Document
advertisement

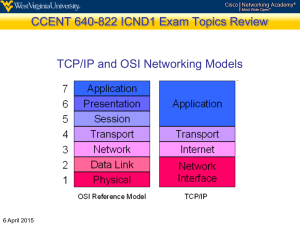
DCN286 INTRODUCTION TO DATA COMMUNICATION TECHNOLOGY Network Fundamentals Network hardware/software Network hardware: NIC on the computer Hub/switch/router Cables (or wireless router/NIC) Patch panel and cable jacks Network Software: Protocols Application software programs Network Standard Organizations Abbreviation ISO IETF IEEE ANSI TIA EIA ITU Full Name International Organization for Standardization Internet Engineering Task Force Institute of Electrical and Electronic Engineers American National Standards Institute Telecommunications Industry Association Electronic Industries Alliance International Telecommunications Union Cisco IBM Products Symbols Cisco LAN Symbols More Cisco Icons Cisco People Icons Cisco WAN Icons Cisco Building Icons Network Topologies Bus Star Ring Mesh Network Topology Ethernet Ethernet is a family of frame-based computer networking technologies for local area networks (LANs). The name comes from the physical concept of the ether. Old Ethernet 10Base2 and 10Base5 Use Coaxial cable (TV cable) 10 means 10mbps BASE means baseband 2 or 5 means 200m / 500m length limit Bus topology 10BASET The 10Base-T standard (also called Twisted Pair Ethernet) uses a twisted-pair cable with maximum lengths of 100 meters. The cable is thinner and more flexible than the coaxial cable used for the 10Base-2 or 10Base-5 standards. Its bandwidth is as same as 10base2 or 10 base5. But, it is using different connector, RJ45. It also use STAR topology. 100BASE-TX 10BASE-T and 100BASE-TX only require two pairs to operate, pins 1 and 2 (transmit or TX), and pins 3 and 6 (receive or RX). The cabling length limit is 100 meter. 1000BASET (gigabit) All connection cables must be qualified to 1000mbps. All switches, equipment NICs and connectors must be qualified to 1000mbps. Ethernet Cabling Repeater 10base5 – 500meter cable length limit; 10base2 - 200meter cable length limit; 10BaseT - 100meter cable length limit; Repeater is to amplify signal and extend the cabling distance. Working in layer 1 (Physical) of TCP/IP model Hub Central connection of Ethernet LAN. Physically Star topology and could be logically RING, Bus and/or Star May have built-in repeater Working in layer 1 (Physical) of TCP/IP model Ethernet Bridge Intelligent device to forward frame according to destination Media Access Control (MAC) address Forwarding: If the destination MAC address has a port different to the originate port, the frame will be sent. Filtering: If the destination MAC address is reachable with the same interface when it arrived, the frame will be discarded. Working in layer 2 (Data Link) of TCP/IP model Switch Think switch as a hub with bridge functioning on each port (interface): 1. Switch will offer central connection to all hosts. 2. Switch will only forward frame according to destination MAC address on per-port base. 3. Will regenerate signals (repeater function) 4. Most switches are working in layer 2 (Data Link) of TCP/IP model. Router Redirect packets according to destination logical address (IP address). Can build routing path between different network segments (subnets) Can act as firewall Can work as VPN (server) connection Working in layer 3 (Network) of TCP/IP model LAN (Local Area Network) Has physical high speed connections in the network. Usually in the same office building. Private owned network. May contain one to hundreds computers Local-area Networks (LANs) WAN (Wide Area Network) Connected by more than one LANs. Connection could be dedicated line, lease line and / or other remote connections: Modem (dial up) 56Kbps over analog phone line. ISDN (Integrated Services Digital Network) 128Kbps DSL (Digital Subscriber Line): over digital phone line such as Bell Sympatico Frame Relay T1, T3, E1 or E3 lease line SONET (Synchronous Optical Network): using Optical Carrier (OC) Wide-area Networks (WANs) VPN (Virtual Private Network) VPN is a kind of encryption tunnel built based on internet connection. It could be: Site-to-Site (two locations of same or different organizations connection) Point-to-Site (for travelers) VPN must have three components working together: VPN server, VPN client and VPN protocol such as L2TP and PPTP. MAN and SAN MAN (Metropolitan-Area-Network) is between LAN and WAN. SAN (Store-Area-Network) is for performance (load balance), availability and scalability. The server farm is a typical example of SAN. Bandwidth Term Bits per second (bps) Number of Bits Per Second 1 Kilobits per second (kbps) 1 thousand Megabits per second (Mbps) 1 million Gigabits per second (Gbps) 1 billion Terabits per second (Tbps) 1 trillion LAN bandwidth 10 Mbps: 10BASE2 (185m), 10BASE5 (500m) and 10BASE-T (100m) 100Mbps: 100BASE-TX (100m Cat 5 cable), 100 BASE-FX (2000m optic fiber), 1000Mbps: 1000BASE-TX (100m Cat5e cable), 1000BASE-SX (220m/550m optical fiber), 1000BASE-LX (500m single mode optical fiber) WAN bandwidth WAN connection Bandwidth Dial up 56Kbps ISDN 128Kbps DSL 128Kbps – 6.1Mbps T1 1.5Mbps T3 44.736 Mbps (28T1) STS1 (OC-1) 51.84Mbps STS3 (OC-3) 155.52Mbps STS48 (OC-48) 2.5Gbps STS192 (OC-192) 10Gbps Bandwidth planning Predict business demand Bandwidth is not free Reserve the upgrade option TCP/IP ISO OSI model Name 7 Application 6 Presentation 5 Session Description Interact with programs. Application protocols are HTTP, HTTPS, FTP, IMAP, SMTP, POP3, and Telnet Format conversion, encryption and decryption 3 Network Establish, maintain and terminate connection sessions between hosts Error recovery and segment. UDP and TCP are here. IP addressing and routing 2 Data Link MAC addressing and switching 1 Physical Defines the electrical and physical connections 4 Transport TCP/IP model Name Description Application Covers 3 layers of OSI model: Application, Presentation and Session ) Transport Transport Internet work Equals to Network Network Access Equivalent to Data Link and Physical Layer of OSI Encapsulation 1. Application layer add application protocol header. 2. Transport layer add TCP or UDP header and breaks into Segment which has TCP header and data. 3. Network layer adds logical address header and the PDU packets have IP header and data 4. Data link layer adds header including destination MAC address. Frame has Ethernet header, trailer and data. 5. Physical layer will be responsible to transmit bits (electrical signals) over the medium. De-encapsulation 1. According to the Ethernet encoding scheme, assemble received bits. 2. Frames would be delivered according to destination MAC address. 3. Or, the packet is routed to destination IP address. 4. Transport layer protocol (TCP) may assemble segment 5. Application layer will interpret the data from segments. PDU Bit Frame L1PDU for electrical signals L2PDU Packet L3PDU Segment L4PDU Bit L7PDU for data Question Any question? If you do not have question, please practice conversion calculation between binary and decimal numbering system. 1. Please convert decimal value 123, 240 and 255 to binary. 2. Please convert binary value 11001101, 10010011 and 00110011 into decimal value.