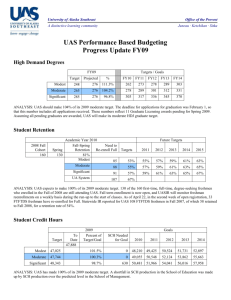
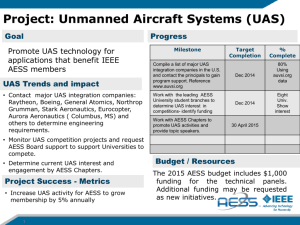
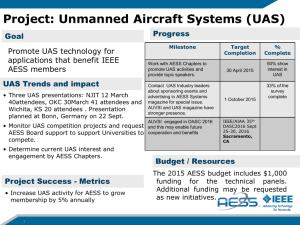
Chapter 1: Defining Network System Components: Lab Work
advertisement

Chapter 1: Defining Network System Components: Lab Work In AS 106, do the following Activities. Record the requested results and submit, either electronically or on paper. Due September 11, 2007. Activity 1-1: Logging in and Changing your Password – page 9 At step #2, log in with the user name that has been given. For example: 10admin, 11admin, 12admin, etc. You will use these same logins for the semester. The password for each is ‘password’. After you enter the password, click the Advanced tab. You’ll have to change the tree, context and server to get into the classroom server. From the Advanced tab, click ‘Tree’ and select UAS_TREE from the options given. Click OK, then click ‘Context’ and select ‘Class’ then select your context from the options given. For example, the student who has 10admin will select 10UAS. These are the contexts (organizations) that you’ll be working with for your assignments this semester. Click OK, then select ‘Servers’. Scroll down to the bottom of the list, double click the UAS organization to display the contents and select UAS-HOST. This object represents the Novell server that we’re working from. Click OK, then OK again to continue the login process. You have just completed Steps #2 and #4. We don’t have to worry about Step #3 because Novell automatically authenticates you into the XP workstation. Keep in mind that the text assumes that we’re working with Windows 2000 workstations, but we’re using XP. Most of the workstation assignments will be slightly different. When you get the message about changing the password, select cancel, and then proceed with the text instructions for changing passwords. Record the Password Policy: Complete the remainder of the steps with the following exception: at Step #5 – f, click Start, Shutdown and restart the workstation. Then proceed to Step #6 to test your password. Activity 1-2: Changing the Windows 2000 User Password – page 10 Read but don’t perform. Activity 1-3: Using Message Services – page 11 Send a message to a classmate or to yourself if you are working on your own. Follow steps to #7, then select your classmate’s (or your own) ‘XXadmin’ account from the list, substituting XX with the appropriate two digit number. If there are multiple instances of your admin account, choose the one with the asterisk (*). That represents the actual account. Any additional entries represent authentications to other services and you’ll get an error if you select them. Send back a reply. What information is displayed in the Send Message Results’ window? _______________________________________________________ Activity 1-4: Viewing eDirectory Information – page 13 Follow the steps as given, paying close attention to Step #2 as you log in as Kari Means. At Step 2d, scroll to the bottom to locate the UAS container, double click it and then select the Engineering container. Remember at Step 2f, the UASHOST server is also located in the UAS container at the bottom of the list. It may take a couple of minutes, but Novell Delivered Apps should display automatically after you have logged in (step 4). Double click ‘User Information’ and wait for Console One to open. What is ConsoleOne? ________________________________________________________ In ConsoleOne, the navigation frame is on the left and the object frame is on the right. This is similar to Windows Explorer or My Computer. Step #5: Follow the instructions to locate the Engineering container. Step #7 - 9: What are the job title descriptions for each Engineering department user? Activity 1-5: Working with Drive Mappings – page 15 Begin at Step #5. At Step #7d, click the + to the left of UAS_TREE, scroll down to find UAS organization. Proceed with Step #7f. Note that our volume is called UASHOST_CORP.UAS. Step #8: What is the full path of the network drive that you mapped to R:? _______________________________________________________ Activity 1-6: Using Application Services – page 17 Record the appropriate applications: Step #3: Step #5: Step #6a: Step #6b: Skip Activities 1-7. Activity 1-8: Identifying Universal Aerospace Network Components– page 22 Be sure to save with the appropriate file name in the shared directory. Work up through Step #5. Don’t print anything. Activity 1-9: Identifying Network Adapter Properties – page 24. Step #1: Log in as your admin user account instead of using the instructions given. Record the following information: Driver date: _____________________________________________ Resources key - interrupt and memory range: ________________________________________________________ Activity 1-10: Identifying Workstation Protocols – page 27. Begin at Step #7 after logging in as your admin user account. Record your IP address information below: