CRYPTOGRAPHY "Ayşe Tatile Çıksın" Is there any one to have you
advertisement

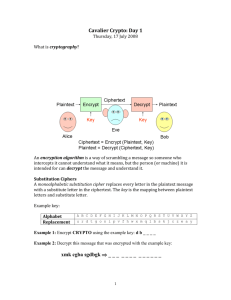
CRYPTOGRAPHY "Ayşe Tatile Çıksın" Is there any one to have you ever heard these words? İn 1974, The Turkish Foreign Minister Turan Güneş had said to the Prime Minister Bülent Ecevit, When I say "Ayşe is going on vacation" ("Ayşe Tatile Çıksın") it will mean that our armed forces are ready to go into action. And he said that was simple crypto and Turkish armed forces attack to Cyprus. After they won. We can see that crypto has very key point in our life. So what is the crypto? Lets look what is the crypto? Crypto is ancient art with this art people try to keep knowledge from 3rd person. Applications of cryptography include ATM cards, computer passwords, and electronic commerce. Who need Cryptography? Militaries Companies Universites Banks Encryption is the manipulation of data, based on a password (also known as a key), for security purposes. Once your data has been encrypted, a person can not make sense of your data without knowing the password (or figuring it out).To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it. For example, if we take HAL and add 1 to each of the letters, we get IBM (betcha didn't know that!). In this case, the password is simply "1". If we use "123456" as our password, then we add 1 to the first letter, 2 to the second, ..., 6 to the sixth, then we start over at 1 and add 1 to the seventh leGer.Now our encrypted data is, "ICN". To decrypt, the password "123456" is "subtracted" from our data. In cryptography, Caesar's code or Caesar shift, is one of the simplest and most known encryption techniques. The rule of cesar is each letter will encrypted from the previous letter but it is easy to solve the Ceaser rule. For example, with a left shift of 3, B would be replaced by Y, E would become B, and so on. A person looks up each letter of the message in the "plain" line and writes down the corresponding letter in the "cipher" line. They used it with a shift of three to protect messages of military significance. Now I will ask a question about this. Due to Ceaser chipper, what should be the basis form for the this word?-it means DENEME. Deneme means try in English. His nephew, Augustus, also used the cipher, but with a right shift of one, and it did not wrap around to the beginning of the alphabet. Whenever he wrote in cipher, he wrote B for A, C for B. Enigma is milestone to cryptography.. Enigma was invented by the German engineer Arthur Scherbius at the end of World War I.. in world war 2 Germany’s use the enigma for encryption and decryption.. it was used between 1928 1945 and it was 12 kilogram. Polish government was close the crack it but they did not. In 1942 Alan Turing cracked enigma with turingismus method. Because of this Turing is widely considered to be the father of computer science and artificial intelligence. In 1954 he committed suicide with poison apple. More complex ciphers use a secret key to control a long sequence of complicated substitutions (14) and transpositions (15). There are two general categories of cryptographic keys: Private key and public key systems. Private key systems use a single key. The single key is used both to encrypt and decrypt the information. Both sides of the transmission need a separate key and the key must be kept secret from. The security of the transmission will depend on how well the key is protected. The US Government developed the Data Encryption Standard ("DES"), which operates on this basis, and it is the actual US standard. DES keys are 56 bits (16) long. In the public key system there are two keys: a public and a private key. Each user has both keys and while the private key must be kept secret the public key is publicly known. Both keys are mathematically related. If A encrypts a message with his private key then B, the recipient of the message can decrypt it with public key. Similarly anyone who knows A's public key can send him a message by encryp'ng it with his public key. A will than decrypt it with his private key. Public key cryptography was developed in 1977 by Rivest, Shamir and Adleman ("RSA") in the US. Where do we use cryptography? Nowadays, we use cryptography in everywhere but the most important usage of place is ATM machines. HOW ?- You can use your password or hand to access your account. Our passwords are encrypted on our ATM cards or computers. And only we can access our accounts because we know what the secret codes . THEN. How we use hand? You can access with your fingerprint or palm. ıf you want to use this way, you must go to bank and you will define your fingerprint on your card. If you are using your hands to passwords, you don’t have to carry the card on your side. Without card you can access your account easily thanks to this way. No one except you cannot access your account with fingerprint. The study of a cryptographic system for the purpose of finding weaknesses in the system and breaking the code used to encrypt the data without knowing the code’s key. Governments use cryptanalysis in military and diplomatic surveillance, by enterprises in testing the strength of security procedures, and by malicious hackers in exploi'ng weaknesses in Web sites. To sum up the every single one that needs keeping some information with crypto. For example, especially banks need to crypto their customers’ information because hacker can access customers’ account easily. In the past we heard lots of news like this. So crypto is significant for banks especially for customers because they don’t want to lose their money. Thanks to crypto , banks can protect the account in secret. Veysel Olgac Muhammed Burak Şahin Muhammed Kılınç