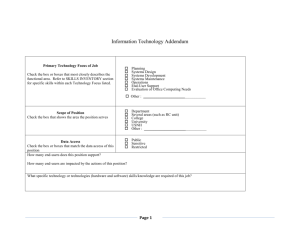
Page |1 Topic: “End-user computing – providing End-user services” CAPITAL UNIVERSITY OF SCIENCE AND TECHNOLOGY FINAL PROJECT REPORT Course: ITC (CSP1003) Semester: 02, Section: 03 Submitted To: Ma’am Saddaf Adalat Submitted By: Farwa Aman (BSP201028), Muqqadas Saba (BSP201002), Mutahra Arshad (BSP201006) Date: December 30, 2020 Page |2 Topic: “End-user computing – providing End-user services” END-USER COMPUTING - PROVIDING END USER SERVICES 1. END-USER IS SERVICES: End user IS services are divided into three main categories. End-User Training Desktop Architecture and Customization Desktop Services Commandeered with this obligation, end-user training handles technical job preparation and provides software training programs. The community for Desktop Design and Customization looks at the latest and greatest technologies in hardware and software. As required, they also customize settings. Process ownership is provided by Desktop Services. END-USER TRAINING: The End-User Training Group's duties include meeting the training needs of standard office automation software, such as electronic mail, as well as programs and/or systems created by internal staff via person and group instruction. The functions of end-user training are as follows: Developing course outlines, visual aids, and end user handouts for training classes offered. Participating in the evaluation and determination of standard office automation software products. Receiving and processing training requests. Scheduling training classes to ensure adequate levels of response to customer requests. Page |3 Topic: “End-user computing – providing End-user services” Evaluating effectiveness of courses and making changes as needed. Responsible for learning new and/or revised software applications to provide training as required. Responsible for developing useful documentation to support instruction. Researching new products to assess and recommend adequate support levels. Receiving training in developed applications to allow support in the customer environment. Maintaining student history of classes attended. DESKTOP ARCHITECTURE AND CUSTOMIZATION: Through focusing on desktop unit management as well as technology direction, the Desktop Architecture community offers continued development for the company. Desktop Customization offers services which specifically deal with productivity tools for end-users. The Desktop Customization group's key support problem is the development of end-user applications and ensuring that user-built system documentation is documented. The functions of Desktop Architecture and Customization are as follows: Responsible for capacity planning. Responsible for all aspects of software distribution: Testing. Interoperability. Rollout plan. Documentation. Defining standards and procedures. Responsible for configuration management. Providing peripherals support. Providing PC maintenance. Responsible for application standards. Responsible for virus control. Responsible for hardware installs. Providing remote desktop support. Providing level 3 support for unique and complex problems. Responsible for the analysis and implementation of productivity tools. Page |4 Topic: “End-user computing – providing End-user services” Providing training to lower-level desktop technicians. Responsible for establishing performance and tuning guidelines. Providing desktop analysis as required. Responsible for desktop automation practices. Responsible for requirements analysis. Responsible for software implementation. Responsible for end-user development management. DESKTOP SERVICES: Desktop Services provides all desktop customers with regular assistance. This is a laborintensive profession. The functions of the Desktop Services group include the following: Providing desktop patrol. Responsible for hardware and software installs. Responsible for level 2 support and troubleshooting. Implementing software distribution rollout. Maintaining inventory. Providing remote customer support (telecommuting). Responsible for telecommuting installs. Responsible for access administration. Responsible for desktop asset management. Providing procurement interface. Responsible for moves of desktop computing environment. FOCUS OF END USER IS SERVICE: Focus of End user IS service is helping organizations achieve their business objectives through their most important asset, their people. ROLE OF END USER IS SERVICE: 1. Provide a help desk service 2. Achieve standardization of software 3. Ensure network efficiency 4. Provide training 5. Deliver services to end users cost-effectively Page |5 Topic: “End-user computing – providing End-user services” 2. MANAGING NETWORK SERVICES: DEFINITION: Managed network services are networking software; functions and services that corporations outsource to a managed service provider to remotely run, track and maintain Managed Service Provider (MSP). Those businesses that don’t have enough resources to manage their own IT infrastructures, the best solution for it is to outsource managed network services to a managed service provider (MSP). The MSP can run, track and manage their respective IT environments by outsourcing these services. Managed network services range from basic network access and transport services like traditional leased WAN and LAN lines to newer software-defined WAN (SD-WAN) connections and virtual network services HISTORY OF MANAGING NETWORK SERVICES: For decades, network operators have provided managed services. An early example of a managed service established in the 1960s is Centrex, a managed private branch exchange (PBX) service. Centrex delivered enterprise telephony services remotely using telecommunications equipment and software operated by the telephone company and installed at switches in its headquarters, not at the premises of the customers. Over the years, managed services continued to adapt as networks changed. When the monopoly of the Bell System was broken up in 1984 and seven independent Regional Bell Operating Companies (RBOCs) were formed to provide local telephone services, some business customers wanted the option to negotiate with one provider instead of individually negotiating services with the RBOC. This has contributed to further growth in communication services under control. The 1996 Telecommunications Act led to the emergence of competitive local exchange carriers (CLECs) which in addition to the RBOCs, could provide communications services. Customers also had a broader variety of manufacturers from which to select. The primary managed service provider often handled its customers' ties to other service providers to ease the management of various connections with different service providers. Page |6 Topic: “End-user computing – providing End-user services” Application service providers (ASPs) originated in the 1990s to provide remote hosting services for applications. ASPs also paved the way for service providers to provide remote support for the IT infrastructure of clients. Since their service model varies from managed network services, these businesses are often referred to as MSPs or IT solution providers. MSPs started providing services to control new cross-provider virtual network services such as SD-WAN with the advent of software-based networking technologies around 2010. As a result, MSPs have gradually integrated SD-WAN into their portfolios of enterprise managed services, frequently collaborating to support the services with SD-WAN vendors. The availability of controlled SD-WAN services negates the need for businesses to manage multiple links based on their geographic positions with different service providers. BASIC NEEDS OF MANAGING NETWORK SERVICES: A Network that is Secure Efficient Workforce Reliable Internet and E-mail Access Secure Company Information ADVANTAGES OF MANAGING NETWORK SERVICES: Since they have minimal in-house IT capabilities and personnel, small and medium-sized companies also contract with MSPs and see managed network services as a way to obtain IT and networking skills without recruiting more employees. MSPs can manage problems with business networking, including integration, troubleshooting, technical support and policy setting. Managed network services are also a viable choice for enterprises who are interested in exploring emerging technology but are concerned about the costs and complexities involved. Managed network services also allow businesses to free up their current IT workers to concentrate on other tasks. This results in operational efficiency since when appropriate; MSPs can track and troubleshoot the necessary services. I. MINIMIZE RISK: As markets and industries are always evolving and developing at a rapid pace, any business investment has some degree of risk. They will bear all of the risk for you when you begin operating with a managed network service provider. Managed network providers know how Page |7 Topic: “End-user computing – providing End-user services” to avoid risk with their particular industry expertise and experience, especially with security and compliance issues. II. REDUCE AND CONTROL EXPANSES: Identifying where the expenses come from and finding out how they add up can be a problem when you're doing IT on your own. Based on your IT needs, a managed service company would be able to send you a line-by-line overview of where your expenses come from. And, since operating with a managed service provider would take your costs and turn them into a fixed cost expense, your expenditures will become regulated and more predictable. III. ENHANCE SECURITY: 70 percent reported not being prepared for a cyber-attack, according to a survey of over 4,000 organizations. Meanwhile, IBM reports that cybercriminals target companies an average of 16,858 times a year. It is important that companies of all sizes adopt some sort of IT protection to protect their networks and sensitive data with cybercrime on the rise. You will be able to collaborate with experts by partnering with a managed network service provider to improve the security for the entire voice and data network. To secure the company from malware, viruses, spam, and other cybercrime boats, the majority of managed service providers provide software and various goods. IV. STREAMLINE PRODUCTIVITY: The greatest benefit is that, when the service company’s deal with the rest, the service helps you to concentrate on making your company the best it can be. Businesses have limited capital, and there is limited time and energy for any business leader. Only when the networks are completely operational will an enterprise achieve its maximum potential. IMPORTANCE: Control IT Costs Gets You Access to Well-Tested Technology Gives You Qualified IT Specialists Strengthens Network Security Provides 24/7 Monitoring Guarantees Fast Response Times Gives Proactive Support Ensure Efficient Data Backup Page |8 Topic: “End-user computing – providing End-user services” BENEFITS OF MANAGING NETWORK SERVICES: Provides scalable and reliable IT solutions with the ability to extend them along with the developing market Improving the company's connectivity through the selection of the best network architecture impacts employee productivity and performance growth and lowers communication costs. Focus on its core activities and entrust high-class professionals with the development and maintenance of local area networks. 3. END-USER COMPUTING: DEFINITION: End-user computing (EUC) refers to computer systems and platforms that help nonprogrammers create applications. However, there's tons more to EUC and its related technology, virtual desktop infrastructure (VDI), which essentially hosts desktop environments on a central server. It's considered a sort of desktop virtualization. OBJECTIVE: The objective is to identify all the key applications or databases that are critical to daily operations and combine those into the same optimized platform as the desktops. USE: Now a days business require new ways to growth, remain successful, and to survive in business world. End User Computing affects how users, with multiple devices, are able to access their applications & data from anywhere at any time. Organizations typically arrange some form of VDI to provide secure access for EUC. Page |9 Topic: “End-user computing – providing End-user services” EUC must be implemented so that mobile workers can access the applications they need at the desired time and device. All-flash storage and converged infrastructure make the EUC implementation faster and easier. Allowing you to focus on delivering uninterrupted access instead of maintaining and configuring the underlying infrastructure. CASES USED BY END-USER COMPUTING: Many organizations are investigating how to use a hyper converged infrastructure (HCI) platform for their EUC initiatives. A few key use cases illustrate the value of building this solution, which is designed to support mixed workload environments without the need for specialized knowledge of compute, network, and storage platforms. I. REMOTE OFFICES: For organizations with a diverse physical footprint, it can be challenging to deliver consistent digital workplace resources. A EUC/VDI solution offers an opportunity to deliver improved consistency in the desktop and access to user applications in remote offices. It's easy to add new users and troubleshooting tasks can be minimized. II. COMPLIANCE AND LICENSING CONTROL: For organizations that are concerned with regulatory compliance, or that want to improve management of their software licensing, a EUC/VDI environment can deliver a centralized platform for all user desktops and applications. With this centralized platform, security can be tightly managed and software licensing can be controlled. The EUC/VDI environment can be designed to provide everything that users need to perform their jobs while closely maintaining the range of external software installations by individual users. III. REMOTE WORKERS AND BYOD USERS: Supporting a remote workforce is now mandatory in almost every organization. This reality requires a more diverse set of digital platforms. A EUC/VDI environment is the first step toward a hybrid multi-cloud experience that can support this diversity without breaking organizational standards of operation. And a EUC/VDI solution can be designed that provides desktops and applications so that remote users can easily consume them across multiple devices and can increase productivity while adhering to the organization's platform requirements. P a g e | 10 Topic: “End-user computing – providing End-user services” ADVANTAGE: Advances in cloud technology and integration have also greatly impacted EUC and VDI. Organizations now need multiple options to help enable worker productivity while also securing data, lowering costs, and managing highly variable workloads. A robust cloud infrastructure helps support that. A hybrid approach to physical, virtual and cloud desktops is inevitable – and a best practice. 4. THE IT HELP DESK: A help desk, in the context of IT, is a department inside an organization that is responsible for answering the technical questions of its users. Most major IT companies have set up help desks to respond to questions from their customers. The questions and their answers are usually transferred using e-mail, telephone, website, or online chat. Additionally, there are internal help desks aimed at offering the same form of help, but only for the employees within the organization. A standard help desk offers a single point of contact for users to get assistance. Normally, the help desks handle requests by using help desk software, or issue tracking system, which enables the help desk operators to keep track of the user requests using a unique identifier, easily find solutions to common queries, prioritize cases, and so on. HELP DESK SETUP: Depending on the size of the organization, a help desk can range from one person with a phone and a PC answering questions all the way up to a multi-national structure with thousands of agents aided By IT support software solutions. P a g e | 11 Topic: “End-user computing – providing End-user services” KEY FEATURES OF IT HELP DESKS: I. USER-FRIENDLY INTERFACE: Remember, an IT helpdesk will also be used by non-technical members of the organization. Therefore, it does not matter how advanced helpdesk software is if users cannot adapt to them easily. When deciding on an IT helpdesk, keep convenience in mind. Efficient software supports the learning curve of the employees who will use it. II. USER IMPORTATION: Every employee who will use the new helpdesk software needs to be imported as either a user or an agent. Depending on your company size, importing users/agents can take time. An IT helpdesk that allows user importation through the company’s active directory, Lightweight Directory Access Protocol (LDAP) or comma separated values (CSV) files will save you a lot of time. III. GROUPING USERS/AGENTS: Apart from tagging employees as either users or agents, the users also need to be grouped into locations or departments. On the other hand, the agents need to be grouped based on their knowledge level and skills set. This will help your organization with better ticket management. Agents with top skill sets can help in handling priority tickets. IV. EFFICIENT TICKET MANAGEMENT: An efficient ticket management and tracking system are one of the key features companies need when looking for an IT helpdesk. The software must be able to organize and monitor the active and passive tickets. Analyzing the software’s active ticket presentation is important. Depending on your servicelevel agreement (SLA) or business priorities, it is important to analyze how software presents active tickets. This will ensure that your business needs are in line with the ticket management system. Some tickets require the participation of multiple team members. There are also some tickets, which share a similar cause that can be grouped. An IT helpdesk that allows easy reassignment and escalation process can help team members fix tickets faster and improve workflow. P a g e | 12 Topic: “End-user computing – providing End-user services” V. EMAIL TO TICKETS CONVERSION: Sometimes, employees ask for help via email. Helpdesk software that can easily convert email inquiries into tickets will save time and effort and ensure faster transactions. VI. EASY ACCESS TO METRICS: Metrics allow teams to analyze their own performance and progress. An IT helpdesk must come with an analysis or evaluation of the tickets solved, as well as responses received. VII. FLEXIBLE CONFIGURATION: There is a lot of helpdesk software that can be tweaked to meet your business needs. This feature is incredibly important because it ensures that investment suits your business needs and goals. VIII. KNOWLEDGE BASE: An efficient IT helpdesk with a knowledge base can help teams work on tickets featuring recurring issues. Apart from saving time, a knowledge base, which is simply a database of historical incidents, can also help lighten the active workload. IX. SELF-SERVICE PORTALS: Helpdesk software that comes with a self-service portal will not just increase your business’ credibility, but it will also enable team members to resolve issues on their own. Through these portals, users must be able to submit their tickets and track them. These can also include answers to frequently asked questions and important announcements within the organization. X. SUPPORT FOR MULTIPLE REGIONS: This is especially important for multinationals. A single installation of IT helpdesk software must be able to support all regional offices around the world regardless of language, holiday, location, and time zone. XI. USER SATISFACTION: Apart from metrics, a use survey is important to help teams analyze their performance. Upon closing a ticket, an automated email must be sent to users with a link to a quick survey about their experience. P a g e | 13 Topic: “End-user computing – providing End-user services” FOR INTERNAL CUSTOMER IT questions, the help desk is supported by IT support Software like IT Service Management and its applications, including: Incident Management Problem Management Request Management Mobile Agent Agent Workspace Employee Service Center FOR EXTERNAL CUSTOMER REQUESTS: The help desk is enabled by customer support software solutions Like Customer Service Management. Good help desk software helps help desk agents to deal with a variety of end-user “contacts” are they related to incidents, requests for service or information, or complaints precisely once. RESPONSIBILITIES OF HELPDESK: Capturing and recording the relevant details of all incidents, requests, complaints, and other end-user issues. In addition to providing a means for help desk agents to enter those details, the help desk software also allows the direct capture from enduser self-service logging, email integration, and automatic capture from monitoring tools and devices. Allocating and routing issues to the appropriate help desk agents or directly to second- or third-line support staff. The help desk software will also manage the transfer of tickets between different help desk agents and resolution groups. Managing and reporting on ticket statuses, so staff and customers can easily check on the status and progress of their tickets. Management can also get visibility into help desk workloads, team and individual performance, service level achievement, and end-user customer satisfaction and feedback. Facilitating self-service to help reduce help desk workloads, with the help desk software’s knowledge base and knowledge management capabilities helping end users to help them. P a g e | 14 Topic: “End-user computing – providing End-user services” 5. END-USER DEVELOPMENT DEFINITION: EUD (End-User Development) is "a set of methods, techniques and tools that allow users of software systems, who are acting as non-professional software developers, at some point to create, modify, or extend a software artifact" USES OF EUD: End user development allows end users to modify or develop the user functionality and interface of software. End users know their personal framework and requirements better than anybody else and they usually have real-time understanding of shifts in their respective areas or fields that is why this is valuable. It tunes software to suit their needs more closely than would be possible without EUD. HISTORY: Prior to the 1980's, most computing occurred on mainframes controlled by professional developers in information systems departments. End users had little influence over the form and function of software running on a mainframe, which they generally viewed through simple terminal windows and controlled with simple textual commands. Spreadsheets were the first major EUD programming environment made possible by these innovations (Bricklin et al 1979), beginning with VisiCalc, then continuing with Lotus 1-2-3 and Excel. Although users of spreadsheet systems may not think of themselves as "doing programming," spreadsheet systems are programming environments because their formulas are first-order functional programs. In such programs, the formulas can refer to input "variables" (cell names) and the results of the formulas are computed output values. The availability of spreadsheet software was a major factor in spurring early demand for microcomputers. Newer technologies such as the web and mobile computing have since opened up increasingly diverse and powerful opportunities for end users to create and tailor software. I. TAILORING: Tailoring is any "activity to modify a computer application within its context of use". Tailoring encompasses specifying parameters to an existing application in a way that changes its behavior at a high level of granularity. P a g e | 15 Topic: “End-user computing – providing End-user services” II. END-USER PROGRAMMING (EUP): End-user programming (EUP) is defined as "programming to achieve the result of a program, rather than the program itself". The developer's goal is to actually use the program; this contrasts with professional programming, where the goal is to create a program for other people to use, often in exchange for monetary compensation. End users can perform EUP through a wide range of interaction styles: Programming using visual attributes Programming-by-demonstration Programming-by-specification Programming with text III. END-USER SOFTWARE ENGINEERING End-user software engineering (EUSE) is defined as "end-user programming involving systematic and disciplined activities that address software quality issues" EUSE combines the goal of EUP, which focuses on enabling end users to create software, with the concern for quality of that software across its entire lifecycle. This lifecycle includes: Requirements and Design Verification and Validation Debugging Code Reuse (in addition to actual implementation, which has already been described above in the context of EUP tools). FUTURE AND IMPLICATIONS OF EUD: EUD is likely to play an increasingly central role in shaping software to meet the broad, varied, rapidly changing needs of the world. Along the way, further research is needed to help end-user developers create and adapt new kinds of programs in new kinds of ways. The rise of EUD to date enables end users to respond to professional developers' backlog of software work, and to the reality that professional software developers are not likely to understand and plan for every user requirement when developing software. CHARECTERISTICS: 1. End user as the developer and maintainer. 2. The developer is the client; therefore there are no communication issues. 3. Small budget and/or short time period for development. P a g e | 16 Topic: “End-user computing – providing End-user services” ADVANTAGES OF END USER DEVELOPMENT: 1. Encourages active user participation 2. Improves requirements determination 3. Strengthens user sense of ownership 4. Increases speed of systems development DISADVANTAGES OF END USER DEVELOPMENT: 1. Inadequate expertise leads to underdeveloped systems 2. Lack of organizational focus creates "privatized" system 3. Insufficient analysis and design leads to subpar systems 4. Lack of documentation of a system may lead to its being short lived PRIMARY BENEFITS OF END USER DEVELOPMENT: 1. Faster Development Cycles: No waiting for approval(s) from an IT governance body. No wasted communication time in e-mails, instant messages, and phone calls between the business user(s) and the developer(s) and/or project manager(s) on the IT side. 2. Higher level of End User Satisfaction: The business user knows exactly what they want (even if they have a hard time fully explaining it). With this in mind, their self-developed results are very rarely anything less than “a bull’s-eye”. 3. Reduced IT Workload: IT will not need to budget, plan, hire, etc. for a pure EUD project; this will allow for funds, effort, and energy to be focused on more strategically important initiatives. 6. MANAGING EUC AS A PART OF IS STRATEGY: ROLE OF IS MANAGER: Setting’s the organization’s IS strategies covering issues such as integration with business strategy, investment level and whether services are centralized or decentralized. Establishing IS infrastructure (networks, hardware, and software services) implementation of corporate strategy through developing line of business system, ensuring that the company follows ethical or legal codes for health and safety and data protection. P a g e | 17 Topic: “End-user computing – providing End-user services” FIVE KEYS TO MANAGING END-USER COMPUTING: I. DRAFT POLICIES: Data governance, along with legal and compliance, needs to draft policies that include these apps under data protection standards. They should also recommend that EUC apps not contain sensitive personal data in the future. II. TAKE STOCK: EUC application management is challenging because most of these apps are stand alone and often hidden. Compliance teams may not even know that such apps exist. Data governance needs to create an inventory of these apps to enforce data protection. III. ANALYZE DATA: After EUC apps are identified, it is important to analyze data to see if there is any sensitive information in use. For example, using special categories such as race, age, etc., are direct violations. Appropriate remediation needs to be taken. IV. ESTABLISH DATA PROTECTION STANDARDS: After identifying the EUC apps and understanding the manner in which they use data, organizations need to establish data protection mechanisms, such as masking fields to conceal identity, when required. V. BRING EUC TO IT: The long-term goal for organizations should be to avoid using stand-alone EUC apps, and eventually bring them under the IT head so better monitoring and support is available. END-USER COMPUTING IS A LONG-TERM RESOURCE SOLUTION End-user computing is a long-term, forward-thinking resource management solution. MANAGEMENT APPROACH TO END USER COMPUTING: Management’s approach to EUC should be designed to fit in with the information systems strategy of the organization. The aim will always be to maximize the benefits and minimize the problems. Two factors needed to be managed: The rate of expansion The level of control P a g e | 18 Topic: “End-user computing – providing End-user services” THE RATE OF EXPANSION CAN BE MANAGED BY: 1. Making hardware/software easier/difficult to obtain. 2. Making information easier/difficult to obtain. 3. Imposing/relieving the end user department of the cost of EUC. THE LEVELS OF CONTROL OVER EUC IS MANAGED BY: 1. More or less restrictive standards over the purchases of hardware/software. 2. Level of requirement of mainframe use as compared to PC use for application. 3. Restrictions on access of data.