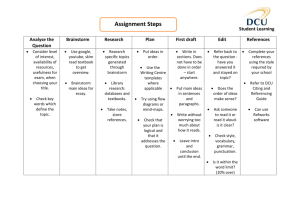
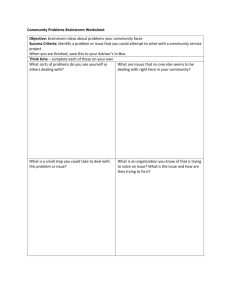
Notes from Brainstorm session at Southern California SPIN on 3/29
advertisement

Notes from Brainstorm session at Southern California SPIN on 3/29/02 (What is Information Survivability and Why Should I Care? by Julia Allen) What are some ways to get these practices into place? Defect Management Use argument/connection that security is related to defects, and link it to defect prevention and elimination Product vulnerabilities as defects waiting to happen “Worst practices” to avoid Requirements Management Needs to be addressed at the beginning of the program, evaluate the scope, opportunity – is it a high security concern, or low impact Security should be a systems requirement that is implemented and tested in the software. Role of SEPG should be to ensure that it is followed through. Some customers expect proposals to include security plan. It’s done where specified, but maybe not being thought of as something that is always needed whether asked for or not. Software Development and QA Use standard design reviews and code reviews, update checklists to include security issues Should be seen as “just another thing” to add to our existing practices Is there a long laundry list of what we should be looking for, such as buffer overflow? Yes, but needs to be codified. CERT is at the tail end, someone calls with the problem after the fact. But we should be working to get it earlier in the lifecycle. Business Assessments Enterprise level assessment of the overall impact of the company, all of the business, not just the one aspect Security audit to show that the company is secure, like a financial audit, part of the financial responsibility of the company to protect itself from risks Training Training – Undergraduate curriculum Training brought into companies (such as DirectTV) Bring awareness training on security practices into refresher training for developers, blending into existing programs Projects looking at safety on COTS, Do you have to wrap them? Need standards for bringing COTS into the program, with promoting and training for standards What else is going on in the industry that can be leveraged? CMM Models: System, Software CMMs? What about Security Model or Security KPA? Put it “on the list” “on the radar” …and then it can be driven by customer base funding. PSP/TSP: Opportunity to put security practices into PSP and TSP JPL tool for Risk Management: Value of mitigation actions on impact on risks, quantify the amount of benefit from a practice, for selecting the best action for the available dollars. (Organization-specific, might broaden applicability generally) Notes from Brainstorm session at Southern California SPIN on 3/29/02 (What is Information Survivability and Why Should I Care? by Julia Allen) What else might affect decisions to use the practices? Increasing “Pain” Increase in incidents - If the curve keeps going up, eventually it will outstrip all other issues Attacks are getting easier to do Reputation for vendors Prosecution What’s the rate of successful prosecutions? Difficulties with attacks coming through countries with less legal enforcement/prosecutions. Still learning what evidence is needed and will hold up in court Changes to product liability laws? But what would the implications be? What about unintended consequences? COTS is not very secure, and it’s black box, legal constraints about reverse engineering. US Patriot Act vs. the “I’m not liable” claims Rating Systems “A UL rating” (Underwriters Laboratories ratings for product safety and independent testing of electronic components. Website: www.ul.com) or “Good Housekeeping” ratings on websites…Can we do something similar for software components that have passed security assessment SANS Institute (System Administration, Networking and Security Institute) – series of checklists for operating environments, companies can say we meet the checklists. Websites: www.sans.org, http://www.sans.org/SCORE/ Internet Security Alliance – collaboration of SEI’s CERT (Software Engineering Institute’s Computer Emergency Response Team) and EIA (Electronics Industry Alliance) defining some standards so companies can demonstrate ability to meet standards, positive reputation spin. Website: www.isalliance.org ISO 9000 certification (may or may not have much pull for high-tech companies) CE mark in Europe, technical and specific, not process-oriented, per se Why is it so difficult? Systems Issues Safety, unreliability. Prescribing what the system must NOT do, rather than what it must do. Safety is a system issue. Human factors issues, human behavior Typically physical security, buildings, or expecting interfaces to be secure, but secure programming practices haven’t been introduced yet Management Issues Don’t think management understands the implications yet Building the base capability for a safety program was a big effort, but now we know what needs to be considered Security costs are too high, so companies don’t bid on proposals that include security and safety. With DO178B – the customer pays for it, but if the customer doesn’t, then where are you? Notes from Brainstorm session at Southern California SPIN on 3/29/02 (What is Information Survivability and Why Should I Care? by Julia Allen) Outsourcing Issues What does the group that we outsource our IT to do? “They” do it, and we don’t know how they do it? IT outsourcing companies should be aware. Maybe the customers of outsourcing IT services should be asking for security practices before renewing contracts What lines of communication will provide feedback on use of the practices? SEI Working Group of advisors? Frame as a written request to bring back to others. Properly framed there would be interest. Mine the May CMMI Workshop for advisor candidates, Birds of a Feather Session. Notes from Brainstorm session at Southern California SPIN on 3/29/02 (What is Information Survivability and Why Should I Care? by Julia Allen) Raw Notes: Use argument/connection that security is related to defects, and link it to defect prevention and elimination Product vulnerabilities as defects waiting to happen Safety, unreliability. Prescribing what the system must NOT do, rather than what it must do. Safety is a system issue. Human factors issues, human behavior JPL tool for Risk Management – Value of mitigation actions on impact on risks, quantify the amount of benefit from a practice, for selecting the best action for the available dollars. Organization specific might be used to broaden applicability generally Security should be a systems requirement that is implemented and tested in the software. Role of SEPG should be to ensure that it is followed through. Some customers expect proposals to include security plan. It’s done where specified, but maybe not being thought of as something that is always needed whether asked for or not. Typically physical security, buildings, or expecting interfaces to be secure, but secure programming practices haven’t been introduced yet Use standard design reviews and code reviews, update checklists to include security issues Don’t think management does not yet understand the implications Should be seen as “just another thing” to add to our existing practices Needs to be addressed at the beginning of the program, evaluate the scope, opportunity – is it a high security concern, or low impact Model: System, Software CMMs? What about Security Model or Security KPA? Put it “on the list” “on the radar” Driven by customer base funding. Building the base capability for a safety program was a big effort, but now we know what needs to be considered Enterprise level assessment of the overall impact of the company, all of the business, not just the one aspect Security audit to show that the company is secure, like a financial audit, part of the financial responsibility of the company to protect itself from risks Security costs are too high, so companies don’t bid on proposals that include security and safety. Projects looking at safety on COTS, Do you have to wrap them? Standards for bringing COTS into the program. Promoting and training for the standards What does the group that we outsource our IT to do? “They” do it, and we don’t know how they do it? IT outsourcing companies should be aware. Maybe the customers of outsourcing IT services should be asking for security practices before renewing contracts If the curve keeps going up, eventually it will outstrip all other issues What’s the rate of successful prosecutions? Attacks coming from countries with less legal enforcement/prosecutions Still learning what evidence is needed and will hold up in court Notes from Brainstorm session at Southern California SPIN on 3/29/02 (What is Information Survivability and Why Should I Care? by Julia Allen) Attacks are getting easier to do Changes to product liability laws? But what would the implications be? What about unintended consequences? Reputation for vendors Is there a long laundry list of what we should be looking for, such as buffer overflow? Yes, but needs to be codified. Opportunity to put security practices into PSP and TSP “Worst practices” to avoid Training – Undergraduate curriculum CERT is at the tail end, someone calls with the problem, working to get it earlier in the lifecycle Training brought in to DirectTV Bring awareness training on security practices into refresher training for developers Blending into existing programs “A UL rating” passed security assessment SANSA – series of checklists for operating environments, can say we meet the checklists EIA – Internet security alliance, demonstrate ability to meet standards, positive reputation spin “Good Housekeeping” ratings on websites ISO 9000 certification DO178B – the customer pays for it, but if the customer doesn’t, then where are you? COTS is not very secure, and it’s black box, legal constraints about reverse engineering. US Patriot Act vs. the “I’m not liable” claims CE mark in Europe, technical and specific, not process-oriented, per se SEI Working Group of advisors? Frame as a written request to bring back to others. Properly framed there would be interest. Mine the May CMMI Workshop for advisor candidates, BOF Session.