Pentium Architecture
advertisement
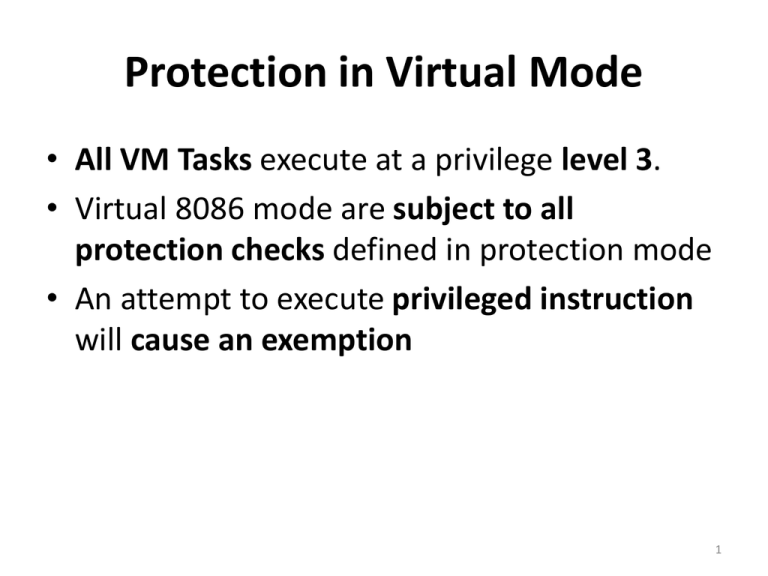
Protection in Virtual Mode • All VM Tasks execute at a privilege level 3. • Virtual 8086 mode are subject to all protection checks defined in protection mode • An attempt to execute privileged instruction will cause an exemption 1 Structure of a V86 Task • A V-86 task consists – Partly of 8086 program – Partly of 80386 code that serves as the VM (Virtual Machine)monitor (80386 protected mode code (PL=0) with initialization and exception handling procedures) • To run in V86 mode, 8086 program needs: – A V-86 monitor – Operating System Services 2 Entering and Leaving V86 Mode • The processor can enter V86 by two means: • Case 1: – A task switch to an 80386 task loads the image of EFLAGS from the new TSS. – The TSS of the new task contains the VM flag – VM = 1 of the new EFLAGS indicates that the new task is executing 8086 instructions and therefore the segment registers from the TSS forms base addresses as 8086 would. 3 Entering and Leaving V86 Mode • Case 2: – An IRET from a procedure of an 80386 task loads the image of EFLAGS from the stack – VM = 1 indicates that the procedure to which control is being returned is an 8086 procedure – CPL at the time IRET is executed must be zero, else the processor does not change VM. 4 5 Entering and Leaving V86 Mode • The processor leaves V86 mode when an interrupt or exception occurs. • Case 1: – The interrupt or exception causes a task switch which loads EFLAGS from the TSS of the new task. – If the new TSS is an 80386 TSS and VM bit is 0 in the EFLAGS, then the processor • clears the VM bit of EFLAGS • loads the segment registers from the new TSS and • begins executing the instructions of the new task according to 80386 protected-mode semantics. 6 Entering and Leaving V86 Mode • Case 2: – The interrupt or exception vectors to a privilegelevel zero procedure. – The processor stores the current setting of EFLAGS on the stack, then clears the VM bit. – The interrupt or exception handler, therefore, executes as 80386 protected-mode code 7 8 Chapter 3 P5 Micro architecture : Intel’s Fifth generation Features of Pentium • Introduced in 1993 with clock frequency ranging from 60 to 66 MHz • The primary changes in Pentium Processor were: – – – – – – – Superscalar Architecture Dynamic Branch Prediction Pipelined Floating-Point Unit Separate 8K Code and Data Caches Writeback MESI Protocol in the Data Cache 64-Bit Data Bus Bus Cycle Pipelining Pentium Architecture UQ: Explain with block diagram how superscalar operation is carried out in Pentium Processor UQ:Draw and explain Pentium Processor architecture . Highlight architectural features Pentium Architecture • It has data bus of 64 bit and address bus of 32-bit • There are two separate 8kB caches – one for code and one for data. • Each cache has a separate address translation TLB which translates linear addresses to physical. • Code Cache: – 2 way set associative cache – 256 lines b/w code cache and prefetch buffer, permitting prefetching of 32 bytes (256/8) of instructions Pentium Architecture • Prefetch Buffers: – Four prefetch buffers within the processor works as two independent pairs. • When instructions are prefetched from cache, they are placed into one set of prefetch buffers. • The other set is used as when a branch operation is predicted. – Prefetch buffer sends a pair of instructions to instruction decoder Pentium Architecture • Instruction Decode Unit: – It occurs in two stages – Decode1 (D1) and Decode2(D2) – D1 checks whether instructions can be paired – D2 calculates the address of memory resident operands Pentium Architecture • Control Unit : – This unit interprets the instruction word and microcode entry point fed to it by Instruction Decode Unit – It handles exceptions, breakpoints and interrupts. – It controls the integer pipelines and floating point sequences • Microcode ROM : – Stores microcode sequences Pentium Architecture • Arithmetic/Logic Units (ALUs) : – There are two parallel integer instruction pipelines: u-pipeline and v-pipeline – The u-pipeline has a barrel shifter – The two ALUs perform the arithmetic and logical operations specified by their instructions in their respective pipeline