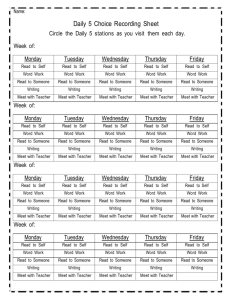
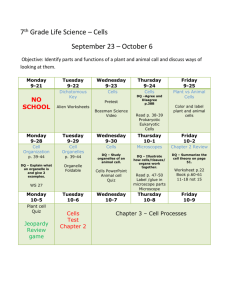
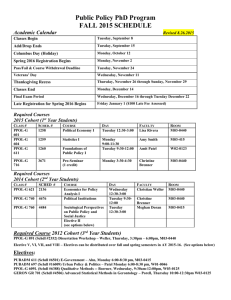
- The University of Texas at Austin
advertisement

Focus on the buzz words highlighted in blue text Reviewed 130123 and 130827 Source — http://www.webopedia.com http://www.webopedia.com/quick_ref/FileSizeConversionTable.asp File Size Conversion Table The table below shows the relationship between the file storage sizes that computers use. Binary calculations are based on units of 1,024, and decimal calculations are based on uints of 1,000. It should be noted that decimal calculations are based on units that have been rounded off to the nearest 1,000 and therefore differ from the actual number of bytes used in binary calculations. Name Symbol Bytes Equal to kilobyte KB megabyte MB gigabyte GB terabyte TB petabyte PB exabyte EB zettabyte ZB yottabyte YB November 9, 2003 Binary Measurement 2^10 2^20 2^30 2^40 2^50 2^60 2^70 2^80 10^3 10^6 10^9 10^12 10^15 10^18 10^21 10^24 Decimal Measurement Number of 1,024 1,024 bytes 1,048,576 1,024KB 1,073,741,824 1,024MB 1,099,511,627,776 1,024GB 1,125,899,906,842,624 1,024TB 1,152,921,504,606,846,976 1,024PB 1,180,591,620,717,411,303,424 1,024EB 1,208,925,819,614,629,174,706,176 1,024ZBLast updated: access Last modified: Friday, February 27, 2004 (v.) (1) To use. For example, programs can access memory , which means they read data from or write data to main memory. A user can access files, directories, computers, or peripheral devices. (2) More specifically, access often means to read data from or write data to a mass storage device. The time it takes to locate a single byte of information on a mass-storage device is called the access time. (3) To visit a Web site. (n.) (1) The act of reading data from or writing data to a storage device. (2) A privilege to use computer information in some manner. For example, a user might be granted read access to a file, meaning that the user can read the file but cannot modify or delete it. Most operating systems have several different types of access privileges that can be granted or denied to specific users or groups of users. (3) When capitalized as Access, short for Microsoft Access. Microsoft Access Last modified: Friday, February 27, 2004 Often referred to as simply Access, Microsoft’s database creation and management software. Access point (yields) AP Last modified: Friday, January 16, 2004 Short for Access Point, a hardware device or a computer's software that acts as a communication hub for users of a wireless device to connect to a wired LAN. APs are important for providing heightened wireless security and for extending the physical range of service a wireless user has access to. Also see infrastructure mode and ad-hoc mode. Also see the Wireless LAN Standards chart in the Quick Reference section of Webopedia Acquistion cost (yields) cost per thousand Last modified: Thursday, August 21, 2003 Abbreviated as CPM (the letter "M" in the abbreviation is the Roman numeral for one thousand). CPM is used by Internet marketers to price ad banners. Sites that sell advertising will guarantee an advertiser a certain number of impressions (number of times an ad banner is downloaded and presumably seen by visitors.), then set a rate based on that guarantee times the CPM rate. A Web site that has a CPM rate of $25 and guarantees advertisers 600,000 impressions will charge $15,000 ($25 x 600) for those advertisers' ad banner. ANSI Last modified: Friday, June 22, 2001 Acronym for the American National Standards Institute. Founded in 1918, ANSI is a voluntary organization composed of over 1,300 members (including all the large computer companies) that creates standards for the computer industry. For example, ANSI C is a version of the C language that has been approved by the ANSI committee. To a large degree, all ANSI C compilers, regardless of which company produces them, should behave similarly. In addition to programming languages, ANSI sets standards for a wide range of technical areas, from electrical specifications to communications protocols. For example, FDDI, the main set of protocols for sending data over fiber optic cables, is an ANSI standard. Apache (yields) Apache Web server Last modified: Tuesday, March 11, 2003 Often referred to as simply Apache, a public-domain open source Web server developed by a loosely-knit group of programmers. The first version of Apache, based on the NCSA httpd Web server, was developed in 1995. Core development of the Apache Web server is performed by a group of about 20 volunteer programmers, called the Apache Group. However, because the source code is freely available, anyone can adapt the server for specific needs, and there is a large public library of Apache add-ons. In many respects, development of Apache is similar to development of the Linux operating system. The original version of Apache was written for UNIX, but there are now versions that run under OS/2, Windows and other platforms. The name is a tribute to the Native American Apache Indian tribe, a tribe well known for its endurance and skill in warfare. A common misunderstanding is that it was called Apache because it was developed from existing NCSA code plus various patches, hence the name a patchy server, or Apache server. application server Last modified: Tuesday, January 28, 2003 Also called an appserver. A program that handles all application operations between users and an organization's backend business applications or databases. Application servers are typically used for complex transaction-based applications. To support highend needs, an application server has to have built-in redundancy, monitors for highavailability, high-performance distributed application services and support for complex database access. See the Server Types page in the quick reference section of Webopedia for a comparison of server types. (Many thanks go out to Paul White, Product Marketing Manager EMEA, BEA Systems, for providing this updated definition.) ARPANET Last modified: Monday, July 02, 2001 The precursor to the Internet, ARPANET was a large wide-area network created by the United States Defense Advanced Research Project Agency (ARPA). Established in 1969, ARPANET served as a testbed for new networking technologies, linking many universities and research centers. The first two nodes that formed the ARPANET were UCLA and the Stanford Research Institute, followed shortly thereafter by the University of Utah. ASCII Last modified: Monday, August 05, 2002 Acronym for the American Standard Code for Information Interchange. Pronounced ask-ee, ASCII is a code for representing English characters as numbers, with each letter assigned a number from 0 to 127. For example, the ASCII code for uppercase M is 77. Most computers use ASCII codes to represent text, which makes it possible to transfer data from one computer to another. For a list of commonly used characters and their ASCII equivalents, refer to the ASCII page in the Quick Reference section. Text files stored in ASCII format are sometimes called ASCII files. Text editors and word processors are usually capable of storing data in ASCII format, although ASCII format is not always the default storage format. Most data files, particularly if they contain numeric data, are not stored in ASCII format. Executable programs are never stored in ASCII format. The standard ASCII character set uses just 7 bits for each character. There are several larger character sets that use 8 bits, which gives them 128 additional characters. The extra characters are used to represent non-English characters, graphics symbols, and mathematical symbols. Several companies and organizations have proposed extensions for these 128 characters. The DOS operating system uses a superset of ASCII called extended ASCII or high ASCII. A more universal standard is the ISO Latin 1 set of characters, which is used by many operating systems, as well as Web browsers. Another set of codes that is used on large IBM computers is EBCDIC. backup Last modified: Tuesday, May 25, 2004 (v.) To copy files to a second medium (a disk or tape) as a precaution in case the first medium fails. One of the cardinal rules in using computers is back up your files regularly. Even the most reliable computer is apt to break down eventually. Many professionals recommend that you make two, or even three, backups of all your files. To be especially safe, you should keep one backup in a different location from the others. You can back up files using operating system commands, or you can buy a specialpurpose backup utility. Backup programs often compress the data so that backups require fewer disks. (n.) (1) The act of backing up. (2) A substitute or alternative. The term backup usually refers to a disk or tape that contains a copy of data. binary Last modified: Friday, March 21, 2003 Pertaining to a number system that has just two unique digits. For most purposes, we use the decimal number system, which has ten unique digits, 0 through 9. All other numbers are then formed by combining these ten digits. Computers are based on the binary numbering system, which consists of just two unique numbers, 0 and 1. All operations that are possible in the decimal system (addition, subtraction, multiplication, division) are equally possible in the binary system. We use the decimal system in everyday life because it seems more natural (we have ten fingers and ten toes). For the computer, the binary system is more natural because of its electrical nature (charged versus uncharged). In the decimal system, each digit position represents a value of 10 to the position's power. For example, the number 345 means: 3 three 100s (10 to the 2nd power) plus 4 four 10s (10 to the first power) plus 5 five 1s (10 to the zeroth power) In the binary system, each digit position represents a value of 2. For example, the binary number 1011 equals: 1 one 8 (2 to the 3rd power) plus 0 zero 4s (2 to the 2nd power) plus 1 one 2 (2 to the first power) plus 1 one 1 (2 to the zeroth power) So a binary 1011 equals a decimal 11. Because computers use the binary number system, powers of 2 play an important role. This is why everything in computers seems to come in 8s (2 to the 3rd power), 64s (2 to the 6th power), 128s (2 to the 7th power), and 256s (2 to the 8th power). Programmers also use the octal (8 numbers) and hexadecimal (16 numbers) number systems because they map nicely onto the binary system. Each octal digit represents exactly three binary digits, and each hexadecimal digit represents four binary digits. bit Last modified: Tuesday, August 03, 2004 Short for binary digit, the smallest unit of information on a machine. The term was first used in 1946 by John Tukey, a leading statistician and adviser to five presidents. A single bit can hold only one of two values: 0 or 1. More meaningful information is obtained by combining consecutive bits into larger units. For example, a byte is composed of 8 consecutive bits. Computers are sometimes classified by the number of bits they can process at one time or by the number of bits they use to represent addresses. These two values are not always the same, which leads to confusion. For example, classifying a computer as a 32bit machine might mean that its data registers are 32 bits wide or that it uses 32 bits to identify each address in memory. Whereas larger registers make a computer faster, using more bits for addresses enables a machine to support larger programs. Graphics are also often described by the number of bits used to represent each dot. A 1bit image is monochrome; an 8-bit image supports 256 colors or grayscales; and a 24- or 32-bit graphic supports true color. blog Last modified: Monday, March 08, 2004 (n.) Short for Web log, a blog is a Web page that serves as a publicly accessible personal journal for an individual. Typically updated daily, blogs often reflect the personality of the author. (v.) To author a Web log. Other forms: Blogger (a person who blogs). byte Last modified: Tuesday, May 21, 2002 Abbreviation for binary term, a unit of storage capable of holding a single character. On almost all modern computers, a byte is equal to 8 bits. Large amounts of memory are indicated in terms of kilobytes (1,024 bytes), megabytes (1,048,576 bytes), and gigabytes (1,073,741,824 bytes). server blade Last modified: Monday, August 05, 2002 A single circuit board populated with components such as processors, memory, and network connections that are usually found on multiple boards. Server blades are designed to slide into existing servers. Server blades are more cost-efficient, smaller and consume less power than traditional box-based servers. Also see the Server Types page in the Quick Reference section of Webopedia for a comparison of server types. bps Last modified: Tuesday, May 21, 2002 Abbreviation of bits per second, the standard measure of data transmission speeds. broadband Last modified: Tuesday, June 15, 2004 A type of data transmission in which a single medium (wire) can carry several channels at once. Cable TV, for example, uses broadband transmission. In contrast, baseband transmission allows only one signal at a time. Most communications between computers, including the majority of local-area networks, use baseband communications. An exception is B-ISDN networks, which employ broadband transmission. CERN Last modified: Wednesday, January 22, 2003 Pronounced sern. Short for Conseil Europeen pour le Recherche Nucleaire (European Laboratory for Particle Physics), a research laboratory headquartered in Geneva, Switzerland, and funded by many different countries. While most work deals with nuclear physics, the CERN is known for Tim Berners-Lee's pioneering work in developing the World Wide Web portion of the Internet. CGI Last modified: Tuesday, March 02, 2004 Abbreviation of Common Gateway Interface, a specification for transferring information between a World Wide Web server and a CGI program. A CGI program is any program designed to accept and return data that conforms to the CGI specification. The program could be written in any programming language, including C, Perl, Java, or Visual Basic. CGI programs are the most common way for Web servers to interact dynamically with users. Many HTML pages that contain forms, for example, use a CGI program to process the form's data once it's submitted. Another increasingly common way to provide dynamic feedback for Web users is to include scripts or programs that run on the user's machine rather than the Web server. These programs can be Java applets, Java scripts, or ActiveX controls. These technologies are known collectively as client-side solutions, while the use of CGI is a server-side solution because the processing occurs on the Web server. One problem with CGI is that each time a CGI script is executed, a new process is started. For busy Web sites, this can slow down the server noticeably. A more efficient solution, but one that it is also more difficult to implement, is to use the server's API, such as ISAPI or NSAPI. Another increasingly popular solution is to use Java servlets. click-through Last modified: Tuesday, February 11, 2003 The process of a visitor clicking on a Web advertisement and going to the advertiser's Web site. Also called ad clicks or requests. The click rate measures the amount of times an ad is clicked versus the amount of times it's viewed. client (klī´&nt) (n.) The client part of a client-server architecture. Typically, a client is an application that runs on a personal computer or workstation and relies on a server to perform some operations. For example, an e-mail client is an application that enables you to send and receive e-mail. coaxial cable Last modified: Thursday, March 27, 2003 A type of wire that consists of a center wire surrounded by insulation and then a grounded shield of braided wire. The shield minimizes electrical and radio frequency interference. Coaxial cabling is the primary type of cabling used by the cable television industry and is also widely used for computer networks, such as Ethernet. Although more expensive than standard telephone wire, it is much less susceptible to interference and can carry much more data. cookie Last modified: Monday, November 03, 2003 A message given to a Web browser by a Web server. The browser stores the message in a text file. The message is then sent back to the server each time the browser requests a page from the server. Also see session cookie and persistent cookie. The main purpose of cookies is to identify users and possibly prepare customized Web pages for them. When you enter a Web site using cookies, you may be asked to fill out a form providing such information as your name and interests. This information is packaged into a cookie and sent to your Web browser which stores it for later use. The next time you go to the same Web site, your browser will send the cookie to the Web server. The server can use this information to present you with custom Web pages. So, for example, instead of seeing just a generic welcome page you might see a welcome page with your name on it. The name cookie derives from UNIX objects called magic cookies. These are tokens that are attached to a user or program and change depending on the areas entered by the user or program. Also see Do Cookies Compromise Security? in the Did You Know . . . ? section of Webopedia. CPC Last modified: Thursday, July 24, 2003 Short for cost-per-click, an Internet marketing formula used to price online advertisements. Advertisers will pay Internet publishers based on the number of clicks a specific ad gets. CPM Last modified: Thursday, August 21, 2003 (1) Short for Critical Path Method. (2) Short for cost per thousand. Also see CP/M. CP/M Last modified: Friday, January 31, 2003 Abbreviation of Control Program for Microcomputers. Created by Digital Research Corporation, CP/M was one of the first 8-bit operating systems for personal computers. However, Digital Research Corporation made a critical strategic error by not agreeing to produce an operating system for the first IBM PC. According to the folklore, the president of Digital Research was flying his airplane when IBM came to call. IBM marched out and never looked back. Instead, IBM turned to Microsoft Corporation, which developed MS-DOS based on version 2.2 of CP/M. By the mid 1980s, MS-DOS had become the standard operating system for IBM-compatible personal computers. CP/M is now obsolete. CPU Last modified: Wednesday, January 15, 2003 Abbreviation of central processing unit, and pronounced as separate letters. The CPU is the brains of the computer. Sometimes referred to simply as the processor or central processor, the CPU is where most calculations take place. In terms of computing power, the CPU is the most important element of a computer system. On large machines, CPUs require one or more printed circuit boards. On personal computers and small workstations, the CPU is housed in a single chip called a microprocessor. Two typical components of a CPU are: * The arithmetic logic unit (ALU), which performs arithmetic and logical operations. * The control unit, which extracts instructions from memory and decodes and executes them, calling on the ALU when necessary. CRM Last modified: Thursday, July 24, 2003 Short for customer relationship management. CRM entails all aspects of interaction a company has with its customer, whether it be sales or service related. Computerization has changed the way companies are approaching their CRM strategies because it has also changed consumer buying behavior. With each new advance in technology, especially the proliferation of self-service channels like the Web and WAP phones, more of the relationship is being managed electronically. Organizations are therefore looking for ways to personalize online experiences (a process also referred to as mass customization) through tools such as help-desk software, e-mail organizers and Web development apps. cryptography Last modified: Tuesday, March 16, 2004 The art of protecting information by transforming it (encrypting it) into an unreadable format, called cipher text. Only those who possess a secret key can decipher (or decrypt) the message into plain text. Encrypted messages can sometimes be broken by cryptanalysis, also called codebreaking, although modern cryptography techniques are virtually unbreakable. As the Internet and other forms of electronic communication become more prevalent, electronic security is becoming increasingly important. Cryptography is used to protect e-mail messages, credit card information, and corporate data. One of the most popular cryptography systems used on the Internet is Pretty Good Privacy because it's effective and free. Cryptography systems can be broadly classified into symmetric-key systems that use a single key that both the sender and recipient have, and public-key systems that use two keys, a public key known to everyone and a private key that only the recipient of messages uses. daemon Last modified: Tuesday, April 22, 2003 Pronounced DEE-mun or DAY-mun. A process that runs in the background and performs a specified operation at predefined times or in response to certain events. The term daemon is a UNIX term, though many other operating systems provide support for daemons, though they're sometimes called other names. Windows, for example, refers to daemons as System Agents and services. Typical daemon processes include print spoolers, e-mail handlers, and other programs that perform administrative tasks for the operating system. The term comes from Greek mythology, where daemons were guardian spirits. data mining Last modified: Monday, December 02, 2002 A class of database applications that look for hidden patterns in a group of data that can be used to predict future behavior. For example, data mining software can help retail companies find customers with common interests. The term is commonly misused to describe software that presents data in new ways. True data mining software doesn't just change the presentation, but actually discovers previously unknown relationships among the data. Data mining is popular in the science and mathematical fields but also is utilized increasingly by marketers trying to distill useful consumer data from Web sites. database Last modified: Friday, June 27, 2003 (1) Often abbreviated DB. A collection of information organized in such a way that a computer program can quickly select desired pieces of data. You can think of a database as an electronic filing system. Traditional databases are organized by fields, records, and files. A field is a single piece of information; a record is one complete set of fields; and a file is a collection of records. For example, a telephone book is analogous to a file. It contains a list of records, each of which consists of three fields: name, address, and telephone number. An alternative concept in database design is known as Hypertext. In a Hypertext database, any object, whether it be a piece of text, a picture, or a film, can be linked to any other object. Hypertext databases are particularly useful for organizing large amounts of disparate information, but they are not designed for numerical analysis. To access information from a database, you need a database management system (DBMS). This is a collection of programs that enables you to enter, organize, and select data in a database. (2) Increasingly, the term database is used as shorthand for database management system. DNS Last modified: Tuesday, March 23, 2004 (1) Short for Domain Name System (or Service or Server), an Internet service that translates domain names into IP addresses. Because domain names are alphabetic, they're easier to remember. The Internet however, is really based on IP addresses. Every time you use a domain name, therefore, a DNS service must translate the name into the corresponding IP address. For example, the domain name www.example.com might translate to 198.105.232.4. The DNS system is, in fact, its own network. If one DNS server doesn't know how to translate a particular domain name, it asks another one, and so on, until the correct IP address is returned. (2) Short for digital nervous system, a term coined by Bill Gates to describe a network of personal computers that make it easier to obtain and understand information. DOS Last modified: Friday, December 14, 2001 (1) Acronym for disk operating system. The term DOS can refer to any operating system, but it is most often used as a shorthand for MS-DOS (Microsoft disk operating system). Originally developed by Microsoft for IBM, MS-DOS was the standard operating system for IBM-compatible personal computers. The initial versions of DOS were very simple and resembled another operating system called CP/M. Subsequent versions have became increasingly sophisticated as they incorporated features of minicomputer operating systems. However, DOS is still a 16bit operating system and does not support multiple users or multitasking. For some time, it has been widely acknowledged that DOS is insufficient for modern computer applications. Microsoft Windows helped alleviate some problems, but still, it sat on top of DOS and relied on DOS for many services. Even Windows 95 sat on top of DOS. Newer operating systems, such as Windows NT and OS/2 Warp, do not rely on DOS to the same extent, although they can execute DOS-based programs. It is expected that as these operating systems gain market share, DOS will eventually disappear. In the meantime, Caldera, Inc. markets a version of DOS called DR-OpenDOS that extends MS-DOS in significant ways. (2) See DoS attack. dpi Last modified: Tuesday, May 21, 2002 Abbreviation of dots per inch, which indicates the resolution of images. The more dots per inch, the higher the resolution. A common resolution for laser printers is 600 dots per inch. This means 600 dots across and 600 dots down, so there are 360,000 dots per square inch. DRAM Last modified: Thursday, June 12, 2003 Pronounced dee-ram, DRAM stands for dynamic random access memory, a type of memory used in most personal computers. dumb terminal Last modified: Sunday, September 01, 1996 A display monitor that has no processing capabilities. A dumb terminal is simply an output device that accepts data from the CPU. In contrast, a smart terminal is a monitor that has its own processor for special features, such as bold and blinking characters. Dumb terminals are not as fast as smart terminals, and they do not support as many display features, but they are adequate for most applications. easter egg Last modified: Tuesday, September 24, 2002 A secret message or screen buried in an application. Typically, easter eggs are used to display the credits for the development team or to display a humorous message. To see an easter egg, you need to know a special procedure or sequence of keystrokes. For example, follow these instructions to see a list of people who worked on the User Assistance feature of Microsoft Word 2000: 1. Open Microsoft Word2000 2. Press F1 or click the "Office Assistant" button 3. Under the "What would you like to do?", type "Cast" (No quotes) 4. Click SEARCH 5. Click the MICROSOFT OFFICE 2000 USER ASSISTANCE STAFF topic 6. Click the graphic in the Microsoft Word Help screen Ethernet Last modified: Tuesday, February 18, 2003 A local-area network (LAN) architecture developed by Xerox Corporation in cooperation with DEC and Intel in 1976. Ethernet uses a bus or star topology and supports data transfer rates of 10 Mbps. The Ethernet specification served as the basis for the IEEE 802.3 standard, which specifies the physical and lower software layers. Ethernet uses the CSMA/CD access method to handle simultaneous demands. It is one of the most widely implemented LAN standards. A newer version of Ethernet, called 100Base-T (or Fast Ethernet), supports data transfer rates of 100 Mbps. And the newest version, Gigabit Ethernet supports data rates of 1 gigabit (1,000 megabits) per second. Also see the Ethernet Designations chart in the Quick Reference section of Webopedia. firewall Last modified: Tuesday, August 03, 2004 (f¥r´wâl) (n.) A system designed to prevent unauthorized access to or from a private network. Firewalls can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria. There are several types of firewall techniques: * Packet filter: Looks at each packet entering or leaving the network and accepts or rejects it based on user-defined rules. Packet filtering is fairly effective and transparent to users, but it is difficult to configure. In addition, it is susceptible to IP spoofing. * Application gateway: Applies security mechanisms to specific applications, such as FTP and Telnet servers. This is very effective, but can impose a performance degradation. * Circuit-level gateway: Applies security mechanisms when a TCP or UDP connection is established. Once the connection has been made, packets can flow between the hosts without further checking. * Proxy server: Intercepts all messages entering and leaving the network. The proxy server effectively hides the true network addresses. In practice, many firewalls use two or more of these techniques in concert. A firewall is considered a first line of defense in protecting private information. For greater security, data can be encrypted. FLOPS Last modified: Tuesday, October 30, 2001 Short for floating-point operations per second, a common benchmark measurement for rating the speed of microprocessors. Floating-point operations include any operations that involve fractional numbers. Such operations, which take much longer to compute than integer operations, occur often in some applications. Most modern microprocessors include a floating-point unit (FPU), which is a specialized part of the microprocessor responsible for executing floating-point operations. The FLOPS measurement, therefore, actually measures the speed of the FPU. One of the most common benchmark tests used to measure FLOPS is called Linpack. Many experts feel that FLOPS is not a relevant measurement because it fails to take into account factors such as the condition under which the microprocessor is running (e.g., heavy or light loads) and which exact operations are included as floating-point operations. For this reason, a consortium of vendors created the Standard Performance Evaluation Corporation (SPEC), which provides more meaningful benchmark values. A megaFLOPS (MFLOPS) is equal to one million floating-point operations per second, and a gigaFLOPS (GFLOPS) is equal to one billion floating-point operations per second. fps Last modified: Monday, August 02, 2004 (pronounced as separate letters) Short for frames per second (and typically written in lower case), a measure of how much information is used to store and display motion video. The term applies equally to film video and digital video. Each frame is a still image; displaying frames in quick succession creates the illusion of motion. The more frames per second (fps), the smoother the motion appears. Television in the U.S., for example, is based on the NTSC format, which displays 30 interlaced frames per second (60 fields per second). In general, the minimum fps needed to avoid jerky motion is about 30. Some computer video formats, such as AVI, provide only 15 frames per second. fractal Last modified: Sunday, September 01, 1996 A word coined by Benoit Mandelbrot in 1975 to describe shapes that are "self-similar" -that is, shapes that look the same at different magnifications. To create a fractal, you start with a simple shape and duplicate it successively according to a set of fixed rules. Oddly enough, such a simple formula for creating shapes can produce very complex structures, some of which have a striking resemblance to objects that appear in the real world. For example, graphics designers use fractals to generate images of mountainous landscapes, coastlines, and flowers. In fact, many of the computer -generated images that appear in science fiction films utilize fractals. FORTRAN Last modified: Tuesday, May 19, 1998 Acronym for formula translator, FORTRAN is the oldest high-level programming language. Designed by John Backus for IBM in the late 1950s, it is still popular today, particularly for scientific applications that require extensive mathematical computations. The two most common versions of FORTRAN are FORTRAN IV and FORTRAN 77. FORTRAN IV was approved as a USASI standard in 1966. FORTRAN 77 is a version of FORTRAN that was approved by ANSI in 1978 (they had expected to approve it in 1977, hence the name). FORTRAN 77 includes a number of features not available in older versions of FORTRAN. A new ISO and ANSI standard for FORTRAN, called FORTRAN-90, was developed in the early 90s. front end Last modified: Friday, November 01, 1996 (1) For software applications, front end is the same as user interface. (2) In client/server applications, the client part of the program is often called the front end and the server part is called the back end. (3) Compilers, the programs that translate source code into object code, are often composed of two parts: a front end and a back end. The front end is responsible for checking syntax and detecting errors, whereas the back end performs the actual translation into object code. FTP Last modified: Wednesday, July 21, 2004 Short for File Transfer Protocol, the protocol for exchanging files over the Internet. FTP works in the same way as HTTP for transferring Web pages from a server to a user's browser and SMTP for transferring electronic mail across the Internet in that, like these technologies, FTP uses the Internet's TCP/IP protocols to enable data transfer. FTP is most commonly used to download a file from a server using the Internet or to upload a file to a server (e.g., uploading a Web page file to a server). GIF Last modified: Monday, May 05, 2003 Pronounced jiff or giff (hard g) stands for graphics interchange format, a bit-mapped graphics file format used by the World Wide Web, CompuServe and many BBSs. GIF supports color and various resolutions. It also includes data compression, but because it is limited to 256 colors, it is more effective for scanned images such as illustrations rather than color photos. GPS Last modified: Wednesday, September 25, 2002 Short for Global Positioning System, a worldwide MEO satellite navigational system formed by 24 satellites orbiting the earth and their corresponding receivers on the earth. The satellites orbit the earth at approximately 12,000 miles above the surface and make two complete orbits every 24 hours. The GPS satellites continuously transmit digital radio signals that contain data on the satellites location and the exact time to the earthbound receivers. The satellites are equipped with atomic clocks that are precise to within a billionth of a second. Based on this information the receivers know how long it takes for the signal to reach the receiver on earth. As each signal travels at the speed of light, the longer it takes the receiver to get the signal, the farther away the satellite is. By knowing how far away a satellite is, the receiver knows that it is located somewhere on the surface of an imaginary sphere centered at the satellite. By using three satellites, GPS can calculate the longitude and latitude of the receiver based on where the three spheres intersect. By using four satellites, GPS can also determine altitude. GPS was developed and is operated by the U.S. Department of Defense. It was originally called NAVSTAR (Navigation System with Timing and Ranging). Before its civilian applications, GPS was used to provide all-weather round-the-clock navigation capabilities for military ground, sea, and air forces. GPS has applications beyond navigation and location determination. GPS can be used for cartography, forestry, mineral exploration, wildlife habitation management, monitoring the movement of people and things and bringing precise timing to the world. GUI Last modified: Wednesday, January 22, 2003 Pronounced GOO-ee. Acronym for graphical user interface. HTML Last modified: Monday, June 14, 2004 Short for HyperText Markup Language, the authoring language used to create documents on the World Wide Web. HTML is similar to SGML, although it is not a strict subset. HTML defines the structure and layout of a Web document by using a variety of tags and attributes. The correct structure for an HTML document starts with <HTML><HEAD>(enter here what document is about) and ends with </BODY></HTML>. All the information you'd like to include in your Web page fits in between the <BODY> and </BODY> tags. There are hundreds of other tags used to format and layout the information in a Web page. Tags are also used to specify hypertext links. These allow Web developers to direct users to other Web pages with only a click of the mouse on either an image or word(s). For a more complete list of tags, check out some of the URLs below. IEEE Last modified: Monday, July 19, 2004 Abbreviation of Institute of Electrical and Electronics Engineers, pronounced I-triple-E. Founded in 1884 as the AIEE, the IEEE was formed in 1963 when AIEE merged with IRE. IEEE is an organization composed of engineers, scientists, and students. The IEEE is best known for developing standards for the computer and electronics industry. In particular, the IEEE 802 standards for local-area networks are widely followed. impression Last modified: Tuesday, February 11, 2003 An advertisement's appearance on an accessed Web page. For example, if the page you're on shows three ads, that's three impressions. Advertisers use impressions to measure the number of views their ads receive, and publishers often sell ad space according to impressions. (It can be tough to know, though, whether an impression really means a visitor saw the ad, since they could be browsing without graphics or might not have scrolled down far enough.) Impressions are tracked in a log maintained by a site server and are often sold on a cost per thousand (CPM) basis. Intel Last modified: Thursday, November 08, 2001 The world's largest manufacturer of computer chips. Although it has been challenged in recent years by newcomers AMD and Cyrix, Intel still dominates the market for PC microprocessors. Nearly all PCs are based on Intel's x86 architecture. Intel was founded in 1968 by Bob Noyce and Gordon Moore. Strategically, it is closely allied with Microsoft because the Windows 3.x and 95 operating systems are designed for x86 microprocessors. The popularity of Windows creates a demand for Intel or Intelcompatible microprocessors. Many people refer to this alliance as Wintel (short for Windows-Intel). InterNIC Last modified: Thursday, January 08, 2004 Short for Internet Network Information Center, a registered service mark of the U.S. Department of Commerce and now a defunct entity. InterNIC began as a collaborative project between AT&T and Network Solutions, Inc. (NSI) supported by the National Science Foundation. When active, the project offered four services: * InterNIC Directory and Database Services -- online white pages directory and directory of publicly accessible databases managed by AT&T. * Registration Services -- domain name and IP address assignment managed by NSI. * Support Services -- outreach, education, and information services for the Internet community managed by NSI. * Net Scout Services -- online publications that summarize recent happenings of interest to Internet users (managed by NSI). The InterNIC is currently an informational Web site established to provide the public with information about domain name registration. ICANN now oversees the domain name registration industry. IP Last modified: Monday, June 07, 2004 Abbreviation of Internet Protocol, pronounced as two separate letters. IP specifies the format of packets, also called datagrams, and the addressing scheme. Most networks combine IP with a higher-level protocol called Transmission Control Protocol (TCP), which establishes a virtual connection between a destination and a source. IP by itself is something like the postal system. It allows you to address a package and drop it in the system, but there's no direct link between you and the recipient. TCP/IP, on the other hand, establishes a connection between two hosts so that they can send messages back and forth for a period of time. The current version of IP is IPv4. A new version, called IPv6 or IPng, is under development. ISDN Last modified: Monday, July 28, 2003 Abbreviation of integrated services digital network, an international communications standard for sending voice, video, and data over digital telephone lines or normal telephone wires. ISDN supports data transfer rates of 64 Kbps (64,000 bits per second). There are two types of ISDN: * Basic Rate Interface (BRI) -- consists of two 64-Kbps B-channels and one Dchannel for transmitting control information. * Primary Rate Interface (PRI) -- consists of 23 B-channels and one D-channel (U.S.) or 30 B-channels and one D-channel (Europe). The original version of ISDN employs baseband transmission. Another version, called B-ISDN, uses broadband transmission and is able to support transmission rates of 1.5 Mbps. B-ISDN requires fiber optic cables and is not widely available. ISP Last modified: Friday, March 12, 2004 Short for Internet Service Provider, a company that provides access to the Internet. For a monthly fee, the service provider gives you a software package, username, password and access phone number. Equipped with a modem, you can then log on to the Internet and browse the World Wide Web and USENET, and send and receive e-mail. In addition to serving individuals, ISPs also serve large companies, providing a direct connection from the company's networks to the Internet. ISPs themselves are connected to one another through Network Access Points (NAPs). ISPs are also called IAPs (Internet Access Providers). Java Last modified: Thursday, May 01, 2003 A high-level programming language developed by Sun Microsystems. Java was originally called OAK, and was designed for handheld devices and set-top boxes. Oak was unsuccessful so in 1995 Sun changed the name to Java and modified the language to take advantage of the burgeoning World Wide Web. Java is an object-oriented language similar to C++, but simplified to eliminate language features that cause common programming errors. Java source code files (files with a .java extension) are compiled into a format called bytecode (files with a .class extension), which can then be executed by a Java interpreter. Compiled Java code can run on most computers because Java interpreters and runtime environments, known as Java Virtual Machines (VMs), exist for most operating systems, including UNIX, the Macintosh OS, and Windows. Bytecode can also be converted directly into machine language instructions by a just-in-time compiler (JIT). Java is a general purpose programming language with a number of features that make the language well suited for use on the World Wide Web. Small Java applications are called Java applets and can be downloaded from a Web server and run on your computer by a Java-compatible Web browser, such as Netscape Navigator or Microsoft Internet Explorer. JPEG Last modified: Monday, May 05, 2003 Short for Joint Photographic Experts Group, and pronounced jay-peg. JPEG is a lossy compression technique for color images. Although it can reduce files sizes to about 5% of their normal size, some detail is lost in the compression. Also see JPG vs. GIF vs. PNG in the Did You Know . . . ? section of Webopedia. LAN (yields) local-area network Last modified: Tuesday, February 18, 2003 A computer network that spans a relatively small area. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected to other LANs over any distance via telephone lines and radio waves. A system of LANs connected in this way is called a wide-area network (WAN). Most LANs connect workstations and personal computers. Each node (individual computer ) in a LAN has its own CPU with which it executes programs, but it also is able to access data and devices anywhere on the LAN. This means that many users can share expensive devices, such as laser printers, as well as data. Users can also use the LAN to communicate with each other, by sending e-mail or engaging in chat sessions. There are many different types of LANs Ethernets being the most common for PCs. Most Apple Macintosh networks are based on Apple's AppleTalk network system, which is built into Macintosh computers. The following characteristics differentiate one LAN from another: * topology : The geometric arrangement of devices on the network. For example, devices can be arranged in a ring or in a straight line. * protocols : The rules and encoding specifications for sending data. The protocols also determine whether the network uses a peer-to-peer or client/server architecture. * media : Devices can be connected by twisted-pair wire, coaxial cables, or fiber optic cables. Some networks do without connecting media altogether, communicating instead via radio waves. LANs are capable of transmitting data at very fast rates, much faster than data can be transmitted over a telephone line; but the distances are limited, and there is also a limit on the number of computers that can be attached to a single LAN. LCD Last modified: Wednesday, June 02, 2004 Short for liquid crystal display, a type of display used in digital watches and many portable computers. LCD displays utilize two sheets of polarizing material with a liquid crystal solution between them. An electric current passed through the liquid causes the crystals to align so that light cannot pass through them. Each crystal, therefore, is like a shutter, either allowing light to pass through or blocking the light. Monochrome LCD images usually appear as blue or dark gray images on top of a grayish-white background. Color LCD displays use two basic techniques for producing color: Passive matrix is the less expensive of the two technologies. The other technology, called thin film transistor (TFT) or active-matrix, produces color images that are as sharp as traditional CRT displays, but the technology is expensive. Recent passive-matrix displays using new CSTN and DSTN technologies produce sharp colors rivaling activematrix displays. Most LCD screens used in notebook computers are backlit, or transmissive, to make them easier to read. Linux Last modified: Wednesday, April 28, 2004 Pronounced lee-nucks or lih-nucks. A freely-distributable open source operating system that runs on a number of hardware platforms. The Linux kernel was developed mainly by Linus Torvalds. Because it's free, and because it runs on many platforms, including PCs and Macintoshes, Linux has become an extremely popular alternative to proprietary operating systems. log file Last modified: Tuesday, March 12, 2002 A file that lists actions that have occurred. For example, Web servers maintain log files listing every request made to the server. With log file analysis tools, it's possible to get a good idea of where visitors are coming from, how often they return, and how they navigate through a site. Using cookies enables Webmasters to log even more detailed information about how individual users are accessing a site. mainframe Last modified: Monday, October 14, 2002 A very large and expensive computer capable of supporting hundreds, or even thousands, of users simultaneously. In the hierarchy that starts with a simple microprocessor (in watches, for example) at the bottom and moves to supercomputers at the top, mainframes are just below supercomputers. In some ways, mainframes are more powerful than supercomputers because they support more simultaneous programs. But supercomputers can execute a single program faster than a mainframe. The distinction between small mainframes and minicomputers is vague, depending really on how the manufacturer wants to market its machines. middleware Last modified: Friday, June 04, 2004 Software that connects two otherwise separate applications. For example, there are a number of middleware products that link a database system to a Web server. This allows users to request data from the database using forms displayed on a Web browser, and it enables the Web server to return dynamic Web pages based on the user's requests and profile. The term middleware is used to describe separate products that serve as the glue between two applications. It is, therefore, distinct from import and export features that may be built into one of the applications. Middleware is sometimes called plumbing because it connects two sides of an application and passes data between them. Common middleware categories include: * * * * * * * ESBs TP monitors DCE environments RPC systems Object Request Brokers (ORBs) Database access systems Message Passing MIDI Last modified: Friday, May 16, 2003 Pronounced middy, an acronym for musical instrument digital interface, a standard adopted by the electronic music industry for controlling devices, such as synthesizers and sound cards, that emit music. At minimum, a MIDI representation of a sound includes values for the note's pitch, length, and volume. It can also include additional characteristics, such as attack and delay time. The MIDI standard is supported by most synthesizers, so sounds created on one synthesizer can be played and manipulated on another synthesizer. Computers that have a MIDI interface can record sounds created by a synthesizer and then manipulate the data to produce new sounds. For example, you can change the key of a composition with a single keystroke. A number of software programs are available for composing and editing music that conforms to the MIDI standard. They offer a variety of functions: for instance, when you play a tune on a keyboard connected to a computer, a music program can translate what you play into a written score. Moore's Law Last modified: Sunday, March 22, 1998 The observation made in 1965 by Gordon Moore, co-founder of Intel, that the number of transistors per square inch on integrated circuits had doubled every year since the integrated circuit was invented. Moore predicted that this trend would continue for the foreseeable future. In subsequent years, the pace slowed down a bit, but data density has doubled approximately every 18 months, and this is the current definition of Moore's Law, which Moore himself has blessed. Most experts, including Moore himself, expect Moore's Law to hold for at least another two decades. Mosaic Last modified: Sunday, September 01, 1996 An application that simplifies accessing documents on the World Wide Web. Originally produced by the National Center for Supercomputing Applications (NCSA), Mosaic has always been distributed as freeware. In 1994, however, the NCSA turned over commercial development of the program to a company called Spyglass. There are now several varieties of Mosaic, some free and some for sale. Mozilla Last modified: Monday, January 13, 2003 The original name for Netscape's browser, now called Navigator. Some people claim that the term is a contraction of Mosaic Godzilla (e.g., Mosaic killer), since Mosaic was the number one Web browser at the time Netscape began developing its product. The term Mozilla is still used by many Web developers and appears in server log files that identify the browsers being used. In 1998, Netscape decided to make the source code for Navigator freely available to the public, or open source. The Netscape group responsible for releasing the code is called mozilla.org, and its Web site is www.mozilla.org. MPEG Last modified: Thursday, January 22, 2004 Short for Moving Picture Experts Group, and pronounced m-peg, a working group of ISO. The term also refers to the family of digital video compression standards and file formats developed by the group. MPEG generally produces better-quality video than competing formats, such as Video for Windows, Indeo and QuickTime. MPEG files can be decoded by special hardware or by software. MPEG achieves high compression rate by storing only the changes from one frame to another, instead of each entire frame. The video information is then encoded using a technique called DCT. MPEG uses a type of lossy compression, since some data is removed. But the diminishment of data is generally imperceptible to the human eye. There are three major MPEG standards: MPEG-1, MPEG-2 and MPEG-4. * The most common implementations of the MPEG-1 standard provide a video resolution of 352-by-240 at 30 frames per second (fps). This produces video quality slightly below the quality of conventional VCR videos. * MPEG-2 offers resolutions of 720x480 and 1280x720 at 60 fps, with full CDquality audio. This is sufficient for all the major TV standards, including NTSC, and even HDTV. MPEG-2 is used by DVD-ROMs. MPEG-2 can compress a 2 hour video into a few gigabytes. While decompressing an MPEG-2 data stream requires only modest computing power, encoding video in MPEG-2 format requires significantly more processing power. * MPEG-4 is a graphics and video compression algorithm standard that is based on MPEG-1 and MPEG-2 and Apple QuickTime technology. Wavelet-based MPEG-4 files are smaller than JPEG or QuickTime files, so they are designed to transmit video and images over a narrower bandwidth and can mix video with text, graphics and 2-D and 3-D animation layers. MPEG-4 was standardized in October 1998 in the ISO/IEC document 14496. •E-mail this definition to a colleague• MP3 Last modified: Monday, May 17, 2004 The name of the file extension and also the name of the type of file for MPEG, audio layer 3. Layer 3 is one of three coding schemes (layer 1, layer 2 and layer 3) for the compression of audio signals. Layer 3 uses perceptual audio coding and psychoacoustic compression to remove all superfluous information (more specifically, the redundant and irrelevant parts of a sound signal. The stuff the human ear doesn't hear anyway). It also adds a MDCT (Modified Discrete Cosine Transform) that implements a filter bank, increasing the frequency resolution 18 times higher than that of layer 2. The result in real terms is layer 3 shrinks the original sound data from a CD (with a bit rate of 1411.2 kilobits per one second of stereo music) by a factor of 12 (down to 112128kbps) without sacrificing sound quality. Because MP3 files are small, they can easily be transferred across the Internet. NOC Last modified: Thursday, October 18, 2001 Short for network operations center, the physical space from which a typically large telecommunications network is managed, monitored and supervised. The NOC coordinates network troubles, provides problem management and router configuration services, manages network changes, allocates and manages domain names and IP addresses, monitors routers, switches, hubs and UPS systems that keep the network operating smoothly, manages the distribution and updating of software and coordinates with affiliated networks. NOCs also provide network accessibility to users connecting to the network from outside of the physical office space or campus. OC Last modified: Wednesday, August 18, 2004 Short for Optical Carrier, used to specify the speed of fiber optic networks conforming to the SONET standard. The table shows the speeds for common OC levels. OC = Speed OC-1 = 51.85 Mbps OC-3 = 155.52 Mbps OC-12 = 622.08 Mbps OC-24 = 1.244 Gbps OC-48 = 2.488 Gbps OC-192 = 9.952 Gbps OC-255 = 13.21 Gbps optical character recognition Last modified: Thursday, December 19, 2002 Often abbreviated OCR, optical character recognition refers to the branch of computer science that involves reading text from paper and translating the images into a form that the computer can manipulate (for example, into ASCII codes). An OCR system enables you to take a book or a magazine article, feed it directly into an electronic computer file, and then edit the file using a word processor. All OCR systems include an optical scanner for reading text, and sophisticated software for analyzing images. Most OCR systems use a combination of hardware (specialized circuit boards) and software to recognize characters, although some inexpensive systems do it entirely through software. Advanced OCR systems can read text in large variety of fonts, but they still have difficulty with handwritten text. The potential of OCR systems is enormous because they enable users to harness the power of computers to access printed documents. OCR is already being used widely in the legal profession, where searches that once required hours or days can now be accomplished in a few seconds. OEM Last modified: Monday, August 23, 2004 (pronounced as separate letters) Short for original equipment manufacturer, which is a misleading term for a company that has a special relationship with computer producers. OEMs buy computers in bulk and customize them for a particular application. They then sell the customized computer under their own name. The term is really a misnomer because OEMs are not the original manufacturers -- they are the customizers. Contrast with IHV. object-oriented programming Last modified: Tuesday, January 07, 2003 A type of programming in which programmers define not only the data type of a data structure, but also the types of operations (functions) that can be applied to the data structure. In this way, the data structure becomes an object that includes both data and functions. In addition, programmers can create relationships between one object and another. For example, objects can inherit characteristics from other objects. One of the principal advantages of object-oriented programming techniques over procedural programming techniques is that they enable programmers to create modules that do not need to be changed when a new type of object is added. A programmer can simply create a new object that inherits many of its features from existing objects. This makes object-oriented programs easier to modify. To perform object-oriented programming, one needs an object-oriented programming language (OOPL). Java, C++ and Smalltalk are three of the more popular languages, and there are also object-oriented versions of Pascal. open source Last modified: Friday, March 12, 2004 (1) Generically, open source refers to a program in which the source code is available to the general public for use and/or modification from its original design free of charge, i.e., open. Open source code is typically created as a collaborative effort in which programmers improve upon the code and share the changes within the community. Open source sprouted in the technological community as a response to proprietary software owned by corporations. (2) A certification standard issued by the Open Source Initiative (OSI) that indicates that the source code of a computer program is made available free of charge to the general public. The rationale for this movement is that a larger group of programmers not concerned with proprietary ownership or financial gain will produce a more useful and bug -free product for everyone to use. The concept relies on peer review to find and eliminate bugs in the program code, a process which commercially developed and packaged programs do not utilize. Programmers on the Internet read, redistribute and modify the source code, forcing an expedient evolution of the product. The process of eliminating bugs and improving the software happens at a much quicker rate than through the traditional development channels of commercial software as the information is shared throughout the open source community and does not originate and channel through a corporation's research and development cogs. OSI dictates that in order to be considered "OSI Certified" a product must meet the following criteria: * The author or holder of the license of the source code cannot collect royalties on the distribution of the program * The distributed program must make the source code accessible to the user * The author must allow modifications and derivations of the work under the program's original name * No person, group or field of endeavor can be denied access to the program * The rights attached to the program must not depend on the program's being part of a particular software distribution * The licensed software cannot place restrictions on other software that is distributed with it. opt-in e-mail Last modified: Wednesday, May 19, 2004 A term that refers to promotional e-mails that have been requested by the individual receiving them. Unlike spam promotional e-mails that get sent out to large lists of recipients without regard to whether or not they want the information, opt-in e-mails are only sent to people who specifically request them. Opt-in e-mails are targeted and often personalized and carry information about specific topics or promotions that users are interested in learning about. Typical opt-in e-mails contain newsletters, product information or special promotional offers. For example, if a user frequented a Web site that sold books and music online, that user could "opt in" to receive announcements when his favorite author or musician released new material. The promotional e-mail may even present the recipient with a special promotional offer to purchase the product at a discount available only to those on the opt-in list. Spammers, however, have found a way to use the opt-in feature to their advantage. Spam e-mails often come with opt-in features in fine print or obscured somewhere in the body of the e-mail with text that reads something to the effect of "Failure to respond to this e-mail will automatically opt-in the recipient to future mailings." The strategy of responding to the spam and asking to be removed from future mailings also has critics as some claim that responding to a spam e-mail with a request to be removed from the mailing list signals that the e-mail address is a working address and the address can then be passed on to other spammers. Oracle Last modified: Friday, September 26, 2003 Based in Redwood, California, Oracle Corporation is the largest software company whose primary business is database products. Historically, Oracle has targeted highend workstations and minicomputers as the server platforms to run its database systems. Its relational database was the first to support the SQL language, which has since become the industry standard. Along with Sun Microsystems, Oracle has been one of the leading champions of network computers. packet Last modified: Tuesday, August 03, 2004 (pak´it) (n.) A piece of a message transmitted over a packet-switching network. See under packet switching. One of the key features of a packet is that it contains the destination address in addition to the data. In IP networks, packets are often called datagrams. Perl Last modified: Friday, March 12, 2004 Short for Practical Extraction and Report Language, Perl is a programming language developed by Larry Wall, especially designed for processing text. Because of its strong text processing abilities, Perl has become one of the most popular languages for writing CGI scripts. Perl is an interpretive language, which makes it easy to build and test simple programs. PGP (yields) Pretty Good Privacy Last modified: Wednesday, May 19, 2004 (n.) Abbreviated as PGP, a technique developed by Philip Zimmerman for encrypting messages. PGP is one of the most common ways to protect messages on the Internet because it is effective, easy to use, and free. PGP is based on the public-key method, which uses two keys -- one is a public key that you disseminate to anyone from whom you want to receive a message. The other is a private key that you use to decrypt messages that you receive. To encrypt a message using PGP, you need the PGP encryption package, which is available for free from a number of sources. The official repository is at the Massachusetts Institute of Technology. PGP is such an effective encryption tool that the U.S. government actually brought a lawsuit against Zimmerman for putting it in the public domain and hence making it available to enemies of the U.S. After a public outcry, the U.S. lawsuit was dropped, but it is still illegal to use PGP in many other countries. PING Last modified: Tuesday, February 18, 2003 A utility to determine whether a specific IP address is accessible. It works by sending a packet to the specified address and waiting for a reply. PING is used primarily to troubleshoot Internet connections. There are many freeware and shareware Ping utilities available for personal computers. It is often believed that "Ping" is an abbreviation for Packet Internet Groper, but Ping's author has stated that the names comes from the sound that a sonar makes. pixel Last modified: Wednesday, June 02, 2004 Short for Picture Element, a pixel is a single point in a graphic image. Graphics monitors display pictures by dividing the display screen into thousands (or millions) of pixels, arranged in rows and columns. The pixels are so close together that they appear connected. The number of bits used to represent each pixel determines how many colors or shades of gray can be displayed. For example, in 8-bit color mode, the color monitor uses 8 bits for each pixel, making it possible to display 2 to the 8th power (256) different colors or shades of gray. On color monitors, each pixel is actually composed of three dots -- a red, a blue, and a green one. Ideally, the three dots should all converge at the same point, but all monitors have some convergence error that can make color pixels appear fuzzy. The quality of a display system largely depends on its resolution, how many pixels it can display, and how many bits are used to represent each pixel. VGA systems display 640 by 480, or about 300,000 pixels. In contrast, SVGA systems display 800 by 600, or 480,000 pixels. True Color systems use 24 bits per pixel, allowing them to display more than 16 million different colors. POP Last modified: Tuesday, May 13, 2003 (1) Short for Post Office Protocol, a protocol used to retrieve e-mail from a mail server. Most e-mail applications (sometimes called an e-mail client) use the POP protocol, although some can use the newer IMAP (Internet Message Access Protocol). There are two versions of POP. The first, called POP2, became a standard in the mid80's and requires SMTP to send messages. The newer version, POP3, can be used with or without SMTP. (2) Short for point of presence, an access point to the Internet. ISPs have typically multiple POPs. A point of presence is a physical location, either part of the facilities of a telecommunications provider that the ISP rents or a separate location from the telecommunications provider, that houses servers, routers, ATM switches and digital/analog call aggregators. queue Last modified: Friday, February 13, 2004 (v.) To line up. In computer science, queuing refers to lining up jobs for a computer or device. For example, if you want to print a number of documents, the operating system (or a special print spooler) queues the documents by placing them in a special area called a print buffer or print queue. The printer then pulls the documents off the queue one at a time. Another term for this is print spooling . The order in which a system executes jobs on a queue depends on the priority system being used. Most commonly, jobs are executed in the same order that they were placed on the queue, but in some schemes certain jobs are given higher priority. (n.) (1) A group of jobs waiting to be executed. (2) In programming, a queue is a data structure in which elements are removed in the same order they were entered. This is often referred to as FIFO (first in, first out). In contrast, a stack is a data structure in which elements are removed in the reverse order from which they were entered. This is referred to as LIFO (last in, first out). RAID Last modified: Wednesday, July 28, 2004 (rÇd) Short for Redundant Array of Independent (or Inexpensive) Disks, a category of disk drives that employ two or more drives in combination for fault tolerance and performance. RAID disk drives are used frequently on servers but aren't generally necessary for personal computers. There are number of different RAID levels: * Level 0 -- Striped Disk Array without Fault Tolerance: Provides data striping (spreading out blocks of each file across multiple disk drives) but no redundancy. This improves performance but does not deliver fault tolerance. If one drive fails then all data in the array is lost. * Level 1 -- Mirroring and Duplexing: Provides disk mirroring. Level 1 provides twice the read transaction rate of single disks and the same write transaction rate as single disks. * Level 2 -- Error-Correcting Coding: Not a typical implementation and rarely used, Level 2 stripes data at the bit level rather than the block level. * Level 3 -- Bit-Interleaved Parity: Provides byte-level striping with a dedicated parity disk. Level 3, which cannot service simultaneous multiple requests, also is rarely used. * Level 4 -- Dedicated Parity Drive: A commonly used implementation of RAID, Level 4 provides block-level striping (like Level 0) with a parity disk. If a data disk fails, the parity data is used to create a replacement disk. A disadvantage to Level 4 is that the parity disk can create write bottlenecks. * Level 5 -- Block Interleaved Distributed Parity: Provides data striping at the byte level and also stripe error correction information. This results in excellent performance and good fault tolerance. Level 5 is one of the most popular implementations of RAID. * Level 6 -- Independent Data Disks with Double Parity: Provides block-level striping with parity data distributed across all disks. * Level 0+1 – A Mirror of Stripes: Not one of the original RAID levels, two RAID 0 stripes are created, and a RAID 1 mirror is created over them. Used for both replicating and sharing data among disks. * Level 10 – A Stripe of Mirrors: Not one of the original RAID levels, multiple RAID 1 mirrors are created, and a RAID 0 stripe is created over these. * Level 7: A trademark of Storage Computer Corporation that adds caching to Levels 3 or 4. * RAID S: EMC Corporation's proprietary striped pairty RAID system used in its Symmetrix storage systems. RAM Last modified: Tuesday, February 24, 2004 Pronounced ramm, acronym for random access memory, a type of computer memory that can be accessed randomly; that is, any byte of memory can be accessed without touching the preceding bytes. RAM is the most common type of memory found in computers and other devices, such as printers. There are two basic types of RAM: * dynamic RAM (DRAM) * static RAM (SRAM) The two types differ in the technology they use to hold data, dynamic RAM being the more common type. Dynamic RAM needs to be refreshed thousands of times per second. Static RAM does not need to be refreshed, which makes it faster; but it is also more expensive than dynamic RAM. Both types of RAM are volatile, meaning that they lose their contents when the power is turned off. In common usage, the term RAM is synonymous with main memory, the memory available to programs. For example, a computer with 8M RAM has approximately 8 million bytes of memory that programs can use. In contrast, ROM (read-only memory) refers to special memory used to store programs that boot the computer and perform diagnostics. Most personal computers have a small amount of ROM (a few thousand bytes). In fact, both types of memory (ROM and RAM) allow random access. To be precise, therefore, RAM should be referred to as read/write RAM and ROM as read-only RAM. reboot Last modified: Monday, May 18, 1998 To restart a computer. In DOS, you can reboot by pressing the Alt, Control and Delete keys simultaneously. This is called a warm boot. You can also perform a cold boot by turning the computer off and then on again. On Macs, you reboot by selecting the "Restart" option from the Special menu. RFID Last modified: Thursday, August 12, 2004 (pronounced as separate letters) Short for radio frequency identification, a technology similar in theory to bar code identification. With RFID, the electromagnetic or electrostatic coupling in the RF portion of the electromagnetic spectrum is used to transmit signals. An RFID system consists of an antenna and a transceiver, which read the radio frequency and transfer the information to a processing device, and a transponder, or tag, which is an integrated circuit containing the RF circuitry and information to be transmitted. RFID systems can be used just about anywhere, from clothing tags to missiles to pet tags to food -- anywhere that a unique identification system is needed. The tag can carry information as simple as a pet owners name and address or the cleaning instruction on a sweater to as complex as instructions on how to assemble a car. Some auto manufacturers use RFID systems to move cars through an assembly line. At each successive stage of production, the RFID tag tells the computers what the next step of automated assembly is. One of the key differences between RFID and bar code technology is RFID eliminates the need for line-of-sight reading that bar coding depends on. Also, RFID scanning can be done at greater distances than bar code scanning. High frequency RFID systems (850 MHz to 950 MHz and 2.4 GHz to 2.5 GHz) offer transmission ranges of more than 90 feet, although wavelengths in the 2.4 GHz range are absorbed by water (the human body) and therefore has limitations. RFID is also called dedicated short range communication (DSRC). RGB monitor Last modified: Tuesday, August 06, 2002 Short for red, green, blue monitor, a monitor that requires separate signals for each of the three colors. This differs from color televisions, for example, which use composite video signals, in which all the colors are mixed together. All color computer monitors are RGB monitors. An RGB monitor consists of a vacuum tube with three electron guns -- one each for red, green, and blue -- at one end and the screen at the other end. The three electron guns fire electrons at the screen, which contains a phosphorous coating. When the phosphors are excited by the electron beams, they glow. Depending on which beam excites them, they glow either red, green, or blue. Ideally, the three beams should converge for each point on the screen so that each pixel is a combination of the three colors. Also see The Science of Color and Northern vs. Southern Hemishpere Monitors in the Did You Know . . . ? section of Webopedia. RISC Last modified: Tuesday, October 30, 2001 Pronounced risk, acronym for reduced instruction set computer, a type of microprocessor that recognizes a relatively limited number of instructions. Until the mid-1980s, the tendency among computer manufacturers was to build increasingly complex CPUs that had ever-larger sets of instructions. At that time, however, a number of computer manufacturers decided to reverse this trend by building CPUs capable of executing only a very limited set of instructions. One advantage of reduced instruction set computers is that they can execute their instructions very fast because the instructions are so simple. Another, perhaps more important advantage, is that RISC chips require fewer transistors, which makes them cheaper to design and produce. Since the emergence of RISC computers, conventional computers have been referred to as CISCs (complex instruction set computers). There is still considerable controversy among experts about the ultimate value of RISC architectures. Its proponents argue that RISC machines are both cheaper and faster, and are therefore the machines of the future. Skeptics note that by making the hardware simpler, RISC architectures put a greater burden on the software. They argue that this is not worth the trouble because conventional microprocessors are becoming increasingly fast and cheap anyway. To some extent, the argument is becoming moot because CISC and RISC implementations are becoming more and more alike. Many of today's RISC chips support as many instructions as yesterday's CISC chips. And today's CISC chips use many techniques formerly associated with RISC chips. ROM Last modified: Friday, February 08, 2002 Pronounced rahm, acronym for read-only memory, computer memory on which data has been prerecorded. Once data has been written onto a ROM chip, it cannot be removed and can only be read. Unlike main memory (RAM), ROM retains its contents even when the computer is turned off. ROM is referred to as being nonvolatile, whereas RAM is volatile. Most personal computers contain a small amount of ROM that stores critical programs such as the program that boots the computer. In addition, ROMs are used extensively in calculators and peripheral devices such as laser printers, whose fonts are often stored in ROMs. A variation of a ROM is a PROM (programmable read-only memory). PROMs are manufactured as blank chips on which data can be written with a special device called a PROM programmer . server Last modified: Monday, July 26, 2004 (ser´ver) (n.) A computer or device on a network that manages network resources. For example, a file server is a computer and storage device dedicated to storing files. Any user on the network can store files on the server. A print server is a computer that manages one or more printers, and a network server is a computer that manages network traffic. A database server is a computer system that processes database queries. Servers are often dedicated, meaning that they perform no other tasks besides their server tasks. On multiprocessing operating systems, however, a single computer can execute several programs at once. A server in this case could refer to the program that is managing resources rather than the entire computer. Also see the Server Types page in the Quick Reference section of Webopedia for a comparison of server types. client Last modified: Tuesday, August 10, 2004 (kl¥´&nt) (n.) The client part of a client-server architecture. Typically, a client is an application that runs on a personal computer or workstation and relies on a server to perform some operations. For example, an e-mail client is an application that enables you to send and receive e-mail. SGML Last modified: Tuesday, January 21, 2003 Short forStandard Generalized Markup Language, a system for organizing and tagging elements of a document. SGML was developed and standardized by the International Organization for Standards (ISO) in 1986. SGML itself does not specify any particular formatting; rather, it specifies the rules for tagging elements. These tags can then be interpreted to format elements in different ways. SGML is used widely to manage large documents that are subject to frequent revisions and need to be printed in different formats. Because it is a large and complex system, it is not yet widely used on personal computers. However, the growth of Internet, and especially the World Wide Web, is creating renewed interest in SGML because the World Wide Web uses HTML, which is one way of defining and interpreting tags according to SGML rules. SOAP Last modified: Wednesday, March 12, 2003 Short for Simple Object Access Protocol, a lightweight XML-based messaging protocol used to encode the information in Web service request and response messages before sending them over a network. SOAP messages are independent of any operating system or protocol and may be transported using a variety of Internet protocols, including SMTP, MIME, and HTTP. spam Last modified: Tuesday, July 20, 2004 Electronic junk mail or junk newsgroup postings. Some people define spam even more generally as any unsolicited e-mail. However, if a long-lost brother finds your e-mail address and sends you a message, this could hardly be called spam, even though it's unsolicited. Real spam is generally e-mail advertising for some product sent to a mailing list or newsgroup. In addition to wasting people's time with unwanted e-mail, spam also eats up a lot of network bandwidth. Consequently, there are many organizations, as well as individuals, who have taken it upon themselves to fight spam with a variety of techniques. But because the Internet is public, there is really little that can be done to prevent spam, just as it is impossible to prevent junk mail. However, some online services have instituted policies to prevent spammers from spamming their subscribers. There is some debate about the source of the term, but the generally accepted version is that it comes from the Monty Python song, "Spam spam spam spam, spam spam spam spam, lovely spam, wonderful spam…" Like the song, spam is an endless repetition of worthless text. Another school of thought maintains that it comes from the computer group lab at the University of Southern California who gave it the name because it has many of the same characteristics as the lunchmeat Spam: * Nobody wants it or ever asks for it. * No one ever eats it; it is the first item to be pushed to the side when eating the entree. * Sometimes it is actually tasty, like 1% of junk mail that is really useful to some people. Also see spim. Also see Getting Rid of Spam in the Did You Know section of Webopedia. SQL Last modified: Wednesday, March 10, 2004 Abbreviation of structured query language, and pronounced either see-kwell or as separate letters. SQL is a standardized query language for requesting information from a database. The original version called SEQUEL (structured English query language) was designed by an IBM research center in 1974 and 1975. SQL was first introduced as a commercial database system in 1979 by Oracle Corporation. Historically, SQL has been the favorite query language for database management systems running on minicomputers and mainframes. Increasingly, however, SQL is being supported by PC database systems because it supports distributed databases (databases that are spread out over several computer systems). This enables several users on a local-area network to access the same database simultaneously. Although there are different dialects of SQL, it is nevertheless the closest thing to a standard query language that currently exists. In 1986, ANSI approved a rudimentary version of SQL as the official standard, but most versions of SQL since then have included many extensions to the ANSI standard. In 1991, ANSI updated the standard. The new standard is known as SAG SQL. sysop Last modified: Sunday, September 01, 1996 Pronounced siss-op, short for system operator, an individual who manages a bulletin board system (BBS) , online service , or special interest group (SIG). T-1 carrier Last modified: Wednesday, January 09, 2002 A dedicated phone connection supporting data rates of 1.544Mbits per second. A T-1 line actually consists of 24 individual channels, each of which supports 64Kbits per second. Each 64Kbit/second channel can be configured to carry voice or data traffic. Most telephone companies allow you to buy just some of these individual channels, known as fractional T-1 access. T-1 lines are a popular leased line option for businesses connecting to the Internet and for Internet Service Providers (ISPs) connecting to the Internet backbone. The Internet backbone itself consists of faster T-3 connections. T-1 lines are sometimes referred to as DS1 lines. table Last modified: Tuesday, January 13, 2004 Refers to data arranged in rows and columns. A spreadsheet, for example, is a table. In relational database management systems, all information is stored in the form of tables. tag Last modified: Tuesday, January 21, 2003 (n) A command inserted in a document that specifies how the document, or a portion of the document, should be formatted. Tags are used by all format specifications that store documents as text files. This includes SGML and HTML. (v) To mark a section of a document with a formatting command. TCP Last modified: Monday, April 12, 2004 Abbreviation of Transmission Control Protocol, and pronounced as separate letters. TCP is one of the main protocols in TCP/IP networks. Whereas the IP protocol deals only with packets, TCP enables two hosts to establish a connection and exchange streams of data. TCP guarantees delivery of data and also guarantees that packets will be delivered in the same order in which they were sent. telephony Last modified: Friday, February 28, 2003 The science of translating sound into electrical signals, transmitting them, and then converting them back to sound; that is, the science of telephones. The term is used frequently to refer to computer hardware and software that performs functions traditionally performed by telephone equipment. For example, telephony software can combine with your modem to turn your computer into a sophisticated answering service. Voice mail is another popular telephony application. Telnet Last modified: Monday, July 26, 2004 (tel´net) (n.) A terminal emulation program for TCP/IP networks such as the Internet. The Telnet program runs on your computer and connects your PC to a server on the network. You can then enter commands through the Telnet program and they will be executed as if you were entering them directly on the server console. This enables you to control the server and communicate with other servers on the network. To start a Telnet session, you must log in to a server by entering a valid username and password. Telnet is a common way to remotely control Web servers. terabyte Last modified: Friday, June 21, 2002 2 to the 40th power (1,099,511,627,776) bytes. This is approximately 1 trillion bytes. petabyte Last modified: Tuesday, March 12, 2002 2 to the 50th power (1,125,899,906,842,624) bytes. A petabyte is equal to 1,024 terabytes. TIFF Last modified: Tuesday, April 02, 2002 Acronym for tagged image file format, one of the most widely supported file formats for storing bit-mapped images on personal computers (both PCs and Macintosh computers). Other popular formats are BMP and PCX. TIFF graphics can be any resolution, and they can be black and white, gray-scaled, or color. Files in TIFF format often end with a .tif extension. unique visitor Last modified: Thursday, June 13, 2002 When tracking the amount of traffic on a Web site, it refers to a person who visits a Web site more than once within a specified period of time. Software that tracks and counts Web site traffic can distinguish between visitors who only visit the site once and unique visitors who return to the site. Different from a site's hits or page views -- which are measured by the number of files that are requested from a site -- unique visitors are measured according to their unique IP addresses, which are like online fingerprints, and unique visitors are counted only once no matter how many times they visit the site. There are some ISPs that use Dynamic Host Configuration Protocol, such as AOL and cable modem providers, which use different IPs for every file requested, making one visitor look like many. In this case, a single IP address does not indicate a unique visitor. user session Last modified: Wednesday, April 14, 2004 (1) The session of activity that a user with a unique IP address spends on a Web site during a specified period of time. The number of user sessions on a site is used in measuring the amount of traffic a Web site gets. The site administrator determines what the time frame of a user session will be (e.g., 30 minutes). If the visitor comes back to the site within that time period, it is still considered one user session because any number of visits within that 30 minutes will only count as one session. If the visitor returns to the site after the allotted time period has expired, say an hour from the initial visit, then it is counted as a separate user session. Contrast with unique visitor, hit, click-through and page view, which are all other ways that site administrators measure the amount of traffic a Web site gets. (2) The period of time a user interfaces with an application. The user session begins when the user accesses the application and ends when the user quits the application. UNIX Last modified: Monday, September 22, 2003 Pronounced yoo-niks, a popular multi-user, multitasking operating system developed at Bell Labs in the early 1970s. Created by just a handful of programmers, UNIX was designed to be a small, flexible system used exclusively by programmers. UNIX was one of the first operating systems to be written in a high-level programming language, namely C. This meant that it could be installed on virtually any computer for which a C compiler existed. This natural portability combined with its low price made it a popular choice among universities. (It was inexpensive because antitrust regulations prohibited Bell Labs from marketing it as a full-scale product.) Bell Labs distributed the operating system in its source language form, so anyone who obtained a copy could modify and customize it for his own purposes. By the end of the 1970s, dozens of different versions of UNIX were running at various sites. After its breakup in 1982, AT&T began to market UNIX in earnest. It also began the long and difficult process of defining a standard version of UNIX. Due to its portability, flexibility, and power, UNIX has become a leading operating system for workstations. Historically, it has been less popular in the personal computer market. Today, the trademarked "Unix" and the "Single UNIX Specification" interface are owned by The Open Group. An operating system that is certified by The Open Group to use the UNIX trademark conforms to the Single UNIX Specification. According to The Open Group's Web site, "As the owner of the UNIX trademark, The Open Group has separated the UNIX trademark from any actual code stream itself, thus allowing multiple implementations. Since the introduction of the Single UNIX Specification, there has been a single, open, consensus specification that defines the requirements for a conformant UNIX system. There is also a mark, or brand, that is used to identify those products that have been certified as conforming to the Single UNIX Specification, initially UNIX 93, followed subsequently by UNIX 95, UNIX 98 and now UNIX 03. Both the specification and the UNIX trade mark are managed and held in trust for the industry by The Open Group." URL Last modified: Thursday, January 08, 2004 Abbreviation of Uniform Resource Locator, the global address of documents and other resources on the World Wide Web. The first part of the address indicates what protocol to use, and the second part specifies the IP address or the domain name where the resource is located. For example, the two URLs below point to two different files at the domain pcwebopedia.com. The first specifies an executable file that should be fetched using the FTP protocol; the second specifies a Web page that should be fetched using the HTTP protocol: * * ftp://www.pcwebopedia.com/stuff.exe http://www.pcwebopedia.com/index.html USB Last modified: Wednesday, February 04, 2004 Short for Universal Serial Bus, an external bus standard that supports data transfer rates of 12 Mbps. A single USB port can be used to connect up to 127 peripheral devices, such as mice, modems, and keyboards. USB also supports Plug-and-Play installation and hot plugging. Starting in 1996, a few computer manufacturers started including USB support in their new machines. It wasn't until the release of the best-selling iMac in 1998 that USB became widespread. It is expected to completely replace serial and parallel ports. Also see USB 2.0. user session (1) The session of activity that a user with a unique IP address spends on a Web site during a specified period of time. The number of user sessions on a site is used in measuring the amount of traffic a Web site gets. The site administrator determines what the time frame of a user session will be (e.g., 30 minutes). If the visitor comes back to the site within that time period, it is still considered one user session because any number of visits within that 30 minutes will only count as one session. If the visitor returns to the site after the allotted time period has expired, say an hour from the initial visit, then it is counted as a separate user session. Contrast with unique visitor, hit, click-through and page view, which are all other ways that site administrators measure the amount of traffic a Web site gets. (2) The period of time a user interfaces with an application. The user session begins when the user accesses the application and ends when the user quits the application. vaporware Last modified: Tuesday, May 19, 1998 A sarcastic term used to designate software and hardware products that have been announced and advertised but are not yet available. vector graphics Last modified: Sunday, September 01, 1996 Same as object-oriented graphics, refers to software and hardware that use geometrical formulas to represent images. The other method for representing graphical images is through bit maps, in which the image is composed of a pattern of dots. This is sometimes called raster graphics. Programs that enable you to create and manipulate vector graphics are called draw programs, whereas programs that manipulated bitmapped images are called paint programs. Vector-oriented images are more flexible than bit maps because they can be resized and stretched. In addition, images stored as vectors look better on devices (monitors and printers) with higher resolution, whereas bit-mapped images always appear the same regardless of a device's resolution. Another advantage of vector graphics is that representations of images often require less memory than bit-mapped images do. Almost all sophisticated graphics systems, including CADD systems and animation software, use vector graphics. In addition, many printers (PostScript printers, for example) use vector graphics. Fonts represented as vectors are called vector fonts, scalable fonts, object-oriented fonts, and outline fonts. Note that most output devices, including dot-matrix printers, laser printers, and display monitors, are raster devices (plotters are the notable exception). This means that all objects, even vector objects, must be translated into bit maps before being output. The difference between vector graphics and raster graphics, therefore, is that vector graphics are not translated into bit maps until the last possible moment, after all sizes and resolutions have been specified. PostScript printers, for example, have a raster image processor (RIP) that performs the translation within the printer. In their vector form, therefore, graphics representations can potentially be output on any device, with any resolution, and at any size. W3C Last modified: Thursday, October 31, 2002 Short for World Wide Web Consortium, an international consortium of companies involved with the Internet and the Web. The W3C was founded in 1994 by Tim BernersLee, the original architect of the World Wide Web. The organization's purpose is to develop open standards so that the Web evolves in a single direction rather than being splintered among competing factions. WAN Last modified: Wednesday, March 26, 2003 Short for wide-area network. WAP Last modified: Friday, May 21, 2004 Short for the Wireless Application Protocol, a secure specification that allows users to access information instantly via handheld wireless devices such as mobile phones, pagers, two-way radios, smartphones and communicators. WAP supports most wireless networks. These include CDPD, CDMA, GSM, PDC, PHS, TDMA, FLEX, ReFLEX, iDEN, TETRA, DECT, DataTAC, and Mobitex. WAP is supported by all operating systems. Ones specifically engineered for handheld devices include PalmOS, EPOC, Windows CE, FLEXOS, OS/9, and JavaOS. WAPs that use displays and access the Internet run what are called microbrowsers-browsers with small file sizes that can accommodate the low memory constraints of handheld devices and the low-bandwidth constraints of a wireless-handheld network. Although WAP supports HTML and XML, the WML language (an XML application) is specifically devised for small screens and one-hand navigation without a keyboard. WML is scalable from two-line text displays up through graphic screens found on items such as smart phones and communicators. WAP also supports WMLScript. It is similar to JavaScript, but makes minimal demands on memory and CPU power because it does not contain many of the unnecessary functions found in other scripting languages. Because WAP is fairly new, it is not a formal standard yet. It is still an initiative that was started by Unwired Planet, Motorola, Nokia, and Ericsson. Wi-Fi Last modified: Friday, January 16, 2004 Short for wireless fidelity and is meant to be used generically when referring of any type of 802.11 network, whether 802.11b, 802.11a, dual-band, etc. The term is promulgated by the Wi-Fi Alliance. Any products tested and approved as "Wi-Fi Certified" (a registered trademark) by the Wi-Fi Alliance are certified as interoperable with each other, even if they are from different manufacturers. A user with a "Wi-Fi Certified" product can use any brand of access point with any other brand of client hardware that also is certified. Typically, however, any Wi-Fi product using the same radio frequency (for example, 2.4GHz for 802.11b or 11g, 5GHz for 802.11a) will work with any other, even if not "Wi-Fi Certified." Formerly, the term "Wi-Fi" was used only in place of the 2.4GHz 802.11b standard, in the same way that "Ethernet" is used in place of IEEE 802.3. The Alliance expanded the generic use of the term in an attempt to stop confusion about wireless LAN interoperability. Also see the Wireless LAN Standards chart in the Quick Reference section of Webopedia. wiki Last modified: Monday, May 19, 2003 (n.) A collaborative Web site comprised of the perpetual collective work of many authors. Similar to a blog in structure and logic, a wiki allows anyone to edit, delete or modify content that has been placed on the Web site using a browser interface, including the work of previous authors. In contrast, a blog, typically authored by an individual, does not allow visitors to change the original posted material, only add comments to the original content. The term wiki refers to either the Web site or the software used to create the site. Wiki wiki means “quick” in Hawaiian. The first wiki was created by Ward Cunnigham in 1995. worm Last modified: Thursday, April 22, 2004 (1) A program or algorithm that replicates itself over a computer network and usually performs malicious actions, such as using up the computer's resources and possibly shutting the system down. Also see virus. (2) When used in all capital letters, WORM is an acronym for for write once, read many, an optical disk technology that allows you to write data onto a disk just once. After that, the data is permanent and can be read any number of times. Unlike CD-ROMs, there is no single standard for WORM disks, which means that they can only be read by the same type of drive that wrote them. This has hampered their acceptance, although they have found a niche market as an archival media. WORM is also called CD-R. Also see Understanding CD Burner Speeds in the Did You Know . . . ? section of Webopedia World Wide Web Last modified: Friday, January 09, 2004 A system of Internet servers that support specially formatted documents. The documents are formatted in a markup language called HTML (HyperText Markup Language) that supports links to other documents, as well as graphics, audio, and video files. This means you can jump from one document to another simply by clicking on hot spots. Not all Internet servers are part of the World Wide Web. There are several applications called Web browsers that make it easy to access the World Wide Web; Two of the most popular being Netscape Navigator and Microsoft's Internet Explorer. World Wide Web is not synonymous with the Internet. Also see The Difference Between the Internet and the World Wide Web in the Did You Know . . . ? section of Webopedia. XML Last modified: Tuesday, May 18, 2004 Short for Extensible Markup Language, a specification developed by the W3C. XML is a pared-down version of SGML, designed especially for Web documents. It allows designers to create their own customized tags, enabling the definition, transmission, validation, and interpretation of data between applications and between organizations. XSL Last modified: Tuesday, January 21, 2003 Short for Extensible Style Language, a specification for separating style from content when creating HTML or XML pages. The specifications work much like templates, allowing designers to apply single style documents to multiple pages. XSL is the second style specification to be offered by the World Wide Web Consortium (W3C )(www.w3c.org). The first, called Cascading Style Sheets (CSS), is similar to XSL but does not include two major XSL's innovations -- allowing developers to dictate the way Web pages are printed, and specifications allowing one to transfer XML documents across different applications. W3C released the first draft of XSL in August 1998, and promotes the specifications as helpful to the Web's speed, accessibility, and maintenance. XSLT Last modified: Tuesday, January 21, 2003 Short for Extensible Style Language Transformation, the language used in XSL style sheets to transform XML documents into other XML documents. An XSL processor reads the XML document and follows the instructions in the XSL style sheet, then it outputs a new XML document or XML-document fragment. This is extremely useful in e-commerce, where the same data need to be converted into different representations of XML. Not all companies use the exact same programs, applications and computer systems. XSLT Recommendation was written and developed by the XSL Working Group and became ratified by the W3C on November 16, 1999.