slides - SAC 2013
advertisement

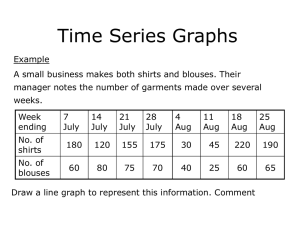
Towards Practical Lattice-Based Public-Key Encryption on Reconfigurable Hardware SAC 2013, Burnaby, Canada Thomas Pöppelmann and Tim Güneysu Horst Görtz Institute for IT-Security, Ruhr-University Bochum, Germany 14. Aug. 2013 Agenda • • • • • Introduction Ring-LWE Encryption Lattice Processor Results Conclusion 14. Aug. 2013 2 Motivation • Advantages of lattices: – Post-quantum security – Security proofs – Versatility • Goal of this work: – Provide a simple and reusable hardware building block • Starting point to solve more advanced implementation problems • Make source code available – Deal with aspects important in practice • Ciphertext expansion • Error rate 14. Aug. 2013 3 Agenda • • • • • Introduction Ring-LWE Encryption Lattice Processor Results Conclusion 14. Aug. 2013 4 Recap: Ideal Lattices • Ideal lattices correspond to ideals in the ring R = 𝑍𝑞 𝑥 / 𝑥 𝑛 + 1 with 𝑛 being a power of two and 𝑞 being a prime such that 𝑞 = 1 mod 2𝑛 (*) – Introduces algebraic structure into previously random lattices – no serious advantage for attackers so far – Most standard lattice problems have an ideal lattice counterpart • Polynomial multiplication is the basic operation – Runtime 𝛰(𝑛 log(𝑛)) when using the number theoretic transform (NTT) – 𝑎 ∗ 𝑏 = INTT NTT 𝑎 ∘ NTT 𝑏 with 𝑎, 𝑏 ∈ 𝑅 • Ring-LWE problem requires to distinguish whether samples 𝑎1 , 𝑡1 , … 𝑎𝑚 , 𝑡𝑚 are 𝑡𝑖 = 𝑎𝑠𝑖 + 𝑒𝑖 with 𝑎, 𝑠𝑖 ∈ 𝑅, 𝑒𝑖 ← 𝐷𝜎 or uniformly random – Decisional problem as hard as search – 𝐷𝜎 is a small discrete Gaussian distribution (*) Other choices are also possible but this one has emerged as standard for security and efficiency. 14. Aug. 2013 5 LWE-Encryption Gen: Choose 𝑎 ← 𝑅 and 𝑟1 , 𝑟2 ← 𝐷𝜎 . Compute 𝑝 = 𝑟1 − 𝑎 ⋅ 𝑟2 ∈ R 𝑛 ): 𝑒 , 𝑒 , 𝑒 1 2 3 Enc(𝑎, 𝑝, 𝑚 ∈ 0,1 ← 𝐷𝜎 . 𝑚 = 𝑒𝑛𝑐𝑜𝑑𝑒 𝑚 . Ciphertext: [𝑐1 = 𝑎 ⋅ 𝑒1 +𝑒2 , 𝑐2 = 𝑝 ⋅ 𝑒1 +𝑒3 + 𝑚] 𝑎 x + 𝐷𝜎 𝐷𝜎 𝑝 x 𝑚 Dec(𝑐 = [𝑐1 , 𝑐2 ], 𝑟2 ): Output 𝑑𝑒𝑐𝑜𝑑𝑒(𝑐1 ⋅ 𝑟2 +𝑐2 ) 𝑐1 𝑐1 𝐷𝜎 + + 𝑐2 𝑒𝑛𝑐𝑜𝑑𝑒 x + 𝑟1 𝑐2 𝑑𝑒𝑐𝑜𝑑𝑒 𝑚 [LP11] Richard Lindner, Chris Peikert: Better Key Sizes (and Attacks) for LWE-Based Encryption. CT-RSA 2011 14. Aug. 2013 6 LWE-Encryption • Parameters: 128-bit CPA security (𝑛=256,𝑞=7681,𝑠=11.32) – Approx. 1600 bit secret key – 3328 bit public key – Message expansion factor 26 • Encoding/Decoding: Small noise 𝑒1 𝑟1 + 𝑒2 𝑟2 + 𝑒3 still present after decryption – One message bit is encoded into one coefficient of the polynomial 𝑚 (0 ⇒ 0, 1 ⇒ q/2) – May fail with low probability • Optimization – Use different encoding – Remove some LSBs of ciphertext coefficients 14. Aug. 2013 7 Agenda • • • • • Introduction Ring-LWE Encryption Lattice Processor Results Conclusion 14. Aug. 2013 8 Reconfigurable Hardware (FPGA) • Field Programmable Gate Array (FPGA) – A chip containing programmable logic blocks – Logic blocks are connected by a configurable interconnect – Limited number of dedicated „hard-cores“ like block memory or embedded multipliers (DSPs) are available • Hardware is inherently parallel – Time vs. area 14. Aug. 2013 9 The Challenge • Ring-LWE encryption and also other schemes (e.g., signature schemes) basically just require polynomial arithmetic – So far results are only available for polynomial multiplication – Temporary values have to be stored – Operations for addition and subtraction are necessary – An easy interface is required Solution: Build a lattice processor/micro-code engine 14. Aug. 2013 10 Lattice Processor • Supports any power of two 𝑛 > 64 and prime 𝑞 satisfying 1 = 𝑞 mod 2𝑛 • Configurable amount of registers (register = polynomial) • Discrete Gaussian sampler using the inverse transform method • Instruction set (simplified): – – – – – – 𝑛 NTT: Perform NTT on register ( log(𝑛) cycles) 2 PW_MUL: Point-wise multiplication of two polynomials (𝑛 cycles) 𝑛 INTT: Perform inverse NTT on register ( log(𝑛) cycles) 2 ADD: Add two polynomials (𝑛 cycles) SUB: Subtract two polynomials (𝑛 cycles) MOV: Transfer polynomial or obtain polynomial from the sampler 14. Aug. 2013 11 Lattice Processor 14. Aug. 2013 12 Optimizing Encryption Key Generation 1. 𝑟1 , 𝑟2 ← 𝐷𝜎 . Compute 𝑝 = 𝑟1 − 𝑎 ⋅ 𝑟2 ∈ R 2. 𝑎= NTT (𝑎), 𝑝= NTT (𝑝), Encryption 1. 𝑒1 , 𝑒2 , 𝑒3 ← 𝐷𝜎 2. 3. 4. 5. 𝑒1 = NTT ( 𝑒1 ) ℎ1 = 𝑎 ∘ 𝑒1 ℎ2 = 𝑝 ∘ 𝑒1 6. 𝑐2 = INTT ℎ2 + 𝑒3 + 𝑒𝑛𝑐𝑜𝑑𝑒(𝑚) 𝑐1 = INTT ℎ1 + 𝑒2 Note: Straightforward version would require at least two multiplications: 3𝑛 log 𝑛 +6n 14. Aug. 2013 3𝑛 1 𝑛 2 log(n) + 2𝑛 𝑛 𝑛 1 𝑛 log(𝑛) + 2𝑛 2 1 𝑛 log 𝑛 + 3𝑛 2 3 = 𝑛 log 𝑛 + 12𝑛 2 13 Agenda • • • • • Introduction Ring-LWE Encryption Lattice Processor Results Conclusion 14. Aug. 2013 14 Results • Implemented encryption scheme on Spartan-6 and Virtex-6 for medium security (n=256,q=7681) and high security (n=512, q=12289) • Core supports encryption, decryption and key generation • Gaussian sampler is bounded with relatively low precision 14. Aug. 2013 15 Performance and Resources Post-place-and-route performance on a Virtex-6 LX75T FPGA. 14. Aug. 2013 16 Comparison with Previous Work • Compared to previous implementation by Göttert et al. from CHES 2012 – Three times slower – Up to 60 times lower area • While speed is important the design has to fit onto a reasonably sized FPGAs – Hardware allows parallel placement to make up for lower speed • Higher flexibility with one general purpose core (Gen/Enc/Dec) [Göttert et al.] Norman Göttert, Thomas Feller, Michael Schneider, Johannes Buchmann, Sorin A. Huss: On the Design of Hardware Building Blocks for Modern Lattice-Based Encryption Schemes. CHES 2012 14. Aug. 2013 17 Comparison with Other Schemes 14. Aug. 2013 18 Agenda • • • • • Introduction Ring-LWE Encryption Lattice Processor Results Conclusion 14. Aug. 2013 19 Future Work and Conclusion Conclusion • Flexible building block for a large number of applications in ideal lattice-based cryptography • Source code (VHDL) of the encryption scheme/lattice processor available for evaluation at http://www.sha.rub.de/research/projects/lattice/ Future Work • Side-channel evaluation • Bimodal Lattice Signature Scheme (BLISS), Crypto 2013 • Performance and resource optimization • Implementation and acceleration of high-level constructions like homomorphic encryption or IBE 14. Aug. 2013 20 Towards Practical Lattice-Based Public-Key Encryption on Reconfigurable Hardware SAC 2013, Burnaby, Canada Thomas Pöppelmann and Tim Güneysu Horst Görtz Institute for IT-Security, Ruhr-University Bochum, Germany 14. Aug. 2013 Thank You for Your Attention! Any Questions?