Introduction to Computers
advertisement

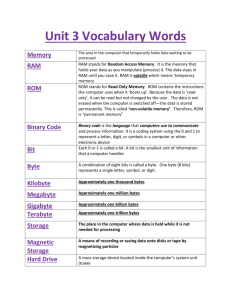
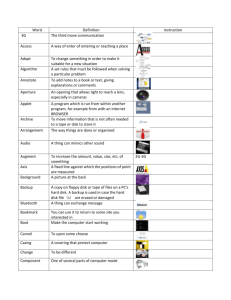
Introduction to Computers & Technology Terminology A computer is a device that accepts information and instructions from the user, processes the data in a way in which the user designates, and displays the information in a form stipulated by the user. It is an electronic device using electronic signals to manipulate the data. There are many different types of computers on the market today. They include but by no means limited to: Personal Digital Computers, Desktop Computers, laptops or notebook computers, handheld computers, cell phones, mainframe computers, and supercomputer. A computer system includes all the computer’s hardware and software. Hardware is anything that is tangible or the physical components of a computer. It is any part of the system that you can actually touch. Software is the intangible component such as programs. Programs are lists of instructions that instruct the hardware to perform certain tasks. Hardware works with software to process data. Data can be words, numbers, figures, sounds, and graphics. Data is processed according to instructions (software). System software manages the operations of the computer such as loading programs, executing programs, displaying information, etc. It essentially consists of the operating system with additional utilities, drivers, and program languages. System software is located either in the root directory (C:\) or the windows directory on Drive C. The user should not change or rename any system folder. If these files and/or folders are changed, the computer may not function properly. Application software consists of lists of instructions that tell the hardware what to do. Application software includes programs such as Microsoft Word, Microsoft Excel, Microsoft PowerPoint, MicroType, etc. APPLICATION software helps the USER perform specific tasks; whereas the SYSTEM software helps the COMPUTER perform specific tasks. APPLICATION/USER SYSTEM/COMPUTER An input device allows the user to insert or input data into the computer for processing. The most common input device is the keyboard. Other input devices include the mouse and scanner. Input devices enter data as well as issue commands to the computer. Output devices display or print on to hard copy what is inputted a computer. The two main output devices are the monitor and the printer. The main permanent storage on any computer system is the hard drive. The hard drive is a compact disk found on the inside of computer. The computer system sets aside an area for storage of your personal documents. This is called the My Documents Folder. Another permanent storage device is a flash drive. This is a portable external storage device that plugs into your computer. The flash drive is more durable and holds more memory and is faster than a floppy disk. The floppy disk was used for many years as an external permanent storage device. However, it was unreliable and not very durable. The flash drive that was sold by IBM in 1998 took the place of the floppy disk. The newer computers don’t have floppy drives making the floppy disk outdated. Other storage devices include: · CD-R which is compact disc recordable; · CD-RW which is compact disc rewritable; · CD-ROMS which is compact disc read-only memory. · DVD which is digital versatile disc DVD-R, recordable · DVD-RW rewritable · DVD-ROMS. Read only memory CD-ROM means you can read only and can’t modify the data such music CDs and software programs that are on CDs. RAM memory is Random Access Memory. It temporarily stores data. When the computer is turned off, the data is gone. RAM is a form of data storage. Random refers to the fact that data can be accessed in any order or random order regardless of where it is located. The user should always save his/her data before turning off the computer. Adding more RAM can help your computer run faster. ROM is Read Only Memory. ROM is non-volatile or permanent memory. ROM stays constant whether the computer is on or off. ROM contains instructions for the computer to check the components to make sure they are working properly and to activate the system software. The computer doesn’t recognize letters of the alphabet or numbers in the way humans do. Computers are electronic devices, and they recognize switches that are either on or off much like the light switch. If the switch is on, it is represented as a “1”. If the switch is off, it is represented by a “0”. These numbers are referred to as binary digits or bits. A series of 8 bits is called a byte. A byte represents one keystroke. A byte is abbreviated as “B,” and a bit is abbreviated as “b.” If you see 10MB (10 megabytes, it means 10 million bytes; 10GB (gigabytes) means 10 billion bytes; 10KB (Kilobytes) means 10 thousand bytes; and TB or terabyte means approximately one trillion bytes. KB, MB, GB, and TB refer file sizes, storage capacity, and processing capacity. A CD can store up to 700 MB; a DVD can store between 4.7 GB and 15.9 GB. A DVD with a storage capacity of 4.7 GB can hold nine hours of video. A printer is a device that can print data on paper. Laser printers are the most popular because of their high-quality output. The speed of the laser printer is dependent upon how many pages per minute it can produce. Dot matrix printers transfer ink to the paper by striking a ribbon with pins. The speed of the dot matrix printer is measured in characters per inch or cps. A network connects one computer to another. Any computer on a network must have a Network Interface Card or NIC. The NIC allows interaction and/or communication between the computer and the network. A NIC is connected to the network via a cable. A server is a computer that is the central storage location for programs and user data. When a client is combined with a server, you have a client/server network. The clients are the individual computers and the server provides shared software and storage for these computers. You can network computers in order to play games, but this isn’t a client/server environment. This is just a client/client network where each client is equal. The internet is a worldwide collection of networks that allow people to communicate and share information. WWW stands for the World Wide Web or just web. The web is a service the internet offers that enables users to communicate with each other. It is a system of web servers with web pages. Web pages are specially formatted documents created in programming languages such as HTML or SML or ASP. These are programming languages for writing and creating web pages. HTML stands for hypertext markup language; XML means Extensive Markup Language and ASP means Active Server Pages. If you are on a web page, click on the main menu VIEW go down and click on SOURCE, you will see the programming language the web page was written in. A web server stores web sites; the web server (computer) manages and displays pages on a web site. A web site is a collection of web pages that have the same theme. These web sites are stored on web servers belonging to individuals, companies, and/or organizations. Hyperlinks connect one web page to another web page. These web pages usually have the same theme. The hyperlink can be a word, phrase or icon and are usually underlined or have a different color. An ISP is an Internet Service Provider. An ISP is a company that sells internet access. Examples of ISP are Bellsouth, Insight, AOL, PeoplePC, etc. A web browser is software used to access, retrieve, and interact with web pages. It allows different operating systems to communicate over the internet. Examples of web browsers are Internet Explorer, Safari, and FireFox. You must have a browser in order to access the web. The URL or Uniform Resource Locator is the address of a web site you want to retrieve. For an example: http://www.kytech.ky.gov/ http://www.uky.edu/ http://louisville.edu/ https:// The “s” indicates the site is a secure site. The http stands for hypertext transfer protocol; www stands for World Wide Web; kytech.ky.gov is the domain name where the server is located. The Internet Protocol address is the address of the computer. It is like your home address. Every computer has an address which is a set of 4 numbers separated by a period. For example: 123.143.23.14. No number can be above 254. All computers and servers have IP addresses. Instead of keying in the IP address, users can key in domain/computer names. Users remember names better than numbers. All computers users need to take the appropriate steps to keep unauthorized persons from gaining access to their computer in order to do harm. Malware (malicious software) is software created in order to bring harm or convey information taken from your computer to use in a harmful way. Virusprotection software searches out malware and erases or disables the malware commands that would do harm. Spyware programs are designed to keep track of a user’s internet usage and send the information back over the internet to the company or person who created it. This is usually done without the permission of the owner. Some spyware programs now can interfere with the computer such as changing computer settings and interfering with software applications. A spoofed site is a site that looks exactly like an authentic site. An example of a spoofed web page is one that looks exactly like your bank’s web page. The spoofed site is created in order to get your personal banking information. A user doesn’t realize it isn’t the authentic site; therefore may give personal information. The spoofed web site can even have the “s” in the URL indicating it is a secure site. Viruses are programs that can copy themselves and infect a computer without the knowledge of the user. They are designed to spread through attachments and emails. Viruses don’t infect compressed files or write-protected files. The sole purpose for the creation of a virus is to do harm to your computer system. A worm can spread from computer to computer without any action on the part of the user. Once it is on your computer, it replicates itself thousands of times. It can copy itself to everyone in your address book. The biggest threat of the worm is taking up space on your computer, a network, or the internet. It can slow down a system quickly. A Trojan Horse can be more annoying than malicious like changing the icons on the desktop, but can delete and destroy files. Trojans will make itself look like a legitimate system file.