WA1 - Andrew.cmu.edu
advertisement

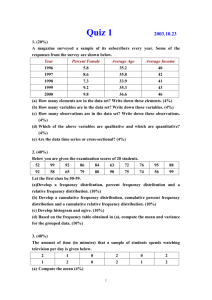
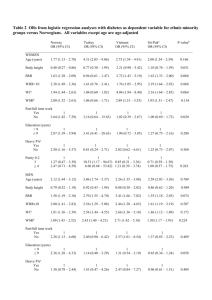
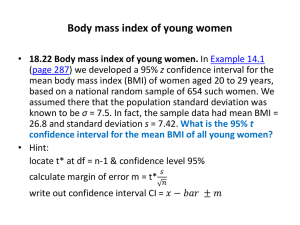
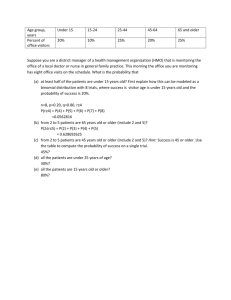
15110 Summer II 2012 [adapted from Cortina/von Ronne] Written Assignment 1 – due Monday, July 9 at 9 am sharp. Reading assignment Read sections 1.1-1.2 of chapter 1 and sections 2.1-2.4 in chapter 2 of the textbook Explorations in Computing and chapter 1 and pages 19-42 of chapter 2 of the book Blown To Bits. Instructions Type or neatly write the answers to the following problems. Please STAPLE your homework before you hand it in. On the first page of your homework, include your name, andrew ID, date, and the assignment number. Number your pages. You must hand in your homework at the start of class on the given due date. Exercises 1. Babbage's Difference Engine utilized the method of finite differences to compute the values of a polynomial function. Babbage computes the values of the function and all of its difference functions for x=0, and these values are given below. What does the machine compute for f(1), f(2), f(3) and f(4) when the machine is cranked? (Show all your work.) f(0) = 7 Δf(0) = 6 Δ2f(0) = 3 Δ3f(0) = 2 2. Charles Babbage wants to compute all of the function values for the polynomial f(x) = 3x2 + 6x + 7 for x = 1 to 1000. Using the method of finite differences, what initial values does he set his machine to if he wants it to start at x = 0? (HINT: You'll need to compute the difference (delta) functions first.) 3. What was the purpose of each of the following computational machines? Why was each machine desperately needed? a. Herman Hollerith's tabulating machine b. ENIAC 4. a. An electronic device has 128GB of memory. It is connected to a communication port that receives data at a rate of 256Mbps. How long will it take to fill up the memory of this device if it starts off as empty? b. Moore's Law states that the processing power of a computer doubles approximately every 2 years. Based on this observation, how many years will it take to have a computer that is approximately a thousand times more powerful than today's computer? 5. For each of the following Ruby expressions, show how they are evaluated by evaluating one operation at a time and showing the reduced expression until you have a final answer. For example, if the Ruby expression is 3 * 4 + 5, you answer would look like this: 3 * 4 + 5 12 + 5 17 HINT: Check your final answers with irb!!! a. b. c. d. (11 - 9 + 10) / (4 + 1 ** 2) 2 ** 2 ** 2 ** 2 15100 % 2000 % 300 % 45 % 25 18 * 4+5 / 5-2 6. For each of the following invalid Ruby expressions, run them in irb and explain the errors that you see. a. b. c. d. Math.sqrt(-100) 11 % 0 end = "Friday" "15000" + 110 7. Consider the following Ruby method that returns the body mass index (BMI) of an individual given the person's height in inches and weight in pounds. def compute_bmi(height, weight) return weight * 703 / height ** 2 end a. Suppose Alice has a height of 63 inches and a weight of 132 pounds. If we call this function to compute her BMI as follows: compute_bmi(63, 132) will we get an integer result or a floating point result? Why? b. Suppose Bob has a height of 72 inches and a weight of 180 pounds, but we call this function with these values mixed up: compute_bmi(180, 72) Does Ruby report an error? Why or why not? c. Suppose we only know that Carol's height is 65 inches, and we try to compute her BMI as follows: compute_bmi(65) Does a default weight get used in our function or does Ruby complain about this function call? Explain. d. Suppose we replace the return statement with a print statement as shown below: def compute_bmi(height, weight) print weight * 703 / height ** 2 end e. Why does the following computation fail? average_bmi=(compute_bmi(63,132)+compute_bmi(72,180)+compute_bmi(65,147))/3.0 NOTE: Don't just say how to fix the function. Explain why the computation fails based on the current function definition. 8. Consider the following Ruby method definition that uses a loop: def mystery(n) value = 1 for i in 1..n do value = value * i print value print "\n" # print a newline character end end a. What does this method display if we call it as follows: mystery(6) b. What mathematical function is this Ruby method computing in general if n > 0? c. Suppose we replace the first instruction inside the loop with the following: value = value * 2 d. Now what mathematical function is this Ruby method computing if n > 0? e. Using irb, see what happens in the original function if we replace the print statements with a return statement instead: def mystery(n) value = 1 for i in 1..n do value = value * i return value end end Store the function in a file, then load it in irb and call it with different positive integers and observe the results. What do your observations suggest about how the return statement works? 9. Based on your reading of Chapter 1 of Blown To Bits, answer the following questions. a. A common theme in computing is dealing with advances in technology that change exponentially. Exponential changes are often hard to see at first but become very obvious once it's too late to adapt. Give an example from this chapter of a company that didn't see exponential changes in its core business, resulting in massive layoffs and a major loss in revenue. b. Eliot Spitzer, former governor of New York, was forced to resign due to a prostitution scandal. How was his involvement detected digitally? c. Years ago, people copied songs on to cassette tapes and shared them with their friends, yet the recording industry didn't pursue these people for copyright infringement. Today, however, sending a friend a copyrighted mp3 file can get you into trouble. Why is the response different now? d. Once digital data about you is stored, can it be completely erased? Why or why not? 10. Besides learning how to use computational devices to solve a problem, we should understand what happens once the device solves the problem for us. Based on your reading of Chapter 2 (pages 19-42) of Blown To Bits, answer the following questions about the digital data you generate and how all of this digital data affects your privacy. a. Give two examples of how you might leave "digital footprints" while driving your vehicle, based on what you read in the chapter. (Write 2-3 sentences for each example you cite.) b. Briefly describe one example from the reading where a person's confidential medical records were discovered by linking the anonymized records with another data set. c. Identify one example of how stores might digitally track your purchases so they can suggest new items for you to purchase, based on what you read in the chapter. (Write 2-3 sentences to explain how the tracking is done.)