RISK MANAGEMENT
advertisement
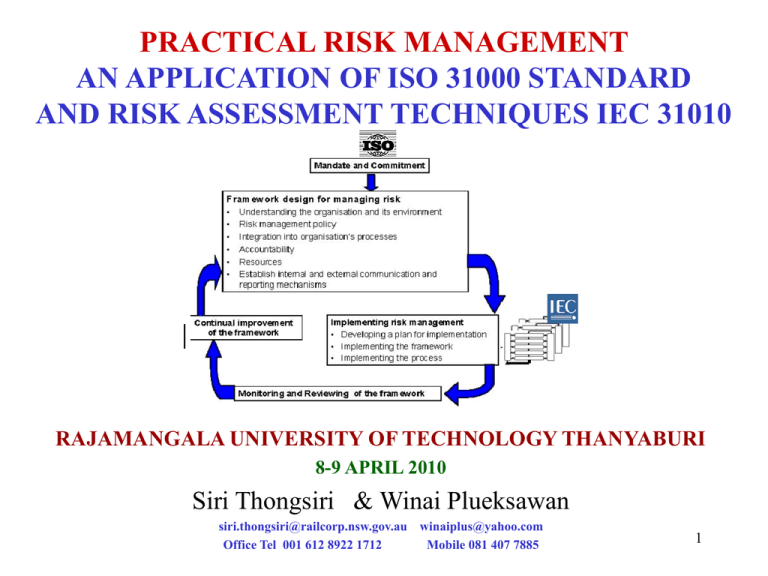
PRACTICAL RISK MANAGEMENT AN APPLICATION OF ISO 31000 STANDARD AND RISK ASSESSMENT TECHNIQUES IEC 31010 RAJAMANGALA UNIVERSITY OF TECHNOLOGY THANYABURI 8-9 APRIL 2010 Siri Thongsiri & Winai Plueksawan siri.thongsiri@railcorp.nsw.gov.au winaiplus@yahoo.com Office Tel 001 612 8922 1712 Mobile 081 407 7885 1 SESSION OBJECTIVES วัตถุประสงค์ ของการสั มมนา • Understand the Principles and Application of Modern Risk Management & Internal Control • Understand the Principles of Enterprise Risk Management and its Application • Able to Apply International Risk Management Standard ISO 31000 at both Strategic and Operational Levels • Gain Hand-on Experience in the Application of ISO/IEC 31010 Risk Management Risk Assessment Techniques 2 COURSE CONTENTS 1. The ISO 31000 Risk Management 2. Risk and Risk Management 3. Risk Management Process 4. Enterprise Risk Management 5. Internal Control 6. Risk Identification Tools 7. The Thongsiri Risk Identification Methodology (TRIM) 8. Risk and Analysis Techniques IEC 31010 9. Risk Analysis and Decisions 3 1. THE ISO 31000:2009 RISK MANAGEMENT มาตรฐานการบริหารความเสี่ ยงของ ISO 4 Contents of ISO Documents RISK MANAGEMENT INTERNATIONAL STANDARD ISO 31000:2009 ISO Guide 73 Risk Management Vocabulary ISO 31000 Risk Management – Principles and guidelines IEC 31010 Risk Management Risk Assessment Techniques 5 ISO 31000:2009 - SCOPE To provide principles and generic guidelines on risk management It can be used by any public, private or community enterprise, association, group or individual It can be applied throughout the life of an organisation, and to a wide range of activities, including strategies and decisions, operations, processes, functions, projects, products, services and assets It can be applied to any type of risk, whatever its nature, whether having positive or negative consequences It is not intended to promote uniformity of risk management across organisations To harmonize risk management processes in existing and future standards ISO 31000 is not intended for the purpose of certification 6 ISO 31000:2009 - USERS ISO 31000:2009 is intended to meet the needs of a wide range of stakeholders including: those responsible for developing risk management policy within their organisation; those accountable for ensuring that risk is effectively managed within the organisation as a whole or within a specific area, project or activity; those who need to evaluate an organisation effectiveness in managing risk; and developers of standards, guides, procedures, and codes of practice that, in whole or in part, set out how risk is to be managed within the specific context of these documents. 7 a) Creates value b) Integral part of organizational processes c) Part of decision making d) Explicitly addresses uncertainty e) Systematic, structured and timely f) Based on the best available information g) Tailored h) Takes human and cultural factors into account i) Transparent and inclusive j) Dynamic, iterative and responsive to change k) Facilitates continual improvement and enhancement of the organization Mandate and Commitment (4.2) Design of framework (4.3) Continual improvement of the Framework (4.6) Implementing risk Management (4.4) Monitoring and review of the Framework (4.5) C o m u n i c a t i o n & c o n s u l t a t i o n Establishing the context (5.3) Risk assessment (5.4) Risk identification (5.4.2) Risk analysis (5.4.3) & Risk evaluation (5.4.4) r e v i e w (5.6) Risk treatment (5.5) 5.2 Principles (Clause 3) Framework (Clause 4) M o n i t o r i n g Process (Clause 5) 8 ISO 31000:2009 Relationship between the Principles, Framework and Process Principles (Clause 3) Risk management should…. 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. Create value An integral part of organisational processes Part of decision making Explicitly address uncertainty Be systematic and structured Be based on the best available information Be tailored Take into account human factors Be transparent and inclusive Be dynamic, iterative and responsive to change Be capable of continual improvement and enhancement 9 Mandate and commitment (4.2) 4.3 Design of framework 5.3.1 Understanding the organization and its context 5.3.2 Risk management policy 5.3.3 Integration into organizational processes 5.3.4 Accountability 5.3.5 Resources 5.3.6 Establishing internal communication and reporting mechanisms 5.3.7 Establishing external communication and reporting mechanisms 4.6 Continual improvement of the framework 4.4 Implementing risk management 4.4.1 Implementing the framework 4.4.2 Implementing the risk management process 4.5 Monitoring and review of the framework ISO 31000 Relationship between the components of the framework for managing risk 10 ISO 31000: MANDATE AND COMMITMENT Articulate and endorse the risk management policy แสดงจุดยืนที่ชัดเจนและรับรอง นโยบายการบริหารความเสี่ยง Ensure that the necessary resources are allocated to risk management ดาเนินการจัดหาทรัพยากรที่จาเป็ น สาหรับการบริหารความเสี่ยง The Management Should ผู้บริหารจะต้ อง Ensure legal and regulatory compliance ดาเนินการบริหารความเสี่ยงให้ ถูกต้ องตามระเบียบและกฎหมาย Ensure alignment of risk management objectives with the objectives and strategies of the organization ดาเนินการให้ วตั ถุประสงค์ของการ บริหารความเสี่ยงสอดคล้องกับ วัตถุประสงค์และกลยุทธ์ ขององค์ กร Communicate the benefits of risk management to all stake holders สื่อสารกับผู้มีส่วนได้ เสียทั้งหลายให้ เข้ าใจถึงประโยชน์ ของการบริหารความ เสี่ยง Define risk management performance indicators that align with organizational performance จัดทาดัชนีชี้วดั ผลของการบริหารความ เสี่ยงให้ สอดคล้องกับผลประกอบการ ขององค์กร 11 ISO 31000: FRAMEWORK DESIGN FOR MANAGING RISK 7. Establishing external communication and reporting mechanisms การจัดทากลไกการสื่อสารและการ รายงานสาหรับผู้มีส่วนได้ เสียนอก องค์กร 1. Understand the organization and its environment ความเข้ าใจในองค์กรและ สิ่งแวดล้อมขององค์กร 6. Establishing internal communication and reporting mechanisms การจัดทากลไกการสื่อสารและการ รายงานภายในองค์กร 5. Resources ทรัพยากรพอเพียงและเหมาะสม สาหรับการบริหารความเสี่ยง 2. Risk Management policy นโยบายบริหารความเสี่ยงที่ชัดเจน Risk Management Framework Elements ส่ วนประกอบของกรอบ การบริหารความเสี่ยง 3. Integration into organizational processes การบูรณาการการบริหารความเสี่ยง เข้ ากับกระบวนการขององค์กร 4. Accountability การมอบหมายความรับผิดชอบที่ ชัดเจนเป็ นลายลักษณ์ อกั ษร 12 RISK FRAMEWORK ELEMENTS 13 ISO 31000 Risk Management Process Establishing the context (5.3) Risk assessment (5.4 ) Risk identification (5.4.2) Communication and Consultation (5.2) Risk analysis (5.4.3) Monitoring and Review (5.6) Risk evaluation (5.4.4) Risk treatment (5.5) 14 Risk Management Process (Clause 5) Should be an integral part of management, be embedded in culture and practices and tailored to the business processes of the organization. Includes five activities: communication and consultation; establishing the context; risk assessment; risk treatment; and monitoring and review. 15 Reporting • Reporting is incidental to good Risk Management, not the sole focus of it! • If you only focus on reporting, you will not motivate the required culture change • Advanced Governance Codes (e.g. ASX, LSX) require two sets of reports: – The maturity and performance of the RM framework – The risk profile and how/why it has changed 16 IEC 31010 RISK ASSESSMENT TECHNIQUES 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15. 16. Brainstorming Structured or Semi-structured Interviews Delphi Technique Check-lists Preliminary Hazard Analysis HAZOP HACCP Toxicological Risk Assessment Structured What If (SWIFT) Scenario Analysis Business Impact Analysis BIA Root Cause Analysis (RCA) Failure Modes and Effects Analysis (FMEA) Fault Tree Analysis (FTA) Event Tree Analysis (ETA) Cause-consequence Analysis 17. 18. 19. 20. 21. 22. 23. 24. 25. 26. 27. 28. 29. 30. 31. Cause-and-effect Analysis Layers of Protection Analysis Decision Tree Analysis Human Reliability Assessment (HRA) Bow Tie Analysis Reliability Centred Maintenance Sneak Analysis Markov Analysis Monte Carlo Simulation Bayesian Statistics and Bayes Nets FN Curves Risk Indices Consequence /Likelihood Matrix Cost Benefit Analysis Multi-Criteria Decision Analysis 17 ISO Guide 73 - Scope Provides a basic vocabulary of the definitions of generic terms related to risk management Aims to encourage a mutual and consistent understanding, a coherent approach to the description of activities relating to the management of risk, and use of risk management terminology in processes and frameworks dealing with the management of risk. 18 Terms included in Guide 73 in Alphabetical order • • • • • • • • • • • • • • • • • • • • • • • • • COMMUNICATION & CONSULTATION CONSEQUENCE CONTROL ESTABLISHING THE CONTEXT EVENT EXPOSURE EXTERNAL CONTEXT FREQUENCY HAZARD INTERNAL CONTEXT LEVEL OF RISK LIKELIHOOD MONITORING PROBABILITY RESIDUAL RISK RESILIENCE REVIEW RISK RISK ACCEPTANCE RISK AGGREGATION RISK ANALYSIS RISK APPETITE RISK ASSESSMENT RISK ATTITUDE RISK AVERSION • • • • • • • • • • • • • • • • • • • • • • • • RISK AVOIDANCE RISK CRITERIA RISK EVALUATION RISK FINANCING RISK IDENTIFICATION RISK MANAGEMENT RISK MANAGEMENT AUDIT RISK MANAGEMENT FRAMEWORK RISK MANAGEMENT PLAN RISK MANAGEMENT POLICY RISK MANAGEMENT PROCESS RISK MATRIX RISK OWNER RISK PERCEPTION RISK PROFILE RISK REGISTER RISK REPORTING RISK RETENTION RISK SHARING RISK SOURCE RISK TOLERANCE RISK TREATMENT STAKEHOLDER VULNERABILITY 19 ISO 31000 Reducing the Risk in Risk Management Avoids organisations re-inventing the wheel Allows all to benefit from proven best practice Provides a universal benchmark Reduces barriers to trade Advises exactly what you need to do and how you need to do it – no wasted effort and no false starts Scalable – works for all sizes of organisation Risk management = Making optimal decisions in the face of uncertainty 20 ISO 31000:2009 เปรียบเทียบกับ ERM(COSO II) The Leading Edge ISO31000:2009 • ISO 31000 fully complying with COSO ERM . • ISO 31000 is more practical • Easy to apply (less than 30 pages) • Applicable to organisations in all industries, large or small • More clearly written and terms are explicitly defined • Wider acceptance as reference for risk management in existing and future standards • No need to redesign existing management system to apply • Apply to all levels of organisation for any type of risk, both positive and negative consequences ERM (COSO II) • COSO ERM does not comply with ISO 31000 • COSO is very theoretical • Very complicate (over 200 pages) • Better suited for large financial organisations • COSO is not easy to understand • Limited acceptance, mainly in the US within financial industry • Major system modification is required to comply with COSO • Focus on negative risk at corporate level, often very confusing when apply at 21 operational level Why 31000? ISO 31000:2009 is a natural successor to AS/NZS 4360:2004 Hopefully it will influence a revision of COSO It fits ‘ERM’ requirements, but also allows silo/project risk management Following ISO 31000 will provide a low cost, high chance of success approach to ERM ISO 31000 adds value and reduces risk in risk management ISO 31000 provides generic guidance on how to embed risk management, and reinforce the concept of “positive” risk Managing risk is about creating value out of uncertainty 22 2. RISK AND RISK MANAGEMENT 23 What is Risk? ความเสี่ยงคืออะไร ISO 31000:2009 defines risk as: “The effect of uncertainty on objectives” A deviation from the expected – positive and/or negative Deficiency of information relating to an event,its consequence, or likelihood • Can have different aspects e.g. finance, safety, environment goal • Can apply at different levels e.g. strategic, department, project What can go wrong? 24 How likely is it? What are the consequences? How to Describe a Risk? Risk Register Minimum Records A source of risk (hazard) An event (including when and where) An outcome (consequence) A cause (how and why) Fire Fire at head office Estimated cost 100 million Baht Short circuit Virus H1N1 Pandemic Operations Interruption Employees contact virus 25 Describing Risk – Poor Example Poor example “ there is a risk that a fraud occurs” It leaves too many questions: – How might it occur? – What parts of the organisation might be affected? – Who in the organisation might be affected? – What are the consequences? – What clues are there for developing treatments? 26 26 Describing Risk – Good Example A better description “ there is a risk that a researcher falsifies research findings resulting in cancelation of the program, loss of grant funds and reputational harm to the university” • Allows better consideration of causal factors • Allows us to better frame consequence and likelihood • Allows us to consider what controls are in place and how effective they are. For example: - Staff codes and professional conduct Peer review and quality assurance mechanisms Relationship management Reputational management 27 27 UNDERSTANDING RISK A RISK IS GENERALLY DESCRIBED AS AN EVENT WHICH LEADS TO A RANGE OF CONSEQUENCES. DO NOT CONFUSE A RISK WITH A RISK CAUSE, RISK FACTOR, AND CONTROL FAILURE. RISK CAUSE A risk cause is something that leads to the source of risk, to an exposure to it, or to a risk event. A cause can also be called contributory factor particularly when it does not necessarily result in the risk occurring but increases its likelihood. RISK FACTOR A risk factor is something that makes the magnitude of risk (likelihood or consequence) higher or lower without being specifically a cause. It may also be called a vulnerability. CONTROL FAILURE A control failure can be considered to be an uncertain event with an outcome that affects objectives. However a control failure only becomes a problem if there is a source of risk and an event 28 occurs, i.e. it is a conditional risk. EXAMPLES FOR UNDERSTANDING RISK RISK TYPE RISK SOURCE EVENT OR EXPOSURE CONSEQUE NCE RISK CAUSE RISK FACTOR Safety Working at height Fall Injury or death Poor design Height from ground Health Chemical Contact Cancer Lack of chemical knowledge Amount of chemical Finance Interest rate Rate rise more Decrease in profit than 2% in a year Inflationary pressures Extent of loans Project Supply chain Fire at factory Alternative supplier Late delivery of component Delay in project 29 DO NOT CONFUSE TYPES OF RISK Distinguish Between Direct Risk An event by which a source of risk causes harm e.g. Indirect Risk (Control Failure) An event which is described as control failure (but not necessarily causes harm) e.g. A supplier goes out of business resulting in delay to the project Failure to organise back up suppliers may result in delay to a project A person gets his hand caught in a machine resulting in serious injury A machine guard is missing which may result in hand being caught in a machine 30 Risk Management is Part of Our Daily Lives Annual Risk of dying from…. • • • • • • • • Heart disease Motor vehicle accident Homicide Drowning Fire Bicycle accident Lightening Bioterrorism 1 in 397 1 in 6,745 1 in 15,440 1 in 64,031 1 in 82,977 1 in 376,175 1 in 4,478,159 1 in 56,424,800 Don’t forget Risk Factor (Vulnerability) that may apply to you! 31 UNDERSTANDING RISKS เข้ าใจความหมาย ความเสี่ ยง ปัจจัยเสี่ ยง และ ผลกระทบ Distinguish Between Effect of a Risk Cause of a Risk (Risk Cause) สาเหตุของความเสี่ยง ปัจจัยเสี่ยง (Risk Outcome) ผลกระทบ ความเสี่ยง ความเสียหาย The Reason why the Risk might be Realised เหตุที่อาจทาให้ เกิดความเสี่ยง The Ultimate Consequence, the Harm is Done when the Risk is Realised ผลกระทบที่เกิดขึน้ (มากหรือน้ อย) Example: Staff Failed to Follow Regulations ตัวอย่ าง: พนักงานปฏิบัตผิ ดิ ระเบียบ Example: Heavy Financial Penalties Incurred ตัวอย่ าง: องค์กรเสียค่าปรับเป็ นมูลค่าสู ง More Effective to Design Controls to Manage the “Causes” of the Risk การควบคุมที่ต้นเหตุจะได้ ผลมากกว่า Often Too Late, Now that We are in Trouble, What do We Do? 32 มักสายเกินไป เมื่อเกิดความเสียหายแล้วเราจะทาอย่ างไร How can Risk be Measured? Level of Risk (Magnitude of a risk) Likelihood of occurrence Consequence of an event Risk is often expressed in terms of the consequences of an event or a change in circumstances and the associated likelihood of occurrence 33 RISK CLASSIFICATION (BY TYPE) การจัดประเภทความเสี่ ยง Risks may be classified in a variety of risk frameworks as follows: • Strategic Riskความเสี่ยงด้ านกลยุทธ์ – examples include risks related to strategy, political, economic, regulatory, and global market conditions; also include reputation risk, leadership risk, brand risk, and changing customer needs.ตัวอย่ างรวมถึงความเสี่ ยงเชิงกลยุทธ์ ที่เกีย ่ วกับ การเมือง เศรษฐกิจ กฎระเบียบ ภาวะตลาดโลก ชื่อเสียง ภาวะผู้นา ตราสัญลักษณ์ ฯลฯ • Operational Riskความเสี่ยงด้ านการดาเนินงาน – risks related to the organisation’s systems, processes, technology, and people.ความเสี่ ยงเกีย ่ วกับระบบ กระบวนการ เทคโนโลยี และบุคลากร • Financial Risk ความเสี่ยงด้ านการเงิน– includes risks from volatility in foreign currencies, interest rates, and commodities; also include credit risk, liquidity risk, and market risk. เช่ น ความอ่อนไหวในอัตราแลกเปลีย่ น ดอกเบีย้ ตลาดซื้อขาย เครดิต สภาพคล่อง และ การลงทุน • Hazard Riskความเสี่ยงด้ านอันตราย – risks that are insurable such as natural disasters; various insurable liabilities; impairment of physical assets; terrorism.ความเสี่ ยงที่เกีย ่ วกับความ ปลอดภัยซึ่งโดยทั่วไปสามารถประกันได้ เช่ น ความเสี่ยงจากภัยธรรมชาติ ความเสียหายของทรัพย์ สิน การ ก่อการร้ าย 34 RISK CLASSIFICATION (BY SOURCE OF RISK) • • • • • • • • • • • • • Business Objectives Missing, non-compliance Commercial Decline in profit, commercial contract, business partners Competition Increased competition, decrease market share, new competitor Corporate Governance Environment Low integrity, lack motivation, weak internal control Customers Key customer left, increasing pressure/demand Diseases Affecting humans, animals and plants Economic Currency fluctuations, interest rates, recession Employees Corrupt culture, lack motivation, knowledge gap Environmental Noise, contamination, pollution Financial/Economic Contractual risks, misappropriation of funds, fraud, fines Fraud/Corruption Corrupted culture, weak control, frequent fraud Human Riots, strikes, sabotage, error Information Unreliable, irrelevant, untimely, insecure • • • • • • • • • • • • Legal/Regulatory New unfavorable regulation, litigation action, non-compliance Natural Hazards Climatic conditions, earthquakes, flood, bushfires Occupational Health & Safety Inadequate safety measures, poor safety management Political Influences Intervention by politician, new government policy/direction Product/Service Liability Design error, substandard quality, inadequate testing Professional Liability Wrong advice, negligence, design error Property Damage Fire, water damage, earthquake, contamination, human error Public Liability Public access, egress and safety Public Perception Poor public image, bad reputation, brand name erosion Security Cash handlings, vandalism, theft, misappropriation of information, illegal entry Suppliers Out of business, poor quality/services, high price Technological/Equipment Obsolescence, innovation, dependability 35 Taking a risk: isn’t all bad Risk taking is positive, not implicitly negative. การยอมเสี่ ยงเป็ นเรื่องบวก ไม่ ใช่ หมายถึงแต่ เพียงเรื่องลบ We take risks not to avoid harm, but to achieve benefits and gains. เรายอมเสี่ ยงไม่ ใช่ เพือ่ เพียงหลีกเลีย่ งความเสี ยหาย แต่ เพือ่ ได้ รับผลประโยชน์ และกาไร Taking controlled, informed risks is a sensible and everyday essential part of life. การยอมเสี่ ยงในสิ่ งที่เราทราบและควบคุมได้ เป็ นสิ่ งที่สมเหตุสมผลและจาเป็ นในชีวติ ประจาวัน The higher the risk the higher the reward. ความเสี่ ยงยิง่ สู ง ผลตอบแทนยิง่ สู ง Without risk there is no progress. ไม่ มีความเสี่ ยงไม่ มีความก้ าวหน้ า 36 Risk Management as defined By ISO 31000:2009 “COORDINATED ACTIVITIES TO DIRECT AND CONTROL AN ORGANISATION WITH REGARD TO RISK” C O M M U N I C A T E C O N S U L T Activities 1. Strategic Ct 2. Identify Threats M O N I T O R & A S S E S S 3. Analyze 4. Assess 5. Assess/ R E V I E W 7. Manage the Risk Processes Opportunities Risks 37 Managing Risk We all manage risk consciously or unconsciously – but rarely systematically. เราทุกคนจัดการความเสี่ ยงโดยรู้ตัวหรือไม่ รู้ตัว-แต่ น้อยมากที่จะทาอย่ างเป็ นระบบ Managing risk involves both threats and opportunities. การจัดการความเสี่ ยงเกีย่ วข้ องทั้งภัยคุกคามและผลประโยชน์ Managing risk requires rigorous thinking. การจัดการความเสี่ ยงต้ องอาศัยความคิดทีท่ รงพลัง Managing risk means forward thinking. การจัดการความเสี่ ยงหมายถึงการคิดไปข้ างหน้ า Managing risk requires accountability and authority for decision making. การจัดการความเสี่ ยงต้ องอาศัยความรับผิดชอบทีเ่ ป็ นลายลักษณ์ อกั ษรและการมอบอานาจในการตัดสิ นใจ Managing risk requires communication. การจัดการความเสี่ ยงต้ องอาศัยการสื่ อสารทีด่ แี ละทัว่ ถึง Managing risk requires balanced thinking. การจัดการความเสี่ ยงต้ องอาศัยความคิดสมดุล Risk management provides a framework to facilitate effective decision making. การบริหารความเสี่ ยงทาให้ ได้ กรอบทีช่ ่ วยในการตัดสิ นใจอย่ างมีประสิ ทธิผล 38 Evolution of Risk Management The Past Risk Management as Compliance Identify problems Rank them Demonstrate every risk has a control (usually a standard procedure) Monitor controls The Present Risk Management to Prioritise Problems Identify problems Rank them Check if level of risk above target level (qualitative) Implement improved controls starting from highest risks Monitor implementation The Future Risk Management as Business Optimisation Identify potential problems and opportunities Understand causes and factors which affect likelihood and consequence Optimise treatment considering Effectiveness of current and proposed controls Causal factors Costs and benefits of treating the risk Costs and benefits of taking the risk Treat according to risk appetite Monitor and feedback 39 THE THREE KEY PROCESSES The Future Risk Assessment “Foresight” •Threats and opportunities when changes occurs •What are the ramifications •Cost effective risk treatment The Present Control Assurance “Insight” •Are controls adequate? •Are they effective? •Can they be cost effectively improved? The Past Root Cause Analysis “Hindsight” •Root cause analysis of successes and failures •Dissemination of learnings •Codification of learnings 40 3. Risk Management Process Establishing the context Risk assessment Risk identification Communication and Consultation Risk analysis Monitoring and Review Risk evaluation Risk treatment 41 3.1 ESTABLISH THE CONTEXT กาหนดวัตถุประสงค์ ขอบเขต และ สิ่ งแวดล้ อม 2. Identify the Internal and External Environment 1. Identify the Organisation and/or Function Objectives ระบุสิ่งแวดล้ อมภายใน และภายนอก ระบุวตั ถุประสงค์ของ องค์ กรหรือกิจกรรม 3. Identify and Analyse Relevant Stakeholders ระบุและวิเคราะห์ ผ้มู สี ่ วน ได้ เสีย THE SIX STEPS TO ESTABLISH THE CONTEXT 6 ขั้นตอนของการ กาหนดวัตถุประสงค์ ขอบเขตและ สิ่งแวดล้ อม 6. Define Key Elements for Structuring the Risk Assessment Process กาหนดองค์ ประกอบหลัก สาหรับกระบวนการประเมิน ความเสี่ยง 4. Specify the Main Scope of the Risk Management Activities กาหนดขอบเขตหลักของ กิจกรรมบริหารความเสี่ ยง 5. Identify Criteria for Risks Measurement and Acceptable Level of Risks กาหนดเกณฑ์ สาหรับการวัดค่าความ เสี่ยงและระดับความเสี่ยงที่ยอมรับ ได้ 42 EXTERNAL CONTEXT - EXAMPLES OF SOURCES OF RISK External Sources of Risk Risk issues Economic Market growth, economic cycle, shares & interest rates, capital movement, regional stability, credit availability & costs, exchange rates Political and Regulatory Legislation, regulation, government policy, political involvement, investment, standards & protocols, acceptable practices, intellectual property, societal security Supply Components, outsourcing, contractors, quality assurance, logistics, costs, availability Technology Communications, transportation, hardware, software, security, availability Competition Resources, skills, funding, market positioning, new entrants Community Reputation, ethics, partners, practices, stakeholder expectations, activism, relationships, support, 43 INTERNAL CONTEXT - EXAMPLES OF SOURCES OF RISK Internal sources of risk Risk issues People Knowledge retention, skills, integrity, loyalty, industrial relations, competency, currency of expertise, employment costs, equity, workload management, ethics, demographics, health and safety Data/information Integrity, currency, relevance, access, storage, quality, timeliness, security, communication Strategy Robustness, flexibility, strategic fit, planning capability, implementation, involvement, ownership Stakeholder management Stakeholder needs, segmentation, fulfilment, relationships, service proposition, knowledge & understanding Leadership Vision, management capability, innovation, culture, ethics, effectiveness, communication, involvement Process/product/ser vices Robustness, capability, intellectual property, life cycle, innovation, management controls, currency and relevance, quality, efficiency and effectiveness Business results Business objectives, growth, sustainable development, performance, resilience, sustainability 44 3.2 COMMUNICATION AND CONSULTATION การสื่ อสารและการให้ คาปรึกษา Internal and External Stakeholders ผู้มีส่วนได้ เสี ย ทั้งภายใน และ ภายนอก Two-Way Communication and Consultation at Each Stage of Risk Management ใช้ การสื่ อสารและให้ คาปรึกษาแบบสองทางทุกขั้นตอน Improve Understanding of risks and risk management Process เพิม่ ความเข้ าใจในเรื่องความเสี่ยง และกระบวนการบริหารความเสี่ยง Ensure varied views of stakeholders are considered Ensure all participants are aware of their roles and responsibilities ทาให้ มั่นใจได้ว่า ความเห็นทั้งหลาย ของผู้มีส่วนได้ เสี ยได้รับการพิจารณา ทาให้ มั่นใจได้ ว่าผู้เข้ าร่ วมโครงการ ทั้งหลายทราบและตระหนักในบทบาท และความรับผิดชอบของตนเอง 45 3.3 RISK IDENTIFICATION 46 WHAT NEED TO BE IDENTIFIED? Generate a comprehensive list of risks, based on those events that may enhance, prevent, degrade or delay the achievement of the objectives (including risks associated with not pursuing an opportunity) Risk Identification is critical because what is not identified cannot be managed Minimum Records A source of risk (hazard) An event (including when and where) Disease An outbreak of Bird Flu epidemic An outcome (consequence) A cause (how and why) Many people die People contact with affected chicken 47 Top 10 Emerging Risks – The Heat Map (January 2010 Survey Results by the Risk Integration Strategy Council, USA) 48 THE RISK IDENTIFICATION PROCESS กระบวนการระบุความเสี่ ยง Brainstorm Workshop ระดมสมอง Relevant Business Issues กรณีธุรกรรมทีเ่ กีย่ วข้ อง Organisation Objectives วัตถุประสงค์ ขององค์ กร Establish Risk Identification Team แต่ งตั้งคณะทางานเพือ่ ระบุความเสี่ ยง Identify Key Business/Function Elements ระบุองค์ ประกอบหลักของกิจกรรม/ธุรกรรม Identify/Clarify Business and Key Elements Objectives ระบุวตั ถุประสงค์ ของกิจกรรม/ธุรกรรม Knowledge, Commitment and Ownership ความรู้ ความมุ่งมัน่ และความเป็ นเจ้ าของ Business/Function Life Cycle วงรอบชีวติ ของกิจกรรม/ธุรกรรม Elements/Activities Objectives วัตถุประสงค์ ของ ธุรกรรม/กิจกรรม Identify Events/Risks that might Impact the Objectives Threats ภัยคุกคาม Root Cause of Risks ต้ นเหตุของความเสี่ ยง Controls that are Already in Place การควบคุมเดิมทีม่ อี ยู่แล้ว ระบุ เหตุการณ์ /ความเสี่ ยง ทีอ่ าจมีผลกระทบต่ อวัตถุประสงค์ Determine the Cause/Effect of the Risks Identified หาสาเหตุ/ผลกระทบ ของความเสี่ ยงทีถ่ ูกระบุ Opportunities โอกาส Effect of Risks on Objectives ผลกระทบของความเสี่ ยงต่ อวัตถุประสงค์ Effectiveness of the Existing Controls Evaluate the Existing Controls that Mitigate the Risks ประเมินการควบคุมทีม่ อี ยู่ทบี่ รรเทาความเสี่ ยง ประสิ ทธิผลของการควบคุมทีม่ อี ยู่เดิม 49 NEED TO SEPARATE RISK FROM CONTROL FAILURE The level of risks cannot be compared against control failures TRUE RISKS – HAZARD AND/OR SOURCE BASED Bird flu might enter country (event) •People die •Closing the chicken industry in the country •Other businesses close due to staff absent CONTROL FAILURE •Control restrictions fail (increased probability) •Slow quarantine action (increased probability) •Inadequate medicine (increased consequences) MANAGEMENT SYSTEM FAILURE •Insufficient research staff in labs doing analysis 50 STRATEGIC RISK IDENTIFICATION Strategic risk concerned with where the organisation wants to go, how it plans to get there, and how it can ensure survival. Strategic risks are generally identified through interviews with managers and other stakeholders. A structured brainstorming may be conducted to cover key issues as follow: KEY ISSUES CONSIDERATION Objectives How might they not be achieved? Resources and assets to achieve objectives How might they fail or be lost? Critical functions How they might be harmed? Events that might affect organisations What might be the outcome? Sources of risk How might they cause harm? 51 Strategic Risk Classification Strategic risk is the array of external events and trends that can devastate a company's growth trajectory and shareholder value. Typical strategic risks are: • Industry: Margin Squeeze, Rising R&D / capital expenditure costs, • • • • • • • Overcapacity, Deregulation, Increased power among suppliers, Extreme business-cycle volatility Technology: Shift in technology, Patent expiration, Process becomes obsolete Brand: Erosion, Collapse Competitor: Emerging global rivals, Gradual market-share gainer, Oneof-a-kind competitor Customer: Customer priority shift, Increasing customer power, Overreliance on a few customers Project: R&D failure, IT failure, Business development failure, Merger or acquisition failure Stagnation: Flat or declining volume, Volume up-price down, Weak pipeline Others: Certain financial-, operational-, and hazardous risks can potentially also be of strategic significance 52 3.4 RISK ANALYSIS AND TYPE OF ANALYSIS Risk analysis is a process to comprehend the nature of risk and to determine the level of risk. Risk analysis provides the basis for risk evaluation and decisions about risk treatment. There are three main types of analysis: WEIGHTING Which option? UNDERSTANDING How do we deal with a situation? SORTING What shall we do first? •Outsource maintenance or not •Which technology to choose •Introducing new IT system •Move operations to new location •Reduce safety risks •Minimising project risk •Rating gives rough idea of relative importance •Priorities for budget •What needs detailed assessment 53 PURPOSE OF RISK ANALYSIS To provide more information about possible positive and negative outcomes to improve the quality of decisions in strategic planning. To gain a better understanding of the factors which will affect risks so that negative impacts can be reduced. To prioritise risks so that important risks are dealt with first. To find a level of risk which can be compared with criteria for acceptability. To define the best treatment. To see which of a number of options has the best balance positive and negative risks. To meet regulatory requirements. 54 RISK ANALYSIS INVOLVES CONSIDERING Causes and sources of risk Positive and negative consequences The likelihood particular consequences will occur Factors affecting likelihood and consequence Existing controls (ISO31000 more focus on understanding rather than measuring compared with AS4360) 55 3.5 RISK EVALUATION RISK EVALUATION INVOLVES COMPARING ESTIMATED LEVELS OF RISK TO DETERMINE THE SIGNIFICANCE OF THE LEVEL AND TYPE OF RISK TO MAKE DECISIONS ABOUT FUTURE ACTIONS • • • • • Whether a risk needs treatment Priorities for treatment Which option to choose Whether an activity should be undertaken Which of a number of paths should be followed 56 RISK (EVALUATION) CRITERIA ALARP (As Low as Reasonably Practicable) การให้ ค่าความเสี่ ยง Generally Intolerable Region ความเสี่ ยงทีท่ นไม่ ได้ Tolerable Region (Risk is undertaken only if a benefit is desired) ความเสี่ ยงทีท่ นได้ Broadly Acceptable Region เสี่ ยงความ ทีร่ ับได้ Negligible Risk ความเสี่ ยงน้ อยมาก Risk reduction measures are essential whatever their cost จาเป็ นต้ องมีมาตรการ ลดความเสี่ ยงไม่ ว่าจะต้ องใช้ เงินเท่าใด Residual risk tolerable only if further risk reduction is impractical จาเป็ นต้ องรับความเสี่ ยงคงเหลือระดับทน ได้ นีห้ ากการลดความเสี่ ยงลงอีก ไม่ เหมาะสม/ไม่ ค้ ุมค่ า Risk reduction not likely to be required ความเสี่ ยงเหลือน้ อย ไม่ ต้องลดความเสี่ ยง แต่ ต้องคอยเฝ้ าระวังติดตามกากับดูแล 57 ISO 31000: RISK APPETITE Risk appetite is not necessarily measured in financial term Some level of risk is desirable Risk Appetite Amount and type of risk an organisation is prepared to pursue or take Risk appetite is directly related to an organisation’s strategy Risk appetite is not necessarily uniform against different type of risk 58 AN EXAMPLE OF RISK APPETITE LEVEL All Risk Total Organisational strategy 100’000 and stability 10’000 Security exposures Product design 1’000 100 10 Asset exposures Finished product or service quality expectation Time to market restrictions Customer exposure Contract management Installation and Reliance on suppliers maintenance activity Goods are stored Production activities and transported Expected Loss Unexpected Loss Expected and Unexpected Loss by Vulnerability (Euro ‘000) 59 Implementing Risk Appetite through Risk Appetite Table The risk appetite table helps an organisation to align real risk exposure with its management and escalation activities. An event or risk is assessed in the risk appetite table and assigned a risk score by multiplying the consequence and likelihood scores. Ranges of risk scores are then associated with different levels of management attention. Likelihood A (5) (Almost Certain) B (4) (Likely) C (3) (Moderate) D (2) (Unlikely) E (1) (Rare) Consequences Insignificant 1 H Minor 2 H Moderate 3 E Major 4 E Catastrophic 5 E M H H E E L M H E E L L M H E L L M H H 60 3.6 RISK TREATMENT การบาบัดความเสี่ ยง 1. 2. 3. 4. 5. 6. 7. Avoid the risk by deciding not to start or continue with the activity that gives rise to the risk Taking or increasing the risk in order to pursue an opportunity Removing the risk source Changing the likelihood Changing the consequences Sharing the risk with another party or parties (including contracts and risk financing) Retain the risk by informed decision 61 RISK TREATMENT STRATEGIES แผนกลยุทธ์ ในการบาบัดความเสี่ ยง Avoid Risks High Likelihood High Consequences Share Risks Medium Likelihood High Consequences หลีกเลีย่ งความเสี่ ยง โอกาสเกิดสูง ผลกระทบสูง แบ่ งปันความเสี่ ยง โอกาสเกิดปานกลาง ผลกระทบสูง Treat Risks with Controls High Likelihood Medium Consequences บาบัดความเสี่ ยงด้ วยการควบคุม Retain Risk Low Likelihood Low Consequence โอกาสเกิดสูง ผลกระทบปานกลาง ยอมรับความเสี่ ยง โอกาสเกิดต่า ผลกระทบต่า Likelihood โอกาสเกิด 62 RISK AVOIDANCE/ELIMINATION • • • Reduce the probability of occurrence or the impact of the risk to zero Can avoid risk by not undertaking a specific activity or choosing an alternative path, but may: • Lose potential benefit • Often substitute one risk for another Impossible to eliminate risk completely 63 RISK CHANGE/REDUCTION ADVERSE RISKS CAN BE REDUCED EITHER BY REDUCING THE LIKELIHOOD OF LOSS OR BY REDUCING THE SEVERITY OF THE EFFECTS. CONTROLS TO REDUCE NEGATIVE RISKS INCLUDE PREVENTATION, PROTECTION AND DETECTION Change Probability of Occurrence Change Consequence Fire – Separate combustion from ignition sources Fire – Automatic Sprinkler Systems Fraud – perform background checks Fraud - Audits Key Staff – Offer attractive retention package Key Staff – Succession Planning 64 RISK SHARING/TRANSFER CANNOT COMPLETELY “TRANSFER RISK” OR RESPONSIBILITY. RESIDUAL RISK OR ALTERNATIVE RISK WILL STILL EXIST. Share the risk with someone else Example of Risk Transfer/Share The financial burden and/or •Contracting consequences of the risk •Outsourcing •Insurance The level of uncertainty •Alternative Risk Transfer Some of the responsibility 65 RETAINED RISK RISK THAT REMAIN AFTER CONTROL OR TRANSFER/SHARE IS THE “RESIDUAL RISK” • • • • Those risk that can be tolerated Those risks not identified Residual risks which are not transferred Develop recovery plans for residual risk 66 BUSINESS CONTINUITY MANAGEMENT Why do we need BCM? SURVIVAL! • Recovery from a major Incident/Disaster • Responding to changing environment 67 3.7 MONITORING AND REVIEW การติดตามกากับดูแล และ ทบทวน • Few risks remain static ความเสี่ยงจานวนน้ อยทีอ่ ยู่นิ่ง • Factors affecting likelihood and consequences may change ปัจจัยทีม่ ผี ลต่อโอกาสเกิดความเสี่ยงและผลกระทบ อาจเปลีย่ นไป • Factors affecting the suitability or cost of treatment options may also change ปัจจัยทีม่ ผี ลต่ อความเหมาะสมหรือค่ าใช้ จ่ายของทางเลือกของการควบคุม อาจเปลีย่ นไป • Ongoing review of risks is essential การทบทวนอย่างต่อเนื่องเป็ นสิ่งจาเป็ น • Necessary to regularly repeat the risk management cycle จาเป็ นต้องทาซ้าวงรอบการบริหารความเสี่ยงอย่างสมา่ เสมอ 68 MONITORING PURPOSES Ensuring that controls are effective and efficient in both design and operation. Obtaining further information to improve risk assessment. Analyzing and learning lessons from events (including near-misses), changes, trends, successes and failures. Detecting changes in the external and internal context, including changes to risk criteria and the risk itself which can require revision of risk treatments and priorities. Identifying emerging risks. Progress in implementing risk treatment plans provides a performance measure. 69 HIERARCHY OF ASSURANCE ACTIVITIES ระดับชั้นของกิจกรรมเพือ่ สร้ างความมัน่ ใจในการติดตามกากับดูแล Scope and Frequency Day to day ทาเป็ นงานประจาวัน Regular Checking and Continuous - embedded into place and methods of work Monitoring ให้ ฝังตัวอยู่ในที่ทางานและวิธีทางาน การติดตามกากับดูแลอย่ างต่ อเนื่องสม่าเสมอ Control Self Assessment Line Management Review การทบทวน โดยสายการบริหาร ทาCSAการประเมินตนเองด้านการควบคุม - driven by risk profile and Manager’s span of control ซึ่งขึน้ อยู่กบั ลักษณะ ความเสี่ยงและการควบคุมของฝ่ ายบริหาร Third Party Audit การตรวจโดย บุคคลที่สาม Internal or External Auditing ตรวจสอบโดย บุคคลภายในหรือภายนอก 70 4. ENTERPRISE RISK MANAGEMENT 71 ENTERPRISE RISK MANAGEMENT (ERM) Enterprise Risk Management as defined (by COSO:2004) : “A process, effected by an entity’s board of directors, management and other personnel, applied in strategy setting and across the enterprise, designed to identify potential events that may affect the entity, and manage risk to be within its risk appetite, to provide reasonable assurance regarding the achievement of entity objectives.” ERM หมายถึง กระบวนการทีจ่ ัดทาขึน ้ โดยฝ่ ายบริหารทั้งหลายเพือ่ ประยุกต์ ใช้ ในการจัดทา แผนกลยุทธ์ ทวั่ ทั้งองค์ กรโดยออกแบบมาเพือ่ ระบุเหตุการณ์ ทอี่ าจเกิดขึน้ ที่อาจมีผลกระทบ ต่ อองค์ กร และจัดการกับความเสี่ ยงให้ อยู่ในระดับทีร่ ับได้ เพือ่ ให้ ความมัน่ ใจอย่ าง สมเหตุสมผล ในการบรรลุวตั ถุประสงค์ ขององค์ กร 72 FUNDAMENTAL CONCEPT OF ENTERPRISE RISK MANAGEMENT The definition of ERM (COSO:2004) reflects certain fundamental concepts of Enterprise Risk Management as: • • • • A process, ongoing and flowing through an entity Effect by people at every level of organisation Applied in strategy setting Applied across the enterprise, at every level and unit, and includes taking an entity-level portfolio view of risk • Designed to identify potential events that, if they occur, will affect the entity and to manage risk within its risk appetite • Able to provide reasonable assurance to an entity’s management and Board of Directors • Geared to achievement of objectives in one or more separate but overlapping categories 73 KEY ELEMENTS THAT CHARACTERISE ERM องค์ ประกอบหลักทีเ่ ป็ นคุณลักษณะของ ERM • Takes note of the interrelationships and interdependencies among risks มีการพิจารณาความสัมพันธ์ และการพึง่ พากันของความเสี่ยงทั้งหลายในองค์กร • Improve ability to manage risks within and across business units เพิม่ ขีดความสามารถในการจัดการกับความเสี่ ยงภายในและให้ ทวั่ ทั้งองค์ กร • Improve organisation’s capacity to identify and seize opportunities inherent in future events เพิม่ ความสามารถในการระบุและฉกฉวยโอกาสในเหตุการณ์ ในอนาคต • Considers risk in the formulation of strategy พิจารณาความเสี่ ยงในการวางแผน • Applies risk management at every level and unit of an entity ประยุกต์ ใช้ การบริหารความเสี่ ยงทุกระดับและทุกหน่ วยงานในองค์ กร • Takes a portfolio view of risks throughout the enterprise พิจารณาภาพรวมของความเสี่ ยงครอบคลุมตลอดทัว่ ทั้งองค์ กร 74 ERM INTEGRATED FRAMEWORK COSO (2004) Internal Environment Objective Setting Event Identification Risk Assessment Risk Response Control Activities Information & Communication Monitoring 75 Components of Risk Managements ERM(COSO II) vs ISO 31000:2009 ERM(COSOII) เปรี ยบเทียบกับ ISO 31000:2009 ERM (COSO II) • Internal Environmentสภาพแวดล้อม ISO31000 • Establish the Contextกาหนดเนือ้ หา • Objective Settingกาหนดวัตถุประสงค์ • Establish the Contextกาหนดเนือ้ หา ภายใน . วัตถุประสงค์ • • • • • Event Identificationระบุเหตุการณ์ Risk Assessmentประเมินความเสี่ยง . Risk Responseตอบสนองต่อความเสี่ยง Control Activitiesกิจกรรมการควบคุม Information and ข้ อมูลและการ Communication สื่อสาร • Monitoring การติดตามกากับดูแล • • • • • Identify Risks ระบุความเสี่ยง Analyse Risks วิเคราะห์ /ค่าความเสี่ยง Evaluate Risks ค่าความเสี่ยง Treat Risks จัดการกับความเสี่ยง Communicate and Consultการ สื่อสารและปรึกษาแลกเปลีย่ นความคิดเห็น • Monitor and Reviewการติดตามกากับดูแล และทบทวน 76 CORE PERFORMANCE MEASURES FOR ORGANISATION BALANCED SCORE CARD APPROACH Financial Profitability, Return on Investment, Revenue Growth Customer Market Share, Customer Retention, Customer Satisfaction, Customer Profitability Internal Business Process Process Time, Quality, Cost Innovation and Growth Employee Capabilities, Motivation Empowerment, Information Systems Capabilities 77 BALANCED SCORE CARD APPROACH FOR ERM (AN EXAMPLE OF UNIVERSITY PERFORMANCE) PERSPECTIVE OBJECTIVES KPI RISK OUTCOME Financial Revenue growth Market share in students% Lose/gain market share Customer Improved student satisfaction Better performance on rating scale Better/worse rating Internal operations Top research University in Thailand Number of research More/less grants grants Learning and growth % academics with a More/less academics PHD with PHD Employee capabilities 78 ERM – THE ATTRIBUTES FOR SUCCESS Embedded and integrated, consistent process for all risks, holistic Clearly defined accountability for risks and controls Line management accountability for risk management performance and maturity – linked to KPIs Risk Management is aligned with the achievement of organisation’s objectives and the strategy development and management process Emphasis on control assurance – providing “line of sight” down the organisation Emphasis on root cause analysis, for successes and failures – leading to learning Governance reporting is not just focussed on risk but on reporting on risk management performance and progress Projects are viewed in the context of the organisations objectives, not just the project outcomes 79 Efficiency of Risk Management Process Overall Risk Management Maturity Risk Governance Specific RM Driven RM •There are different type of processes for different type of risk •Risk categorization is largely consequence based •There may be attempts at some form of “integrated” measurement •Risk is seen as loss, harm and detriment •RM is closely linked to insurance •The terms ‘Risk’ and ‘hazards’ and ‘threats’ are used interchangeably •RM is motivated by reporting •High level risk assessment is stimulated by a reporting requirements •RM measures varied according to types of risk •Risk is seen as events – mostly with negative consequences •There are some inconsistent approaches to managing different types of risks Change Driven RM Enterprise Wide RM •RM is associated with the management of change •RM is driven by performance based Standards •Risk is seen as uncertainty •There is a uniform system for the analysis of all types of risk •RM is implicit in all decisions •RM processes are integrated in all processes •RM is culturally driven •Risk is seen as uncertainty •RM is about gaining strategic advantage Stage 1 Stage 2 Stage 3 Degree of Integration of Risk Management Stage 4 80 ERM AT ITS MOST MATURE ERM has the potential both to mitigate downside exposures and optimizing opportunities to add the greatest value and using risk information to gain long-term competitive advantage. •Compliance •Hazard & adverse event management •Minimising loses •Protecting the entity’s key values •Facilitating the identification of strategic opportunity •Realising opportunities for gain •Driving long-term competitive advantage and value creation Opportunities Risks 81 BUILDING AN EFFECTIVE ROBUST ERM FRAMEWORK An effective ERM framework can provide a reasonable assurance that the organization’s strategic objectives can be achieved. Building an effective framework requires a number of interrelated components include: A strong risk governance structure A clearly articulated risk appetite A clear risk strategy aligned with strategic objectives and key value drivers A strong risk management culture and capability Ongoing review of the risk framework, tolerances, and settings A common risk language and criteria Clear risk prioritisation and coordination Clear line of responsibility and accountability A strong compliance focus Continuous risk monitoring and review Efficient and effective processes, with appropriate tools and technology A commitment to continuous improvement, training and learning 82 THE MAIN RISK MANAGEMENT GAPS AND DEFICIENCIES – THE AUSTRALIAN EXPERIENCE (Standard & Poor’s Survey November 2006) The 4 Gaps where Risk Not Actively Managed •New project risk •Change Management •People Risk •Innovation Risk Top 3 Issues that Keep Management “Awake at Night” •Strategic risks •People Risk •Operating Risk Key Areas Earmarked for More Investment •Better aligning performance incentives with risk management objectives •Using risk information to add greater value •Increasing risk accountability •Creating an enterprise-wide more integrated approach •Balancing risk and reward 83 THE KEY CHALLENGES TO IMPLEMENTING RISK MANAGEMENT • • • • • • • • • • • Board/CEO support Responsibility/accountability Risk measurement Link to corporate strategy Link and impact to good corporate governance Adding value Common risk language Management buy-in Link to control self assessment Risk reporting Technology 84 Common Excuses for NOT do Risk Management We have no risk The program is too small to do risk management Making risks public performance and maturity will kill the program The customer goes ballistic whenever he/she hears of a potential problem We deal with problems as they arise Identifying risks is bad for my career Risk management creates more work for me How can you predict what will happen from now We plan to start implementing risk management 85 next year WHY ERM IMPLEMENTATION FAILS? • • • • • • • • Allowing too much complacency Failing to create a powerful coalition Underestimating power of vision Under-communicating vision Permitting obstacles to block vision Failing to create short term wins Declaring victory too soon Neglecting to anchor changes in culture 86 5. INTERNAL CONTROL 87 WHAT IS CONTROL? การควบคุมคืออะไร • Control is any action taken by management to enhance the likelihood that established objectives and goals will be achieved • การควบคุมคือกิจกรรมใดๆทีน่ ามาใช้ โดยฝ่ ายบริหารเพือ่ เพิม่ โอกาสในการบรรลุ วัตถุประสงค์ และเป้ าหมายขององค์ กร In Real-Life Language กล่ าวง่ ายๆในชีวิตจริงก็คอื • Controls are things that help to meet an organisation’s objectives • การควบคุมคือสิ่ งทีช่ ่ วยให้ บรรลุวตั ถุประสงค์ ท้งั หลายขององค์ กร 88 CONTROLS CLASSIFICATION ประเภทของการควบคุม Things Done to Help Meet a Business Objectives สิ่งที่ทาเพือ่ ช่ วยให้ บรรลุวตั ถุประสงค์ขององค์กร Preventive ป้ องกัน Stop a Risk from Occurring หยุดความเสี่ ยงไม่ ให้ เกิดขึน้ Detective ตรวจพบ Directive แนะนา Determine if a Risk Has Occurred Avoid Risks by Providing Specific Ways to Do Things ตรวจดูว่าความเสี่ ยงได้ เกิดขึน้ หรือไม่ หลีกเลีย่ งความเสี่ยงโดยแนะนาวิธีปฏิบัติ Example: Prior Approvals of Purchases Example: Exception Reports, Reconciliation Example: Guidelines and Training ต้ องมีการอนุมัติอย่ างเหมาะสมก่ อนจัดซื้อ การรายงานสิ่งผิดปกติ การตรวจกระทบยอดบัญชี คู่มือแนะนาและการฝึ กอบรม 89 CONTROL DESIGN CONCEPT แนวคิดในการออกแบบการควบคุม Controls Required to Mitigate The Risks Identified การควบคุมทีจ่ าเป็ นเพือ่ ลดความเสี่ยงทีถ่ ูกระบุ Design as Few Design Controls Only Control As Possible for Risks with Material ออกแบบการควบคุมให้ น้อยแต่ มีประสิทธิภาพ Consequences to Reaching Objectives Excess Control are All Negative การควบคุมส่ วนเกินเป็ นผลลบทั้งสิ้น ใส่ การควบคุมเฉพาะความเสี่ ยงที่มีผลกระทบ ที่สาคัญต่ อวัตถุประสงค์ 90 SIX GENERAL CATEGORIES FOR CONTROL TECHNIQUES เทคนิคการควบคุมทัว่ ไป 6 ประเภท • Competent, trustworthy personnel with clear lines of authority and responsibilityต้องใช้ บุคลากรทีม่ ีความรู้ ความสามารถและซื่อสั ตย์ มีการมอบอานาจหน้ าทีร่ ับผิดชอบชัดเจน • • Adequate segregation of dutiesมีการแบ่งแยกหน้าทีอ่ ย่างเพียงพอ Proper procedures for authorisationมีกระบวนการทีเ่ หมาะสม ในการอนุมัติต่างๆ • Adequate documents and recordsมีการทาบันทึกและเอกสารอย่าง เพียงพอ • Physical control over assets and recordsมีการเก็บรักษา ทรัพย์ สินและบันทึกต่ างๆอย่ างดีด้วยการควบคุมทางกายภาพเช่ นตู้เซฟ กุญแจ ล็อคฯลฯ • Independent checks on performanceมีการตรวจสอบการ ดาเนินงานโดยอิสระ เช่ น จากบุคคลภายนอก 91 UNDERSTANDING CONTROLS ทาความเข้ าใจกับการควบคุม Distinguish Between แยกแยะระหว่าง Hard Control Formal and/or Tangible เป็ นทางการ จับต้ องได้ (เป็ นรู ปธรรม) Easier to Determine the Existence ตรวจสอบง่ ายว่ ามีหรือไม่ Example: Written Approvals Reconciliations Segregation of Duties เช่ นกฏระเบียบต่ างๆ การแบ่ งแยกหน้ าที่ Soft Control Informal and/or Intangible ไม่ เป็ นทางการ จับต้ องไม่ ได้ (เป็ นนามธรรม) Harder to Evaluate ยากต่ อการประเมินค่ า Example: Ethics จรรยาบรรณ Integrityความถูกต้ องโปร่ งใส Commitmentความมุ่งมัน่ 92 CAN YOU TELL THE DIFFERENCE? ลองพิจารณาความแตกต่ างระหว่ าง วัตถุประสงค์ และ การควบคุม OBJECTIVES วัตถุประสงค์ CONTROLS การควบคุม ENSURE INTEGRITY OF FINANCIAL RECORDS ENSURE RECONCILIATION IS REGULARLY CONDUCTED ความถูกต้ องโปร่ งใสของรายงานการเงิน มีการตรวจกระทบยอดอย่ างสมา่ เสมอ ENSURE COMPLIANCE TO REGULATIONS ENSURE REGULAR MANAGEMENT MONITORING มีความถูกต้ องตามระเบียบและกฎหมาย มีการติดตามกากับจากฝ่ ายบริหารอย่ างสมา่ เสมอ ENSURE STAFF SAFETY มีความปลอดภัยของพนักงาน ENSURE EMERGENCY EVACUATION IS CONDUCTED มีการซ้ อมการอพยพในกรณีฉุกเฉิน 93 CAN YOU TELL THE RELATIONSHIP BETWEEN OBJECTIVES, RISK OUTCOME,RISK CAUSES & CONTROLS? ความสั มพันธ์ ระหว่ าง วัตถุประสงค์ ความเสี่ ยง ปัจจัยเสี่ ยง และ การควบคุม The Risk outcome is “not arriving at the destination due to accident,car breakdown etc.” ความเสี่ ยงคือไม่ ถึงทีห่ มาย (เนื่องจากอุบตั ิเหตุ รถเสี ย ฯลฯ) The objective of a journey is “to arrive at the destination safely” วัตถุประสงค์ ของการเดินทาง คือ ถึงทีห่ มายด้ วยความปลอดภัย การควบคุม •Police monitoringการกากับ ดูแลของตารวจ •Safe speed limitควบคุมความเร็ ว Key controls: •Effective driving Education &Test ให้ ความรู้ในการขับรถและมีการสอบที่ดี •Regular car inspection การตรวจสอบรถอย่ างสม่าเสมอ ปัจจัยเสี่ ยงทีส่ าคัญ •Bad road ถนนไม่ ดี •Bad car รถไม่ ดี •Bad driver คนขับไม่ ดี •Unsafe driving rules กฎจราจรไม่ ดี •Bad rest area ทีพ ่ กั ระหว่ างทางไม่ ดี •Hit by other cars ถูกรถอืน ่ ชน 94 Main Risk Causes: BALANCING RISKS AND INTERNAL CONTROLS Control procedures need to be developed so that they decrease risk to a level where management can accept the exposure to that risk. To achieve a balance between risk and controls, internal controls should be proactive, value-added, cost-effective and address exposure to risk. Being out of balance can cause the following problems: Excessive Risks • Loss of Assets • Poor Business Decisions • Noncompliance • Increased Regulations • Public Scandals Excessive Controls • • • • • Increased Bureaucracy Reduced Productivity Increased Complexity Increased Cycle Time Increase of No-Value Activities 95 6. RISK IDENTIFICATION TOOLS An Organisation faces Three Categories of Risks The Known Risks • • • • Past Data Checklists Thinking Prompts Human Error Analysis The Known Unknown Risks • • • • • Work System Analysis Pathway Analysis HAZOPS FMEA HACCP The Unknown Unknowns • Analysis of the past combined with imaginative thinking 96 BRAINSTORMING Brainstorming involves stimulating and encouraging free flowing conversation amongst a group of knowledgeable people to identify potential failure modes and associated hazards, risks, criteria for decisions and/or options for treatment. True brainstorming involves particular techniques to try to ensure that people's imagination is triggered by the thoughts and statements of others in the group. Brainstorming can be used in conjunction with other risk assessment methods or may stand alone as a technique to encourage imaginative thinking at any stage of the risk management process and any stage off the life cycle of a system. Normal facilitated process include: Objectives of the session are defined and rules explained. The idea is to collect as many diverse ideas as possible for later analysis. There is no discussion at this point about whether things should or should not be in a list or what is meant by particular statements because this tends to inhibit free flowing thought. All input is accepted and none is criticised and the group moves on quickly to allow ideas to trigger lateral thinking. 97 PAST DATA Process Risk can be identified from past records such as: •Financial statements •Incidents statistics •Non-compliance or complaints •Project debriefing reports Applicability Where a loss occurs relatively frequently within organisation or industry wide Strength A good way of identifying known common failures Weakness Rare but severe events may be ignored because it has not happened before within the organisation 98 CHECKLISTS Process Applicability Strength Limitation The technique provides a listing of typical uncertainties which need to be considered. Users refer to a previously developed list, codes or standards and review whether items on the checklist are present. When there is a large experience of risk which demonstrates that the same problems occur on many occasions. It is applied to check that everything has been covered. •May be used by non experts •Combine wide ranging expertise for easy to use •Help ensure common problems are not forgotten •Tend to inhibit imagination •Address only “known knowns” risks •Encourage ‘tick the box’ behaviour •Tend to miss problems not readily seen 99 THINKING PROMPTS Process List of topics or reminders which help establish a train of thought in identifying risks in an imaginative way, for example: •Project/activity objectives and critical resources needed to achieve these objectives •Risk categories such as financial, reputation, safety Applicability Thinking prompts encourage imagination more than most checklists so are appropriate when there is more variation in the things which occur than can be included in a checklist. Strength Limitation •May be used by non experts, easy to use •Help ensure key issues are not overlooked •Address mainly “known knowns” risks •Tend to miss problems not readily seen 100 HUMAN ERROR ANALYSIS A human error is a cause of risk events but not a risk itself. For each task (operation, maintenance, communication etc) apply error check list below to identify “failure modes and effect” e.g Clerk enters incorrect data resulting in incorrect billing. • • • • • • • Action omitted Action too early Action too late Action too much Action too little Action too long Action too short • • • • • Action in wrong direction Right action wrong object Wrong action right object Wrong action wrong object Information not obtained and/or transmitted • Wrong information obtained/transmitted 101 WORK SYSTEM ANALYSIS Work to be performed is separated into tasks and sub tasks to form a structure for identifying risks, for each task think about: • The environment in which it operates • Objective of the step and what could go wrong and what are opportunities • Sources of risk • Human errors • Equipment failure • Existing controls and how they could fail 102 PATHWAY ANALYSIS (SOURCE – TARGET MODEL) Undesirable Event = Risk Barriers failed = Control Failure e.g. Chemical Chemical spills into waterway Barriers may be at source, pathway, target: e.g. Chemical treatment, Regulation over use of chemical Target Local wildlife 103 MULTIPLE SOURCES AND PATHWAYS Barriers placed in either pathway can prevent explosion Barriers along each pathway can prevent escalation and the consequences 104 HAZARD AND OPERABILITY (HAZOP) Process Applicability Strength Limitation •Separate process into components •Define what the component is supposed to do •Define operating conditions •Use Hazop key words to see how performance or conditions could vary from design intent HAZOP was developed by the chemical and processing industry to identify safety and operational problems of new plant. It is applicable to any process. •Provides effective systematic means to examine a system, process or procedure •It generates solutions and risk treatment action •It involves a multidisciplinary team •Very time consuming •Hazop does not identify all risks (outside the process) or apply to all circumstances •Focus on finding solutions rather than challenging “why are we doing this” 105 HAZOP SUMMARY KEY WORDS NO or NOT MORE LESS REVERSE OF OTHER THAN PART OF AS WELL AS WHAT CAUSES IT CONDITIONS TEMPERATURE FLOW PRESSURE QUANTITY SPEED ETC HOW WOULD WE KNOW HOW MUCH DOES IT MATTER WHAT ARE THE CONSEQUENCES WHAT SHOULD BE DONE 106 EXAMPLE OF HAZOP APPLICATION OPERATING CONDITIONS Chemical Flow (in glue mixing process) Information Transfer (in project management) TYPE OF DEVIATION CAUSE CONSEQUENCES DETECTION MECHANISM None Valve shut Process stop Flow meter in pipe Too slow Valve partly blocked Product outside spec Flow meter in pipe No Do not talk to customer Dissatisfied customer No record of customer needs Too little Insufficient time for discussion Project delayed Inadequate records Too much information Over enthusiasm Difficult to pick out key requirements Large volume of records 107 FAILURE MODE AND EFFECT ANALYSIS (FMEA) Process •Consider each component individually •How it might fell •What would be the result •Would it matter •How would you detect the failure mode •Look at safety, performance &operability, and ask “What would happen if this component failed?” Applicability FMEA traditionally used for equipment failure. FMEA is similar to Hazop, however it it considers the mechanisms whereby the component can fell where Hazop considers how the intended result may not be achieved. Strength •Identify component fault modes, their causes and effects on the system, and present in an easy readable format •It identifies problems early in the design process •Identify single point failure modes Limitation •Only identify single failure modes not combinations of failure modes •Can be time consuming and costly •Can be difficult and tedious for complex multi-layered systems 108 EXAMPLE OF FMEA APPLICATION Activity/component Enter name and address from list Function Failure mode To link data to correct person Wrong name entered Failure mechanism Lost place on list Failure effect Data for wrong person Current controls Use ruler to keep aligned How would you know (before too late) Name checked before action 109 EXAMPLE OF FMEA APPLICATION ITEM 1 COMPONENT Valve FAILURE MODES FAILURE EFFECT FAILURE DETECTION Valve mechanism jammed close Low flow of A Flow meter line A Motor which operates valve fails to start Low flow of A Warning lights Motor operating valve fails to stop High flow of A Warning lights Valve gasket fails Leak of A Low flow meter reading Valve leaks when closed Unwanted flow of A Direct observation 110 HAZARD ANALYSIS AND CRITICAL CONTROL POINT (HACCP) Process Applicability •Identify hazards – any biological, chemical or physical property that may cause a food to be unsafe for consumption •Identify Critical Control Points – step, or procedure in a process at which control can be applied •Identify Control Point Conditions •Define monitoring, record keeping, corrective actions and verification procedures to remain in control Used by organisations operating anywhere within the food chain to control risks from physical, chemical or biological contaminants of food. Also extended for use in manufacture of pharmaceuticals and medical devices Strength •A structured process for quality control as well as identifying and reducing risks •Focus on how and where hazards can be prevented •Encourage risk control throughout the process Limitation •HACCP requires identification of hazards, risks, controls as inputs to the process in order to specify critical control points and control parameters •Take action when control parameters exceed defined limits may miss gradual changes 111 EXAMPLE OF HACCP APPLICATION CRITICAL CONTROL POINTS (Food Manufacturing) SOURCE OF RISK CONTROL PARAMETER MONITORING MECHANISM Receipt of ingredients Biological contamination Correct refrigeration temperature Temperature under 4 degree celcious Alarm in refrigerator when temperature over 4 degree Storage of ingredients Biological contamination Storage time prior to use Less than 24 hours Red flag for ingredients stored over 24 hours Mixing Biological contamination Temperature of mixing Temperature under 4 degree celcious Alarm in mixing room when temperature over 4 degree Cooking Biological contamination Time and temperature of cooking Cooking at 100 degree for 5 minutes System report for deviation from cooking time and temperature Packing Biological contamination Time between cooking and packaging Packing within 5 minutes after cooked Alarm when packing time exceed 5 minutes 112 CONTROL GENERAL MODEL FOR IDENTIFYING RISK conditions actions actions of people or equipment decisions What could go wrong? How would we know? 113 METHODOLOGY FOR GENERIC RISK IDENTIFICATION MODEL THE GENERIC MODEL CAN BE APPLIED TO MOST PROCESSES OR PROJECTS. IT CAN ALSO BE USED IN A POSITIVE SENSE TO IDENTIFY OPPORTUNITIES • Divide the process or project into steps • For each step identify required inputs, actions and outputs ie the things that should be there • Seek things that can cause deviations to inputs, actions and outputs. List these as risks ie an event or deviation and its consequences • This will produce one set of risks. Continue as follows: • List the required outputs of the step • Consider how those outputs may not be achieved list these as risks – (ie events and the effect on outputs). 114 EXAMPLE OF FAILURES OF REQUIRED INPUTS PROJECT STEPS INPUTS Dig trenches for cable Digger machine REQUIRED CONDITIONS ACTIONS Fine weather Employ contractors EVENTS OUTCOMES RECOMME NDATION Digger not available Delay in completion Digger machine fails Cost of digger repairs Choose reliable contractor with good maintenance process Rain Rain causes slippery surface – people fell Trench collapse Delay Choice of contractor not available Delay or incompetent contractor Injuries Exclude weather related delays from penalty clause Time cost Recruit own staff 115 EXAMPLE OF FAILURES OF REQUIRED OUTPUTS REQUIRED OUTPUT Trench 1 m deep 50 cm wide by 31 December 2008 DEVIATION Trench too deep CAUSE Specification unclear OUTCOME Extra time and money spent CONSEQUENCE RECOMMENDA TION Not significant Pay for job not time Miscommunicati on Trench not deep enough Trench completed late Time pressure Poor weather Contractor has too many jobs Soil harder than expected Explain job to people on duty Have to reemploy contractors and diggers Significant financial cost Extra time required Significant financial cost Inspect on completion before contractor leave Delay Delay Allow contingency time Review contractor before appointing 116 7. THE THONGSIRI RISK IDENTIFICATION METHODOLOGY (TRIM) วิธีการระบุความเสี่ ยงแบบ ตงศิริ A Demonstration of Risk Identification for A Procurement Process 117 SIX STEPS IN THE TRIM PROCESS 6 ขั้นตอน ของการระบุความเสี่ ยงแบบ ตงศิริ 6. Develop a TRIM Risk Map from the Identified Risks 5. Identify Events and their Consequences (Risks) that can cause Deviations to Inputs, Outputs, Actions and Conditions 4. Identify the Key Components (inputs, outputs, actions and conditions) for each Process 3. Identify the Key Processes and their Prime Objectives 2. Establish Clear System Objective 1. Gain a Clear Understanding of the System 118 STEP 1: UNDERSTAND THE SYSTEM (WHAT IS INVOLVED IN THE SYSTEM OPERATIONS?) ขั้นตอนที่ 1 ทาความเข้ าใจระบบการทางาน What is the scope of this assessment ? ขอบเขตของงาน เป็ นอย่ างไร What is the system trying to achieve? What are the key activities? กิจกรรมหลัก คืออะไร THE SYSTEM ระบบงาน ระบบต้ องการ บรรลุ วัตถุประสงค์ ใด Who are the key players within the system? ใครบ้ างทีเ่ ป็ น ตัวการในระบบ How are activities being carried out? กิจกรรมหลัก ทาอย่ างไร Who is responsible for what? ใครรับผิดชอบอะไร 119 STEP 2:ESTABLISH CLEAR SYSTEM OBJECTIVES ขั้นตอนที่ 2: ระบุวตั ถุประสงค์ ของระบบงานให้ ชัดเจน Other Objectives are Success Criteria for the Key Process The System Prime Objective For “Procurement” is to ‘Meet Organisation Requirements’ วัตถุประสงค์ รองระดับ กระบวนการเป็ นองค์ ประกอบ แห่ งความสาเร็จ ของกระบวนการ 6 5 The Prime Objective of a Key Process is a Success Criteria for the System 4 1 3 2 วัตถุประสงค์ หลักระดับกระบวนการ เป็ นองค์ ประกอบแห่ งความสาเร็จของระบบ 120 STEP 3: IDENTIFY THE KEY PROCESSES AND THEIR OBJECTIVES Example: Procurement Process Specification accurately reflecting the needs Good/services meet the need of users 2.0 Develop Specificatio n 1.0 Determine users Requirement s System Prime Objective = Good/services purchased meet the organization requirements in the most effective, efficient, and economical manner 6.0 Managemen t Monitoring 3.0 Purchase goods and/or Services 5.0 Payment for Goods & Services Payment for Good/services is accurate 4.0 Receive and Distribution Goods & Services Value for money is achieved Good/services are delivered as per the agreement 121 STEP 4: IDENTIFY KEY COMPONENTS FOR EACH KEY PROCESS (INPUTS, OUTPUTS, ACTIONS AND CONDITIONS) •Weather – rain, hot, cold •Regulations, Rules. Policy •Infrastructure CONDITIONS •Resources •People •Equipment •Budget •Materials •IT System •Information INPUTS Process 1 OUTPUTS •Objectives •Products •Profits •Reputation •Security •Etc etc Strategic Operation Financial Compliance ACTIONS •Action of people •Functioning of equipment •Decisions •Authorization 122 EXAMPLE 4.1: KEY COMPONENTS FOR THE PROCESS “USERS REQUIREMENTS” •Time available •Market/technical availability •Government policy/intervention •Align with Business Plan/Strategy (S) •Compatible with existing systems CONDITIONS •Stakeholders •Buyer •Knowledge of the goods/services •Feedback from stakeholders •Technical experts •Approved budget •Business plan •Organization strategies INPUTS 1.0 Determine users Requirements OUTPUTS ACTIONS Meet operational requirements (O) Good/services meet the need of users (this is the Prime Objective for the Process 1.0) Within budget (F) Comply with organizational policy (C) •Survey of users requirements •Communication and coordination between buyers and users •Decision making to proceed 123 EXAMPLE 4.2: KEY COMPONENTS FOR THE PROCESS “DEVELOP SPECIFICATION” •Time available •Market/technical availability •Government policy/intervention •Open for competitive bidding (S) CONDITIONS •Users requirements •Professional standards •Organization standard •Knowledge of the goods/services •Technical experts in developing specification •Business plan •Organization strategies INPUTS 2.0 Develop Specification OUTPUTS ACTIONS •Writing of specification •Review and approval of specification •Decision making to proceed Reflects users requirements (O) Specification accurately reflecting the users needs (this is the Prime Objective for the Process 2.0) Within budget (F) •Comply with professional standards (C) •Comply with organizational standard 124 EXAMPLE 4.3: KEY COMPONENTS FOR THE PROCESS “PURCHASE GOOGDS/SERVICES” •Time available •Market/technical availability •Government and/or organizational policy/intervention •Specification •Budget •Suppliers •Selection committee •Selection criteria •Industry standards •Organization procurement procedures •Knowledge of the goods/services •Technical product experts •Advertising media CONDITIONS INPUTS 3.0 Purchase goods and/or Services OUTPUTS ACTIONS •Advertise for quotations and/or tenders •Selection and approval of supplier •Develop supply contract •Appropriate supply contract (S) Reflects specification (O) Value for money is achieved (this is the Prime Objective for the Process 3.0) •Within budget (F) •Competitive price •Comply with industry standards (C) •Comply with organizational procurement policy and procedures 125 EXAMPLE 4.4: KEY COMPONENTS FOR THE PROCESS “RECEIVE & DISTRIBUTION OF GOOGDS/SERVICES” •Natural environment •Products availability •Contract terms and conditions •Supplier •Goods/services •Store •Users •Logistic personnel •Technical product experts •Quality assurance personnel •Delivery dockets •Supply contract •Purchasing/delivery plan •Logistic MIS CONDITIONS INPUTS 4.0 Receive and Distribution Goods & Services OUTPUTS ACTIONS •Deliver of goods/services •Inspection and/or quality assurance action •Storage of delivered goods •Delivery of goods to users •Meet business plan/strategy (S) •Synchronize with interrelated parties Meet operational/industry requirements (O) Good/services are delivered as per the purchase agreement (this is the Prime Objective for the Process 4.0) •Appropriate security (F) Comply with purchase contract (C) 126 EXAMPLE 4.5: KEY COMPONENTS FOR THE PROCESS “PAYMENT FOR GOOGDS/SERVICES” •Funds availability •Contract terms and conditions •Organizational payment procedures •Supplier •Goods/services •Budget •Funds •Bank •Accounts personnel •Store personnel •Approval delegation •Users •Invoices •Delivery dockets •Supply contract •Accounts MIS CONDITIONS INPUTS 5.0 Payment for Goods & Services OUTPUTS ACTIONS •Receive claims for payment •Check claims against goods/services received and terms of payment •Approval for payment •Make payment Payment for Good/services is accurate (this is the Prime Objective for the Process 5.0) •Within budget (F) •Comply with purchase contract (C) •Comply with organizational payment procedures 127 EXAMPLE 4.6: KEY COMPONENTS FOR THE PROCESS “MANAGEMENT MONITORING” •Political influence •Budget availability •Government/organizational policy and procedures •Probity and transparency •Managers •Management information system •Security system •Budget •Procurement staff •Policy and procedures •Strategy •Risk Management •Internal Controls CONDITIONS INPUTS 6.0 Management Monitoring OUTPUTS ACTIONS •Regular monitor the performance of the procurement process •Plan and coordinate interrelated activities •Communicate and provide report and/or feedback to relevant stakeholders •Ensure compliance with organizational, regulatory and standards requirements •Provide appropriate strategy, direction and resources •Meet business plan/strategy (S) •Synchronize with interrelated parties Meet operational & OHS requirements (O) Good/services purchased meet the organization requirements in the most effective, efficient, and economical manner (this is the Prime Objective for the Process 6.0) •Value for money (F) •Within budget Meet all stakeholders requirements (C) 128 EXAMPLE 4.7: THE SUCCESS CRITERIA FOR THE “PROCUREMENT PROCESS” 6. Good/services purchased meet the organization requirements in the most effective, efficient, and economical manner 5. Payment for Good/services is accurate 4. Good/services are delivered as per the purchase agreement 3. Value for money is achieved 2. Specification accurately reflecting the users needs 1. Good/services meet the need of users 129 STEP 5: IDENTIFY RISKS FOR THE KEY COMPONENTS THE MOST SIGNIFICANT RISK IN EACH PROCESS IS A FAILURE TO ACHIEVE THE PRIME OBJECTIVE OF THE PROCESS (i.e. EACH OF WHICH WILL STOP THE BANKNOTE PRODUCTION) CONSIDER HOW THE OTHER OUTPUTS (SUCCESS CRITERIA) MAY NOT BE ACHIEVED. LIST THESE AS RISKS (EVENTS AND THE EFFECT ON OUTPUTS). SEEK THINGS THAT CAN CAUSE DEVIATIONS TO ACTIONS & INPUTS; AND ALSO ADVERSE CONDITIONS. LIST THESE AS RISKS (AN EVENT OR DEVIATION AND ITS CONSEQUENCE) 130 EXAMPLE 5.1: KEY RISKS FOR THE PROCESS “USERS REQUIREMENTS” Goods/services do not meet the need of users Restriction by stakeholders lead to inappropriate goods/services procured Goods/services do not meet operational requirements Goods/services are not aligned with Business Plan and/or strategy 1.0 Determine Users Requirements Inappropriate goods/services due to inaccurate users requirements information Poor communication lead to incorrect goods/services procured Inferior goods/services due to poor judgment by decision maker 131 EXAMPLE 5.2: KEY RISKS FOR THE PROCESS “DEVELOP SPECIFICATION” Specification does not accurately reflecting the users needs Poor quality of specification due to unreasonable time pressure Specification does not comply with professional and/or organizational standards 2.0 Develop Specification Inaccurate specification due to unclear users’ requirements and/or poor communication Specification consists of inadequate and/or anticompetitive requirements Poor quality of specification due to incompetent technical writer Poor quality of specification due to lack of appropriate supervision and/or approval 132 EXAMPLE 5.3: KEY RISKS FOR THE PROCESS “PURCHASE GOODS AND/OR SERVICES” Inappropriate supply contract resulted in loss for organisation Goods and/or Services do not match specification and/or meet organisation & industry standards Value for money is not achieved Non compliance with proper procurement procedures lead to loss for the organisation Unreliable supply of critical materials in terms of availability & quality resulted in operations disruption Non competitive bidding lead to inferior products and/or high price 3.0 Purchase Goods and/or Services Ineffective selection process resulting in inferior products and/or high price Favouritism, corruption and/or fraud lead to loss for the organisation 133 EXAMPLE 5.4: KEY RISKS FOR THE PROCESS “RECEIVE & DISTRIBUTION OF GOODS/SERVICES” Goods & Services (quality, quantity and timeliness) are not delivered as per the supply agreement resulted in loss and/or disruption to business Good/services are not delivered as per the purchase agreement Inappropriate and/or unclear supply contract lead to disputes and loss for organization Supplier in liquidation or operations disruption cause major loss and/or disruption to business Poor delivery planning to synchronize with interrelated parties resulted in operations disruption 4.0 Receive and Distribution Goods & Services Improper inspection resulted in receiving inferior products Improper handling and/or security of goods delivered resulted in damages or loss of assets 134 EXAMPLE 5.5: KEY RISKS FOR THE PROCESS “PAYMENT FOR GOOGDS/SERVICES” Financial loss due to payment in excess of the agreed supply terms and conditions Financial loss due to payment for goods and/or services not received or inferior quality or not properly completed Inaccurate payment for Good/services Inefficient/ineffective budget administration lead to shortage of funds for payment 5.0 Payment for Goods & Services Inaccurate MIS resulted in financial loss due to overpayment Financial loss from unauthorized payment due to fraud or corruption Valuable suppliers left due to excessive delay in payment 135 EXAMPLE 5.6: KEY RISKS FOR THE PROCESS “MANAGEMENT MONITORING” Good/services purchased DO NOT meet the organization requirements in the most effective, efficient, and economical manner Litigation action and/or financial/reputation loss due to lack of transparency and probity in the procurement process Financial and/or reputation loss due to lack of appropriate procurement policy and procedures Good/services become obsolete due to a lack of management planning and/or strategy 6.0 Managemen t Monitoring Management decision making is not optimal due to lack of effective MIS and Risk Management Financial loss and/or business disruption due to lack of appropriate procurement plan and coordination of interrelated activities Fraud/ corruption or inefficient/effective procurement due to lack of management monitoring Fraud or corruption due to non compliance with mandatory procurement procedures 136 EXAMPLE 5.7: THE SHOW STOPPERS FOR THE “PROCUREMENT PROCESS” Mission Impossible Good/services purchased meet the organization requirements in the most effective, efficient, and economical manner Inaccurate payment for Good/services Good/services are not delivered as per the purchase agreement Value for money is not achieved Specification does not accurately reflecting the users needs Goods/services do not meet the need of users 137 STEP 6: DEVELOP THE TRIM RISK MAP (COMPILE ALL THE IDENTIFIED RISKS FROM STEP 5 INTO A RISK MAP) ขั้นตอนที่ 6:พัฒนาแผนที่ความเสี่ยงแบบ ตงศิริ Goods/services do not meet the need of users 1 3 7 Inappropriate goods/services due to inaccurate users’ requirements information 1.0 Determine Users Requirements Inefficient/ ineffective budget administration lead to shortage of funds for payment 39 44 6.0 Management Monitoring 43 Management decision making is not optimal due to lack of effective MIS Inaccurate payment for goods/services 35 Inaccurate MIS resulted in financial loss due to overpayment Inferior goods/services due to poor judgment by decision maker Fraud/ corruption or inefficient/effective procurement due to lack of management monitoring 40 42 41 Fraud or corruption due to non compliance with mandatory procurement procedures Financial loss due to payment in excess of the agreed supply terms and conditions 32 5.0 Payment for Goods & Services 33 34 Valuable suppliers left due to excessive delay in payment Poor quality of specification due to unreasonable time Inaccurate specification due to unclear users’ requirements and/or poor communication Inappropriate and/or unclear supply contract lead to disputes and loss for organization Financial loss from unauthorized payment due to fraud or corruption 2.0 Develop Specification 24 23 4.0 Receive and Distribution Goods & Services 29 26 28 Supplier in liquidation or operations disruption cause major loss and/or disruption to business 10 12 Poor quality of specification due to incompetent technical writer 11 Inappropriate supply contract resulted in loss for organisation Value for money is not achieved Poor delivery planning to synchronize with interrelated parties resulted in operations disruption Improper inspection resulted in receiving inferior products 27 Improper handling and/ or security of goods delivered resulted in damages or loss of assets 15 Goods and/or Services do not match specification and/or meet organisation & industry standards 16 17 Non compliance with proper procurement procedures lead to loss for the organisation 25 Specification consists of inadequate and/or anticompetitive requirements 13 Poor quality of specification due to lack of appropriate supervision and/or approval Goods & Services (quality, quantity and timeliness) are not delivered as per the supply agreement resulted in loss and/or disruption to business Good/services are not delivered as per the purchase agreement 8 14 Financial loss due to payment for goods and/or services not received or inferior quality or not properly completed 31 30 36 5 Poor communication lead to incorrect goods/ services procured Financial loss and/or business disruption due to lack of appropriate procurement plan and coordination of interrelated activities 38 Financial and/or reputation loss due to lack of appropriate procurement policy and procedures 4 37 Litigation action and/or financial/reputation loss due to lack of transparency and probity in the procurement process Specification does not comply with professional and/or organizational standards 9 6 Good/services become obsolete due to a lack of management planning and/or strategy Specification does not accurately reflecting the users’ needs Goods/services are not aligned with Business Plan and/or strategy 2 Restriction by stakeholders lead to inappropriate goods/ services procured Good/services purchased Do Not meet the organization requirements in the most effective, efficient, and economical manner Goods/services do not meet operational requirements 22 3.0 Purchase Goods and/or Services 21 19 20 Unreliable supply of critical materials in terms of availability & quality resulted in operations disruption 18 Non competitive bidding lead to inferior products and/or high price Ineffective selection process resulting in inferior products and/or high price Favouritism, corruption and/or fraud lead to loss for the organisation 138 ANALYSE THE TRIM RISK MAP (USE CONSEQUENCE LIKELIHOOD MATRIX) Estimated Level of Risk ประเมินระดับของความเสี่ยง (โอกาสเกิดxผลกระทบ) Paint the Risk Map (Step 6) with appropriate colour code as per the Risk Matrix to show the level of Residual Risk Prioritised List of Risks จัดลาดับของความเสี่ยง Compare Against Organisation Risk Appetite Compare Against Organisation Risk Tolerance เปรียบเทียบกับความอยากในความเสี่ยงขององค์กร เปรียบเทียบกับความเสี่ยงที่ทนได้ขององค์กร Low Risk ความเสี่ยงต่า Acceptable Risk Unacceptable Risk ความเสี่ยงที่ยอมรับได้ ความเสี่ยงที่ยอมรับไม่ ได้ Monitor and Periodically Review ติดตามกากับดูแล ทบทวน เป็ นระยะๆ Risk Treatment จัดการบาบัดความเสี่ยง 139 BOW TIE ANALYSIS EXAMPLE PROCUREMENT PROCESS Incompetent contract administrator Impractical and/or unclear contract terms and conditions Training Financial loss Insurance Recruitment process Expert advice Penalty Approval Disadvantages contract terms and conditions Legal advice Approval Inappropriate supply contract resulted in loss for organization Contingency plan Business disruption KPI Monitoring No enforcement for compliance with contract terms and conditions Media control Job description Procedures Unclear accountability over contract administration Risk source/Cause Reputation damage 140 Controls Risk Event Controls Consequences 8. RISK AND ANALYSIS TECHNIQUES IEC 31010 141 METHODS OF RISK ANALYSIS Qualitative Analysis วิเคราะห์ เชิงคุณภาพ (ตามความรู้ สึก) ใช้ การอธิบายโอกาสเกิดและผลกระทบ Use words to describe likelihood and consequences (eg high, medium, low) Semi-quantitative Analysis วิเคราะห์ เชิงกึง่ ปริมาณ Quantitative Analysis กาหนดค่าของโอกาสเกิดและ ผลกระทบ ตามสเกลแต่ ไม่ ใช่ ค่าจริง วิเคราะห์ เชิงปริมาณ ใช้ กระบวนการคณิตศาสตร์ (ความน่ าจะเป็ นและสถิต)ิ เพือ่ กาหนดค่าโอกาสเกิดและผลกระทบ Give values for ranking scales but not the realistic values for risk (eg scale 1-100) Use numerical values for both likelihood and Consequences (eg loss $5 million) 142 Risk Analysis – What to Measure? Normally involves estimation of range of possible consequences and their associated likelihoods in order to measure risk Level of risk should be expressed in suitable terms for the type of risk and to aid evaluation. In some instances risk can be expressed as a probability distribution across a range of consequences Taking a single consequence and its likelihood as required in the matrix is an approximation to the level of risk One must either take maximum consequences and their likelihood or most likely consequences and their likelihood really it is the sum of all consequences and their likelihoods 143 RISK AND ANALYSIS TECHNIQUES Human error Analysis Organisational analysis Individual and organisational motivators/drivers Fault trees Casual analysis Source of risk Cause of events Event Trees and Scenario Analysis Consequence modelling Detect events and reduce Consequences Respond and recover Risk Event Risk Event Hazards Remove underlying Reduce/eliminate causes sources of risk/hazards Prevent Event Detect Event Loss to people Assets, Reputation etc Response Recovery Contingency plans Recovery plans Insert Barriers Rehabilitation Detect early damage Protect targets Limit consequences Share risk preconditions occurrence consequence Return to normal 144 DETAILED ANALYSIS OF RISK Which technique to choose? CONSEQUENCES • Scenario Analysis • Event Tree Analysis • Consequence Modelling CAUSES • Statistical Analysis • Root Cause Analysis • Fault Tree Analysis • Ishikawa Analysis CAUSES AND CONSEQUENCES • Cause Consequence Diagrams • Bow Tie Analysis CONSEQUENCE AND LIKELIHOOD • Consequence and Likelihood Matrix ANALYSIS OF CONTROLS • LOPA • Bow Tie Analysis • CSA 145 CONSEQUENCE LIKELIHOOD MATRIX The consequence likelihood matrix is a means of combining qualitative or semi-quantitative ratings of consequence and likelihood to produce a level of risk or risk rating. A consequence likelihood matrix is used to rank risks, sources of risk or risk treatments on the basis of the level of risk. It is commonly used as a screening tool to define which risks need further more detailed analysis or which risks need treatment first, or which risks need not be considered further at this time. Points to remember: The consequence scale should cover the range of different types of consequence to be considered (for example financial loss, safety, environment or other parameters depending on context). The lowest likelihood must be acceptable for the highest defined consequence otherwise all activities with the highest consequence are defined as intolerable. Many risk events may have a range of outcomes with different associated likelihood. It is appropriate to focus on the most serious outcome, or to rank both common problems and unlikely catastrophes as separate risks. 146 CONDUCT RISK ANALYSIS ทาการ วิเคราะห์ ความเสี่ ยง Key Process กระบวนการ หลัก Objectives วัตถุประสงค์ Critical path for a system life cycle. Key functions that help a system achieves its mission. What the process try to achieved? What are the key success criteria for the process? เส้ นทางสาคัญของ วงรอบชีวติ ของ ระบบธุรกรรม กิจกรรมหลักที่ ช่ วยให้ ระบบบรรลุ เป้ าหมาย กระบวนการต้องการ บรรลุวตั ถุประสงค์ใด อะไรคือเงื่อนไขแห่ง ความสาเร็ จหลักของ กระบวนการ Risk Outcome ผลกระทบของ ความเสี่ ยง Risk Cause สาเหตุของ ความเสี่ ยง Likelihood (1-5) The outcomes of the process that we do not want to happen. They are indicators of a process failure. The event that cause or lead to the undesirable risk outcomes. Probability or frequency of an event to occur. Can be expressed qualitatively or quantitatively ผลลัพท์ของ กระบวนการที่เราไม่ ต้องการให้เกิดขึ้น ผลลัพท์เหล่านี้เป็ นตัว บ่งชี้ถึงความล้มเหลว ของกระบวนการ เหตุการณ์ที่ทา ให้เกิดหรื อ นาไปสู่ ผลลัพท์ ของความเสี่ ยงที่ เราไม่ตอ้ งการ โอกาสเกิด Consequence (1-5) ผลกระทบ Risk Rating (1-25) อัตราเสี่ยง ความน่าจะเป็ นหรื อ ความถี่ของเหตุการณ์ ที่จะเกิดขึ้น อาจแสดงในเชิงอนุ มาณหรื อเชิงปริ มาณ Outcome or impact of an event. There can be more than one consequence from an event, can be positive or negative, qualitative or quantitative. ผลลัพท์หรื อ ผลกระทบจาก เหตุการณ์ อาจมี มากกว่าหนึ่ง อาจ เป็ นผลบวกหรื อลบ เป็ นรู ปธรรมหรื อ นามธรรม Risk rating or risk score is the product of multiplying the likelihood level with the consequence level. It helps to determine the level of risk whether it is low, medium, high or very high ค่ าของอัตราเสี่ยงมาจาก ผลคูณของโอกาสเกิด และผลกระทบซึ่งช่ วย ให้ ทราบว่ าความเสี่ยงอยู่ ระดับในตา่ กลาง สู ง หรือสู งมาก 147 SAMPLE CONSEQUENCES RANKING ตัวอย่างการจัดลาดับ ผลกระทบ Level ระดับ Descriptor ความรุนแรง 1 Insignificant น้ อยมาก 2 Minor น้ อย Medium financial loss, first aid treatment, on-site release immediately contained 3 Moderate ปานกลาง High financial loss, medical treatment required, on-site release contained with outside assistance สู ญเสี ยทรั พย์ สินสู ง ต้ องรั กษาพยาบาล Major มาก Major financial loss, extensive injuries, loss of production capability, off-site release with no detrimental effects สู ญเสี ยทรั พย์ สินสู งมาก 4 5 Catastrophic มากทีส่ ุ ด Description/Impact คาอธิบาย/ผลกระทบ Low financial loss, no injuries สู ญเสี ยทรัพย์สินน้ อย ไม่ มกี ารบาดเจ็บ สู ญเสี ยทรัพย์สินปานกลาง ใช้ ปฐมพยาบาล สามารถควบคุมได้ ทนั ที ควบคุมสถานการณ์ ได้ โดยต้ องอาศัยความช่ วยเหลือจากภายนอกด้ วย บาดเจ็บสาหัส สู ญเสี ยความสามารถในการผลิต สารพิษรั่วออกภายนอกแต่ ไม่ มี ผลกระทบมากนัก Huge financial loss, death, toxic release off-site with detrimental effect สู ญเสี ย ทรัพย์ สินมากทีส่ ุ ด เสี ยชี วติ สารพิษรั่วออกภายนอกและเกิดผลกระทบร้ ายแรง 148 SAMPLE LIKELIHOOD RANKING ตัวอย่ างการจัดลาดับ โอกาสเกิดเหตุการณ์ Level ระดับ Probability ความน่ าจะเป็ น Description คาอธิบาย 1 Rare น้ อยมาก 2 Unlikely น้ อย Could occur at some time (e.g. once in 5 years) 3 Possible ปานกลาง Might occur at some time (e.g. once a year) 4 Likely มาก 5 Almost Certain มากทีส่ ุ ด May occur only in exceptional circumstances (e.g. once in 10 years) อาจเกิดได้ ในสถานการณ์ พเิ ศษเท่ านั้น(เช่ น เกิด 1 ครั้ง ใน 10 ปี ) สามารถเกิดได้ ในบางครั้ง(เช่ น เกิด 1 ครั้ง ใน 5 ปี ) อาจเกิดได้ ในบางครั้ง(เช่ น เกิดปี ละ 1 ครั้ง) Will probably occur in most circumstances (e.g. monthly) น่ าจะเกิดได้ ในทุกสถานการณ์ (เช่ น เกิดขึน้ ทุกเดือน) Is expected to occur in most circumstances (e.g. daily) คาดว่ าจะเกิดได้ ในทุกสถานการณ์ (เช่ น เกิดขึน้ ทุกวัน) 149 SAMPLE RISK ANALYSIS MATRIX Likelihood A (5) (Almost Certain) B (4) (Likely) C (3) (Moderate) D (2) (Unlikely) E (1) (Rare) Consequences Insignificant 1 H Minor 2 H Moderate 3 E Major 4 E Catastrophic 5 E M H H E E L M H E E L L M H E L L M H H E: Extreme Risk, Immediate Action Required ความเสี่ ยงสู งมาก ต้องจัดการทันที H: High Risk, Senior Management Attention Needed ความเสี่ ยงสู ง ผูบ้ ริ หารระดับสู งต้องลงมาดูแล M: Moderate Risk, Management Responsibility Must be Specifiedความเสี่ ยงปานกลาง ต้องแจ้งผูบ้ ริ หารที่รับผิดชอบการบริ หารความเสี่ ยง L: Low Risk, Manage by Routine Procedures ความเสี่ ยงต่า จัดการโดยขั้นตอนตามปกติ 150 SCENARIO ANALYSIS Applicability Scenario analysis can be used to assist in making policy decisions and planning future strategies as well as to consider existing activities. Process Scenario analysis consists of defining a simplified ‘model’ of a real system and using the model to consider what might happen given various possible future developments. Sets of scenarios reflecting best case, worst case and ‘expected’ case may be used to identify what might happen under particular circumstances and analyse potential consequences and their likelihood for each scenario Strength •It takes account of a range of possible futures rather than focus on the use of historical data Limitation •Where there is a high uncertainty some of the scenarios may be unrealistic •Data may not be available to develop realistic scenario 151 EVENT TREE ANALYSIS (ETA) Applicability ETA can be used at any stage in the lifecycle of a product or process. It may be used qualitatively or quantitatively to help brainstorm potential scenarios and sequences of events following an initiating event and how outcomes are affected by various treatments, barriers or controls intended to mitigate unwanted outcomes. Process ETA identify possible pathways following an initiating event or failure and assessing the frequency of the various possible outcomes. •Select an initiating event. •List as headings for functions or systems which are in place to mitigate outcomes in sequence. •For each function draw a line to represent their success or failure. There can be only 2 branches for each function (yes it will happen or no it won’t). •Estimate the probability of success or failure for each branch. •The frequency of the outcome is the product of the individual probabilities and the frequency of the initiation event. 152 EXAMPLE OF AN EVENT TREE Initial event Alternative supplier Immediate No modification supply needed Yes 0.7 Yes 0.9 No 0.1 Outcome Probability No delay 0.252 Delay for modification 0.026 Yes 0.4 Yes 0.9 Delay for supply 0.108 No 0.3 Supplier fails to deliver No 0.1 No 0.6 Very late 0.012 Cannot complete 0.600 1.000 153 MODELLING A NUCLEAR ACCIDENT SCENARIO (Sizewell Power Station) The aim of the model was to find out how people would be affected and the best emergency response strategy WHAT DO WE WANT TO KNOW HOW WOULD WE FIND OUT How much radiation would get out Design accident How far and how fast would it spread Use bomb tests for size and temperature of radioactive particles and use standard plume dispersal model What is the radiation dose to people at different distances from the plant Absorbtion distance known from penetration tests How much protection is needed How will people absorb radiation (skin, soil, food etc) How would it affect them Dose response – data from bombs and testing Identify and assess risk of evacuation From past experience, develop Emergency 154 Evacuation Plan MODELLING DOSE CONTOURS FOR A RADIOACTIVE RELEASE FROM SIZEWELL It was estimated that: •400 face immediate death •2000 risk of cancer next 20 years •Dust settled after 24 hrs 155 MONTE CARLO ANALYSIS Monte Carlo is a complex mathematical sensitivity analysis when there is a known relationship between input parameters (variables) and an outcome but the values of the parameters are uncertain. The effect of the variables on the result is calculated many times by computer (using software Crystal Ball or @risk) to achieve the best estimated outcome. • Monte Carlo analysis is a means of including uncertainty in models and equations • It is a way of doing the calculation with distributions of values rather than single values • Estimate range of outcomes can be obtained by repeating the calculation with lowest estimates and highest estimates • It is very unlikely all variable will be the minimum at once or all the highest estimate 156 Overview The analysis of a major loss to prevent its reoccurrence is commonly referred to as Root Cause Analysis (RCA), Root Cause Failure Analysis (RCFA) or Loss Analysis. RCA is focused on asset losses due to various types of failures while Loss Analysis is mainly concerned with financial or economic losses due to external factors or catastrophes. It attempts to identify the root or original causes instead of dealing only with the immediately obvious symptoms. Applicability ROOT CAUSE ANALYSIS •For accident investigations and occupational health & safety •In technological systems related to reliability & maintenance •Quality control for industrial manufacturing •On business processes •In change management, risk management and systems analysis 157 EXAMPLE OF ROOT CAUSE ANALYSIS Problem Symptom Leak from paint factory Yellow discharge in creek First Level Cause Pump leaked Second Level Cause Seal failed Third Level Cause Pump not maintained Fourth Level Cause No preventative maintenance Root Cause No preventative Workshop not Maintenance policy available Lack of knowledge Old equipment Low staff level of managers Financial constraints 158 ROOT CAUSE ANALYSIS FOR POSITIVE RISK Objective Maximum profitability Necessary Conditions (Success Criteria) Dominant market share Leading edge technology Customer satisfaction World class communication systems/products World class customer support Innovation Speed of development and/or response High quality hardware, software High quality, secure, satisfied workforce Highly competent associates Fulfillment of individual needs 159 EXAMPLE OF A FAULT TREE The fault tree below demonstrates the causes of the problem of a projector failure during a lecture. Projector Lamp Outage Head Event Top Event Power outage Unresolved Lamp Failure OR (Any one of the events below causes the one above) Accidental Shutdown Wiring Failure Base Event Lamp Failure No spare lamp Operator error AND (All of the events below needed to cause events above) Trip and unplug Internal External 160 EXAMPLE OF AN EVENT TREE The event tree below demonstrates the consequences of the problem of a projector failure during a lecture. Lecturer fixes Light Projector Failure Lecture proceeds Y Technician fixes N Slight delay Y Back up projector available N Y Lecture delayed Lecturer has to print out Lecture N Y N delayed Lecture cancelled 161 CAUSE-AND-EFFECT ANALYSIS Cause-and-effect analysis is a structured method to identifying possible causes of an undesirable event or problem. It is used to enable consideration of all possible scenarios and causes generated by a team of experts. The information is organized in either a fishbone or sometimes a tree diagram (below) 162 ISHIKAWA – FISHBONE DIAGRAMS Identify the problem to be solved as the fish head, the main bones of the fish represent the main categories under which problems might fall. The team brainstorms each category to identify potential causes and sub causes and factors which affect the risk. 163 BOW TIE ANALYSIS Bow tie analysis combines a fault tree and an event tree . The fault tree investigates the cause of the problem, the event tree the consequences and the bow tie focuses on the barriers to threats. Light Projector Failure Lecture proceeds Preventative maintenance Setup error Lecturer Fixes Training Power cut Ventilation Projector Failure Lecture delayed Back up projector Globe failure Hard copy Preventative maintenance Training Accidentally unplug Risk source/Cause Design Tape down cable Lecture Cancelled 164 Controls Risk Event Controls Consequences LAYER OF PROTECTION (LOPA) Layer of Protection Analysis (LOPA) LOPA is a semi-quantitative technique for analysing the effectiveness of controls. It considers the different layers of controls along the time line of risk from the initiating event to response and recovery. An initiating event and a consequence pair is selected. The possible controls which could be put in place for the particular cause consequence pair and layer of protection from the diagram below are then identified. 165 INDEPENDENT PROTECTIVE LAYER (IPL) An IPL is a device system or action that is capable of preventing a scenario proceeding to its undesired consequence independent of the initiating event or any other layer of protection associated with the scenario. The IPL must be: Effective in preventing consequences if functions as designed Independent of Initiating event and of other IPLs already included The effectiveness of an IPL must be auditable Safeguards which are not IPLs: × Training × Procedures × Normal testing and inspection × Maintenance × Communications × Signs × Information These are considered normal conditions not preventative measures They are also common mode failures ie not independent 166 COMPARISON BETWEEN LOPA AND EVENT TREE ANALYSIS IPL1 IPL2 IPL3 Consequence Occurs (eg casualties) Fire Springer Alarm Evacuation Success Safe Outcome Initiating Event Success Failure Undesired but tolerable outcome Success Undesired but tolerable outcome Failure Failure Consequence exceeding criteria 167 QUANTIFICATION OF LOPA LOPA estimates the likelihood of the undesired consequence by multiplying the frequency of the initiating event by the product of the PDFs (Probability of Failure on Demand) for the applicable IPLs. Frequency of consequences = Frequency of initiating event x the Probability of Failure on Demand of each IPL C I J fi = fi × I IPFDij f=1 C I (fi = fi × PFDi1 × PFDi2 ×…. × PFDiJ) Where fiC = frequency for consequence C for initiating event i fiI = initiating event frequency for initiating event i PFDij = probability of failure on demand of the jth IPL that protects against consequence C for initiating event i 168 EXAMPLE QUANTIFICATION OF LOPA IPL1 IPL2 IPL3 Consequence Occurs (eg casualties) Fire 10-3 Springer Alarm 10-2 10-1 Evacuation 10-1 Frequency of Protection Barriers Failure Frequency of Occurrence C I fi = fi × PFDi1 × PFDi2 ×…. × PFDiJ Frequency of Fire with Casualties = 10-3× 10-2 × 10-1 × 10-1 = 10-7 (one in ten million chance) 169 9. RISK ANALYSIS AND DECISIONS 170 RISK MANAGEMENT vs DECISION MAKING • Establishing Context • • • • • • • Identify Risks Analyse Risks Decide Acceptability Evaluate Alternatives Decide Treatment Implement Treatment Monitor • • • • Explore Backgrounds Define Problem Identify Issues Analyse Issues • • • • Evaluate Alternatives Make Decision Implement Decision Check It Works 171 DIFFERENT DECISIONS NEED DIFFERENT TYPE OF ANALYSIS Decisions involving risk are not necessarily made on the basis of a level of a risk DECISION Deciding whether treatment is required ANALYSIS & EVALUATION METHOD Define criteria for when risk can be accepted and compare the level of risk with these criteria Deciding whether controls Assess controls against a standard or analyse are good enough the level of risk with existing controls and compare this risk with defined criteria Deciding how to treat a risk Analyse risk cause (causal factor), the way event can be prevented or modified and the ways consequences can be reduced Deciding priorities – which to treat first Use a rating tools Deciding between options Weigh positive and negative risks and incorporate this into normal cost benefit analysis 172 DECISION TREE ANALYSIS A decision tree is similar to an event tree but rather than considering only chance events, both events and decisions are included in the analysis. Decision nodes an a decision tree are indicated by rectangles and chance events by circles. Below is a decision tree whether to proceed with a development project. $23m High demand $55m 0.55 Medium $33m $43m $21m Low demand $15m $3m -$2m 0 173 MULTI-ATTRIBUTE UTILITY THEORY (MAUT) MAUT combines dissimilar measures of costs and benefits, along with individual stakeholder preferences, by calculating a value for each attribute on a common scale from 0 (worst) to 1 (best). All attributes are weighted subjectively but are defined to add up to 1. Example below showed that Option B is preferred. Attribute Option Option Option Weight Cost A 0 B 0.3 C 1 Reliability 1 0.6 0 0.25 0.6 1 0 0.30 1 0 0.5 0.20 0.45 1.0 Safety Performance Total Score 2.25 2.45 0.25 174 And Finally The greatest risk of all is to take no risk at all! The End Questions? 175