Risk Assessment-Security Plan
advertisement

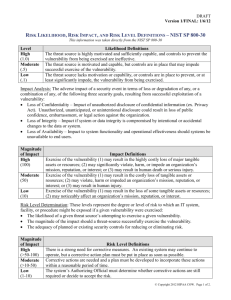
BAA 607 MIS MBA Risk Assessment Terminology Threat: Something that can occur and cause damage to a valuable asset. Vulnerability: An exposure in the system that can lead to a threat becoming realized. Vulnerability level: The probability of the treat occurring. Risk: Cost that occurs when a threat successfully exploits a vulnerability. Risk Assessment: The process of identifying an organization’s assets and determining to what extent each asset is vulnerable. The vulnerability level of the asset to each threat is approximated. The threat associated with each asset is identified and the risk (expected annual loss) associated with the threat is approximated. The Risk Assessment is then used to determine what resources should be allocated to protect specific assets from the specified risk. Not all threats can be anticipated, but most businesses can identify some of the threats they may face. Not all vulnerabilities can be identified, but businesses can anticipate some of these. Risk Assessment for information systems is very important. Business managers working with information system specialists can try to determine the points of vulnerability and the vulnerability level of an asset. For our case study, we will use the three levels of likelihood: High, Medium and Low. These levels will replace actual probabilities of occurrence. If the vulnerability level is High, we will use a probability = 1 (sure to occur). If the vulnerability level is Medium, we will use a probability level = .5 (occurs 50% of the time). If the vulnerability level is Low, we will use a probability level = .1 (occurs 10% of the time). As an example of how the Risk Assessment is used, if a threat has a vulnerability level that is low (likely to occur no more than once a year) with a risk of a $1,000 loss to the organization for each occurrence, then it would not be wise to spend $20,000 to protect against that threat. However, if that same threat could occur at least once a day, then the potential annual risk is more than $300,000 a year. In this case, spending $100,000 to control this threat might be entirely appropriate. Consider an on-line process system that processes 30,000 orders per day. The table below illustrates the results of a Risk Assessment done on this system. The likelihood of each threat occurring over a one-year period is expressed as: High, Medium, or Low. The next column shows the amount of loss that might occur each time the exposure occurs. The expected annual loss is then determined by multiplying the Loss per event by the Likelihood of occurrence. Risk Assessment for an Order Processing Information System Threat Vulnerability Level Risk per Occurrance Power Failure Embezzlement User Error Medium = .5 Low = .1 High = 1 $100,000 $25,000 $20,000 Expected Annual Risk $50,000 $2,500 $20,000 In the case above, there should be some controls built in to minimize the risk of power failure and user errors because the Expected Annual Risk is high for these areas. Your job is to perform a Risk Assessment for our Smith Volunteer Clinic. You may consider all assets of the clinic, but concentrate in particular on the Information System assets. A Risk Assessment should be conducted on each information system that is part of the organization. After the Risk Analysis is performed, you may use the results to establish additional Security Policies for the clinic. As an example of a security policy, suppose that through the Risk Assessment process, you discover a high risk of unauthorized access to the computers using the EMR software. You may then want to establish some security policies to prevent this occurrence: 1) A unique account and password combination must be used to authenticate all users of the information system. The account name must be used only by a single individual and the password must be a secret know only to that individual. 2) When an account is no longer needed, it must be disabled. 3) Requests for changes in access permissions must be approved by a manager. 4) Passwords must expire after a certain period (three months) This is a group project. Time outside of class will need to be devoted to this project. Note that a Risk Assessment and Security Plan for an information systems is conducted after the information system has been designed and implemented. You may assume that this has occurred for the Smith Volunteer Clinic. Use the information systems that you identified in your systems analysis process. You should now know exactly what information systems the Smith Volunteer Clinic will use. Be sure to consider the four areas of security that we discussed in Meeting #4: Physical Security, Data Security, Network Security, and Computer Security. Name your file: Risk Assessment-Security Plan.Group#. Place this file in your Group folder under Homework#5.