of rule format: Action Src allow/block IPsubnet, use * to refer any host port port number or * (refer any) dest IPsubnet, use * to refer any host port port number or * (refer any) flags flag can be TCP, UDP comment The description of this rule Write firewall rules based on the above format to the Ditty worm traffic towards our network (129.105.100.0/24). Hint: assume that we do not have benign traffic on those services which the ditty worm rely on to propagate. Action Src allow/block IPsubnet, use * to refer any host block * port port number or * (refer any) * block * * dest IPsubnet, use * to refer any host port port number or * (refer any) 129.105.100.0/24 8008 flags flag can be TCP, UDP TCP 129.105.100.0/24 UDP 4004 comment The description of this rule Blocks any incoming traffic on TCP 8008 Blocks any incoming traffic on UDP 40004 4. In this question, we explore some applications and limitations of a packet filtering firewall. For each of the question, briefly explain 1) can stateless firewall be configured to defend against the attack and how? 2) if not, what about stateful firewall ? 3) if neither can, what about application-level proxy? 1. Can the firewall prevent an online password dictionary attack from the external network on the telnet port of an internal machine? Neither a Stateless or stateful packet filter can read the payload to recognize it is a login attempt, especially when the attacker uses the same TCP connection to launch the dictionary attack. Page 2 of 5 An application proxy will recognize multiple unsuccessful login attempt requests and block them. 2. Can the firewall prevent a user on the external network from opening a window on an X server in the internal network? Recall that by default an X server listens for connections on port 6000 Stateless firewall can defend against this attack by blocking port 6000 (default port used by X server) or any other port that X server listens to for display commands. 3. Can the firewall block a virus embedded in an incoming email? Stateless and Stateful firewalls will not be able to block the virus as they only inspect the header. Viruses are detected at Application level and that is why an application proxy would be the best way to block it. 4. Can the firewall be used to block users on the internal network from browsing a specific external IP address? A stateless firewall rule can block any traffic with the source on the internal network and destination that specific external IP. 5. Can the firewall prevent external users from exploiting a security bug in a CGI script on an internal web server (the web server is serving requests from the Internet)? Firewalls are supposed to allow traffic that reaches the internal web server. None of the packet filters can check payload to detect the CGI script exploit. An Application proxy would be the best solution in this situation and allow prevention at the Application layer. 5. Please give the major classifications for existing IDS/IPS systems. Based on different feature selection and modeling approaches, it can be classified as misuse detection and anomaly detection. What is the major advantage and disadvantage for each of the two approaches (just list the most important one advantage and the most important one disadvantage for each)? Misuse detection Advantage: accurate identification of previously known attacks Disadvantage: cannot detect new attacks Anomaly detection Page 3 of 5 Advantage: can detect new and unknown attacks, check against “normal” Disadvantage: relatively high false positives 6. In this question, we explore some applications and limitations of a network and host based IDS/IPS. For each of the question, briefly explain 1) can network based IDS/IPS detect such attacks and how? and 2) if not, what about host-based IDS/IPS? a. An unknown malware infection to a host The host-based IDS is effective because it needs to analyze its system level behaviors for anomaly based detection. The network based IDS does not have signature or abnormal traffic pattern for detection. b. Botnet scans for machines having a vulnerability associated with a certain service with fixed port numbers Botnet scans: The network-based IDS can be effective, it can detect abnormal network traffic patterns caused by botnet scans. For example, the large number of TCP SYN packets, with much less SYN ACK packets. 7. KS problem 9-2 It is secure for eavesdropping attack, but it is not secure against server database reading attack because it can generate the hash(Z,R) when Z is known. 8. Problem 8 Page 4 of 5 It is not secure against eavesdropping (playback) attack because Trudy can replay the same packet that Alice sent to Bob earlier. Bob will accept the packet because it does not remember what nonce R was sent. It is not secure against server database reading attack because when K_AB is known, Trudy can generate K_AB(R) for any given R. 9. Consider the KDC and CA servers. Suppose a KDC goes down. What is the impact on the ability of parties to communicate securely; that is, who can and cannot communicate? Justify your answer. Suppose now a CA goes down. What is the impact of this failure? When KDC goes down, no parties can communicate with each other because they all need to go to KDC to get the session key. When CA goes down, no new party can get a certificate. But those who have certificates can authenticate with their clients. Page 5 of 5