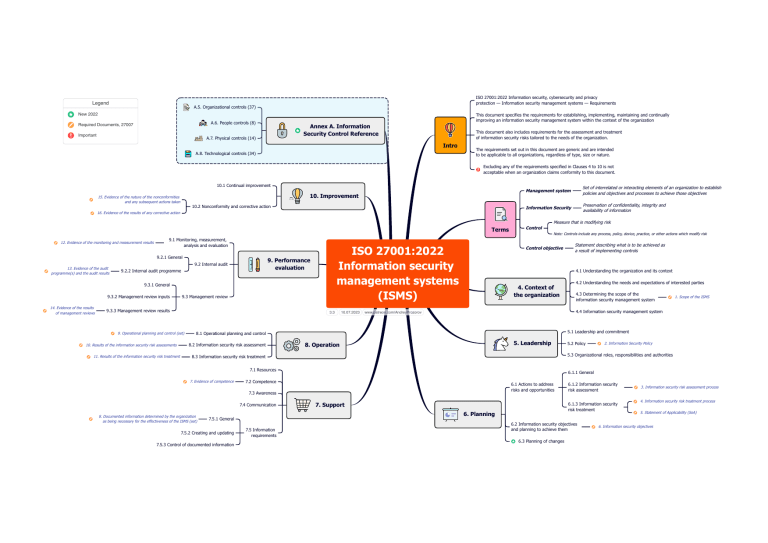
Legend I SO 27001:2022 Information security, cybersecurity and privacy protection — Information security management systems — Requirements A.5. Organizational controls (37) his document specifies the requirements for establishing, implementing, maintaining and continually T improving an information security management system within the context of the organization New 2022 A.6. People controls (8) Required Documents, 27007 Important Annex A. Information Security Control Reference A.7. Physical controls (14) his document also includes requirements for the assessment and treatment T of information security risks tailored to the needs of the organization. Intro A.8. Technological controls (34) he requirements set out in this document are generic and are intended T to be applicable to all organizations, regardless of type, size or nature. xcluding any of the requirements specified in Clauses 4 to 10 is not E acceptable when an organization claims conformity to this document. 10.1 Continual improvement 10. Improvement 15. Evidence of the nature of the nonconformities and any subsequent actions taken 10.2 Nonconformity and corrective action Management system et of interrelated or interacting elements of an organization to establish S policies and objectives and processes to achieve those objectives Information Security reservation of confidentiality, integrity and P availability of information 16. Evidence of the results of any corrective action Measure that is modifying risk Terms 12. Evidence of the monitoring and measurement results 9.1 Monitoring, measurement, analysis and evaluation 9.2.1 General 3. Evidence of the audit 1 programme(s) and the audit results I SO 27001:2022 Information security management systems (ISMS) 9. Performance evaluation 9.2 Internal audit 9.2.2 Internal audit programme 9.3.1 General 9.3.2 Management review inputs 14. Evidence of the results of management reviews 9.3 Management review 9.3.3 Management review results 3.3 9. Operational planning and control (set) 10. Results of the information security risk assessments 11. Results of the information security risk treatment 10.07.2023 Control Note: Controls include any process, policy, device, practice, or other actions which modify risk Control objective 4.1 Understanding the organization and its context 4. Context of the organization 8. Operation .1 Actions to address 6 risks and opportunities 7.5.2 Creating and updating 7.5.3 Control of documented information 7. Support 7.5 Information requirements 2. Information Security Policy .1.2 Information security 6 risk assessment .1.3 Information security 6 risk treatment 6. Planning 7.5.1 General 5.2 Policy 6.1.1 General 7.2 Competence 7.3 Awareness 8. Documented information determined by the organization as being necessary for the effectiveness of the ISMS (set) 1. Scope of the ISMS 5.3 Organizational roles, responsibilities and authorities 7.1 Resources 7.4 Communication .3 Determining the scope of the 4 information security management system 5.1 Leadership and commitment 5. Leadership 8.3 Information security risk treatment 7. Evidence of competence 4.2 Understanding the needs and expectations of interested parties 4.4 Information security management system www.patreon.com/AndreyProzorov 8.1 Operational planning and control 8.2 Information security risk assessment tatement describing what is to be achieved as S a result of implementing controls .2 Information security objectives 6 and planning to achieve them 6.3 Planning of changes 3. Information security risk assessment process 4. Information security risk treatment process 5. Statement of Applicability (SoA) 6. Information security objectives