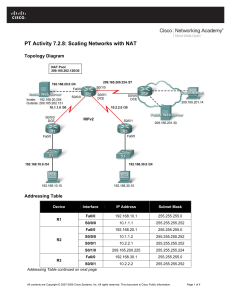
LAB Instructions Device R1 R2 R3 PC1 PC2 Server1 Interface F0/0 F0/1 Se0/0/0 F0/0 Se0/0/0 Se0/0/0 Se0/0/1 Se0/1/0 NIC NIC NIC IP 10.192.103.1 10.192.103.129 10.192.101.1 10.192.104.1 10.192.102.1 10.192.100.2 10.192.101.2 10.192.102.2 10.192.103.2 10.192.103.130 10.192.104.2 Subnet 255.255.255.128 255.255.255.128 255.255.255.252 255.255.255.0 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.252 255.255.255.128 255.255.255.128 255.255.255.0 Default Gateway N/A N/A N/A N/A N/A N/A N/A N/A 10.192.103.1 10.192.103.129 10.192.104.1 (PART - 1) Configure ip addresses on all devices in the network. Run OSPF on R1, R2 and R3. • All the hosts in the network must be able to ping each other. (PART - 2) Create ACL 150 • PC1 should not be able to access the web (only http). • However, make sure that HTTPS connection is successful. Create ACL 1 • Only devices from LAN 3 should be able to access VTY line in R3 Create named ACL Blocked_V. This name must match. • Only Server2 should be able to access VTY line in R4. (Note: R4 enable password: cisco) (PART - 3) Configure NAT overload or PAT on R3 • Create two ACLs using ACL number 10 to permit ip addresses that belongs to LAN 1 and LAN 3 • Link ACL 10 to the WAN facing interface for NAT • Configure appropriate inside and outside area. • Verify NAT by looking at the nat translations on R3.