WCMSRiskManagement
advertisement

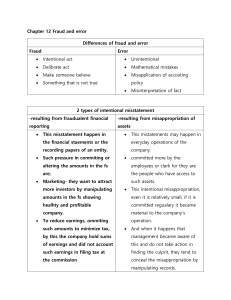
Notes provided by: Deonna Grimes Every risk management program should have the following components: Risk Identification (where are the risks?) Risk Measurement (how bad is it?) Risk Control (mitigating factors) Risk Monitoring (systematically review to ensure key components have not changed) Creating an ERM program can be difficult. An effective program requires cooperation from everyone in the organization Key players in an ERM program include: Board of Directors and CEO (have ultimate responsibility for ERM) Senior Management (likely have the biggest roles) Department/Business Units Support Functions Internal Audit and Compliance Risk Management (if resources allow) Determine and document risk appetite. This is the credit union’s chance to strategically establish its risk tolerance (i.e. the capacity to take risk and tolerance for potential loss).. Although certain tasks may be delegated to management, the Board and CEO are ultimately responsible for all of the risk in the organization Categories of Risk: Credit Risk Interest Rate Risk Liquidity Risk Transaction Risk Compliance Risk Strategic/Reputation Risk Fraud risk Transaction Risk Risk to Earnings and Capital Arises from a Credit Union’s Inability to deliver products or services, maintain a competitive position, and manage information This type of risk is usually the result of: - Fraud and errors - A function of internal controls, operating processes, information systems, and employee integrity Two Primary Types of Internal Fraud 1. Financial Misstatement—financial reporting fraud. Recent economic conditions have resulted in a “spike” 2. Embezzlement—can have direct and indirect consequence Formula Motive Opportunity—one thing we can control. Credit unions can minimize opportunity through controls Rationalization The credit union made it too easy for the perpetrator. Increased opportunity through: Lack of supervision Lending committee approval is a sham (nothing but a rubber stamp) Ineffective controls—loan reports are not validated Separate data system was not integrated into the credit union’s controls Opportunity presented itself when the two tellers shared their codes, and keys. Mitigation Strategy Enforce segregation and password controls Periodic “full” audits with proper timing Training and education