Cyber-ops as `armed attack`
advertisement

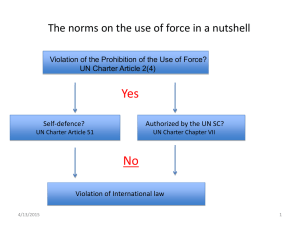
CYBER-WARFARE FROM THE PERSPECTIVE OF INTERNATIONAL LAW Vasileios Makris, Hellenic MoD, Mil. Justice Directorate Mil. Judge Grade B’ 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 1 Definitions: • • • • “Information Operations” “Information Warfare” Cyber-Warfare Computer Network Attacks – CNAs: they may be cyber-warfare or just ‘’info ops’’. “cyber-warfare” /”cyber-operations” (cyber-ops), in the context of jus ad bellum 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 2 The computer /computer network as a WEAPON: Most used methods /techniques: • Corruption of hardware (by chip-level actions – “chipping”) • Corruption of software : • Denial of Service (DoS) & Distributed DoS (DDoS) attacks • Trojans, viruses, worms, time & logic bombs, etc • Various combinations of the above 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 3 The prohibition of the use of inter-State force • International customary law • The Charter of the United Nations Nowadays there are only two cases in which international law permits the use of inter-State force: (a) collective security (art. 39 et seq. of the UN Charter) and (b) self-defence (art. 51). 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 4 UN Charter, art. 2(4) “All Members shall refrain in their international relations from the threat or use of force against the territorial integrity or political independence of any state, or in any other manner inconsistent with the Purposes of the United Nations.” 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 5 UN Charter, art. 39 “The Security Council shall determine the existence of any threat to the peace, breach of the peace, or act of aggression and shall make recommendations, or decide what measures shall be taken in accordance with Articles 4 and 42, to maintain or restore international peace and security.” 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 6 UN Charter, art. 51 “Nothing in the present Charter shall impair the inherent right of individual or collective self-defence if an armed attack occurs against a Member of the UN, until the Security Council has taken measures necessary to maintain international peace and security. …” 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 7 The purpose of the presentation: To provide answers to the following questions: • ?-When cyber-ops constitute use of force outlawed by art. 2(4) of the Charter. • ?-When cyber-ops constitute threat to the peace, breach of the peace or act of aggression (art. 39 of the Charter). • ?-When cyber-ops amount to armed attack against which a state can recourse to selfdefence (art. 51 of the Charter). 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 8 The purpose of the presentation: • We will not examine cyber-ops from the perspective of jus in bello • We will not examine “cyber-crime”, ‘’cyberespionage”, “cyber-sabotage” etc. • We will not look into cases like Stuxnet either (isolated /small scale). The threshold of CYBER-FORCE (cyber-warfare) between states is higher… 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 9 ΝΑΤΟ Strategic Concept, 2010 US National Security Strategy, 2010 [The Heads of State and Government of the NATO nations will] “…develop further our ability to prevent, detect, defend against and recover from cyber-attacks,…” Cyber-security threats: “…one of the most serious national security, public safety and economic challenges we face as a nation”. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 10 United Nations A series of General Assembly Resolutions… World Summit on the Information Society (Geneva 2003, Tunis 2005). 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 11 Real life cases … 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 12 Estonia 2007 • From 27 Apr. 2007 and for 3 weeks Estonia was victimized by massive computer network attacks (: mainly DoS and DDos attacks, defacement of websites, attacks against DNS servers etc). • All government websites went down (the PM’s office incl.), to be followed by the websites of newspapers, TV stations, banks, public utilities etc. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 13 Estonia 2007 • The same fate was shared by the websites of the Parliament, hospitals, newspapers, electronic media, ISPs, universities, the telephone network etc. • It is estimated that over 1.000.000 computers were used against Estonia (a number of them from within Estonia itself), linked with the technique of “botnets”… [= ro(bot) computer (net)works] 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 14 Estonia 2007 • Estonian officials claimed that their country was the victim of a new kind of war and named specific sources as the attackers. • Estonia, as a NATO member-country, asked for help by the Organization. • NATO did not find any grounds to implement the provisions of art.V of the NATO Charter. It just sent experts on the spot… 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 15 Georgia 2008 • On Aug. 9, 2008 Georgia invaded the semiautonomous S. Osetia. The Russian Federation responded with arms. • At the same time Georgia became the target of systematic and extended cyber-attacks (DDoS, defacement, malicious software distribution, etc). • The first phase of these attacks is believed to have started on 19 July, 2008! (two weeks earlier!!) 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 16 A bizarre incident… • Mumbai, India, Nov. 2008: Terrorist organization Lashkar-e-Taiba (LeT), allegedly based in Pakistan: attacks against luxurious hotels -- over 500 casualties (179 dead) -- VoIP technology with the call server located in the US(!) -- 60 GPS devices -- Google Earth maps, etc… 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 17 Cyber-warfare as a use of force under art. 2(4) of the Charter 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 18 Cyber-warfare as a use of force under art. 2(4) of the Charter • It is generally accepted that the prohibition of the threat /use of force represents customary international law (also). • It binds all States, regardless of membership in the UN. However, at the time of drafting of the Charter, cyber-ops simply did not exist and could not even be contemplated upon. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 19 Cyber-warfare as a use of force under art. 2(4) of the Charter • The prohibition of art. 2(4) is framed in terms of the instrument of coercion employed: force (the drafters meant military and ‘kinetic’ force). That was something absolutely logical and presumable for the 1940s… • Yet, what matters for States are the consequences suffered by the use of a weapon or anything that can be used as such! 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 20 Cyber-warfare as a use of force under art. 2(4) of the Charter • Cyber-ops are ‘non-forceful’, that is nonkinetic… • Yet, computers /networks can be used with hostile intent as WEAPONS and their consequences can range from mere annoyance to death and severe property damages. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 21 Cyber-warfare as a use of force under art. 2(4) of the Charter • Given the above fact and also that, for example, there is no doubt that biological or radiological or chemical modes of warfare, which are also ‘non-kinetic’, are accepted to constitute, nevertheless, ‘uses of force’… 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 22 Cyber-warfare as a use of force under art. 2(4) of the Charter • Many analysts are beginning to accept that cyber-ops that directly cause death and /or property damages may constitute use of force! • The above mentioned do not apply to cyber-ops which cause economic and /or political consequences only, irrespective of how severe they may be. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 23 Cyber-warfare as a use of force under art. 2(4) of the Charter • The International Court of Justice (ICJ) accepts that art. 2(4), 42 and 51 of the Charter do NOT refer to specific weapons. • They apply to any use of force, regardless of the weapon employed (Nuclear Weapons Advisory Opinion, 1996) • The ICJ has also recognized that the use of nonkinetic weapons can lead to a violation of art. 2(4) (Nicaragua case, 1986, arming & training of the contras). 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 24 Cyber-warfare as a use of force under art. 2(4) of the Charter For cyber attacks that do not cause death /property damage directly, prof. Schmitt proposed seven criteria in 1999 to help determine a possible use of force. The seven ‘Schmitt criteria’: • Severity • Immediacy • Directness • Invasiveness 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 25 Cyber-warfare as a use of force under art. 2(4) of the Charter ( cont.) ‘Schmitt criteria’: • Measurability • Presumptive legitimacy (for example, cyber espionage, cyber propaganda or psychological ops are legal by int. law) • Responsibility (: causal nexus to some state). [Not all theorists accept the above criteria] 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 26 Cyber-warfare as a use of force under art. 2(4) of the Charter • Art. 2(4) is binding upon states. • Not upon individual persons (e.g. ‘patriotic hackers’) or other “non-state actors”, like groups, terrorist (or other) organizations, organized hacker groups etc. • Unless… 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 27 Cyber-warfare as a use of force under art. 2(4) of the Charter Unless … • (ICJ, “Nicaragua Case”, 1986): “effective control”. • (ITFY, Appeals Chamber, “Tadić Case”, 1999): “overall control”. • ICJ, “Congo vs Uganda”, 2005, “Bosnia & Herzegovina vs Serbia & Montenegro”, 2007: “effective control” yet again. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 28 Cyber-warfare as a use of force under art. 2(4) of the Charter • The same apply to cyber-ops. The “effective control’’ criterion is more suitable to cyber-ops (and safer) because their origin is very hard and time consuming to locate. Note also that: even if a conduct is not directly attributable to a state it will nevertheless be considered an act of that state if : • The state acknowledges and adopts cyber-ops conducted by some non-state actor. • Possesses concrete information that cyber attacks emanate from its territory and does nothing to stop them. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 29 Remedies against cyber-attacks: (Assuming that the victim-state is able to identify the origin of cyber-force and attribute the conduct to a state) • • • • Resort to the UN Security Council (S.C.) Resort to a competent International Tribunal. Adopt retortions. Ask for some kind of reparation according to international law (: satisfaction, restitution, compensation). • Resort to non-forceful countermeasures. • Use armed force in self-defence if the criteria of art. 51 of the Charter are fulfilled. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 30 Cyber-warfare as threat to the peace, breach of the peace or act of aggression (art. 39) 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 31 Cyber-warfare as threat to the peace, breach of the peace or act of aggression • The assessment of the situation rests with the S.C. of the U.N. • The S.C. uses mainly POLITICAL criteria. • A cyber-attack may be judged to fit into one of the three above cases, irrespective of its scale and effects. • The S.C. --as a response to such a situation-may decide measures not involving or involving the use of force (art. 41 and 42). 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 32 Cyber-ops as ‘armed attack’ justifying self-defence (art. 51 of the UN Charter) 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 33 Cyber-ops as ‘armed attack’ justifying self-defence The scope of self-defence as a right: • Self-defence (individual or collective) is only permitted against “armed attack”. • Every armed attack is, at the same time, a use of force. The opposite is not always true. • No prior authorization from the S.C. is required in order for a state to exercise self-defence ! 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 34 Cyber-ops as ‘armed attack’ justifying self-defence The scope of self-defence as a right: • Only the victim-state may judge that it is under an armed attack. • The victim-state must first ask for help. Only after this may third states offer their help (: collective self-defence). • Three principles apply: necessity, proportionality, immediacy. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 35 Cyber-ops as ‘armed attack’ justifying self-defence The scope of self-defence as a right: All the above are especially crucial in the context of cyber-ops, because it is very difficult and time-consuming to locate the source of a cyber-attack and, at the same time, “bleed-over” effects might be caused, which make it even harder and time consuming to locate the perpetrator! 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 36 Cyber-ops as ‘armed attack’ justifying self-defence • The drafters of the Charter used the “instrument-based” approach to the issue of self-defence also (: the Charter requires prior ‘’armed attack’’). • The phrase “armed attack” is more restrictive than the phrase “use of force” (something more is needed in order to have “armed attack” and not mere “force”). 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 37 Cyber-ops as ‘armed attack’ justifying self-defence • Nevertheless, the hard core of an armed attack is the infliction of death to persons and severe property damages. • It is neither the designation of a device, nor its normal use, which make it a WEAPON, but the intent with which it is used and its effect. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 38 Cyber-ops as ‘armed attack’ justifying self-defence • Thus, many analysts are starting to accept that an armed attack does not have to be conducted the classic military way at all times provided that its consequences are analogous to those caused by ordinary military force. • If the above is not the case, then a cyber-attack, irrespective of its scale, can not be judged as an “armed attack” justifying self-defence. Of course, it may constitute an instance of mere “use of force”… 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 39 Cyber-ops as ‘armed attack’ justifying self-defence • The mere destruction, corruption or disruption etc of data (in computers, networks etc) is not enough, no matter how widespread it may be. • It must be accompanied by “physical consequences” (: death /physical damages to persons /property). 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 40 Cyber-ops as ‘armed attack’ justifying self-defence • This legal structure is not entirely satisfactory… • Yet it is the only one we have and as far as modern international law has gone up to this date… 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 41 … don’t forget that: • International law is not necessarily a “just” and equitable law in all its aspects. • “International law is the law that the wicked are unwilling to enforce and the weak and righteous are unable to enforce”! 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 42 Cyber-ops as ‘armed attack’ justifying self-defence • The ‘’threshold’’ of armed attack is not prescribed in any legal text or rule. The ICJ alluded to it in the “Nicaragua Case” (: most grave forms of the use of force vs less grave forms). • In the “Oil Platforms Case” (Iran vs US, 2003), the ICJ accepted that the attack with sea mines against one ship could constitute armed attack justifying self-defence. • The same can apply to computer network attacks /cyber attacks. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 43 Cyber-ops as ‘armed attack’ justifying self-defence • In a fashion analogous to --e.g., isolated border incidents-- a cyber-attack may be judged as a “non-armed attack”, if it causes death /damages but not of a “significant scale”… (it will constitute “force” though). 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 44 Cyber-ops as ‘armed attack’ justifying self-defence • Cyber-ops that are part of military ops of the classic type or constitute the initial stage thereof, are less problematic (e.g. Georgia, 2008). • The same apply to cyber-ops that are part of a legitimate military response to the use of (military – kinetic) force (armed attack). 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 45 Cyber-ops as ‘armed attack’ justifying self-defence ?-When a cyber-attack by “non-state actors” can be attributed to a state? • ICJ /ITFY criteria: “effective control” -“overall control”. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 46 What will come next? • ?-Will an ad hoc new rule of customary international law develop to prohibit cyberattacks as “illegal” use of force? • ?-Will, perhaps, a new treaty be drafted? 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 47 What will come next? • Cyber-warfare is a reality and cyber-attacks are as old as computer networks themselves (at least 30 years old). • Recent state practice so far (USA, UK, Russian Federation, NATO, etc) shows that a new int. customary law is in the process of crystallization. The outcome is still difficult to predict. • The need for an int. treaty prohibiting the use of cyber-force is also in debate. Many states, though, still hesitate to commit themselves to specific restrictions. 02 June, ''ATHENA '11'' Mil.J. Gr.B' V.G. Makris 48