SM468 Cryptography, codes, and information security Syllabus
advertisement
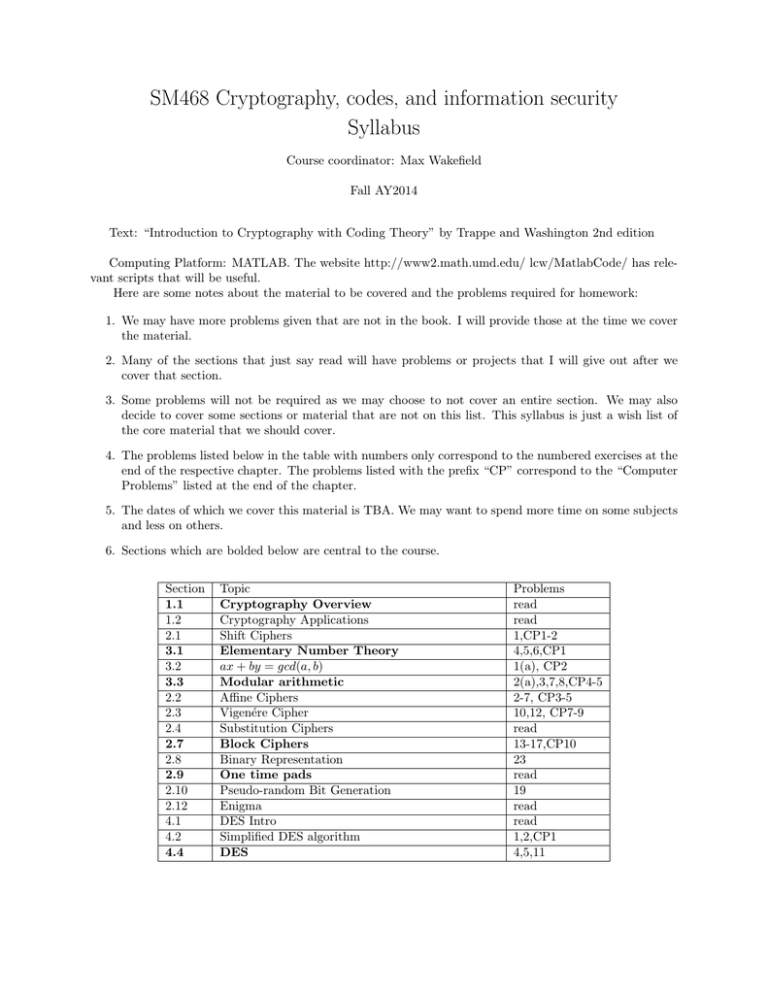
SM468 Cryptography, codes, and information security Syllabus Course coordinator: Max Wakefield Fall AY2014 Text: “Introduction to Cryptography with Coding Theory” by Trappe and Washington 2nd edition Computing Platform: MATLAB. The website http://www2.math.umd.edu/ lcw/MatlabCode/ has relevant scripts that will be useful. Here are some notes about the material to be covered and the problems required for homework: 1. We may have more problems given that are not in the book. I will provide those at the time we cover the material. 2. Many of the sections that just say read will have problems or projects that I will give out after we cover that section. 3. Some problems will not be required as we may choose to not cover an entire section. We may also decide to cover some sections or material that are not on this list. This syllabus is just a wish list of the core material that we should cover. 4. The problems listed below in the table with numbers only correspond to the numbered exercises at the end of the respective chapter. The problems listed with the prefix “CP” correspond to the “Computer Problems” listed at the end of the chapter. 5. The dates of which we cover this material is TBA. We may want to spend more time on some subjects and less on others. 6. Sections which are bolded below are central to the course. Section 1.1 1.2 2.1 3.1 3.2 3.3 2.2 2.3 2.4 2.7 2.8 2.9 2.10 2.12 4.1 4.2 4.4 Topic Cryptography Overview Cryptography Applications Shift Ciphers Elementary Number Theory ax + by = gcd(a, b) Modular arithmetic Affine Ciphers Vigenére Cipher Substitution Ciphers Block Ciphers Binary Representation One time pads Pseudo-random Bit Generation Enigma DES Intro Simplified DES algorithm DES Problems read read 1,CP1-2 4,5,6,CP1 1(a), CP2 2(a),3,7,8,CP4-5 2-7, CP3-5 10,12, CP7-9 read 13-17,CP10 23 read 19 read read 1,2,CP1 4,5,11 4.5 4.6 4.8 5.1 5.2 3.4 3.5 3.6 6.1 3.7 3.9 6.2 6.3 6.4 6.7 7.1 7.2 7.4 7.5 8.1 8.3 8.4 18.1 18.2 18.3 18.5 18.7 18.9 18.10 Operation modes Braking DES Password Security Intro to AES AES Chinese Remainder Theorem Modular Exponentiation Fermat’s little theorem and Euler’s theorem RSA Primitive Roots Square roots mod n Attacking RSA Primality Testing Factoring Public Key Systems Discrete Logs Discrete log computations Diffie-Hellman Key Exchange ElGamal Cryptosystem Hash functions A simple Hash function Birthday Attacks Intro to Coding theory Error correcting codes Linear codes Hamming codes Cyclic codes Reed-Solomon codes The McElienceMcElice Cryptosystem 3 read read read 1,2 9,10 11,13,14 15,16,20,39 1-5,10,CP1-3 21 25,26 read read 12-14,18, CP4-9 read read 1-6 10 11 1-3 read 4,CP1-2 1,2 read 3,4,9,10 read 12-14 read read