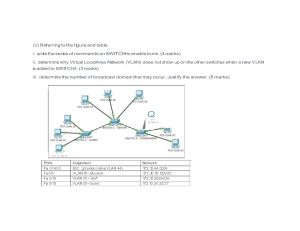
Simulation of Virtual LANs (VLANs) Using OPNET Khulood Salem Mohammed ALwasabi Faculty of Engineering, Computers and Control Engineering Department, Abstract: Virtual LANs (VLANs) offer a method of dividing one physical network into multiple broadcast domains. This paper simulates a VLAN using OPNET. Different scenarios are designed and simulated, where a step-by-step procedure using the workspace of OPNET is given. The first scenario will build a network for a university with two departments. Each department has three local area networks. One LAN is for the professors, the second is for the staff members, and the third is for the students. The university has three servers: one server is for research, the second is for human resources databases, and the third server is for online courses (e-learning). The second scenario uses VLANs to allow access to the research server only by professors. The staff members are allowed to access only the human resources server. The students can only access the e-learning server. The VLANs settings will not allow a hacker to have access to any of the servers. In the third scenario, a router is added to allow for communication between different VLANs. Here we will allow both the professors and students to communicate with each other and to have access to both the research and e-learning servers. The simulation results show us that VLANs also decrease the load on some of the links in the networks. Introduction Virtual LANs (VLANs) have recently developed into an integral feature of switched LAN solutions from every major LAN equipment vendor. A virtual LAN (VLAN) is any broadcast domain that is partitioned and isolated in a computer network at the data link layer (OSI layer 2). This is usually achieved on switch or router devices. Simpler devices only support partitioning on a port level (if at all), so sharing VLANs across devices requires running dedicated cabling for each VLAN. More sophisticated devices can mark packets through tagging, so that a single interconnect (trunk) may be used to transport data for various VLANs. Grouping hosts with a common set of requirements regardless of their physical location by VLAN can greatly simplify network design. A VLAN has the same attributes as a physical local area network (LAN), but it allows for end stations to be grouped together more easily even if they are not on the same network switch. VLAN membership can be configured through software instead of physically relocating devices or connections. Most enterprise-level networks today use the concept of virtual LANs. Without VLANs, a switch considers all interfaces on the switch to be in the same broadcast domain. In this lab, we will build a network for a university with two departments. Each department has three local area networks. One LAN is for the professors, the second is for the staff members, and the third is for the students. The university has three servers: one server is for research, the second is for human resources databases, and the third server is for online courses (e-learning). VLAN TYPES 1. No_VLAN Scenario : the setting of the network allows all members of computer into any of the network switches can also have access to the network servers. 2. VLAN Scenario: scenario uses VLANs to allow access to the research server only by professors. The staff members are allowed to access only the human resources server. The students can only access the e-learning server. The VLANs settings will not allow a hacker to have access to any of the servers. both departments to have access to all three servers. Even a hacker who plugs his or her. 3. The VLAN_Comm Scenario: Scenario a router is added to allow for communication between different VLANs. Here we will allow both the professors and students to communicate with each other and to have access to both the research and e-learning servers. The simulation results show us that VLANs also decrease the load on some of the links in the networks. VLAN Identifier (VID) VLAN Members 1111 Professors_A LAN, Professors_B LAN, and Research_Server. 2222 Staff_A LAN, Staff_B LAN, and HR_Server. 3333 Students_A LAN, Students_B LAN, and ELearning_Server. Table (1): shows the VLANs we plan to create and the members of each VLAN. |P age 1 Simulated Model Design Network Configuration : Each object in the VLAN Model (server, node, and application) has a specific set of parameters. In general those parameters can be classified as follows: • • Application Parameter: Application Attribute definition will be used to create user profiles; these profiles can be specified on different nodes in a network designed to generate the application traffic. Profile Parameter: Profile Attribute definition is used to specify/choose the required application among the available applications such as FTP, HTTP, Video, Voices, and Print etc. Figure 1: Configuration Profile different applications • Server Parameters: In each server, supported services are based on the user profiles that may support FTP, HTTP, VoIP, Video, etc.... • Nodes Parameters (PC): Network parameters are set for all nodes, such as workstations as shown in figure 2. Figure 2: Configuration node with applications |P age 3 Scenarios: Scenario #1: "NO_VLAN" This scenario generates network traffic without any separation between departments (classical network). To configure no VLANs, specify "NO_vlan" as the value for the "VLAN scheme" attribute on the switch devices which support VLANs. Switch devices, connected to gather by 100baseT links and each port in switch connection with several PC and the server. In the first case three network department is shown in figure 3. Figure 3: First scenario "No_vlan" with three Departments. • Scenario #2:" Vlan" The previous network has been modified and configured in order to generate three VLAN (1111, 2222, and 3333) as shown in figure 5. The procedure configuring VLAN is as follows: 1. Select Duplicate Scenario from the Scenarios menu and name it VLAN. 2. In the new scenario, select Switch_A , Switch_B , and ServersSwitch simultaneously . 3. Expand the VLAN Parameters hierarchy. Figure4: Edit the Supported VLANs attribute 4. Connected all the node with other,groub1(Professors_A LAN, Professors_B LAN, and Research_Server) the cables connected between them yellow color as shown figure 5. Figure 5: Group1 |P age 5 group2(Staff_A LAN, Staff_B LAN, and HR_Server.) the cables connected between them white color as shown figure 6. Figure 6: Group2 group3(Students_A LAN, Students_B LAN, and ELearning_Server.) the cables connected between them blue color as shown figure 7. Figure 7: Group3 • Scenario #3:" Vlan_Comm" The VLAN scenario members of each VLAN are not allowed to communicate with members of any other VLAN. Assume that we need students to have access to the Research_Server and we need the professors to have access to the ELearning_Server. In this case, we need VLAN1111 to communicate with VLAN3333. This can be done on the IP layer by configuring a router to forward traffic between the two VLANs. Each VLAN will be assigned its own IP subnetwork. Figure 8:vlan with router Now we need to assign the members of each VLAN to the same IP subnetwork. Figure 9: IP subnetwork |P age 7 Results – Evaluation This section introduces the results for the scenarios that highlight comparison between with and without VLAN mechanism on the network have different types of traffic. The results related to these scenarios are presented and analyzed in the following subsections. Figure 10: Show Animations Figure 11: Simulation Speed Figure 12: Simulation(ServerSwitch<->CenterSwitch) |P age 9 Figure 13: Simulation (Research_Server<->ServerSwitch) Figure 14: Simulation(Elearning_Server<>ServerSwitch) Figure15: Ethernet delay between three VLAN conclusion: When the number of PCs increased in a local area network, the need for configuring VLANs becomes necessary in order to reduce the traffic handled by the main switch. As it had been shown in the analysis Performed in this paper, increasing the number of VLANs reduce the traffic rapidly, can also control the size and composition of the broadcast domain by controlling the size and composition of a VLAN.This is due to the fact that VLANs creates many broadcast domains. The other conclusion is related to security. VLAN groups, many PCs into multiples LANs as if they are physically separated. The reduction in traffic using 3_vlans is around 50% with NO-vlan and increase reduced when moving to 6_vlans 60% with NO–VLAN. This means that a gain of an extra can be added to the overall network. Finally, the results also show that, advice on a VLAN is restricted to only communicate with devices that are on their own VLAN. Just as a router Reference: 1. Tambe, S. S., (2015) “Wireless technology in networks”, International Journal of Scientific and Research Publications 2. Rik Farrow, "VLAN INSECURITY on 2014-04-21http:// rikfarrow.com/Network/net0103.html.". 3. AlliedWare Plus™ OS, "Overview of |VLANs (Virtual LANs)", 2008 Allied T ele sis, Inc. | P a g e 11