Chris McAuley
advertisement

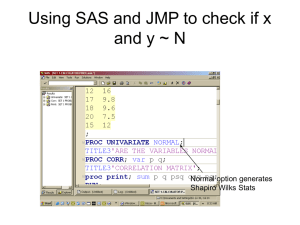
DATA ANALYTICS IN FRAUD PREVENTION DURBAN, AUG 24TH 2014 Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. AGENDA 1. 2. 3. 4. 5. Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. Introductions General Concepts around Fraud ,Waste, and Abuse Overview of the SFF Screenshots Questions/Discussion INTRODUCTIONS Chris McAuley, Director, Security & Intelligence Practice Chris.McAuley@SAS.com +44 7747 100189 (m) Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. GENERAL CONCEPTS ON FWA Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. HEALTHCARE FRAUD: WHO HAS THIS PROBLEM? Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. HEALTHCARE FRAUD: HOW BIG IS THE PROBLEM? “…potential losses to healthcare fraud and corruption between €30-100 billion across Europe” “…estimates conservatively that $68 billion (3%) is fraud” “…approximately €180 billion euros or 6 percent of global health care spending is lost to fraud each year” Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. HEALTHCARE FRAUD: WAIT…THERE’S MORE?? Fraud Abuse? Waste? Corruption? Estimates of 20% – 30% total FWAC in health care Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. HEALTHCARE FWA: SO THESE ARE DIFFERENT, RIGHT? Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. Fraud Abuse Waste Corruption FRAUD, WASTE, & ABUSE A CONTINUUM Waste Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. Abuse Fraud FRAUD, WASTE, & ABUSE NEFARIOUSNESS SCALE Abuse Waste Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. TM Fraud FRAUD, WASTE, & ABUSE HOWEVER, IN TERMS OF [€£$] TO THE SYSTEM… Abuse Fraud Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. Waste FRAUD, WASTE, & ABUSE WE NEED TO FOCUS ON ALL OF IT Waste Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. Abuse Fraud COMBATING FWA: HOW DO WE DEAL WITH IT? Sometimes prosecutions are in order: • Criminal organizations • Doctors committing true fraud • Grievously offending doctors • In other words – for Fraud What if companies do not want to prosecute? • Bad PR • Bad for customer retention • Legal action not possible • What do they do about waste and abuse? • Want to develop alternative strategies for identifying and dealing with doctors who are engaging in aberrant behavior (as opposed to fraud) Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. COMPREHENSIVE COST-CONTAINMENT STRATEGY Provider FWA Adherence to Guidelines Quality of Care Hospital FWA Cost Containment Member FWA Contract Negotiation Policy Modification Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. Pharmacy FWA EXAMPLES: PROVIDER FRAUD AND ABUSE Overutilization Billing for services not medically warranted, to receive insurance payments, or falsifying diagnosis to justify medically unnecessary procedures. Upcoding Using a code for a more expensive treatment than what was performed. False Claims Billing for services not performed or supplies not provided. Unbundling Improper submission of separate claims for services that should be combined under a global fee. Billing for Non-Covered Treatments Billing for non-covered treatment as though they were covered treatment (e.g. experimental not covered by insurance plan). Fraudulent Dates of Service Falsifying the date to avoid contract limitations on eligibility or payment maximums. Waiver of Co-pay Waiving coinsurance or deductible to accept insurance as payment in full, and then inflating charges to insurer. Free Medical Service Free service to patient, then billed to insurer, to entice ongoing other treatments. Kickbacks Providers receiving cash payments in exchange for driving business to certain ancillary providers (e.g. labs). Phantom Providers Unlicensed providers posing as physicians. Misrepresenting Medical Records Falsifying the medical records to justify services that were not provided or not warranted. Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. EXAMPLES: MEMBER FRAUD False Claims Patient misrepresents services and submits false claims for reimbursement. Collusion Patient and provider collude to submit false claims, typically with provider returning portion of reimbursement to patient for cooperation. Speculation Patient has multiple individual health insurance policies without revealing other coverage and collects on all. Application Fraud Misrepresentation of material statements on application for insurance in order to obtain coverage that would be denied or modified. Identity Theft Member has SSN or Benefits ID stolen for purposes of someone else receiving insurance benefits, or sells or “rents” their ID to another for an access fee. Disability Fraud Patient misrepresents the nature or extent of a disability or misrepresents loss of income to obtain higher benefits. Doctor Shopping Member keeps looks to many doctors for the same services (often narcotics) Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. EXAMPLES: WASTE Using brand name drugs when an alternative generic is available Using a second line drug when a first line drug is indicated Consistently selecting a surgical option when non-surgical options are available and effective Preventative prescription of a drug when not indicated Using high intensity diagnostic tools when a lower intensity tool is available Over-utilization of laboratory testing when it is not necessary Under-utilization of laboratory testing leading to disease progression Under-treatment of a disease early in onset leading to more severe disease Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. NOT JUST DOCTORS Radiological Centers Infusion Centers Nursing Homes Doctors Dialysis Centers Chiropractors Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. Transportation Services Personal Care Assistants Optometrists Hospitals Medical Equipment Suppliers Pharmacies Home Health Care Adult Foster Care Substance Abuse Clinics Podiatrists Dentists Laboratories OVERVIEW OF THE SFF Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SAS FRAUD END-TO-END SOLUTION FOR HEALTH INSURANCE FRAMEWORK Data It’s all in the prep • Structured & unstructured data Sources • Batch or real time processing • Data cleansing • Data integration • Advanced network linking • Text mining Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. Detection Unique hybrid approach • Business rules • Anomaly detection • Predictive models • Text mining • Database searches • Social network analysis Investigation Taking action • Layered alert ranking • Tailored workflow • Easy to use web based interface • Advanced query of integrated data • Claim system integration • Case management integration Management Self administered • Alert suppression • Modification of rules • Model management • Champion challenger • Alert queue management • Workflow analysis • MI reporting SAS FRAUD UNIQUE HYBRID APPROACH TO ANALYTICS FRAMEWORK Anomaly detection (example): Providers that have volumes or intensity far above their peers Predictive modelling (example): Number of previous investigations on the network may be input to the predictive model of a suspicious claim Text mining (example): Harnessing call center data Database Text Searches Mining Predictive Modeling Anomaly Detection Business rule (example): A claim is suspicious if it is submitted for a person of the wrong gender Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. Automated Business Rules Analytic Decisioning Engine Database Searches (example): Looking for matches across the lists of sanctioned providers or death master files Social Network Analysis SNA (example): Looking for a number of similar connected actors INDUSTRY BEST PRACTICE USING HYBRID ANALYTICS FOR FRAUD DETECTION Enterprise Data Employer Medical Data Procedure Claims Provider / Member Known Bad Lists For known patterns For unknown patterns For complex patterns Rules Anomaly Detection Predictive Models Rules to surface known fraud behaviors Algorithms to surface unusual (out-of-band) behaviors Examples: • Inaccurate eligibility information Referral • Daily provider billing exceeds possible 3rd Party Data • CPT up-coding • Value of charges for procedure exceeds threshold For unstructured data Network Analysis Text Mining Identify attributes of known fraud behavior Associative discovery thru automated link analysis Leverage unstructured data elements in analytics Examples: Examples: Examples: Examples: • Abnormal service volume compared to similar providers • Like patterns of claims as confirmed known fraud • Provider/claimant associated to known fraud • Claim/call center notes high-lighting key fraud risks (e.g., policy questions) Payments • Unlicensed or Suspended Provider For associative linking • Ratio of $ / procedure exceed norm • # patients from outside surrounding area exceeds norm • Provider behavior similar to known fraud cases • Like provider/ network growth rate (velocity) • Linked members with like suspicious behaviors • Suspicious referrals to linked providers • Collusive network of providers & referrals • Static data elements (e.g., address) used for linking suspicious activity • Integration of rich case file information Hybrid Approach Proactively applies combination of all approaches at entity and network levels Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. INDUSTRY BEST PRACTICE USING HYBRID ANALYTICS FOR FRAUD DETECTION Internationally Developed IP Rules Employer Medical Data Procedure Claims Provider / Member Known Bad Lists Network Analysis Text Mining Identify attributes of known fraud behavior Associative discovery thru automated link analysis Leverage unstructured data elements in analytics Examples: Examples: Examples: Examples: • Abnormal service volume compared to similar providers • Like patterns of claims as confirmed known fraud • Provider/claimant associated to known fraud • Claim/call center notes high-lighting key fraud risks (e.g., policy questions) Anomaly Detection Predictive Models Rules to surface known fraud behaviors Algorithms to surface unusual (out-of-band) behaviors Examples: • Inaccurate eligibility information Payments Referral • Unlicensed or Suspended Provider • Daily provider billing exceeds possible 3rd Party Data • CPT up-coding • Value of charges for procedure exceeds threshold • Ratio of $ / procedure exceed norm • # patients from outside surrounding area exceeds norm • Provider behavior similar to known fraud cases • Like provider/ network growth rate (velocity) • Linked members with like suspicious behaviors • Suspicious referrals to linked providers • Collusive network of providers & referrals • Static data elements (e.g., address) used for linking suspicious activity • Integration of rich case file information Hybrid Approach Proactively applies combination of all approaches at entity and network levels Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SAS FRAUD EFFICACY AND THE HYBRID APPROACH FRAMEWORK FRAUD Additional variables further this benefit even more Analytics enhance fraud detection, improving the accuracy as well as finding cases near impossible in a manual process If you examine 50% of the population, you would expect to find 50% of the fraud █ Advanced analytics via Hybrid █ Advanced analytics without Hybrid █ RANDOM POPULATION If the accuracy of detection doubles by using a hybrid approach, an investigation team would be able to find twice the amount of fraud with the same number of referrals! Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SAS FRAUD IMPROVED IDENTIFICATION, QUALITY, AND EFFICIENCY FRAMEWORK Detection Investigation Capability Enhanced scoring model with network attributes and scores incorporated Visual representation of data from multiple systems in one single environment Outcome Increase in volume & quality of fraud detected Increased efficiency during fraud investigations Benefit Increased fraud saving Improved operational saving Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SAS FRAUD OUR APPROACH FRAMEWORK Operational Sources Policies Data Management Alert Generation Fraud Detection Alert Management & Reporting Ingest GUI for selfadministration Cleansing Enrichment Claims Investigations Investigations Quality analysis Entity resolution Social networks generation Intelligence Repository Potential Fraud Risk Suspicious alerts for Investigation Watch-lists Additional sources Intelligence updates Data updates Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. Case Management Actions taken SCREENSHOTS? Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SFF SCREENSHOTS – ALERTS VIEW Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SFF SCREENSHOTS – DRILL INTO ALERT Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SFF SCREENSHOTS – DRILL INTO ALERT Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SFF SCREENSHOTS – SNA Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SFF SCREENSHOTS – SNA Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SFF SCREENSHOTS – SNA Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SFF SCREENSHOTS – SNA Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SFF SCREENSHOTS – SNA Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SFF SCREENSHOTS – DASHBOARDS Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SFF SCREENSHOTS – DASHBOARDS Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. SFF SCREENSHOTS – ALERT VIEW Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed. QUESTIONS? Cop yrig ht © 2012, SAS Institute Inc. All rig hts reserv ed.