Cryptography Applied to Linear Functions
advertisement

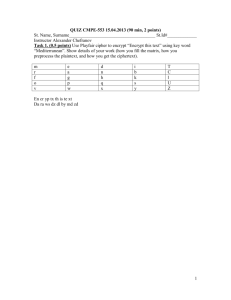
Cryptography Applied to Linear Functions Louena L. Manluctao East Early College High School Houston Independent School District Dr. Guofei Gu Assistant Professor College of Computer Science and Engineering Texas A & M University Roadmap • Introduction • • • • - Bridging Research to Lesson - STAAR/TEKS Objective The Classroom Project Samples of Pre-Test/Post-Test Acknowledgements Q&A Research Interest •Network and system security such as Internet malware detection, defense, and analysis • Intrusion detection, anomaly detection • Network security • Web and social networking security Relevance of the Research • http://www.youtube.com/watch?v=Mh1tf KyC-bY Sony Pictures hacked by Luiz Security, 1,000,000 passwords claimed stolen (update) http://consumerist.com/2011/06/how-hackers-stole-200000-citiaccounts-by-exploiting-basic-browser-vulnerability.html Bridging Research to Lesson in Algebra 1 Research Lab Cryptography Probability and Statistics Number Theory Abstract Algebra Programming Algebra 1 Linear Functions and Sequences STAAR/TEKS OBJECTIVES A1.3 & A1.4 (C) Linear Functions: (A) use symbols to represent unknowns and variables; and (B) look for patterns and represent eneralizations algebraically. (C) connect equation notation with function notation, such as y = x + 1 and f(x) = x + 1. STAAR/TEKS OBJECTIVE (7) Linear functions. The student formulates equations and inequalities based on linear functions, (A) analyze situations involving linear functions and formulate linear equations or inequalities to solve problems; THE CLASSROOM PROJECT : CRYPTOGRAPHY APPLIED TO LINEAR FUNCTION • Day 1: • Pre-Test • Hook • Power Point Presentation on Computer Network Security and Cryptography • Explain ( How to encrypt and decrypt) • Worksheets on finding the function key HOOK • Find the sum of 5 sets of 4-digit numbers without using the calculator. • I am texting this message, -4, -13, 2, -22, -1, -46, -46, -73 what do you think is it? • Do you think your computers are safe from cyber attack in your own homes? Power Point on Cryptography • What is cryptography? • Different Kinds of Cryptography • How to Encrypt and Decrypt Encrypt/Decrypt Finding The Key (Linear Equation) • The key will be the equation from a given sequence: • Consider: 3, 6, 9, 12, 15 5,9,13,17,21 9,7,5,3,1,-1 -3,3,9,15,21 Cont. • The common difference is the multiplier of n (the position of the term) • To find out what should be added or subtracted, find the zero term • We are now going to develop a formula • First let us define our variables: • T = the nth term z = the zero term • d= the common difference • n = position in the sequence Cont. Sequence Difference of terms Difference Multiplied by Position n The zero The term Equation (1st term-d) 3,6,9,12,15 3 3n 3-3=0 T = 3n+0 5,9,13,17,21 4 4n 5-4=1 T = 4n+1 9,7,5,3,1,-1 -2 -2n 9—2=11 T = -2n+11 -3,3,9,15,21 6 6n -3-6=-9 T = 6n - 9 The equation is T = dn + z or y = mx + b Write an equation to describe the following sequences 1. 9, 8, 7, 6, 5 2. 13, 17 , 21, 25, 29 3. 6, 11, 16, 21, 26 4. 112, 100, 88, 76 Day 2: • Review of Previous Lesson • Discussion of Finding the Inverse of the equation of the line. • Decoding Activity • Post-Test To Find the Inverse of an Equation • Exchange x and y • Solve for y in terms of x Ex. Y = 3x x = 3y x/3 = y Find the inverse of the following equations • 1. • 2. • 3. • 4. y y y y = = = = 3x + 5 -2x -4 4x – 6 3/4x + 2 The Decoding Activity • Students will be grouped by two’s • Each pair will be given a sequence where they will need to find the key. • Use the key to find the encrypted code • Decipher using inverse equation. • Use : Space = 0 ; A = 1; B=2; C=3…Z=26 • Give the message. What is the text message? -4, -13, 2, -22, -1, -46, -46, -73 • Key: -1, -4, -7, -10, . . . • What is the encrypted key? y = -3x+2 • What is the decrypted key? Y = -(x-2)/3 • What is the deciphered message? 2, 5 , 0, 8, 1, 16, 16, 25 Plaintext message is: BE HAPPY Decoding Activity: What is the message? • -21 3 -35 -11 5 -13 -33 5 - 37 -33 -5 -7 -37 -15 • 5 3 -23 -3 5 -7 -37 -23 KEY: 3, 1, -1, -3, … • What is the encrypted key? ( y = mx+b) • • • • ___________________ What is the decrypted key? ________ What is the deciphered message?__________ Remember : Space = 0 A = 1 B =2 C =3… Z = 26 Plaintext Message: _________________________________ Assessment: Pre-Test/Post Test Sample Questions 1. The nth term of a sequence is defined to be 3n +7. The 35th term is how much less than the 39th term? A)4 B) 12 C) 19 D) 33 2. Given the sequence -5, -2, 1, 4 … which equation best represents the sequence? A) y =3x-5 C) y = 3x-8 B) y = -3x-5 D) y = -3x-8 Acknowledgements Dr. Robin Autenrieth, Dr. Cheryl Page, Dr. Arun Srinivasa Matthew Pariyothorn, Ashwin Rao, Roberto Dimaliwat, Stephen Hudson Dr. Guofei Gu, Chao Yang, Jialong Zhang , Wilber Rivas Question and Answer Thanks to Chao Yang’s Presentation