Powerpoint
advertisement

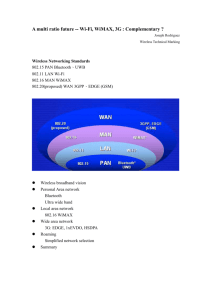
WIRELESS SECURITY Chapter 8 History • 1971 AlohoNet – Ethernet Protocol • 1997 1st version of 802.11 • 1999 Wi-Fi Alliance trade association US Frequency Bands Band Frequency range UHF ISM 902-928 MHz S-Band 2-4 GHz S-Band ISM 2.4-2.5 GHz (The higher than cell phones - frequency allows the signal to carry more data.). C-Band 4-8 GHz C-Band satellite downlink 3.7-4.2 GHz C-Band Radar (weather) 5.25-5.925 GHz C-Band ISM 5.725-5.875 GHz C-Band satellite uplink 5.925-6.425 GHz X-Band 8-12 GHz X-Band Radar (police/weather)8.5-10.55 GHz What do the waves look like? Wave Video Wireless Local Area Network (WLAN) • • • • • Connecting two or more systems using wireless 802.11 Standards WiFi uses radio waves Wireless cards are cheap Irda (direct line of sight – not as many security problems) 150 Feet Access Point/Hot Spots • An AP (access point also known as a AP) is the wireless server that connects clients to the internal network. AP’s typically act as a bridge for the clients. Wifi Wififreespot.com wi-fiplanet.com Boing.com Gogoair.com Antennas • Antennas come in all shapes and styles: – Omni-directional: • Vertical Whip • Ceiling mount – Directional: • Yagi (“Pringles can”) • Wall mounted panel • Parabolic dish HotSpots – Are they Safe? Piggybacking on someone’s else Wireless Internet • Google the name: David M. Kauchak Bluetooth Bluetooth • proprietary open wireless technology standard for exchanging data over short distances (using shortwavelength radio transmissions in the ISM band from 2400–2480 MHz) from fixed and mobile devices. • WiFi – replaces cables for your network vs. Bluetooth – replaces cables for your devices Bluetooth Bluetooth Attacks • Bluejacking -sends a message to a phone that you don’t know. Usually harmless. • Bluesnarking – is unauthorized access of information & often times retrieves information. • Blue bugging – similar to bluesnarking but leaves a backdoor and then the “hacker” can come and use the phone. Page 376-377 How to Secure Your Bluetooth • • • • Always Turn off your Bluetooth. Make Your Phone Visibility to Hidden. Set up a code when pairing devices Set your “Auto Connection without Confirmation” to No in all paired Devices. 802.11 Security Tools • http://sectools.org/tag/wireless/ • Airsnort http://freshmeat.net/projects/airsnort/ • Wepcrack http://sourceforge.net/projects/wepcrack • Netstumbler - http://www.netstumbler.com/ • Kismet - http://www.kismetwireless.net/